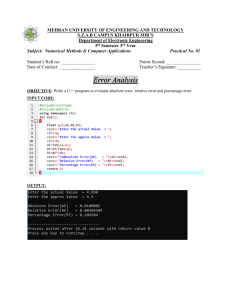
Chapter 1—The Information System: An Accountant’s Perspective TRUE/FALSE 1. Information is a business resource. ANS: T 2. An information system is an example of a natural system. ANS: F 3. Transaction processing systems convert non-financial transactions into financial transactions. ANS: F 4. Information lacking reliability may still have value. ANS: F 5. A balance sheet prepared in conformity with GAAP is an example of discretionary reporting. ANS: F 6. The Management Reporting System provides the internal financial information needed to manage a business. ANS: T 7. Most of the inputs to the General Ledger System come from the Financial Reporting System. ANS: F 8. When preparing discretionary reports, organizations can choose what information to report and how to present it. ANS: T 9. Retrieval is the task of permanently removing obsolete or redundant records from the database. ANS: F 10. Systems development represents 80 to 90 percent of the total cost of a computer system. ANS: F 11. The database administrator is responsible for the security and integrity of the database. ANS: T 12. A backbone system is completely finished, tested, and ready for implementation. ANS: F 13. The internal auditor represents the interests of third-party outsiders. ANS: F 14. Information Technology (IT) audits can be performed by both internal and external auditors. ANS: T 15. The single largest user of computer services is the personnel function. ANS: F 16. Increased control is one of the key advantages of distributed data processing. ANS: F 17. The flat-file approach is most often associated with so-called legacy systems. ANS: T 18. In a flat-file system, files are easily shared by users. ANS: F 19. Legacy systems were eliminated in the effort to make systems Y2K compliant. ANS: F 20. One of the greatest disadvantages of database systems is that all data is always available to all users. ANS: F 21. Under SOX legislation auditors are no longer allowed to provide consulting services to audit clients. ANS: T 22. Under SOX legislation auditors are no loger allowed to provide consulting services to their clients. ANS: F They cannot provide such services to audit clients but may still provide them to non-audit clients MULTIPLE CHOICE 1. Which of the following is not a business resource? a. raw material b. labor c. information d. all are business resources ANS: D 2. Which level of management is responsible for short-term planning and coordination of activities necessary to accomplish organizational objectives? a. operations management b. middle management c. top management d. line management ANS: B 3. Which level of management is responsible for controlling day-to-day operations? a. top management b. middle management c. operations management d. executive management ANS: C 4. The ability to achieve the goals of a system depends upon the effective functioning and harmonious interaction between its subsystems. This is called a. system decomposition b. system redundancy c. backup system d. subsystem interdependency ANS: D 5. The value of information for users is determined by all of the following but a. reliability b. relevance c. convenience d. completeness ANS: C 6. An example of a nonfinancial transaction is a. sale of products b. cash disbursement c. log of customer calls d. purchase of inventory ANS: C 7. An example of a financial transaction is a. the purchase of computer b. a supplier’s price list c. a delivery schedule d. an employee benefit brochure ANS: A 8. Which subsystem is not part of the Accounting Information System? a. Transaction Processing System b. Expert System c. General Ledger/Financial Reporting System d. Management Reporting System ANS: B 9. The major difference between the Financial Reporting System (FRS) and the Management Reporting System (MRS) is the a. FRS provides information to internal and external users; the MRS provides information to internal users b. FRS provides discretionary information; the MRS provides nondiscretionary information c. FRS reports are prepared using information provided by the General Ledger System; the MRS provides information to the General Ledger System d. FRS reports are prepared in flexible, nonstandardized formats; the MRS reports are prepared in standardized, formal formats ANS: A 10. The purpose of the Transaction Processing System includes all of the following except a. converting economic events into financial transactions b. recording financial transactions in the accounting records c. distributing essential information to operations personnel to support their daily operations d. measuring and reporting the status of financial resources and the changes in those resources ANS: D 11. The Transaction Processing System includes all of the following cycles except a. the revenue cycle b. the administrative cycle c. the expenditure cycle d. the conversion cycle ANS: B 12. The primary input to the Transaction Processing System is a. a financial transaction b. an accounting record c. an accounting report d. a nonfinancial transaction ANS: A 13. When designing the data collection activity, which type of data should be avoided? a. data that is relevant b. data that is efficient c. data that is redundant d. data that is accurate ANS: C 14. The most basic element of useful data in the database is a. the record b. the key c. the file d. the attribute ANS: D 15. In a database, a complete set of attributes for a single occurrence of an entity class is called a. b. c. d. a key a file a record a character ANS: C 16. Effective information has all of the following characteristics except a. relevance b. completeness c. summarization d. structure ANS: D 17. Database management tasks do not include a. summarization b. storage c. retrieval d. deletion ANS: A 18. The author distinguishes between the Accounting Information System and the management Information System based on a. whether the transactions are financial or nonfinancial b. whether discretionary or nondiscretionary reports are prepared c. the end users of the reports d. the organizational structure of the business ANS: A 19. Which activity is not part of the finance function? a. cash receipts b. portfolio management c. credit d. general ledger ANS: D 20. Market research and advertising are part of which business function? a. materials management b. finance c. marketing d. production ANS: C 21. Which function manages the financial resources of the firm through portfolio management, banking, credit evaluation, and cash receipts and disbursements? a. accounting b. finance c. materials management d. distribution ANS: B 22. Which of the following is not part of the accounting function? a. managing the financial information resource of the firm b. capturing and recording transactions in the database c. distributing transaction information to operations personnel d. managing the physical information system of the firm ANS: D 23. The term “accounting independence” refers to a. data integrity b. separation of duties, such as record keeping and custody of physical resources c. generation of accurate and timely information d. business segmentation by function ANS: B 24. In the distributed data processing approach a. computer services are consolidated and managed as a shared organization resource b. the computer service function is a cost center c. the end users are billed using a charge-back system d. computer services are organized into small information processing units under the control of end users ANS: D 25. The data control group is responsible for a. performing the day-to-day processing of transactions b. security and integrity of the database c. liaison between the end user and data processing d. providing safe storage for off-line data files ANS: C 26. Data processing does not involve a. data control b. computer operations c. system maintenance d. data conversion ANS: C 27. Independent auditing is performed by a. external auditors b. internal accountants c. licensed auditors d. third-party accountants ANS: A 28. Which individual is least involved in new systems development? a. systems analyst b. external auditor c. end user d. data librarian ANS: D 29. The objectives of all information systems include all of the following except a. support for the stewardship function of management b. evaluating transaction data c. support for the day-to-day operations of the firm d. support for management decision making ANS: B 30. Which individuals may be involved in the Systems Development Life Cycle? a. accountants b. systems professionals c. end users d. all of the above ANS: D 31. An appraisal function housed within the organization that performs a wide range of services for management is a. internal auditing b. data control group c. external auditing d. database administration ANS: A 32. Advantages of a database system include all of the following except a. elimination of data redundancy b. open access to all data by all users c. single update for changes in data d. confidence that all data is current ANS: B 33. Disadvantages of distributed data processing include all of the following except a. mismanagement of organizationwide resources b. hardware and software incompatibility c. cost reductions d. difficulty in hiring qualified IT professionals ANS: C 34. Advantages of distributed data processing include each of the following except a. cost reductions b. better management of organization resources c. improved operational efficiency d. increased user satisfaction ANS: B 35. Disadvantages of the distributed data processing approach include all of the following except a. possible mismanagement of organization resources b. redundancy of tasks c. software incompatibility d. system is not responsive to the user’s situation ANS: D 36. ERP packages include all of the following modules except a. human resources b. general ledger c. inventory management d. they include all of the above ANS: D 37. All of the following are external end users except a. cost accountants b. creditors c. stockholders d. tax authorities ANS: A 38. Useful information must possess all of the following characteristics except a. relevance b. timelessness c. accuracy d. completeness ANS: B 39. The objectives of an information system include each of the following except a. support for the stewardship responsibilities of management b. furthering the financial interests of shareholders c. support for management decision making d. support for the firm’s day-to-day operations ANS: B 40. Accountants play many roles relating to the accounting information system, including all of the following except a. system users b. system designers c. system auditors d. system converters ANS: D SHORT ANSWER 1. Entities outside the organization with a direct or indirect interest in the firm, such as stockholders, financial institutions, and government agencies, are called ____________________. ANS: stakeholders 2. The process of breaking a system into smaller subsystem parts is called ______________________________. ANS: system decomposition 3. Transactions with trading partners include ____________________ and ____________________. ANS: sales, purchases 4. A system is a group of two or more interrelated components that ___________________________________. ANS: serve a common purpose 5. The task of locating and transferring an existing record from the database for processing is called data ____________________. ANS: retrieval 6. Three ways that a business can be divided into segments are by __________________________, __________________________ and by __________________________. ANS: geographic location, product lines, function 7. Three activities that are part of the finance function are __________________________, __________________________, and __________________________. ANS: portfolio management, treasury, credit, cash disbursements, cash receipts 8. Two distinct ways to structure the Data Processing Department are ____________________ and ____________________. ANS: centralized, distributed 9. Two methods to acquire information systems are to __________________________ and to __________________________. ANS: develop customized systems, purchase commercial systems 10. Audits are conducted by ____________________, ____________________, and ____________________ auditors. ANS: internal, external, IT 11. Sales of products to customers, purchases of inventory from vendors, and cash disbursements are all example of __________________________. ANS: financial transactions 12. The three major subsystems of the AIS are _______________________________, ___________________________, and _______________________________. ANS: the transaction processing system, the general ledger/financial reporting system, the management reporting system 13. The __________________________ and __________________________ standards that characterize the AIS clearly distinguish it from the MIS. ANS: legal, professional 14. The transaction processing system is comprised of three cycles: __________________________, __________________________, and __________________________. ANS: revenue, expenditure, conversion 15. The REA model identifies an organization’s ____________________, ____________________, and ____________________. ANS: resources, events, agents. 16. Sarbanes-Oxley legislation requires that management designs and implements controls over the entire financial reporting process. What systems does this include? ANS: This includes the financial reporting system, the general ledger system, and the transaction processing systems that supply the data for financial reporting. 17. Why is it necessary to distinguish between AIS and MIS? ANS: Because of the highly integrative nature of modern information systems, management and auditors need a conceptual view of the information system that distinguishes key processes and areas of risk and legal responsibility from the other (non-legally binding) aspects of the system. Without such a model, critical management and audit responsibilities under SOX may not be met. 18. How has SOX legislation impacted the consulting practices of public accounting firms? ANS: Prior to SOX, a gray area of overlap existed between assurance and consulting services. Auditors were once allowed to provide consulting services to their audit clients. This is now prohibited from doing so under SOX legislation. 19. What is discretionary reporting? ANS: Reports used by management that the company is not obligated by law, regulation, or contract to provide. These are often used for internal problem-solving issues rather than by external constituents. 20. Name the five characteristics of information? ANS: Relevance, accuracy, completeness, summarization, and timeliness. ESSAY 1. Contrast the responsibilities of operations management, middle management, and top management. Explain the different information needs for each level of management. ANS: Operations management is directly responsible for controlling day-to-day operations. Operations managers require detailed information on individual transactions such as sales, shipment of goods, usage of labor and materials in the production process, and internal transfers of resources from one department to another. Budgeting information and instructions flow downward from top and middle management to operations management. Middle managers perform short-term planning and coordination of activities necessary to accomplish organizational objectives. Middle management requires information that is more summarized and oriented toward reporting on overall performance and problems, rather than routine operations. Top management is responsible for longer-term planning and setting organizational objectives. Information provided to top management is highly summarized. 2. Explain the difference between data and information. ANS: Data are facts which may or may not be processed; data have no particular impact on the user. Information is processed data that causes the user to take action. 3. Why do accountants need to understand the organizational structure of the business? ANS: The structure of an organization reflects the distribution of responsibility, authority, and accountability throughout the organization. Accountants need to understand this distribution pattern in order to assess the information needs of users, and to design the Accounting Information System to meet those needs. 