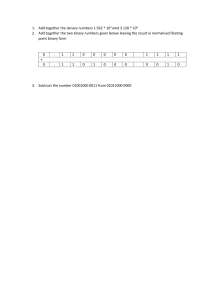
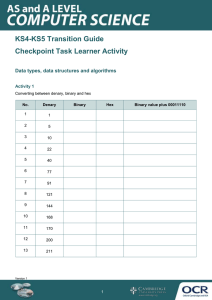
Cambridge IGCSE Computer Science Student Book (Greg Shilton, Megha Goel) (Z-Library)
advertisement

Cambridge IGCSETM Computer Science For over 60 years Marshall Cavendish Education has been empowering educators and students in over 80 countries with high-quality, research-based, Pre-K-12 educational solutions. We nurture world-ready global citizens by equipping students with crucial 21st century skills through our resources for schools and education centres worldwide, including Cambridge schools, catering to national and international curricula. The Marshall Cavendish Education Cambridge IGCSETM Computer Science series is designed for students studying for the Cambridge IGCSE and IGCSE (9–1) Computer Science syllabuses (0478/0984). The series focuses on developing important computer science skills relevant to real-world applications. SB The Student’s Book: • Encourages active and inquiry-based learning through hands on activities and discussions • Supports subject literacy with concise language, language support and bite-sized concepts • Caters to the international landscape with multicultural photographs, visuals and other references • Promotes visual learning through concept infographics and clear illustrations • Includes mind maps and links that build learners’ understanding of the relationships between concepts • Nurtures life-long learning in building digital literacy skills which students can use beyond their course • Helps students develop 21st century competencies, so that they become future-ready ✓ Supports the full Cambridge IGCSE and IGCSE (9–1) Computer Science syllabuses (0478/0984) for examination from 2023. ✓ Has passed Cambridge International’s rigorous TM Computer Science STUDENT’S BOOK STUDENT'S BOOK This resource is endorsed by Cambridge Assessment International Education Cambridge IGCSE Series architecture • Student’s Book • Workbook • Teacher’s Guide • e-book quality-assurance process ✓ Developed by subject experts ✓ For Cambridge schools worldwide ISBN 978-981-4941-59-4 Greg Shilton Megha Goel 9 789814 941594 C01(S)IGCSECS_SB_Cover.indd All Pages 12/5/21 11:11 AM Cambridge IGCSE TM Computer Science Greg Shilton Megha Goel SB CS PP.indb 1 STUDENT’S BOOK 14.5.21. 14:13 © 2021 Marshall Cavendish Education Pte Ltd Published by Marshall Cavendish Education Times Centre, 1 New Industrial Road, Singapore 536196 Customer Service Hotline: (65) 6213 9688 E-mail: cs@mceducation.com Website: www.mceducation.com First published 2021 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior permission of the copyright owner. Any requests for permission should be addressed to the Publisher. Marshall Cavendish is a registered trademark of Times Publishing Limited. ISBN 978-981-4941-59-4 Printed in Singapore Questions and answers have been written by the authors. Third-party websites and resources referred to in this publication and videos linked to the Watch feature have not been endorsed by Cambridge Assessment International Education. SB CS PP.indb 2 14.5.21. 14:13 The publisher would like to acknowledge the following who have kindly given permission for the use of copyright materials. Chapter 1 p.1 Futuristic technology concept, Mixed media, Innovations data systems connecting people and robots devices. AI, Artificial Intelligence, Robotic hand on blue circuit board background. Innovative technologies and communication, © Pop Nookunrat dreamstime.com; p.2 Two hands on a white background, fingers © Sergii Galkin dreamstime.com; p.16 Simple vector illustration. The icon baseball cap, © Dychek dreamstime.com; p.17 Voice wave isolated on white background. Voice visualisation in simple black and white monochrome style. Voice icon, vector, © Seveniwe dreamstime.com; Chapter 2 p.21 Double exposure of businessman use smartphone, communication node tower or 4G 5G network telephone cellsite and cityscape urban at sunset as business, technology and telecom concept, © Thissatan Kotirat 123rf.com; p.23 cable on network switches background, © wklzzz 123rf.com; p.26 Beautiful mature woman talking on phone at creative office. Happy smiling businesswoman answering telephone at office desk. Casual business woman sitting at her desk making telephone call and taking notes on notebook. © rido 123rf.com; p.26 Realistic usb cable connectors types set of images with modern types of usb plugs and sockets vector illustration © macrovector 123rf.com; p.27 corrupted data. red binary code with missing pieces. computer technology problem virus error darknet and hacking background. computer language data transfers © suebsiri 123rf. com; p.28 Close up of a barcode © Alain Lacroix dreamstime.com; p.29 Closeup on the screen with depth of field and focus on the padlock. The image is a security concept in the search engine and web browser address. Hyper Text Transfer Protocol Secure (https). © ktsdesign 123rf.com; p.30 Data encryption concept with a screen full of hexidecimal information and padlock symbol © Anthony Brown 123rf.com; Chapter 3 p.33 On board are capacitors resistors, slots, integrated circuits, diodes, microprocessor © jk21 123rf.com; p.34 Macro view of CPU socket on PC computer motherboard © scanrail 123rf.com; p.36 colour cable bus isolated on white background © Nadezhda Tsarenko 123rf.com; p.36 DDR RAM memory module isolated on white background © Volodymyr Krasyuk 123rf.com; p.38 CPU Microprocessor. Flat style icon on transparent background © asmati 123rf.com; p.39 Touching a monitor with navigation map of the modern car, close-up view © Olena Kachmar 123rf.com; p.40 hands on keyboard © Maxim Evdokimov 123rf.com; p.40 Numerical keypad © Laymul 123rf.com; p.41 Closeup of business woman hand with mouse. Shallow depth of field. Selective focus © Aliaksei Verasovich 123rf.com; p.41 Woman freelance worker touching on laptop touch pad by her hand to select something while working in cafe on weekday morning. Freelance business working lifestyle concept © Silatip dreamstime.com; p.41 Graphic designer using digital tablet and computer in office or home © Maksim Kostenko 123rf.com; p.41 Industrial control panel with red trackball, close up photo with soft selective focus © Eugene Sergeev 123rf.com; p.41 A floating white Microsoft XBOX One controller isolated on a white background © Robert Klein 123rf.com; p.42 Hands of a doctor who uses the medical ultrasound diagnostic machine © aksakalko 123rf.com; p.42 Designer using graphics tablet © Kaspars Grinvalds dreamstime.com; p.42 Playing video games on Xbox console © Razvan Nitoi dreamstime.com; p.42 Customer satisfaction response People hand on Touch screen Digital media device Business © Vtt Studio dreamstime.com; p.43 using scanner in office or library, closeup of hands scanning documents © anyaberkut 123rf.com; p.43 web camera © alexlmx 123rf.com; p.44 Computer microphone © Marius Scarlat dreamstime.com; p.44 Scanning barcode with bar code reader isolated on white background. © Vchalup dreamstime.com; p45 Qr code or smartphone © Gualtiero Boffi dreamstime.com; p.45 Smiling asian office employee looking at camera working with multiracial colleagues, happy young company manager sitting at corporate workplace, cheerful team member posing with desktop computer © fizkes 123rf.com; p.46 Customer satisfaction response People hand on Touch screen Digital media device Business © Vtt Studio dreamstime.com; p.46 Close up projector in conference room with blurry people background © Mr.Smith Chetanachan 123rf.com; p.46 LCD image projector © Antares614 dreamstime.com; p.47 Compact laser home printer isolated on white background © Sergey Peterman 123rf.com; p.47 Printer prints business report on white isolated background. 3d © Maksym Yemelyanov 123rf.com; p.48 The 3D printer prints blue plastic model © Olga Ilina dreamstime.com; p.48 Small computer speaker isolated © Alexgerbergolts dreamstime.com; p.48 Digital camera on white © Yury Shirokov dreamstime.com; p.49 Digital thermo-hygrometer wires with an external sensor for measurements © Pavel Kruglov dreamstime.com; p.51 Harddisk drive (HDD) with top cover open on white background © Parinya Agsararattananont 123rf.com; p.51 External Hard Drive SB CS PP.indb 3 isolated on white background © WORAWUT PHUKHOKWAY123rf.com; p.52 Close-up macro view of new SSD Solid state drive fast data transmission disk for personal computer during upgrade © adrianhancu 123rf.com; p.52 Stacked macro shot of a folding red and silver USB pen drive © Mike Caffrey istockphoto.com; p.53 DVD drive with disc isolated on white background © Igor Purici 123rf.com; p.54 Modern web network and internet telecommunication technology, big data storage and cloud computing computer service business concept: server room interior in datacenter in blue light © scanrail 123rf.com; p.54 Global network mesh. Social communications background. Earth map. Vector illustration © maxborovkov 123rf.com; Chapter 4 p.56 Router icon © arcady31 123rf.com; p.59 Programming code abstract technology background of software developer and Computer script © Monsit Jangariyawong 123rf.com; p.60 Windows 8.1 on HP Pavilion Ultrabook © Manaemedia dreamstime. com; p.62 Young african male programmer writing program code sitting at the workplace with three monitors in the office. Image focused on the screen © Olena Kachmar 123rf.com; p.64 Real Python code developing screen. Programing workflow abstract algorithm concept. Lines of Python code visible under magnifying lens © piotrkt 123rf.com; Chapter 5 p.67 Modern city buildings and connection grid. 3d rendering © Sergey Nivens 123rf.com; p. 69 Amazon Verification security © Dimarik16 dreamstime.com; p.75 Password stolen © Amsis1 dreamstime.com; p.76 Fingerprint recognition technology for digital biometric cyber security with place for text © Sergey Chuyko dreamstime.com; p.77 Closeup hands to press the ATM key in the red cabinet. Finger pressing a pin code on a number pad. Security code on an pink © Rattanachot2525 dreamstime.com; p.77 Facial recognition by smartphone allows biometric authentication © Axel Bueckert dreamstime.com; p.77 Hotel door woman& x27;s hand inserting a magnetic stripe hotel key © Nuttawut Parasert dreamstime.com; p.77 Credit or debit cards. Smart chip © Buradaki dreamstime.com; p.78 Man open the door with NFC tag © Szabolcs Stieber dreamstime.com; p. 78 male using a password generator to perform online banking. Security token for banking security. Concept of e-commerce, online business and data security © Valerio Rosati 123rf.com; p.80 Man unboxing latgest Apple Computers iPhone 11 Pro © Ifeelstock dreamstime.com; p.81 World map point and line composition concept of global business. Vector Illustration stock illustration © royyimzy istockphoto.com; p.81 Bitcoin symbol in flat design. stock illustration © iNueng istockphoto.com; Chapter 6 p.83 Close-up Of A Man’s Hand Using Smart Home Application On Mobile Phone At Home © Andriy Popov 123rf.com; p.84 Round temperature sensor on the hot water pipe © Denis Shipunov dreamstime.com; p.84 Microprocessor with motherboard background © Yuliia Mols dreamstime.com; p.84 Piston or actuator as part of hydraulic and pneumatic mechanism in machine. Technology © Ratmaner dreamstime.com; p.85 Infrared motion sensor nightvision security camera © Alexxl66 dreamstime.com; p.86 Picture of a woman flying a professional grade camera drone (UAS) © Printezis dreamstime.com; p.87 welding robots in a car manufacturer factory © Sasin Tipchai 123rf.com; p.89 Fallen chess king as a metaphor for fall from power stock photo © Maudib istockphoto.com, p.89 People examining economic statistic. Financial examiner. Vector stock illustration © AndSim istockphoto.com; p.89 GPS navigation concept © scanrail istockphoto.com; p.89 Car diagnostic concept Close up of laptop with OBD2 wireless scanner and retro car on gray gradient background 3d © kvsan istockphoto.com; p.89 Nutrition elements © Madmaxer istockphoto.com; p.89 Beautiful butterfly Tailed jay, Graphium agamemnon, in tropical forest © Jag_cz istockphoto.com; p.90 room with rows of server hardware in the data center © Timofeev Vladimir 123rf.com; Chapter 7 p.93 Abstract background image of a flowchart diagram on a white floor. Computing algorithm concept © infografx 123rf. com; Chapter 8 p.111 Creative dark coding background with text. Programming and future concept. 3D Rendering © Daniil Peshkov 123rf.com; Chapter 9 p.127 Pixelated effect of an image of a room of virtual database. 3aD Rendering © Alphaspirit dreamstime.com; p.128 Grocery shopping list till roll printout on a wooden table © Brian Jackson 123rf.com; Chapter 10 p.141 Abstract, close up of Circuits Electronic on Mainboard Technology computer background (logic board,cpu motherboard,Main board,system board,mobo) © Narong Rotjanaporn 123rf.com; p.142 Businessman entering safe code to unlock the door © stockyimages 123rf.com; p.149 Three happy friends planning a travel on lineThree happy friends sharing on line content with multiple devices sitting on a sofa at home Happy woman sitting on sofa and using mobilephone at home, enjoying content on cellphone, chatting with friends, sharing mobile devices with friends. Line art style indoor house. Happy friends using cellular, sitting on sofa at home, browsing internet and sharing content, and consulting a guide sitting on a sofa at home © Antonio Guillem 123rf.com; p.158 Young teen girl in the elevator, presses the elevator button © Valeriy_G istockphoto.com 14.5.21. 14:13 This book is designed to help you build your knowledge and understanding of essential Computer Science concepts. It will also enable you to appreciate the application of Computer Science in your everyday life. This Student’s Book is part of the Marshall Cavendish Education suite of resources that will support you as you follow the Cambridge IGCSETM and IGCSE (9-1) Computer Science syllabuses (0478/0984) and prepare for your examinations. Chapter opener introduces the topic and CHAPTER key learning goals. 4 Software COMPUTER SCIENCE WATCH* makes learning ‘come alive’. The videos can be launched from a smartphone or a tablet by scanning a page using the MCE Cambridge IGCSE App. COMPUTER SCIENCE WATCH Scan the page to watch a clip on the differences between system and application software. Please refer to www.mceapps.com for user guide and further information. *As the Watch videos are authentic and therefore reflect real-life situations, they might in some instances contain content that is beyond the scope of this syllabus. Always refer to the appropriate syllabus document for the year of your examination to confirm the details and for more information. The syllabus document is available on the Cambridge International website at www.cambridgeinternational.org. Before watching discuss what you expect to see or hear. QUESTIONS • What is the link between hardware and software? • How is software essential to the operation of a computer? • How do humans use software to interact with computing devices? At the end of this chapter, you will be able to: understand the difference between system software and application software • What is programming and how do pieces of software begin their existence? define the role and basic functions of an operating system identify the hardware, firmware and operating systems that are used to run applications software Content in this feature has not been through the Cambridge Assessment International Education endorsement process. define the role and operation of interrupts identify the difference between a high-level language and a low-level language understand the advantages and disadvantages of each type of language define the two types of translator: compilers and interpreters identify the advantages and disadvantages of each type of translator understand what an integrated development environment is used for, including its common functions QUESTIONS 59 IGCSE_CS_TB_Chapter_4.indd 59 assess your prior knowledge on the topic. 13.5.21. 16:32 Chapter 10 DEFINITION explains key terms used in Computer Science. DEFINITION Logic gates: the basic units of a digit circuit that control the flow of electronic signals. . Logic Gates Logic gates are the basic building units of any digital circuit. Today, these circuits are used in almost every computer system. From elevators to washing machines, logic gates are used all around you. WORD ALERT Words commonly associated with the topic are highlighted in red and explained in a simpler way. This also helps you to be more familiar with the words and be confident in using them. Digital circuit used to open electronic door. WORD ALERT Combination: a joining of different parts or qualities. There are a number of different types of logic gate, with different logic rules. The combination of several logic gates forms a circuit, which allows for the design and performance in modern computers. The gates receive binary data, apply a Boolean operation and then output a binary result. Arithmetic: use of numbers to calculate an outcome. Boolean Operations Equivalent: the same or equal meaning. HELPFUL NOTES LINK Be careful not to confuse the Boolean operator ‘+’ with ‘+’ , which means ‘plus’ in normal maths. leads you to exercises in the Workbook for further practice. SB CS PP.indb 4 The word ‘Boolean’ comes from Boolean algebra, which is the basis of computer arithmetic and especially logic gates. There are only two Boolean values: true and false. They have equivalents in normal language and in binary notation. Boolean expressions can compare data of any type as long as both parts of the expression have the same data. In computer science, Boolean expressions can be used in programming and produce Boolean values when evaluated. Boolean values are either true or false: Boolean value Binary value True On Synonyms Yes Positive False Off No Negative There are also three logical operators: NOT, AND and OR. The Boolean operators for these are AND ‘•’, OR ‘+’, and NOT ‘ ’, which is written above the letter. Ā means NOT A. A • B means A AND B. A + B means A OR B. Logic gates use both Boolean values and operators. 142 iv This chapter will explore the types and functions of common logic gates. IGCSE_CS_TB_Chapter_10.indd 142 Logic Gates and Circuits 13.5.21. 16:32 14.5.21. 14:13 Chapter 2 ENRICHMENT This type of data transmission occurs when a computer or device is connected to another computer or device using a single data channel. Data is transmitted one bit at a time, sequentially, down the channel. ENRICHMENT promotes deeper thought by: offering snippets of information to supplement your knowledge; providing activities which help reinforce learning; or posing challenging questions to encourage you to apply the concepts learnt to various contexts. An example of this type of data transmission occurs when a computer is connected directly to a modem. Can you find out when serial and parallel ports were no longer included in computers? What replaced them and why? One of the advantages of using a serial transmission method is that it is very reliable for transferring data over longer distances, although sometimes it is not the most practical. There are also much fewer errors in serial transmission, as bits are sent one at a time, and only one single channel is required to achieve this transmission. Thus, this is a lower cost method of transmitting data. The disadvantage of a serial transmission is that transmission speeds can be slow as only one channel is being used to transfer data. Parallel Data Transmission Computer Figure . Parallel transmission. REFLECT Printer Bits (Multiple) Parallel data transmission is where multiple bits of data are sent at the same time along different channels in the same cabling. Most modern printers now are connected to computers using network cables and data is transmitted much faster this way. An example of this type of data transmission is where a computer is connected directly to a printer. The advantages of this type of transmission is that faster data transmission takes place because of the multiple channels being used. The disadvantages are that this type of transmission is more expensive and synchronisation errors can occur due to the separation of data across different channels. Input also leads you to exercises in the Workbook for further practice. Computer stimulates you to be aware of your own thought processes and explore different ways of solving problems. Unidirectional Figure . Simplex transmission. QUICK CHECK LINK WB Simplex Data Transmission REFLECT Simplex transmission is a one-directional (or unidirectional) mode of data transmission. The data will only go one way, and the receiver of the data does not send any data back to the sender. What other devices can you think of that use unidirectional data transmission? An example of this type of transmission occurs between a keyboard and a monitor. The keyboard sends input data to be displayed on a monitor, but the monitor does not send any data back to the keyboard. The advantage of simplex transmission is that the process can use the full bandwidth of the channel. The disadvantage of this transmission type is that it is not possible to engage in two-way transmission using this method, and most forms of communication rely on this to be successful. Activity 1 24 Data Transmission 2 Chapter 10 Now do the same for this situation. You can skip some steps if you don’t need them. Tip: the circuits are normally on so something needs to happen if they go off. • An alarm makes no warning sound if the door is closed and the window is closed. There are hidden switches on the door and window through which a current is constantly passing. If someone opens the door or window, the alarm sounds. Name the logic gates represented by these truth tables: IGCSE_CS_TB_Chapter_2.indd 24 QUICK CHECK Write the Boolean algebra expression for NAND, NOR, XOR. 13.5.21. 16:33 Inputs a Worked Example demonstrates how to solve problems by applying concepts learnt. A Output B Inputs b X WB Output A B X LINK Consolidate your understanding by completing the Exercises 1-2 from pages 123-129 in the Workbook. Chapter 10 Worked Example We use Boolean logic all the time. Look at this situation using Boolean operators: You have decided that you will do extra study if you are falling behind at school. You also decide that you will do extra study even when you are not behind if your friend asks you to study together. Express this using Boolean operators. Solution To express this formally and logically we need two pieces of information to make our decision and another piece to represent the result of the decision. We can name our information like this: WORD ALERT Formally: officially / explicitly. Information needed to make decision (behind at school) = TRUE if fall behind. If not, FALSE. (friend asks you to study) = TRUE if friend asks you to study. If not, FALSE. Result (do extra study) = TRUE if we decide to do extra study. If not, FALSE. Our logical expression is then: (do extra study) = (behind at school) OR (NOT (behind at school)) AND (friend asks you to study) This expression uses the three Boolean operators: NOT, AND, OR. Activity 1 2 Activity gives you opportunities to apply what you have learnt and assess what you know. Write a logical expression like the example above for this given scenario. There are two methods of getting to your part time job on time. You can get the bus but only if you wake up before .am. If you wake up after this time, you will need to ask your parents to take you in the car. If you wake up before .am but your parents offer to take you, then you will always say yes as it is easier. Draw the Boolean algebra symbols for the following: a) A NOT B b) A AND B c) A OR B Logic Gates and Circuits IGCSE_CS_TB_Chapter_10.indd 149 149 13.5.21. 16:32 HELPFUL NOTES Types of Logic Gate There are three basic types of logic gate that will be examined in this chapter: NOT, AND and OR. NOT AND OR WORD ALERT The left side of the logic gate is referred to as the input and the right side as the output. We can use a truth table to show the function of the logic gate. Each of the logic gates has a different truth table. These truth tables display all possible input combinations and the correct output. Logic Gates and Circuits IGCSE_CS_TB_Chapter_10.indd 143 SB CS PP.indb 5 In all logic gates except the NOT gate, there are two inputs. The inputs or outputs have two possible states: a value of 1 or a value of 0. Referred: denoted / identified. HELPFUL NOTES supports your learning by providing tips and highlighting important notes that you need to be aware of. 143 13.5.21. 16:32 v 14.5.21. 14:13 Chapter 10 Here is the truth table for the OR gate above: Inputs A REFLECT Output B If someone asks you, ‘Do you want a soda or some water?’, you can’t answer ‘Both, please’. If you could have both that would be an inclusive use of OR. Is the OR gate inclusive or exclusive? X Logic notation: X = A OR B Boolean algebra: X = A + B Out of the four possible output states, the only time output X will be is when both the inputs A and B are . An inclusive OR is what is shown in the truth table if either A or B is True, or if both are True, then the statement value is True. An exclusive OR only returns True when A OR B is True only. Worked Example WORD ALERT A security light outside a house comes on after .pm or if it is dark. Make a table showing the operation in normal language with corresponding Boolean and binary values. Make the resulting truth table and choose the logic gate that will make this happen. QUICK CHECK Condition: the state of something in relation to its appearance, quality or working order. Solution We have to state the conditions under which the light will come on: if it is after .pm if it is dark serves as a checkpoint to check your understanding of concepts. Rate your confidence level in your answer by drawing a pointer on the confidence meter. Then we convert these into the Boolean values ‘True’ and ‘False’: it is after .pm = Yes/True/Positive if it is dark = Yes/True/Positive QUICK CHECK Next we add the binary values: it is after .pm it is dark Let’s Map It provides a visual summary of the concepts covered to help you integrate your learning and form connections between different concepts. Yes Yes True True Positive Positive In all logic gates except the NOT gate, there are two inputs. The inputs or outputs have two possible states. What are they? Then we make the truth table. The inputs are ‘it is after .pm and ‘it is dark’: Inputs it is after .pm it is dark The light coming on is the output: Inputs it is after .pm Output it is dark the light comes on Remember that the light will come on if either of the conditions is true: Inputs it is after .pm No No Yes Yes Let’s Review offers questions to test your understanding and gives you consolidated practice. Output it is dark No Yes No Yes the light comes on No Yes Yes Yes Logic Gates and Circuits 145 IGCSE_CS_TB_Chapter_10.indd 145 13.5.21. 16:32 Chapter 4 Chapter 10 Let’s Map It Let’s Review HARDWARE What logic gate matches these truth tables? SOFTWARE Software and hardware are essential to work together. SYSTEM A B X A B X Label the following logic gates: APPLICATION Allows a computer to function Allows a computer to be used Draw the logic circuit for the following statement X = (A AND B) AND (NOT C). Complete a combined truth table including any intermediate outputs for the following: <?> A P AND B OR X C Operating System Enables a user to interact with the computer. Applications are required to enable a user to carry out tasks and work. Draw the correct logic gate circuit and truth tables to match these Boolean algebra expressions: A˙B A+B Ā Draw the logic circuit diagram and corresponding truth table represented by the below Boolean algebra epressions. Consider the logic statement: X = If [(A is NOT OR B = ) NAND C is ] NOR [(A is AND C is ) NAND B is ] A Interrupts All software starts as code X B A stop in a process needing a user or program input. Python 1 2 3 Handled in order of priority. Perl C++ Java C# C 4 Integrated Development Environment Low- and high-level languages X 1 2 00110 111001 3 4 Code Editor if a == 10: b += 1 Low 5 High 6 7 8 9 10 Simulation Translator Compiler/Interpreter A B C Working space X 11 Software IGCSE_CS_TB_Chapter_4.indd 65 65 13.5.21. 16:32 The following are also included at the end of the book: 162 Logic gates and circuits IGCSE_CS_TB_Chapter_10.indd 162 13.5.21. 16:32 • Answers – provided for questions in Let’s Review (only numerical and short answers are included) • Glossary – provided to give you a list of the vocabulary words and definitions highlighted in Word Alert • Index – provided to help you search for key terms and phrases in the book vi SB CS PP.indb 6 14.5.21. 14:13 Contents vii SB CS PP.indb 7 14.5.21. 14:13 SB CS PP.indb 8 14.5.21. 14:13 CHAPTER 1 Computer Systems QUESTIONS • What is data? At the end of this chapter, you will be able to: • How is data represented by computers? • How is data stored and compressed for use? convert between the binary, denary and hexadecimal number systems understand why hexadecimal is used for representing data add two -bit binary numbers and know why overflow happens perform both a left and right logical binary shift use two’s compliment to represent positive and negative binary numbers understand how a computer represents text, sound and images identify the different data storage measurements understand how to calculate the size of a file understand why files need to be compressed explain how files are compressed using lossy and lossless compression methods 1 SB CS PP.indb 1 14.5.21. 14:13 Chapter 1 WORD ALERT Efficiently: to perform something in a well-organised and competent way. DEFINITION Binary: a number system that contains just 2 numbers, 0 and 1, and the number system that a computer uses to process data. QUICK CHECK What is the difference between a base-10 and a base-2 number system? Computers and computing devices are capable of processing millions of pieces of information every second. Computers read and write an enormous variety of information; in order for the processing to happen efficiently, that information must be broken down into code that every computer can understand. Information used by a computer is called data. The code that computers and machines use to process information is called binary. This is a number system that only uses two digits, and . All data that a computer is required to process has to be converted into binary in order to be understood. This chapter will explore how computer systems represent data in a variety of ways. . Number Systems In order to understand the binary number system, we must first understand the decimal, or denary, number system that we are used to. There are several different theories about how ancient civilisations began counting in decimal numbers. One theory is that people began counting using their hands, and we have two hands, each with four fingers and one thumb making up ten digits. .. Denary Number System Humans probably started to count using the ten digits that they had on their hands. The denary system is a base- system, meaning that there are ten digits that form the basis of the place value system. All numbers in the denary system are formed from , , , , , , , , or , and the place value of each position of the decimal numbers is ten times larger than the place to its right, written in powers – , , and so on. WORD ALERT Powers: the product obtained when a number is multiplied by itself a certain number of times. Worked Example We can represent the denary number as in the table below: Hundreds of thousands Tens of thousands Thousands Hundreds Tens Units × = × = × = × = × = × = + + + + + = .. Binary Number System HELPFUL NOTES When reading binary numbers, it is important to read them from right to left. 2 SB CS PP.indb 2 Binary is a base- system, meaning that only two digits form the basis of the place value system. All numbers in the binary system are formed from either or . The place value of each position of the binary numbers is two times larger than the place to its right, otherwise written in powers, , , and so on. You will notice in the worked example that the columns increase by a power of from the first column as you read from right to left. Computer Systems 14.5.21. 14:13 Chapter 1 Worked Example We would represent the binary number in the table below: × = × = × = × = × = DEFINITION Transistors: a small electronics device that amplifies electrical current. + + + + = Therefore, the binary number represents in denary. Computers use the binary system because all of the processing takes place using components such as registers and memory. These components are made up of transistors that can hold either an electric charge () or no electric charge (). Logic gates are used to make decisions about the processing of data, and they have two options – on () or off (). Depending on the gate, data bits are either kept the same, or switched from to or to for the operation being carried out. LINK See Chapter 10 for more information about logic gates. .. Hexadecimal Number System REFLECT The hexadecimal number system is another number system that computers use for processing. • It is different from the binary and denary systems as it is a base- system. • It is similar to the denary system as it begins with the digits –, but it also uses the alphabetic characters A–F to form the remainder of its place values. Computers only use binary code, however the conversion to hexadecimal is mostly for human benefit as this conversion shortens the long binary codes. This is illustrated by the conversion table below. Note that the first ten digits are identical. Denary Hexadecimal A B C D E F We will discuss the uses of these in section .. . Binary, Denary and Hexadecimal Conversions Have you ever seen what looks like a hexadecimal number on your computer? If you find one try and convert it to a denary number. WB LINK Consolidate your understanding by completing Exercise 1, page 1 in the Workbook. LINK Section 1.3. To better understand how a computer carries out the processing of numerical information, it is important to know how to convert numbers from one system to another. There are various mathematical approaches to these conversions. .. Converting a Denary Number to Binary WORD ALERT An easy way to convert a denary number into binary is to use the ‘divide by ’ method: • Divide the number by each time and note the remainder. • When you are unable to divide by any further, the sequence of remainders becomes the binary number that represents the denary number you began with. • These remainders should be read from the last division to the first. Computer Systems SB CS PP.indb 3 Remainder: the number left over in a division in which one quantity does not exactly divide another. 3 14.5.21. 14:13 Chapter 1 For example: 29 divided by = remainder divided by = remainder divided by = remainder divided by = remainder divided by = remainder Read in this direction Therefore, in binary notation would be . .. Converting a Binary Number to Denary When converting a binary number to denary, it is important to use the rules of place value. Each time you move a place to the right, the places increase in value by times the amount of the previous place. LINK WB Consolidate your understanding by completing Exercise 2, page 2 in the Workbook. Tens thousands Thousands Hundreds Tens Units s s s s s So, applying place value to a denary number like will look like this: Tens thousands Thousands Hundreds Tens Units s s s s s × = × = × = × = ×= + + + + = LINK Section 1.1.2. HELPFUL NOTES You can continue writing place values for binary numbers and keep doubling the places in each column. The normal length of number is 8 bits. Worked Example Binary place values can be written in a similar way (see section ..), but the difference here is that the places double in value from to the previous place. Therefore, you can apply place value to a binary number like as follows: × = ×= ×= ×= ×= + + + + = So, using the mathematics above, the binary number is in denary. ENRICHMENT Can you write your date of birth in binary? 4 SB CS PP.indb 4 Activity Show your working out for these exercises. Convert the denary number into binary. Convert the denary number into binary. Convert the binary number into denary. Convert the binary number into denary. Computer Systems 14.5.21. 14:13 Chapter 1 .. Converting a Denary Number to Hexadecimal Using Binary To convert a denary number to hexadecimal, it is important to know the binary equivalents of the first hexadecimal digits (see section ..). Denary number Hexadecimal digit Binary code A B C D E F The table shows that converting any of the first denary digits into its hexadecimal equivalent is straightforward. However, converting denary numbers larger than requires combining the -bit binary nibbles in the binary code column. For example, the denary number in hexadecimal is created by combining the binary nibble equivalent to denary number and the binary nibble equivalent to denary number . Combining two binary nibbles in this way creates an -bit binary number, or a byte. Denary number Binary nibbles Hexadecimal notation ( + ) Worked Example To convert the denary number to hexadecimal you would do the following: • Convert the denary number to -bit binary using the ‘divide by ’ method, which becomes (see section ..). • To write the denary number as an -bit binary number rather than a binary number, add three s to the front of the five-digit number – so becomes . For this conversion we can then split the two sets of four binary digits into nibbles, to get . • Once you have constructed the -bit binary conversion, use the table above to match the two nibbles to the hexadecimal column. In this instance, the nibble is the equivalent of the hexadecimal digit , and the nibble is the equivalent of the hexadecimal digit F. Denary number Binary equivalent -bit binary Hexadecimal notation F QUICK CHECK What are the differences between binary and hexadecimal? LINK Section 1.1.3. DEFINITION Nibble: a set of four binary bits. HELPFUL NOTES Bytes are a common measurement of bits. Octets, or groups of 8, are used to represent different types of data. LINK See section 1.2 to refresh your memory about denary to binary conversion. LINK Section 1.2.1. Therefore, combining the two digits gives the hexadecimal code F. Computer Systems SB CS PP.indb 5 5 14.5.21. 14:13 Chapter 1 .. Converting a Hexadecimal Number to Denary Using Binary LINK Section 1.2.2. In the same way that you can use binary to convert from denary to hexadecimal, you can also convert the opposite way: • Take the hexadecimal number, separate the digits, and then convert those digits back to binary nibbles. • Once combined into an -bit binary number, use the place value method (see section ..) to convert the binary number back to denary. Worked Example To convert the hexadecimal number C to denary, do the following: . Separate the two parts of the hexadecimal number into and C. . Using the table in section .., convert the two hexadecimal digits into their binary nibble equivalents – hexadecimal digit is equivalent to the binary nibble , and the hexadecimal digit C is equivalent to the binary nibble . . The two binary nibbles combined make the -bit binary number . . Put the -bit binary code into a binary place value table: LINK See section 1.2 to remind yourself about the place value method. × = × = × = × = ×= ×= ×= ×= + + + + + + + = Therefore, the hexadecimal code C is equivalent to the denary number . Activity Show your working out for these exercises. Convert the denary number into hexadecimal, using binary to help you. Convert the denary number into hexadecimal. Convert the hexadecimal number F into denary, using binary to help you. Convert the hexadecimal number A into denary. . Examples of the Use of Hexadecimal Numbers in Data Representation Data in its most basic form has to be converted to binary so it can be processed by a computer. However, hexadecimal numbers are useful for a number of purposes, and are easier for humans to read than long strings of binary bits. 6 SB CS PP.indb 6 Computer Systems 14.5.21. 14:13 Chapter 1 Hexadecimal numbers can be found in computer science in the following examples: MAC Address Media Access Control A number that identifies a network interface controller of a device on a network. :::d::a HEXADECIMAL NUMBERS Error codes Often operating system errors are represented with hexadecimal numbers for reference. xCDL HTML Colour Codes Websites use colour codes to represent one of the million colours in the palette. IPv6 Address Internet Protocol version 6 A number that identifies locations of devices for the routing of data packets across the internet. :da:ae:: . Binary Addition WB Addition is one of the most common mathematical operations a computer performs. To appreciate this, it is important to understand how to carry out binary addition. Before attempting binary addition, we must look at the similarities with denary addition because the two processes are alike. LINK Consolidate your understanding by completing Exercises 3 and 4, pages 5-10 in the Workbook. .. Adding Two Binary Numbers Together To add together the two denary numbers and , we would place them one above the other, draw a line underneath the sum and add the columns, starting from the numbers on the right. Where the sum of the numbers in the column equals or more, we carry the tens underneath the next column according to place value. + REFLECT Note the similarities between binary and denary addition – always start with the right-hand column. The total of + is therefore . Adding together two binary numbers is a very similar process. However, it is important that the two binary numbers have the same number of binary digits. Computer Systems SB CS PP.indb 7 7 14.5.21. 14:13 Chapter 1 Worked Example Add together the binary numbers and as follows: • Write the numbers out in columns, as if you were adding two denary numbers. would become . • Begin from the furthest right and add the numbers in each column. + The binary number is equal to in denary, and the binary number is equal to in denary. QUICK CHECK What would you need to do in the addition to add two 1s in one column? + = and the binary number that is produced by the addition () is equal to the denary number . As with denary, we carry values when adding two s in the same column. Worked Example Add the binary numbers and as follows: • Write the numbers out in columns as if you were adding two denary numbers. • Begin from the furthest right and add the numbers in each column. + When you add the two s in the third column, this becomes a , and is carried across to the next column. This also then produces an addition of two s, which means that a new column has to be created. The binary number is equivalent to the denary number , and the binary number is equivalent to the denary number . + = and the binary number that is produced by the addition () is equal to the denary number . .. Overflows As we learnt in the previous section, adding together binary numbers can often lead to the creation of an additional column on the left-hand side of the number. Activity Show your working out for these exercises. Convert the denary numbers and to binary and perform an addition on the two numbers. Convert the denary numbers and to binary and perform an addition on the two numbers. HELPFUL NOTES The number 255 is significant in 8-bit binary as it is the largest number that can be represented in an 8-bit binary octet. 8 SB CS PP.indb 8 To apply this theory to a computer, if a register in a central processing unit (CPU) had a capacity of bits, the largest binary number that it could possibly hold would be , equivalent to the denary number . If one more bit was added to this number, it would push the number above the capacity of the register and would cause an overflow error. Computer Systems 14.5.21. 14:13 Chapter 1 This is highlighted by the following sum, which is a binary addition of + : + As the column additions carry forward a each time, eventually a ninth column is added. This creates a total that becomes a binary number consisting of bits, one more than the maximum capacity of bits. In this instance, the CPU will drop the extra digit, or the overflow digit, because it has nowhere to store it. The computer would then think that + = . This action would cause an overflow error, which means that there is not enough capacity to carry out an instruction, and this may make the computer processing unstable or stop. Most modern computing devices have a much larger capacity than bits, however, overflow errors can still occur if the arithmetic and additions push the numbers being returned above that capacity. WORD ALERT Overflow: the generation of a number or other data item that is too large for the assigned location or memory space. Shift: movement either to the left or right. .. Binary Shifting So far we have only looked at addition. Computers are capable of carrying out logical arithmetic on the binary numbers that they process, and for multiplication and division a CPU uses a process called binary shift. To understand this, we must refresh our memory about binary place value. When we converted a binary number to denary, we used the base- table below: We will now explore multiplication and division, using the binary place value table to understand the process of shifting, or logical shifts. ... Multiplication For a CPU to multiply a binary number, the number needs to be shifted to the left and will fill the remaining gaps with zeros. For example: • multiplying by shifts the digits one place to the left • multiplying by shifts the digits two places to the left • multiplying by shifts the digits three places to the left You will notice that multiplications happen in line with the order of place value in the base- sequence. WB LINK Consolidate your understanding by completing Exercise 5, page 10 in the Workbook. REFLECT How many shifts to the left would take place if you were multiplying a binary number by 32? Worked Example Take the binary number , equivalent to in denary and a multiplication of × . We would begin with the number written like this: Multiplication by requires the digits to be shifted to the left by one place, and the gap is filled with a zero: Therefore, the left binary shift operation gives a binary number of , equivalent to the number in denary. Computer Systems SB CS PP.indb 9 9 14.5.21. 14:13 Chapter 1 ... Division For a CPU to divide a binary number, the number needs to be shifted to the right: • dividing by shifts the digits one place to the right • dividing by shifts the digits two places to the right • dividing by shifts the digits three places to the right You will notice that divisions happen in line with the order of place value in the base- sequence. Worked Example Take the binary number , equivalent to in denary and a division of ÷ . We would begin with the number written like this: A division by requires the digits to shifted to the right by one place: Therefore, the left binary shift operation gives a binary number of , equivalent to the number in denary. ... Binary Shifts with -bit Binary Numbers REFLECT How many shifts to the right would take place if you were dividing a binary number by 8? LINK See Chapter 3 to learn about the role of registers in the CPU. HELPFUL NOTES The most significant and the least significant bits are at the far left or right of a binary number, respectively. LINK Section 1.4.2. 10 SB CS PP.indb 10 We have learnt about binary shifts left and right when multiplying and dividing with small binary numbers. It is important to also learn what happens when multiplying or dividing -bit binary numbers. This is because registers contained within the CPU (see Chapter ) often have -bit limits on the amount of data they can hold at any one time. If an -bit binary number needs to be multiplied the shifting process can cause bits to be lost at one end of the register, and zeros added at the opposite end. This process is known as losing the ‘most significant’ bit and can cause data to lose precision. It also provides the mathematical explanation for an overflow error. Worked Example Multiplying an -bit binary number by If we wish to multiply the binary number (the equivalent to denary number ), we would first write the number in the place value table: We would then perform a shift of one place to the left: 1 However, what has happened to the that was placed in the furthest-left column? The multiplication shift produces the binary number – the equivalent to denary number and not , which arithmetic suggests would be returned. This number is larger than the () capacity that the -bit register can store (see section ..). This bit is called the ‘most significant bit’, and when it is shifted beyond the furthest-left column the binary data that is stored loses precision due to overflow. Computer Systems 14.5.21. 