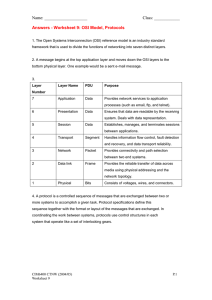
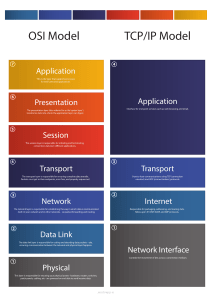
Computer Networks and Information Security UNIT - I DR.S.SRIDEVI, ASSOCIATE PROFESSOR, DEPARTMENT OF COMPUTER SCIENCE 1 21BCA5C10 Computer Networks and Information Security UNIT-I SURESH KUMAR S Assistant Prof, IT Department, STC, Pollachi Topic 1- Introduction to Network 3 Technology Revolution • 18th Century - The great mechanical systems accompanying the Industrial Revolution •19th Century - The age of the steam engine • 20th Century - The key technology was information gathering, processing, and distribution 4 Technology Revolution •During the first two decades of their existence, computer systems were highly centralized, usually within a single large room. •A medium-sized company or university might have had one or two computers •While very large institutions had at most a few dozen. 5 Technology Revolution The old model of a single computer serving all of the organization’s computational needs has been replaced by one in which a large number of separate but interconnected computers do the job. These systems are called computer networks. 6 What is a Computer Network The term ‘‘computer network’’ to mean a collection of autonomous computers interconnected by a single technology. Two computers are said to be interconnected if they are able to exchange information. 7 What is a Computer Network A set of communication elements connected by communication links ➭ Communication elements • Computers, printers, mobile phones, … • Routers, switches, ... ➭ Communication links • optic fiber • coaxial cable • twisted pair • wireless (radio, microwave, satellite) ➭ Topologies • Ring, Star, Bus, Tree, Mesh 8 What is a Computer Network A software/hardware infrastructure ➭ Share resources • data, files, computing power, video,… ➭ Information highway • communication between geographically dispersed users ➭ Electronic Society •Cyberspace •Virtual global nation 9 Introduction Computer Network – an interconnected collection of autonomous computers Internet: “network of networks” – loosely hierarchical – public Internet versus private intranet WWW a distributed systems run on the top of Internet Distributed System – High degree of cohesiveness and transparency – A software system built on top of a network 10 Uses of Computer Networks • • • • Business Applications Home Applications Mobile Users Social Issues 11 Business Applications of Networks a. Resource sharing (hardware, software, information, …) b. Providing communication medium (e-mail, videoconferenceing) c. Doing business electronically (B2B, B2C, e-commerce) A network with two clients and one server. 12 Goals of Networks for Companies Resource sharing: equipment, programs, data high reliability – replicated data – hardware Saving money – mainframe: 10 times faster, but 1000 times more expensive than PC – client-server model Scalability – mainframe: replace a larger one – client-server model: add more servers Communication medium for separated employees 13 Business Applications of Networks (2) a. Two processes are involved b. A communication network is needed • The client-server model involves requests and replies. 14 Home Network Applications • • • • Access to remote information Person-to-person communication Interactive entertainment Electronic commerce 15 Networks for People – Access to remote information • e.g.: financial, shopping, customized newspapers, on-line digital library, WWW – Person-to-person communication • email, video conference, newsgroup – Interactive entertainment • interactive movies or TVs, game playing 16 Home Network Applications (2) In peer-to-peer system there are no fixed clients and servers. 17 Home Network Applications (3) Some forms of e-commerce. 18 Mobile Network Users mobile-commerce Combinations of wireless networks and mobile computing. 19 Social Issues • • • • • • Politics Religion Sex Privacy Crime junk mail Each country has different laws. Debate rages! 20 Network Hardware • • • • • • Local Area Networks Metropolitan Area Networks Wide Area Networks Wireless Networks Home Networks Internetworks 21 Network Hardware Types of transmission technology • Broadcast links • Point-to-point links 22 Network Hardware – Broadcast networks • single communication channel shared by all machines • broadcasting or multicasting (via packets) – broadcasting: a special code in address field – multicasting: reserve one bit to indicate multicasting, the remaining n-1address bits can hold a group number. Each machine can subscribe to any groups • used by localized networks (or satellites) – point-to-point networks • many hops • routing algorithms: multiple routes are possible • used by large networks 23 Classification of interconnected processors by scale 24 Local Area Networks (LANs) · Characterics of LANs: (a) privated-owned, (b) small size, (c) transmission technology, (d) topology · Ethernets are most popular (up to 10 Gb/s) Two broadcast networks (a) Bus (b) Ring 25 Local Area Networks Characteristics – small size – transmission technology • single cable • 10Mbps ~ 10Gb/s • 10Gb/s : 10,000,000.000 bps – topology: • bus – Ethernet (IEEE 802.3): 10 or 100 Mbps (10Gb/s) • ring – IBM token ring (IEEE 802.5): 4 or 16 Mbps Channel allocation of broadcast networks – static: each machine has an allocated time slot – dynamic 26 Metropolitan Area Networks A metropolitan area network based on cable TV. 27 Wide Area Networks (WANs) ·WANs are point-to-point networks ·WANs consist of two distinct components: transmission lines (copper, fiber, microwave) and switches (electronics, optics) Store-and-forward or packet-switched subnet Relation between hosts on LANs and the subnet. 28 Network Topology 29 Subnet (WANs) Subnet (WANs) is consists of two components: – transmission lines (circuits, channels, trunks) • move bits between machines – switching elements • connect transmission lines • Router: also called packet switching nodes, intermediate systems, and data switching exchanges • Operate in store-and-forward, or packet-switched mode. 30 Wide Area Networks (2) Routing decisions are made locally· How A makes that decision is called the routing algorithm. Will be studied in detail in Chapter 5. A stream of packets from sender to receiver. (virtual- circuit) 31 9/17 End Wireless Networks Categories of wireless networks: • System interconnection (short-range radio, e.g. Bluetooth) • Wireless LANs (802.11a, 802.11b, 802.11g) • Wireless WANs (802.16, Cellular telephones, Satellites) • Wireless sensor networks 32 Wireless Networks (2) (a) Bluetooth configuration (b) Wireless LAN 33 Wireless Networks (3) (a) Individual mobile computers (b) A flying LAN 34 Home Network Categories Computers (desktop PC, PDA, shared peripherals) Entertainment (TV, DVD, VCR, camera, stereo, MP3) Telecomm (telephone, cell phone, intercom, fax) Appliances (microwave, fridge, clock, furnace, airco., light) Telemetry (utility meter, smoke/burglar alarm, babycam). 35 Fundamentally different properties 1. Devices have to be easy to install 2. The network and devices have to be foolproof in operation 3. Low price is essential 4. The network needs sufficient capacity ( for multimedia application) 5. The network interface and wiring have to be stable for many years 6. Security and reliability will be very important (minimize false alarm or misalarm) Home networks may be wired or wireless 36 Internetworks • • • • Internetworks connect networks with different hardware and software A collection of interconnected networks is called an internetwork or internet Internet is one specific internet Gateways are used to make the connection and to provide the necessary translation (protocol convertion) 37 Network Software Network Software • • • • • Protocol Hierarchies (Layer structure) Design Issues for the Layers Connection-Oriented and Connectionless Services Service Primitives The Relationship of Services to Protocols Network Software Protocol Hierarchies – a series of layers (levels) – lower layer provides service to higher layers – protocol: • an agreement between the communication parties on how communication is to proceed – Peers: • the corresponding layers on different machines. – Network architecture: a set of layers and protocols – Protocol stack: • a list of protocols used by a certain system, one protocol per layer Network Software Protocol Hierarchies Virtual Communication Peer Physical Communication Layers, protocols, and interfaces. Network Architecture: A set of layers and protocols Protocol Stack: A list of protocols used by a certain system, one protocol per layer. Network Software Layering ➭ To make things simple: modularization ➭ Different layer has different functions ➭ Create layer boundary such that • description of services can be small • number of interactions across boundary are minimized • potential for interface standardized ➭ Different level of abstraction in the handling of data (e.g., syntax, semantics) ➭ Provide appropriate services to upper layer ➭ Use service primitives of lower layer Protocol Hierarchies (2) The philosopher-translator-secretary architecture. Protocol Hierarchies (3) Message segmentation Encapsulation Example information flow supporting virtual communication in layer 5. Design Issues for the Layers • • • • • Addressing (telephone number, e-mail address, IP address,…) Error Control (error correction codes, ARQ, HARQ,…) Flow Control (feedback-based, rate-based) Multiplexing (gathering several small messages with the same destination into a single large message or vice versa Demultiplexing) Routing (directing traffic to the destination) Design Issues for Layers Identify senders and receivers – multiple computers and processes: addressing Data transfer – simplex, half-duplex, full-duplex communication – # of logical channels per connections, priorities Error control – error detection – error correction Sequencing of pieces Design Issues for Layers Flow control – feedback from the receiver – agreed upon transmission rate Length of messages – long messages: disassemble, transmit, and reassmeble messages – short messages: gather several small messages Multiplexing and Demultiplexing – when expensive to set up a separate connection – needed in physical layer Routing: split over two or more layers – High level: London -> France or Germany -> Rome – Low level: many available circuits Connection-Oriented and Connectionless Services Six different types of service. Service Primitives (Operations) A service is formally defined by a set of primitives (operations) available to a user process to access the services. Five service primitives for implementing a simple connectionoriented service. Service Primitives (2) If the protocol stack is located in the operating system, the primitives are normally system calls. Packets sent in a simple client-server interaction on a connection-oriented network. Services to Protocols Relationship ·The service defines what operations the layer is prepared to perform on behalf of its users ·A service is a set of primitives that a layer provides to the layer above it. ·A protocol is a set of rules governing the format and meaning of the packets which are exchanged by the peer entities in the same layer. Services related to the interfaces between layers; Protocols related to the packets sent between peer entities on different machine. Service Users Service Providers The relationship between a service and a protocol. Reference Models • • • • • The OSI Reference Model The TCP/IP Reference Model A Comparison of OSI and TCP/IP A Critique of the OSI Model and Protocols A Critique of the TCP/IP Reference Model OSI Reference Model • Reference Model gives a conceptual framework that standardizes communication between heterogeneous networks. •OSI Reference model is based on a proposal developed by the International Standards Organization (ISO) as a first step toward international standardization of the protocols used in the various layers (Day and Zimmermann, 1983). • It was revised in 1995 (Day, 1995). • The model is called the ISO-OSI (Open Systems Interconnection) Reference Model because it deals with connecting open systems, i.e. systems that are open for communication with other systems. Principles that were applied to arrive at the seven layers • A layer should be created where a different abstraction is needed. • Each layer should perform a well-defined function. • The function of each layer should be chosen with an eye toward defining internationally standardized protocols. • The layer boundaries should be chosen to minimize the information flow across the interfaces. • The number of layers should be large enough that distinct functions need not be thrown together in the same layer out of necessity and small enough that the architecture does not become unwieldy. The OSI layers 1. 2. 3. 4. 5. Physical Layer Data Link Layer Network Layer Transport Layer Session Layer 6. Presentation Layer 7. Application Layer The Physical Layer •Tansmits raw bits over a communication channel. •Design issue : To make sure that when one side sends a 1 bit, it is received by the other side as a 1 bit, not as a 0 bit. The Data Link Layer •The sender break up the input data into data frames and transmits the frames sequentially. If the service is reliable, the receiver confirms correct receipt of each frame by sending back an acknowledgement frame. •Design Issues: Error Handling - To transform a raw transmission facility into a line that appears free of undetected transmission errors to the network layer. Flow Control - To keep a fast transmitter from drowning a slow receiver in data - Some traffic regulation mechanism is needed to let the transmitter know how much buffer space the receiver has at the moment. These two issues are frequently integrated. The Network Layer The network layer controls the operation of the subnet. Design issues: • How packets are routed from source to destination. •Routes can also be determined at the start of each conversation, •Routes can be highly dynamic, based on the current network load. • To control congestion in the network layer • Quality of service provided •When a packet has to travel from one network to another to get to its destination, many problems can arise. The addressing used may be different The packet size may vary The protocols may differ, and so on. .. Other Issues in the Network Layer a packet has to travel from one network •When to another to get to its destination, many problems can arise. •The addressing used may be different •The packet size may vary •The protocols may differ, and so on. .. •The network layer have to overcome all these problems to allow heterogeneous