4. Several disadvantages of distributed data processing have been discussed. Discuss at least three. ANS: Distributing the control of information resources can lead to mismanagement of organizational resources. Hardware and software incompatibility can result. Distribution of responsibility can result in many users performing redundant tasks. Individual user control can lead to internal control concerns when users perform incompatible duties. Small organizational units may have difficulty hiring qualified IT professionals. Distribution of decision making can result in a lack of standards. 5. Name and explain the purpose of the three major subsystems of the AIS: ANS: TPS GL/FRS records the financial transactions of the firm produces the financial statements etc. required by law MRS provides information to internal management for decision making 6. What are the three primary functions performed by the transaction processing system? ANS: converting economic events into financial transaction, recording financial transaction in the accounting records (journals and ledgers), and distributing essential financial information to operations personnel to support daily operations. 7. The most commonly stated benefits of DDP are cost savings, increased user satisfaction, and improved operational efficiency. Explain. ANS: The costs of both processing and data storage have declined significantly in the time since early automation. In addition, data entry can be distributed and application complexity reduced. Users are typically more satisfied when they can control the resources that affect their profitability. Also users want systems people who will respond to their needs and involve them in development and implementation of their own systems. Delegation of cost control to individual units leads to more efficient use of unit resources. 8. Data redundancy is described as a problem in flat-file systems due to data storage, updating, and currency issues. Explain. ANS: Data that is stored 10 different times takes up 10 times the storage space of data stored once. If data is stored in multiple files, each file must be updated when a change occurs. If the issue of updates is mismanaged in a flat-file environment, some data may be unchanged, therefore be non-current and lead to incorrect decisions. 9. Explain the elements of the REA model and give an example of each. ANS: Economic resources are the assets of the organization. They are objects that are scarce and under the control of the organization. They do not include accounts receivable. An example is inventory. Economic events are actions that affect changes is resources. An example is a sale to a customer. Economic agents are individuals and business units that participate in economic events. An example is a sales clerk. 10. Distinguish between the accounting information system and the management information system. ANS: The AIS processes financial (e.g., cash receipts) and nonfinancial (e.g., addition to the approved vendor list) transactions that directly affect the processing of the financial transaction. These are handled by the three major subsystems: transaction processing, general ledger/financial reporting, and management reporting. The MIS processes additional nonfinancial transactions that contribute to the decision making of managers. 11. Why have re-engineering efforts been made to integrate AIS and MIS? ANS: Managers of all areas typically need data from both the AIS and the MIS. If the data needed by managers for decision-making processes are located in two or more data sets, the preparation of reports is both inefficient and expensive. Further, a lack of coordination between the two data sets can result in data that is not consistent and is unreliable. 12. Why is it important to organizationally separate the accounting function from other functions of the organization? ANS: The accounting function provides record-keeping services for all of the operations and day-to-day activities of other departments, which affect the financial position of the organization. Record keeping tasks must be kept separate from any area that has custody over assets. Thus, the accounting function must remain independent so that the protection of the firm’s assets is carried out in an environment with minimum possibilities for theft. 13. The REA model is based on the premise that “business data must not be preformatted or artificially constrained and must reflect all relevant aspects of the underlying economic events.” What does this mean and how is it applied ANS: The REA model requires that accounting phenomena be characterized in a manner consistent with the development of multiple user views not simply those of the accounting function. As such, REA procedures and databases are structured around events rather than accounting artifacts such as journals, ledgers, charts-of-accounts, and double entry accounting. Under the REA model, business organizations prepare financial statements directly from the event database. 14. ERP systems are comprised of a highly integrated set of standardized modules. Discuss the advantages and potential disadvantages of this approach. ANS: Advantages of ERP Enterprise Resource Planning (ERP) systems enable organizations to automate and integrate key business processes. ERPs break down traditional functional barriers by facilitating data sharing ERP software embodies and supports the best business practices of a given industry thus encouraging positive changes in the way firms do business Organizations experience internal efficiencies by employing standard business practices among all organizational units. Disadvantages of ERP The implementation of an ERP system can be a massive undertaking that can span several years. Because of their complexity and size, few organizations are willing or able to commit the necessary financial resources and incur the risk of developing an ERP system in-house. Hence, virtually all ERPs are commercial products designed to solve standardized business problems. Many organizations have unique needs that require customized systems. Organizations that implement an ERP often need to modify their business processes to suit unique business functions, particularly industry-specific tasks. These applications, often called bolt-ons, are not always designed to communicate with ERP packages. ERP packages are enormously expensive. Organization management should exercise great care in deciding which, if any, ERP is best for them. 15. Distinguish between the centralized and distributed approaches to organizing the computer services function. ANS: In a centralized data processing approach, the computer services function is centrally located. The databases are housed in one place where all of the data processing occurs by one or more main computers. All systems development and maintenance work for the entire organization is performed by systems professionals. End users wishing to have new systems or features must submit a formal request to this group and are usually prioritized and placed in a queue. In a distributed data processing approach, the CPUs are spread out and control over data and processing is at the information processing unit (IPU) level. Thus, end users have more influence over the systems development projects, which are typically handled by systems professionals at the IPU level. Chapter 2—Introduction to Transaction Processing TRUE/FALSE 1. Processing more transactions at a lower unit cost makes batch processing more efficient than real-time systems. ANS: T 2. The process of acquiring raw materials is part of the conversion cycle. ANS: F 3. Directing work-in-process through its various stages of manufacturing is part of the conversion cycle. ANS: T 4. The top portion of the monthly bill from a credit card company is an example of a turn-around document. ANS: T 5. The general journal is used to record recurring transactions that are similar in nature. ANS: F 6. Document flowcharts are used to represent systems at different levels of detail. ANS: F 7. Data flow diagrams represent the physical system. ANS: F 8. Document flowcharts are often used to depict processes that are handled in batches. ANS: T 9. Program flowcharts depict the type of media being used (paper, magnetic tape, or disks) and terminals. ANS: F 10. System flowcharts represent the input sources, programs, and output products of a computer system. ANS: T 11. Program flowcharts are used to describe the logic represented in system flowcharts. ANS: T 12. Batch processing systems can store data on direct access storage devices. ANS: T 13. Backups are automatically produced in a direct access file environment. ANS: F 14. The box symbol represents a temporary file. ANS: F 15. Auditors may prepare program flowcharts to verify the correctness of program logic. ANS: T 16. A control account is a general ledger account which is supported by a subsidiary ledger. ANS: T 17. The most significant characteristic of direct access files is access speed. ANS: T 18. Real time processing is used for routine transactions in large numbers. ANS: F 19. Batch processing is best used when timely information is needed because this method processes data efficiently. ANS: F 20. An inverted triangle with the letter “N” represents a file in “name” order. ANS: F 21. Real-time processing in systems that handle large volumes of transactions each day can create operational inefficiencies. ANS: T 22. Operational inefficiencies occur because accounts unique to many concurrent transactions need to be updated in real time. ANS: F 23. Operational inefficiencies occur because accounts common to many concurrent transactions need to be updated in real time. ANS: T 24. Batch processing of noncritical accounts improves operational efficiency. ANS: T 25. Batch processing of accounts common to many concurrent transactions reduces operational efficiency. ANS: F MULTIPLE CHOICE 1. Which system is not part of the expenditure cycle? a. cash disbursements b. payroll c. production planning/control d. purchases/accounts payable ANS: C 2. Which system produces information used for inventory valuation, budgeting, cost control, performance reporting, and make-buy decisions? a. sales order processing b. purchases/accounts payable c. cash disbursements d. cost accounting ANS: D 3. Which of the following is a turn-around document? a. remittance advice b. sales order c. purchase order d. payroll check ANS: A 4. The order of the entries made in the ledger is by a. transaction number b. account number c. date d. user ANS: B 5. The order of the entries made in the general journal is by a. date b. account number c. user d. customer number ANS: A 6. In general a special journal would not be used to record a. sales b. cash disbursements c. depreciation d. purchases ANS: C 7. Which account is least likely to have a subsidiary ledger? a. sales b. accounts receivable c. fixed assets d. inventory ANS: A 8. Subsidiary ledgers are used in manual accounting environments. What file is comparable to a subsidiary ledger in a computerized environment? a. archive file b. reference file c. transaction file d. master file ANS: D 9. A journal is used in manual accounting environments. What file is comparable to a journal in a computerized environment? a. archive file b. reference file c. transaction file d. master file ANS: C 10. In a computerized environment, a list of authorized suppliers would be found in the a. master file b. transaction file c. reference file d. archive file ANS: C 11. Which of the following is an archive file? a. an accounts payable subsidiary ledger b. a cash receipts file c. a sales journal d. a file of accounts receivable that have been written off ANS: D 12. Which document is not a type of source document? a. a sales order b. an employee time card c. a paycheck d. a sales return receipt ANS: C 13. The most important purpose of a turn-around document is to a. serve as a source document b. inform a customer of the outstanding amount payable c. provide an audit trail for the external auditor d. inform the bank of electronic funds deposits ANS: A 14. Which type of graphical documentation represents systems at different levels of detail? a. data flow diagram b. document flowchart c. system flowchart d. program flowchart ANS: A 15. Data flow diagrams a. depict logical tasks that are being performed, but not who is performing them b. illustrate the relationship between processes, and the documents that flow between them and trigger activities c. represent relationships between key elements of the computer system d. describe in detail the logic of the process ANS: A 16. Document flowcharts a. depict logical tasks that are being performed, but not who is performing them b. illustrate the relationship between processes, and the documents that flow between them and trigger activities c. represent relationships between key elements of the computer system d. describe the logic of the process ANS: B 17. When determining the batch size, which consideration is the least important? a. achieving economies by grouping together large numbers of transactions b. complying with legal mandates c. providing control over the transaction process d. balancing the trade off between batch size and error detection ANS: B 18. In contrast to a real-time system, in a batch processing system a. there is a lag between the time when the economic event occurs and the financial records are updated b. relatively more resources are required c. a greater resource commitment per unit of output is required d. processing takes place when the economic event occurs ANS: A 19. In contrast to a batch processing system, in a real-time system a. a lag occurs between the time of the economic event and when the transaction is recorded b. relatively fewer hardware, programming, and training resources are required c. a lesser resource commitment per unit of output is required d. processing takes place when the economic event occurs ANS: D 20. The type of transaction most suitable for batch processing is a. airline reservations b. credit authorization c. payroll processing d. adjustments to perpetual inventory ANS: C 21. The type of transaction most suitable for real-time processing is a. recording fixed asset purchases b. recording interest earned on long-term bonds c. adjusting prepaid insurance d. recording a sale on account ANS: D 22. Which step is not found in batch processing using sequential files? a. control totals b. sort runs c. edit runs d. immediate feedback of data entry errors ANS: D 23. Both the revenue and the expenditure cycle can be viewed as having two key parts. These are a. manual and computerized b. physical and financial c. input and output d. batch and real-time ANS: B 24. All of the following can provide evidence of an economic event except a. source document b. turn-around document c. master document d. product document ANS: C 25. Which method of processing does not use the destructive update approach? a. batch processing using direct access files b. real-time processing c. batch processing using sequential files d. all of the above use the destructive update approach ANS: C 26. Which symbol represents a data store? a. b. c. d. ANS: B 27. Which symbol represents a manual operation? a. b. c. d. ANS: D 28. Which symbol represents accounting records? a. b. c. d. ANS: A 29. Which symbol represents a document? a. b. c. d. ANS: B 30. Which symbol represents a magnetic tape (sequential storage device)? a. b. c. d. ANS: D 31. Which symbol represents a decision? a. b. c. d. ANS: A 32. The characteristics that distinguish between batch and real-time systems include all of the following except a. time frame b. resources used c. file format d. efficiency of processing ANS: C 33. A file that stores data used as a standard when processing transactions is a. a reference file b. a master file c. a transaction file d. an archive file ANS: A 34. Sequential storage means a. data is stored on tape b. access is achieved through an index c. access is direct d. reading record 100 requires first reading records 1 to 99 ANS: D 35. Real-time processing would be most beneficial in handling a firm’s a. fixed asset records b. retained earning information c. merchandise inventory d. depreciation records ANS: C 36. Which accounting application is least suited for batch processing? a. general ledger b. vendor payments c. sales order processing d. payroll ANS: C 37. Which accounting application is best suited for batch processing? a. general ledger b. vendor payments c. sales order processing d. payroll ANS: D 38. Operational inefficiencies occur because a. accounts both common and unique to many concurrent transactions need to be updated in real time. b. accounts common to many concurrent transactions need to be updated in real time. c. accounts unique to many concurrent transactions need to be updated in real time. d. None of the above are true statements ANS: B 39. Operational efficiencies can be improved by a. updating accounts both common and unique to many concurrent transactions in real time. b. updating accounts both common and unique to many concurrent transactions in batch mode. c. updating accounts unique to many concurrent transactions in real time and updating common accounts in batch mode. d. None of the above are true statements ANS: C SHORT ANSWER 1. List two of the three transaction cycles. ANS: expenditure cycle, conversion cycle, revenue cycle 2. Documents that are created at the beginning of the transaction are called __________________________. ANS: source documents 3. ______________________________________ are the two data processing approaches used in modern systems. ANS: Batch processing and real-time processing 4. Give a specific example of a turn-around document. ANS: credit card, electricity, water, or telephone bill, etc. 5. Explain when it is appropriate to use special journals. ANS: Special journals are used to record large volumes of recurring transactions that are similar in nature. 