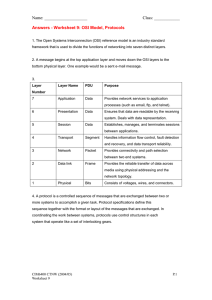
Chapter One Introduction to data communication And Networking 1 Outlines • Model for data communication • Protocols and architectures used in data communication OSI and TCP/IP • Introduction to network devices (switch, hub, router…) 2 Introduction • The term telecommunication means communication at a distance. • The word data refers to information presented in whatever form is agreed upon by the parties creating and using the data. • Data communications are the exchange of data between two devices via some form of transmission medium such as a wire cable. 3 • A Network: A group of devices that can communicate with each other over links. – It’s a connection between two or more devices. – Which is connected by a communication links. • A node can be computer, printer or any other devices which is capable of sending and receiving information at each other. – Each device is called a host. – Each host has a unique address. 4 Components of a data communication system 1. protocol 2. Message 3. Medium 4. Sender 5. Receiver 5 Model for data communication Source • Generates data to be transmitted Transmitter • Converts data into transmittable signals Transmission System • Carries data 6 Receiver •Converts received signal into suitable data form Destination •Takes incoming data 7 Simplified Data Communications Model Protocols and architectures used in data communication OSI and TCP/IP • A protocol is a set of rules or procedures for transmitting data between electronic devices, such as computers. • it a set of mutually accepted and implemented rules at both ends of the communications channel for the proper exchange of information. • It is a digital language through which we communicate with others on the Internet. 9 • Rules are defined for each step and process during communication between two or more computers. • Networks have to follow these rules to successfully transmit data. • Protocols are needed in every field like society, science & technology, Data Communication, media and etc. 10 • In order for computers to exchange information, there must be a pre-existing agreement as to how the information will be structured and how each side will send and receive it. • Without a protocol, a transmitting computer, for example, could be sending its data in 8-bit packets while the receiving computer might expect the data in 16-bit packets. • Protocols are established by international or industry wide organizations. 11 • Perhaps the most important computer protocol is OSI (Open Systems Interconnection), a set of guidelines for implementing networking communications between computers. • Among the most important sets of Internet protocols are TCP/IP (Transmission Control Protocol/Internet Protocol), HTTPS (Secure Hypertext Transmission Protocol), SMTP (Simple Mail Transfer Protocol), and DNS (Domain Name System). 12 Levels of a Protocol • There are mainly three levels of a protocol, they are as follows: • Hardware Level: In this level, the protocol enables the hardware devices to connect and communicate with each other for various purposes. • Software Level: In the software level, the protocol enables different software to connect and communicate with each other to work collaboratively. 13 • Application Level: In this level, the protocol enables the application programs to connect and communicate with each other for various purposes. • Hence protocols can be implemented at the hardware, software, and application levels. 14 Types of Protocols • Protocols can be broadly divided into the following two types: – Standard Protocols – Proprietary Protocols • Standard Protocols: • A standard protocol is a mandated protocol for all devices. – It supports multiple devices and acts as a standard. – Standard protocols are not vendor-specific 15 – i.e. they are not specific to a particular company or organization. – They are developed by a group of experts from different organizations . • These protocols are publicly available, and we need not pay for them. • Some of the examples of Standard Protocols are FTP, DNS, DHCP, SMTP, TELNET, TFTP, etc. 16 • FTP(File transfer protocol): is basically used for transferring files to different networks. – There may be a mass of files such as text files, multimedia files, etc. – This way of file transfer is quicker than other methods. • SMTP(Simple mail transfer protocol): manages the transmission and outgoing mail over the internet. 17 • Proprietary Protocols: – Proprietary protocols are developed by an individual organization for their specific devices. – We have to take permission from the organization if we want to use their protocols. – It is not a standard protocol and it supports only specific devices. – We may have to pay for these protocols. – Some of the examples of Proprietary Protocols are IMessage, Apple Talk, etc. 18 OSI and TCP/IP • Open Systems Interconnection (OSI) protocols: are a family of standards for information exchange. • They consist of a set of rules that should represent a standard for physical connections, cabling, data formats, transmission models. • These protocols were developed and designed by the International Organization of Standardization (ISO). • In 1977 the ISO model was introduced, which consisted of seven different layers. 