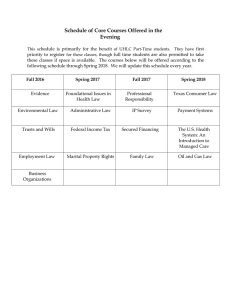
The Six Cybersecurity Challenges of ESInet Cybersecurity for Public Safety Timothy Lorello - President & CEO Tim.Lorello@SecuLore.com A few things before we begin… This webinar is being recorded. You will receive a follow-up email with the webinar presentation and recording. Ask any questions you have to the Questions box, we will address them at the end. Optional polls will be asked throughout the presentation and your participation is greatly appreciated! 04/11/2018 2 Presenters Tim Lorello - CEO • • • • • • • Former CMO (TCS) 15+ years public safety 5+ years cybersecurity 30+ years telecomm Guidance to FCC BA Physics, MSEE 20 patents Sean Scott - CTO • • • • • • Former CEO, CTO Resilience 30+ years IT/cybersecurity HW/SW architect/designer Numerous cyber products Electronic warfare specialist Veteran, USAF 04/11/2018 3 Public Safety Infrastructure Faces Cyber Threats HIGH VULNERABILITY FIRST LINE OF DEFENSE 24X7 = HIGH VALUE • 80% are small centers • Many PSAPs have inadequate cyber infrastructure • Most public safety personnel are not cyber trained HIGH THREAT ~6000 PSAPs & Dispatch Centers HIGH RISK OF 9-1-1 DISRUPTION • Ransomware payments for 2017 have doubled to $2B (Bitdefender) • 206 incidents have affected public safety agencies in 46 states over the last 24 months • SecuLore helped local MD county with recovery from Thanksgiving Day ransomware attack 04/11/2018 4 Public Safety Is Being Targeted SecuLore has recorded a total of 206 State & Local incidents in 46 states in the last 24 months! 04/11/2018 5 Cyber Attack Profiles Phishing An email attack, intended to make the victim take an action that installs malware on the victim’s machine Web site drive by A technique that lures a victim to an infected web site, thereby installing malware on the victim’s machine Ransomware Malware which, once activated on a victim’s machine, encrypts data that can only be unlocked by paying a ransom Persistent threat Malware that hides on a system and which either slowly leaks information to the attacker or awaits activation Hacking A brute-force attack method by which an attacker identifies a system vulnerability and then directly exploits that weakness 04/11/2018 6 Analysis of the 206 Cyber Incidents Most preferred vehicle Phishing Web site drive by In fastest decline Ransomware Persistent threat Largest Most undocumented Hack Fastest growing 04/11/2018 7 Poll: Which Cyber Attacks Are Unique to NG911? 1. Ransomware 2. Phishing 3. Brute Force Hacking 4. All of them 5. None of them 04/11/2018 8 Poll: Which Cyber Attacks Are Unique to NG911? 1. Ransomware 2. Phishing 3. Brute Force Hacking 4. All of them 5. None of them 04/11/2018 9 So Isn’t This Bad for NG9-1-1: an All-IP Network? Sounds Logical ✓ Cyber attacks occur on IP networks ✓ NG9-1-1 is an IP network ✓ Therefore cyber attacks will occur on NG9-1-1 networks! Let’s compare ESInet vulnerabilities to today’s challenges 04/11/2018 10 Legacy Networks: The Illusion of Cyber Safety How can a PSAP or Dispatch Center get hacked if it isn’t connected to the internet? 04/11/2018 11 An Historical View of the PSAP & 9-1-1 Response Voice PSTN The Layering Begins! Call Takers Dispatchers Public Safety Answering Point Dispatch Center I Don’t Need Anything! Except This!! 04/11/2018 12 We Need the Street Address of the Caller Voice PSTN ALI Call Takers Dispatchers So Let’s Get a Dedicated Data Line Public Safety Answering Point Dispatch Center 04/11/2018 13 Great Brokered Content Becomes Available Voice PSTN ALI Call Takers Dispatchers Public Safety Datasets Logs And those logs should be connected Public Safety Answering Point Dispatch