6. What are the subsystems of the revenue cycle? ANS: sales order processing, cash receipts 7. What are the subsystems of the expenditure cycle? ANS: purchasing, cash disbursements, payroll 8. Most organizations have replaced the general journal with a _______________________________. ANS: journal voucher system 9. Provide a specific example of a general ledger account and a corresponding subsidiary ledger. ANS: accounts receivable control account and accounts receivable subsidiary, accounts payable control account and accounts payable subsidiary, inventory control and a subsidiary of specific inventory items, fixed asset control account and a subsidiary of specific fixed assets, notes receivable/payable and individual notes receivable and payable 10. Name five documentation techniques? ANS: entity-relationship diagrams, data flow diagrams, document flowcharts, system flowcharts, program flowcharts 11. Why is the audit trail important? ANS: The audit trail is used to track transactions from the source document to the financial statements and vice versa. Accountants use the audit trail to correct errors, answer queries, and perform audits. 12. List a method of data processing that uses the destructive update approach? ANS: batch method using direct access files or real-time processing 13. Only four symbols are used in data flow diagrams. What are they? ANS: process, data store, data flow, entity 14. Which flowchart depicts the relationship between processes and the documents that flow between them and trigger activities? ANS: document flowcharts 15. What are the three characteristics that are used to distinguish between batch and real-time systems. ANS: time lag, resource use, efficiency 16. Give one advantages of real-time data collection. ANS: certain transaction errors can be prevented or detected and corrected at their source. 17. In one sentence, what does updating a master file record involve? ANS: Updating a master file record involves changing the value of one or more of its variable fields to reflect the effects of a transaction. 18. What is destructive update? ANS: Destructive update involves replacing an old data value with a new value and thus destroying the original. ESSAY 1. Describe the key activities in the revenue, conversion, and expenditure cycles. ANS: Revenue cycle: Sales order processing involves preparation of sales orders, credit granting, shipment and billing. Cash receipts collects cash and makes bank deposits. Conversion cycle: Production system involves planning, scheduling, and control of the manufacturing process. Cost accounting system monitors the flow of cost information related to production. Expenditure cycle: Purchases/accounts payable involves the acquisition of physical inventory. Cash disbursements authorizes payment and disburses funds. Payroll monitors labor usage and disburses paychecks to employees. 2. Categorize each of the following activities into the expenditure, conversion or revenue cycles and identify the applicable subsystem. a. Preparing the weekly payroll for manufacturing personnel. b. Releasing raw materials for use in the manufacturing cycle. c. Recording the receipt of payment for goods sold. d. Recording the order placed by a customer. e. Ordering raw materials. f. Determining the amount of raw materials to order. ANS: a. Expenditure cycle-payroll subsystem. b. Conversion cycle-production system subsystem. c. Expenditure cycle-accounts payable subsystem. d. Revenue cycle-sales order processing subsystem. e. Expenditure cycle-purchases subsystem. f. Conversion cycle-production subsystem. 3. What does an entity-relationship diagram represent? Why do accountants need to understand them? ANS: Entity-relationship diagrams represent the relationship between entities in a system. An entity is either 1) a resource (such as cash or inventory), 2) an event (such as a sale or a receipt of cash), or 3) an agent (such as a customer or vendor). ERDs represent the relationship between entities graphically. ERDs are used in the design of databases. 4. Time lag is one characteristic used to distinguish between batch and real-time systems. Explain. Give an example of when each is a realistic choice. ANS: Batch processing collects similar transactions into groups (batches) and processes them all at once. Hence, affected files are up to date immediately after the update, but can be expected to be out of date until the next run. Hence, there is a time lag between the event and its recording in the system. A payroll system is often handled with batch processing since it must be up to date at fixed time periods and need not be modified between pay dates. Real-time systems process each transaction as it occurs and files are always up to date–there is no time lag. This is preferred when there may be a need to query the system for the status of transactions. A sales order processing system would benefit from real-time processing. Hence, customer questions could be answered easily, without waiting for the next update (as would be required if the system was batch). 5. There are two subsystems to the revenue cycle. What are they and what occurs within each? ANS: The two subsystems of the revenue cycle are sales order processing and cash receipts. In the sales order processing subsystem, the sales order is processed, credit granted, goods are shipped, customer is billed, and related files updated (sales, accounts receivable, inventory, etc.). In the cash receipts subsystem, cash is collected and deposited in the bank and files updated (cash, accounts receivable, etc.). 6. Resource use is one characteristic used to distinguish between batch and real-time systems. Explain. ANS: Batch processing typically requires the use of fewer resources including programmer time and effort, computer time, hardware, and user training. Real-time systems require significantly more programming time, especially in the development of the user interface, often require much more computer time, and more expensive hardware, even a dedicated processor. 7. Give a brief description of each of the following documentation techniques: document flowchart, systems flowchart, and program flowchart. ANS: Document flowcharts present the entities of a system (especially in manual systems): records (e.g., documents, journals, ledgers, and files), the organizational units involved in the process, and the activities performed in each unit. System flowcharts portray the relationships between source data, transaction files, computer programs, master files, and output, including the form or type of media of each. Program flowcharts represent the logic of a particular program. Each step is represented by a separate symbol, each of which represents one or more lines of computer instructions. The order of the steps is represented by the flow lines. 8. Give an example of how cardinality relates to business policy? ANS: Cardinality reflects normal business rules as well as organizational policy. For instance, the 1:1 cardinality between the entities “Salesperson” and “Company Car” suggests that each salesperson in the organization is assigned one company car. If instead the organization’s policy were to assign a single automobile to one or more salespersons who share it, this policy would be reflected by a 1:M relationship. 9. For what purpose are ER diagrams used? ANS: An entity relationship (ER) diagram is a documentation technique used to represent the relationship between entities. One common use for ER diagrams is to model an organization’s database. 10. What is an entity? ANS: Entities are physical resources (automobiles, cash, or inventory), events (ordering inventory, receiving cash, shipping goods) and agents (salesperson, customer, or vendor) about which the organization wishes to capture data. 11. Is a DFD an effective documentation technique for identifying who or what performs a particular task? Explain. ANS: No. A DFD shows which tasks are being performed, but not who performs them. It depicts the logical system. 12. Is a flowchart an effective documentation technique for identifying who or what performs a particular task? Explain. ANS: Yes. A flowchart depicts the physical system and illustrates who, what, and where a task is performed. 13. How may batch processing be used to improve operational efficiency? ANS: A single transaction may affect several different accounts. Some of these accounts, however, may not need to be updated in real-time. In fact, the task of doing so takes time which, when multiplied by hundreds or thousands of transactions, can cause significant processing delays. Batch processing of non-critical accounts, however, improves operational efficiency by eliminating unnecessary activities at critical points in the process. 14. If an organization processes large numbers of transactions that use common data records, what type of system would work best (all else being equal)? ANS: Large-scale systems that process high volumes of transactions, often use real-time data collection and batch updating. Master file records that are unique to a transaction such as customer accounts and individual inventory records can be updated in real time without causing operational delays. Common accounts should be updated in batch mode. Real-time processing is better suited to systems that process lower transaction volumes and those that do not share common records. 15. Why might an auditor use a program flowchart? ANS: When testing an application program, the auditor needs details about its internal logic provided by the program flowchart to design the audit tests. 16. How are computer system flowcharts and program flowcharts related? ANS: The system flowchart shows the relationship between two computer programs, the files that they use, and the outputs that they produce. However, this level of documentation does not provide the operational details that are sometimes needed An auditor wishing to assess the correctness a program’s logic cannot do so from the system flowchart. A program flowchart provides this detail. Every program represented in a system flowchart should have a supporting program flowchart that describes its logic. 17. What are the key distinguishing features of legacy systems? ANS: Legacy systems tend to have the following distinguishing features: they are mainframe based applications; they tend to be batch oriented; early legacy systems use flat-files for data storage, however, hierarchical and network databases are often associated with later era legacy systems. These highly structured and inflexible storage systems promote a single-user environment that discourages information integration within business organizations. 18. What information is provided by a record layout diagram? ANS: Record layout diagrams are used to reveal the internal structure of the records that constitute a file or database table. The layout diagram usually shows the name, data type, and length of each attribute (or field) in the record. 19. Comment on the following statement: “Legacy systems use flat file structures.” ANS: A flat-file structure is a single-view model that characterizes legacy systems in which data files are structured, formatted, and arranged to suit the specific needs of the owner or primary user of the system. Such structuring, however, may omit or corrupt data attributes that are essential to other users, thus preventing successful integration of systems across the organization. 20. What factor influences the decision to employ real-time data collection with batch updating rather that purely real-time processing? Explain. ANS: Transaction volume is the key factor. Large scale systems that process high volumes of transactions, often use real-time data collection and batch updating. Master file records that are unique to a transaction such as customer accounts and individual inventory records can be updated in real time without causing operational delays. Common accounts should be updated in batch mode. Real-time processing is better suited to systems that process lower transaction volumes and those that do not share common records. 21. How is backup of database files accomplished? ANS: Each record in a database file is assigned a unique disk location or address that is determined by its primary key value. Because only a single valid location exists for each record, updating the record must occur in-place. APPENDIX QUESTION 22. Contrast procedures for preparing backups in a sequential file environment and direct access file environment. ANS: The finished product of a sequential file update process is a new physical master file. The new file contains all the records from the original file, including records updated by transactions, as well as those unprocessed and copied in their original state. The old master file continues to exist in its original form. This feature provides an automatic backup capability called the Grandfather-Father-Son approach. The father is the original master file and the son is the newly created (updated) file. Following the next file update, the father become the grandfather, the son becomes the father, and the new file is the new son. If the current master is destroyed, the backup file (grandfather or father) can be restored and transactions can be reprocessed. In the direct access file environment, the destructive update approach is used. The original value in an account on the master file is “destroyed” and replaced with the new value. This approach leaves no backup copy of the master file after the update process. If the current version of the master file is damaged, there is no version of the master file to use to reconstruct the data. Therefore, special backup procedures must be implemented. Before processing, the master file must be copied to create a backup file. If the master file is destroyed, the backup copy of the master file and a copy of the transaction file are used to recreate the new master file. 23. Explain how a hashing structure works and why it is quicker than using an index. Give an example. If it so much faster, why isn't it used exclusively? ANS: A hashing structure typically works by taking a key value and using it to divide a prime number. The result is a unique number almost all of the time if enough decimal places are used. The resulting numbers are used to find the unique location of the record. Calculating a record's address is faster than searching for it through an index. It is not used exclusively because it does not use the storage disk efficiently. Some disk locations will never be selected because they do not correspond to legitimate key values. Also, different record keys may sometimes translate to the same address and data collision could occur. A way around this exists using pointers, but the additional pointers slow down the system. 