19 • Each layer of the ISO model has its own protocols and functions. • The OSI protocol stack was later adapted into the Transmission Control Protocol (TCP)/ internet protocol (IP) stack. • TCP/IP helps you to determine how a specific computer should be connected to the internet and how you can transmit data between them. – It helps you to create a virtual network when multiple computer networks are connected together. • TCP/IP stands for Transmission Control Protocol/ Internet Protocol. – It is specifically designed as a model to offer highly reliable and end-to-end byte stream over an unreliable internetwork. 20 21 OSI Model Explained 22 23 • The following are the OSI protocols used in the seven layers of the OSI Model: • Layer 1, the Physical Layer – This layer deals with the hardware of networks such as cabling. – It defines the mechanical and electrical standards of interface devices and the types of cables used to transmit digital signals (e.g. optical fiber, coaxial cable, wireless, etc.). – The major protocols used by this layer include Bluetooth, PON, OTN, DSL, IEEE.802.11, IEEE.802.3, L431 and TIA 449. 24 •Transmitting individual bits from one node to the next. 25 • Layer 2, the Data Link Layer – This layer receives data from the physical layer and compiles it into a transform form called framing or frame. – The principal purpose of this layer is to detect transfer errors by adding headers to data packets. – The protocols are used by the Data Link Layer include: ARP, CSLIP, HDLC, IEEE.802.3, PPP, X-25, SLIP, ATM, SDLS and PLIP. 26 • It is responsible for node-to-node delivery of data. 27 • Layer 3, the Network Layer – This is the most important layer of the OSI model, which performs real time processing and transfers data from nodes to nodes. – Routers and switches are the devices used for this layer that connects the notes in the network to transmit and control data flow. – The network layer assists the following protocols: – Internet Protocol (IPv4), Internet Protocol (IPv6), IPX, AppleTalk, ICMP, IPSec and IGMP. 28 29 • Layer 4, the Transport Layer – The transport layer works on two determined communication modes: Connection oriented and connectionless. – This layer transmits data from source to destination node. – It uses the most important protocols of OSI protocol family, which are: Transmission Control Protocol (TCP), User Datagram Protocol (UDP), SPX, Datagram Congestion Control Protocol (DCCP) and Stream Control Transmission Protocol (SCTP). 30 31 • Layer 5, the Session Layer – The session layer creates a session between the source and the destination nodes and terminates sessions on completion of the communication process. – The protocols used are: PPTP, SAP, L2TP and NetBIOS. 32 33 • Layer 6, the Presentation Layer – The functions of encryption and decryption are defined on this layer. – It ensures that data is transferred in standardized formats by converting data formats into a format readable by the application layer. – The following are the presentation layer protocols: XDR, TLS, SSL and MIME. 34 35 • Layer 7, the Application Layer – This layer works at the user end to interact with user applications. – QoS (quality of service), file transfer and email are the major popular services of the application layer. – A few examples of application layer protocols are the Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), and Domain Name System (DNS). 36 37 Difference between TCP/IP and OSI Model • Here are some important differences between the OSI and TCP/IP model: 38 39 Introduction to network devices • A network is a set of devices (often referred to as nodes) connected by communication links. • A node can be a computer, printer or any other device capable of sending and/or receiving data generated by other nodes on the network. • A link can be a cable, air, optical fiber or any medium which can transport a signal carrying information. 40 • Network devices, or networking hardware, are physical devices that are required for communication and interaction between hardware on a computer network. • Types of network devices • The common network device are: – Hub – Switch – Router – Bridge – Gateway – Modem – Repeater – Access Point 41 Switch • A Switch is a networking device that has the ability to link multiple devices together on one computer network. • It uses a data link layer to connect the devices. • When it comes to switching, we prefer the packet switching method to dispatch the data packet over the web. 42 Hub • A Hub is a networking connector device that aids in connecting multiple devices to a single network. • It is a common connection point that is also known as a network hub. • It is a physical layer network device that connects a series of LANs. 43 44 Router • A router is a device for computer networking devices that helps in connecting two or more packet-switched networks. • The major role of the router is to perform the two functions. • It supports in handling the traffic between the networks by dispatching data packets, and permits several devices to use the same internet connection. 45 46 47 Exercise (Individual) 1. Discuss on the following network devices; a) Gateway b) Bridge c) Modem and d) Repeater 2. Explain the following protocols: HTTP, SMTP, DHCP, FTP, Telnet, SNMP, SMPP, POP, DNS, PPTP, SAP, L2TP, NetBIOS, XDR, TLS, SSL and MIME, Bluetooth, PON, OTN, DSL, IEEE.802.11, IEEE.802.3, L431 and TIA 449. 48