14:13 Chapter 1 The same process can occur when dividing an -bit binary number. There is also a further level of complexity, because performing a logical right shift can cause a binary number to become a decimal. Worked Example Dividing an -bit binary number by . If we wish to divide the binary number (the equivalent to denary number 189), we would first write the number in the place value table: We would then perform a shift of five places to the left: However, what has happened to the binary numbers that have dropped off from the right-hand column? The division shift produces the binary number – the equivalent to denary number not the decimal number . that arithmetic suggests would be returned. This is because working with binary in this way does not use decimals, only positive binary integers. The decimal part of the number is therefore discarded. These bits are called the ‘least significant bits’ and when they are shifted beyond the righthand column, just like with multiplication, the binary data that is stored loses precision due to overflow. REFLECT Why do you think that decimal numbers are discarded when dividing? Activity Show your working out for these problems. Multiply the binary number by . Multiply the binary number by . Divide the binary number by . Divide the -bit binary number by . .. Two’s Complement WB We have looked at positive numbers and the way that they are represented by a CPU. However, a processor can also represent negative numbers, and there are a few ways it handles this process. One of the methods a processor can use to represent negative numbers is called two’s complement. We can use a reference table to help understand this method. Computer Systems SB CS PP.indb 11 LINK Consolidate your understanding by completing Exercise 6, page 11 in the Workbook. 11 14.5.21. 14:13 Chapter 1 Binary numbers and place values WORD ALERT Inverted: reversed or transformed into its corresponding opposite. Denary equivalent – – – – – – – – To represent negative numbers, it is important to think about the place value of the furthest-left bit in a different way. Processors can be set up to see the bit in the eighth column as a sign bit (shaded). • If the digit in the sign bit column is a , this indicates that the binary number being represented is positive. • If the digit in the sign bit column is a , this indicates that the number being represented is negative. You will also notice that for each of the -bit positive binary numbers represented in the table, their negative opposite numbers have had their bits inverted. The final step in this process once all of the bits have been inverted is to add to the calculation when completed. Worked Example Converting a positive binary integer to a two’s complement -bit integer To convert the binary number ( in denary) to a positive two’s complement integer, put the number into the place value columns, ensuring that the left-hand digit is a (to show that positive is represented). HELPFUL NOTES The furthest-left column represents the sign bit; this tells us whether a number is positive or negative. If the column contains a 0 the number is positive, if it contains a 1 the number is negative. 12 SB CS PP.indb 12 The digit in the shaded left-hand column is the sign bit, and represents a positive integer. As we learnt earlier, adding the place columns as shown gives us the denary equivalent: + + = Converting a positive two’s complement -bit integer to a binary integer To convert positive from a two’s complement integer to a binary integer, we essentially need to reverse the process above. We would represent the number as follows: The in the left-hand column indicates a positive number, and the positive two’s complement -bit binary number can therefore be written as . Computer Systems 14.5.21. 14:13 Chapter 1 Converting a negative binary integer to a two’s complement -bit integer To represent the binary number ( in denary) as - and a negative two’s complement integer, put the number into the place value columns, but invert the s to s and s to s. This gives you the integer’s complement. This time, the sign bit column becomes - as there is a in that column. The calculation then becomes – + + + + = – and is added to the product to make –. – = + = . Converting a negative two’s complement -bit integer to a binary integer In order to achieve this, we would essentially reverse the above process. To convert - we would first of all write out the table for + and invert the bits. This would then give us the negative two’s complement -bit binary number . ENRICHMENT Why do you think that we omit the inverse of the binary number representing 0 (00000000)? What would the denary equivalent of 11111111 be within the context of two’s complement? . Text, Sound and Images Modern computers are required to represent data in many different forms. The most basic form is textual data. However, as we live in an increasingly digital world, the information and data that humans require to be processed becomes ever more complex. .. Text Representation Every character that is input into a computer must be represented by binary code, including the spaces we type between words and the special characters we use for punctuation. As textual communication is vital for users around the world, it is important that computers have a common set of characters that are recognised by a variety of systems. These are called character sets, and the most common are American Standard Code for Information Interchange (ASCII) and Unicode. ASCII code uses seven binary bits to represent all the commonly used characters. This provides a character set that has different characters, made up as follows: • upper case letters • lower case letters • Digits • Punctuation marks The basic form of ASCII does have restrictions, as it does not allow for the representation of characters such as á or ê, which are commonly used characters in different languages. So Extended ASCII was created, which allows characters to be represented, meaning that characters from languages such as French and Spanish could be stored. As textual communication developed further and became increasingly global, even Extended ASCII was too restrictive for all of the different languages and characters required. Computer Systems SB CS PP.indb 13 REFLECT What do you think control codes are used for? 13 14.5.21. 14:13 Chapter 1 Inserting a special character in Word is made possible by using the Unicode character set. HELPFUL NOTES An emoji is made up of combinations of different symbols, usually beginning with a colon. WORD ALERT Analogue: using signals or information represented by a continuously variable physical quantity. Computers began to be programmed using Unicode to represent text. Unicode uses -bits to represent the characters in its set, which enables over , characters. In this way, languages such as Chinese and Arabic, which have many additional characters, can be stored, displayed and shared. Unicode can also display the pictorial symbols known as ‘emojis’, which are used in the world of instant messaging and texting. .. Sound Representation Just as text can be represented by binary, so too can sound. For a computer to successfully process sound, the analogue signal input has to be converted into a digital signal. Sound is normally captured by a microphone, and a piece of software will capture it and convert the analogue to digital. This recording is called a sample. The sample is recorded over a period of time measured in seconds. The sample generates a continuous sound wave that is a measure of amplitude over time. 9 DEFINITION 8 7 Amplitude Amplitude: the strength of a sound wave, measured at the highest level. 6 5 4 3 2 1 0 1 2 3 4 5 6 Time 14 SB CS PP.indb 14 Computer Systems 14.5.21. 14:13 Chapter 1 The conversion software records the amplitude at each moment in time during the sample. Each amplitude number (denary) is then converted into binary and stored. The example in the graph above shows one sample being converted into a sound wave. However, the recording software is capable of taking multiple samples every second. This number is called the sample rate and it is measured in hertz, or cycles per second. The greater the sample rate, the larger the audio file that is created by the software. Sample rate is also very important in determining the sound quality of the audio – if the rate is too low, the sound quality will be impaired. Most audio clips are recorded at . kilohertz, which is suitable for listening while keeping the file at a manageable size for storage. Bit depth and bit rate is another aspect of digital audio. Bit depth is also known as sample resolution, and measures how many bits are used to record each sample. A recording with a resolution of bits will be lower quality than a recording with a resolution of bits. The file will also be much larger at the higher resolution. The bit rate marks how much data is processed for each second of sound recorded and is formulated by multiplying the sample rate by the sample resolution. When both the sample rate and sample resolution are increased, so is the accuracy of the audio recording. The pixels are stored as a series of binary codes, and the number of pixels determines the resolution of an image. The greater the number of pixels, the higher the resolution and quality of the image. Another factor of image representation is colour depth, which is the number of bits that are used to represent each colour. If two bits were used per colour instead of just one, this would allow twice the number of colours to be used in a picture. If -bit binary codes were used to represent colours, there would be , possible colours. As the colour depth and resolution increase, so do both the image size and the image quality. Hertz: frequency of samples, measured in cycles per second. WORD ALERT Impaired: weakened or damaged. ENRICHMENT What is the lowest sample resolution a sound file could be recorded at before the listener would detect a drop in quality? .. Image Representation By their very nature, images are visual; however, these are also represented by binary numbers. In the simplest form, we can think of images as being a grid of pixels where a is represented in white and a is represented in black. DEFINITION DEFINITION Pixel: a tiny area of illumination on a display screen. REFLECT How many colours would be represented by 4-bit colour depth? . Data Storage Data in computers and computing devices require appropriate storage media. Each device uses different types of storage media, with advantages and disadvantages. One thing that is unique to all storage media is the measurement of its capacity. The capacity of the storage medium is measured in bits. • A bit can either be a or a in binary, and represents one binary decision. • There are bits in a nibble, and bits or nibbles in a byte. • Typically, a byte would be the equivalent of one single character typed in a document. Computer Systems SB CS PP.indb 15 15 14.5.21. 14:13 Chapter 1 There are bytes in a kibibyte. The reason that there are bytes rather than (decimal) is because of the way that numbers are counted in binary. Binary numbers are counted using a system of powers, and the next number in the sequence is always double the previous one. Therefore, kilo is to the power , equal to times the value of . Kibi is to the power of , equal to times the value of . This table sets out the units of measurement for storage devices in computing. Unit of measurement HELPFUL NOTES You may have heard the terms kilobytes and megabytes, rather than kibibytes and mebibytes. Kilo and mega refer to multiples of 1000, rather than 1024, and so it is more helpful to use the terms in the table. bit Equal to The smallest unit of data storage nibble bits byte bits kibibyte (KiB) bytes mebibyte (MiB) kibibytes gibibyte (GiB) mebibytes tebibyte (TiB) gibibytes pebibyte (PiB) tebibytes exbibyte (EiB) pebibytes zebibyte (ZiB) exbibytes yobibyte (YiB) zebibytes As of yet, there is no measurement of computer storage larger than yobibytes, mainly because humans have not yet needed this. Each storage device is capable of supporting storage media up to a certain number of bytes depending upon its type and usage. .. Calculating the File Size of an Image File It is important to know how the size of an image file is calculated for storage on a computer’s hard disk. There are four steps: . Multiply the number of horizontal pixels by the number of vertical pixels to obtain the total number of pixels. . Multiply the total number of pixels by the colour depth of the image to obtain the total number of bits. . Divide the total number of bits by to get the file size in bytes. . Divide the file size in bytes by to get the file size in kibibytes. Worked Example The image here is to be stored on a computer’s hard disk. To work out the total file size in kibibytes we can use the following information: • The number of horizontal pixels is and the number of vertical pixels is . • The colour depth is bits. Therefore, the calculation of the file size is as follows: vertical pixels × horizontal pixels = (total number of pixels) × (colour depth in bits) = (total number of bits) ÷ = bytes (file size in bytes) ÷ = KiB (file size in kibibytes) 16 SB CS PP.indb 16 Computer Systems 14.5.21. 14:13 Chapter 1 .. Calculating the File Size of a Sound File The size of a sound file can also be calculated by following several steps. . Obtain the following data about the sound file: • the sample rate (sometimes referred to as the frequency) • the resolution (sometimes referred to as the bit depth) • the number of audio channels that have been recorded (one channel is a mono recording, and two channels is a stereo recording) . Multiply the sample rate by the resolution by the number of channels to calculate the bit rate, in bits per second. . Multiply the bits per second by the length of the sound recording in seconds, to calculate the total number of bits. . Divide the total number of bits by to get the file size in bytes. . Divide the file size in bytes by to get the file size in kibibytes. . Divide the file size in kibibytes by to get the file size in mebibytes. WB LINK Consolidate your understanding by completing Exercises 1-3, pages 12-14 in the Workbook. Worked Example The sound file below is to be stored on a computer’s hard disk, and we need to work out the total file size in mebibytes. We know the following information: • the sample rate of this sound file is samples per second (hertz) • the resolution of the file is bits per sample • the number of channels used to make the recording is • the sound file is seconds in length Therefore, we can calculate the file size as follows: × × = (the bit rate, in bits per second) × = (total number of bits) ÷ = bytes (file size in bytes) ÷ = kib (file size in kibibytes – rounded) ÷ = . mib (file size in mebibytes – rounded) Activity Calculate the file size in kibibytes of an image file that has horizontal pixels and vertical pixels, and a colour depth of bits. Calculate the file size of a sound file in mebibytes that has been recorded at a sample rate of samples per second, has a resolution of bits per sample and has been recorded using two audio channels. The sound file is seconds in length. Computer Systems SB CS PP.indb 17 17 14.5.21. 14:13 Chapter 1 . Data Compression DEFINITION Bandwidth: the transmission capacity of a computer network. As files and media become higher quality, the files we use increase in size. Computers only have a finite amount of storage capacity, so some software applications can compress the files to store and share them efficiently . Compression is a technique that reduces the size of a file. The benefits of this are that files can be sent successfully across a network, which requires lower bandwidth and takes less time to deliver, and the compressed files also take up less storage space. There are two types of data compression: lossless and lossy. Each method reduces the number of bits in a file. .. Lossless Compression LINK In lossless compression, file sizes are reduced but there is no loss of data. A simple example is converting a text document to a portable document format (or PFD) file. WB Consolidate your understanding by completing Exercise 2, page 15 in the Workbook. A process called run length encoding (RLE) is another method of lossless compression. This is where a piece of compression software will look for runs of duplicated data and recode these runs as smaller amounts of data. For example, if a run of notes for a sound file looked like this: A A A B B B B B C C it might be displayed as data like this: RLE would look at the duplicates in a run, find the number of duplications and would reprogram the line: (three s) ENRICHMENT Can you find examples of different file types that are created using lossless compression? (five s) (two s) ABC This way, none of the data is lost but the file is compressed by the software finding efficient savings of data where possible. .. Lossy Compression As the name suggests, in lossy compression data is permanently removed from the file to reduce the size. WORD ALERT mp3: MPEG (Moving Picture Experts Group: the organisation that created the file type) Layer 3. jpeg: Joint Photographic Experts Group: the organisation that created the file type. 18 SB CS PP.indb 18 Some ways the software can do this include reducing the resolution or colour depth of an image, or reducing the sample rate or resolution of a sound file. When a sound file is converted to an mp3 file this is an example of lossy sound. An mp file has had enough bits removed to reduce the file size, but not enough to change the sound of the sound file dramatically. This type of compression is perfect for storing many mp files on personal media-playing devices. Similarly, when an image is saved as a jpeg file, bits are removed so that the file looks lower in quality but not enough so that the meaning is lost. Jpegs are often found on websites, as they tend to be smaller in actual size and this allows the page to load faster. Computer Systems 14.5.21. 14:13 Chapter 1 Let’s Map It Computers display many forms of information This is represented by binary code • MAC addresses • IP addresses • Color codes BINARY DENARY HEXADECIMAL Binary Hexadecimal Denary POSITIVE + NEGATIVE - We can convert between the ADDITION MULTIPLICATION DIVISION Text Sound Can lead to BINARY SHIFT Images File sizes can be calculated ASCII Unicode Storage Bits Bytes B I N A R Y Kibi bytes COMPRESSION Files can be reduced in size Mebi bytes Computer Systems SB CS PP.indb 19 IGCSE_CS_TB_CHAPTER_1_with mindmap.indd 19 19 14.5.21.8:08 14:13 10/05/21 PM Chapter 1 Let’s Review 20 SB CS PP.indb 20 What are the differences between the binary, denary and hexadecimal number systems? What is the number in binary? What is the number in denary? In which direction should you read a binary number? Convert the denary number to hexadecimal, using binary to help you. Convert the hexadecimal number D to denary, using binary to help you. Name three examples of the use of hexadecimal numbers in computing. Multiply the binary number by and show the binary result and its denary equivalent. Divide the binary number by and show the binary result and its denary equivalent. What is the name of the furthest-left bit in an -bit byte, used when multiplying? What happens to decimal numbers after a binary division is carried out? What is the name of the process used to convert a positive binary number into its negative equivalent? What is the binary number that represents –? Find the binary number that represents – What is ASCII and how many characters are contained in the character set? Explain the difference between a kilobyte and a kibibyte. An image is pixels horizontal and pixels vertical. It has been created with a colour depth of bits. What is the file size of the image in kibibytes? What is the difference between lossless and lossy compression? Computer Systems 14.5.21. 14:13 CHAPTER 2 Data Transmission COMPUTER SCIENCE WATCH Scan the page to watch a clip on the types of data transmission. Before watching discuss what you expect to see or hear. QUESTIONS At the end of this chapter, you will be able to: understand that data is broken down into packets to be transmitted identify the structure of a data packet describe the process of packet switching define how data is transmitted from one device to another, using different methods of transmission • How is data transmitted between different devices? • How do computers ensure that the data that is transmitted gets to its intended destination correctly and accurately? • Why is it important to keep data secure when sending it to another device across a network? understand what the USB interface is and how it is used to transmit data understand that data needs to be checked for errors and the different methods used to do this explain why data is encrypted and how this is done 21 SB CS PP.indb 21 14.5.21. 14:13 Chapter 2 QUICK CHECK How are computers connected together? How does the internet work? ENRICHMENT The origins of data packets can be traced back to the 1800s when Samuel Morse sent the first telegraphic message and invented what is known as Morse Code, a series of dots and dashes that needed to be translated into letters and words. Data transmission is a vital part of electronic communication. In order for computers and humans to communicate with one another, it is important to understand how that communication data makes its way around a network, transfers from one device to another and how systems ensure that errors are detected and corrected. It is also important to learn how encryption keeps data safe and secure during the transmission process. . Types and Methods of Data Transmission When data is generated by a computer from information provided by human input, it is often necessary for that data to be transmitted either to another device connected directly to a computer, or across a network such as the internet to a device elsewhere in the world. In order for this transmission to occur, data has to be first broken down into packets ready for sending. A packet is a small chunk of data and, when these are sent across a network, the chunks have to be put back together again to formulate the original data that was intended to be received. .. Packet Structure A packet of data contains the following pieces of information: Item Packet header DEFINITION Internet Protocol (IP) address: a unique string of numbers separated by full stops that identifies each computer using the protocol to communicate over a network. Description This is added to the data prior to sending the packet and contains both the Internet Protocol (IP) address of the computer that is receiving the packet, and also the IP address of the computer sending it (the originator). The packet header also adds two identification numbers to the data: the number of packets that the data has been broken down into, and the packet number. This is used for ‘rebuilding’ the data at the end of transmission. Payload This is the bundle of data that is contained within the packet. Trailer Each packet has a trailer which is sometimes known as a footer. It contains bits of data that tells the receiving device when it has reached the end of the packet transmission. This is what is known as a validation check, and the trailer ensures that the data that left one computer matches the data that has arrived at the other computer. If the check does not match, the packet will be requested again from the originator. Originator: the sending device. Once data is ready for transmission, it will be broken down into as many packets as are required to send it by the originator and will then be sent across the network or the internet. .. Packet Switching The packets do not travel along cables in the same order that they were created and will often take different routes across a network to get to their intended destination. This process is called ‘packet switching’ and it means that data can be transmitted by the most suitable route to get to its intended destination. The routes that are taken by packets are determined by the router, a device that directs incoming and outgoing traffic on a network. 22 SB CS PP.indb 22 Data Transmission 14.5.21. 14:13 Chapter 2 Data being sent along network cables. As the packets arrive at the destination device, they may arrive out of order. This is where the bits of data that make up the packet header and the trailer become important, as the receiving device will wait until all packets have arrived. Once the packets have all arrived at the destination and the last packet is received, the device will reorder them into the correct order so that the computer can read the data that it has obtained. Finally, the trailer is checked for parity with the originating device and, if the data matches, the transmission process is complete. As with all computing processes, data transmission and packet switching occurs extremely quickly, in a matter of seconds. WORD ALERT Parity: ensuring that something is the same. .. Methods of Data Transmission There are several different methods of transmitting data depending on the type of hardware and connections being used. This is usually a key decision when it comes to buying a new computer, as a user will want to know how fast data can be transmitted between devices. The amount of data that can be transmitted at a given time is called bandwidth. The higher amount of bandwidth available, the quicker the transmission speed. The types of transmission that devices can use to perform data transfer are: • Serial • Parallel • Simplex • Half-Duplex • Full-Duplex HELPFUL NOTES It is important to read the small print carefully when purchasing a new computer to see what connection ports it has – this can make a big difference to your work efficiency. Serial Data Transmission Computer Figure . Serial transmission. Computer Bits (Single) Data Transmission SB CS PP.indb 23 23 14.5.21. 14:13 Chapter 2 ENRICHMENT Can you find out when serial and parallel ports were no longer included in computers? What replaced them and why? This type of data transmission occurs when a computer or device is connected to another computer or device using a single data channel. Data is transmitted one bit at a time, sequentially, down the channel. An example of this type of data transmission occurs when a computer is connected directly to a modem. One of the advantages of using a serial transmission method is that it is very reliable for transferring data over longer distances, although sometimes it is not the most practical. There are also much fewer errors in serial transmission, as bits are sent one at a time, and only one single channel is required to achieve this transmission. Thus, this is a lower cost method of transmitting data. The disadvantage of a serial transmission is that transmission speeds can be slow as only one channel is being used to transfer data. Parallel Data Transmission Computer Figure . Parallel transmission. REFLECT Most modern printers now are connected to computers using network cables and data is transmitted much faster this way. Bits (Multiple) Printer Parallel data transmission is where multiple bits of data are sent at the same time along different channels in the same cabling. An example of this type of data transmission is where a computer is connected directly to a printer. The advantages of this type of transmission is that faster data transmission takes place because of the multiple channels being used. The disadvantages are that this type of transmission is more expensive and synchronisation errors can occur due to the separation of data across different channels. Simplex Data Transmission Input Computer Unidirectional Figure . Simplex transmission. QUICK CHECK What other devices can you think of that use unidirectional data transmission? Simplex transmission is a one-directional (or unidirectional) mode of data transmission. The data will only go one way, and the receiver of the data does not send any data back to the sender. An example of this type of transmission occurs between a keyboard and a monitor. The keyboard sends input data to be displayed on a monitor, but the monitor does not send any data back to the keyboard. The advantage of simplex transmission is that the process can use the full bandwidth of the channel. The disadvantage of this transmission type is that it is not possible to engage in two-way transmission using this method, and most forms of communication rely on this to be successful. 24 SB CS PP.indb 24 Data Transmission 14.5.21. 14:13 Chapter 2 Half-Duplex Data Transmission Transmission Not simultaneous Figure . Half-duplex data transmission. In half-duplex transmission, two-way communication is possible because both devices can send and receive data packets. With half-duplex transmission, although the direction of the data flow can be reversed, transmission cannot be sent in both directions simultaneously. As with simplex transmission, the full bandwidth of the channel is used, but only in a single direction at any one time. Simultaneously: at the same time. ENRICHMENT An example of half-duplex data transmission is in the use of a walkie-talkie handheld communication device. When one device sends data, the other device is unable to do so until the transmission has completed. One advantage of this type of transmission is that it enables two-way transmission using full bandwidth, which is important for communication, representing an improvement on simplex transmission. The disadvantage of half-duplex is that there are delays in the transmission process due to the need to wait to be able to use the bandwidth. WORD ALERT Why would half-duplex data transmission not be an appropriate method of data transmission for a video phone call? Walkie talkies. Full-Duplex Data Transmission WB LINK Consolidate your understanding by completing Exercises 1-3, pages 17-21 in the Workbook. Bi-Directional Figure . Full-duplex data transmission. This method of data transmission is bi-directional, and data can flow simultaneously to and from sender to receiver simultaneously. Full-duplex transmission is made up of two simplex channels, one flowing in one direction, and the other flowing in the opposite direction. It is the fastest method of transmitting data. An example of full-duplex transmission is a telephone network, where users can talk and listen at the same time. Data Transmission SB CS PP.indb 25 25 14.5.21. 14:13 Chapter 2 The advantages of using full-duplex transmission are that it is the fastest method of data transmission due to each communication using its own simplex channel, and there are no delays in receiving data. The disadvantage of using full-duplex is that some networks are not capable of utilising the technology, especially if older equipment is being used, and the technology is only as good as its oldest devices. .. Universal Serial Bus (USB) HELPFUL NOTES USB technology was first designed and created in the 1990s by Ajay Bhatt from the IBM Corporation and has now become the standard technology for plug and play devices in modern computing. LINK WB Consolidate your understanding by completing Exercise 4, page 22 in the Workbook. REFLECT How many different devices do you own that uses a USB connection? WORD ALERT Ubiquitous: located everywhere. 26 SB CS PP.indb 26 A telephone call is bi-directional. The Universal Serial Bus (USB) is a type of communication port that has been built into computers in order to do away with other older forms of port. As discussed earlier in the chapter, serial and parallel transmission of data were the industry standard for sending and receiving bits of data to and from devices such as printers, keyboards and mice, and this meant that computers had to be manufactured with several of these ports built into them. The USB logo. The USB port was designed to be a much more versatile port and, soon after it was designed, computing manufacturers began designing devices that had USB connectors as a standard. USB connectors come in a variety of types, with Type-A (rectangular) and Type-B (square with slanted corners) being the most popular type at first, being joined more recently by Micro-USB and Type-C connectors. Type-C are now the standard for many types of mobile devices and laptops, due to their ability to supply power as well as transmit data. USB cables contain two wires for power supply purposes and two wires for data transmission. They are designed to be able to supply power and transmit data across a variety of different devices. Due to their inter-operability, USB is now the connection of choice for manufacturers, and devices such as keyboards, mice, hard disk drives, headphones, mobile phones, tablets and laptops all use the technology. Different devices have different numbers and types of USB ports depending on their usage, and many mobile phones just have one USB port that is used for both charging the device and transferring data to other devices. The advantages of USB are that they are so ubiquitous, and there are millions of devices that have been produced that use the technology in some form. The technology is very easy to use as the connectors plug in simply. The ability to supply power as well as data means that external power sources are not needed for devices, keeping costs lower. USB connectors and their ports. Data Transmission 14.5.21. 14:13 Chapter 2 The disadvantages of USB are that data transmission speeds are still relatively low compared with other types of transmission (although it is increasing all of the time as the technology develops). Also, the length of cable can have an effect on the transmission quality, therefore it should not exceed metres. . Methods of Error Detection Despite all of the technology that is evolving when it comes to data transmission, sometimes errors can occur in the transfer of data from sender to receiver. When data is changed or altered in transmission, it is known as corruption, and it is usually due to interference with the data during the process of transmission. It is therefore important for computers to be able to detect these errors. DEFINITION Corruption: where something is altered or changed without a user knowing. Parity check: is a bit added to a string of binary code as the simplest form of error detecting code. There are several methods that are built into computer processes for error detection, including the parity check, checksum, echo check and automatic repeat requests. There are also methods for checking errors in data entry. Data transmission errors can lead to problems and need to be detected and stopped. .. Parity Check WORD ALERT This type of error checking first requires a protocol to be agreed upon between the sender device and receiver device. A protocol is a set of rules that both devices will follow. When parity check is used as the method of error detection, the protocol can either be even or odd parity. Protocol: a set of rules that are applied to the transfer of data. Whichever type of protocol is used, a parity check involves adding an additional binary bit (a or a ) to the end of a -bit byte to ensure that the number of bits is either even or odd. Computer Computer 10110011 1 10110011 1 Parity bit Even Parity bit Parity check passed Computer Computer 10110011 1 10110011 0 Parity bit Even Parity bit Parity check failed Figure . No Parity check. Retry Once the protocol of parity has been agreed, the sender then adds either an extra or extra to the end of the code. The byte is then sent, with the parity bit attached to the receiver. Once the data has been received, the receiving device will check that the number of bits is correct according to the agreed protocol (odd or even). As long as this is the case, then the data transmission has been successful. If the parity does not match the agreed protocol, the receiving device will ask for the data to be re-transmitted. Data Transmission SB CS PP.indb 27 27 14.5.21. 14:13 Chapter 2 It is also important to note that a parity check will not always detect an error, if the number of s in the received byte adds up to the correct parity. It is also important to recognise that the examples discussed here are in relation to single bytes; when data is transmitted, it is often many multiples of bytes that are sent. In this instance, the same process occurs, however the parity is calculated either using a parity byte attached to a set of bytes, or using a parity block, which is a symbol added to the end of a block of code. .. Checksum ENRICHMENT The arithmetic that is carried out in checksum is usually an algorithm of some description. This method again requires an agreed protocol to be determined prior to the data transfer, this time involving a mathematical calculation or sum. An algorithm is used to calculate a checksum value from the data that will be transmitted, and then the block of data is transmitted along with the checksum that has been calculated using this method. The receiving device will then re-use the algorithm based on the data it has received, and will compare the two checksum values. If the values match, then the data transmission has been successful. If the checksum values do not match, the receiving device will ask for the data to be re-transmitted. .. Echo Check This is a different type of error check, in that there is no agreed protocol prior to transmission. In an echo check, the receiving device will immediately send a copy of the data back to the sender and a comparison is carried out. If there is any difference between the two sets of data during the echo check, the data will be re-transmitted. .. Automatic Repeat Requests (ARQ) HELPFUL NOTES An ARQ is based upon repetition, and this repetition will occur as often as needed before the data is sent successfully. This form of error checking uses the concept of time to ensure successful transmission of data. When a sending device sends a block of data, the computer will wait for a positive or negative acknowledgement from the receiving device. A positive acknowledgement will be a recognition that the receipt of the data has been successful, and a negative acknowledgment will indicate that data has not been received. If a positive acknowledgement is received, the ARQ will stop sending the data, but, if a negative acknowledgement is received, the ARQ will continue sending the data until a positive receipt is notified. The ARQ check also recognises that timeouts may occur, in that no acknowledgement is received at all. In this case, after a set period of time waiting, the data will be sent again, and this will continue until an acknowledgement comes back to the sender. .. Check Digits DEFINITION Barcode: a machinereadable code in the form of numbers and a pattern of parallel lines of varying widths, printed on a physical item. This pattern identifies it from other barcodes. ISBN number: International Standard Book Number, a global system for identifying individual books. ISBN numbers have 13 digits. 28 SB CS PP.indb 28 The error detection systems described above help to spot errors during the transmission of data between two different devices. Sometimes, data discrepancies can occur due to human input errors. The check digit is an error check that is designed to spot these human errors and is a final number that is added to the end of a numerical code. Check digits can be found on barcodes and ISBN numbers on the back of books. It is a digit that is calculated using all of the other digits in the code and, depending on the product, there will be a particular mathematical calculation that will be carried out on the code to generate the check digit. A barcode found on products in shops. If the check digit does not match the expected result, then it may be that the barcode has been mis-read or that a human error has occurred. This would then mean that the item code has to be rechecked to ensure that it is correctly listed and priced. Data Transmission 14.5.21. 14:13 Chapter 2 Worked Example A barcode is created for a new toy on the market. The barcode number is as follows: 5 ENRICHMENT The check digit in this barcode is the number 5, this is highlighted in red above. This has been generated by carrying out the following mathematical calculation: Step : Add Digit to Digit Step : Divide by Digit Step : Add Digit + += The computer in the toy store will know this calculation and so, when the barcode is scanned, the check digit will be read to make sure it matches the expected result. ( ) Check digits are often found at the end of numerical codes, such as on a barcode. Can you find the check digit on the barcode for this book? . Encryption As we rely ever more on communication and transmission of data across networks like the internet, it is so important to ensure that these transmissions are as secure as possible. Insecure transmission of data can lead to potentially harmful situations and leave your data vulnerable to hacking or interception. A way of keeping data safe and secure during transmission is to use a method of protection called encryption. The origins of encryption can be traced back to Julius Caesar, in Roman times, who came up with the fairly simple idea of changing messages by moving the alphabet forwards or backwards a number of steps. This is called the Caesar cipher. You would first number the alphabet from to starting with the letter ‘a’ and numbering all the way to ‘z’. Once you have done this, you can then decide on an encryption protocol such as −, meaning that you move the alphabet backwards two steps, as per the table below: Text Cipher A B C D E F G H I C D E F G H I J K L M N O P Q R S T U V W X Y Z J K L M N O P Q R S T U V W X Y Z A B REFLECT It is possible to make your own Caesar cipher code wheel to enable different forms of encryption protocol to be used. QUICK CHECK What types of information do you think you might share when buying an item online? Therefore, a message such as “HELLO WORLD” would become “JGNNQ YQTNF”. As long as both parties know the protocol, messages can be deciphered. Data can contain private or sensitive information, for example, users’ personal information from their online bank accounts, or payment card details when purchasing an item from a website. When these packets of data are transmitted across a network, it is vital that this information remains private and secure to prevent criminals from accessing potentially sensitive information. When using websites such as online banking or making online purchases, you will notice that, when completing a transaction, the protocol changes from just hypertext transfer protocol (http) to secure hypertext transfer protocol (https). This can be noticed by looking at the address bar of the browser being used to access the web page. WORD ALERT Transaction: the process of buying or selling something. Data Transmission SB CS PP.indb 29 29 14.5.21. 14:13 Chapter 2 WORD ALERT Decipher: converting code into normal language. Secure http ensures that a secure connection is made between the two devices engaging in the transfer of data. The data packets are encrypted before they are transmitted across the network and are decrypted only when they reach their intended destination. This ensures that criminals such as hackers would be unable to access the private and confidential information as they would be unable to decipher the encryption. Any data that was intercepted during this process would be meaningless to the hacker. The process of encryption requires the devices at either end of the transfer to use an encryption key to unscramble the secure data. Websites built with encryption technology will give users the confidence to carry out these transactions. There are two types of encryption that use keys to scramble and unscramble data: symmetric and asymmetric encryption. .. Symmetric Encryption HELPFUL NOTES When dealing with the encryption of computer data, unencrypted data is referred to as ‘plaintext’ and encrypted data is referred to as ‘ciphertext’. This is the simplest type of data encryption, and involves the sender and receiver of data having a secret key that is used to cipher and decipher the data. A symmetric secret key is usually a string of numbers, a word or random letters that is merged with the text of a message to change the data. As both the sender and receiver know what the key is, it can be easily removed from the message, leaving the actual text in its place. The problem with symmetric encryption is that the key has to be known and shared by both sender and receiver prior to transmission, meaning that it could potentially be intercepted and become insecure. A better and newer method of encryption would be asymmetric encryption. LINK WB Consolidate your understanding by completing the Exercises from pages 23-25 in the Workbook. .. Asymmetric Encryption Encryption requires the use of keys. This type of encryption is also what is called ‘public key encryption’. This type of encryption uses two different keys to cipher and decipher a message. It is more secure than symmetric encryption which only uses one key. When a message is ciphered ready for transmission by a sender, the receiver will generate a pair of keys: a public key and a private key. The public key is shared with any device that might wish to send a message to the receiver. The sender will then use the receiver’s public key to encrypt the message ready for sending. However, the public key cannot be used to decipher the message. When the receiving device obtains the message, it then has to use the private key to decipher the message and since this is never shared, it is a more secure process compared to asymmetric encryption. Activity 1 2 30 SB CS PP.indb 30 You wish to send the following message to your friend: MEET ME AT THE SHOP ON SATURDAY MORNING Come up with a cipher key protocol to encrypt this message, encrypt it and ask your friend to decrypt it using your protocol. Once you have tried this, send a message of your own, using a different encryption protocol. How would you encrypt and decipher numbers and punctuation codes, such as question marks? Data Transmission 14.5.21. 14:13 Chapter 2 Data Transmission SB CS PP.indb 31 31 14.5.21. 14:13 Chapter 2 Let’s Review 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 32 SB CS PP.indb 32 What is a data packet? Inside a data packet there are three components, what are they called? What is the job of the trailer in a data packet? What does packet switching mean? What is the difference between serial and parallel data transmission? Explain the link between simplex and full-duplex transmission. Why is half-duplex transmission not used in telephone communication? What do the initials USB mean? Name three devices that have USB connections. What are two ways that data could be changed during transmission? What are the two types of parity checks? True or false: a echo check is where data is checked only by the receiving device. What is the purpose of a check digit in a barcode? Explain a timeout when an automatic repeat request occurs. True or false: asymmetric encryption uses just one key when ciphering and deciphering data. Why is encryption important when transmitting data? Data Transmission 14.5.21. 14:13 CHAPTER 3 Hardware COMPUTER SCIENCE WATCH Scan the page to watch a clip on CPUs and the main characteristics of the Von Neumann model. Before watching discuss what you expect to see or hear. QUESTIONS At the end of this chapter, you will be able to: • understand that a microprocessor is a type of integrated circuit on a single chip • How does the CPU control the internal and external hardware? • What does computer architecture look like? • How do the input, output and storage devices link together in a computer? • define the role of the central processing unit (CPU) in a computer • identify how each component in the CPU operates to create the fetchdecode-execute cycle • explain what can affect the performance of a CPU • define what is meant by an instruction set • understand that an embedded system is used to perform a dedicated function in a range of different systems • identify a range of different input and output devices • explain what a sensor is used for, including the type of data they capture • identify that there are two types of storage: primary and secondary storage • understand how virtual memory is created and used • define what cloud storage is and what the advantages and disadvantages are • identify the components required to connect a computer to a network, including the role of each component • understand what is meant by a media access control (MAC) address and an internet protocol (IP) address and how they are used 33 SB CS PP.indb 33 14.5.21. 