24. Explain the following three types of pointers: physical address pointer, relative address pointer, and logical key pointer. ANS: A physical address pointer contains the actual disk storage location (cylinder, surface, and record number) needed by the disk controller. This approach allows the system to access the record directly without obtaining further information. A relative address pointer contains the relative position of a record in the file. This address (i.e., the 200th record on the file) must be further manipulated to convert it to the actual physical address. The conversion software determines this by using the physical address of the beginning of the file, the length of each record in the file, and the relative address of the record being sought. A logical key pointer contains the primary key of the related record. This key value is then converted into the record’s physical address by a hashing algorithm. Chapter 3—Ethics, Fraud, and Internal Control TRUE/FALSE 1. The ethical principle of justice asserts that the benefits of the decision should be distributed fairly to those who share the risks. ANS: T 2. The ethical principle of informed consent suggests that the decision should be implemented so as to minimize all of the risks and to avoid any unnecessary risks. ANS: F 3. Employees should be made aware of the firm’s commitment to ethics. ANS: T 4. Business ethics is the analysis of the nature and social impact of computer technology, and the corresponding formulation and justification of policies for the ethical use of such technology. ANS: F 5. Para computer ethics is the exposure to stories and reports found in the popular media regarding the good or bad ramifications of computer technology. ANS: F 6. Source code is an example of intellectual property. ANS: T 7. Copyright laws and computer industry standards have been developed jointly and rarely conflict. ANS: F 8. Business bankruptcy cases always involve fraudulent behavior. ANS: F 9. Defalcation is another word for financial fraud. ANS: T 10. The trend toward distributed data processing increases the exposure to fraud from remote locations. ANS: T 11. The external auditor is responsible for establishing and maintaining the internal control system. ANS: F 12. Segregation of duties is an example of an internal control procedure. ANS: T 13. Controls in a computer-based information system are identical to controls in a manual system. ANS: F 14. Preventive controls are passive techniques designed to reduce fraud. ANS: T 15. Ethical issues and legal issues are essentially the same. ANS: F 16. Internal control systems are recommended but not required of firms subject to the Foreign Corrupt Practices Act. ANS: F 17. Operations fraud is the misuse or theft of the firm’s computer resources. ANS: T 18. The Foreign Corrupt Practices Act requires only that a firm keep good records. ANS: F 19. A key modifying assumption in internal control is that the internal control system is the responsibility of management. ANS: T 20. Database management fraud includes altering, updating, and deleting an organization’s data. ANS: F 21. While the Sarbanes-Oxley Act prohibits auditors from providing non-accounting services to their audit clients, they are not prohibited from performing such services for non-audit clients or privately held companies. ANS: T 22. The Sarbanes-Oxley Act requires the audit committee to hire and oversee the external auditors. ANS: T 23. Section 404 requires that corporate management (including the CEO) certify their organization’s internal controls on a quarterly and annual basis. ANS: F 24. Section 302 requires the management of public companies to assess and formally report on the effectiveness of their organization’s internal controls. ANS: F 25. The objective of SAS 99 is to seamlessly blend the auditor’s consideration of fraud into all phases of the audit process. ANS: T MULTIPLE CHOICE 1. Which ethical principle states that the benefit from a decision must outweigh the risks, and that there is no alternative decision that provides the same or greater benefit with less risk? a. minimize risk b. justice c. informed consent d. proportionality ANS: D 2. Individuals who acquire some level of skill and knowledge in the field of computer ethics are involved in which level of computer ethics? a. para computer ethics b. pop computer ethics c. theoretical computer ethics d. practical computer ethics ANS: A 3. All of the following are issues of computer security except a. releasing incorrect data to authorized individuals b. permitting computer operators unlimited access to the computer room c. permitting access to data by unauthorized individuals d. providing correct data to unauthorized individuals ANS: B 4. Which characteristic is not associated with software as intellectual property? a. uniqueness of the product b. possibility of exact replication c. automated monitoring to detect intruders d. ease of dissemination ANS: C 5. For an action to be called fraudulent, all of the following conditions are required except a. poor judgment b. false representation c. intent to deceive d. injury or loss ANS: A 6. One characteristic of employee fraud is that the fraud a. b. c. d. is perpetrated at a level to which internal controls do not apply involves misstating financial statements involves the direct conversion of cash or other assets to the employee’s personal benefit involves misappropriating assets in a series of complex transactions involving third parties ANS: C 7. Forces which may permit fraud to occur do not include a. a gambling addiction b. lack of segregation of duties c. centralized decision making environment d. questionable integrity of employees ANS: C 8. Which of the following best describes lapping? a. applying cash receipts to a different customer’s account in an attempt to conceal previous thefts of funds b. inflating bank balances by transferring money among different bank accounts c. expensing an asset that has been stolen d. creating a false transaction ANS: A 9. Operations fraud includes a. altering program logic to cause the application to process data incorrectly b. misusing the firm’s computer resources c. destroying or corrupting a program’s logic using a computer virus d. creating illegal programs that can access data files to alter, delete, or insert values ANS: B 10. Who is responsible for establishing and maintaining the internal control system? a. the internal auditor b. the accountant c. management d. the external auditor ANS: C 11. The concept of reasonable assurance suggests that a. the cost of an internal control should be less than the benefit it provides b. a well-designed system of internal controls will detect all fraudulent activity c. the objectives achieved by an internal control system vary depending on the data processing method d. the effectiveness of internal controls is a function of the industry environment ANS: A 12. Which of the following is not a limitation of the internal control system? a. errors are made due to employee fatigue b. fraud occurs because of collusion between two employees c. the industry is inherently risky d. management instructs the bookkeeper to make fraudulent journal entries ANS: C 13. The most cost-effective type of internal control is a. preventive control b. accounting control c. detective control d. corrective control ANS: A 14. Which of the following is a preventive control? a. credit check before approving a sale on account b. bank reconciliation c. physical inventory count d. comparing the accounts receivable subsidiary ledger to the control account ANS: A 15. A well-designed purchase order is an example of a a. preventive control b. detective control c. corrective control d. none of the above ANS: A 16. A physical inventory count is an example of a a. preventive control b. detective control c. corrective control d. feedforward control ANS: B 17. The bank reconciliation uncovered a transposition error in the books. This is an example of a a. preventive control b. detective control c. corrective control d. none of the above ANS: B 18. In balancing the risks and benefits that are part of every ethical decision, managers receive guidance from each of the following except a. justice b. self interest c. risk minimization d. proportionality ANS: B 19. Which of the following is not an element of the internal control environment? a. management philosophy and operating style b. organizational structure of the firm c. well-designed documents and records d. the functioning of the board of directors and the audit committee ANS: C 20. Which of the following suggests a weakness in the internal control environment? a. the firm has an up-to-date organizational chart b. monthly reports comparing actual performance to budget are distributed to managers c. performance evaluations are prepared every three years d. the audit committee meets quarterly with the external auditors ANS: C 21. Which of the following indicates a strong internal control environment? a. the internal audit group reports to the audit committee of the board of directors b. there is no segregation of duties between organization functions c. there are questions about the integrity of management d. adverse business conditions exist in the industry ANS: A 22. According to SAS 78, an effective accounting system performs all of the following except a. identifies and records all valid financial transactions b. records financial transactions in the appropriate accounting period c. separates the duties of data entry and report generation d. records all financial transactions promptly ANS: C 23. Which of the following is the best reason to separate duties in a manual system? a. to avoid collusion between the programmer and the computer operator b. to ensure that supervision is not required c. to prevent the record keeper from authorizing transactions d. to enable the firm to function more efficiently ANS: C 24. Segregation of duties in the computer-based information system includes a. separating the programmer from the computer operator b. preventing management override c. separating the inventory process from the billing process d. performing independent verifications by the computer operator ANS: A 25. Which of the following is not an internal control procedure? a. authorization b. management’s operating style c. independent verification d. accounting records ANS: B 26. The decision to extend credit beyond the normal credit limit is an example of a. independent verification b. authorization c. segregation of functions d. supervision ANS: B 27. When duties cannot be segregated, the most important internal control procedure is a. supervision b. independent verification c. access controls d. accounting records ANS: A 28. An accounting system that maintains an adequate audit trail is implementing which internal control procedure? a. access controls b. segregation of functions c. independent verification d. accounting records ANS: D 29. Employee fraud involves three steps. Of the following, which is not involved? a. concealing the crime to avoid detection b. stealing something of value c. misstating financial statements d. converting the asset to a usable form ANS: C 30. Which of the following is not an example of independent verification? a. comparing fixed assets on hand to the accounting records b. performing a bank reconciliation c. comparing the accounts payable subsidiary ledger to the control account d. permitting authorized users only to access the accounting system ANS: D 31. The importance to the accounting profession of the Foreign Corrupt Practices Act of 1977 is that a. bribery will be eliminated b. management will not override the company’s internal controls c. firms are required to have an effective internal control system d. firms will not be exposed to lawsuits ANS: C 32. The board of directors consists entirely of personal friends of the chief executive officer. This indicates a weakness in a. the accounting system b. the control environment c. control procedures d. this is not a weakness ANS: B 33. Computer fraud can take on many forms, including each of the following except a. theft or illegal use of computer-readable information b. theft, misuse, or misappropriation of computer equipment c. theft, misuse, or misappropriation of assets by altering computer-readable records and files d. theft, misuse, or misappropriation of printer supplies ANS: D 34. When certain customers made cash payments to reduce their accounts receivable, the bookkeeper embezzled the cash and wrote off the accounts as uncollectible. Which control procedure would most likely prevent this irregularity? a. segregation of duties b. accounting records c. accounting system d. access controls ANS: A 35. The office manager forgot to record in the accounting records the daily bank deposit. Which control procedure would most likely prevent or detect this error? a. segregation of duties b. independent verification c. accounting records d. supervision ANS: B 36. Business ethics involves a. how managers decide on what is right in conducting business b. how managers achieve what they decide is right for the business c. both a and b d. none of the above ANS: C 37. All of the following are conditions for fraud except a. false representation b. injury or loss c. intent d. material reliance ANS: D 38. The four principal types of fraud include all of the following except a. bribery b. gratuities c. conflict of interest d. economic extortion ANS: B 39. The characteristics of useful information include a. summarization, relevance, timeliness, accuracy, and completeness b. relevance, summarization, accuracy, timelessness, and completeness c. timeliness, relevance, summarization, accuracy, and conciseness d. disaggregation, relevance, timeliness, accuracy, and completeness ANS: A 40. Internal control system have limitations. These include a. b. c. d. possibility of honest error circumvention management override stability of systems ANS: D 41. Management can expect various benefits to follow from implementing a system of strong internal control. Which of the following benefits is least likely to occur? a. reduced cost of an external audit. b. prevents employee collusion to commit fraud. c. availability of reliable data for decision-making purposes. d. some assurance of compliance with the Foreign Corrupt Practices Act of 1977. e. some assurance that important documents and records are protected. ANS: B 42. Which of the following situations is not a segregation of duties violation? a. The treasurer has the authority to sign checks but gives the signature block to the assistant treasurer to run the check-signing machine. b. The warehouse clerk, who has the custodial responsibility over inventory in the warehouse, selects the vendor and authorizes purchases when inventories are low. c. The sales manager has the responsibility to approve credit and the authority to write off accounts. d. The department time clerk is given the undistributed payroll checks to mail to absent employees. e. The accounting clerk who shares the record keeping responsibility for the accounts receivable subsidiary ledger performs the monthly reconciliation of the subsidiary ledger and the control account. ANS: B 43. Which of the following is not an issue to be addressed in a business code of ethics required by the SEC? a. Conflicts of interest b. Full and Fair Disclosures c. Legal Compliance d. Internal Reporting of Code Violations e. All of the above are issues to be addressed ANS: E SHORT ANSWER 1. What are the main issues to be addressed in a business code of ethics required by the SEC? ANS: Conflicts of interest, Full and Fair Disclosures, Legal Compliance, Internal Reporting of Code Violations, Accountability 2. List the four broad objectives of the internal control system. ANS: safeguard assets, ensure the accuracy and reliability of accounting records, promote organizational efficiency, comply with management’s policies and procedures 3. Explain the purpose of the PCAOB ANS: The PCAOB is empowered to set auditing, quality control, and ethics standards; to inspect registered accounting firms; to conduct investigations; and to take disciplinary actions. 4. What are the five internal control components described in the SAS 78 / COSO framework ANS: the control environment, risk assessment, information and communication, monitoring, and control activities 5. What are management responsibilities under section 302 and 404? ANS: Section 302 requires that corporate management (including the CEO) certify their organization’s internal controls on a quarterly and annual basis. Section 404 requires the management of public companies to assess and formally report on the effectiveness of their organization’s internal controls. 