Center Might as well get an ALI connection Brokered Content 04/11/2018 14 In Counties & Cities – Add the Support! Voice PSTN ALI Call Takers Dispatchers Public Safety Datasets Logs Brokered Content IT Network Administrative Public Safety Answering Point Dispatch Center 04/11/2018 15 Those Damn Hackers – Cybersecurity Needs Voice PSTN ALI Call Takers Dispatchers Public Safety Datasets Logs IT Network Administrative Public Safety Answering Point Dispatch Center 04/11/2018 16 If Your IT Team Is Clever – Segment the Networks PSTN ALI Call Takers Dispatchers Public Safety Datasets Logs IT Network Administrative Public Safety Answering Point Dispatch Center 04/11/2018 17 But The Firewall Runs Out of Ports – Routers! PSTN ALI Call Takers Dispatchers Public Safety Datasets Logs IT Network Administrative Public Safety Answering Point Dispatch Center Result: interconnected network segments, multiple routers, no firewalls on internal traffic 04/11/2018 19 Introducing ESInets – Core to NG911 Services Note Firewall not in PSAP 04/11/2018 20 The Six ESInet Cybersecurity Challenges1 Threat #1: The Citizen 04/11/2018 21 Poll: Which Two Hacks Affect Every Computer? 1. Bonnie & Clyde 2. Petya & NotPetya 3. Spectre & Meltdown 4. Donald & Hillary 5. WannaCry & WannaMine 04/11/2018 22 Poll: Which Two Hacks Affect Every Computer? 1. Bonnie & Clyde 2. Petya & NotPetya 3. Spectre & Meltdown 4. Donald & Hillary 5. WannaCry & WannaMine 04/11/2018 23 Smartphones Have Been Compromised All Android Phones Vulnerable to “Cloak and Dagger” Full Device Takeover Attack May 2017 – The Hacker News Android Malware 'Judy' Hits as Many as 36.5 Million Phones May 2017 – Fortune 41 percent of Android phones are vulnerable to 'devastating' Wi-Fi attack October 2017 – The Verge Hacked Android APKs Using CoinHive’s Script to Mine Monero on Compromised Phones January 2018 – Cryptovest iPhone hack that threatened emergency 911 system lands teen in jail October 2016 – Ars Technica John Kelly's personal cellphone was compromised, White House believes October 2017 – Politico iPhone 7 Compromised Several Times at Hacking Event November 2017 – Softpedia News Apple confirms iPhone, Mac affected by Meltdown, Spectre flaws January 2018 – ZDnet 04/11/2018 24 Encrypted Citizen Data Passes Through Firewalls Threat #1: The Citizen All endpoints in an ESInet must implement media security with SRTP as defined in RFC 3711 and SDP Security Descriptions for Media Streams as defined in RFC 4568. SRTP Security must be requested in all calls originated within an ESInet. If a call is presented to the ESInet with SRTP, SRTP must be maintained through the ESInet13. Sandbox Talk to your vendor!! …meaning that the compromised picture would pass through ESInet firewalls …requiring a sandbox 04/11/2018 25 The Six ESInet Cybersecurity Challenges2 Other ESInets Threat #2: Other ESInets/networks Other Networks 04/11/2018 26 ESInets Should Be Thoroughly Firewalled Firewalls between services Firewalls between networks Firewalls between ESInets Recommended architectures address this 04/11/2018 27 The Six ESInet Cybersecurity Challenges3 Threat #3: The Internet [Legacy] 04/11/2018 28 CyberBenchmark Discovered ESInet Vulnerabilty Expected only US traffic Instead, saw two-way traffic to 23 non-US destinations And one-way traffic to others How could this happen? 