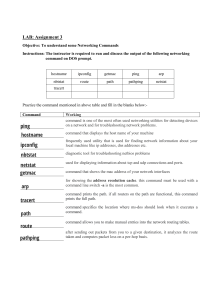
IT Network Security Lab #01 B. Tech CSF V Semester By: Dr. Akashdeep Bhardwaj Lab Objective: Troubleshoot Network without using tools Description: Perform basic network information gathering without using any tools, use just Windows command line utilities to gather network information OR troubleshoot. These commands can also be used to run living-off-the-land (LOTL) commands when connected on any victim’s system remotely & using in form of ‘Fileless Malware’ attacks. Attackers are increasingly making use of tools already installed on targeted computers or are running simple scripts and shellcode directly in memory. Creating less new files on the hard disk means less chance of being detected by traditional security tools and therefore minimizes the risk of an attack being blocked. Requirements: • Windows 10 OS/VM • Administrator privileges to run commands Step 1: Logon as Admin to the Windows OS. Step 2: Check execution of the below mentioned commands. 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. Objectives List IP configuration, host name, adapter installed and MAC address View/Access the Windows OS Group Policies implemented Flushe the DNS resolver cache of the system Discover who is logged/connected to the system Purge and reload the remote cache name table Lists local NetBIOS names Detect error when browsing WINS or NetBIOS The ‘b’ switch links each used port with its application Shows open ports of the Windows system Retrieve list of network connections Show user accounts for the computer Specifies computers available in a specific domain Resolve IP to Hostname (try using Facebook or Twitter IP) Shows the Logon server Confirms whether the port is open Locates lines with number 15868 and redisplays every one second 17. Shows open ports with LISTENING status Commands C:\> ipconfig /all C:\> Gpresult Ipconfig /flushdns nbtstat -a <System name> nbtstat -R nbtstat -n nbtstat -r netstat -ab netstat -an net use net user net view / domain ping -a <IP Address> set L telnet <IP> <port> netstat -an 1 | find “15868” netstat -an | find “LISTENING” Step 3: Create a batch file of the following commands and execute them on your VM. 1. Information Gathering done by Hacker Group ‘Waterbug’ • Systeminfo • net view • net view /domain • tasklist /v • gpresult /z • netstat –nao • ipconfig /all • arp –a • net share • net use • net user administrator • net user /domain • net user administrator /domain • tasklist /fi • dir %systemdrive%\Users\*.* • dir %userprofile%\AppData\Roaming\Microsoft\Windows\Recent\*.* • dir %userprofile%\Desktop\*.* 2. Information Gathering done by Hacker Group ‘Appleworm/Lazarus’ • hostname • whoami • ver • ipconfig -all • ping www.google.com • query user • net user • net view • net view /domain • reg query \"HKCU\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\" • tasklist /svc • netstat -ano | find \TCP\ • msdtc [IP] [port] 3. Information Gathering done by Hacker Group ‘Billbug’ • net user • ipconfig /all • net start • systeminfo • gpresult Lab #01 Assignment: Execute the commands for each hacker group on the victim VM. You have a choice to execute them using batch files or MSF payloads or document macros to run them automatically. Gather the output in screenshots as objective for this lab for each of the group’s attack commands. Note: • Submit only WORD DOCX. Do not copy experiments from others OR share your work with others. • Those who copy from others or share their documents with others will be graded as ZERO.