6. Identify to indicate whether each procedure is a preventive or detective control. a. authorizing a credit sale Preventive Detective b. preparing a bank reconciliation Preventive Detective c. locking the warehouse Preventive Detective d. preparing a trial balance Preventive Detective e. counting inventory Preventive Detective ANS: A. preventive; B. detective; C. preventive; D. detective; E. detective Use the internal control procedures listed below to complete the statements. segregation of duties general authorization access controls supervision specific authorization accounting records independent verification 7. A clerk reorders 250 items when the inventory falls below 25 items. This is an example of __________________________. ANS: general authorization 8. The internal audit department recalculates payroll for several employees each pay period. This is an example of __________________________. ANS: independent verification 9. Locking petty cash in a safe is an example of __________________________. ANS: access controls 10. Approving a price reduction because goods are damaged is an example of __________________________. ANS: specific authorization 11. Using cameras to monitor the activities of cashiers is an example of __________________________. ANS: supervision 12. Not permitting the computer programmer to enter the computer room is an example of _______________________________. ANS: segregation of duties 13. Sequentially numbering all sales invoices is an example of __________________________. ANS: accounting records 14. What are the five conditions necessary for an act to be considered fraudulent? ANS: false representation, material fact, intent, justifiable reliance, and injury or loss 15. What is the objective of SAS 99? ANS: The objective of SAS 99 is to seamlessly blend the auditor’s consideration of fraud into all phases of the audit process. 16. Distinguish between exposure and risk. ANS: Exposure is the absence or weakness of a control which increases the firm’s risk of financial loss or injury. Risk is the probability of incurring such a loss or injury. 17. Explain the characteristics of management fraud. ANS: Management fraud typically occurs at levels above where the internal control system is effective. Financial statements are frequently modified to make the firm appear more healthy than it actually is. If any misappropriation of assets occurs, it is usually well hidden. 18. The text discusses many questions about personal traits of employees which might help uncover fraudulent activity. What are three? ANS: executives: with high personal debt, living beyond their means, engaged in habitual gambling, appear to abuse alcohol or drugs, appear to lack personal codes of ethics, appear to be unstable 19. Give two examples of employee fraud and explain how the theft might occur. ANS: Charges to expense accounts: Cash could be stolen and charged to a miscellaneous expense account. Once the account is closed, detection would be more difficult. Lapping: This involves converting cash receipts to personal use. If a customer’s check is taken, his/her balance will not reflect a payment and will be detected when a statement is sent. In order to conceal this fraud, a later payment is used to cover the stolen check. This is in effect a small scale Ponzi scheme. 20. What are the six broad classes of physical control activities defined by SAS 78? ANS: Transaction authorization, segregation of duties, supervision, access controls, accounting records, independent verification ESSAY 1. The text describes six internal control activities. List four of them and provide a specific example of each one. ANS: Control Activity Authorization Example general (purchase of inventory when level drops) or specific (credit approval beyond normal limit) Segregation of functions separate authorization from processing separate custody of assets from record keeping Supervision Accounting records required when separation of duties is not possible, such as opening the mail (cash receipts) maintain an adequate audit trail Access controls maintain physical security Independent verification bank reconciliation, physical inventory count 2. Contrast management fraud with employee fraud. ANS: Employee fraud is usually designed to directly convert cash or other assets to the employee’s personal benefit. Management fraud involves less of a direct benefit to the perpetrator. Management fraud may involve an attempt to misstate financial performance in order to gain additional compensation or to earn a promotion. Management fraud may also involve an attempt to misstate financial performance in order to increase the price of the company’s stock or to reduce the cost of debt. 3. Discuss the importance of the Foreign Corrupt Practices Act of 1977 to the accounting profession. ANS: The Foreign Corrupt Practices Act of 1977 (FCPA) is a law that requires all companies registered with the Securities and Exchange Commission to: keep records that fairly and reasonably reflect the transactions of the firm and its financial position maintain a system of internal control that provides reasonable assurance that the organization’s objectives are met As a result of the Foreign Corrupt Practices Act of 1977, management devotes substantial time to developing and maintaining the internal control structure because failure to do so violates the FCPA and could lead to heavy fines and imprisonment. Accountants are key participants in establishing and maintaining the internal control structure. Therefore, it is accountants who are instrumental in ensuring that the firm is in compliance with the Foreign Corrupt Practices Act of 1977. 4. Why are the computer ethics issues of privacy, security, and property ownership of interest to accountants? ANS: Privacy is a concern because the nature of computer data files makes it possible for unauthorized individuals to obtain information without it being recognized as “missing” from its original location. Security is a concern because its absence makes control from a privacy viewpoint questionable. In addition lack of security may permit unauthorized changes to data, therefore distorting information that is reported. Property ownership raises issues of legitimacy of organizational software, valuation of assets, and questions of lost revenues. 5. According to common law, there are five conditions that must be present for an act to be deemed fraudulent. Name and explain each. ANS: In order for an act to be deemed fraudulent under common law, it must possess the following characteristics: false representation, meaning some misrepresentation or omission must have occurred, material facts, meaning that the facts must influence someone’s actions, intent, meaning there must have been the intention to deceive others, justifiable reliance, meaning it did affect someone’s decision, and injury or loss must have occurred. 6. Management fraud is regarded as more serious than employee fraud. Three special characteristics have been discussed for management fraud. What are they? Explain. ANS: It usually occurs at levels above the normal internal control system. There is typically an intent to present a better picture of the business than is valid, often to deceive creditors and/or shareholders. If assets are misappropriated, the route is quite devious involving a maze of business transactions. 7. Four principal types of corruption are discussed. Name all four and explain at least two. ANS: Corruption involves an executive, manager, or employee of a business working in collusion with an outsider. The four principal types of corruption are: bribery, illegal gratuities, conflicts of interest, and economic extortion. Bribery involves giving, offering, soliciting, or receiving things of value to influence an official in the performance of his or her lawful duties. An illegal gratuity involves giving. receiving, offering, or soliciting something of value because of an official act that has been taken. A conflict of interest occurs when an employee acts on behalf of a third party during the discharge of his or her duties or has self-interest in the activity being performed. Economic extortion is the use (or threat) of force (including economic sanctions) by an individual or organization to obtain something of value. 8. Misappropriation of assets can involve various schemes: charges to expense accounts, lapping, and transaction fraud. Explain each and give an example. ANS: Charges to expense accounts involve fictitious charges to such accounts as miscellaneous expense to offset theft of an asset. Because the expense account is closed to revenue at the end of the period, the period in which it could be detected is short. Lapping is a technique whereby an early theft is covered up by a later one, i.e., with the moves “lapping” over each other. The simplest example involves taking a customer’s payment. A later payment is then credited to the first customer’s account, not the second. And on it goes. This requires some control over billing to avoid tipping off the last customer. Transaction fraud involves deleting, altering, or adding false transactions to divert assets to the perpetrator. For example, if an employee leaves the business and the supervisor fails to notify payroll and continues to clock the employee in and out, a fraudulent paycheck would be produced. If, in addition, the supervisor distributes the paycheck, it can be kept, and cashed. 9. Computer fraud is easiest at the data collection stage. Why? ANS: Computer fraud is easiest at the data collection stage because much of what occurs after the data collection or input stage is not visible to human eyes. Once entered, the system will presume that the input is legitimate and will process it as all others. 10. Explain why collusion between employees and management in the commission of a fraud is difficult to both prevent and detect. ANS: Collusion among employees in the commission of a fraud is difficult to both prevent and detect. This is particularly true when the collusion is between managers and their subordinate employees. Management plays a key role in the internal control structure of an organization. They are relied upon to prevent and detect fraud among their subordinates. When they participate in fraud with the employees over whom they are supposed to provide oversight, the organization’s control structure is weakened, or completely circumvented, and the company becomes more vulnerable to losses. 11. Since all fraud involves some form of financial misstatement, how is Fraudulent Statement fraud different? ANS: Fraudulent statements are associated with management fraud. While all fraud involves some form of financial misstatement, to meet the definition under this class of fraud scheme, the statement itself must bring direct or indirect financial benefit to the perpetrator. In other words, the statement is not simply a vehicle for obscuring or covering a fraudulent act. For example, misstating the cash account balance to cover the theft of cash does not fall under this class of fraud scheme. On the other hand, understating liabilities to present a more favorable financial picture of the organization to drive up stock prices does qualify. 12. Explain the problems associated with lack of auditor independence. ANS: Auditing firms who are also engaged by their clients to perform non-accounting activities such as actuarial services, internal audit outsourcing services, and consulting lack independence. They are essentially auditing their own work. This risk is that as auditors they will not bring to management’s attention detected problems that may adversely affect their consulting fees. For example, Enron’s auditors – Arthur Andersen – were also their internal auditor’s and their management consultants. 13. Explain the problems associated with lack of director independence ANS: Many boards of directors are comprised of individuals who are not independent. Examples of lack of independence are directors who: have a personal relationship by serving on the boards of other directors companies; have a business trading relationship as key customers or suppliers of the company; have a financial relationship as primary stockholders or have received personal loans from the company; have an operational relationship as employees of the company. 14. Explain the problems associated with Questionable Executive Compensation Schemes ANS: A survey by Thompson Financial revealed the strong belief that executives have abused stock-based compensation. The consensus is that fewer stock options should be offered than currently is the practice. Excessive use of short-term stock options to compensate directors and executives may result in short term thinking and strategies aimed at driving up stock prices at the expense of the firm’s long-term health. In extreme cases, financial statement misrepresentation has been the vehicle to achieve the stock price needed to exercise the option. 15. Explain the problems associated with inappropriate accounting practices. ANS: The use of inappropriate accounting techniques is a characteristic common to many financial statement fraud schemes. Enron made elaborate use of Special Purpose Entities (SPE) to hide liabilities through off balance sheet accounting. WorldCom management transferred transmission line costs from current expense accounts to capital accounts. This allowed them to defer some operating expenses and report higher earnings. Also, they reduced the book value of hard assets of MCI by $3.4 billion and increased goodwill by the same amount. Had the assets been left at book value, they would have been charged against earnings over four years. Goodwill, on the other hand, was amortized over much longer period. 16. Explain the purpose of the PCAOB. ANS: The Sarbanes-Oxley Act creates a Public Company Accounting Oversight Board (PCAOB). The PCAOB is empowered to set auditing, quality control, and ethics standards, to inspect registered accounting firms, to conduct investigations, and to take disciplinary actions. 17. Why is an Independent Audit Committee important to a company? ANS: The Sarbanes-Oxley Act requires all audit committee members to be independent and requires the audit committee to hire and oversee the external auditors. This provision is consistent with many investors who consider the board composition to be a critical investment factor. For example, Thompson Financial survey revealed that most institutional investors want corporate boards to be comprised of at least 75% of independent directors 18. What are the key points of the “Issuer and Management Disclosure” of the Sarbanes-Oxley Act? ANS: 1. Public companies must report all off balance-sheet transactions. 2. Annual reports filed with the SEC must include a statement by management asserting that it is responsible for creating and maintaining adequate internal controls and asserting to the effectiveness of those controls. 3. Officers must certify that the company’s accounts ‘fairly present’ the firms financial condition and results of operations. Knowingly filing a false certification is a criminal offence. 19. In this age of high technology and computer based information systems, why are accountants concerned about physical (human) controls? ANS: This class of controls relates primarily to the human activities employed in accounting systems. These activities may be purely manual, such as the physical custody of assets, or they may involve the use of computers to record transactions or update accounts. Physical controls do not relate to the computer logic that actually performs these accounting tasks. This is the subject matter of chapter 16. Rather, they relate to the human activities that initiate such computer logic. In other words, physical controls do not suggest an environment in which clerks update paper accounts with pen and ink. Virtually all systems, regardless of their sophistication, employ human activities that need to be controlled. 20. How has the Sarbanes-Oxley Act had a significant impact on corporate governance? ANS: The Sarbanes-Oxley Act requires all audit committee members to be independent and requires the audit committee to hire and oversee the external auditors. This provision is consistent with many investors who consider the board composition to be a critical investment factor. For example, a Thomson Financial survey revealed that most institutional investors want corporate boards to be comprised of at least 75 percent independent directors. 