14:13 Chapter 3 . Computer Architecture DEFINITION Architecture: how a computer system is designed, including the rules and methods that the system should follow. A computer device is made up of a range of components, both internal and external. All the components have important roles in the successful operation of the device. Whether it is a desktop computer, a laptop, a tablet or a smartphone, the basic principles of the architecture are the same. An important part of this architecture is the rules and methods the components follow. Figure . maps out these principles. INPUT PROCESS OUTPUTS STORAGE Figure . A basic computer architecture diagram. HELPFUL NOTES In computing terms, instructions and information tend to be qualitative and data is quantitative (numerical). WORD ALERT Intricate: very complicated or detailed. All computing devices are based upon the straightforward premise that items of processing hardware require some input of information. This information is converted into data that the processor can carry out calculations with and turns the information into instructions. Some of this data may need to be stored and recalled, and the computer will then produce an output depending on the instructions and data that has been processed. .. The Central Processing Unit (CPU) At the heart of every computer system sits a processor chip. This central processing unit (CPU) is crucial to the operation of a computer system, and it is the job of this device to process the instructions and data entered through the input devices. The CPU then uses the data to perform various operations and ultimately produces an output. The CPU is also known as a microprocessor, which is an intricate set of circuits contained on a chip. These circuits are microscopic in size so can be built into a variety of devices. The central processing unit. 34 SB CS PP.indb 34 Hardware 14.5.21. 14:13 Chapter 3 .. von Neumann Architecture In the s, computer scientist and mathematician John von Neumann further developed the computer architecture principles shown in Figure .. He established a design still used in the development and manufacture of computer systems today – to work effectively, computer systems need a method of storing programs while they are running. ENRICHMENT What other developments was John von Neumann responsible for? Central processing unit Control unit Input device Arithmetic / Logic unit Registers AC PC CIR MAR MDR Output device Memory unit REFLECT Figure . von Neumann architecture. This type of architecture is used as the starting point for most computer devices. Von Neumann discussed how the CPU requires input and produces output, and that the microprocessor contains several different components: a control unit, an arithmetic logic unit and a set of smaller components called registers. The architecture also includes a memory unit with instructions and data, both read from and written to. This acts as a storage bank for instructions that are used regularly by the CPU while the computer is powered, and is called random access memory (RAM) (see section ..). Finally, buses or connections carry the data from one component of the CPU to another, as shown by the arrows in Figure .. Can you draw the flow of data between the different components of the CPU? LINK See section 3.1.7 The Memory Unit. .. The Control Unit (CU) The control unit is the part of the CPU that controls all of the input and output devices as well as the arithmetic logic unit (ALU) (see below) and the memory unit. The CU is responsible for making sure all these components follow the instructions it has processed from the input. .. The Arithmetic Logic Unit (ALU) As the name suggests, the arithmetic logic unit enables the processor to carry out mathematical operations on data, such as adding and subtracting, and logical operations, such as AND, OR and NOT. This is important in respect of processing data, which is numerical digits in its most basic form. LINK See Chapter 10 Logic Gates and Circuits. .. Registers There are five different registers contained within a CPU, all of which are data storage areas. Before data can be processed it must be stored in one of these. The Memory Address Register (MAR) Program Counter (PC) The Memory Data Register (MAR) The Accumulator (ACC) The Current Instruction Register (CIR) Hardware SB CS PP.indb 35 35 14.5.21. 14:13 Chapter 3 REFLECT What is the fastest current speed of processor fitted to computer hardware? How can you find a computer’s specification and the processing speed? • The memory address register (MAR) is responsible for remembering the memory location of data that the processor needs to access. • The memory data register (MDR) holds data that is being transferred either to or from the memory unit. • The accumulator (ACC) stores mathematical or logical results of processing that has been carried out. • The program counter (PC) contains the address or location of the next instruction to be carried out by the CPU. • The current instruction register (CIR) contains the instruction that is being carried out at the current time. The processing of instructions and data by these components is carried out extremely quickly, and this processing speed depends on the specification of the processor installed inside the computer. .. Buses Several buses, otherwise known as connections, carry data around a computer. Of these, there are three specific buses that the CPU uses to transfer information between the control and arithmetic logic units and the memory unit: The address bus The data bus The control bus • The address bus carries the address (or location) but not the data between the memory unit and the CPU. • The data bus carries data between the processor and memory units and the input and output devices connected to the computer. • The control bus carries instructions from the CPU to control the actions of the computer. .. The Memory Unit The memory unit of the CPU stores instructions and processes that the computer needs regularly while processing data. This is a much faster way for the CPU to obtain these instructions than retrieving them from a storage device like a hard disk. This unit is a component called random access memory (RAM), so named because the CPU can directly access any part of the memory. RAM is a type of volatile memory, in that it does not retain its contents when the computer is powered off. The unit is made up of small microchips, each with its own address, which is important for speed of access. Computer bus cables. Random access memory. Activity Can you draw a flowchart to represent the order that data flows from the input devices, around the components of the CPU and to the output devices? 36 SB CS PP.indb 36 Hardware 14.5.21. 14:13 Chapter 3 . The Fetch-Decode-Execute Cycle Arthmetic Logic Unit Input Devices Address Address LOAD SUBSTRACT STORE Random Access Memory (RAM) WB Registers Program Counter Memory Address Register Memory Data Register Current Instruction Register Accumulator LINK Consolidate your understanding by completing Exercises 1-2, pages 27-30 in the Workbook. Key Address Bus Data Bus Control Bus Figure . Fetch-decode-execute cycle illustrated. All modern computers with architecture based upon the work of John von Neumann use a method of processing data known as the fetch-decode-execute cycle. This cycle happens in a matter of milliseconds and enables a computer to logically process the data it receives in the correct order for the user’s requirements. All the component parts of the central processing unit (CPU) are used to make the cycle work. The cycle begins with an instruction given by a user via an input device and is sent to the control unit (CU) via the control bus. The CU then moves the appropriate processing instructions into the RAM. The program counter stores the address location of the next instruction to be carried out. This location number is copied into the memory address register (MAR). The program counter is incremented or increased by one and this register now stores the next instruction to be processed. The control unit (CU) makes a request to the RAM for the instruction and obtains the address of the instruction from the MAR by sending a signal along the address bus. The data that is being held in the RAM in the correct address is carried along the data bus to the memory data register (MDR). Once the instruction arrives at the MDR, it is copied into the current instruction register (CIR). The instruction is then decoded in the CIR using the arithmetic logic unit (ALU) and then carried out. The result of this processing is stored in the accumulator (ACC). WORD ALERT Control bus: a bus that carries instructions from the CPU to control the actions of the computer. The cycle then begins again. Once all the necessary instructions have been decoded and executed within the CPU, the CU then sends the results of the processing to the output devices using the control bus. . Cores, Cache Memory and Clock Speed Other components make up part of the CPU and can make a significant difference to the overall operating speed of a computer. While the CPU processes instructions and data extremely quickly, other factors can affect a computer’s performance. Hardware SB CS PP.indb 37 37 14.5.21. 14:13 Chapter 3 .. CPU Cores REFLECT In traditional computer architecture, there would be one CU, one ALU and one set of registers that comprise the CPU. This would be known as a processing core. Computers are now available that are dual-core and quad-core, with eight cores or more also possible within one system. What is the highest number of cores that a computer has been manufactured with? With a dual-core processor a computer has two CUs, two ALUs and two sets of registers, enabling it to fetch, decode and execute twice as many instructions, simultaneously. More cores mean more processing power and a higher capability compared to a system with a single processor core. Each core can perform the fetch-decode-execute cycle independently. LINK WB Consolidate your understanding by completing Exercise 3, page 31 in the Workbook. .. Cache A CPU core. Modern CPU chips have a small amount of RAM built in, called a cache memory. This is different from a computer’s main memory and is used where a processor has instructions and data it needs regularly. These are stored in the cache for quicker access, rather than fetching the instructions and data from the main RAM each time they are required. The bigger the cache memory, the less time it takes for the processor to fetch the instructions and data it needs most often. ENRICHMENT What is meant by ‘overclocking’ a processor? .. Clock Speed Clock speed is an important measure in terms of CPU performance capabilities. This refers to the number of electrical pulses that the clock inside the CPU can produce every second. This measurement is made in hertz, and modern clock speeds are usually measured in gigahertz. One gigahertz equals one billion electrical pulses per second. The higher gigahertz that a processor is clocked at, the more fetch-decode-execute cycles can be carried out by the CPU. . Instruction Sets A set of common instructions have been developed by processor manufacturers so that CPUs operate as efficiently as possible. This instruction set is all the commands that can be processed by a CPU. The instructions are the most basic types of command a computer can respond to and execute, and these are referred to as operations. These operations ensure that the control unit and arithmetic logic unit can carry out their respective jobs easily. Operations are made up of opcodes and operands. Opcodes are used to perform an action on an operand. We refer to coding such as this as machine code. .. Opcodes In straightforward terms, an opcode, short for operation code, gives the CPU a precise job that is required to happen, and the opcode then needs a piece of data to carry out this job on. Opcodes can either tell the components an operation to carry out or can instruct one of the units to do something to a particular piece of data. An example of an opcode would be ‘ADD’, ‘DIV’ or ‘GOTO’. The opcodes are stored on a computer’s hard disk and would usually be copied into the main RAM when the computer is powered on. The most regularly used opcodes would then be moved from the RAM to the cache memory. 38 SB CS PP.indb 38 Hardware 14.5.21. 14:13 Chapter 3 .. Operands An operand is the data that is required for the specific job as detailed by the opcode. The operand may be a piece of data itself, or it may be an address location within the main RAM or a register. Examples of opcodes and operands • ADD (where may be a number to add to a different piece of data held for processing) • DIV , (where and may refer to address locations) • GOTO (where may refer to an address location) Activity Make a list of five additional opcodes that a computer uses and write down a definition of what each opcode does. . Embedded Systems When discussing processors and computer systems, we have traditionally tended to think about desktop and laptop computers. These are referred to as general purpose computers, capable of performing a wide range of different activities. However, there are other types of computer system that carry out rather more specific tasks and jobs. An example of this is known as an embedded system. With an embedded system a larger device uses a small built-in computer to carry out its functions in a more effective way. The computer system usually has a very specific job, and only carries out that job when required. Embedded systems in the home Embedded systems outside the home Dishwashers Vending machines GPS and satellite navigation Lighting systems Central heating systems Closed circuit television (security) A GPS device is an example of an embedded system. Calculators One of the key features that sets an embedded system apart from a general-purpose system is that the user is simply a user rather than having an influence over the programming of the device. On a laptop, for instance, a user can upgrade the operating system of the computer, but on a satellite navigation device they have to plug the device into a computer and let it update automatically or send the device away to the manufacturer for an update. Embedded systems tend to be low power devices due to their limited nature and capabilities. This does mean that they can be quite compact (for example a watch), and they can also be operated using a battery for power (such as a calculator). Activity Think of three devices in your house that you would classify as an embedded system? For each device, describe the information and data that it processes, and how a user might interact with the device. Hardware SB CS PP.indb 39 39 14.5.21. 14:13 Chapter 3 . Input Devices A variety of input and output devices are used to control and interact successfully with computer software. An input device is a piece of hardware that a human uses to give commands to and interact with the computer, and provide data for the computer to use. This data is then processed by the computer to produce an output. Keyboard DEFINITION Universal serial bus (USB): a standard connector found on many different types of computer and used to connect external devices. Bluetooth: a form of wireless connection for connecting devices together when they are near each other. • A keyboard is one of the most important input devices used to give data and instructions to a computer. • It has a selection of keys that all perform different tasks. • Its main role is for the entering and typing of letters and numbers. • A keyboard also has arrow keys for movement, control keys that perform standard input tasks and function keys that perform more specific tasks. A standard computer keyboard. • Larger keyboards have a numeric keypad (see below), which is useful for financial or accounting purposes. • Laptop keyboards tend to be more compact with essential keys only. This means the keyboard is lighter and smaller. • The keyboard is connected to the computer using either a universal serial bus (USB) port or wirelessly using a Bluetooth connection. • Tablets and smart phones have electronic touch keypads instead of a physical keyboard. Numeric Keypad REFLECT The QWERTY keyboard is the standard one used in computers around the world. It is named after the order of the first six letters. Can you find out about different types of keyboard layout? A numeric keypad is a small numbered pad of keys or buttons labelled from to . It is often found on a standard computer keyboard but not usually on smaller laptops. Numeric keyboards are also often located beside locked doors or control boxes for alarm systems and are used to gain access to a building or a room. While they are useful for entering numerical data quickly, this keypad often has a single purpose, such as entering a keycode. The buttons or keys also tend to be much smaller than keys on a computer keyboard. A numeric keypad. 40 SB CS PP.indb 40 Hardware 14.5.21. 14:13 Chapter 3 Pointing Devices – Mouse A mouse is a standard pointing device, usually packaged with a computer alongside a keyboard but also available to buy separately. A mouse typically has two buttons – for left and right clicks – and often has a jog wheel in between the buttons for easy scrolling. This device is connected to a computer using either a USB port or wirelessly with a Bluetooth connection. A standard computer mouse. A mouse is used with operating systems and other software for giving point and click instructions to the computer and for more complicated processes such as selection and dragging. It works by shining optical light onto a flat surface, which is translated into directional movements of the onscreen pointer. Other Pointing Devices DEFINITION Operating system: a piece of software that communicates with the hardware and allows other programs to run. There are several other pointing devices that operate in a similar way to a mouse. • Touchpads are pointing devices installed within a laptop for convenience and portability. • Trackballs are used to point and move in any direction and allow greater accuracy in precision movements. • Stylus pens are used with tablets to input graphical information and for digital drawing. • Gaming controllers are bespoke pointing devices for interacting with gaming scenarios on a games console. WORD ALERT Stylus: a pen that can be used either directly onto a screen or a pad connected to a computer. ENRICHMENT Can you find other types of device that act as a point and click input? Think about computerbased devices in your home – how do you control them? A selection of pointing input devices. Hardware SB CS PP.indb 41 41 14.5.21. 14:13 Chapter 3 Real world examples where these pointing devices are found include: • a trackball on medical equipment • a stylus pen used for graphic design • a gaming controller used with a console Touchpads, trackballs and gaming control devices. Touch Screens A touch screen is made of glass and reacts to a finger press. They usually have a built-in menu. Once the user has made a selection with a finger press, the screen reacts by displaying a different screen or drop-down menu. The touch screen works with simple decisions and does not require huge amounts of input data. They are most common in smartphones and tablets, but larger touch screens can also be found in public places such as airports and shopping centres. There are three different types of touch screen technology: resistive, capacitive and infra-red. Resistive Screens These are the most common type of touch screen. The name resistive relates to resistance – the amount of downward pressure made on the screen by the user. The pressure causes a change in the resistance, or an increase in voltage. The layers of the screen detects the voltage change and calculates the co-ordinates of where the pressure change has happened. This then enables the processor to react to the pressure and display the item the user requires. 42 SB CS PP.indb 42 A customer uses a touch screen to give feedback. Hardware 14.5.21. 14:13 Chapter 3 Capacitive Screens In a capacitive touch screen, there are four electrodes at each corner that maintain an even amount of voltage across the whole touch screen. Capacitive technology works on the basis of the human body being naturally conductive, and the electrodes cause a small current flow between the human finger and the screen. As with a resistive screen, this current flow causes a voltage change, which is used by the processor to calculate the co-ordinates where this change occurred. Capacitive screens are more expensive to manufacture than resistive screens, display better quality images and also the ability for multiple touch sensing. WORD ALERT Conductive: heat and electricity can pass through an object. Electrodes: a conductor where electricity enters or leaves an object. Infra-Red Screens While capacitive and resistive screens work through pressure and conductivity, infra-red screens emit a constant grid of lights underneath the top surface layer. The technology works when this light grid is interrupted, and a touch on the infra-red screen causes a disturbance. The disturbance is then located by the processor and translated into co-ordinates. An infra-red screen is much more sensitive than capacitive or resistive screens, and only requires a very light touch to create the interruption. This means that the screens can be much more durable, however they are susceptible to false touches because of the increased sensitivity. Scanners Scanners are used to convert text or images on paper into digital information as follows: • A paper document is placed on the scanner and a beam of light is shone onto the paper. • This light reflects onto a sensor, which determines the colour of the text or image on the paper. • The information is used by the computer, as an input, to create a digital copy of the document. Scanners can also be used alongside software called optical character recognition to convert written text into digital text, however some words may not be converted accurately because of the handwriting. You might also use a scanner to preserve and save old photographs. ENRICHMENT A paper document being scanned using a flatbed scanner. The most popular type of scanner is a flatbed scanner, however handheld scanners and specialist film scanners perform similar functions. Scanners can also work in three dimensions and use reflected laser light to build up a D model of a scanned object. These images can then be used with a D printer to create a model. Camera WORD ALERT A web camera (webcam) takes a digital image of the view in front of its lens. If the camera takes set images one after the other at a high enough frame rate, this can be viewed on a computer screen as a video feed. These videos can then be sent from one computer to another in the form of a video conference. Web cameras are either stand-alone devices connected by a USB port, or they can be built into a laptop or PC monitor just above the screen. A web camera (or webcam) used for sending digital images to other users. Hardware SB CS PP.indb 43 Scanned documents have replaced many forms of paper-based communication. How is this technology being used in business to replace things that have traditionally involved paper? Video conference: a form of visual communication where users in different places can see, hear and speak to each other using a variety of equipment, including web cameras, monitors and microphones. 43 14.5.21. 14:13 Chapter 3 These cameras can also be used for security purposes by recording images when movement is detected in front of the lens. Another popular use of webcams is viewing attractions such as landmarks or tourist destinations over the internet. WORD ALERT Analogue signals: continuous signals that cannot be processed by a computer until they are converted into digital data. Dictation: the process of reading words into a microphone so that they can be converted from analogue signals to digital words on a screen. Microphone A microphone is used to convert sound analogue signals into digital information. In computers microphones are mainly used with webcams for video-conferencing. The digital signals are sent to another computer user and can be heard as a sound. They are also useful for gaming so players can speak to each other during multiplayer games. Microphones can also be used with dictation software to convert spoken words into digital text. Many computers have microphones built in, but external microphones and those built into specialised headsets are attached to computers using the audio port. Barcode Reader A computer microphone for converting vocal signals into digital information. REFLECT Does the language or dialect you speak make a difference to computers when you are speaking into a microphone? How does a computer ‘get used’ to your voice? A handheld barcode scanner reads a barcode with infrared light. A barcode reader is often found attached to a point of sale (POS) computer in a shop or business. The reader accesses information about a product within the store. The barcode holds information such as the product identification number, country of origin and manufacturer. However, it does not store the price of products, which is held in a database. During the purchase process the computer scans the barcode information and matches the data to the database to check the most up-to-date price. The barcode scanner uses infra-red light to read the bars in the code. This light is reflected back to the device and is converted into digital data. Barcodes are also used for tracking parcel deliveries or baggage in airports. 44 SB CS PP.indb 44 Hardware 14.5.21. 14:13 Chapter 3 Quick Response Scanner A quick response (QR) scanner is a device that reads QR codes. QR codes tend to look like square patterns. The codes in the pattern contain a small amount of data as information such as website URLs and contact details. Many smartphones have QR readers and the codes can be scanned quickly to access information. The codes avoid the user having to remember long telephone numbers and website addresses, because the QR reader will quickly convert the QR code into the information. REFLECT Why would you use QR codes instead of barcodes? A smartphone is used with a built in QR scanner. . Output Devices Output devices are the hardware a computer uses to display or send out the data that has been processed. Input devices that provide the computer with the instructions are linked to the output devices, so the user can see or hear the results of those instructions. The choice of output device depends on the most appropriate use of the data that has been processed. WORD ALERT Array: a data structure that holds related data. Monitor A monitor or a screen is a common output device that comes in various sizes and shapes and has different uses depending on the data being processed and output. • Monitors are measured diagonally from one corner to another in inches, e.g. a -inch screen. • The picture that a monitor can display is made up of thousands of coloured dots. These are called pixels. • Liquid crystal display (LCD) monitors use a combination of red, green and blue to make any colour of pixel required for the output. • Light emitting diode (LED) screens use an array of light emitting pixels. • Monitors can display a certain number of pixels depending on the quality – more pixels mean a better quality of picture output. • However, the larger the monitor the more expensive they tend to be. • Most laptop computers come with small monitors built into the case, whereas PC towers tend to have stand-alone external monitors. • Modern monitors connect to a computer using a high-definition multimedia interface (HDMI) connector. DEFINITION HDMI: high-definition multimedia interface technology displays high-definition images and sound through a single cable. HDMI is a standard connection port for audio/visual devices in computers. A large screen monitor in use in an office. Hardware SB CS PP.indb 45 45 14.5.21. 14:13 Chapter 3 Touch screens A touch screen can be used both as an input device (refer to page ) and an output device. Touch screens are used on smartphones and tablets. They are menu- and choice-driven and require a user to interact with the screen for it to work correctly. Once the user has made a selection with a finger press, the screen reacts by displaying a different screen. Digital Light Processing (DLP) Projector • A digital light processing (DLP) projector is a device that connects to a computer and a monitor to project the video output from the A touch screen being used to computer onto a wall or a whiteboard. The select icon options. video can be viewed at a much larger size when projected. • They are often used in school classrooms or home cinemas for showing video or presentations. • Projectors are often fixed to the wall or ceiling but can also be portable. • They are connected to a computer with a high-definition multimedia interface (HDMI) connector. • DLPs can be large and use powerful bulbs to project the image. A projector being used to display a computer image at a conference. Liquid Crystal Display (LCD) Projector A liquid crystal display (LCD) projector works in a similar way to a DLP projector. However, the key difference is that red, green and blue lights are shone through three prisms, then brought together, or converged, through a second prism to produce the image. LCD projectors tend to display more vivid images than DLP projectors, however they are often larger and heavier. An LCD projector. 46 SB CS PP.indb 46 Hardware 14.5.21. 14:14 Chapter 3 Laser Printer A laser printer produces a printed output by transferring powdered toner onto paper using heat. The printer connects to a computer using a universal serial bus (USB) interface, or wirelessly across a network. This is a very common type of printer because it prints quickly and produces good-quality results either in black and white or colour, depending on the model of the printer. A laser printer commonly found in a business workplace. The quality of output and the low noise levels make laser printers popular choices for workplaces. Inkjet Printer An inkjet printer commonly found in a home office. Inkjet printers are the cheapest type of printer. They work by spraying ink directly onto paper as it is heated by the printer. The ink flows from a cartridge through tiny holes and when the paper is fed out from the printer the ink is still slightly wet. Inkjet printers can produce either black and white or colour output and are popular choices for use at home and for printing photographs. The printer connects to a computer using a universal serial bus (USB) interface, or wirelessly across a network. Hardware SB CS PP.indb 47 WORD ALERT Interface: a device or program used to communicate with a computer. 47 14.5.21. 14:14 Chapter 3 D Printer ENRICHMENT Three-dimensional or D printers are output devices that can create objects rather than printed pieces of paper. The 3D printer has changed the way that organisations carry out their planning. Can you find out the different types of materials that a 3D printer uses to produce models? D printers often use heated liquid such as plastic or metal. The type of liquid used depends on the item being produced. This liquid is given instructions by the computer to create a surface and then it solidifies. The printer uses several layers of this liquid material to create the shape. D printers are used mainly by designers to create prototypes of objects and have been used in car manufacturing for many years. The printer is used with a computer and computer aided design (CAD) software. A D printer prints a blue model. ENRICHMENT Large actuators can be used to control flood defences on large rivers, which protects towns and cities. Can you find another example of a large actuator in current use? WORD ALERT Sound card: an internal device of a computer that provides a method of input and output of audio signals for use with multimedia applications. Speakers Most computers are fitted with a speaker, which produces sounds to alert the user to a problem or to a decision to be made. Speakers are also used to output music, sound and video soundtracks for a highquality multimedia experience. The sound quality the computer produces depends on the type of speaker used. The internal speakers supplied as standard within a computer tend to produce lower quality sound, but externally powered speakers connected to a computer’s sound card through an audio port produce better quality output. A pair of external computer speakers. Actuator An actuator is a mechanical motor that carries out an action when a computer gives it an instruction. For example, a digital camera has an actuator built into the lens and the motor moves the lens in and out depending on the level of zoom required. It is the actuator that controls this movement. Actuators can be small, as in the case of a camera, or can be large, such as those that control heavy duty computer-controlled drills. A digital camera with an actuator built into the zoom lens. 48 SB CS PP.indb 48 Hardware 14.5.21. 14:14 Chapter 3 . Sensors Sensors are usually external devices that are connected to a computer for measuring something, such as temperature, light or moisture. The sensor tends to be located in a suitable position for collecting the information, and then sends measurements at regular intervals to the computer for analysis. These measurements are converted into readable data. For example, sensors are used to detect certain changes in a home and automatically turn the central heating on when the temperature drops below a set level. DEFINITION Small microprocessors can be used in situations where a portable computer is needed, for example in a restaurant kitchen. A moisture sensor. Types of Sensors Sensor Microprocessor: Microprocessors are integrated circuits that contain all the functions of a CPU of a computer. Data captured Data type Example of use Acoustic Sound levels At a concert Decibels Accelerometer Whether an object is static or in motion; can detect motion changes Fitness tracking devices Kilometres/miles per hour Flow The amount of liquid or vapour that passes through them Medical equipment Millilitres, vapour pressure Gas The presence of gas Used by gas engineers Cubic metres/feet Humidity and moisture The amount of moisture in the air Air conditioning systems Grams per cubic metre Infra-red Light in the infra-red spectrum – often used for measuring distances Professional sporting events such as the javelin Voltage (on or off ) Level Height of liquid In rivers that flood regularly Millimetres, centimetres, metres Light The level of ambient light Security systems or streetlights Lux Ambient: the immediate surroundings. Magnetic field The strength of a magnetic field Satellite navigation and GPS systems Tesla pH Acidity or alkalinity of a liquid Water treatment or sewage systems pH Pressure: continuous physical force exerted on an object. Pressure The pressure of gases or liquids in a system For measuring weather Millibars, Newtons Proximity Can detect the presence of objects without any physical contact Security systems Centimetres Temperature Changes in the ambient temperature of a room or object In a kitchen for food safety purposes Degrees Celsius or Fahrenheit WB Consolidate your understanding by completing Exercise 1, page 32 in the Workbook. Hardware SB CS PP.indb 49 LINK WORD ALERT 49 14.5.21. 14:14 Chapter 3 Activity Read each of the following scenarios. Select from the table above the most appropriate sensor(s) for each task. State why this is useful for the user. A A shop owner wishes to improve security in their store and is also keen to find out how many customers are visiting the shop each day. B A band is playing a series of differently sized venues over a three-week period and wants to set the correct sound levels for their sound system. C A science laboratory is growing vegetables in a small greenhouse and needs to see how well the plants are doing over the period of months. . Data Storage DEFINITION Volatile: loses its contents when there is no electrical charge. It is important to know the differences between memory and storage before we begin to understand their purpose within a computer system. • Memory is the microchips, transistors and capacitors that store all the instructions a computer needs to operate. It can be volatile – one type of memory (RAM) loses its content when a computer is powered off, but the other type of memory (ROM) has a fixed set of instructions and these cannot be changed or overwritten. • Storage refers to the devices within a computer where user information and data such as files, documents, applications, video and music is kept. This storage is non-volatile, and the contents remain stored even when the computer is powered off. Memory is referred to as primary storage because it is essential for the computer to function, to power up correctly, and ensures that the input, storage and output devices are able to start. There are two types of primary storage: random access memory (RAM) and read only memory (ROM). Secondary storage refers to hard disk drives and other types of flash storage devices that are used for storing user data. LINK See section 3.1.2. .. Primary Storage Random Access Memory (RAM) As explored earlier in the chapter, the memory component of the CPU is important to store instructions and a list of processes that a computer needs regularly while processing data. It is also a much faster way for a CPU to obtain these instructions than retrieving them from a secondary storage device like a hard disk. This component is called random access memory (RAM) because the CPU can directly access any part of the memory. RAM is a type of volatile memory as it does not retain its contents when the computer is powered off. Read Only Memory (ROM) Read only memory (ROM) contains the vital instructions a computer uses when it is first powered up. The ROM will initialise all the component parts and will enable the input and output devices to communicate with the hardware inside the computer. The ROM also contains instructions on which secondary storage device to access first to enable the operating system to load. Once the ROM instructions have all been carried out, the RAM is then used as the primary storage. The CPU can access the ROM directly. 50 SB CS PP.indb 50 Hardware 14.5.21. 14:14 Chapter 3 .. Secondary Storage Secondary storage is any device that is used by a computer to store data longer term. This can include internal or external hard disk drives, solid state drives, flash storage such as pen drives and optical storage. Unlike primary storage components, secondary storage is not accessed directly by the CPU. Secondary storage is non-volatile, meaning that it retains data even when a computer is powered off. There are three different types of secondary storage: magnetic, optical and solid state. Each has different characteristics and uses. Magnetic Hard Disk Drive A open view of an internal magnetic hard drive. WORD ALERT Magnetic hard drives are the most common hard drives inside computers. The hard drive consists of a stack of round metal plates, known as platters. These platters are coated in a magnetic material. Data is stored within this magnetic material and the platters rotate very quickly on a spindle. An electromagnetic read/write head, which looks a little bit like a needle, can access, add and remove data from the platters. The head never touches the metal platters because it floats on an air layer created by the spinning of the plates. If the head did touch the platters, or some dust was able to access the drive, this would be enough to damage the device. This type of storage is known as non-volatile storage. Non-volatile means that the device keeps its data stored when the device has no power. The storage device is connected directly to the motherboard of the computer, usually using a serial advanced technology attachment (SATA) cable. The hard drive also requires power and is connected with a second cable directly to the computer’s power supply. The hard drive is securely mounted within the casing of a desktop or laptop computer. For this reason, fixed hard drives do not need much in the way of external protection, as they are protected by the casing of the computer itself. When a magnetic hard disk has been used and re-used several times, data can be moved around the disc and split into different sectors, which can slow the access to the data by the computer. This is known as fragmentation – hard disk drives often have to be defragmented in order to improve the access to them. Electromagnetic: the electrical and magnetic forces or effects produced by an electric current. DEFINITION Serial advanced technology attachment (SATA): a type of cable usually found inside computers. It connects a hard drive with the motherboard. A portable external magnetic hard drive. Hardware SB CS PP.indb 51 Platter: a circular magnetic plate that is used for storing data in a hard disk. 51 14.5.21. 14:14 Chapter 3 DEFINITION Lightning connection: a high-speed connection that was developed by Apple for the purpose of connecting multiple external devices to their computers. LINK See Chapter 10 Boolean Logic. WORD ALERT Capacitor: a small electronics device that stores an electrical charge. A portable magnetic hard drive works in the same way as a fixed hard drive. However, the platters and read/write head are much smaller, and the hard drive is protected by a durable casing. The drive is usually connected to a computer using a universal serial bus (USB) connection, or a faster lightning connection. Solid State Hard Drive Solid state hard drives are becoming more common in computers – mainly due to the technology getting cheaper. Solid state drives (SSD) are very similar to flash drives (see Pen Drives and Flash Drives, below) as they both use technology known as non-volatile storage. The key difference between an SSD and a magnetic drive is that an SSD has no moving parts. This means that the transfer of data between the drive and the computer processor is much quicker. As with the magnetic drive, this device is connected directly to the motherboard of the computer, usually using a SATA cable. An SSD also requires power so is connected directly to the computer’s power supply with a second cable. A solid state hard drive. In this type of non-volatile storage, the computer forces electrons to be stored within a series of transistors and capacitors. The transistors hold their electrical charge so data can be stored in the capacitors for a period of time without electrical power. When the device is reconnected to the power, the transistors are then charged up again. The forcing (or “flashing”) of electrons into the capacitors and transistors gives this type of device its name – flash storage. This type of storage does degrade under extreme temperatures and the lifespan is determined by the number of read/write cycles. SSD such as flash memory use either NAND or NOR technology. The main difference between these is the way the memory cells inside the semiconductor chips are wired together. ENRICHMENT Computers are now increasingly sold with minimal internal storage, and users have ‘cloud’ storage instead. What do you understand about storing files and documents in the cloud, and what are the advantages and disadvantages of doing so? LINK See the reference to nonvolatile storage earlier in the chapter. 52 SB CS PP.indb 52 • NAND (NOT AND) technology is better for writing and erasing data, and is cheaper to manufacture. NOR (NOT OR) technology is better for reading data. Therefore, NAND technology is more common in computing devices. • A NAND flash memory device contains transistors called control gates and floating gates, and the writing and erasing of data to the device takes place within this component. Control gates sit on top of floating gates. Electrons that register as a , as opposed to a , are squeezed through the gates and are stored as the data that the user requires. When this flow occurs, the electron value changes from to . Portable SSDs are also becoming more popular. These are essentially high-capacity flash storage drives that connect to a computer using a USB connection or a faster lightning connection. Pen Drives and Flash Drives A folding USB pen drive. Pen drives and flash drives are remarkably similar in terms of their general characteristics, and both are non-volatile flash storage devices. A flash drive is a collective term for any drive that uses flash technology to store data. Examples include pen drives, card readers or the storage inside small devices such as digital cameras or television set top boxes. While flash drives do not have unlimited capacity storage space, they do tend to have enough to store a large amount of data depending on the purpose. Hardware 14.5.21. 14:14 Chapter 3 A pen drive, sometimes known as a thumb drive, is a type of flash drive that is designed to insert directly into a USB port on a computer. Pen drives tend to be smaller in capacity than other flash drives, because their main intended use is portability – they can be moved between computers for transferring data from one to another. While pen drives are very useful, it is important that they are not used as the only storage device for personal data; as discussed earlier, the nature of flash storage means that the technology degrades over multiple read-write cycles, and data could be lost. Pen drives are often used as personal data backup storage devices. WORD ALERT Portability: the ability to carry or move something. Degrades: breaks down or deteriorates. Optical Drives Some desktop computers are fitted with an optical disc drive. These drives can read from and write to a variety of media, including compact discs (CD), digital versatile discs (DVD) and Blu-ray discs (BD). Optical disc drives are so called because they use laser light and the light spectrum to read or write the data. Optical drives are becoming less common in desktop or laptop computers as manufacturers attempt to make devices slimmer and lighter. They are, however, a common feature of games consoles. • Compact disc (CD) drives: The most basic CD drive can only read a software application CD or an audio CD. However, CD-R/W/RW drives (CD readable/writable/re-writable) are also capable of writing and/or rewriting data to compatible media. Basic CD drives have been a feature of An optical disc drive. music stereo systems for many years, and the CD is still a popular format for delivering music to consumers. • Digital versatile disc (DVD) drives: DVD drives are similar to CD drives, in that the basic drives can only read applications or video formats such as films. DVD-R/W/RW drives (DVD readable/ writable/re-writable) are also capable of writing and re-writing data to discs. Stand-alone DVD players are common in many home media set ups, and the DVD is a popular format for distributing films and computer applications software to consumers. • Blu-ray disc (BD) drives: Many newer laptops and games consoles are fitted with BD drives. This format is popular for distributing high-definition media content to consumers. The term Blu-ray refers to the blue laser that reads the data on the disc, which uses a much shorter wavelength than the standard red laser in CD and DVD disc drives. This shorter wavelength means much more information can be stored on a BD, even though they are the same physical size as CDs and DVDs. Optical storage devices such as CD/DVD/BD-rewriting drives use the in-built laser to create and read pits and lands as the disc spins. A pit represents a and a land represents a to enable data to be reflected or digitally read from optical media. When data is being written to an optical disc, a read/ write head moves across the surface of the disk and the laser burns a pit into the surface of the disc. These pits and the spaces between the pits (lands) enables the laser to reflect back and convert the data to ’s and ’s – binary data, that is ready to be processed. . Virtual Memory Virtual memory is created by a computer when it has many processes running at the same time. Sometimes, the RAM can become overloaded with trying to process too many instructions at once, so the operating system will use a portion of the secondary storage, usually the internal hard disk, and will designate it a temporary area of RAM. This type of memory is much slower because the data is having to travel much further than if it was contained within the actual RAM. Another thing that causes the computer to operate more slowly is the process of paging or swapping data between the virtual memory and the RAM. Paging is where the computer will move instructions that it does not currently need out of the RAM into the virtual memory and swap in instructions that it does need. Hardware SB CS PP.indb 53 REFLECT What advice would you give to somebody who told you that they only use their flash storage drive to store important files or documents? REFLECT Optical discs have changed over a short space of time, and there was quite a rapid move from CD to DVD to Blu-ray. It looks now like the days of the optical disc will soon come to an end. Can you think of anything you do that would be difficult if you didn’t have a disc? ENRICHMENT Many games consoles are moving away from disc-based games and are moving to something called DLC (downloadable content). Why do you think the disc is now used less? 53 14.5.21. 