networks to be interconnected. •In broadcast networks, the routing problem is simple, so the network layer is thin or nonexistent. The Transport Layer •The basic function is to accept data from above, split it up into smaller units if needed and pass these to the network layer. Design Issues: •To ensure that the pieces arrive correctly at the other end. •To determine what type of service to provide to the session layer, and, also to the users of the network. The most popular type - an error-free point-to-point channel. Transporting of isolated messages. Broadcasting of messages to multiple destinations. (The type of service is determined when the connection is established.) The transport layer is a true end-to-end layer, all the way from the source to the destination. •A program on the source machine carries on a conversation with a similar program on the destination machine, using the message headers and control messages. •In the lower layers, the protocols are between each machine and its immediate neighbours, and not between the ultimate source and destination machines, which may be separated by many routers. The Session Layer To establish sessions between users on different machines. Sessions offer various services: •Dialog Control - keeping track of whose turn it is to transmit •Token Management - preventing two parties from attempting the same critical operation at the same time •Synchronization check pointing long transmissions to allow them to continue from where they were after a crash The Presentation Layer •It is concerned with the syntax and semantics of the information transmitted. • For computers with different data representations to communicate, abstract data structures can be defined along with a standard encoding to be used. •This layer manages these abstract data structures and allows higher-level data structures to be defined and exchanged. The Application Layer •The application layer contains a variety of protocols that are commonly needed by users. •One widely-used application protocol is HTTP (Hypertext Transfer Protocol), which is the basis for the World Wide Web. When a browser wants a Web page, it sends the name of the page it wants to the server using HTTP. The server then sends the page back. •Other application protocols are used for file transfer, electronic mail, and network news. Questions The OSI model has _______ layers. a) 4 b) 5 c) 6 d) 7 Which layer is responsible for process to process delivery? a) network layer b) transport layer c) session layer d) data link layer Which layer links the network support layers and user support layers a) session layer b) data link layer c) transport layer d) network layer Which layer provides the services to user? a) application layer b) session layer c) presentation layer d) none of the mentioned OSI stands for a) open system interconnection b) operating system interface c) optical service implementation d) none of the mentioned The TCP/IP Protocol Suite •The TCP/IP protocol suite was developed prior to the OSI model. •Therefore, the layers in the TCP/IP protocol suite do not match exactly with those in the OSI model. •The original TCP/IP protocol suite was defined as four software layers built upon the hardware. •Today, however, TCP/IP is thought of as a five-layer model with the layers named similarly to the ones in the OSI model. Layers in the TCP/IP Protocol Suite TCP/IP reference model has only 4 layers, 1. Host-to-Network Layer 2. Internet Layer 3. Transport Layer 4. Application Layer The TCP/IP internet layer is similar in functionality to the OSI network layer Host-to-Network Layer •The host has to connect to the network using some protocol so it can send IP packets to it. •This protocol is not defined and varies from host to host and network to network. Internet Layer •This layer holds the whole architecture together. •It allows hosts to inject packets into any network and let them travel independently to the destination (potentially on a different network). They may even arrive in a different order than they were sent, in which case it is the job of higher layers to rearrange them, if in-order delivery is desired. •The internet layer defines an official packet format and protocol called IP (Internet Protocol) - It delivers IP packets to their respective destinations. Major issues: Packet Routing Congestion Control The Transport Layer •It is designed to allow peer entities on the source and destination hosts to carry on a conversation, just as in the OSI transport layer. •Two end-to-end transport protocols are defined here: TCP (Transmission Control Protocol) - Reliable Connection-oriented Protocol UDP (User Datagram Protocol) – Unreliable Connectionless Protocol TCP (Transmission Control • Protocol) It is a reliable connection-oriented protocol that allows a byte stream originating on one machine to be delivered without error on any other