21. Discuss the non accounting services that external auditors are no longer permitted to render to audit clients under SOX legislation. ANS: The Act addresses auditor independence by creating more separation between a firm’s attestation and non-auditing activities. This is intended to specify categories of services that a public accounting firm cannot perform for its client. These include the following nine functions: Bookkeeping or other services related to the accounting records or financial statements; Financial information systems design and implementation; Appraisal or valuation services, fairness opinions, or contribution-in-kind reports; Actuarial services; Internal audit outsourcing services; Management functions or human resources; Broker or dealer, investment adviser, or investment banking services; Legal services and expert services unrelated to the audit; and Any other service that the PCAOB determines is impermissible. While the Sarbanes-Oxley Act prohibits auditors from providing the above services to their audit clients, they are not prohibited from performing such services for non-audit clients or privately held companies. 22. What are the key points of the “Issuer and Management Disclosure” of the Sarbanes-Oxley Act? ANS: The Sarbanes-Oxley Act imposes new corporate disclosure requirements including: Public companies must report all off-balance-sheet transactions. Annual reports filed with the SEC must include a statement by management asserting that it is responsible for creating and maintaining adequate internal controls and asserting to the effectiveness of those controls. Officers must certify that the company’s accounts “fairly present” the firm’s financial condition and results of operations. Knowingly filing a false certification is a criminal offence. Chapter 4—The Revenue Cycle TRUE/FALSE 1. The packing slip is also known as the shipping notice. ANS: F 2. The bill of lading is a legal contract between the buyer and the seller. ANS: F 3. Another name for the stock release form is the picking ticket. ANS: T 4. Warehouse stock records are the formal accounting records for inventory. ANS: F 5. The purpose of the invoice is to bill the customer. ANS: T 6. In most large organizations, the journal voucher file has replaced the formal general journal. ANS: T 7. The cash receipts journal is a special journal. ANS: T 8. In the revenue cycle, the internal control “limit access” applies to physical assets only. ANS: F 9. In real-time processing systems, routine credit authorizations are automated. ANS: T 10. In a computerized accounting system, segregation of functions refers to inventory control, accounts receivable, billing, and general ledger tasks. ANS: F 11. A written customer purchase order is required to trigger the sales order system. ANS: F 12. Inventory control has physical custody of inventory. ANS: F 13. The principal source document in the sales order system is the sales order. ANS: T 14. Sales orders should be prenumbered documents. ANS: T 15. Integrated accounting systems automatically transfer data between modules. ANS: T 16. If a customer submits a written purchase order, there is no need to prepare a sales order. ANS: F 17. Sales return involves receiving, sales, credit, and billing departments, but not accounts receivable. ANS: F 18. A remittance advice is a form of turn-around document. ANS: T 19. A bill of lading is a request for payment for shipping charges. ANS: F 20. In point of sale systems, authorization takes the form of validation of credit card charges. ANS: T MULTIPLE CHOICE 1. The revenue cycle consists of a. one subsystem–order entry b. two subsystems–sales order processing and cash receipts c. two subsystems–order entry and inventory control d. three subsystems–sales order processing, credit authorization, and cash receipts ANS: B 2. The reconciliation that occurs in the shipping department is intended to ensure that a. credit has been approved b. the customer is billed for the exact quantity shipped c. the goods shipped match the goods ordered d. inventory records are reduced for the goods shipped ANS: C 3. The adjustment to accounting records to reflect the decrease in inventory due to a sale occurs in the a. warehouse b. shipping department c. billing department d. inventory control department ANS: D 4. Which document triggers the revenue cycle? a. the sales order b. the customer purchase order c. the sales invoice d. the journal voucher ANS: B 5. Copies of the sales order can be used for all of the following except a. purchase order b. credit authorization c. shipping notice d. packing slip ANS: A 6. The purpose of the sales invoice is to a. record reduction of inventory b. transfer goods from seller to shipper c. bill the customer d. select items from inventory for shipment ANS: C 7. The customer open order file is used to a. respond to customer queries b. fill the customer order c. ship the customer order d. authorize customer credit ANS: A 8. The stock release copy of the sales order is not used to a. locate and pick the items from the warehouse shelves b. record any out-of-stock items c. authorize the warehouse clerk to release custody of the inventory to shipping d. record the reduction of inventory ANS: D 9. The shipping notice a. is mailed to the customer b. is a formal contract between the seller and the shipping company c. is always prepared by the shipping clerk d. informs the billing department of the quantities shipped ANS: D 10. The billing department is not responsible for a. updating the inventory subsidiary records b. recording the sale in the sales journal c. notifying accounts receivable of the sale d. sending the invoice to the customer ANS: A 11. Customers should be billed for backorders when a. the customer purchase order is received b. the backordered goods are shipped c. the original goods are shipped d. customers are not billed for backorders because a backorder is a lost sale ANS: B 12. Usually specific authorization is required for all of the following except a. sales on account which exceed the credit limit b. sales of goods at the list price c. a cash refund for goods returned without a receipt d. write off of an uncollectible account receivable ANS: B 13. Which of following functions should be segregated? a. opening the mail and making the journal entry to record cash receipts b. authorizing credit and determining reorder quantities c. maintaining the subsidiary ledgers and handling customer queries d. providing information on inventory levels and reconciling the bank statement ANS: A 14. Which situation indicates a weak internal control structure? a. the mailroom clerk authorizes credit memos b. the record keeping clerk maintains both accounts receivable and accounts payable subsidiary ledgers c. the warehouse clerk obtains a signature before releasing goods for shipment d. the accounts receivable clerk prepares customer statements every month ANS: A 15. The most effective internal control procedure to prevent or detect the creation of fictitious credit memoranda for sales returns is to a. supervise the accounts receivable department b. limit access to credit memoranda c. prenumber and sequence check all credit memoranda d. require management approval for all credit memoranda ANS: D 16. The accounts receivable clerk destroys all invoices for sales made to members of her family and does not record the sale in the accounts receivable subsidiary ledger. Which procedure will not detect this fraud? a. prenumber and sequence check all invoices b. reconcile the accounts receivable control to the accounts receivable subsidiary ledger c. prepare monthly customer statements d. reconcile total sales on account to the debits in the accounts receivable subsidiary ledger ANS: C 17. Which department is least likely to be involved in the revenue cycle? a. credit b. accounts payable c. billing d. shipping ANS: B 18. Which document is included with a shipment sent to a customer? a. sales invoice b. stock release form c. packing slip d. shipping notice ANS: C 19. Good internal controls in the revenue cycle should ensure all of the following except a. all sales are profitable b. all sales are recorded c. credit is authorized d. inventory to be shipped is not stolen ANS: A 20. Which control does not help to ensure that accurate records are kept of customer accounts and inventory? a. reconcile accounts receivable control to accounts receivable subsidiary b. authorize credit c. segregate custody of inventory from record keeping d. segregate record keeping duties of general ledger from accounts receivable ANS: B 21. Internal controls for handling sales returns and allowances do not include a. computing bad debt expense using the percentage of credit sales b. verifying that the goods have been returned c. authorizing the credit memo by management d. using the original sales invoice to prepare the sales returns slip ANS: A 22. The printer ran out of preprinted sales invoice forms and several sales invoices were not printed. The best internal control to detect this error is a. a batch total of sales invoices to be prepared compared to the actual number of sales invoices prepared b. sequentially numbered sales invoices c. visual verification that all sales invoices were prepared d. none of the above will detect this error ANS: A 23. Which department prepares the bill of lading? a. sales b. warehouse c. shipping d. credit ANS: C 24. A remittance advice is a. used to increase (debit) an account receivable by the cash received b. is a turn-around document c. is retained by the customer to show proof of payment d. none of the above ANS: B 25. A weekly reconciliation of cash receipts would include comparing a. the cash prelist with bank deposit slips b. the cash prelist with remittance advices c. bank deposit slips with remittance advices d. journal vouchers from accounts receivable and general ledger ANS: A 26. At which point is supervision most critical in the cash receipts system? a. accounts receivable b. general ledger c. mail room d. cash receipts ANS: C 27. EDI trading partner agreements specify all of the following except a. selling price b. quantities to be sold c. payment terms d. person to authorize transactions ANS: D 28. A cash prelist is a. a document that records sales returns and allowances b. a document returned by customers with their payments c. the source of information used to prepare monthly statements d. none of the above ANS: D 29. An advantage of real-time processing of sales is a. the cash cycle is lengthened b. current inventory information is available c. hard copy documents provide a permanent record of the transaction d. data entry errors are corrected at the end of each batch ANS: B 30. Commercial accounting systems have fully integrated modules. The word “integrated” means that a. segregation of duties is not possible b. transfer of information among modules occurs automatically c. batch processing is not an option d. separate entries are made in the general ledger accounts and the subsidiary ledgers ANS: B 31. The data processing method that can shorten the cash cycle is a. batch, sequential file processing b. batch, direct access file processing c. real-time file processing d. none of the above ANS: C 32. Which of the following is not a risk exposure in a microcomputer accounting system? a. reliance on paper documentation is increased b. functions that are segregated in a manual environment may be combined in a microcomputer accounting system c. backup procedures require human intervention d. data are easily accessible ANS: A 33. Which journal is not used in the revenue cycle? a. cash receipts journal b. sales journal c. purchases journal d. general journal ANS: C 34. Periodically, the general ledger department receives all of the following except a. total increases to accounts receivable b. total of all sales backorders c. total of all sales d. total decreases in inventory ANS: B 35. The credit department a. prepares credit memos when goods are returned b. approves credits to accounts receivable when payments are received c. authorizes the granting of credit to customers d. none of the above ANS: C 36. Adjustments to accounts receivable for payments received from customers is based upon a. the customer’s check b. the cash prelist c. the remittance advice that accompanies payment d. a memo prepared in the mailroom ANS: C 37. The revenue cycle utilizes all of the following files except a. credit memo file b. sales history file c. shipping report file d. cost data reference file ANS: D 38. All of the following are advantages of real-time processing of sales except a. The cash cycle is shortened b. Paper work is reduced c. Incorrect data entry is difficult to detect d. Up-to-date information can provide a competitive advantage in the marketplace ANS: C SHORT ANSWER 1. Distinguish between a packing slip, shipping notice, and a bill of lading. ANS: The packing slip travels with the goods to the customer, and it describes the contents on the order. Upon filling the order, the shipping department sends the shipping notice to the billing department to notify them that the order has been filled and shipped. The shipping notice contains additional information that the packing slip may not contain, such as shipment date, carrier and freight charges. The bill of lading is a formal contract between the seller and the transportation carrier; it shows legal ownership and responsibility for assets in transit. 2. State two specific functions or jobs that should be segregated in the sales processing system. ANS: sales order processing and credit approval; inventory control (record keeping) from warehouse (custody); and general ledger from accounts receivable subsidiary ledger 3. State two specific functions or jobs that should be segregated in the cash receipts system. ANS: cash receipts (custody) from accounts receivable (record keeping); and general ledger from accounts receivable subsidiary ledger mail room (receiving cash) and accounts receivable subsidiary ledger 4. List two points in the sales processing system when authorization is required. ANS: credit check, sales returns policy, preparation of cash prelist 5. For the revenue cycle, state two specific independent verifications that should be performed. ANS: shipping verifies that the goods sent from the warehouse are correct in type and quantity; billing reconciles the shipping notice with the sales order to ensure that customers are billed only for the quantities shipped; general ledger reconciles journal vouchers submitted by the billing department (sales journal), inventory control (inventory subsidiary ledger), and cash receipts (cash receipts journal) treasurer determines that all cash received got to the bank 6. What task can the accounts receivable department engage in to verify that all checks sent by the customers have been appropriately deposited and recorded? ANS: The company should periodically, perhaps monthly, send an account summary to each customer listing invoices and amounts paid by check number and date. This form allows the customer to verify the accuracy of the records. If any payments are not recorded, they will notify the company of the discrepancy. These reports should not be handled by the accounts receivable clerk or the cashier. 7. What specific internal control procedure would prevent the sale of goods on account to a fictitious customer? ANS: credit check 8. The clerk who opens the mail routinely steals remittances. Describe a specific internal control procedure that would prevent or detect this fraud. ANS: supervision (two people) when opening the mail; customer complaints when monthly statements mailed 9. A customer payment of $247 was correctly posted in the general ledger but was recorded as $274 in the customer’s account receivable. Describe a specific internal control procedure that would detect this error. ANS: reconcile the accounts receivable control account to the accounts receivable subsidiary ledger; compare control totals of cash received with total credits to A/R subsidiary ledger 10. Goods are shipped to a customer, but the shipping department does not notify billing and the customer never receives an invoice. Describe a specific internal control procedure that would detect this error. ANS: Billing department matches the stock release copy of the sales order (from shipping) to the invoice, ledger, and file copies of the sales order (sent directly to billing), and then mails the invoice to the customer. After a certain amount of time has passed, the billing department should investigate any unmatched invoice, ledger, and file copies of the sales order. 