14:14 Chapter 3 . Cloud Storage ENRICHMENT Do you think that the commonality of solid state hard disks will improve virtualisation? Is there an improvement that could be made to the technology of RAM that would remove the need for virtual memory? HELPFUL NOTES Many mobile phone services come with cloud storage plans, which is enabling manufacturers to reduce the amount of flash storage inside a phone. This frees up space for users to install more applications on their phones, as we increasingly rely on mobile technology to access essential services. LINK With cloud storage, files, data, documents, images, music and video are stored in a remote location. Users purchase some space on an external server that is located somewhere in the world, and access it via the world wide web. The server is connected to the internet and can be downloaded from and uploaded to as necessary. Cloud storage is often used as backup and is also very good for sharing files with other people. The other advantage is that data can be accessed from anywhere with an internet connection. The disadvantage of using cloud storage is that if there is no internet connection then the files cannot be accessed. Additionally, it is the job of the organisation providing the storage to ensure the security of the data, and cloud storage is just as susceptible to hackers as personal storage is. Cloud computing refers to data stored externally. . Network Hardware WB Consolidate your understanding by completing the Exercises 1-3 from pages 34-38 in the Workbook. Computers worldwide connected to the internet. A computer requires certain hardware to access a network. This hardware is a network interface card or controller (NIC), and it provides the computer with wired or wireless connections to a network. When the controller is manufactured, it is given a unique media access control (MAC) address, but this should not be confused with an Internet Protocol (IP) address. 54 SB CS PP.indb 54 Hardware 14.5.21. 14:14 Chapter 3 .. Media Access Control (MAC) Address DEFINITION When the controller connects the computer to the internet, the MAC address gives the controller a unique address and identifies the device on the network. Any device that connects to the internet, either wired or wirelessly, has a unique MAC address. These are made up of a string of numbers, usually from the hexadecimal number system. As the number is preset at the point of manufacture, the address never changes, even when you connect the computer to the internet in a different location. A typical MAC address looks like this: The address is made up of six groups of hexadecimal digits and this represents bits. The first half of the address identifies the manufacturer of the network interface card, and the second half is the serial number of the card. This half of the MAC address identifies the manufacturer of the NIC. Hexadecimal: a number system that uses 16 characters instead of the 10 characters used in the decimal system or the two used in binary. D0 : 81 : 7A : A6 : 82 : D2 The composition of a MAC address. This half identifies the serial number of the device. .. Internet Protocol (IP) Address An Internet Protocol (IP) address is a unique address issued to the device whenever it connects to the internet. These addresses are issued either by the internet service provider (ISP) that provides the connection or the network the computer is connected to. It is the IP address that enables computers all around the world to communicate with each other via the internet. Think of an IP address in a similar way to a postal address – without a postal address on an envelope, letters would not reach their chosen destination. IP addresses are usually four groups of digits separated by dots. The digits are between and , representing bits. This type of IP address is known as IPv and has been in use since the early days of internet usage. This format of IP address allocation offers almost . billion unique addresses. IP address Postal address 63 . 41 . 136 . 21 45 New Street London W1 3BL England An IPv address and a As the internet and its use evolved, there was a need for ISPs postal address. and networks to issue increasing numbers of IP addresses, as more devices became internet enabled. A new standard for the protocol was introduced, called IPv, which allowed for an increase in unique IP addresses from . billion unique IPv addresses up to an enormous undecillion potential unique IPv addresses. Whereas an IPv IP address is made up of four groups (or octets) of numerical digits separated by dots, an IPv address is made up of eight groups of hexadecimal numbers separated by colons. IPv4 ENRICHMENT How do you find out the IP address of the computer you are using? IPv6 63 . 4 1 . 1 36 . 21 2002 : O d a9 : 6 3a3 : 0 0 0 0 : 0 0 0 0 : 7 b 3f : 0 2 2 0 : 64 66 4 groups of numerical digits 8 groups of hexadecimal numbers IPv addresses compared to IPv addresses. There are sometimes double colons within an IPv address – where one of the hexadecimal groups contains all zeros and therefore to save computing space the additional colon marks the gap where these groups would have sat. Hardware SB CS PP.indb 55 55 14.5.21. 14:14 Chapter 3 2002 : O d a 9 : 6 3a3 : 7 b 3f : 0 2 2 0 : 6 4 6 6 The IPv address from above with complete zero groups of hexadecimal numbers replaced by an additional colon. When an IP address is issued to a device accessing the internet, the address can be static or dynamic. REFLECT What would be the benefit of a network administrator setting IP addresses to static? A static IP address is created by a user in the settings of the router (see below). These are rare because static IP addresses can cause problems on a network if set incorrectly. A dynamically issued address is more common. These are issued by routers on a network using a service called dynamic host configuration protocol (DHCP). This enables a router to assign an IP address to any new device that is connected to a network. When a device is removed or unplugged from the network, the address is recycled to another device that may replace it. The use of DHCP and dynamic IP addresses ensures that there is no duplication of addresses on a network and enables all the devices to share the internet connection. .. Routers ENRICHMENT Most home broadband systems have combined modem routers provided by an internet service provider (ISP). What would be the benefits or drawbacks of using an alternative modem and router other than the one from the broadband provider? A router enables a home or business to connect devices to the internet and is normally provided by an internet service provider (ISP). Routers send data to specific destinations on a network using the IP addresses it has issued to devices at those destinations. A router creates what is called a local area network (LAN), and often incorporates another piece of vital equipment to make this connection – a modem. Modems are used to convert signals from a telephone or fibre optic line into data that is readable by a computer, and similarly converts data from a computer into signals that can be sent down a telephone line or fibre optic cable. Many modern routers have modems built in. A router connects devices to the internet. Activity You have been asked to create a small network for your home. There are eight rooms in the house: a lounge, a kitchen, a dining room, three bedrooms, an office and a bathroom. There will be at least one device in each room that will be connected to the internet, as in the table. Draw a simple sketch map of how the house would be connected and what devices are required for this connection. LINK Room WB Consolidate your understanding by completing Exercise 1, page 38 in the Workbook. 56 SB CS PP.indb 56 Device(s) Lounge Smart television, games console, tablet Dining Room Smart speaker Kitchen Smart speaker Bedroom Smart television, games console Bedroom Smart television, laptop Bedroom Smart speaker Office Desktop computer, printer, smart speaker Bathroom Smart speaker Hardware 14.5.21. 14:14 Chapter 3 Let’s Map It HARDWARE Input Process Output Catche CPU RAM Storage CPU CPU Fetch - Decode - Execute CPU CPU CU Memory Unit Registers ALU Cores Buses °C/°F 24.1° 24.2° 24.3° Sensors Networks Home Server www Router Cloud Storage Hardware SB CS PP.indb 57 57 14.5.21. 14:14 Chapter 3 Let’s Review 58 SB CS PP.indb 58 What is meant by computer architecture? What is the job of the central processing unit? List the five different registers that sit within a CPU. Describe the von Neumann architecture. Fill in the gaps: the main method of processing data within the CPU is the __________ _________ - __________ cycle. Explain the purpose of a bus. What is the purpose of cache memory? If a processor has two cores, what is it known as? What is a processor’s clock speed measured in? Give an example of an embedded system. A touch screen as an input device can be either capacitive, resistive or infra-red. Briefly explain the differences between each type of screen. What would be the most appropriate sensors to use when measuring average rainfall in an outdoor location? Define what is meant by cloud storage. What is the difference between a MAC address and an IP address? How does a device that you wish to connect to the internet obtain a dynamic IP address? What is the main purpose of a router? Hardware 14.5.21. 14:14 CHAPTER 4 Software COMPUTER SCIENCE WATCH Scan the page to watch a clip on the differences between system and application software. Before watching discuss what you expect to see or hear. QUESTIONS • What is the link between hardware and software? • How is software essential to the operation of a computer? At the end of this chapter, you will be able to: understand the difference between system software and application software • How do humans use software to interact with computing devices? • What is programming and how do pieces of software begin their existence? define the role and basic functions of an operating system identify the hardware, firmware and operating systems that are used to run applications software define the role and operation of interrupts identify the difference between a high-level language and a low-level language understand the advantages and disadvantages of each type of language define the two types of translator: compilers and interpreters identify the advantages and disadvantages of each type of translator understand what an integrated development environment is used for, including its common functions 59 SB CS PP.indb 59 14.5.21. 14:14 Chapter 4 A computer system is made up of both hardware (as we have examined in Chapter ) and software, and both are essential for the successful operation of the system. This chapter will explore different types of software and how they exist and work. We will also learn about how the different pieces of software control and use the hardware of the computer. . Types of Software There are two different types of software that a computer system uses: system software and application software. System software is a variety of programs and processes that a computer needs in order to function. System software that is embedded into hardware devices are known as firmware. Firmware is often installed onto components of the hardware when the computer is built and users do not need to involve themselves with the installation of system software at all. WORD ALERT Function: in order to work correctly. .. System Software and Application Software DEFINITION Firmware: small applications which enable a computer to start all of its devices. An example of system software is the BIOS program that is installed in the Read Only Memory (ROM) of a computer. BIOS stands for Basic Input Output System, and it is a set of instructions that are executed by a computer once it receives the power to start all of the necessary hardware. Utility: a small piece of software that controls specific parts of the hardware. LINK Another example of system software is the operating system (OS) of the computer, such as Microsoft’s Windows OS or Apple’s macOS. The operating system allows users to work with the hardware and applications software in a user-friendly way, usually through the operation of a mouse and keyboard. There are often other pieces of system software built into the operating system that allow a user to control the power, attached devices and memory. This type of system software is called utility software. Application software is the term used for any software that a user requires in order to make use of the computer system for their needs. Examples of applications software are office applications such as word processors, spreadsheet applications and presentation software, games, web browsers and communications software. They are not essential to the functioning of a computer, but they may be essential to a user’s particular needs. WB Consolidate your understanding by completing Exercise 1, page 42 in the Workbook. .. The Operating System A laptop running the Microsoft Windows operating system. Most computer systems that we interact with as users have a form of operating system installed on them, to allow us to quickly begin work or start accessing the applications that we require in our lives. The operating system is a special piece of system software that manages many things that allow us to use the system for our needs. ENRICHMENT Can you find out about other types of operating system, and their advantages and disadvantages? Find out about Linux, and what makes it different from the other operating systems mentioned here. 60 SB CS PP.indb 60 In addition to the roles explored in Figure ., an operating system is also the platform for a computer to run the applications software that is required by a user. Computer software developers have to ensure that the software that they design, code and produce is able to be run on multiple operating systems. Operating systems exist within various systems that require humans to interface with them. Devices such as personal computers, laptops, mobile phones and smart TV’s all require user interaction. There are various ways in which the interaction can occur, including textually through a command line interface, visually using a graphical user interface with point and click methods and verbally using voice commands and natural language interfaces. Some of the current examples of this that you might find around the home that use these interfaces are smart speakers such as Google Home and Amazon Alexa, as well as mobile based apps such as Bixby and Siri. Software 14.5.21. 14:14 Chapter 4 The Operating System Managing drivers Managing peripherals Managing Peripherals Enables all attached Enables all attached hardware to hardware to funtion function effectively effectively Managing Memory Managing memory Allows the computer system Allows the computer to move things in and out of system to move things in memory when needed and out of memory when needed Managing Drivers Drivers are small utility software that give specific instructions Drivers are small utility software that give specific operating devices such as printers instruction to devices such as printers Managing FilesManaging files Helps us to save, retrieve and files created Helps us to save, retrieve and print files created print Manages Multitasking Provides Interface Enables the computer to do several things at once Allows us to interact with the physical hardware Managing multitasking Enables the computer to do several things at once to Handling interrupts Alert us as users when an Alert us as users when an action action needs to be carried out needs to be carried out Handling Interrupts Provides interface Allows us to interact with the physical hardware Figure . The role of the operating system. Creates more effective and efficient code Takes less time to translate As we will explore in Chapter , system security is something that all computer users have to be aware of when using devices. The operating system provides a useful line of defence, and usually has a variety of small utility programs, such as firewalls and authentication, that help to guard against threats to files. Operating systems create and manage essential user accounts such as the system Code can be Things can be hidden COMPILER account, administrator user kept account, regular user account and guest user account. Theyinare secret and not detected codeable to handle multiple users being able to access the computer, with separate profiles created for each user VS. based on their individual needs. This is especially important when it comes to protecting younger users from accessing unsuitable content. INTERPRETER A further feature of operating systems is to manage the memory available within a system. This can Slower translation Code is more versatile, can be involve the allocation of resources to the hardware to enable the carryingviewed outonofdifferent usersystems instructions, as it is line-by-line easily and also to ensure that the same memory locations are not utilised by different processes. LINK See Chapter 5.3. REFLECT Why do you think it is important to enable different user profiles on a shared computer? .. Application Software Running Sequence Easier for beginners as errors are easily idatified and corrected Applications, or ‘apps’, are the pieces of software that users want or need to use as part of their lives, both in work and leisure usage. It is a combination of the operating system, bootloader (firmware) and hardware working together that allows application software to operate, and the sequence is crucial to that operation. The firmware (such as the BIOS) is run and activates the hardware The operating system is run on the firmware The applications are run on the operating system Figure . Application software running sequence. WORD ALERT .. Interrupts Handling interrupts are an important function of the operating system. An interrupt is a signal sent from a device or a program to the operating system that causes a temporary stop in the current program. When the program is halted and control is transferred to the operating system, it usually has a decision to make, either to continue running the program, run a different program or require a further intervention from a user. When a device sends an interrupt signal, for instance when a user presses a key on a keyboard, the interrupt is collected by an interrupt handler, and an interrupt service routine is carried out. This usually involves the interrupt being assigned a place in a queue, so that the handler can decide which interrupt is the highest priority. The interrupts are then handled according to their importance. This process happens so fast that it is impossible for a user to notice that the operating system has been interrupted temporarily. Software SB CS PP.indb 61 Intervention: an action taken by someone to make something different happen. DEFINITION Interrupt service routine: a software routine that hardware invokes in response to an interrupt. 61 14.5.21. 14:14 Chapter 4 DEFINITION Division by zero: a mathematical calculation that has no answer, and one that is automatically rejected by a computer for this reason. There are two different types of interrupt, a software interrupt and a hardware interrupt. Software interrupts are usually signals sent to an operating system by applications, such as a mathematical problem like a division by zero or processes attempting to access the same memory location. Hardware interrupts could be a press of a key on a keyboard, or the click of a mouse button. . Types of Programming Language, Translators and Integrated Development Environments (IDEs) All of the software that we use has to be created and coded by software developers, and the computer programs that are created have to be translated into signals that can be understood by a computer system. Here we will examine the processes and sequences that enable this translation to occur. .. High-level and Low-Level Programming Languages QUICK CHECK What is the key difference between a low-level and high-level programming language? In its most basic form, computer language is made up of binary code, which is a series of s and s. This is called machine code, and basic instructions that a computer is required to carry out are written in this language. Machine code is a low-level language, and this is so named because it is the language of a computer rather than that of a human. As machine code is difficult for humans to program in, mainly due to the difficulty in debugging the code, programmers usually write code in high-level languages such as Python, JavaScript, C, C++ and Java. They are called high-level languages because they contain English-like words and terms that we use in communication and are easier for programmers to understand. Writing and debugging code. All of the programming languages listed above have evolved over a number of years as programmers develop their knowledge of how to program a computer. Advantages of low-level language Programmers who can write programs in low-level code will be able to create very effective and efficient programs that tend to run very quickly. These programs tend to be specific to the machine they are programmed on. Programs written in low-level code will use both processor capacity and memory very well. There are likely to be more errors and code is harder to debug. Low-level coding can directly change or manipulate computer hardware. It is much more challenging for humans to write low-level coding. Advantages of high-level language LINK See Chapter 1.1. 62 SB CS PP.indb 62 Disadvantages of low-level language Disadvantages of high-level language Code is easier to debug. Code has to be translated into machine code before it can be executed. Code is much easier to write and be read by fellow programmers. Programs tend to be slower than those programmed in low-level code. Programs written in high-level code tend to be portable, meaning they can run on more than one type of machine. Inefficiencies in hardware usage are a common feature of high-level coding. Software 14.5.21. 14:14 Chapter 4 .. Assembly Language HELPFUL NOTES We discussed earlier that machine code is the binary code that is understood by a computer. Assembly language is a type of programming that sits just above machine code and is a low-level language that uses mnemonics for its instructions and commands. A mnemonic is a pattern of letters or ideas that helps a user to remember something. An example that may be found in assembly language is INP, which is a low-level mnemonic for Input, and RET, which is a mnemonic for Return. Activity Mnemonics help us to remember complex information. We often use them to remember how to spell difficult words, where computers use them to translate programming terminology. What do you think the following mnemonics might represent? CL INC HLT DEC WORD ALERT When a program is written in assembly language, in order for a computer to carry out the programming, it must first be translated into machine code. An assembler is needed to carry out this task, and this is a translator application that is usually built into programming software when coding at low-level. .. Compilers and Interpreters REFLECT There are other types of code translation applications that are built into high-level programming languages, called compilers and interpreters. Both have different characteristics, but a key feature of these types of translator is to report errors in the code to the programmer. A programmer will produce a piece of code in a high-level language that is designed for a specific purpose. It is then important that the code is tested out to see if it does what it is meant to do. When a compiler is used, it will translate an entire block of code that has been created and will produce an executable file. When this code then runs, the compiler will produce an error report for the whole block of code if any errors have been detected. Examples of languages that use compiled code are C and C++. When an interpreter is used, it will translate and execute the code that has been written line-byline. Unlike a compiler, which waits until the end of the execution process before reporting errors, an interpreter will stop the execution of the code when it detects an error. Unlike a compiler, interpreters do not report syntax errors at the end of the processing. The interpreter will also not produce an executable file at the end of the process. Examples of languages that use interpreted code are Python and JavaScript. Creates more effective and efficient code Depending on the type of programming language, compilers and/or interpreters are used during the code production process. It can take hours to compile a large application. DEFINITION Executable: a file that launches and runs a series of code when opened. Slower translation as it is line-by-line Code can be kept secret Takes less time to translate Translated: changed into a different language. COMPILER VS INTERPRETER Things can be hidden and not detected in code Easier for beginners as errors are easily identified and corrected Code is more versatile, can be viewed on different systems easily Figure . Advantages and disadvantages of compilers and interpreters. Software SB CS PP.indb 63 63 14.5.21. 14:14 Chapter 4 When programmers are developing code, an interpreter is used for ease of debugging and a compiler is used to translate the finished program. WORD ALERT Debugging: finding errors or mistakes in code. .. Integrated Development Environments (IDEs) An Integrated Development Environment or IDE is an application that programmers use to test and develop new software. An IDE allows a programmer to write code in various different programming languages and will simulate the running of the code so that development can take place easily. DEFINITION Simulate: run a test version of an application. An IDE has a number of different features all designed to assist a programmer in their work. Code Editor This part of the environment is called the shell and is a text editing area. Programmers can write their code in the shell. There are a number of features built into this part of the IDE that can help programmers work more efficiently, such as auto-completion, autocorrection and prettyprint. Auto-Completion WORD ALERT When a programmer types in a common function or piece of syntax, the IDE will recognise the start of the piece of code and suggest or complete it for the programmer. This saves time while programming. Syntax: the structure of not just statements but also symbols, punctuation, etc., in a computing language. Auto-Correction Similar to auto-completion, an IDE can detect when an obvious error has been made and will suggest a correction automatically for the programmer to review. Also built into this feature is bracket matching, where the IDE will suggest or highlight closing brackets or braces that were missed out by the programmer. Prettyprint ENRICHMENT There are several different IDEs that have been developed for programmers. Download one yourself and try writing a simple program – you will be surprised at how easy it is to use! As discussed in section .., translators provide a vital bridge between high-level and low-level code. Some IDEs will have a translator built into it, and will be capable of both compiling and interpreting code written by a programmer. Only the most advanced IDEs support almost all languages. Run-time Environment WB Consolidate your understanding by completing Exercise 1, page 46 in the Workbook. SB CS PP.indb 64 Translators When code is compiled or interpreted, the IDE will pinpoint errors, either in a report or on a line-byline basis. It will show the programmer the line number of the error and indicate the type of error that has been detected. See section 4.2.3. 64 To make life easier for programmers, most IDEs will format code using indentation and a colour scheme to make lines and functions easier to spot. Prettyprint also helps programmers to see where subroutines and loops sit within a larger block of code. Error Diagnostics LINK LINK Coding in Python – a high-level language. This allows a programmer to execute the program one step at a time and is useful to ensure that all parts of the code are correct before creating the final version of the code. Software 14.5.21. 14:14 Chapter 4 Let’s Map It HARDWARE SOFTWARE Software and hardware are essential to work together. SYSTEM APPLICATION Allows a computer to function Operating System Enables a user to interact with the computer. Allows a computer to be used Applications are required to enable a user to carry out tasks and work. Interrupts All software starts as code A stop in a process needing a user or program input. Python 1 2 3 Handled in order of priority. Perl C++ Java C# 4 Integrated Development Environment Low- and high-level languages X 1 2 00110 111001 3 4 Low 5 Code Editor if a == 10: b += 1 High 6 7 8 9 10 Simulation Translator Compiler/Interpreter 11 Software SB CS PP.indb 65 65 14.5.21. 14:14 Chapter 4 Let’s Review 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. Name two different types of system software. What are three main features of an operating system? What is the function of firmware in a computer system? Complete the sentence. An interrupt is where a piece of software requires... What are the two different types of interrupt? Give one example of a software interrupt. What is the difference between low-level and high-level programming languages? Why do programmers mainly use high-level languages to write their code? What is a definition of assembly language? Name the two types of translators found within programming. What are the main reasons for choosing between the two types of translators? Why is it a good thing for a programmer to check their code line-by-line when developing a program? 13. What does IDE stand for? 14. Name two functions of an IDE. 66 SB CS PP.indb 66 Software 14.5.21. 14:14 CHAPTER 5 The Internet and Cyber Security COMPUTER SCIENCE WATCH: Scan the page to watch a clip on common types of cyber-crime. Before watching discuss what you expect to see or hear. QUESTIONS At the end of this chapter, you will be able to: explain the difference between the internet and the world wide web understand what is meant by a uniform resource locator (URL) • What is the difference between the internet and the world wide web? • How do we access and use websites effectively? • What exactly is digital currency? • How important is it to keep our computers safe from cyber-crime? explain the purpose of the hypertext transfer protocol (HTTP) and the hypertext transfer protocol secure (HTTPS) define how a web browser operates and what functions it provides understand how web pages are found, retrieved and displayed on your computer explain what is meant by a cookie and why they are used understand the concept of a digital currency and how blockchain is used to keep track of digital currency understand a range of cyber security threats and the solutions used to protect data from these threats 67 SB CS PP.indb 67 14.5.21. 14:14 Chapter 5 HELPFUL NOTES The idea of a world wide web was created by Sir Tim Berners-Lee, a British computer scientist. He decided to gift the idea to the world and did not make any money from the idea. He also published the world’s first website in 1990. One of the greatest developments in computing during the late th century was the introduction of the internet into our working and home lives. The ability to communicate on a global scale both in business and leisure has opened up infinite possibilities for users all around the world. However, with these opportunities also come risks, and with user data increasingly being shared across computer networks, the need to be safe and secure in our practices online is of paramount importance. . The Internet and the World Wide Web It is important to know the difference between the internet and the world wide web. The two terms are often used interchangeably and wrongly, so it is vital to ensure that the differences are known. The internet is the enormous network of computers, devices and hardware that are all connected together as a set of small networks enabling communication between devices to take place. This is known as infrastructure and represents all of the physical pieces of equipment connected through service providers to servers all around the world. The world wide web is the collection of websites and web pages that store the information that users wish to access. These web pages are stored on servers and users access them using the internet infrastructure. .. Uniform Resource Locators QUICK CHECK What are the important pieces of information that are required for the receiver’s address on an envelope when sending a letter through the post? Just like houses and homes have unique postal addresses to identify where they are in a given country or city, websites and web pages also have addresses to help users find them. These web addresses are called Uniform Resource Locators, or URLs for short. They enable a user to locate a website easily by typing the URL into the address bar of a web browser. A URL can contain the protocol, the domain name and the web page/file name. Every website address has a URL with an equivalent Internet Protocol (IP) address. IP addresses are made up of numbers and letters and can be very difficult for a user to remember. Refer to section .. for more information on how IP addresses are matched to website addresses. Worked Example A website for a company called My Favourite Cars might have a web page with a web address of http://myfavouritecars.com. This URL is much easier to remember than the website’s actual IP address which might be something like .... The URL is better to give to people looking for the website and is much more memorable than a string of numerical digits. Just as a postal address has certain items in it that identifies a house, a URL also has identifying elements. With some or all of these missing, a letter may not arrive at its intended destination. Postal address example , City Road House number and road name Strickland Town or city Walthamshire County, state or province England Country WE QQ Postal code The same is true of a URL. If you only know part of the address, you may not get to the website that you require. 68 SB CS PP.indb 68 The Internet and Cyber Security 14.5.21. 14:14 Chapter 5 These are the elements of a URL: • protocol • domain name • folder structure leading to where the webpage is located • name of the requested web page http://clotheswarehouse.com/clothes/shirts Protocol http:// Domain name clotheswarehouse.com Area within website clothes/ Web page name shirts The whole address then takes a user directly to the part of the website that they wish to view. In the example above, the website is a business site with a domain name ‘clotheswarehouse.com’ and the user wishes to access the exact page containing shirts sold by the business. Each element of URL will be further explained in subsequent sections. .. Hypertext Transfer Protocol and Hypertext Transfer Protocol Secure Data packets are sent around the internet using different protocols, or rules. The protocol that web pages use for data transfer is called hypertext transfer protocol (HTTP) and all URLs begin with the letters ‘http’. DEFINITION Hypertext transfer protocol: the agreed set of rules that all computers use for transmitting files (data) over the world wide web. The internet is also capable of providing other means of data transfer, and different protocols exist to ensure the correct packets of data reach their intended destinations. Some of the other services that the internet provides include email, file sharing and video streaming. QUICK CHECK Data can contain private or sensitive Keeping your data secure is crucial when using information, for example, users’ personal the internet. information from their online bank accounts, or payment card details when purchasing an item from a website. When these packets of data are transmitted across a network, it is vital that this information remains private and secure to prevent criminals from accessing potentially sensitive information. What types of information do you think you might share when buying an item online? When using websites such as online banking or making online purchases, you will notice that, when completing a transaction, the protocol changes from just hypertext transfer protocol (http) to secure hypertext transfer protocol (https). This can be noticed by looking at the address bar of the browser being used to access the web page. Secure http ensures that a secure connection is made between the two devices engaging in the transfer of data. The data packets are encrypted before they are transmitted across the network and are decrypted only when they reach their intended destination. This ensures that criminals such as hackers would be unable to access the private and confidential information as they would be unable to decipher the encryption. Any data that was intercepted during this process would be meaningless to the hacker. The process of encryption requires the devices at either end of the transfer to use an encryption key to unscramble the secure data. Websites built with encryption technology will give users the confidence to carry out these transactions. The Internet and Cyber Security SB CS PP.indb 69 69 14.5.21. 14:14 Chapter 5 .. Web Browsers ENRICHMENT How have websites evolved over the years? Name some things you can do on a website that you couldn’t have done 10 years ago. The main application on a computer that is used to retrieve and display web pages is called a web browser. Most web pages are written in a variety of different programming languages, including Hypertext Markup Language (HTML) and JavaScript, or make use of cascading style sheets (CSS). The job of the web browser is to translate HTML code from websites and display it to the user as web pages. Other functions of a web browser are as follows: Bookmarks and favourites This is the ability to store the URLs of your favourite websites as bookmarks for future reference. Modern browsers allow you to create quick link buttons to enable faster access to these websites and cut out the need to type the URL each time. Recording user history A web browser can store a list of recently viewed web pages in reverse date and time order. This list will keep growing from the first use of the browser until it is cleared by a user. Allowing the use of multiple browsing tabs Users can open multiple web pages in different tabs, enabling several sites to be accessed at the same time. Storing cookies Cookies are tiny files that are saved to your computer when you access a website. They can be used to store your personal preferences or your activity within that website. Cookies enable websites to display relevant advertisements that the browser thinks may be of interest to you, based on your browsing history within a particular website (see section ..). Providing tools for navigation A web browser contains various icons and buttons at the top of the window, including a back button, a forward button and a home button. These navigation buttons enable a user to move smoothly between all previously viewed web pages without the need to re-enter their URLs. HELPFUL NOTES A phone book is a directory containing all of the listed telephone numbers for a town. While web servers do not contain a book, as it would be immediately out of date, the DNS uses nameservers to locate different websites. DEFINITION Search engine: a webbased tool that is used to find web pages based on a given topic or keyword entered by the user. It then returns a list of relevant web pages and their respective URLs. 70 SB CS PP.indb 70 Providing an address bar This is where a user can type in the URL for a website they wish to visit if they know the web address. Modern browsers will also use the address bar to access the facilities of a search engine if it does not recognise the URL immediately. The Internet and Cyber Security 14.5.21. 14:14 Chapter 5 .. Locating and Viewing a Web Page As discussed in sections .. and .., web pages are located on a server somewhere in the world. It is the job of the web browser to retrieve the web page for the user to view. It is firstly important to know the URL of the site or page that the user wishes to retrieve. This is typed into the address bar of the web browser. The browser then makes a request through the user’s internet service provider (ISP) to locate the web page that has been requested. This process is called making a Domain Name System (DNS) Query and is like looking up someone’s phone number in a phone directory. WB LINK Consolidate your understanding by completing Exercises 1 and 2, pages 50-53 in the Workbook. As we learned in section .., each website has a URL that is linked directly to a unique IP address. The DNS Query uses the URL that has been entered by the user and looks up the matching IP address. The IP address then connects the user’s browser to the web server that hosts the site and retrieves the required website for the user to view from the database. It is the job of the browser to firstly request the files for the webpage from the DNS and then translate all of the data that the DNS Query returns into HTML code (see section ..) so that a user can interact with the website. .. Cookies ENRICHMENT Cookies can be switched off on websites. What do you think would change about your website browsing if you did so? Cookies are very small text files that are stored on your computer when you are browsing the world wide web and websites. They are sent to your computer by the web servers that hold the websites you are visiting. Cookies are designed to personalise your user experience while browsing a particular website. They are generally used to: • store user preferences on a website Session Persistent cookies are cookies have • store login details temporary cookies that expiration dates and are • track user behaviour are deleted when you close stored in a folder on your • store items in online shopping carts your web browser. They provide computer until they expire • help advertisers show relevant information on your browsing or the user deletes them. They website adverts based on user’s while you are on that particular make websites appear to browsing habits website and this is not remember a user on the There are two different types of cookies retained once you close next visit. that are stored. your browser. Worked Example If you have been recently on a website that sells sunglasses, and you have browsed several designer brands of sunglasses, the web server of that site will have sent your computer some cookies that have been designed by those designer brands. As you then make your way around other websites that contain adverts and advertising space, those cookies will activate and you will begin to see adverts for designer sunglasses, even if the site you are viewing has nothing to do with designer sunglasses. This is because your preference for the designer brands you viewed previously has been stored in their cookies and their cookies have been accessed in order to find and display an appropriate advert. This is an example of a persistent cookie in use. Look out for this next time you are browsing, particularly if you are visiting shopping websites. Some users consider that browsers collecting data in this way is an invasion of privacy and could lead to criminal activity like identity theft. Users do have the choice on a website to disable cookies, however this can affect the user experience and make browsing less interactive. The Internet and Cyber Security SB CS PP.indb 71 71 14.5.21. 14:14 Chapter 5 . Digital Currency HELPFUL NOTES Bitcoin has been in existence since 2008 and, although it is not fully accepted as a method of payment by many organisations, it is considered a highly efficient way of doing business due to its low usage costs. As the world moves to operate in ever more digital situations, traditional methods of exchanging money begin to be joined by digital currencies. A digital currency is one that exists electronically. It is a method of payment, but rather than exchanging physical coins and bank notes, the payment is made electronically. Payments made using this cryptocurrency are encrypted. It also operates using what is known as a decentralised system. This means that there are no central banks to keep track of payments, instead a system known as a digital ledger is used for cryptocurrency. The most popular digital currency, or cryptocurrency, is Bitcoin, and these types of financial transactions are not controlled by the central banks of countries, as they are not issued by these institutions. Other types of cryptocurrency that are currently in existence are Ethereum, Tether and Litecoin, but these are worth less than Bitcoin due to the smaller amount of the currency in circulation. Units of the cryptocurrency are generated by users, also known as ‘miners’, who use the power of their personal computers to process transactions. The ‘reward’ for doing so is that miners receive some of the transaction fees involved in the process of payments made. In order that cryptocurrency transactions are processed fairly and are not obtained dishonestly, there is a technology that sits behind all transactions called blockchain. Effectively, blockchain is a digital record or ledger that tracks all cryptocurrency transactions, meaning that each unit of the currency can only ever be used once by one user. LINK WB Consolidate your understanding by completing Exercise 1, page 53 in the Workbook. The data behind the cryptocurrency is time-stamped and stored in the blockchain when it is used in a transaction, and these records cannot be altered by users. This makes cryptocurrency highly secure, because the way that the data is stored, and the number of bits involved, means that around billion combinations would need to be tried in order to fraudulently replicate or fake a unit. . Cyber Security User data is highly valuable and highly sought-after by cyber criminals, and just as thieves operate in the real world, computer users who wish to steal data are operating within the world wide web. Any risk posed to a computer system from an internet source is considered a cyber threat. By taking steps to understand what the potential risks are, people and businesses are able to better protect their systems and data. ENRICHMENT Some cyber criminals have been given jobs by cyber security companies because of the skills that they possess. They are ethical hackers who use their skills to identify security flaws and make improvement recommendations. Can you find an example of a cyber- criminal who now uses their skills for good reasons? There are various cyber-attacks on our computers and data that users have to protect themselves against. Some of the attacks are against data and are designed to obtain information from computers and devices, whereas other attacks can be against human users and are designed to change behaviour in order to obtain information. .. Brute-Force Attack This type of attack is designed to try and obtain a user’s password without their consent. It is like a thief taking all available keys (not just yours) and trying them all in a door lock one after the other until the correct key is found. A brute-force attack is where a computer program floods a system with an enormous number of potential passwords or passcodes and uses trial and error to try and find the password that matches. Brute-force attacks target weak passwords created by users. .. Data Interception When data is being transmitted around a network such as the internet, if it is unencrypted it has the potential to be intercepted on its way to its intended destination. A cyber criminal could use a piece of software called a packet sniffer to examine packets of data as they make their way around a 72 SB CS PP.indb 72 The Internet and Cyber Security 14.5.21. 