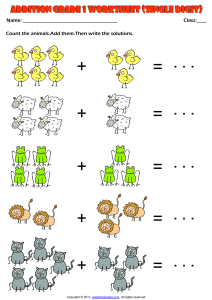
Week 1 Assignment for Applied Cryptography Fall 2023 Do the following five problems. 1. (5 points) We define an affine Caesar cipher acting on the digits 0-9 based on modulo 10 arithmetic. Specifically, the digit p = 0,…,9 is encrypted by c = a p + b (mod 10) for some fixed values a and b a. Show the complete mapping (i.e., what happens to all digits) for a = 7 and b = 6. b. Express the time (to the hour) that you do your homework in the 10digit form YYYYMMDDHH and encrypt it using the previous mapping. c. Show the complete mapping for a = 6 and b = 7. d. Using that mapping, show why one cannot decrypt the ciphertext 555. e. What restrictions are there, if any, on the value of b? Explain why. f. What restrictions are there, if any, on the value of a? Explain why. g. How many legitimate affine ciphers are there? h. For the mapping a = 7, b = 6, give an equation for decryption procedure. Show with an example that it works. 2. (3 points) Write down the powers of 8 modulo 11 for 8^1 to 8^10. Use this as a mapping from the numbers 1, …, 10 to the corresponding powers. x → y = 8^x (mod 11), x = 1, …, 10 The result should be a permutation of the integers 1, …, 10. Write down a sentence of at least 70 characters. Break the sentence into blocks of size ten. For each block, scramble it using the above mapping. That is, index the letters in a block with indices 1, …, 10, and then permute them based on the mapping, so position j goes to position 8^j mod 11 (positions indexed by 1 – 10). What can be observed in the resulting ciphertext? 3. (2 points) Using the Vigenère cipher, encrypt your name using the key cyber. Next, choose a phrase of the same length as your name. Find a key that can be used to encrypt this phrase into the same ciphertext. Discuss the implications as to why a brute force attack cannot work to find your original key. 4. (3.5 points) Alice and Bob agree to use a Playfair cipher to encrypt email texts sent to each other. Discuss how they could do this. You should address what information they need to exchange, how they would exchange, and how the protocol goes in general. In addition, answer: • What security goals could be achieved? Why? • What security goals are not achieved? Why? • Under what assumptions would this be a reasonable protocol? Discuss both security and practical implications. 5. (1.5 point) Check digits used to provide a redundancy check to a data field are widely used. See, for example, the Wikipedia page on check digit. One example is the algorithm used to provide the last digit in a 13-digit ISBN number. Look up the procedure to compute the ISBN-13 check digit, explain the procedure briefly, and run it on an example. Does the check digit provide for any security goal? Why or why not?