11. A clerk embezzles customer payments on account and covers up the theft by making an adjustment to the accounts receivable ledger. Describe a specific internal control procedure that would prevent this fraud. ANS: segregation of duties; do not let one person have custody of payments and the ability to make adjustments to the records; all adjustments to accounts receivable records must be authorized 12. A credit sale is made to a customer, even though the customer’s account is four months overdue. Describe a specific internal control procedure that would prevent this from happening. ANS: perform a credit check and require management approval for all sales to accounts that are overdue 13. What specific internal control procedure would prevent a customer from being billed for all 50 items ordered although only 40 items were shipped? ANS: billing should reconcile the shipping report with the sales order 14. What specific internal control procedure would prevent the shipping clerk from taking goods from the storeroom and sending them to someone who had not placed an order? ANS: shipping clerk should not have access to the storeroom 15. What specific internal control procedure would prevent an accounts receivable clerk from issuing a fictitious credit memo to a customer (who is also a relative) for goods that were “supposedly” returned from previous sales? ANS: credit memo should be authorized after verifying the return of goods based on evidence from the person who received the goods 16. What specific internal control procedure would prevent an increase in sales returns since salesmen were placed on commission? ANS: customer credit should be verified by the credit department reduce commissions for sales returns 17. What specific internal control procedure would detect the misplacement of a sales invoice after preparation and not mailed to the customer? The invoice was never found. ANS: all documents should be prenumbered 18. What function does the receiving department serve in the revenue cycle? ANS: The receiving department counts and inspects items which are returned by customers. The receiving department prepares a return slip of which a copy goes to the warehouse for restocking, and a copy goes to the sales order department so that a credit memo can be issued to the customer. 19. What are the three rules that ensure that no single employee or department processes a transaction in its entirety. ANS: The three rules that ensure segregation of functions are: 1. Transaction authorization should be separate from transaction processing 2. Asset custody should be separate from asset record keeping. 3. The organization structure should be such that the perpetration of a fraud requires collusion between 2 or more individuals. 20. What is automation and why is it used? ANS: Automation involves using technology to improve the efficiency and effectiveness of a task. Automation of the revenue cycle is typically used to reduce overhead costs, make better credit granting decisions, and better collect outstanding accounts receivable. 21. What is the objective of re-engineering? ANS: The objective of re-engineering is to greatly reduce costs by identifying and eliminating non value-added tasks and also by streamlining necessary existing processes. 22. What are the key segregation of duties related to computer programs that process accounting transactions. ANS: Response: The tasks of design, maintenance, and operation of computer programs need to be segregated. The programmers who write the original computer programs should not also be responsible for making program changes. Both of these functions must also be separate from the daily task of operating the system. 23. How is EDI more than technology? What unique control problems may it pose? ANS: EDI represents a unique business arrangement between the buyer and seller in which they agree, in advance, to the terms of their relationship on such items as selling price, quantities, delivery times, payment terms and methods of handling disputes. The terms of agreement are binding. One problem is ensuring that only valid transactions are processed. Another risk is that a non-trading partner will masquerade as a trading partner and access the firm's processing systems. 24. What makes point-of-sales systems different from revenue cycles of manufacturing firms? ANS: In point-of-sale systems, the customer literally has possession of the items purchased, thus the inventory is in hand. Typically, for manufacturing firms, the order is placed and the good is shipped to the customer at some later time period. Thus, updating inventory at the time of sale is necessary in point-of-sale systems since the inventory is changing hands, while it is not necessary in manufacturing firms until the goods are actually shipped to the customer. 25. Give three examples of Access Control in a Point-of-Sale (POS) system. ANS: Lock on the cash drawer Internal cash register tape that can be accessed only by the manager Physical security over the inventory. The following are examples: Steel cables to secure expensive leather coats to the clothing rack. Locked showcases to display jewelry and costly electronic equipment. Magnetic tags attached to merchandise, which will sound an alarm when removed from the store. Note to Instructor: Some physical security devices could also be classified as supervision ESSAY 1. When Clipper Mail Order Co. receives telephone and fax orders, the billing department prepares an invoice. The invoice is mailed immediately. A copy of the invoice serves as a shipping notice. The shipping department removes inventory from the warehouse and prepares the shipment. When the order is complete, the goods are shipped. The clerk checks the customer’s credit before recording the sale in the general journal and the account receivable subsidiary ledger. The receptionist opens the mail and lists all payments. The receptionist also handles all customer complaints and prepares sales return forms for defective merchandise. The cashier records all cash receipts in the general journal and makes the appropriate entry in the accounts receivable subsidiary ledger. The cashier prepares the daily bank deposit. Describe at least four internal control weaknesses at Clipper Mail Order Co. ANS: no sales order is prepared; credit should be checked before shipping the items; invoices are mailed before the goods are shipped; shipping has access to the warehouse; record keeping duties are not segregated (general ledger from subsidiary ledger); only one person opens the mail; sales return forms are not authorized by management; custody and record keeping duties are not separated; the cashier has custody of cash, makes journal entries, and maintains A/R ledger; Cashier has custody of cash and handles customer complaints (e.g., about unrecorded payments). 2. How may an employee embezzle funds by issuing an unauthorized sales credit memo if the appropriate segregation of functions and authorization controls were not in place? ANS: An employee who has access to incoming payments, either cash or check, as well as the authorization to issue credit memos may pocket the cash or check of a payment for goods received. This employee could then issue a credit memo to this person’s account so that the customer does not show a balance due. 3. For each of the following documents, describe its purpose, the functional area preparing it, and the key data included: sales order, bill of lading, credit memo. ANS: A sales order is used to collect information needed to initiate the sales process. It can be a copy of the customer’s purchase order prepared by the customer or a document prepared by a member of the sales staff in response to mail, phone or personal contact with the customer. It contains information about the customer, the type and quantity of merchandise being requested, price information, shipping information, etc. The bill of lading is prepared by the shipping clerk. It is a formal contract between the seller and the carrier who will transport the goods to the customer. It contains information about the carrier, the customer, descriptions of the package(s) being shipped, declared value of the goods, and information on freight charges, including how much and who will pay. A credit memo is a document authorizing issuance of credit to a customer for returned goods. It is prepared in the sales department after receipt of a return slip from receiving. It shows the customer’s name, reason for the return, a list of items and prices, and the total amount of credit. Many credit memos require additional authorization. 4. What features of a reengineered cash receipts system contribute to improved control and reduced costs? What complicates the process? ANS: A reengineered cash receipts system can include automated mail processing that opens envelopes and separates checks and remittance advices in a manner that limits access of the mail room clerk to the checks. Software can be used to read the amount of payment and compare to the amount due, verify that the check has been signed, etc. “Good” transactions continue through processing, exceptions are handled separately. Checks are sent to the cash receipts department for deposit, listings of transactions are sent to accounts receivable, cash receipts, and general ledger departments. This process is complicated when the organization receives many partial payments, single payments covering multiple invoices, or encounters many clerical errors on the part of customers. 5. What role does each of the following departments play in the sales order processing subsystem: sales, credit, and shipping? Be complete. ANS: The sales department receives the order information from the customer, either by mail, phone, or in person. Information is captured on a sales order form which includes customer name, account number, name, number and description of items ordered, quantities and unit prices plus taxes, shipping info, discounts, freight terms. This form is usually prepared in multiple copies that are used for credit approval, packing, stock release, shipping, and billing. The credit department provides transaction authorization by approving the customer for a credit sale and returns and allowances. The shipping department receives information from the sales department in the form of packing slip and shipping notice. When the goods arrive from the warehouse, the documents are reconciled with the stock release papers. The goods are packed and labeled. The packing slip is included. The shipping notice is sent to billing. A bill of lading is prepared to accompany the shipment. 6. With regard to segregation of duties, rule one is that transaction authorization and transaction processing should be separated. What does this require in the revenue cycle? ANS: Within the revenue cycle, the credit department is separate from the rest of the process. Hence, the authorization of the transaction (granting of credit) is independent. If other people, e.g., sales staff, were able to authorize credit sales, there would be the temptation to approve sales to any customer, even those known to not be credit worthy. 7. With regard to segregation of duties, rule two is that asset custody and record keeping should be separated. What does this require in the revenue cycle? ANS: In the revenue cycle, the warehouse has custody of physical assets while accounting (especially general ledger and inventory control) maintains the records. Also, in the cash receipts subsystem, cash receipts has custody of the asset (cash) while general ledger and accounts receivable keep the records. 8. What role does each of the following departments play in the cash receipts subsystem: mail room, cash receipts, accounts receivable, and general ledger? Be complete. ANS: The mail room receives the customer’s payment–usually a check accompanied by a document called a remittance advice (which may be a copy of the invoice sent to the customer). Mail clerks separate the two, prepare a cash prelist or remittance list which lists all the payments received and sends the checks to the cashier and remittance advices to accounts receivable. In cash receipts someone (e.g., cashier) restrictively endorses the checks and records the payments in the cash receipts journal. A deposit slip is prepared which accompanies the checks to the bank. The accounts receivable department posts from the remittance advices to the customer accounts in the AR subsidiary ledger. The general ledger department records cash receipts to the cash and AR control accounts based on the list from the mailroom and the summary report of posting from A/R. 9. For each of the following documents, describe its purpose, the functional area preparing it, and the key data included: remittance advice, remittance list, deposit slip. ANS: A remittance advice is sent by the customer to accompany payment. However, it is often part of or a copy of the invoice sent by the billing department after the goods were shipped. A remittance list is often called a cash prelist and is prepared by the mail room clerk to record all cash received. It accompanies the checks to the cashier. A deposit slip is prepared by the cashier to accompany the checks to the bank. This is usually a preprinted bank form. 10. How is independent verification carried out in a manual revenue system? ANS: Independent verification occurs in several departments as part of the sales order processing system. The shipping department verifies that the goods released by the warehouse for shipment, as shown on the stock release document, match the packing slip. Billing compares the shipping notice with the invoice to be sure customers are billed only for goods shipped. And general ledger reconciles the journal vouchers prepared by billing, inventory control, cash receipts, and accounts receivable. This reconciliation focuses on a match between what was ordered, what was removed from the stockroom, what was shipped, what was billed, cash received, and credit to the customer account. Chapter 5—The Expenditure Cycle Part I: Purchases and Cash Disbursements Procedures TRUE/FALSE 1. Purchasing decisions are authorized by inventory control. ANS: T 2. The blind copy of the purchase order that goes to the receiving department contains no item descriptions. ANS: F 3. Firms that wish to improve control over cash disbursements use a voucher system. ANS: T 4. In a voucher system, the sum of all unpaid vouchers in the voucher register equals the firm’s total voucher payable balance. ANS: T 5. The accounts payable department reconciles the accounts payable subsidiary ledger to the control account. ANS: F 6. The use of inventory reorder points suggests the need to obtain specific authorization. ANS: F 7. Proper segregation of duties requires that the responsibility approving a payment be separated from posting to the cash disbursements journal. ANS: T 8. A major risk exposure in the expenditure cycle is that accounts payable may be overstated at the end of the accounting year. ANS: F 9. When a trading partner agreement is in place, the traditional three way match may be eliminated. ANS: T 10. Authorization of purchases in a merchandising firm occurs in the inventory control department. ANS: T 11. A three way match involves a purchase order, a purchase requisition, and an invoice. ANS: F 12. Authorization for a cash disbursement occurs in the cash disbursement department upon receipt of the supplier’s invoice. ANS: F 13. An automated cash disbursements system can yield better cash management since payments are made on time. ANS: T 14. Permitting warehouse staff to maintain the only inventory records violates separation of duties. ANS: T 15. A purchasing system that employs electronic data interchange does not use a purchase order. ANS: F 16. Inventory control should be located in the warehouse. ANS: F 17. Inspection of shipments in the receiving department would be improved if the documentation showed the value of the inventory. ANS: F 18. One reason for authorizing purchases is to enable efficient inventory management. ANS: T 19. If accounts payable receives an invoice directly from the supplier it needs to be reconciled with the purchase order and receiving report. ANS: T 20. Supervision in receiving is intended to reduce the theft of assets. ANS: T MULTIPLE CHOICE 1. The purpose of the purchase requisition is to a. order goods from vendors b. record receipt of goods from vendors c. authorize the purchasing department to order goods d. bill for goods delivered ANS: C 2. The purpose of the receiving report is to a. b. c. d. order goods from vendors record receipt of goods from vendors authorize the purchasing department to order goods bill for goods delivered ANS: B 3. All of the following departments have a copy of the purchase order except a. the purchasing department b. the receiving department c. accounts payable d. general ledger ANS: D 4. The purpose of the purchase order is to a. order goods from vendors b. record receipt of goods from vendors c. authorize