14:14 Chapter 5 network. The packet sniffer can then feed the contents back to the criminal, who may be able to use the information for fraudulent purposes. .. Distributed Denial of Service (DDoS) Attack A Distributed Denial of Service (DDoS) attack can happen to a website or web server and is designed to cause disruption to website owners. A criminal would use software that can ‘force’ thousands of innocent computers around the world to send a viewing request to a web server. This unofficial network of recruited computers is known as a botnet and would have likely been infected with some form of malware (see .. below). The flooding of requests sent to a server will overload it and either slow the website right down or cause it to go offline altogether. REFLECT The biggest DDoS attack to date took place in February 2020, after Amazon Web Services (AWS) was targeted. Can you find any other high profile examples of DDoS attacks? .. Hacking In simple terms, a hacker is a user who is seeking to gain unauthorised access to a computer system. Hackers who are attempting to do this for criminal purposes are referred to as black-hat hackers, and are usually doing so to access, change or damage the data held on the system being hacked. .. Malicious Code Software (Malware) Malware (short for malicious software) are pieces of software that have been written and coded with the intention of causing damage to or stealing data from a computer or system. There are several different types of malware that criminals have coded and used against users and systems. Type of malware Virus Description Like a human virus, this type of malware infects a computer and then replicates itself to be sent to another computer. This transmission can happen where infected files are shared via hard disk drives or sending online. Trojan horse A trojan horse is malware that is hidden away in the code of software that appears to be harmless. Criminals will often hide trojan horses in illegal or pirate software to obtain user data. Worm A worm operates similarly to a virus, however rather than trying to damage files, it simply replicates itself until the computer’s resources are used to their maximum capacity and no further processing can take place, leading to system failure and crashing. Spyware Spyware is a piece of malware that behaves a little bit like a cookie but, instead of benefitting the user, it actually sends data back to a criminal. Spyware collects information about online browsing habits without a user knowing. Adware Adware is not always malicious, but almost always involves installing processes for displaying pop-up adverts while browsing websites, and will install tracking cookies, often without user permission. Ransomware This type of malware is often quite nasty and makes threats to users about bad things that will happen to their data unless a payment of money is made. The Internet and Cyber Security SB CS PP.indb 73 HELPFUL NOTES A black-hat hacker is aiming to access systems for criminal purposes, whereas a white-hat hacker is doing the opposite. Often called ethical hackers, a whitehat hacker will try to find security loopholes in a system and give advice to the network owners about how to close them. REFLECT The trojan horse malware is named after the Greek myth of the same name. 73 14.5.21. 14:14 Chapter 5 .. Social Engineering QUICK CHECK How is social engineering different from other forms of cyber-crime? This form of cyber-crime is where users are manipulated into behaving in a way that they would not normally do. There are several different forms of social engineering when it comes to cyber-crime, but a physical form of the attack is shouldering, when someone attempts to gain information by looking over your shoulder. This can occur in public places like ATMs or at the cashier when you are paying for goods. Criminals will attempt to obtain things like Personal Identification Numbers (PINs), and social engineering is one of the reasons why passwords appear as asterisks onscreen when users type them in. .. Pharming Pharming is a type of social engineering. It is where a user will be sent from a genuine website to a fake one, with the hope that this goes unnoticed. A user may then be prompted to enter login details, and this can then be collected by a criminal for use on the genuine site. Pharming attacks occur when web servers are attacked, and code is inserted into a website that redirects visitors. These attacks are quite difficult to spot when they occur and require a user to be vigilant to changes to the URL (for example, how the domain name is spelt) and subtle changes in the way a site looks. .. Phishing WORD ALERT Spoof: something that is fake but pretends to be genuine. Phishing is a form of social engineering which takes place largely through emails. A criminal will send an email that looks genuine as if it has come from a business and will often ask a user to click a link within the email, after an instruction that their data is at risk if they do not comply. Once a user clicks on a link, it often takes them to a spoof website that is designed to try and obtain login details. Phishing emails often look convincing but may contain spelling errors and the URL of the link and the sender’s email address are often giveaways that the email is not genuine. Other features of phishing emails are that users are generally not referred to by name, where a genuine company usually would do so. . Solutions to Cyber Security Issues One of the most important things that a computer user or network manager must do is protect their systems from the attacks described above. There are a number of ways in which this is possible, and users must select the most appropriate method(s) of guarding against cyber-crime. .. Access Levels WORD ALERT Compromise: become vulnerable or function less effectively. DEFINITION Corrupt: the act of making data unreliable by errors or alterations. 74 SB CS PP.indb 74 This method of protection is hugely important in organisations where there are lots of users accessing a network. Users should be assigned different levels of access depending on the role they have. Administrators of a network have full access and control, and there are several levels of access going down to basic user access which has only limited rights of usage. This method of protection ensures that user behaviour can be controlled while they use a computer on a network. .. Anti-Malware, Anti-Spyware and Anti-Virus It is essential that networks are regularly protected from harmful or malicious software being installed. Such software could potentially compromise security of the network, and may allow criminal activity to occur, including the theft of personal or company data. In extreme cases, such software could also potentially corrupt data in a network to the point that it becomes unreadable – this type of corruption is called a virus attack. The Internet and Cyber Security 14.5.21. 14:14 Chapter 5 In order to guard against this type of behaviour, a network should have anti-malware and anti-virus applications installed that protect all devices on the network. Anti-malware and anti-virus software are constantly scanning documents, files and also incoming data from the internet. They are designed to detect suspicious activity and files prior to them being opened or stored and warn the user against opening the files. If the anti-malware or anti-virus software does detect a file or application that is potentially harmful, it will immediately quarantine that file away from the rest of the network, preventing it from installing or multiplying itself to other areas of the network or hard disk drive. Upon user instructions, the software will then remove and delete the offending malware or virus. It is important that network managers regularly perform deep file scanning to maintain the safety of the data that is stored. Users should also be particularly careful when downloading files and software from the internet and should always check that the downloaded files are from a reputable source. Additionally, as computer viruses and malware become increasingly more sophisticated, it becomes vital to update the anti-malware and anti-virus software to the latest versions, including updating their database of known security threats. Refer to section .. on automatic software updates. .. Authentication A simple and basic method of data security is to set a password that is only known to the user in order to access secure information. Passwords can be set on many different websites or devices; mobile telephones encourage users to set a password to use the device, and common web applications require users to create a password in order to access the features of the application. WORD ALERT Quarantine: to place into isolation. Sophisticated: more complex. ENRICHMENT Can you find out the names of the most recent viruses that have infected computers around the world? QUICK CHECK What are the differences between spyware, malware and a virus? It is vitally important that your passwords are not obtained by unauthorised users. Passwords should be strong enough to stop criminals from guessing them or hacking into your personal accounts or applications. A weak password such as a simple seven-character word can be cracked by a professional hacker in a fraction of a millisecond. An eight-character password would take on average five hours to crack and a nine-character password would take around five days to discover. The Internet and Cyber Security SB CS PP.indb 75 75 14.5.21. 14:14 Passwords should be strong enough to stop criminals from guessing them or hacking into your personal accounts or applications. A weak password such as a simple seven-character word can be cracked by a professional hacker in a fraction of a second. An eight-character password would take on average five hours to crack and a nine-character password would take around five days. Chapter 5 LINK WORD ALERT Alphanumeric: letters and numbers. Substitute: exchange for something different. LINK Some applications will not allow you to progress beyond the sign-up stage if the password you provided is not strong enough. Check your password strength here: http:// howsecureismypassword. net. REFLECT Do you use the same password for multiple accounts? How often have you changed your password? Are you the only person who knows it? 5 PASSWORDS Some Inapplications order to make will not enable you to passwords stronger, progress beyond the it sign is always initial up stage ifadvisable yourto password not use aiscombination strong enough. You can of alpha (letters) and check your password numeric characters. If strength here: http:// howsecureismypassword. your password was a net characters less than milliseconds string of nine numbers, and then you added a letter to those numbers, your password would be strong enough that it would take somewhere in the region of years to crack the password. Once you start combining alphanumeric characters, upper-case and lower-case letters and special characters such as question marks and dollar signs, these are the most secure sorts of password you can set. characters hours characters days One common problem with setting passwords, however, is where users substitute letters in easy words with similar symbols (see graphic below). Hackers are already aware of this practice and would make your password use a combination of alpharandom (letters) and characters. still be able to crack theseTocombinations withstronger, ease. Passwords that appear arenumeric the best type, If your was a string of nine numbers, and then you added a letter to those numbers, it would take however they do becomepassword less memorable to a user and can be quite easily forgotten or mistyped. WORD ALERT Alphanumeric: letters and numbers Substitute: exchange for something different somewhere in the region of years to crack. The most secure passwords combine alphanumeric characters, capital and lower-case letters and special characters such as question marks and dollar signs. A common problem with setting passwords, however, is when users substitute letters in easy words oK3<jF8$jT8@iO8* with similar symbols (see the graphic below). Hackers are already aware of this practice and could easily crack these combinations. Passwords that appear random are best, however they do become less memorable, and are easily forgotten or mistyped. cabbage Weak undesirable password Medium undesirable password Strong password Passwords should be changed regularly, however, it is unrealistic for users to change their passwords every few weeks. It is common Weak Medium Strong practice in most organisations for users to change their Password Password Password passwords yearly, but the reality is that many users never change their password to access popular applications from Passwords should be changed regularly. It is common practice in most organisations for users to the first time they have been set. Other examples of poor change their passwords every few months or yearly, but the reality is that many users never change password security are when users set the same password their password for some applications. It is also poor password security to use the same password for mostaccounts; or all your online once one application is compromised, it could then compromise for most or all of their online onceaccounts; one account the others.with the same password is compromised, other accounts could potentially be compromised as well. Another way that a user can ensure their passwords are not 18 compromised is to install a piece of anti-spyware software on their computer. Spyware is software that can be installed onto a computer without the knowledge of a user, and usually happens when a user has been careless or has visited an insecure website. Biometric authentication is just one way of a user authenticating Spyware runs in the background of your computer, and often themselves onto a network. makes processes slow down deliberately, however some of the more malicious spyware can also track the keys pressed by a user. The spyware then feeds the information to a criminal using a data collection application and will gather possible passwords to access private information. Installing a piece of anti-spyware software will scan regularly for this type of rogue application and remove them. Passwords are not the only method of authentication that users can undertake to ensure security of data. Several different methods can be used by websites, businesses, shops and other transactional devices. 76 SB CS PP.indb 76 The Internet and Cyber Security 14.5.21. 14:14 Chapter 5 Method of authentication Zero login Unusual behaviour can trigger a system to lock a user out. Biometric authentication A mobile device scans a user’s face to authenticate them. Magnetic stripes Magnetic stripe cards can be used for hotel door keys. Smart cards Smart cards have been used in banking for many years. Features Zero login is based on the idea that machines and devices can detect changes in user behaviour, rather than relying on passwords to authenticate activity. An example of this is with mobile devices – software detects when and where logins occur and check with a user that it is a genuine attempt to access an account. Zero login authentication builds up a picture of a pattern of behaviours based on usage of various different devices to ensure that access to software and systems is granted to the right user. This is where a user’s human features are used to grant access to devices or applications. Common biometric methods of authentication include fingerprint matching and retina scanning, and more recently facial recognition. Most credit card-sized cards feature a magnetic stripe on the back of the card. These stripes can contain up to characters of data about a human, such as a name and account number, and this data is stored magnetically. The card is then ‘swiped’ through a magnetic stripe reader and the device is able to collect the magnetic data from the card for processing. As long as it matches user data that is stored, the reading of the stripe authenticates the user successfully. This type of authentication is most commonly found in a credit or bank card. The smart card has a chip that is read when inserted into an Electronic Funds Transfer Point of Sale (EFTPOS) device, containing a chip and PIN reader. The chip on a card is capable of holding a lot of information and, when a user inserts the card into the device, they also need to enter a four-digit PIN that will enable a purchase to take place. The device reads the information from the chip and, if the PIN matches the information, the card can be successfully used. This type of authentication is called two-factor authentication. The Internet and Cyber Security SB CS PP.indb 77 77 14.5.21. 14:14 Chapter 5 Method of authentication Physical tokens A token can be used in conjunction with a keycode. Electronic tokens A user should know the answer to an electronic token question. HELPFUL NOTES Operating systems are almost always released with security ‘bugs’ in them as the developers often rush to get software out on sale. System updates usually occur immediately when the user runs an operating system for the first time. Features These tokens are often found in the form of a numerical display device. When a user is required to authenticate themselves on a network, a one-time passcode is generated and sent to the token. As long as a genuine user is in possession of the token, they can enter the passcode on a device and gain access to a system or network. The tokens can communicate with a network server through various methods, most commonly through a USB port or Bluetooth. Similar to physical tokens, electronic tokens allow users to authenticate themselves onto a network or system using virtual methods. An example of an electronic token could be an answer to a question that only a genuine user would know, or a passcode generated and sent to a trusted device such as a mobile phone. The passcode can then be keyed into a network device in order to authenticate a genuine user. Sometimes during authentication, a system will ask for multiple electronic tokens, for example a password, PIN, confirmation of email address and a trusted word. Activity For each of the following authentication methods, list the hardware that a system would need in order for the authentication to work successfully: 1 Physical tokens 2 Smart cards 3 Magnetic stripe .. Automating Software Updates This type of protection ensures that applications like operating systems, anti-virus and other commonly used pieces of software are always operating with the latest version installed. Software developers will often discover problems in their applications after they have been released and will develop ‘patches’ that will close potential security loopholes. By enabling automatic updates, these ‘patches’ will be installed routinely without a need for the user to worry and constantly check for updates. 78 SB CS PP.indb 78 The Internet and Cyber Security 14.5.21. 14:14 Chapter 5 .. Spelling and Tone in Communications As we learned earlier in section .., phishing emails are a threat to security. However, one thing that tends to set them apart from other emails is that they tend to have spelling errors and mistakes are often made by criminals when constructing the emails. As users, if we write our communications professionally and accurately, the recipient is more likely to believe it is a genuine communication and respond accordingly. .. Checking the URL of a Link Before clicking on any link, whether on a website or in an email, a user should always double check that it is a genuine link. Usually by hovering over a link, web browsers or email software will enable you to see the intended destination. If the URL has different words in it other than the name of the website you expect to visit, or if it is simply an IP address, then the link should be treated with caution and should not be clicked. Activity Can you spot the things in this image that suggest this is a phishing email? This might be a phishin message and is potentially ussafe. Links and other functionality have been disabled. Click here to enable functionality (not recommended). From: PayPal [service@paypal-australia.com.au To: Mr. xyz Sent: Thu // : AM Cc: Subject: Your account has been limited PayPal How to restore your Paypal account Dear PayPal member, To restore your PayPal account, you’ll need to log in your account. It’s easy: . Click the link below to open a secure browser window. . Confirm that you’re the owner of the account, and then follow the instructions. PayPal Email ID PP .. Firewalls A firewall is a piece of hardware or software that sits between a computer and the internet. Firewalls carefully look at all incoming and outgoing traffic to a network or a computer. Computer users can set different rules and criteria for the traffic that the firewall must apply and can be set to block traffic that doesn’t meet the rules set. The Internet and Cyber Security SB CS PP.indb 79 79 14.5.21. 14:14 Chapter 5 Computer users can create a blacklist of websites (websites that cannot be visited) or a whitelist of websites (a list of the only websites that can be visited) and the firewall will apply these rules to all network or computer traffic. When the traffic is checked, if it meets the rules or criteria it will be accepted by the firewall. If the traffic does not meet the rules or criteria that have been set, the firewall will reject the traffic and halt the data transmission. .. Privacy Settings As more online profiles are used to share content on social media, there is an everincreasing need for users to ensure that their privacy settings are set correctly. If no privacy settings are set, then a user’s content is accessible to anyone using a particular site or platform. Privacy settings should be set to ensure that a user has full control over who sees and interacts with data and information online. .. Proxy Servers One way of keeping website browsing activity secure is by using a proxy server. The user will then view web pages through a proxy server rather than directly via the home router. The proxy server sends out the requests to view a website and sends the information back to the user. This has the advantage of enabling a Privacy settings are vital for protecting against unauthorised access. user to keep their IP address secret, thus minimising the opportunities for cyber- criminals to know where data is being sent to and from. DDoS attacks are therefore much less likely to occur when using a proxy. Proxy servers can also be used as parental controls on a network, as they can be set up to block incoming and outgoing web traffic to specified websites. .. Secure Sockets Layer Security Protocol SSL is a protocol that is commonly found on websites where financial transactions take place. Any website that requires users to use a bank card to make a purchase should have secure sockets layer security. SSL encrypts the connection between the user’s computer and the website that is being used. All data that is transmitted between the user’s web browser and the web server that hosts the website is encrypted by the protocol and stays private. The types of data transmitted securely through the protocol are bank card numbers, login details and passwords. LINK WB Consolidate your understanding by completing Exercise 1, page 54 in the Workbook. 80 SB CS PP.indb 80 It is important to check whether a website uses the secure socket layer before carrying out a financial transaction. If a website has got https:// at the start of the URL, then the site is using SSL and is safe to transmit personal data. If the URL only has http:// at the start, private data is in danger of being intercepted, and may not be secure. An SSL connection is created between a web browser and a web server. This connection is known as an SSL ‘handshake’, whereby the browser asks the server to identify itself. In order for this connection to be secure, the web server needs to be certificated. This then provides the appropriate identification to enable the connection to be made. The encryption information is shared via the certificate, and the communication then takes place between server and browser, with both pieces of technology having secured the asymmetrically encrypted connection. The Internet and Cyber Security 14.5.21. 14:14 Chapter 5 The Internet and Cyber Security SB CS PP.indb 81 81 14.5.21. 14:14 Chapter 5 Let’s Review 1 2 3 4 5 10 What is the difference between the internet and the world wide web? What do the letters URL stand for? Http stands for hypertext transfer protocol. What does https mean? Name three features of web browsing software. What do the letters DNS stand for? Describe the process of a DNS Query. What are the two types of cookies stored when browsing the web. Name two things a cookie can do while you are browsing the web. Bitcoin is one type of digital currency. Name another two types. Explain what blockchain is in terms of digital currency. Name three different types of cyber-attack that could occur. What is malware? What is the difference between pharming and phishing? Explain what social engineering is. Explain how enabling software updates can protect user data. What does a proxy server do? 82 The Internet and Cyber Security SB CS PP.indb 82 14.5.21. 14:14 CHAPTER 6 Automated and Emerging Technologies COMPUTER SCIENCE WATCH Scan the page to watch a clip on emerging technologies in computer science. Before watching discuss what you expect to see or hear. QUESTIONS • What are the newest technologies coming into our lives? At the end of this chapter, you will be able to: explain how sensors, microprocessors and actuators work together to create automated systems • What is an automated system? • What is a robot? • How can artificial intelligence change our lives? the advantages and disadvantages of using automated systems in different scenarios explain what is meant by robotics, including the common characteristics of a robot understand the role of robots in different areas of society and the advantages and disadvantages of this explain what is meant by artificial intelligence, including the main characteristics of artificial intelligence and their basic operation 83 SB CS PP.indb 83 14.5.21. 14:14 Chapter 6 WORD ALERT Automated: machines carrying out a job that would otherwise have been done by humans. QUICK CHECK Do you use any automated systems? Do you operate them yourself? As technologically advances there is less need for humans to carry out some jobs, especially repetitive tasks. Computers created for specific purposes can automate this type of work, leaving humans to ensure that nothing goes wrong with the automated processes. This chapter will explore some of the new ways that computer science has helped to enhance the way we work and live. . Automated Systems For a system to be fully automated and operate independently of a human, it combines several different component parts. The three important components of an automated system are: • sensors • a microprocessor • actuators A temperature sensor attached to a water pipe. A microprocessor embedded into a machine. An actuator, in the form of a piston carrying out a physical movement. 84 SB CS PP.indb 84 Automated and Emerging Technologies 14.5.21. 14:14 Chapter 6 Most sensors are based upon changes in the environment. For example, a motion sensor measures change in heat. The sensor detects the change and sends a message to a microprocessor (see Chapter Hardware) to do something different. The microprocessor uses the input from the sensors and sends instructions to other components, such as actuators. Actuators turn electrical signals into physical outputs such as movements. When all three of these components work together, automatic instructions become movements. These movements may be repeated infinitely, depending on the objective of the automated system. LINK See Chapter 3 Hardware. DEFINITION Components: pieces of equipment in a system. A motion sensor used in the home. A microprocessor works mainly on the basis of data comparison. If the data returned by a sensor is greater, or less than data that is stored, a signal is then sent to an actuator to perform an action. The action will only stop being carried out when data has normalised and matches again, or after an amount of time has elapsed. WORD ALERT Infinitely: continues forever, until stopped. Automated systems exist in many different industries and situations (see Figure .). Gaming Artificial intelligence opponents in games Lighting Home control systems Weather Airport weather monitoring systems Science Laboratory automation Agriculture Crop harvesting Industry Packaging of items to be shipped Figure . Automated systems. Table . explores some features of these automated systems and the advantages and disadvantages of automation for different industries and situations. Situation Industry Scenario Items in a factory are packed and packaged by an automated production line. Sensors are used to detect the sizes of items, microprocessors ensure that the correct packaging materials are selected and actuators are used to move the items around to ensure consistent and accurate packaging each time. Advantages Production is much faster and the number of errors are reduced. Disadvantages Fewer job opportunities as humans are replaced by machinery. Automated and Emerging Technologies SB CS PP.indb 85 85 14.5.21. 14:14 Chapter 6 Situation Transport LINK Agriculture Automatic harvesting of crops for supplying to shops and supermarkets. Sensors detect optimal times for harvesting based on factors such as weather conditions, microprocessors determine exact locations for the harvest and actuators are used to carry out the extraction of the goods from the ground. Faster collection of the goods. Weather Automated monitoring of weather at airports to help predict poor flying and landing conditions. Sensors check for potentially dangerous weather such as wind, rain, fog or snow, microprocessors are programmed to issue relevant warnings as a result of the data gathered and actuators can activate emergency systems such as lighting wherever required. Information about the overhead weather conditions is fed constantly to air traffic controllers. Predictions can sometimes be incorrect, for example if snow is forecast and does not arrive. Gaming The introduction of artificial intelligence as opponents in computer games (see section .). Sensors are built into gaming environments where characters interact with human controllers, microprocessors determine game outcomes and decisions, and actuators are activated in controllers to give haptic feedback, such as vibrations. The depth of gaming challenge is increased with computergenerated opponents who behave in a ‘human’ way. Decreases real social interactions with other humans and can create an almost fictional life. Lighting Lighting control systems in a house where routines can be preset based on behaviours. Sensors can detect ambient light levels, microprocessors run routines based on human requirements and actuators can activate home equipment. Systems can be ‘taught’ to react to environmental factors, such as switching lights on and off when the conditions are correct. Systems can become complex as they are different from traditional switches. The lightbulbs and technology also tend to be expensive to maintain. Science Automated laboratory experiments that can be carried out continuously over many days. Sensors detect changes in environmental conditions, microprocessors can calculate required alterations to the experimental settings and actuators can turn on heaters, coolers or water supplies as required. Many more repetitions of experiments and reading of data can take place than when humans carry out tests manually. If something goes wrong it can be several hours before this is discovered, which could ruin any results collected. ENRICHMENT SB CS PP.indb 86 Disadvantages A huge reduction in road traffic accidents and injuries caused by collisions. Consolidate your understanding by completing Exercise 1, page 58 in the Workbook. 86 Advantages Driverless cars can transport goods and passengers around a city based on start and end point instructions. Sensors detect the vehicle proximity to other objects; microprocessors control factors like speed and direction, and actuators are used to move the steering mechanism. WB Can you think of any other situations where an automated system has replaced the work of a human? Scenario Less traffic congestion. Potential for more vehicles on the road if the technology is popular. Automated cars are very expensive. Automated vehicles are large and Able to cover a large expensive. distance in a short Reduced job amount of time. opportunities for humans. Automated and Emerging Technologies 14.5.21. 14:14 Chapter 6 . Robotics The term ‘robotics’ means the design, construction and operation of robots that are used to enhance our working and personal lives. The different types of robots include those used in factories on production lines, domestic robots used in and around the home and airborne robots such as drones. To be classified as a robot, a system should have the following characteristics: • A mechanical structure or framework: a robot should be a piece of machinery that usually has some movable parts. It can be large or small. • Electrical components: a robot should have a combination of sensors, a microprocessor and actuators. The robot should also be able to be programmed by a human to carry out various tasks in a repetitive fashion until complete. A drone is a popular type of robot. The use of robots is increasing all the time, and there are several scenarios where human jobs have been replaced by robotic equivalents (Figure .). Domestic Robotic vacuum cleaners and lawnmowers will carry out the jobs with no human input. Entertainment Robotic cameras are used to position viewing angles. Medicine Use of robots to assist in surgeries where human hands are unable to reach. Industry Manufacturing Robots carrying out tasks like welding. Agriculture Robots are used to apply fertiliser and pesticides to crops. Figure . Robotics. Transport Robots used in space exploration, for example the Mars rover. ENRICHMENT Can you think of any other situations where a robot has replaced the work of a human? Table . explores some of the features of robotics for different industries and situations. Rand the advantages and disadvantages of robots. Robotic arms operating in a car manufacturing factory. 87 SB CS PP.indb 87 14.5.21. 14:14 Chapter 6 Situation LINK Scenario Advantages Industry Manufacturing robots on a production line in a factory, putting together cars. Accuracy in production is vital, and robots ensure that every car is put together the same way and is identical to all of the other cars produced. Fewer job opportunities as humans are replaced by machinery. Transport The introduction of robots into the transport industry may soon mean that we have access to self-driving cars. Space exploration has increased by sending robotic vehicles such as the Mars Rover to other planets. Robotic vehicles can get to places humans are unable to. The priority of the algorithm could be different in each car. Some may prioritise the safety of the driver, some pay priorities the safety of pedestrians etc. This could cause ethical issues. Automated technology is expensive, and could also replace human jobs. Agriculture Crops can be given exact amounts of fertiliser and pesticide by robots. This is particularly useful when the chemicals are potentially hazardous to humans. Accuracy of delivery of the chemicals is very important to the success of farming and crops. Fewer job opportunities as humans are increasingly replaced by machinery. The robots can also be expensive. Medicine Robots can be used during surgeries to perform complex procedures with more precision, flexibility and control. They can also be used to monitor vital life data, in research and development such as tissue engineering, in the replacement of limbs such as bionic prosthetics and to simulate certain medical environments and tasks for training purposes. Surgery can take less time, which improves the chances of recovery for the patient. This technology is highly expensive and has to be tested extensively in research before it is used on humans. Domestic Traditional household appliances like vacuum cleaners and lawnmowers are being replaced by robotic versions. Robots can quickly ‘learn’ This can encourage the environment. They a more sedentary can be programmed to lifestyle in humans. work at convenient times. Entertainment Robots such as drones can be used for film and television programmes, for example with aerial shots. Film can be presented in ways that a human would not be able to normally see due to robotic technology. WB Consolidate your understanding by completing Exercise 1, page 61 in the Workbook. REFLECT Where have you come across AI systems? ENRICHMENT Virtual reality (VR) is another emerging technology that is changing the way we live our lives. Have you ever experienced a VR world? Disadvantages Fewer job opportunities as humans are increasingly replaced by machinery. . Artificial Intelligence Artificial intelligence (AI) is a computer system that thinks like a human, or that simulates human intelligence. What sets AI apart from other forms of computer programming is that the system collects enormous amounts of data from its environment. This data collection is based upon some very specific rules. The system then uses this data alongside the rules and can reason with it, using ‘what-if’ questions. An AI system can then learn and change their output by analysing the data constantly. The two types of AI system you should be aware of are expert systems and machine learning. 88 SB CS PP.indb 88 Automated and Emerging Technologies 14.5.21. 14:14 Chapter 6 .. Expert Systems IT applications and systems are sometimes designed with expert procedures and the expertise of professionals in mind. The systems are designed to imitate a human expert on a specific topic, as if that person was actually present. These applications often have to be reasonably portable to be used in the field of expertise. Chess games As chess is a highly strategic game, developers have designed a system that allows a human user to play against a computer. The computer 'learns' moves and uses its database to play against an opponent. Medical diagnosis As with patient data, medical professionals often call on IT to help diagnose difficult illnesses. Systems will pose questions that doctors can use to narrow down symptoms and make a diagnosis. Mineral prospecting A system which uses sensors and probes in an area. The system calculates the probability of rocks and minerals being present in the area being explored. QUICK CHECK An expert system is any system that replicates the decisions taken by a human expert. Expert systems have to be bespoke to particular circumstances. Financial planning Primarily used by financial advisors, planning systems can help to project savings and investments depending on circumstances. The system can suggest ways of saving money or calculate expenses such as tax based on information given. Car engine fault systems Used if a car goes wrong and the solution to fix it is not immediately obvious. A computer is plugged into a special socket of a car and the system will then use the fault system to diagnose the problem. Plant and aminal identification Expert systems for classifying animals and plants exist, based on a number of questions that are mainly 'yes' and 'no' or factual answers. Route scheduling for delivery vehicles This is a system used by delivery companies to ensure its vehicles make the most efficient journeys and ensure cost effectiveness. The system will look at the number of parcels to be delivered, the number of delivery points, the size of the vehicle and time available, and will calculate the optimum route. WB Table . describes the features of expert systems. Expert System Feature Characteristics User interface How a user communicates and interacts with the expert system. The system will often ask questions that require an answer or a button press. Inference engine The part of the system that draws upon information from the knowledge and rules base to produce possible solutions to a problem. Knowledge base A collection of information from subject experts. Rules base A set of rules that are unable to be broken during problem solving. Explanation system The logical reasoning behind the solutions and decisions offered. Automated and Emerging Technologies SB CS PP.indb 89 LINK Consolidate your understanding by completing Exercise 1, page 63 in the Workbook. DEFINITION Logical reasoning: a set of reasonable conclusions and explanations. 89 14.5.21. 14:14 Chapter 6 WORD ALERT Replicating: creating as close to a copy of something as possible. REFLECT Think of types of system that work like a human brain? HELPFUL NOTES The world chess champion at the time was Gary Kasparov from Russia, and he did manage to beat Deep Blue eventually! When an expert system is implemented and used, the user of the system would firstly interact with the interface. This would be through the answering of questions that would form decisions leading to further questions, a little bit like a tree diagram. Throughout this, the rules base would prevent the user from breaking any rules of the system. This is important for safety. The system would use the answers that were being given to utilise the inference engine. This would begin generating potential solutions. If the answers generated do not automatically produce an obvious solution, the knowledge base would enable the user to refer to related information from experts that may potentially provide a solution. Once a suitable solution has been generated by the expert system, there would then be a logical explanation to accompany the solution to enable the reasoning behind the results. .. Machine Learning Machine learning is a form of AI that allows a computer to perform tasks intelligently and efficiently by learning from examples. The system is programmed with an ability to learn or be trained. This happens by inputting data that can be recalled by the system during development: the more data the system receives, the better it will be at recognising things later. Computer scientists program systems for machine learning by replicating some of the functions of the human brain, such as the nervous system. By producing a system that is as close to a human brain as possible, this ensures that it can begin to react, adapt and change its responses based on the input it receives. One of the most famous AI computers was called Deep Blue – a computer that could play games of chess against humans. In , Deep Blue was the first computer system to beat the world champion chess player, within the same time limits as a normal game. Although Deep Blue was not quite the type of machine learning that we see today, due to restrictions on storage capacity, it paved the way for much more complex systems as the technology evolved. A current example of machine learning is where computers are able to suggest tagged names of people on social media based on the amount of times their previously tagged photographs appear in timelines. The same process happens with places too, and machine learning AI on social media uses previously learned input to suggest place locations to add to photographs. A supercomputer capable of machine learning has enormous processing power. 90 SB CS PP.indb 90 14.5.21. 14:15 Chapter 6 Let’s Map It Microprocessor Sensors Decisions made AUTOMATED SYSTEMS Processing instructions sent Automated system Activaters Movements Science Industry Weather Transport Gaming Agriculture Lighting ROBOTICS COMPUTERS THAT LEARN • Industrial • Transport • Medicine • Domestic • Agriculture • Entertainment ARTIFICIAL INTELLIGENCE Chess your move... Expert system Machine learning Automated and Emerging Technologies SB CS PP.indb 91 91 14.5.21. 14:15 Chapter 6 Let’s Review 1. What are the three components of an automated system? 2. What does an actuator do? 3. Apart from driverless cars, describe an example of an automated system that exists in the world of transport. 4. A disadvantage of automated systems in gaming are that they can reduce social interactions with other humans. Think of another disadvantage? 5. Name a type of robot. 6. What are the characteristics of a robot? 7. Robots are sometimes used for medical purposes during operations. Think of another example of a robot used in medicine? 8. An advantage of a robot for domestic or home use is that they carry out jobs accurately. Think of another advantage? 9. What do the letters AI stand for? 10. What are the two types of AI? 11. In your own words, and using the vocabulary knowledge base, rule base, inference engine and interface, describe how translation software works. 92 SB CS PP.indb 92 Automated and Emerging Technologies 14.5.21. 14:15 CHAPTER 7 Algorithm Design and Problem Solving COMPUTER SCIENCE WATCH Scan the page to watch a clip on algorithms. Before watching discuss what you expect to see or hear. QUESTIONS • How is a problem solved through programming? At the end of this chapter, you will be able to: understand the different stages of the program development cycle, including the tasks performed at each stage • What stages does a problem go through to become a solution? • What are algorithms? • How can algorithms help developers to create programs? explain the purpose of a given algorithm understand how a linear search and a bubble sort are performed understand how totalling, counting and finding values are performed understand the importance of validation checks, including how a range of different validation checks are used understand the importance of verification checks, including visual checks and double entry checks understand how to choose suitable test data to test an algorithm understand how to complete a trace table write, amend and identify errors in an algorithm for a given problem or scenario 93 SB CS PP.indb 93 14.5.21. 14:15 Chapter 7 WORD ALERT Algorithm: a set of rules or instructions for solving a problem. For the purposes of exemplification of coding, the programming language selected is Python. There are a few examples where an alternative language has been used to give an example and, where this is different from Python, this has been stated. The reasons for the differences is that some of the examples in the IGCSE syllabus are not present within Python, so alternative languages have been used to demonstrate these features. Python does not deal with arrays or case statements and, in their place, the list and nested if functions are used instead. In this chapter we are going to explore algorithms and how they are used by programmers – in particular to solve problems. It is important to understand why algorithms are important, so that they can be used for different ways of solving a problem, and also how to structure them correctly. However, we must begin by looking at the program development life cycle and the process programmers go through when creating a solution to a new problem. . The Program Development Life Cycle When creating any new program, developers follow a process called the program development life cycle. This consists of four stages: analysis, design, coding and testing. ENRICHMENT Do you think critical thinking skills are important for asking the client the right questions and gathering maximum details? WORD ALERT Perspective: a particular way of thinking about something. UnPC: an exhaustive discussion to solve problems or generate ideas. Negotiations: a discussion to produce a settlement or agreement. It is a cycle and not a linear process because after developing the software it is often necessary to go back to the start of the process again if something has been discovered during development. .. Analysis Stage Analysis A system process begins with analysing or understanding requirements from the client’s perspective. Here, the client can be an organisation or the end user. The analysis stage may include several UnPC sessions, negotiations, data collection and information exchange. It is very important to allocate time to this – without a thorough understanding of the client’s requirements the entire process can become endless repetitions and corrections. Stage Requirements Ideally, after the initial discussions an analyst will sketch out the requirements. This may not always be practical if the program managers have limited resources and certain strengths and weaknesses in their team. To make the tasks achievable and avoid any potential risks and doubts, it is always good practice in the system process to conduct a feasibility study and create a feasibility study report. This highlights problems and possible solutions. 