machine in the internet. • It fragments the incoming byte stream into discrete messages and passes each one on to the internet layer. • At the destination, the receiving TCP process reassembles the received messages into the output stream. • TCP also handles flow control to make sure a fast sender cannot swamp a slow receiver with more messages than it can handle. UDP (User Datagram Protocol) • It is an unreliable, connectionless protocol for applications that do not want TCP's sequencing or flow control and wish to provide their own. • It is also widely used for client-server-type request reply queries and applications in which prompt delivery is more important than accurate delivery, such as transmitting speech or video. Relationship of IP, TCP &UDP The Application Layer • • • The TCP/IP model does not have session or presentation layers. On top of the transport layer is the application layer. It contains all the higher-level protocols like TELNET, FTP, SMTP,... – – – TELNET - The virtual terminal Protocol allows a user on one machine to log onto a distant machine and work there. FTP - The File Transfer Protocol provides a way to move data efficiently from one machine to another. SMTP – The Simple Mail Transfer Protocol - specialized protocol developed for Electronic mail transfer. – Many other protocols have been added to these over the years: • The Domain Name System (DNS) for mapping host names onto their network addresses, • Hyper Text Transfer Protocol (HTTP) for fetching pages on the World Wide Web, ..... Questions TCP/IP reference model contains how many layers a) 3 b) 4 c) 6 d) 7 Which layer is responsible for process to process delivery? a) network layer b) transport layer c) session layer d) data link layer TCP/IP model was developed _____ the OSI model. a) prior to b) after c) simultaneous to d) none of the mentioned TCP/IP model does not have ______ layer but OSI model have this layer. a) session layer b) presentation layer c) application layer d) both (a) and (b) Telnet A)allows user to connect client machine B)transferring files C)sharing files D)none of above The design principle of the OSI reference model • • • • • A layer should be created where a different abstraction is needed Each layer should perform a well defined function The function of each layer can be chosen as an international standard The layer boundaries should be chosen to minimize the information flow across the interfaces The number of layers should be not too large or not too small Reference Models The OSI reference model. The functions of the seven layers • • • • • • • The physical layer is concerned with transmitting raw bits over a communication channel The data link layer performs flow control and also transforms a raw transmission facility into a line that appears error free (ARQ) The network layer controls the operation of the subnet, e.g. routing, flow control, internetworking,… The transport layer performs assembling and disassembling, isolates the upper layers from the changes in the network hardware, and determines the type of services The session layer establishes sessions (dialog control, …) The presentation layer is concerned with the syntax and semantics The application layer contains a variety of commonly used protocols (e.g. Hyper Text Transfer Protocol for WWW, file transfer, e-mail, network news,…) Reference Models (2) The TCP/IP reference model. Reference Models (3) Protocols and networks in the TCP/IP model initially. Comparing OSI and TCP/IP Models Concepts central to the OSI model • Services: defines layer’s semantics • Interfaces: tells the processes above it how to access it. • Protocols Probably the biggest contribution of the OSI model is to make the distinction between these three concepts explicit. A Critique of the OSI Model and Protocols Why OSI did not take over the world • Bad timing • Bad technology • Bad implementations • Bad politics Bad Timing investment opportunity new discovery right time to make The apocalypse of the two elephants. Bad Technology • • • The choice of seven layers was political - session and presentation layers are nearly empty - Data and network layers are overfull The OSI model is extraordinarily complex Some functions e.g. addressing, flow control, error control reappear again and again Bad Implementations • Huge, Unwieldy, and Slow Bad Politics • bureaucrats involved too much (European telecommunication ministries, community, us government) A Critique of the TCP/IP Reference Model Problems: • Service, interface, and protocol not distinguished • Not a general model • Host-to-network “layer” not really a layer (is an interface) • No mention of physical and data link layers • Minor protocols deeply entrenched, hard to replace (The virtual terminal protocol, TELNET, was designed for mechanical teletype terminal) Hybrid Model The hybrid reference model to be used in this book.