04/11/2018 29 ESInet Focuses on Citizen-Originated Data ESInet addresses data/calls from citizen – it might not address data from other sources 04/11/2018 30 But Modern PSAPs Access Many Data Types NLETS Google Facebook Twitter City/County Network CJIS Body Cam CDC Misconfigured Internet Access And some of those sources could be compromised 04/11/2018 31 Monitoring the ESInet (from the Inside) ESInet can be broadly protected, identifying unwanted traffic 04/11/2018 32 The Six ESInet Cybersecurity Challenges4 Threat #4: The Internet of Things [Legacy] 04/11/2018 33 The Internet of Things – It’s BIG! 04/11/2018 34 The Internet of Things and Public Safety 04/11/2018 35 IoT Is Already Here – Printers Printers are commonly targeted And printer manufacturers are responding 04/11/2018 36 IoT Is Already Here – VoIP Devices This is NOT an analog device (anymore)! 04/11/2018 37 IoT Is Already Here - Detectors 04/11/2018 38 Public Safety IoT Being Directly Targeted Hackers use ransomware to hit [District of Columbia] police closed-circuit camera network (01/27/2017) Hackers took 70% of CCTVs offline using ransomware 04/11/2018 39 Poll: Which BotNet Fueled DDoS Attacks? 1. RoboNet 2. Mirai 3. Reaper 4. Kraken 5. Mr. Robot 04/11/2018 40 Poll: Which BotNet Fueled DDoS Attacks? 1. RoboNet 2. Mirai 3. Reaper 4. Kraken 5. Mr. Robot 04/11/2018 41 IoT Is Fueling DDoS Attacks Closed Circuit TV DVRs Other Devices Mirai Command & Control Server 1 Software Engineering Institute Carnegie Mellon: 1.7M compromised devices Build the BotNet Brute force password hack: • Factory settings • Password dictionary Release the Mirai virus! Target a system Rentable for $100/hr 2 Imperva Incapsula, 3/2017 04/11/2018 42 Continuous Monitoring Detects Unwanted Traffic 04/11/2018 43 The Six ESInet Cybersecurity Challenges5 Threat #5: The Staff Member [Legacy] 04/11/2018 44 Staff Members Will Make Mistakes Half of people plug in USB drives they find in the parking lot April 2016 – The ‘A’ Register Using personal devices on Center network Using Center devices on personal network 04/11/2018 45 The Six ESInet Cybersecurity Challenges6 Threat #6: The IT Network Segment[Legacy] 04/11/2018 46 Example: Web Permit Server Takes Out 9-1-1 Monitor inside traffic Alerts sent to SOC Web Rep Web Web Server Web Server Web Server Web Server AV AV Employee AV Email Firewall AV Email Antispam AV Router ISP for Web Server PSAP Network WS WS WS WS WS 4 Layers of Protection Web reputation Firewall Email antispam Workstation antivirus ISP for Network Mamba Phish Monitor outside traffic Full data capture 04/11/2018 47 Hackers Used the IT Network to Spread PSTN Call Takers Dispatchers Public Safety Datasets Logs A Lateral Attack! IT Network Administrative Public Safety Answering Point Dispatch Center 04/11/2018 48 Legacy Agencies Share Local Cyber Threats Typical county internet traffic Darker color indicates greater amount of traffic 04/11/2018 49 NG911 Promises a Safer Public-Safety Network ESInet can be broadly protected, blocking unwanted traffic Unwanted traffic can still occur because of malware on internal systems (IoT?) 04/11/2018 50 The ESInet Six Cybersecurity Challenges Two are unique to NG911 – Four impact Legacy E911 Malware from citizens needs vendor attention PSAPs will get data via methods beyond ESInets Internet of Things will bring internal attack vectors Hackers know how to exploit staff and IT network Continuous Monitoring Can Catch Bad Traffic Monitor – Visualize - Protect 04/11/2018 51 Next Webinar May 9th, 2018 at 2pm EST Secure Communications: The Hacker’s Dream Timothy Lorello – President & CEO Tim.Lorello@SecuLore.com (410) 703-3523 04/11/2018 52 Questions? The Six Cybersecurity Challenges of ESInet Timothy Lorello Sean Scott President & CEO CTO Tim.Lorello@SecuLore.com Sean.Scott@SecuLore.com 04/11/2018 53 Next Webinar May 9th, 2018 at 2pm EST Secure Communications: The Hacker’s Dream Timothy Lorello – President & CEO Tim.Lorello@SecuLore.com (410) 703-3523 04/11/2018 54