94 SB CS PP.indb 94 Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 Stage Abstraction and Decomposition The next stage of the analysis is to carry out abstraction and decomposition of the requirements. These are of two of the key elements of computational thinking – breaking down a complicated problem and developing a potential solution to it. Abstraction is the process of selecting the information in a problem and focusing only on the important parts of that information. During abstraction, any detail that is irrelevant to the problem is ignored. Decomposition is breaking down a complex problem into small manageable pieces. A problem becomes a series of small tasks that can be handled first individually and then collectively as part of the bigger program. DEFINITION Computational thinking: breaking down a problem into smaller sub-problems to solve them. Worked Example Abstraction Problem: A person wishes to make a cup of tea. Information obtained: teabags, milk, sugar, white mug, water, kettle, teapot. Abstracted information: we can ignore the colour of the mug as this is not relevant to this particular problem. Worked Example Decomposition Problem: A person wishes to make a cup of tea. This complex problem can be broken down into four smaller problems: water, combine, personalise and serve. Decomposed problem: • Water: fill the kettle with water and heat it until it reaches boiling point. • Combine: add the water to a teabag in either a teapot or mug and leave for a set time. • Personalise: remove teabag from water, pour tea into a mug, and add the sugar and milk to taste. • Serve: stir the tea and drink it from the mug. .. Design In the design phase, the developers of the program will continue the decomposition phase from the analysis and begin to draw up visuals of the end product. This will include structure diagrams that help to visualise the end goal. The coding required to make the visual representations happen will be started at this point. The developers will create flowcharts that show how a program’s decomposed parts will run, including any decisions or inputs that are needed. The programmers will then begin to develop pseudocode that enables the complex problems and instructions to be read in plain English. Pseudocode is an excellent way to check that the instructions make sense prior to the coding process. Algorithm Design and Problem Solving SB CS PP.indb 95 WORD ALERT Visualise: to be able to see a prototype of an idea. WB LINK Consolidate your understanding by completing Exercise 1, page 66 in the Workbook. 95 14.5.21. 14:15 Chapter 7 Worked Example Flowcharts Problem: Making a cup of tea – the water stage. A flowchart for this particular decomposed problem might look like this. NO HELPFUL NOTES A test plan includes: • a list of the tests planned YES • the data to be used in the test • the expected outcomes The steps are written out and the appropriate decisions are contained within the flow. • the purpose of each test • the type of tests to be performed WORD ALERT Comprise: include, be made up of. .. Coding and iterative testing This is sometimes known as the implementation stage. The programmers work on the design modules, such as input, output and processes, and write the code to make each part of the program functional. The programming is then linked together as a complete solution. A testing strategy is planned by analysts and the test plan will comprise details of all the programs to be tested. .. Testing DEFINITION Test strategy: test plans for testing the system. 96 SB CS PP.indb 96 Testing every part of the programming requires a test strategy. First, the entire system is divided into small sections that are tested for input, output and validation rules. Test data is used for all of the tests to be carried out. Testing each part of the code individually is known as unit testing, and integration testing is used when this code is all combined to form a program. The testing team reports any errors to the programmers and the testing is repeated until there are no errors found in the system. Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 . Computer Systems LINK As we learned in Chapter , all computer systems require an input, some processing and an output. Also linked to this processing is storage, which enables data to be used as and when required. All computer systems that operate are made up of subsystems, which can have further subsystems within them. These are smaller processes that are vital for the bigger system. We can apply what we know about systems to programs. Each problem to be solved by a program can also be decomposed into its component parts. For every problem, the design stage must consider the inputs required, the processing required and the resultant outputs. Chapter 3: Hardware. QUICK CHECK What are the three ways designers can plan a solution to a problem? Programmers can employ a combination of different methods to plan solutions to problems. Pseudocode, structure diagrams and flowcharts are often used in combination to design these solutions. Flowchart Pseudocode Structure diagram Pour the water into the kettle. Plug the kettle in. Switch the plug on at the wall. Turn the kettle on. Check to see if the water is boiling. If the water isn’t boiling, check the electricity. If the water is boiling, wait for a number of seconds. If the water has not yet reached boiling point, keep waiting. If the water has reached boiling point, turn off the kettle and pour the water. NO YES Algorithm Design and Problem Solving SB CS PP.indb 97 97 14.5.21. 14:15 Chapter 7 .. Flowcharts In a flowchart, a set of standard symbols are used to identify different parts of the data flow. The most common symbols are shown here. Symbol example ENRICHMENT Draw a flowchart for a simple procedure, for example how to brush your teeth? Terminator Use This symbol represents the start and end points of a sequence of data. This symbol represents an instruction. Process This symbol represents a decision, that is a yes or no answer. Decision Input or output This symbol represents an input received or an output sent by a system. This symbol represents connections between the other symbols and the flow of data around the system. Flow direction This symbol represents a smaller procedure running within the larger program. Subroutine DEFINITION Pseudocode: a version of programmable code written in standard English. 98 SB CS PP.indb 98 .. Pseudocode Another way that data flow can be represented at the design stage is by using pseudocode. This is a useful way of designing solutions as it can be written in a way that doesn’t require exact use of the same syntax as any particular programming language. Pseudocode at this stage doesn’t rely on which language the program is to be written in and can be structured in a way that anyone can understand the procedure or flow of data. Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 For example, writing some pseudocode for a procedure for starting a new game might look like this: IF Lives = 0 REFLECT THEN Try writing some pseudocode to describe your decisions about eating. End Game Output “Game Over!” ELSE restart the level ENDIF WB .. Structure Diagrams Structure diagrams are another way of representing data flow in diagram form. They are different from flowcharts as they display the different levels of detail within a set of decomposed problems. LINK Consolidate your understanding by completing Exercise 4, page 74 in the Workbook. The problems are sometimes broken down into smaller problems, or subsystems, and they are represented in a tree diagram, with the big picture at the top. In our tea making example, the structure diagram may look like this: As all of these subsystems happen one after another, this diagram does not have a hierarchical structure, however if these subsystems were decomposed even further, then there may be another level or levels of structure. Just like flow charts, there are a set of pre-defined symbols that go into a structure diagram. Symbol example Use This symbol represents an instruction and will need to be programmed. Process This symbol represents that some sort of iteration is occurring and will need to be coded as such. Loop Algorithm Design and Problem Solving SB CS PP.indb 99 99 14.5.21. 14:15 Chapter 7 Symbol example Selection Use This symbol represents a common procedure that is likely to already exist in a programming language’s library. This symbol represents a selection and that there will be different outcomes. REFLECT Think about the last algorithm you followed, what was the end goal? WORD ALERT Pictorially: in the form of a diagram. Pre-defined function . Algorithms An algorithm is a set of instructions or rules to follow step-by-step to solve a problem. A flat-pack piece of furniture usually comes with an instruction manual that details a set order on how to assemble the item. This is a type of algorithm. As we learned earlier in the chapter, an algorithm can be represented both pictorially and in textual form. There are often multiple ways of solving a problem and exploring all of these at the design stage is beneficial. When designing an algorithm, have the end result in mind. A programmer needs to understand the goal and look at the stages involved in achieving that goal. • Inputs: What are the inputs to the problem? • Outputs: What will the outputs look like? • Order: In what order do things need to be carried out? • Decisions: What decisions will be made while solving the problem? • Repetition: Are any of the stages repeated? HELPFUL NOTES Worked Example When designing an algorithm, always consider the extent of the problem and the end result. Algorithm design An end user needs a program that calculates shipping costs for items sold, and different costs apply depending on where things are being posted to. The end goal is the correct posting costs. The stages of the problem are as follows: ENRICHMENT It is important to remember that flowcharts and pseudocode have to be used together to design an algorithm. Solutions can be unclear if either are missing. 100 SB CS PP.indb 100 • sizes of the items • cost of preparing the item for posting • location of posting destination • cost of posting calculated: size + packaging + destination rate A programmer would take all this information, abstract and decompose the problem, and then create appropriate flow charts, pseudocode and structure diagrams to come up with the most efficient solution based on the information gathered. Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 Activity Design an algorithm that helps a bus or train system determine the correct fare to charge a passenger. (Hint, passengers could be adults or concession fares, children or senior citizens). Draw a flowchart and write some pseudocode to show your working. WB LINK Consolidate your understanding by completing the Exercises 1-3 from pages 66-73 in the Workbook. . Solution Methods The concept of algorithmic thinking has been around for a long time, since computers have existed. So, there have been many algorithms designed that have become common in a variety of programming languages. In particular, algorithms can search and sort data, find totals and count data, and also carry out functional operations such as finding the maximum, minimum and average values. .. Linear Search As its name suggests, this type of search means that all items of data in a set are looked at until the program matches the piece of data it is looking for. Once this match is obtained, the search is completed. We can try to understand linear search by looking at this table of game scores. Position Scores If a program was required to search for a specific score of , a linear search would begin at position , and check the score. This score is and is not a match, so the search moves on to position (no match), then position (no match), position (no match) and then reaches position , where a match for is found. The linear search then ends. This type of search is not the most efficient method of finding a match of data, however it will work on any data set. .. Bubble Sort A bubble sort is another standard solution algorithm, and this is used for turning a data set from an unordered set into an ordered one. A bubble sort is based upon the idea of swapping adjacent items in a data set until the set is in the desired order. A bubble sort becomes increasingly slow as the number of items in the data set increases, as it is based upon making comparisons. Each time a comparison is run through the data set, this is known as a pass. The sort ends when a pass is made through the data and no swaps are carried out. Algorithm Design and Problem Solving SB CS PP.indb 101 REFLECT Linear searches are quite inefficient in nature. Why do you think this is the case? ENRICHMENT A bubble sort is only efficient with a small data set. How would you sort a larger data set? WORD ALERT Adjacent: the item next to another item. Comparisons: checking one item against another and looking for differences or similarities. 101 14.5.21. 14:15 Chapter 7 Worked Example A bubble sort A data set consists of the following unordered game scores, and an algorithm is required to order this list from smallest to largest: Position Scores Pass one The value contained in position () is smaller than position (), so nothing changes at this stage of the pass. The sort moves to the next adjacent position. This time the value in position () is larger than position (), so these two items are swapped. Position Scores The next position, position is considered. The value here () is larger than the value in position (), and so these two items are swapped. Position Scores This is the end of the first pass, but the order still may not be correct. Pass two A second pass now takes place. The value in item () is larger than the value of item () so these are swapped. Position Scores The value in position () is larger than position (), so these are also swapped. Position Scores The value of position is smaller than position , so no further swaps are made. This is the end of pass two. Pass three The sort then begins a third pass. The value in position () is larger than position (), so these items are swapped. 102 SB CS PP.indb 102 Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 Position Scores QUICK CHECK Position is smaller than position , so no swap is made. Position is smaller than position , so again no swap is made. This is the end of pass three. What is meant by a pass when sorting? Pass four A fourth pass is then carried out, but no further swaps are required. This is the end of the sort, and because no swaps occurred in the fourth pass, the algorithm now knows that the data set is in the desired order. As you can see in this example, a bubble sort on a large data set would take a comparatively long time to carry out and would be highly inefficient. Activity How many passes would be required to sort the following data set from smallest to largest using a bubble sort? Position Scores .. Totalling and Counting REFLECT • Totalling: a common algorithm used to add one number to an existing stored number. For example, you might wish to add up the number of different objects collected by a player in a game. Why is a final pass carried out in a bubble sort even when nothing changes? • Counting: keeping a check on how many times a program has repeated a procedure in a loop. For example, you might wish to count the number of attempts at a level in a game. .. Standard methods of solution There are also some common functions that can be performed as algorithms. This may be useful during the problem-solving process. HELPFUL NOTES A count is a fairly standard feature of most computer games. Counting is used for lives, levels and health. • MAXIMUM: Within a specific data set, this standard algorithm can identify and return the largest number in the set. • MINIMUM: Within a specific data set, this standard algorithm can identify and return the smallest number in the set. • AVERAGE: Within a specific data set, this standard algorithm can take all the values in the data set and return an average value of all data. Algorithm Design and Problem Solving SB CS PP.indb 103 ENRICHMENT Can you find any other common functions in programming languages? 103 14.5.21. 14:15 Chapter 7 HELPFUL NOTES Data validation checks include presence, range, length, format, consistency and type. DEFINITION Validation: the process that helps the system know the data entered is correct. Validation check: testing for validations. . Data Validation and Verification When creating coding for a new system, it is important that a programmer considers all the input of data that will be coming into the program. Validation checks on data are therefore essential to the correct working of the program, and these checks ensure inputted data follow the rules. If the data does not follow the rules set by the checks, the data will be rejected by the program. .. Validation There are several types of validation check that a programmer can implement into their code where user input is required. Type of validation Purpose Example usage Coded example Range check This checks for data input that falls within a range, and can apply to numbers, dates and characters. A date of birth is required and the program requires a user to be older than age . if age in range (0,12): print( “you are not old enough to continue”) else: print(“you may continue”) Length check This checks whether an input is too long or too short. A password or passcode is required and must be a particular length. pw = input(“Type your password:” if (len(pw)<5 or len(pw)>10): print(“Your password is not valid”) else: print(“Your password is the correct length”) Type check This checks whether an input is the correct type of data, such as text or a number. An age is required in numbers and any other type of data is rejected. type(object) Presence check This checks whether an input has been made or not, and will not allow a process to continue until something has been entered. The quantity of items ordered was required to make a stock system calculate a total. quant = input(“Please enter number of required items:”) while len(quant) == 0: quant = input(“Please enter number of required items:”) Format check This checks to see if data has been entered in the correct format for the input. A date is required in DD/MM/YYYY format. day = input(“Please enter the day of your date of birth:”) if day in range (1,31) print(“next”) else: print(“please re-enter the day”) repeat for month and year Check digit This checks for the final digit in a code of numbers and is calculated mathematically from all of the other digits in the code. A number from a barcode needs to be stored. num1 = input(“please enter number 1:”) num2 = input(“please enter number 2:”) num3 = input(“please enter number 3:”) sum = float(num1)+float(num2) +float(num3) print(“Digit is” (sum)) ENRICHMENT Validation checks sometimes display a message known as a prompt box to let the user know the data entered is not valid. REFLECT Different form fields can have different validation checks based on the type of data entered. Can you suggest a validation check for entering an appropriate password? QUICK CHECK List the different data validation checks. 104 SB CS PP.indb 104 Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 .. Verification REFLECT It is one thing having a system validate data for input errors, but it is another thing checking to see if the data entered is meaningful and correct. Even with a variety of the validation rules applied from the table above, wrong data could still be entered. There are two methods of verifying data that has been entered: Visual checks have to be carried out by humans, and this increases the cost of this part of verification • Double entry: The same data is entered twice and the first entry is checked against the second one. For example, a system requires a password and asks the user to enter it a second time to ensure it is an absolute match. • Visual check: A human check for erroneous data that has been entered into a system and trying to spot obvious errors or mistyping. . Testing Testing every part of the program requires a test strategy. First, the entire program is divided into procedures that are tested for input, output and validation rules. The testing analysts report any errors to the programmers and the testing is repeated until there are no errors found in the system. There are four types of testing data: • normal data • extreme data • abnormal data • boundary data Consider the following scenario. The qualifying age for an exam is between and years. The different types of testing values for this are shown in the table. Type of testing data Description Example Normal data The data that is entered normally as per the expected outcomes. The values will be , , , , , , , . Extreme data This data includes the extreme values of the normal range given. The values will be , . Abnormal data This data is outside the limits of the acceptable data given. The values will be , , male, female. Boundary data This data includes the extreme values of the normal range given and the corresponding smallest/ largest rejected value. The values will be , , and the rejected boundary data would be and . . Trace Tables Before coding can complete the testing phase, it is important to put algorithms through a ‘dry run’ to ensure that they all work as intended. This is carried out by producing a trace table, which enables a programmer to work through the code on paper, line-by-line, to check where variables, selection, sequencing and iteration take place. The trace table also allows a programmer to check the results of the processing and to see what should be output at any given point in the code. Algorithm Design and Problem Solving SB CS PP.indb 105 105 14.5.21. 14:15 Chapter 7 It is also important to try to list all of the possible user inputs into a program when designing a trace table. Worked Example A trace table Consider the following simple program that iterates four times through an addition of to a starting number: 1 Number = 5 2 PRINT Number 3 FOR x FROM 1 TO 4 4 Number = Number + 3 5 PRINT Number 6 PRINT “Complete!” The trace table for this program would look like this: Line number Number x Output Complete! Each time the variables change, their values are listed in the table. The trace then iterates back through the loop as many times as has been programmed. 106 SB CS PP.indb 106 Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 Activity Draw out a trace table for the following program: 1 Number = 18 2 PRINT Number 3 FOR y FROM 1 TO 5 4 Number = Number + 7 5 PRINT Number 6 LINK See Chapter 8 Programming. PRINT “Done” Your table will require the following headings: Line number Number y Output . Error Checking and Correction Two of the most common errors that can occur when writing programs are syntax errors and logic errors. • Syntax error: some of the code goes against the rules of the language that has been written for the program. This can be a misspelling of a common word, omitting brackets or trying to call a variable before it has been declared. • Logic error: a program behaves unexpectedly and produces unusual results. This type of error can occur when logical or Boolean operators are not used in the correct manner, putting a program accidentally into an infinite loop or using variable names wrongly. The key difference is that with a syntax error the program will not run at all, whereas with a logic error the program will run but it is likely to run incorrectly and not work as expected. Most programming languages will have syntax correction built in and will even identify the line where an error has been found. Syntax errors Each of these lines of code contains a syntax error: STRAT 2 POINT(“hello world”) 3 INPUT(“What is your age: “ Boolean: where a variable can have one of two values, true or false. HELPFUL NOTES Worked Example 1 DEFINITION • Start has been spelt incorrectly in the first line. • Point should be print in line . • Line has had a bracket opened but not closed – a close bracket should be added at the end of the question. Algorithm Design and Problem Solving SB CS PP.indb 107 107 14.5.21. 14:15 Chapter 7 LINK Logic errors This program was written to determine whether a cheap travel fare can be applied for a young person. WB Consolidate your understanding by completing Exercise 5, page 78 in the Workbook. The program has been written in Python for the purposes of looking at the errors in detail. 1 Age = INPUT(“How old are you: “)) 2 IF Age = 13: 3 PRINT(“child fare”) 4 ELSE 5 IF Age >=12: 6 PRINT(“child fare”) This code will work when it runs, however there are several logic errors: • In line , the program will respond if someone is exactly and not or under. • In line , the program states that a child fare is payable if the passenger is greater than or equal to – this is incorrect and should be re-coded. • The program also doesn’t enable an outcome for someone who isn’t a child passenger. The program should look like this: QUICK CHECK What are the three types of design documentation needed to create an algorithm? 1 age = int(input(“How old are you: “)) 2 if age <= 13: 3 4 5 print(“child fare”) else: print(“adult fare”) . Writing Algorithms It is now your turn to create some algorithms. Work through the activities below. For each scenario, create a flowchart and pseudocode, to solve the problem. Activity LINK WB Consolidate your understanding by completing the Exercises 1-3 from pages 66-73 in the Workbook . 108 SB CS PP.indb 108 Design, document and code a solution to the following three problems: A A cinema is looking for a system which only allows customers to see films that are appropriate to their age. Using a date of birth, a system must determine whether a customer can buy tickets for a Universal (U) film, a Parental Guidance (PG) film, a rated film, a rated film or an rated film. B A game needs to store the top ten scores for a level to be able to run a monthly competition. Once a month ends, the top score from each month must be added to a table that shows all of the top monthly scores in a year. C A car hire company wishes to only hire Category vehicles to customers who are over the age of , have a clean driving licence and have been driving for at least years. They wish to hire Category vehicles to customers who are over , may not have a clean driving licence and have been driving for at least years. They wish to hire Category vehicles to customers who are over , may not have a clean licence and have been driving for at least years. They do not wish to hire any vehicles to customers below the age of , regardless of their driving licence status or how many years driving of experience they have. Algorithm Design and Problem Solving 14.5.21. 14:15 Chapter 7 Algorithm Design and Problem Solving SB CS PP.indb 109 109 14.5.21. 14:15 Chapter 7 Let’s Review 1 2 3 4 What are the four stages of the program development life cycle? What is abstraction? What is decomposition? In a flowchart, what is this symbol used to represent? 5 Pseudocode uses only the syntax from a programming language to design a solution to a problem. True or false? What is the difference between a flowchart and a structure diagram? Why is a linear search an inefficient way of searching through data? What is an unordered data set? Describe how a bubble sort works. Name three types of data validation. Visual checking is one form of data verification. Name the other type. Explain the purpose of testing a program. What is extreme data when testing a program? What is the purpose of a trace table? What type of error would be present if a common word had been spelt incorrectly? Write an example of a logic error in a line of code. 6 7 8 9 10 11 12 13 14 15 16 110 SB CS PP.indb 110 Algorithm Design and Problem Solving 14.5.21. 14:15 CHAPTER 8 Programming COMPUTER SCIENCE WATCH Scan the page to watch a clip on Python programming. Before watching discuss what you expect to see or hear. QUESTIONS • What are the key concepts of programming? • What are the different types of data you can work with when coding? At the end of this chapter, you will be able to: understand how to use variables and constants • How can you write code to do mathematics? • What sort of programming goes into a game? understand how to use different data types understand how to use sequence, selection and iteration understand how to use totalling and counting methods understand how to use string handling methods understand how to use procedures and functions understand how to use a range of library routines understand how to create maintainable programmes understand how to use both D and D arrays understand how to use file handling methods 111 SB CS PP.indb 111 14.5.21. 14:15 Chapter 8 In Chapter we looked at the importance of algorithms when solving computer problems. Computers put these algorithms into action while using a programming language. When programming a piece of software, algorithms and instructions can be communicated to a computer’s hardware to carry out the requirements of a user. It is important to note that there are many programming languages and, just like different spoken languages from around the world, each one has its own set of unique words and rules. Even though some ideas seem the same between different languages, the way of achieving the outcome can be quite different. For the purposes of exemplification of coding, the programming language selected is Python. There are a few examples where an alternative language has been used to give an example and, where this is different from Python, this has been stated. The reasons for the differences is that some of the examples in the IGCSE syllabus are not present within Python, so alternative languages have been used to demonstrate these features. Python does not deal with arrays or case statements and, in their place, the list and nested if functions are used instead. QUICK CHECK How much programming have you done? What languages have you programmed? How confident are you with this? . Programming Concepts .. Variables and Constants Data can be constant or variable when used in a program. A variable piece of data can be changed in some way, either by the user or the program. This data has to be declared by a programmer before it can be used in code. LINK WB Consolidate your understanding by completing the Exercises 1-2 from pages 91-92 in the Workbook. Declaring a constant or variable means that the type of data is defined, and an initial value for the variable or constant is set. Variables do not have to have an initial value, but it is often useful. For some programming languages, data types of constants and variables must be specifically declared to be used in programming, however in others, such as Python and JavaScript, this is not the case. Constants stay the same every time a program is run or executed. They do not change their value. A good example of a declared constant might be an amount of time that something should take in a game. Variables are items of data that are expected to change during the program’s operation, usually because of a question that has been asked or activities within the program. A good example of a variable would be the high score for a game. Variables are a location within the computer’s memory, and the data associated with the variable is stored in this location. The variable therefore needs to be given a name by which it can be found during the program’s execution. .. Basic data types There are five basic data types that programmers use when creating code. These are used to declare variables or constants. Data type DEFINITION Floating-point: a number in programming that contains a decimal point, and the decimal point can ‘float’ in different places to help with handling large numbers. 112 SB CS PP.indb 112 Definition Example Integer This is either a positive or negative whole number. Real This is a decimal number and can also be used to store integers. It is also known as the float (referring to floating-point). . Char A data type used for holding a single character, which could be a letter, number or symbol. £ String A combination of letters, numbers and symbols held together as one piece of data. PROGRAM Boolean A data type returning a True or False value, or for On and for Off. FALSE Programming 14.5.21. 14:15 Chapter 8 .. Input and Output Input and output are another two important programming concepts, and refer to communication between a program and a human user. Input The input is used where some information is required by the program, often from a user. The input is used to prompt the user to enter some data. This type of input also requires an instruction to tell the user what sort of data they need to enter. Input can also come from within a program itself, although this is often considered to be an inefficient way of coding. Another way of obtaining input is from an external file that is linked to the program. WORD ALERT Inefficient: not the best or fastest way of achieving a goal. Output The output is where information is communicated back to the user as a result of the input. This is usually done using the print function. This statement usually gives the user some information about the result they are about to see, and then the results of any calculations carried out on the variables or constants are displayed. Worked Example WB LINK Consolidate your understanding by completing Exercise 3, page 94 in the Workbook. Here is an example of some Python code for a program that calculates the area of a circle. Mathematics and geometry show us we can calculate the area of a circle with this formula: πr2 The symbol π (pi) is a constant and is equal to approximately . when rounded. To find the area of a circle we first need to know its radius, r. Most programming languages have a pi constant already built into their library of functions. If we know that the radius of the circle is 5, we could write this Python code to calculate the area: FROM math IMPORT pi r = 5 PRINT (“The area of the circle with radius ” + str(r) + “ is ” + str(pi * r**2)) The circle with a radius of has been hard coded into this program and is stored as a constant. However, it would be much more useful for the programming to be able to accept a user input for the radius and store it as a variable, so that a circle of any radius could be calculated. We could therefore consider the following adjustment to the Python code above: FROM math IMPORT pi r = float(input (“What is the radius of the circle : “)) PRINT (“The area of the circle with radius ” + str(r) + “ is ” + str(pi * r**2)) This time the user is prompted to enter the radius, and the program uses that data to make the calculation. Programming SB CS PP.indb 113 113 14.5.21. 14:15 Chapter 8 DEFINITION Constructs: the building blocks of programming. .. Programming fundamentals There are several constructs in programming and it is important to learn these so you can create your own coding. All algorithms that are written for programming require some constructs in order to work effectively. ... Sequencing An algorithm contains instructions that are carried out one after another, and the sequence determines the order that these instructions are carried out. For example, a basic algorithm for making a cup of tea might look like this: . Boil the kettle. . Pour water into the mug. . Stir. . Put a teabag in a mug. . Add sugar and milk. . Drink the tea. The numbers indicate the order of the steps, and these steps have been sequenced. Imagine if the algorithm had been written like this: . Put a teabag in a mug. . Boil the kettle. . Pour water into the mug. . Stir. . Add sugar and milk. . Drink the tea. REFLECT Can you write an algorithm for an everyday procedure? The Stir step is now in an incorrect place, and the drink would not taste as expected, however a teabag could still be stirred at that point. This is a good example of a computer doing as it is told, whereas humans would recognise that this sequence is wrong. It is therefore important that programmers get the sequence of their programming right to produce the desired result. ... Selection Another fundamental construct in programming is the ability for the code to make a decision or ask a question, usually when there are several possible options. Selection can be written into programs by using either an IF statement or a CASE statement. Selection using IF statements allow a program to take different paths depending on the answer to a question, and take the form of IF, THEN, ELSE instructions. For example, an algorithm could show a user the most appropriate directions to a destination based on their mode of transport. The steps might be: . Find out if you are in a car or on public transport. . If driving a car, show a map using roads. . Otherwise show a map with bus and train routes. When preparing this algorithm for programming, we might consider the following: . Are you driving a car or using public transport? . IF you are driving a car, THEN look at this road map for directions. . ELSE look at this map that contains bus and train routes. Depending on the answer that is given at Step , the program can follow two different paths: one for someone driving themselves, and another for someone using public transport. Another form of selection is by using a CASE statement. This is where a set of options are programmed for a question that has many different potential outcomes. For example, a program may look up the answer to a question based on some similar variables, and output a word or phrase based on the answer. Look at the following code from the Java programming language: ENRICHMENT Write an algorithm in standard English that contains an if, then, else scenario. 114 SB CS PP.indb 114 CASE clothing of: Shirt: OUTPUT “Monday” BREAK; Jacket: OUTPUT “Tuesday” BREAK; Shoes: OUTPUT ‘Wednesday” BREAK; Programming 14.5.21. 14:15 Chapter 8 Jumper: OUTPUT “Thursday” BREAK; Shorts: OUTPUT “Friday” BREAK; DEFAULT: “I don’t know this clothing” The selection will go directly to the appropriate line of code based on the input or condition that is being tested, in this case an item of clothing that is associated with each day of the working week. If the condition is not recognised, the program will go straight to the DEFAULT output. ... Iteration Iteration takes place in an algorithm where the rules determine that a step or steps should be repeated until a condition is met or until told to stop. Iteration is therefore the process of repeating the steps in a program. A straightforward algorithm for eating toast might be as follows: Make the toast. Put toast on the plate. Put butter on the toast. Cut toast in half. Eat slice of toast. Repeat step until all of the toast is eaten. Wash the plate. By inserting the line ‘Repeat step until all of the toast is eaten’ the program is able to be simplified by giving a repeat command until a condition is met, in this case when the toast is eaten. Another word for iteration in programming is loop. In effect, the program is looping Step until the set condition is met. There are different types of loop in iterative programming. Type of loop HELPFUL NOTES It is important to note that the CASE structure is not built into the Python programming language. HELPFUL NOTES Iterating is the process of repeating an instruction as many times as the program requires. Description Count-controlled loop The number of loops or iterations is already decided. A counter is used to record how many times the iteration has occurred. This type of loop is known as a FOR loop. (Example A) Pre-condition loop This is where a condition must be true before the loop or operation takes place. This type of loop is known as a WHILE loop. (Example B) Post-condition loop This is where a condition must be true after a loop or operation has taken place. In the C programming language, post-condition loops are implemented using a DO-WHILE loop. (Example C) Another type of post-condition loop is a REPEAT ... UNTIL loop. This repeats what is within the loop until the condition defined at the end is met. A pseudo-code example of this would be count = 0 REFLECT Can you write an algorithm in standard English for something that requires repeat actions? REPEAT count = count + 1 OUTPUT count UNTIL count == 10 This will output a count from to . Programming SB CS PP.indb 115 115 14.5.21. 14:15 Chapter 8 Worked Example Example A: Count-controlled loop (FOR) If a program was written to add three lives to a total number of lives, the Python code could read like this: ADD Life ADD Life ADD Life More efficient code would be:: REPEAT (ADD Life) 3 times We would therefore write the actual code like this: FOR count IN range(1,4): PRINT(“Add Lives: “ + str (count)) This code would repeat the add lives command three times. Example B: Pre-condition loop (WHILE) This is a loop carried out while a question or a condition is true or false. If a program was written to check that a door was open before switching on a light, the algorithm might look like this: Is the door open? QUICK CHECK What are the three types of iteration? Can you confidently explain the differences? Give the light electricity while the door is open A piece of Python code might look like this: Light = INPUT(“Type shut when you go out: “) WHILE Light!= “shut”: PRINT (Light) Light = INPUT(“Type shut when you go out: ”) This code would keep on asking the user to confirm the door was shut in order to end the pre-condition loop and would carry on checking while the program was iterating. Example C – Post-condition loop (DO-WHILE) This is a loop that would be carried out after a condition is checked for either a true or false answer to a question. Therefore, a do-while loop would always run once, even if the condition checked is false, and would stop after the single iteration. If the condition was true, the loop would iterate again. It is important to note that the DO-WHILE iteration is not built into the Python programming language. Consider this algorithm: Are there litres of water in the bucket? Turn the tap off when there are litres of water. A piece of code from the Java programming language might look like this: LINK WB Consolidate your understanding by completing Exercise 5, page 96 in the Workbook. 116 SB CS PP.indb 116 COUNT = 1 DO PRINT(count) count+=1 WHILE count <5 This type of loop would repeat until the while line returned a false value. It would then stop the program. Programming 14.5.21. 14:15 Chapter 8 ... Totalling and Counting We now know that programs can use a counter when using a FOR loop. Counting keeps a check on how many iterations a program has performed in a loop. For example, you might wish to count a number of attempts at a level in a game. We might write a counter into Python code like this: count = 0 WORD ALERT count = count + 1 It is possible to insert the counter into an iterative loop to increment by each time the loop is carried out. Increment: to increase by a set number. Totalling is used to add one number to an existing stored number, usually contained in two different variables. For example, you might wish to add the number of different objects collected by a player in a game. We might write a total in code like this: total = total + items Total and items are two different variables, and data would be stored in both. REFLECT ... String Handling Strings are a data type used to hold combinations of letters and numbers, or alphanumeric characters. Strings are variables that can be assigned names and can be handled in several different ways within programming. Have you ever played a game where a feature included a counter? A string might look like this in Python code: Name = “Greg” HELPFUL NOTES The variable ‘name’ contains the combination of letters ‘Greg’. The contents could also include numbers and symbols. We are now going to look at the different ways strings can be handled. Strings can contain letters, numbers and symbols. Length Coding can be used to discover the length of a string by using the syntax LEN. For example: LEN(Name) This Python code would return the answer ‘g’, as this letter is in the third position of the string ‘Greg’. Character position Another feature of string handling is determining the content of a character position in a string. For example, we may wish the coding to look up the character at position in the string: Name[3] This Python code would return the answer ‘g’, as this letter is in the third position of the string ‘Greg’. The reason ‘g’ is returned and not ‘e’ is because here the first character is in position []. However, in some programming languages the first character of a string is denoted by position []. Substring WB LINK Consolidate your understanding by completing Exercise 7, page 104 in the Workbook. Another form of string handling is asking a program to look up a substring, or a set of characters from within a string. Name = “Greg” OUTPUT substring(1, 2, name) This Python code routine would return the characters ‘re’ from this code. The routine instructs the program to create a substring from the variable ‘name’, starting at character position (‘r’) and ending at character position (‘e’). Programming SB CS PP.indb 117 117 14.5.21. 14:15 Chapter 8 Upper and lower QUICK CHECK Why does position [3] in the example output the letter ‘g’? This form of string handling turns all the lowercase letters in a string into uppercase (upper) or all the uppercase letters in a string into lowercase (lower), and then returns it. For example: Name = “Greg” Print(Name.UPPER()) This Python code would return the output of GREG, as the ‘reg’ part of the string has been converted to uppercase. Name = “Greg” PRINT(name.LOWER()) ENRICHMENT Can you think why it would be useful to output a portion of a string? REFLECT Many popular games use this coding feature to personalise a game. A user is asked to enter their name, and it then appears throughout the gameplay. This Python code would return the output of greg, as the ‘G’ part of the string has been converted to lowercase. ... Arithmetic, Logical and Boolean Operators An important feature of programming is the ability to carry out mathematical operations. The tables below show the different types of operations that can be carried out within programming languages and some example syntax. Arithmetic Operators These operators are used to carry out arithmetic calculations. Operator Purpose Syntax + Carrying out an addition Lives = Lives + 1 − Carrying out a subtraction Lives = Lives - 1 * Carrying out a multiplication Lives = Lives * 2 HELPFUL NOTES / Carrying out a real division Lives = Lives / 2 Many of these operations are identical to mathematics. ^ Raised to the power of MOD DIV Lives = Lives^2 Finding a remainder from the division of two numbers Lives = Lives MOD 3 Carrying out an integer division Lives = Lives DIV 3 The difference between a real division and an integer division is that an integer division can only be carried out where the two pieces of data being divided are both integers. Where one of the pieces of data is not an integer, and instead may be a floating-point piece of data, a real division should be programmed instead. Logical Operators These operators are used to carry out comparisons and are often found in iterations. 118 SB CS PP.indb 118 Programming 14.5.21. 14:15 Chapter 8 Operator Purpose Syntax = Assigning a value to a variable (assignment) Lives = 10 < Less than IF Lives < 10 <= Less than or equal to IF Lives <= 10 > Greater than IF Lives > 10 >= Greater than or equal to IF Lives >= 10 <> Does not equal IF Lives <> 10 Boolean Operators These operators are used to help a program make more complex decisions. Operator Purpose Syntax LINK If something and something else are true or false IF Lives > 5 AND Health >=10 OR If something or something else is true or false IF Lives > 5 OR Health > 10 NOT If something is NOT true or false WHILE NOT Lives AND Chapter 10. .. Nested Statements We have already learned about the programming constructs of selection and iteration. Sometimes it is necessary to execute one IF statement, followed by another, followed by another. This would form a subroutine, whereby the results of the first selection would execute the inner selection, which in turn would execute the innermost selection. The same would happen with an iterative process, whereby the results of the first loop would execute the inner loop, which in turn would execute the innermost loop. We refer to this type of iteration as nesting, and both selection and iteration is capable of these constructs. Nested Selection This type of programming usually involves several decision points within a process. For example, if Film A was rated at , and Film B was rated at , some Python code could be written for making a decision on whether someone could view one of the films. Age = int(input(“What is your age? “) IF Age >= 12 THEN OUTPUT(“You are able to watch Film A”) ELSE IF Age >= 15 THEN OUTPUT(“You are able to watch Film B”) ELSE OUTPUT(“You cannot watch any of the films”) ENDIF ENDIF Programming SB CS PP.indb 119 119 14.5.21. 14:15 Chapter 8 Nested Iteration In the same way as a selection can be nested, a loop can be nested inside another loop. In this example, the inner (nested) loop would output ‘ to ’ four times because of the iterations specified in the outer loop. FOR Lives = 1 to 4 FOR Health = 1 to 5 PRINT(Health) NEXT Health NEXT Lives You would need to be able to create nests of up to three levels of statements in your programming, either as nested selection or nested iteration. .. Procedures, Functions and Parameters ENRICHMENT Can you think of a procedure or a function that could be used regularly? Hint: think of formulaes in mathematics. Within a computer program there are different sections of coding that do different jobs. Some of these sections are procedures, and others are functions. These can be run at set times within the programming. Often, procedures and functions are run several times within a program, and so they tend to be pre-stored within a programming language ready to be called when required. This saves time as the programmer does not have to type out common functions and procedures repeatedly. Programming languages come with functions and procedures that are pre-defined. However, programmers will often write their own functions and procedures that are relevant to the program. A function can be called by a procedure, but a procedure cannot be called by a function. Worked Example A procedure If a program needs to create several equilateral triangles of the same size, the algorithm to create one triangle might look something like this: Repeat times Draw a line length QUICK CHECK What is the difference between a procedure and a function? Turn right degrees This procedure could then be named triangle and at any point the programmer could run or ‘call’ the triangle procedure to run this code. A function If a program was required to find the perimeter of a triangle, the Python code might look like this: Perimeter_Triangle = (Line * 3) RETURN Perimeter_Triangle This function would be able to be used at any point to return a perimeter of a triangle where the line length variable had been previously defined. This calculation would be stored as Perimeter_Calculate, and this could then be returned and used in the program whenever needed. WORD ALERT Function: a block of organised, reusable code used to perform a single, related action. 120 SB CS PP.indb 120 To carry out processes, a function or procedure sometimes requires additional information or instructions from the programmer. These instructions are called parameters and are the names of information required. Programming 14.5.21. 14:15 Chapter 8 Our triangle procedure in the worked example had a preset line. This could easily be swapped for a variable instead, which for example could be called Linelength. This parameter could then be inserted into the procedure, and a line length could be added to the calling of the procedure instead of the length being hard coded into the procedure. This makes for more efficient coding: Triangle(100) This line, with a parameter built into the triangle procedure, would then draw a triangle with sides of length . The number is called the argument; procedures and functions can have multiple arguments, separated by commas, as long as there are parameters built into the code that are waiting to accept those arguments. REFLECT There are also differences in the variables that can be used by functions and procedures: • A global variable is declared outside of functions and procedures and can be used within any function or procedure in the program. • A local variable is declared inside a function or procedure and can only be used by the function or procedure that it is contained within. .. Library Routines Library routines are small blocks of pre-written code that are stored within the library (a type of database) of a programming language. These are perfectly programmed routines that can be called upon at any time with no pre-programming required and are designed to handle some of the most common problems when writing any software. Here are some common library routines: What parameters might you be able to attach to a procedure that draws a circle? WB LINK Consolidate your understanding by completing Exercise 4, page 95 in the Workbook. • MOD: Short for modulo, this routine is used for finding a remainder from a division. • DIV: Short for division, this routine is used for carrying out a division of two integers. • ROUND: This function returns the output of the nearest integer to a floating-point number that is passed to it. • RANDOM: This function returns a randomly selected integer from a given range of integers. .. A Maintainable Program It is important for programmers to create tidy, well-explained and efficient code. It is highly likely that at various points in the coding process the code that has been written will be passed on to another programmer to work on, complete or test. If the coding is messy, inefficient or lacks sufficient explanation, this can make the process of handing over very difficult or even impossible. Meaningful Identifiers It is very important that the variable names used within code are related to the data contained inside that variable. For example, the variable name ‘item’ does not describe what that variable contains or is used for. The same goes for constants, arrays and procedures – all identifiers should be easily recognisable by programmers to ensure the code can be easily read. Commenting Adding commentary to lines of code is a feature in all programming environments. These are lines of description that are added next to actual code. Comments are not executed by the program and are separated from the coding using a special symbol. These symbols are different depending on the language being used. Commentary can show what a programmer or developer was thinking at the time of writing a particular line or set of lines of code, and any programmer working in a team would be able to access other people’s coding much more easily. Programming SB CS PP.indb 121 ENRICHMENT Look for some other common library routines in the programming language that you use. HELPFUL NOTES Line numbers in programming are vital. You can use them to quickly identify errors in coding. REFLECT Think about your own programming. Would your comments be able to be understood by someone who had no knowledge of your program? 121 14.5.21. 14:15 Chapter 8 Procedures and Functions Many common procedures and functions that are stored in the library (see .. Library Routines) have set names that are common across most high-level programming languages. When a programmer is writing their own procedures and functions, it is important that the names they give are not likely to cross over with anything else, as this would cause an error in the programming. For example, if writing a procedure to draw a circle, the procedure could not be called Round because this is already in use within the library. A better name would be Circle as this would not ordinarily be used by another function or procedure. LINK WB Consolidate your understanding by completing Exercise 8, page 106 in the Workbook. . Arrays In .. we learned that variables are memory locations that can store a piece of data. An array is a series of these memory locations, where all of the data that is stored are related in some way – the same data type. Each location can still only store one piece of data, but locations can be grouped together. In Python, arrays are created using the LIST functionality. Worked Example A program may be required to store five colours. The code could be written like this: Colour_0 Colour_1 Colour_2 Colour_3 Colour_4 While this would work for storing the five colours, an easier way to store the data is in an array: Colour(4) REFLECT Imagine a table like this, called colours: What is the difference between a one- and two-dimensional array? Colours Red Green Blue Purple Orange The number in brackets defines the index and determines how many pieces of data can be stored in the array – in this example, the number would allow five items to be stored. As we learned in Section ..., computers begin counting at the number , however some languages do begin counting at number . 122 SB CS PP.indb 122 Programming 14.5.21. 14:15 Chapter 8 Arrays can be both one- and two-dimensional. The colours example above is a one-dimensional array: one row and multiple columns. A two-dimensional array has multiple columns and multiple rows of data, all with the same data type – this looks a bit like a grid. One example of a twodimensional array is where a program needs to map out a game world of a fixed size, with each square of the game world containing data to define the type of land in a square. World [20][20] The code above would allow a programmer to define a flat world in a game that is squares wide by squares in length using a two-dimensional array. More complicated game environments use three-dimensional arrays. ENRICHMENT Think of a game where the world appears to be three-dimensional. Try to imagine the size of array that exists to code just the world without any characters in it. Data can be read from and written into arrays depending on the functionality of the programming. If the program was required to read the third value from the colours array in our example above, the following code could be used: Colours[2] This would give an output of Blue, the third colour in the array. It is also possible to change or write to an array, for example in the code below, which would change the data in array position from green to pink. Colours[1]=”Pink” It is also possible to create, write to and read from arrays using iteration. Creating an array using this method could be done using a nested FOR loop: World= [[0 FOR x IN range (5)] FOR y IN range (5)] This code would create a two-dimensional × array. REFLECT Can you think of a scenario in a game where data in an array might need to be changed by a program? The array could then have data written into each position, which is similar to grid references on a map: World[0][0] = ‘Red’ World[0][1] = ‘Blue’ World[0][2] = ‘Orange’ World[0][3] = ‘Orange’ World[1][0] = ‘Green’ [0] [1] [2] [3] [0] Red Blue Orange Orange [1] Green [4] WB Consolidate your understanding by completing Exercises 1 and 2, pages 107-110 in the Workbook. [2] [3] [4] Programming SB CS PP.indb 123 LINK 123 14.5.21. 14:15 Chapter 8 . File Handling HELPFUL NOTES Files that are handled by programming languages tend to be text files, such as those viewable in a program like Notepad. We have seen that programming involves the input of a lot of data, whether as variables and constants or output of results of operations. It is therefore often important to store program data in external files so that it is not lost when a program has finished running. Programming can often take weeks and months to create, and to be constantly restoring data to code would be hugely time-consuming. To enable greater efficiency, programming languages have the ability to handle external files of data. The files can be both read from and written to. When reading from a file, a program can be instructed to open it, read from it and close it again. When writing to a file, a program can be instructed to open it, write data to it, save it and close it. .. Reading from a File When reading from a file, a program will read records one line at a time. Data held in a file can be read into a variable or into an array. Here is an example of Python code for reading a single line from a file called colours.txt that has only got one line of information: FILE = openRead(“colours.txt”) Colour = myFile.readLine() FILE.CLOSE() This Python code would open the colours.txt file, read the contents of the file into a variable, create a single record from this data and then close the file. If a file has multiple lines of data, this would have to be read into an array and would create multiple records. .. Writing to a File A program can also be set up to write the contents of a variable or an array to a file – the reverse of the reading operation. Data is written into a file one line at a time. An example of this is shown in the Python code below, where the contents of the colours array can be stored in a file called colours.txt. LINK WB Consolidate your understanding by completing Exercise 1, page 111 in the Workbook. FILE = openWrite(“colours.txt”) FOR x = 0 TO 5 file.writeLine(colours[x]) next x FILE.CLOSE() This Python code would write the data stored in the colours array to the colours.txt file line by line. 124 SB CS PP.indb 124 Programming 14.5.21. 14:15 Chapter 8 Let’s Map It Sequence Logical order Selection Constants If something is true THEN do this ELSE do that Don’t change Iteration Variables Looping until something happens Can be changed INPUT PROGRAMMING OUTPUT Procedures and Functions Data types Integer 0, 1, 2, 3 Real 1.3, 2.6, 3.7 Char £, $, ¥ String hello Boolean True/False Pre-named and Pre-defined LIBRARY Files Arithmetic Arrays + - * / = >< Tables of data Boolean AND OR NOT Read from Write to Programming SB CS PP.indb 125 125 14.5.21. 14:15 Chapter 8 Let’s Review 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 What is a variable? Name two data types used in programming. Explain what the programming construct of sequence means. CASE statements are one form of selection – name another. Name the three types of iteration loops. What is the purpose of counting in programming? When handling strings, name two ways in which they can be changed. Addition and multiplication are two arithmetic operators. Give another three. What is the meaning of the logical operator <>? Boolean operators are used for complex decisions. Explain the three common operators, AND, OR, NOT. What does it mean to use a nested statement? What is a parameter? What is the difference between a local and a global variable? Name two library routines in a programming language. Why is it important to use meaningful names to identify variables and constants? What is the commenting feature of a programming environment? What type of item is stored in an array? True or false: data can only be read from an array. Why do programming languages use external files for data storage? True or false: a program reads all of the lines from a file in one go. 126 SB CS PP.indb 126 Programming 14.5.21. 14:15 CHAPTER 9 Databases COMPUTER SCIENCE WATCH Scan the page to watch a clip on database management systems. Before watching discuss what you expect to see or hear. QUESTIONS At the end of this chapter, you will be able to: understand what is meant by a database, including features such as tables, fields and records • How are records maintained in organisations like your school or any other place? • Ask your elders and understand the different methods of record keeping in earlier times. be able to suggest suitable basic data types for fields identify the purpose of a primary key in a database understand structured query language (SQL) and how to use it to create queries 127 SB CS PP.indb 127 14.5.21. 14:15 Chapter 9 QUICK CHECK What is the difference between data and information? . Understanding Databases Let us first understand what data is. Data can be anything that can be stored on a computer, like numbers, letters, characters, images and so on. Have you seen the computer-generated bills from a supermarket, or a shop (Figure .)? What information do you get from the bill? Had there been no mention about the item ID or name, would it be easy to understand the purchases made? When the data is presented in a meaningful way, what you get is information. A database is an organised collection of data. In a database, you can organise data in a table format. It also allows the user to work on data in the following ways (Figure .). Ad or remove data HELPFUL NOTES Microsoft Access is one of the most popular tools for working on databases. Since it comes along with the Microsoft Office Suite, the interface is very similar to other Microsoft applications. Figure . A sample shopping bill. Database Manipulate or change data Access or analyse data Avoid data duplication Maintain data accuracy and consistency Share data Store data Figure . Uses of a database. REFLECT Can you think of more places where a large amount of data is stored using a database? Databases are used in different places to store and manage information about almost everything. Some common applications of databases are: Student and examination records at schools and universities Book records at libraries or book stores Patient records at hospitals (Figure .) Customer records at banks ENRICHMENT Find out how a country’s population data is stored. 128 SB CS PP.indb 128 Booking and reservation records at railways and airports Employee records at offices Online registration records for websites and social media Figure . Accessing medical records. Databases 14.5.21. 14:15 Chapter 9 .. Important Terms related to Databases Table: In a database, data is entered in a tabular format, that is, organised as rows and columns to provide meaningful information. This structured entry of data helps the user to access and manage the information easily. A column in a database table is referred to as a field. A field is like a title given to every single piece of data. Each row is called a record, which is a collection of fields in the table for a specific person, item or any other entity. Let us look at an example of a database table showing records of students appearing for their final examination. Here the field names are given by Student ID, First Name, Second Name, Date of Birth, Contact number. A column or a field WORD ALERT Entity: object or thing. QUICK CHECK What is a field? A row or a record Figure . Student record table. Query: Sometimes you need to work with a very large database. In such cases, it may be difficult to find specific data required by the user. A query allows the user to find full records or records with specific fields in a database using certain criteria. For example, in the student record database (Figure .), you can run a query to find the information of students from roll numbers to . You will learn more about how to use a query for practical purposes later in this chapter. WORD ALERT Criteria: conditions or questions. Data types: A field in a database table can have its own attribute or property. For example, you can enter data as text, number, date/time, currency and so on. These attributes are defined as data types. A data type helps the computer to identify similar data for the purpose of sorting, searching and calculation. Mostly data types may be defined differently in various database systems. Some common data types are as given in Table .. Table . Some common data types. Data type Text/Alphanumeric Character/Char Integer Number/Numeric Real Attribute description Example of field name Sample data Used for data which is text or number or a combination of both. Student name, phone number, address David, Used for defining data with a fixed-length string that may contain letters, numbers and/or special characters. Name, address, title Mr, Used for data which is a whole number. Roll number, ID, number of items Manisha WORD ALERT String: a set of characters that can also contain spaces and numbers. Mrs, Miss , Used for numbers greater Height, weight, score than zero and may require calculations. It can also have a value in decimals or percentages. ., Used for data in a computer program which are decimal numbers. ., . Weight, height, temperature ., .% Databases SB CS PP.indb 129 129 14.5.21. 14:15 Chapter 9 Data type Attribute description Example of field name Sample data Date/Time Used for date or time. Different formats of date such as DD/MM/ YY and time such as hours:minutes:seconds can be selected. Schedule, last date, first date, time of action //, Used for data that include currencies of different regions around the world. Item price, cost, tax paid, amount credited £., AutoNumber Used for data which can include randomly generated numbers when a record is added. This field cannot be changed. Registration number, product ID, student roll number Boolean Used for data which has a value of / such as True/ False, Yes/No, On/Off. Answer (true/false), active (yes/no), display (on/off ) Yes, Currency :: $. no, true, false DEFINITION Primary key: A primary key is a unique field that allows the user to identify a record. Foreign key: A foreign key is a field or combination of fields that are related to the primary key of another table. . Types of Databases You can use different software applications like Microsoft Access, Oracle, MySQL, LibreOffice Base to create a database. These applications are also called Database Management System (DBMS) applications as they act as an interface between the user and the database. A database can be of two types — Flat-file (single-table) database and Relational Database (Table .). Different DBMS applications work on any one type or both types of database according to how they are programmed. For example, Microsoft Access can work on both flat-file and relational databases. Thus, Access is also a Relational Database Management System (RDBMS). Table . Types of databases. HELPFUL NOTES A primary key cannot have a duplicate value in a database. Also, this field cannot be left blank. WORD ALERT Data duplication: a process of creating an exact copy of data. Data redundacy: the storing of the same data in multiple locations. 130 SB CS PP.indb 130 . Flat-File Database (singletable database) A flat-file database stores simple data formats. They store only a single table of data. The information given by a record is complete with a fixed number of fields. This database is not related to any other table or database. An example is shown in Figure .a. This method of storing data is not efficient and may lead to problems like data duplication, data redundacy and input errors. . Relational database When a database can have mutiple related tables, it is referred to as a relational database. When the tables are linked, the user can work on complex data structures having multiple tables (Figure .b). For example, in a student database, you can create a Student Information table and a Student Examination table. In the Student Information table, Student ID will be unique for each student record. It thus defines the record of each student. This special field is defined as the Primary key for that table. Now, when you link the Student Information table and Student Examination table, the two tables can have a common field, that is Student IDs. A relational database does not allow data duplication. Also, it is more effiecient and consistent than a flat-file database. Databases 14.5.21. 14:15 Chapter 9 WB (a) Flat-file or single-table database Consolidate your understanding by completing Exercise 1, page 115 in the Workbook. (b) Relational database Figure . Example of databases. Activity 1 2 LINK An organisation keeps a record of its employees in separate tables like Employee Joining Details, Employee Payroll Record, etc. Suggest a common link which can help to retrieve all the records of a particular employee. Which type of database must be created? Fill in the blanks. a) A database is an organised collection of __________. b) A flat-file database is also referred to as __________. c) A ________ key is a unique field that allows the user to identify a record. d) The full form of DBMS is __________________________________. . Creating a Database .. Creating a New Database with the Given Information Let us look at the given information. In an inter-school annual sports meet, registration forms were collected with the following information. You are asked to enter the information from the forms into the student database. Given below is the information collected from different schools. • • • • • • • • Registration Number School Name Student ID Student Name Age Gender Contact Sport Selected HELPFUL NOTES If the application is open then you can create a new file using the File tab in the open document. You can create a table using any database application. Here, you will be looking at Access . To create a database in Access, follow these steps. Step 1: Open the Access application. Step 2. In the Backstage view click on the Blank database option (Figure .). Step 3. A dialogue box opens (Figure .) Type the name of the database as Annual Sports Meet. Step 4. Click Create. Access window will open. Databases SB CS PP.indb 131 To create a new database file, you can either select the Blank database option or a built-in template. 131 14.5.21. 14:15 Chapter 9 Figure . Backstage view of Access 2016. Figure . Creating a new database file. .. Creating a Table Access has two views to work with data: Design View and Datasheet View. These two views can be toggled with the help of the View option under Home tab (Figure .). Figure . View option. Although both the views allow the user to create and define the table structure, the Design View is easier to work with. 132 SB CS PP.indb 132 Databases 14.5.21. 14:15 Chapter 9 When you switch to the Design View, you will be prompted to save the table. Enter the table name as Student Participation Table and click OK (Figure .). Figure . Saving a table. The Access window will show the Design View. Now, you can add the Field names for a record, define its data-type and mention the Field Properties. You can also set the Validation Rules from the Properties pane (Figure .). Figure . Entering table fields and defining data types in Design View. By default, the first field is marked as a primary key (shown by a key icon). You can change the primary key by right-clicking on the desired Field name and selecting the Primary key option or just select the Field and click on the Primary key option under the Design tab. .. Data Validation You have learned that data can be a name, date of birth, address, currency, date/time, and so on. There are certain rules that are followed when data is typed into a database system called the data validation rules. For example, a phone number does not contain a character or an alphabet. These rules help in accepting the data which are as per the set format. The data entered into a database can sometimes be entered incorrectly. It can be invalid, inconsistent or incomplete. To avoid any such issue, the user may apply different validation checks. Some of these are given in Table .. Databases SB CS PP.indb 133 DEFINITION Data validation rules: these are some rules which help the user to know that the data being entered in a database is correct. 133 14.5.21. 14:15 Chapter 9 Table . Types of data validation checks. Validation technique Purpose Example Presence check To check the missing data in the field. The system does not move further if this data is not filled. A primary key in a database is mandatory. Range check To check if data is within the set range. Days of a week must be between and . Length check To check the desired length of data characters is met or not. If the format of time is hrs:min:sec, the system will require digits to be entered, anything less than digits will not be considered valid. Format check To check if data is in the desired format. The date format followed in a form can be mm/dd/yyyy. Consistency check To check that data is consistent as per any previous entry. The date of expiry of an item cannot be before the manufacturing date. Type check To check the data type. A phone number field cannot allow characters. You can add a validation rule to a field using the Field Properties Pane (Figure .). Once the data is entered, a validation check can also be performed. To do so, select the Design View Design tab Click on Test Validation Rules. Figure . Creating validation rule for Student Participation Table. .. Entering Data in a Table When a form is designed, save the table and switch to the Datasheet view to enter the data values (Figure .). Figure . Annual sports meet database. 134 SB CS PP.indb 134 Databases 14.5.21. 14:15 Chapter 9 . Using Queries HELPFUL NOTES Queries are used for working with data in a database. You can search data by certain criteria such as “searching the records in which the students have participated before”. You will get the matching records in the database. You can create queries by choosing one or more search criteria. Structured Query Language (SQL) is mainly used for creating and running a query in order to search, sort or manipulate data. However, some DBMS systems like Access also allow the user to create a query using a Graphical User Interface (GUI). This is sometimes referred to as query-by-example. .. Using Query-by-Example WB Using the Student Participation Table created earlier, let us create and run a query to search the records of all students playing the sport ‘Baseball’. To do so, follow the steps given. Step 1. Open the database - Annual Sports Meet. Step 2. Click on Create tab Query Design option. Step 3. A new tab opens in the Access window called Query 1. Step 4. Select the table name from the pop-up window and click on Add. Click Close to close the pop-up window. Step 5. A list of all fields in the table appears in the top pane of the Query 1 window. You can create a query and set a criterion or multiple criteria to search the database by filling up the options in the lower pane of the Query 1 window (Figure .). Step 6. Run the query by clicking on the Run option in the Design tab. The required data will appear (Figure .). LINK Consolidate your understanding by completing Exercise 2, page 116 in the Workbook. Figure . Creating a query. Databases SB CS PP.indb 135 135 14.5.21. 14:15 Chapter 9 Figure . Results of a query. .. Using SQL Programming SQL is mainly used for relational databases. It contains statements which are used to retrieve or modify data from the database. Access also allows you to use SQL to create queries. Let us again take the example of the Annual sports meet database. To create a query using SQL, follow the given steps. Step 1. Open the Query 1 tab Once this tab is opened you will notice one more view in the View tab called SQL view (Figure .). Select the SQL view. The Query 1 window will change to the programming environment for SQL. Step 2. Type the SQL queries and Select Run from the Design tab. Creating the SQL query to retrieve data from the database The syntax used for Data Query Language is: SELECT [Field Name] FROM [Table Name]; Now, let us understand the application using Student Participation Table. . Using * for the field name This will retrieve all properties (fields) of a table Example SELECT * FROM [Student Participation Table]; Figure . View tab with SQL View option. HELPFUL NOTES Some more operators you can use with WHERE clause < Less than > Greater than = Equal to != Not equal to <= Less than and equal to >= Greater than and equal to BETWEEN Within a defined range of data 136 SB CS PP.indb 136 Figure . Output for SQL query using. Output: You will get the complete table information including all Field names. . Using WHERE clause WHERE clause is added to specify a condition. When this clause is added to a SQL query you will get only those records for which the condition is true. Example Figure . Output for SQL query using WHERE clause. SELECT [Registration Number], [Student ID], [Student First Name] FROM [Student Participation Table] WHERE Age<=; Databases 14.5.21. 14:15 Chapter 9 . Using ORDER BY clause ORDER BY clause is used along with the SELECT statement to retrieve information in ascending order. In case you require information to be arranged in descending order, DESC is used along with the ORDER BY clause. Syntax For Ascending order (Output Figure .) SELECT [Registration Number], [Student ID], [Age] FROM [Student Participation Table] ORDER BY Age; Figure . Output for ORDER BY ascending order. For descending order (Output Figure .) SELECT [Registration Number], [Student ID], [Age] FROM [Student Participation Table] ORDER BY Age DESC; You will also learn about two more functions, COUNT and SUM. These are aggregate functions which are used for performing mathematical operations – counting and addition, respectively on the data values of a given field. COUNT function – It is used for counting the number of rows in a field. You can add a condition using WHERE clause. Figure . Output for ORDER BY in descending order. Example SELECT COUNT (Age) FROM [Student Participation Table] WHERE Age = ; Output is shown in Figure .. SUM function – It is used for adding the values in a given field. Figure . Output using COUNT function. You can use the SUM function to add the values in the field, Reg_Amount (Figure .) using the SQL query. Figure . Reg_Amount field of Student Participation Table. SELECT SUM (Reg_Amount) FROM [Student Participation Table]; Output is shown in Figure .. Figure . Output using SUM function. Databases SB CS PP.indb 137 137 14.5.21. 14:15 Chapter 9 Activity Answer the following. Name any DBMS application that allows creating a query using Query-by-example and SQL, or both. The full form of SQL is _________. Which SQL function allows you to arrange data in ascending order? Write the syntax for a WHERE clause. 138 SB CS PP.indb 138 Databases 14.5.21. 14:15 Chapter 9 Let’s Map It Applications of a database • Storing/sharing data • Accessing data • Manipulating data • Adding/Removing data • Avoiding data duplications • Maintaining data accuracy/ consistency Understanding databases • Important terms related to databases • Table • Query • Field • Record • Data types • Primary key Datatypes • Text/Alphanumeric • Character/Char • Integer • Numeric • Real Types of databases • Flat-file database • Relational database • Date/Time • Currency • Autonumber • Boolean DATABASES Creating a database • Creating a new database with the given information • Creating a table • Data validation • Entering data in a table SQL commands: • SELECT Using queries • Using Query-by-example • Using SQL programming • FROM • WHERE • ORDER BY • SUM • COUNT Databases SB CS PP.indb 139 139 14.5.21. 14:15 Chapter 9 Let’s Review Define a database. Explain the difference between flat-file and relational database. Name some statements that can be used to retrieve data using SQL queries. Define data types. State three data types. Assuming you need to plan a health camp for your school, create a sample student database assuming students between age group – will participate. Explain validation. Why is it required? Give the names of any two types of validation checks. In a hospital a patient database is to be created with the given fields Patient First ID Name 140 SB CS PP.indb 140 Second Contact Blood Date of Name Details Group Birth Age Doctor Consulted Date of Visit Fee Paid Assuming you have to maintain the patient database, create a database with at least ten records and define the following. a) Primary key b) Data type for each field In the above table create SQL queries for: a) Selecting the patients who consulted a specific doctor b) Getting a total sum of fee paid c) Arranging the records in ascending order of Age Databases 14.5.21. 14:15 CHAPTER 10 Logic Gates and Circuits QUESTIONS • How could logic gates be used in everyday life? At the end of this chapter, you will be able to: understand the different symbols that are used for logic gates understand the function of a range of different logic gates • How are logic gates and micro controllers used in all computer systems such as games consoles? • What are digital circuits in computer systems and how do they use binary values 1s and 0s? use logic gates to create a logic circuit complete a truth table write a logic expression 141 SB CS PP.indb 141 14.5.21. 14:15 Chapter 10 DEFINITION Logic gates: the basic units of a digit circuit that control the flow of electronic signals. . Logic Gates Logic gates are the basic building units of any digital circuit. Today, these circuits are used in almost every computer system. From elevators to washing machines, logic gates are used all around you. Digital circuit used to open electronic door. WORD ALERT This chapter will explore the types and functions of common logic gates. Combination: a joining of different parts or qualities. There are a number of different types of logic gate, with different logic rules. The combination of several logic gates forms a circuit, which allows for the design and performance in modern computers. The gates receive binary data, apply a Boolean operation and then output a binary result. Arithmetic: use of numbers to calculate an outcome. Boolean Operations Equivalent: the same or equal meaning. HELPFUL NOTES Be careful not to confuse the Boolean operator ‘+’ with ‘+’ , which means ‘plus’ in normal maths. The word ‘Boolean’ comes from Boolean algebra, which is the basis of computer arithmetic and especially logic gates. There are only two Boolean values: true and false. They have equivalents in normal language and in binary notation. Boolean expressions can compare data of any type as long as both parts of the expression have the same data. In computer science, Boolean expressions can be used in programming and produce Boolean values when evaluated. Boolean values are either true or false: Boolean value Binary value Synonyms True On Yes Positive False Off No Negative There are also three logical operators: NOT, AND and OR. The Boolean operators for these are AND ‘•’, OR ‘+’, and NOT ‘ ’, which is written above the letter. Ā means NOT A. A • B means A AND B. A + B means A OR B. Logic gates use both Boolean values and operators. 142 SB CS PP.indb 142 Logic Gates and Circuits 14.5.21. 14:15 Chapter 10 Worked Example We use Boolean logic all the time. Look at this situation using Boolean operators: You have decided that you will do extra study if you are falling behind at school. You also decide that you will do extra study even when you are not behind if your friend asks you to study together. Express this using Boolean operators. Solution To express this formally and logically we need two pieces of information to make our decision and another piece to represent the result of the decision. We can name our information like this: WORD ALERT Formally: officially / explicitly. Information needed to make decision (behind at school) = TRUE if fall behind. If not, FALSE. (friend asks you to study) = TRUE if friend asks you to study. If not, FALSE. Result (do extra study) = TRUE if we decide to do extra study. If not, FALSE. Our logical expression is then: (do extra study) = (behind at school) OR (NOT (behind at school)) AND (friend asks you to study) This expression uses the three Boolean operators: NOT, AND, OR. Activity 1 2 Write a logical expression like the example above for this given scenario. There are two methods of getting to your part time job on time. You can get the bus but only if you wake up before .am. If you wake up after this time, you will need to ask your parents to take you in the car. If you wake up before .am but your parents offer to take you, then you will always say yes as it is easier. Draw the Boolean algebra symbols for the following: a) A NOT B b) A AND B c) A OR B HELPFUL NOTES Types of Logic Gate There are three basic types of logic gate that will be examined in this chapter: NOT, AND and OR. NOT AND OR WORD ALERT The left side of the logic gate is referred to as the input and the right side as the output. We can use a truth table to show the function of the logic gate. Each of the logic gates has a different truth table. These truth tables display all possible input combinations and the correct output. Logic Gates and Circuits SB CS PP.indb 143 In all logic gates except the NOT gate, there are two inputs. The inputs or outputs have two possible states: a value of 1 or a value of 0. Referred: denoted / identified. 143 14.5.21. 14:15 Chapter 10 NOT Gate A DEFINITION Truth tables: used to represent the Boolean expression of a logic gate or logic circuit. X The NOT gate takes a single input, A in the diagram above, and always produces the opposite of that input in a single output, X. Here is the truth table for the NOT gate above. It displays all possible combinations of inputs and the corresponding outputs for the NOT gate. There are only two possible outputs for a NOT gate: and . Input Output A X Besides constructing truth tables, we can describe each gate using logic notation and Boolean algebra. In this case the output is as follows: Logic notation: X = NOT A Boolean algebra: X = Ā ENRICHMENT The total number of possible combinations can be obtained from the formula C = 2n, where C is the number of total possible combinations and n is the number of inputs. AND Gate A X B The AND gate takes the inputs A and B and produces the output, X. If both inputs are , then the output will be , but otherwise the output will be . Here is the truth table for the AND gate above. For example, if there are three inputs, A, B and C, the total possible combination of inputs is C = 23 = 8. Inputs Output A B X Logic notation: X = A AND B Boolean algebra: X = A·B A and B show all possible combinations of inputs, so there are a total of four possible output states. OR Gate A B X The OR gate takes two inputs, A and B, and produces output X. If either or both inputs is , the output will be . 144 SB CS PP.indb 144 Logic Gates and Circuits 14.5.21. 14:15 Chapter 10 Here is the truth table for the OR gate above: Inputs A REFLECT Output B If someone asks you, ‘Do you want a soda or some water?’, you can’t answer ‘Both, please’. If you could have both that would be an inclusive use of OR. Is the OR gate inclusive or exclusive? X Logic notation: X = A OR B Boolean algebra: X = A + B Out of the four possible output states, the only time output X will be is when both the inputs A and B are . An inclusive OR is what is shown in the truth table if either A or B is True, or if both are True, then the statement value is True. An exclusive OR only returns True when A OR B is True only. Worked Example A security light outside a house comes on after .pm or if it is dark. Make a table showing the operation in normal language with corresponding Boolean and binary values. Make the resulting truth table and choose the logic gate that will make this happen. Solution We have to state the conditions under which the light will come on: if it is after .pm if it is dark WORD ALERT Condition: the state of something in relation to its appearance, quality or working order. Then we convert these into the Boolean values ‘True’ and ‘False’: it is after .pm = Yes/True/Positive if it is dark = Yes/True/Positive QUICK CHECK Next we add the binary values: it is after .pm it is dark Yes Yes True True Positive Positive In all logic gates except the NOT gate, there are two inputs. The inputs or outputs have two possible states. What are they? Logic Gates and Circuits 145 Then we make the truth table. The inputs are ‘it is after .pm and ‘it is dark’: Inputs it is after .pm it is dark The light coming on is the output: Inputs it is after .pm Output it is dark the light comes on Remember that the light will come on if either of the conditions is true: Inputs it is after .pm No No Yes Yes SB CS PP.indb 145 Output it is dark No Yes No Yes the light comes on No Yes Yes Yes 14.5.21. 14:15 Chapter 10 Finally, we can replace the normal language with binary and the inputs and output with letters: Inputs Output A B X This is the truth table for the OR gate. Activity 1 2 Now do the same for these situations. You can skip some steps if you don't need them. • To save electricity and be ecological, an ‘up’ escalator will start moving when a pedestrian steps near the bottom and breaks a sensor beam. Tip: there is only one input. • A car park barrier will rise when a car approaches and the driver puts the ticket they have paid for in a slot. Name the logic gates represented by these truth tables: a Input Output A X b QUICK CHECK Write the Boolean algebra expression for NOT, AND, OR gates. HELPFUL NOTES These three additional logic gates look very similar to 'AND', 'OR', 'NOT' with some slight changes. Knowing the appearance of the basic gates will make remembering them easier. Inputs Output A B X c Inputs Output A B X Additional Logic Gates In addition to the three logic gates shown above, there are also different versions of them: NAND, NOR and XOR. NAND NOR XOR Figure . NAND, NOR and XOR logic gate symbols 146 SB CS PP.indb 146 Logic Gates and Circuits 14.5.21. 14:15 Chapter 10 The NAND Logic Gate A X B You can see that the NAND gate has a small circle after an AND gate symbol. This means that it is like an AND gate plus a NOT gate. The NAND gate functions like an AND gate but with the opposite output. The NAND gate takes the input A and B and gives output, X. It will only give an output of if both inputs A and B are . Here is the truth table for the NAND gate above: Inputs Output A B X Logic notation: X = A NAND B Boolean algebra: X = A·B This means that the output X is always , unless both inputs A and B are and then the output X is . The NOR Logic Gate A X B Like the NAND gate, you can see that the NOR gate has a small circle after an OR gate symbol. This means that it is like an OR gate plus a NOT gate. The NOR gate takes the input A and B and produces an output of if both inputs A and B are . Here is the truth table for the NOR gate above. Inputs Output A B X Logic notation: X = A NOR B Boolean algebra: X = A+B The output X is always , unless both inputs A and B are and then the output X is . Logic Gates and Circuits SB CS PP.indb 147 147 14.5.21. 14:15 Chapter 10 The XOR Gate A X B The XOR gate (which means ‘exclusive OR gate’) is similar to the OR gate, except that if both inputs are then the output is . The XOR gate has a different logic outcome to the OR gate: the output X is when either (but not both) of the A or B inputs is . Here is the truth table for the XOR gate above: HELPFUL NOTES In Boolean algebra, the symbol for ‘exclusive OR’ is a ‘+’ inside a circle: ENRICHMENT You have now looked at six logic gates. There are actually seven – can you find the other one? Inputs Output A B X Logic notation: X = A XOR B Boolean algebra: X = A B or X = (A·B)+(A·B) This also means that the output is when both inputs A and B are or . Worked Example Two people are walking towards each other along a corridor wide enough for two people to pass. On one side of the corridor there are windows and on the other there is a blank wall. Find the gate that describes the conditions where they can pass without bumping into each other. QUICK CHECK Draw the logic gates for NAND, NOR, XOR. Solution The inputs are: Person = A Person = B And the values are: Near the window = True Not near the windows (near the wall) = False Result If both walk near the wall obviously, they can’t pass. If A walks near the window and B near the blank wall, they can pass. If B walks near the window and A near the blank wall, they can pass. If both walk near the windows, they can’t pass. REFLECT What would happen if we used an inclusive OR gate to describe this situation? Why do we need different symbols for inclusive and exclusive OR? The truth table looks like this: Inputs A Output B X This is the table for the XOR gate. The XOR gate is an exclusive OR gate. If both inputs are true then the output is false. 148 SB CS PP.indb 148 Logic Gates and Circuits 14.5.21. 14:15 Chapter 10 Activity 1 2 Now do the same for this situation. You can skip some steps if you don’t need them. Tip: the circuits are normally on so something needs to happen if they go off. • An alarm makes no warning sound if the door is closed and the window is closed. There are hidden switches on the door and window through which a current is constantly passing. If someone opens the door or window, the alarm sounds. Name the logic gates represented by these truth tables: Inputs a B X Inputs WB Output A B X LINK Consolidate your understanding by completing the Exercises 1-2 from pages 123-129 in the Workbook. Logic Gates and Circuits SB CS PP.indb 149 Write the Boolean algebra expression for NAND, NOR, XOR. Output A b QUICK CHECK 149 14.5.21. 14:16 Chapter 10 . Combining Logic Gates WORD ALERT Complex: more difficult / more components involved. Basic logic gates can be combined together in a certain way to get different outputs. These allow for complex operations to be carried out, for example, controlling a processing unit. The combination of two or more logic gates forms a logic circuit. Just as individual gates have truth tables, logic circuits have their own, more complex, truth tables. Logic Circuits Worked Example REFLECT Examine the truth table for this logic circuit, below. Create your own logic circuits using the AND, OR and NOT gates. B P X A Draw the corresponding truth tables. Input A Intermediate output Output P = A AND B X = NOT (A AND B) B Solution A P X B HELPFUL NOTES When combining logic circuits it is often easier to break them down into smaller sections. Part Part We can see that Part of the circuit is an AND gate. The intermediate output is at P. Part of the circuit is a NOT gate, and therefore X = NOT P. The truth table can then be constructed as follows: Input LINK WB Consolidate your understanding by completing Exercise 2 in the Workbook, page 127. A B Intermediate output Output P = A AND B X = NOT P If we look at only the initial inputs A and B and the final output X, the truth table becomes: Inputs A Output B X This is also known as a NAND gate, which was discussed above. 150 SB CS PP.indb 150 Logic Gates and Circuits 14.5.21. 14:16 Chapter 10 Activity ENRICHMENT Make this logic circuit into a table that shows the intermediate outputs and the final outputs and that has the same function as the NOR gate. A B Gate? P Create revision cards on the rules for each of the six logic gates we have discussed. X Part Part Inputs Intermediate output Output A B P X ? ? ? ? Logic Circuits with More Than Two Inputs A logic circuit with three inputs is known as a two-level logic circuit. The more inputs in the logic circuits, the more possible combinations there are. For example, if there are three inputs and each one can take two values ( or ), then × × = rows will be required. A P B X Q C REFLECT Do you think it is cheaper to use simple logic circuits like this AND gate and NOT gate or to find a single gate that will perform the same function, such as a NAND gate? Break down the logic circuit into sections. 1 Work out P by completing the OR gate: P = A OR B This can then be added to the P column in the truth table below. A P B Logic Gates and Circuits SB CS PP.indb 151 151 14.5.21. 14:16 Chapter 10 2 Work out Q by completing the NOT gate. Q = NOT C HELPFUL NOTES If is often the case that intermediate outputs do not continue as D, E, etc., but begin a new sequence as shown here. This can then be added to the Q column in the truth table below. Input This does not change the logic behind each gate or logic circuit. ENRICHMENT Can you write the output in Boolean algebra? WORD ALERT Q C Intermediate outputs Output A B C P = (A OR B) Q = (NOT C) X = (A OR B) AND (NOT C) Worked Example We already have a fire alarm that sounds in the building when the circuit detects heat and smoke. However, we need a special alarm that will directly alert the fire service if there is no-one in the building. This system uses three inputs to a logic circuit. The alarm X will sound if inputs A (smoke) and C (heat) are both on, and where input B (motion detector) is off. Detects: identifies. Design a logic circuit and make a truth table to show when the fire alarm will sound; i.e. where X = . Solution To show the conditions where X = we must write the logic statements that represent this situation. X= , if (A = AND B = ) AND (C = AND B = ) To explain this a little further: (A = AND B = ) means A is ON and B is OFF (C = AND B = ) means C is ON and B is OFF In Boolean algebra, we can write this as X = (A·B)·(C·B). The logic circuit can be made up of Part (A·B), which is (A = AND B = ) as follows: A B 152 SB CS PP.indb 152 Logic Gates and Circuits 14.5.21. 14:16 Chapter 10 Part (C·B), which is (C = AND B = ): B C If we combine Parts and , we get the circuit below: A B REFLECT C Draw a combined logic gate circuit which includes a NAND gate and create the corresponding completed truth table. To complete the circuit, we combine Parts and with the AND gate: P A R B X C Q The truth table can be constructed as follows: Inputs Intermediate outputs Output A B C R P Q X Logic Gates and Circuits SB CS PP.indb 153 153 14.5.21. 14:16 Chapter 10 Activity Draw a truth table for this logic circuit: P A HELPFUL NOTES Add all possible input combinations into the truth table first. Then decompose each problem into smaller sections to help complete the intermediate outputs. R B X C Q Writing Logic Circuit Statements You will need to be confident in writing and understanding logic statements. This logic circuit is for an AND gate. B X A The AND gate logic circuit statement is written as X = A AND B. You can use these statements to draw the corresponding logic circuits. Logic gates can be combined to make more complicated circuits, such as this one below: Worked Example A P B X Work out the logic statement for this circuit. Solution 154 SB CS PP.indb 154 Start at the final output, X. The X output depends on its inputs. X = NOT P P is an intermediate output, so we have to break it down into a mini problem and put that into brackets. The P output depends on its inputs. P = (A OR B) Now our logic statement only has the final output and the first inputs, so we know it is complete. X = NOT (A OR B) Logic Gates and Circuits 14.5.21. 14:16 Chapter 10 Activity Work out the logic statement for this circuit: A B P X Q C D Figure 7.2 Combined logic circuit with four inputs. f Start at the final output. The output of X depends on its inputs. P is an intermediate output. Break it down and put it in brackets. The P output depends on its inputs. Q is also an intermediate output. Break it down and put it in brackets. The Q output depends on its inputs. Final output and the initial inputs Drawing Combined Logic Circuits using Statements You can draw a logic circuit directly from a logic statement. You may need to go back and revisit the logic gate symbols first. For example, the logic circuit for the statement X = (A OR B) AND C is as follows: A P B C X This is possible by breaking down the statement and working through each stage. X = P AND C f P = (A OR B) X = (A OR B) AND C HELPFUL NOTES When converting a circuit into a statement, always start from the final output and work backwards . Convert each intermediate output into its inputs. When you have only the first input on the left and the final output on the right in your statement, you have completed the table. Remember to check you have the right gates and the correct number of inputs. Worked Example We can also produce a circuit from a statement. For example, a car’s wipers will operate only when the engine is on, the car is moving and the windscreen sensor is sensing rain. There are three input conditions: • the engine is on • the car is moving • the windscreen sensor is sensing rain Solution Let’s call them A, B and C. The output is that the car’s wipers operate. This is X. We have to reduce three inputs to X for the final gate. We do this by combining two inputs into one, like this: X = A AND (B AND C) Logic Gates and Circuits SB CS PP.indb 155 155 14.5.21. 14:16 Chapter 10 The resulting logic circuit is this: LINK Consolidate your understanding by completing the Exercises 3-4 from pages 129-133 in the Workbook. A B X C The truth table is this: Inputs Intermediate outputs Output A B C B AND C X Activity A photocopier has two options for putting in paper to print: a place to slide in a single sheet of paper and a multifeed drawer for a stack of paper. If there is paper in either of these places and we press the start button then the photocopier will work. Make the logic statements to describe this scenario and then draw the resulting logic circuit and truth table for the entire circuit. ENRICHMENT Can you think of other logic circuits in use? Logic Circuits in Use In practice, logic gates are often built up using a combination of NAND gates. NOT A AND A B X X A X OR B 156 SB CS PP.indb 156 Logic Gates and Circuits 14.5.21. 14:16 Chapter 10 A X NOR B A XOR X B Worked Example REFLECT Show that the circuit below is logically equivalent to the NOT gate. A Why do you think the NAND gate is often called the ‘universal’ NAND Gate? X Solution ENRICHMENT Inputs What careers/job roles do you think require the use of logic circuits? Output A A X From the results given in the truth table, we can see that the truth table is logically equivalent to the NOT gate, and the output X is the inverse of the two inputs of A. Explain examples of when these job roles would have to use this knowledge when carrying out their work. Activity Show that the circuit below is logically equivalent to the AND gate. A B X In your home and in everyday life, there are many electrical items and appliances that rely on logic circuits in order to function. Consider the following scenario. • In order for an elevator to travel to the correct floor, someone must have pressed a floor number button inside the elevator and the doors must be closed. • The total weight in the elevator must also be under the limit (false, , negative). • The elevator moving = X (positive, , true). Logic Gates and Circuits SB CS PP.indb 157 157 14.5.21. 14:16 Chapter 10 The logic circuit for the scenario would look like this: A B P X Q C And the logic statement would be: X = (A AND B) AND (NOT C) And the truth table would be as follows:: Inputs A B Intermediate outputs C P= (A AND B) Q = (NOT C) Output X Writing logical expressions from Truth Tables You can use a Truth Table to create the logical expression and create the logic circuit. Using the Truth Table below where X is the output, we can see that both A and B need to be ON for the output X to be ON. This tells us that the logic gate it is representing is the AND gate. Look at each row and where the output (X) is ON () you look at the inputs (A and B). • If the input is ON () then the input is written as the letter: A • If the input is OFF () then the input is written as the letter with a line above it: A 158 SB CS PP.indb 158 A B X AB Logic Gates and Circuits 14.5.21. 14:16 Chapter 10 In the example above the output is ON () on the last row and both inputs are ON (). • The logical expression would be written as X = A AND B Notice that everything is in capitals, this is expected when writing logical expressions. We can then draw the logic gate to represent the truth table and logical expression. A X B More than inputs Looking at the example below we can see the Truth Table shows an A, B and C input and an output X. Inputs A B C X Look down the X column and circle where the output is ON (). On each row where the output is ON (), use the method to note down which inputs are ON () and OFF () The first row would be written as A B C Inputs A B C X . A B- - C ABC ABC Logic Gates and Circuits SB CS PP.indb 159 159 14.5.21. 14:16 Chapter 10 LINK WB Consolidate your understanding by completing Exercise 5, page 133 in the Workbook. Row Notes on inputs Logical expression for row ABC NOT A AND NOT B AND NOT C ABC A AND NOT B AND NOT C ABC A AND B AND NOT C Each part is placed within brackets and placed together with OR written between each. The logical expression for the Truth Table would be: X = (NOT A AND NOT B AND NOT C) OR (A AND NOT B AND NOT C) OR (A AND B AND NOT C) 160 SB CS PP.indb 160 Logic Gates and Circuits 14.5.21. 14:16 Chapter 10 7 Let’s Map It Truth tables Logic gates have logic states given by: LOGIC GATES Boolean values which are used in truth tables: Boolean value Binary value Synonyms True On Yes Positive False Off No Negative Truth tables are used to represent the Boolean expression of a logic gate or logic circuit. A X B A Inputs B Output X and in the different types of logic gates: COMBINING LOGIC GATES Types of gates NOT Input A Using Boolean algebra: AND Output X A Inputs B OR Output X A Inputs B Output X Boolean algebra A NOT A A+B A NAND B A+B A and B A+B A NOR B A+B A OR B A B A XOR B XOR A and by combining different logic gates: Inputs B NAND Output X A Inputs B NOR Output X A Inputs B Output X All have 2 inputs except for 'NOT' gate Combining logic gates B P X A Inputs A B Intermediate output P Output X Examples of logic circuits used in the real world -Security alarms -Elevators -Eletrical circuits eg light switches We can write logic statements for logic circuits: -Bank vaults Logic statements Break down the statements always A start with the output B X = (A AND B) OR C AND P OR X Logic LogicGates gates and and Circuits circuits SB CS PP.indb 161 161 31 14.5.21. 14:16 Chapter 10 Let’s Review What logic gate matches these truth tables? A B X A B X Label the following logic gates: Draw the logic circuit for the following statement X = (A AND B) AND (NOT C). Complete a combined truth table including any intermediate outputs for the following: <?> A P AND B OR X C Draw the correct logic gate circuit and truth tables to match these Boolean algebra expressions: A˙B A+B Ā Draw the logic circuit diagram and corresponding truth table represented by the below Boolean algebra epressions. Consider the logic statement: X = If [(A is NOT OR B = ) NAND C is ] NOR [(A is AND C is ) NAND B is ] A X B C 162 SB CS PP.indb 162 A B C Working space X Logic gates and circuits 14.5.21. 14:16 Answers Answers to Let’s Review Sections Chapter Binary is a base- number system ( digits); Denary is a base- number system ( dgits); Hexadecimal is a base- number system ( digits) Accept either or Right to left Accept any correct method of working where the answer runs as follows: - – F Accept any correct method of working where the answer runs as follows: D – – Both methods enable the full use of bandwidth in communication Data cannot be sent simultaneously Universal Serial Bus Any three sensible answers, including mouse, printer, keyboard, hard disk drives, mobile devices Some packets of data could be lost, or some digits could be changed Odd or Even False A check digit is calculated using all of the other digits in a barcode and, if the code is correct, the check digit should match Any three from: MAC addresses, error codes, HTML colour codes and IPv addresses A timeout is where a receiving device is waiting for a response and, once the timeout occurs, a repeat request is made for the acknowledgement of the expected data Accept either or = (Denary) False Accept either or = (Denary) The decimal part of the number is discarded Encryption is important to stop unauthorised users intercepting and accessing sensitive data when it is being transmitted across a network The use of two’s complement Chapter Architecture is the components that make up a computer system The ‘most significant bit’ American Standard Code for Information Interchange, a character set used most commonly by computer systems – characters A kilobyte represents bytes, a kibibyte represents bytes – a kibibyte is calculated by powers, whereas a kilobyte is calculated by multiplying whole numbers together Accept .Kb or .Kb Lossless compression – file sizes are reduced but there is no loss of data, duplications are removed instead Lossy compression – data is permanently removed from a file to reduce its size, such as bits of music or images Chapter A small chunk of data designed to be sent around a network Packet header, payload and trailer The trailer tells the receiving device that it has reached the end of the transmission. It is a validation check This is where a transmission of packets travels along a network and takes different routes. Data is transmitted by the most suitable route Serial transmission is where one bit at a time is sent between devices, parallel transmission sends multiple bits of data through multiple channels The CPU processes the instructions and data given by a user through the input devices The Memory Address Register; Memory Data Register; Accumulator; Program Counter; Current Instruction Register The von Neumann architecture is based upon an input device feeding data into a CPU, with a memory unit reading data in and out of the CPU. The result of processing is then sent to an output device Fetch – Decode – Execute Buses are connections that carry data around a computer Cache memory sits within a CPU and holds instructions and data that are needed regularly. Cache memory allows quicker access to these instructions and data leading to faster processing Dual-core Hertz, also accept gigahertz Any sensible example: dishwasher, GPS, sat-nav, central heating, calculator, vending machine, lighting system, CCTV A capacitive touchscreen allows multiple touch sensing, a resistive touchscreen only allows one touch due to using the pressure change, and infra-red works on the basis of breaking a beam of light and is much more sensitive Answers SB CS PP.indb 163 163 14.5.21. 14:16 Either a moisture or level sensor would be acceptable answers Cloud storage is when a user purchases some space on an external server, accesses it via the world wide web and can download from and upload to the space when required A MAC address is a unique identifier for a piece of equipment connected to the internet, the IP address is the location identifier that enables devices to communicate with one another These are issued by a router using a service called DHCP, and are not specific to a device A router is a device that enables a home or business to connect devices to the internet Chapter Any two of: the BIOS, utility software and the operating system Any three of: managing peripherals, drivers, files, multitasking, memory or handling interrupts Small applications which enable a computer to start all of its devices An intervention from a user Software and hardware interrupts Either a division by zero or a process attempting to use the same memory location Low level programming language is machine or binary code. High level programming languages use words that we use as humans It is easier for programmers to debug high level code Assembly language is similar to machine code but it uses mnemonics for instructions and commands alongside numbers A compiler and an interpreter A compiler will run an entire block of code and produce a list of errors and is best used at the end of a programming project. An interpreter will execute code line by line It is better for debugging and finding problems as the interpreter will stop when it finds an error Integrated Development Environment Any two functions from: code editing, auto-completion of syntax, auto-correction of common errors, code formatting, translation of code, error diagnosis and simulation in a run-time environment Chapter The internet is the network of computers connected together as a set of small networks to enable communication to occur. The world wide web is the collection of websites and web pages stored on servers that are accessed through the internet Uniform Resource Locator Secure hypertext transfer protocol Any three from: displaying websites, bookmarks and favourites, recording user history, multiple browsing tabs, storing cookies, navigation tools and an address bar Domain Name System The DNS Query uses the URL that has been entered by the user and looks up the matching IP address. The IP address then connects the user’s browser to the web server that hosts the site and retrieves the required website for the user to view Session and persistent cookies Any two of: cookies can store items in a shopping basket for later, store preferences about how a website loads, store login details or allow targeted adverts to appear Any two of: Ethereum, Tether or Litecoin Blockchain is a database containing digital records of all cryptocurrency transactions Any three of: brute-force attack, data interception, DDoS attack, hacking, malware, pharming, phishing, Malicious software that causes damage to a computer system Pharming is where a user is sent toa fake website that looks genuine; phishing is where an email is received that looks genuine but contains links to malicious websites Where users are manipulated into behaving in a way that they would not normally do This allows security loopholes to be closed and security databases for anti-virus software to be kept up to date It enables browsing of the world wide web while keeping an IP address secret Chapter Sensors, a microprocessor and actuators Actuators turn electrical signals into physical movements Any sensible answer, for example automated motorway signs that control the flow of traffic A danger of creating a fictional life where a user spends more time rather than their real life A factory robot on a production line, a domestic robot that operates in the home or an airborne robot like a drone 164 SB CS PP.indb 164 Answers 14.5.21. 14:16 A mechanical structure or framework, and electrical components, like sensors, microprocessor and actuators Any sensible example, such as a scanner in a CT scanning machine A trace table enables a programmer to work through the code on paper, line by line, to check where variables, selection, sequencing and iteration take place A syntax error They can carry out jobs without humans needing to be present Any reasonable error, such as incorrect use of an arithmetic or Boolean operator Artificial Intelligence Chapter Expert Systems and Machine Learning A variable piece of data can be changed in some way, either by the user or the program Any reasonable explanation, such as: A user would type a word into the user interface and select the language of translation. The software would use the inference engine to determine what was required and would then draw upon its knowledge base to provide a solution. The translation may also utilise the rules base and explanation system to also provide possible alternatives to the translated word, based on similar searches previously carried out by other users Any two from: integer, real, char, string or Boolean The sequence determines the order that a set of instructions are carried out An IF statement Count-controlled, pre-condition and post-condition loops Chapter A counter is used to know how many times the iteration has occurred Analysis – Design – Coding – Testing Changing them into upper or lower case Abstraction is the process of selecting the information in a problem and focusing only on the important parts of that information. During abstraction, any detail that is irrelevant to the problem is ignored Any three from: subtraction, division, raise a power, MOD or DIV Decomposition is breaking down a complex problem into small manageable pieces. It is where a problem becomes a series of small tasks that can be handled first individually and then collectively as part of the bigger program A decision, usually a yes/no answer False Structure diagrams are different from flowcharts in that they display the different levels of detail within a set of decomposed problems All items of data in a set are looked at until the program matches the piece of data it is looking for. Once this match is obtained, the search is completed. In a large data set this would take a long time A data set that has not yet been sorted into a particular order A bubble sort is based upon the idea of swapping adjacent items in a data set until the set is in a desired order Any three answers from: range check, length check, presence check, format check, check digit Double-entry checking The process of testing reports any errors to the programmers and the testing is repeated until there are no errors found in the system Does not equal AND - If something and something else are true or false; OR - If something or something else is true or false; NOT - If something is NOT true or false Where it is necessary to execute one IF statement, followed by another, followed by another. This would form a subroutine, with each routine nested inside another Where a function or procedure sometimes requires a programmer to give them additional information to carry out their processes A global variable is generally declared at the start of a program and can be used anywhere throughout a program. A local variable is declared within a function and can only be used within the function Any two from: MOD, DIV, ROUND, RANDOM All identifiers should be easily recognisable by programmers to ensure the code can be easily read and understood Commentary can be very helpful to know what a programmer or developer was thinking at the time of writing a particular line or set of lines of code, and any programmer working in a team would be able to access other people’s coding much more easily. They are not executed A set of related data that are all of the same data type False This data includes the extreme values of the normal range given, as the highest possible and lowest possible data in a set Answers SB CS PP.indb 165 165 14.5.21. 14:16 It is often important to store program data in external files so that it is not lost when a program has finished running. Programming can often take weeks and months to create, and to be constantly restoring data to code would be hugely time consuming False Practical task - answers may vary Practical task - answers may vary Chapter Chapter OR gate A database is an organised collection of data. It is electronically stored and accessed in a computer system NAND gate Flat-file database Relational database A flat-file database stores simple data formats. They store only a single table of data. The information given by a record is complete with a fixed number of fields. Thus, the database is not related to any other table or database. This method of storing data is not efficient and may lead to problems like data duplication, data redundancy and input errors. A relational database can have multiple related tables. When the tables are linked, the user can work on complex data structures having multiple tables. A relational database does not allow data duplication. Also, it is more efficient and consistent than a flat-file database. NAND gate NOR gate XOR gate The logic circuit for the scenario would look like this: Queries are used for working with data in a database. These are requests that help in arranging, retrieving or modifying information from a database. Example of statement that can be used to retrieve data using SQL queries: SELECT [Field Name] FROM [Table Name] 166 SB CS PP.indb 166 X = P OR C P = A AND B A data type is an attribute or property of a field in a database which helps in helps the computer to identify similar data for the purpose of sorting, searching and calculation. For example, Text, Char, Integer, Number, etc. X = (A AND B) OR C A B Practical task - answers may vary 0 0 Validation refers to checking and confirming the accuracy of data or information in the computer system. There are certain rules that are followed when data is typed into a database system called the data validation rules. For example, a phone number does not contain a character or an alphabet. These rules help in accepting the data which are as per the set format. The data entered into a database can sometimes be entered incorrectly. It can be invalid, inconsistent or incomplete. To avoid any such issue, the user may apply different validation checks. Some validation checks are: Presence check, Range check, Length check and so on. 0 0 The truth table is: Input Intermediate outputs Output C A AND B X 0 0 0 0 1 0 1 1 0 0 0 0 1 1 0 1 1 0 0 0 0 1 0 1 0 1 1 1 0 1 1 1 1 1 1 1 Answers 14.5.21. 14:16 A . B represents AND gate, that is, A AND B The corresponding circuit diagram is: The corresponding Logic gate and circuits are: The truth table is: Input A + B represents OR gate, that is, A OR B The corresponding Logic gate and circuits are: Intermediate outputs Output A B C P=Ā Q=P OR B R=Q NAND C S=A AND C T=B NAND S X=R NOR T 0 0 0 1 1 1 0 1 0 0 0 1 1 1 0 0 1 0 0 1 0 1 1 1 0 1 0 0 1 1 1 1 0 0 1 0 1 0 0 0 0 1 0 1 0 1 0 1 0 0 1 1 1 0 1 1 0 0 1 1 0 1 0 1 1 1 0 1 0 1 0 1 represents NOT gate, that is, NOT A The corresponding Logic gate and circuits are: Answers SB CS PP.indb 167 167 14.5.21. 14:16 Index A abstraction 95 Access 132–133 access levels 74 accumulator 36 actuators 48, 84, 85 address bar 29, 68, 69, 70 address bus 36, 37 adware 73 AI (artificial intelligence) 88–90 algorithms 28, 94, 100–101, 114 flowcharts 97–98 iteration in 115 pseudocode 98–99 solution methods 101–103 structure diagrams 99–100 trace tables 105–107 writing 108 ALU (arithmetic logic unit) 35, 37 analogue signals 14, 44 AND gate 143, 144 AND operator 119 application software 60 running sequence 61 arithmetic operators 118 ARQ (automatic repeat requests) 28 arrays 122–123 ASCII code 13 assembly language 63 authentication 75–78 biometric 77 electronic tokens 78 magnetic stripes 77 passwords 75–76 physical tokens 78 smart cards 77 spyware 76 zero login 77 auto-completion 64 auto-correction 64 automated systems 84–86 automating software updates 78 AutoNumber 130 AVERAGE 103 B barcode check digits 28 reader 44 binary numbers 2–3 adding two binary numbers 7–8 converting to denary 4 dividing 10 multiplying 9 overflow errors 8–9 binary shifting 9 with 8-bit binary numbers 10–11 168 SB CS PP.indb 168 biometric authentication 77 BIOS (Basic Input Output System) 60 bit (binary digit) 15 bit depth 15 bit rate 15 Blu-ray discs 53 bookmarks 70 Boolean algebra 142–143, 144, 145, 147, 148 Boolean data 112, 130 Boolean operators 107, 119, 142 boundary data 105 browsers 70 brute-force attack 72 bubble sort 101–103 buses 36 bytes 5, 15, 16 C cache memory 38 cameras 43 capacitive touchscreens 43 capacitors 52 CASE statements 114–115 CD (compact disc) drives 53 Character/Char, data type 112, 129 check digits 28–29, 104 checksum 28 clock speed 38 cloud storage 54 code editor 64 comments, in computer programs 121 compilers 63–64 computer architecture 34–36 computer systems 60, 97–100 embedded 39 OS (operating system) 60 constants 112 control bus 36 control unit 35 cookies 70, 71 COUNT function 137 count-controlled loop 115, 116 counting 103, 117 CPU (central processing unit) 34 processing cores 38 cryptocurrency 72 currency, data type 130 current instruction registers 36 cyber security 72–80 brute-force attack 72 data interception 72 DDoS (Distributed Denial of Service) attack 73 hacking 73 malware 73 pharming 74 phishing 74 social engineering 74 solutions 74–80 D data 128 abnormal 105 corruption 27 types 112, 129 data bits 3 data bus 36 data compression 18 data entry, validation and verification 104–105 data interception 72 data storage 15–17, 50–53 data transmission 22–27 full-duplex 25–26 half-duplex 25 methods of 23–26 parallel 24 serial 23–24 simplex 24 vis USB 26–27 databases 128–130 creating 131–134 data types 129 data validation 133–134 entering data 134 queries 129, 135–137 tables 129, 132–133, 134 types of 130–131 uses 128 date/time, data type 130 DBMS (Database Management System) 130 decomposition 95 DEFAULT output 115 denary (base-10) numbers 2 converting to binary 3–4 converting to hexadecimal 5 dictation software 44 digital currency 72 digital light processing (DLP) projector 46 Distributed Denial of Service (DDoS) attack 73 DIV (division) 118, 121 Domain Name System (DNS) Query 71 double entry 105 DO-WHILE iteration 116 dual-core processor 38 DVD (digital versatile disc) drives 53 Index 14.5.21. 14:16 E echo check 28 electronic tokens 78 embedded systems 39 encryption 29–30 asymmetric 30 symmetric 30 error detection 27–29 and correction 107–108 error diagnostics 64 executable files 63 expert systems 89 extreme data 105 F favourites 70 fetch-decode-execute cycle 37 fields, in a database 129 file handling 123–124 files reading from 124 writing to 124 firewalls 79–80 flash drives 52–53 flat-file (single-table) databases 130 flowcharts 97–98 FOR loop 116 foreign key 130 format check 104 fragmentation 51 full-duplex data transmission 25–26 functions 120, 121 G gaming controllers 41 global variables 121 H hacking 73 half-duplex data transmission 25 hardware interrupts 62 HDMI (high-definition multimedia interface) 46 hertz 15 hexadecimal numbers 3 converting to denary 6 uses in data representation 6–7 HTML (hypertext markup language) 70 HTTP (hypertext transfer protocol) 69 https (secure hypertext transfer protocol) 69 I IDE (Integrated Development Environment) 64 IF, THEN, ELSE 114 IF statements 114 image files, calculating the file size of 16 image representation 15 information 128 infra-red screens 43 inkjet printers 47 input 113 input devices 40–45 instruction sets 38–39 integers 112, 129 internet 68–71 interpreters 63–64 interrupt service routine 61 interrupts 61–62 IP (Internet Protocol) address 22, 55–56 ISBN numbers, check digits 28 iteration 115–116, 120 J JavaScript 63 jpeg files 18 K keyboard 40 kibibytes (KiB) 16 L LAN (local area network) 56 laser printers 47 LCD (liquid crystal display) monitors 45 LCD (liquid crystal display) projectors 46 LED (light emitting diode) screens 45 length, of a string 117 length checks 104 library routines 121 linear search 101 local variables 121 logic circuits 150–158 drawing 155–156 with more than two inputs 151–154 using 156–158 writing statements 154–155 logic errors 107 logic gates 142–149 combining 150–158 types of 143–149 logical operators 118–119 lossless data compression 18 lossy data compression 18 LOWER 118 M MAC (media access control) addresses 55 machine code 62 machine learning 90 magnetic hard disk drives 51–52 magnetic stripe cards 77 malware (malicious code software) 73 anti-malware software 74–75 MAR (memory address register) 36 MAXIMUM 103 MDR (memory data register) 36 measurement units 16 memory 50 memory unit 36 microphones 44 microprocessors 49, 84, 85 MINIMUM 103 MOD (modulo) 121 modems 56 monitors 45 mouse 41 mp3 files 18 N NAND (NOT AND) logic gate 52, 146, 147 nested statements 119–120 iteration 120 selection 119 network hardware 54–56 nibbles 15 non-volatile storage 51 NOR (NOT OR) logic gate 52, 146, 147 normal data 105 NOT Boolean operator 119 NOT logic gate 143, 144 number systems 2–3 numbers/numeric data 129 numeric keypads 40 O opcodes (operation codes) 38 operands 39 optical character recognition 43 optical disc drive 53 OR Boolean operator 119 OR logic gate 143, 144–146 ORDER BY clause 137 OS (operating system) 60–61 output 113 output devices 45–48 overflow errors 8–9 P packet switching 22–23 packets, structure 22 parallel data transmission 24 parity check 27–28 passwords 75–76 pen drives 52–53 pharming 74 phishing 74, 79 pixels 15 pointing devices 41–42 portable magnetic hard drives 52 portable solid state hard drives (SSDs) 52 post-condition loops 115, 116 pre-condition loops 115, 116 Index SB CS PP.indb 169 169 14.5.21. 14:16 presence checks 104 prettyprint 64 primary key 130, 133 primary storage 50 printers 47–48 privacy settings 80 procedures 120–121 processing core 38 program counter 36 program development life cycle 94–96 analysis 94–95 coding and iterative testing 96 designing 95–96 testing 96 programming concepts 112–122 creating programs 121–122 fundamentals 114–119 programming languages 62–64 high-level and low-level 62 proxy servers 80 pseudocode 97, 98–99 Python 63, 94, 108, 112, 113 arrays 122 functions 120 iteration 116 nested selection 119 reading from a file 124 string handling 117–118 totalling and counting 117 writing to a file 124 Q QR (quick response) scanner 45 quarantine 75 queries, database 129, 135–138 query-by-example 135–136 R RAM (random access memory) 36, 50, 53 RANDOM 121 range checks 104 ransomware 73 reading from a file 124 real numbers 112, 129 records 129 registers 35–36 relational databases 130 resistive screens 42 robotics 87–88 ROM (read only memory) 50 ROUND 121 routers 56 run length encoding (RLE) 18 run-time environment 64 170 SB CS PP.indb 170 S sample rates 15 SATA (serial advanced technology attachment) cable 51 scanners 43 secondary storage 50, 51–53 SELECT statement 137 selection 114 sensors 49, 84, 85 sequencing 114 serial data transmission 23–24 simplex data transmission 24 smart cards 77 social engineering 74 software 60–62 application 60, 61 automating updates 78 OS (operating system) 60–61 software interrupts 62 solution methods 101–103 sound files, calculating the file size of 17 sound representation 14–15 speakers 48 spelling errors, in phishing emails 79 spyware 73, 76 anti-spyware software 74–75, 76 SQL (Structured Query Language) 135, 136–137 SSD (solid state hard drives) 52 SSL (secure sockets layer security protocol) 80 standard solution methods 103 strings 112, 117–118 structure diagrams 97, 99–100 stylus pens 41 substring 117 SUM function 137 symmetric encryption 30 syntax errors 107 system security 61 system software 60 T tables, in a database 129 testing programs 105 text representation 13–14 text/alphanumeric data 129 three-dimensional (3D) printers 48 tokens 78 totalling 103, 117 touch screens 42, 46 touchpads 41 trace tables 105–107 trackballs 41 transistors 3, 52 translators 63, 64 trojan horse 73 truth tables 143 two’s complement 11–13 type checks 104 U Unicode 14 units of measurement 16 UPPER 118 URL (Uniform Resource Locator) 68–69, 79 USB (Universal Serial Bus) 26–27 user history 70 utility software 60 V validation checks for data in databases 133–134 for programs 104 variables 112 in computer programs 121 global 121 local 121 verification 105 video conferences 43 virtual memory 53 viruses 73 anti-virus software 74–75 visual checks 105 von Neumann, John 35 W web address see URL (Uniform Resource Locator) web browsers 70 web pages 71 webcam (web camera) 43–44 WHERE clause 136 WHILE loop 116 world wide web 68 worms 73 writing to a file 124 X XOR gate 146, 148 Z Zero login 77 Index 14.5.21. 14:16 Computer Science Glossary Adjacent (page 101): the item next to another item Algorithm (page 94): a set of rules or instructions for solving a problem Alphanumeric (page 76 ): text on page simply reads ‘letters and numbers’ Ambient (page 49): the immediate Surroundings Amplitude (page 14): the strength of a sound wave, measured at the highest level Analogue (page 14): using signals or information represented by a continuously variable physical quantity Combination (page 142): a joining of different parts or qualities Comparisons (page 101): checking one item against another and looking for differences or similarities Complex (page 150): more difficult / more components involved Comprise (page 96): include, be made up of Components (page 85): pieces of equipment in a system Compromise (page 74): become vulnerable or function less effectively Analogue signals (page 44): continuous signals that cannot be processed by a computer until they Condition (page 145): the state of something in relation to its appearance, quality or working order are converted into digital data. Conductive (page 43): heat and electricity can pass through an object Array (page 45): a data structure that holds related data. Architecture (page 34): how a computer system is designed, including the rules and methods that the system should follow Control bus (page 37): a bus that carries instructions from the CPU to control the actions of the computer Computational thinking (page 95): breaking down a problem into smaller sub-problems to solve them Arithmetic (page 142): use of numbers to calculate an outcome Corruption (page 27): where something is altered or changed without a user knowing Automated (page 84): machines carrying out a job that would otherwise have been done by humans Constructs (page 114): the building blocks of programming Bandwidth (page 18): the transmission capacity of a computer network Criteria (page 129): conditions or questions Barcode (page 28): a machine readable code in the form of numbers and a pattern of parallel lines of varying widths, printed on a physical item. This pattern identifies it from other barcodes Data duplication (page 130): a process of creating an exact copy of data Data redundancy (page 130): the storing of the same data in multiple locations Binary (page 2): a number system that contains just 2 numbers, 0 and 1, and the number system that a computer uses to process data Data validation rules (page 133): these are some rules which help the user to know that the data being entered in a database is correct Bluetooth (page 40): a form of wireless connection for connecting devices together when they are Debugging (page 64): finding errors or mistakes in code near each other Decipher (page 30): converting code into normal language Boolean (page 107): where a variable can have one of two values, true or false Degrades (page 53): breaks down or deteriorates Brainstorming (page 94]: an exhaustive discussion to solve problems or generate ideas Capacitor (page 52): a small electronics device that stores an electrical charge Detects (page 152): identifies Dictation (page 44): the process of reading words into a microphone so that they can be converted from analogue signals to digital words on a screen Computer Science Glossary SB CS PP.indb 171 171 14.5.21. 14:16 Division by zero (Page 62): a mathematical calculation that has no answer, and one that is automatically rejected by a computer for this reason Efficiently (page 2): to perform something in a wellorganised and competent way Electrodes (page 43): a conductor where electricity enters or leaves an object Electromagnetic (page 51): the electrical and magnetic forces or effects produced by an electric current. Entity (page 129): object or thing Equivalent (page 142): the same or equal meaning Address (Page 22): a unique string of numbers separated by full stops that identifies each computer using the protocol to communicate over a network Intervention (page 61): an action taken by someone to make something different happen Intricate (page 34): very complicated or detailed Inverted (page 12): reversed or transformed into its corresponding opposite ISBN number (page 28): International Standard Book Number, a global system for identifying individual books. ISBN numbers have 13 digits Firmware (page 60): small applications which enable a computer to start all of its devices Hertz (page 15): frequency of samples, measured in cycles per second Floating-point (page 112): a number in programming that contains a decimal point, and the decimal point can ‘float’ in different places to help with handling large numbers Interrupt service routine (page 61): a software routine that hardware invokes in response to an interrupt Formally (page 143): officially / explicitly Function (page 120): a block of organised, reusable code used to perform a single, related action HDMI (page 45): high-definition multimedia interface technology displays high-definition images and sound through a single cable. HDMI is a standard connection port for audio/visual devices in computers Hexadecimal (Page 55): a number system that uses 16 characters instead of the 10 characters used in the decimal system or the two used in binary Hypertext transfer protocol (page 69): the agreed set of rules that all computers use for transmitting files (data) over the world wide web Impaired (page 15): weakened or damaged Increment (page 117): to increase by a set number Inefficient (page 113): not the best or fastest way of achieving a goal Infinitely (page 85): continues forever, until stopped SB CS PP.indb 172 Internet Protocol (IP) Executable (page 63): a file that launches and runs a series of code when opened Foreign key (page 130): A foreign key is a fi eld or combination of fi elds that are related to the primary key of another table 172 Interface (page 47): a device or program used to communicate with a computer jpeg (page 18): Joint Photographic Experts Group: the organisation that created the file type Lightning connection (page 52): a high-speed connection that was developed by Apple for the purpose of connecting multiple external devices to their computers Logic gates (page 142): the basic units of a digit circuit that control the flow of electronic signals Logical reasoning (page 89): a set of reasonable conclusions and explanations Microprocessor (page 49): Microprocessors are integrated circuits that contains all the functions of a CPU of a computer mp3 (page 18): MPEG (Moving Picture Experts Group: the organisation that created the file type) Layer 3 Negotiations (page 94): a discussion to produce a settlement or agreement Nibble (page 5): a set of four binary bits Originator (page 22): the sending Device Operating system (page 41): a piece of software that communicates with the hardware and allows other programs to run Computer Science Glossary 14.5.21. 14:16 Overflow (page 9): the generation of a number or other data item that is too large for the assigned location or memory space Parity (page 23): ensuring that something is the same Parity check (page 27): is a bit added to a string of binary code as the simplest form of error detecting code Perspective (page 94): a particular way of thinking about something Pictorially (page 100): in the form of a Diagram Pixel (page 15): a tiny area of illumination on a display screen Platter (page 51): a circular magnetic plate that is used for storing data in a hard disk. Portability (page 53): the ability to carry or move something Powers (page 2): the product obtained when a number is multiplied by itself a certain number of times Pressure (page 49): continuous physical force exerted on an object Primary key (page 130): A primary key is a unique field that allows the user to identify a record Protocol (page 27): a set of rules that are applied to the transfer of data Pseudocode (page 98): a version of programmable code written in standard English Quarantine (page 75): to place into isolation Referred: (page 143) denoted / identified Remainder (page 3): the number left over in a division in which one quantity does not exactly divide another Replicating (page 90): creating as close to a copy of something as possible Search engine (page 70): a web-based tool that is used to find web pages based on a given topic or keyword entered by the user. It then returns a list of relevant web pages and their respective URLs Serial advanced technology attachment (SATA) ( page 51): a type of cable usually found inside computers. It connects a hard drive with the motherboard Shift (page 9): movement either to the left or right Simulate (page 64): run a test version of an application Simultaneously (page 25): at the same time Sophisticated (page 75): more complex Sound card (page 48): an internal device of a computer that provides a method of input and output of audio signals for use with multimedia applications Spoof (page 74): something that is fake but pretends to be genuine String (page 129): a set of characters that can also contain spaces and numbers Stylus (page 41]: a pen that can be used either directly onto a screen or a pad connected to a computer Substitute (page 76): exchange for something different Syntax (page 64): the structure of not just statements but also symbols, punctuation, etc., in a computing language Test strategy (page 96): test plans for testing the system Transaction (page 29): the process of buying or selling something Translated (page 63): changed into a different language Transistor (page 3): a small electronics device that carries, switches and amplifies an electrical current Truth tables (page 144): used to represent the Boolean expression of a logic gate or logic circuit Ubiquitous (page 26): located everywhere Universal serial bus (USB) (page 40): a standard connector found on many different types of computer and used to connect external devices Utility (page 60): a small piece of software that controls specific parts of the hardware Validation (page 104): the process that helps the system know the data entered is correct Validation check (page 104): testing for validations Computer Science Glossary SB CS PP.indb 173 173 14.5.21. 14:16 Video conference (page 43): a form of visual communication where users in different places can see, hear and speak to each other using a variety of equipment, including web cameras, monitors and microphones 174 SB CS PP.indb 174 Visualise (page 95): to be able to see a prototype of an idea Volatile (page 50): loses its contents when there is no electrical charge Computer Science Glossary 14.5.21. 14:16 SB CS PP.indb 175 14.5.21. 14:16 SB CS PP.indb 176 14.5.21. 14:16 Cambridge IGCSETM Computer Science For over 60 years Marshall Cavendish Education has been empowering educators and students in over 80 countries with high-quality, research-based, Pre-K-12 educational solutions. We nurture world-ready global citizens by equipping students with crucial 21st century skills through our resources for schools and education centres worldwide, including Cambridge schools, catering to national and international curricula. The Marshall Cavendish Education Cambridge IGCSETM Computer Science series is designed for students studying for the Cambridge IGCSE and IGCSE (9–1) Computer Science syllabuses (0478/0984). The series focuses on developing important computer science skills relevant to real-world applications. SB The Student’s Book: • Encourages active and inquiry-based learning through hands on activities and discussions • Supports subject literacy with concise language, language support and bite-sized concepts • Caters to the international landscape with multicultural photographs, visuals and other references • Promotes visual learning through concept infographics and clear illustrations • Includes mind maps and links that build learners’ understanding of the relationships between concepts • Nurtures life-long learning in building digital literacy skills which students can use beyond their course • Helps students develop 21st century competencies, so that they become future-ready ✓ Supports the full Cambridge IGCSE and IGCSE (9–1) Computer Science syllabuses (0478/0984) for examination from 2023. ✓ Has passed Cambridge International’s rigorous TM Computer Science STUDENT’S BOOK STUDENT'S BOOK This resource is endorsed by Cambridge Assessment International Education Cambridge IGCSE Series architecture • Student’s Book • Workbook • Teacher’s Guide • e-book quality-assurance process ✓ Developed by subject experts ✓ For Cambridge schools worldwide ISBN 978-981-4941-59-4 Greg Shilton Megha Goel 9 789814 941594 C01(S)IGCSECS_SB_Cover.indd All Pages 12/5/21 11:11 AM