the purchasing department to order goods d. approve payment for goods received ANS: A 5. The open purchase order file in the purchasing department is used to determine a. the quality of items a vendor ships b. the best vendor for a specific item c. the orders that have not been received d. the quantity of items received ANS: C 6. The purchase order a. is the source document to make an entry into the accounting records b. indicates item description, quantity, and price c. is prepared by the inventory control department d. is approved by the end-user department ANS: B 7. The reason that a blind copy of the purchase order is sent to receiving is to a. inform receiving when a shipment is due b. force a count of the items delivered c. inform receiving of the type, quantity, and price of items to be delivered d. require that the goods delivered are inspected ANS: B 8. The receiving report is used to a. accompany physical inventories to the storeroom or warehouse b. advise the purchasing department of the dollar value of the goods delivered c. advise general ledger of the accounting entry to be made d. advise the vendor that the goods arrived safely ANS: A 9. When a copy of the receiving report arrives in the purchasing department, it is used to a. b. c. d. adjust perpetual inventory records record the physical transfer of inventory from receiving to the warehouse analyze the receiving department’s process recognize the purchase order as closed ANS: D 10. The financial value of a purchase is determined by reviewing the a. packing slip b. purchase requisition c. receiving report d. supplier’s invoice ANS: D 11. Which document is least important in determining the financial value of a purchase? a. purchase requisition b. purchase order c. receiving report d. supplier’s invoice ANS: A 12. In a merchandising firm, authorization for the payment of inventory is the responsibility of a. inventory control b. purchasing c. accounts payable d. cash disbursements ANS: C 13. In a merchandising firm, authorization for the purchase of inventory is the responsibility of a. inventory control b. purchasing c. accounts payable d. cash disbursements ANS: A 14. When purchasing inventory, which document usually triggers the recording of a liability? a. purchase requisition b. purchase order c. receiving report d. supplier’s invoice ANS: D 15. Because of time delays between receiving inventory and making the journal entry a. liabilities are usually understated b. liabilities are usually overstated c. liabilities are usually correctly stated d. none of the above ANS: A 16. Usually the open voucher payable file is organized by a. b. c. d. vendor payment due date purchase order number transaction date ANS: B 17. Which of the following statements is not correct? a. the voucher system is used to improve control over cash disbursements b. the sum of the paid vouchers represents the voucher payable liability of the firm c. the voucher system permits the firm to consolidate payments of several invoices on one voucher d. many firms replace accounts payable with a voucher payable system ANS: B 18. In the expenditure cycle, general ledger does not a. post the journal voucher from the accounts payable department b. post the account summary from inventory control c. post the journal voucher from the purchasing department d. reconcile the inventory control account with the inventory subsidiary summary ANS: C 19. The documents in a voucher packet include all of the following except a. a check b. a purchase order c. a receiving report d. a supplier’s invoice ANS: A 20. To maintain a good credit rating and to optimize cash management, cash disbursements should arrive at the vendor’s place of business a. as soon as possible b. on the due date c. on the discount date d. by the end of the month ANS: C 21. The cash disbursement clerk performs all of the following tasks except a. reviews the supporting documents for completeness and accuracy b. prepares checks c. signs checks d. marks the supporting documents paid ANS: C 22. When a cash disbursement in payment of an accounts payable is recorded a. the liability account is increased b. the income statement is changed c. the cash account is unchanged d. the liability account is decreased ANS: D 23. Authorization for payment of an accounts payable liability is the responsibility of a. inventory control b. purchasing c. accounts payable d. cash disbursements ANS: C 24. Of the following duties, it is most important to separate a. warehouse from stores b. warehouse from inventory control c. accounts payable and accounts receivable d. purchasing and accounts receivable ANS: B 25. In a firm with proper segregation of duties, adequate supervision is most critical in a. purchasing b. receiving c. accounts payable d. general ledger ANS: B 26. The receiving department is not responsible to a. inspect shipments received b. count items received from vendors c. order goods from vendors d. safeguard goods until they are transferred to the warehouse ANS: C 27. The major risk exposures associated with the receiving department include all of the following except a. goods are accepted without a physical count b. there is no inspection for goods damaged in shipment c. inventories are not secured on the receiving dock d. the audit trail is destroyed ANS: D 28. When searching for unrecorded liabilities at the end of an accounting period, the accountant would search all of the files except a. the purchase requisition file b. the cash receipts file c. the purchase order file d. the receiving report file ANS: B 29. In regards to the accounts payable department, which statement is not true? a. the purchase requisition shows that the transaction was authorized b. the purchase order proves that the purchase was required c. the receiving report provides evidence of the physical receipt of the goods d. the supplier’s invoice indicates the financial value of the transaction ANS: B 30. In a computerized system that uses an economic order quantity (EOQ) model and the perpetual inventory method, who determines when to reorder inventory? a. the inventory control clerk b. the purchasing department c. the vendor d. the computer system ANS: D 31. Firms can expect that proper use of a valid vendor file will result in all of the following benefits except a. purchasing agents will be discouraged from improperly ordering inventory from related parties b. purchases from fictitious vendors will be detected c. the most competitive price will be obtained d. the risk of purchasing agents receiving kickbacks and bribes will be reduced ANS: C 32. In a real-time processing system with a high number of transactions, the best and most practical control over cash disbursements is to have a. all checks manually signed by the treasurer b. all checks signed by check-signing equipment c. checks over a certain dollar amount manually signed by the treasurer d. checks over a certain dollar amount manually signed by the cash disbursements clerk ANS: C 33. The document which will close the open purchase requisition file is the a. purchase order b. vendor invoice c. receiving report d. none of the above ANS: C 34. Goods received are inspected and counted to a. determine that the goods are in good condition b. determine the quantity of goods received c. preclude payment for goods not received or received in poor condition d. all of the above ANS: D 35. If a company uses a standard cost system, inventory records can be updated from the a. vendor invoice b. purchase order c. receiving report d. purchase requisition ANS: C 36. If a company uses an actual cost system, inventory records can first be updated from the a. vendor invoice b. purchase order c. receiving report d. purchase requisition ANS: A 37. Copies of a purchase order are sent to all of the following except a. inventory control b. receiving c. general ledger d. accounts payable ANS: C 38. The receiving report a. is used to update the actual cost inventory ledger b. accompanies the goods to the storeroom c. is sent to general ledger d. is returned to the vendor to acknowledge receipt of the goods ANS: B 39. A supplier invoice a. is included with the goods b. shows what was ordered even if all was not shipped c. is sent by vendor to accounts payable d. none of the above ANS: C 40. The cash disbursement function is a. part of accounts payable b. an independent accounting function c. a treasury function d. part of the general ledger department ANS: C SHORT ANSWER 1. Which internally generated document should be compared to the supplier’s invoice to verify the price of an item? ANS: purchase order 2. Which internally generated document should be compared to the supplier’s invoice to verify the quantity being billed for? ANS: receiving report 3. List specific jobs that should be segregated in the purchases processing system. ANS: inventory control from warehouse, general ledger from accounts payable subsidiary ledger 4. List specific jobs that should be segregated in the cash disbursements system. ANS: general ledger from accounts payable subsidiary ledger, accounts payable subsidiary ledger from cash disbursements 5. Describe an internal control procedure that would detect that a vendor overcharged for goods delivered. ANS: Accounts payable should compare the price on the purchase order to the price on the supplier’s invoice. Accounts payable should recalculate the math (extensions and additions) and check all other charges such as freight, tax, etc. 6. Describe an internal control procedure that would prevent payment of a invoice for goods that were never delivered. ANS: Accounts payable should match every item on every invoice to a receiving report. 7. Describe an internal control procedure that would prevent issuing two checks in payment of the same invoice. ANS: The supporting documents should be marked “paid” after the check is signed. A computerized system will tag the invoice number as paid. 8. Explain why supervision is so important in the receiving department. ANS: Receiving department employees have custody of the asset and record keeping responsibilities. Without proper supervision, employees may fail to count and inspect incoming shipments. Without proper supervision, shipments may disappear from the receiving dock before being transferred to the warehouse. 9. What type of error or fraud might happen if the accounts payable ledger is not periodically reconciled to the control account in the general ledger? ANS: errors in A/P processing would go undetected, overstated payments produce debit balances in A/P. 10. What type of error or fraud might happen if suppliers’ invoices are not compared to purchase orders or to receiving reports before payment? ANS: payment at higher than anticipated prices, overpayment for goods not received 11. What internal accounting control(s) would be the most effective in preventing a storekeeper from taking inventory home at night? When shortages become apparent, he claims the goods were never received. ANS: receiving records items received on a receiving report, storekeeper initials receipt of goods 12. Why should the copy of a purchase order, which is sent to receiving, be a “blind” copy? ANS: to force workers in receiving to count and inspect the goods received 13. What is(are) the purpose(s) of maintaining a valid vendor file? ANS: Inventories should only be acquired from valid vendors. This control procedure helps to deter the purchasing agent from buying inventories at excessive costs and receiving kickbacks or from buying from an entity in which the purchasing agent has a relationship, such a relative or a friend. 14. Name two major benefits of automating the purchasing effort. ANS: improved inventory control, better cash management, streamlining the purchasing effort 15. What function or department typically initiates a purchase in a merchandising business? ANS: Inventory control determines that the level of certain items warrants restocking and sends a purchase requisition to purchasing. 16. Where in the purchasing/cash disbursement functions is access control exercised? ANS: physical control of inventory and cash, access to documents that control physical assets–such as purchase requisitions, purchase orders, receiving reports, etc. 17. Explain why a three way match may not be required for transactions covered by a trading partner agreement. ANS: Under a trading partner agreement the parties contractually agree to terms of trade such as price, quantities to be shipped, discounts, and lead times. With these sources of potential discrepancy eliminated, financial information about purchases is known in advance and the vendor’s invoice provides no critical information that cannot be derived from the receiving report. Thus, a three way match is unnecessary. ESSAY 1. Differentiate between a purchase requisition and a purchase order. ANS: A purchase order requisition is completed by the inventory control department when a need for inventory items is detected. Purchase requisitions for office supplies and other materials may also be completed by staff departments such as marketing, finance, accounting, and personnel. The purchasing department receives the purchase requisitions, and if necessary, determine the appropriate vendor. If various departments have requisitioned the same order, the purchasing department may consolidate all requests into one order so that any quantity discounts and lower freight charges may be taken. In any case, the purchasing department prepares the purchase order, which is sent to the vendor, accounts payable department, and the receiving department (blind copy). 2. What general ledger journal entries are triggered by the purchases system? From which departments do these journal entries arise? ANS: (Accounts Payable) Inventory Control Accounts Payable Debit Credit (Cash Disbursements) Accounts Payable Cash Debit Credit 3. The Soap Manufacturing Company has three employees who work in the warehouse. All of the warehouse workers are authorized to order inventory when it falls below the reorder level. The workers complete a purchase order and mail it to the supplier of their choice. The inventory is delivered directly to the warehouse. The workers send a memo to accounts payable reporting the receipt of inventory. Accounts payable compares the warehouse memo to the supplier’s invoice. Accounts payable prepares a check which the treasurer signs. Describe at least five needed internal control improvements. ANS: The warehouse workers should prepare a purchase requisition and send it to purchasing. Warehouse workers should make a note that the inventory has been requisitioned to avoid each of the workers requisitioning the same inventory items. Purchasing should prepare a purchase order. Purchasing should select a vendor based on price, quality of goods, delivery time, etc. Inventory should be delivered to the receiving department. The receiving department should prepare a receiving report. Accounts payable should receive a copy of the purchase requisition, purchase order, and receiving report and compare these documents to the supplier’s invoice. Cash disbursements should prepare the check. The supporting documents should be marked “paid” by cash disbursements. 4. How does a voucher payable system work? What documents are reconciled? Who prepares the voucher? How is the A/P balance determined? How does the voucher payable system improve control over cash? ANS: In place of a standard accounts payable system, many firms use a voucher payable system. The A/P department prepares cash disbursement vouchers which are recorded in a voucher register. A clerk would reconcile purchase requisition, purchase order, receiving report, and vendor invoice. If all agree, the clerk would prepare the voucher–which vouches the need to disburse cash. This would then be approved by a superior. The sum of all open (or unpaid) vouchers is the A/P balance. Control is improved over cash disbursements because of the itemization of items on the voucher and the authorization required. Without the data and authorization, no check is prepared. 5. Before authorizing payment for goods purchased, accounts payable reconciles three documents related to the purchase. Name them and explain what each indicates. What control area of SAS 78 is being addressed? ANS: The three documents are: the purchase order verifies the items were ordered, the receiving report that verifies the goods were received, and the invoice that is the vendor’s request for payment is reasonable. This process is a form of independent verification of the purchase. 6. What are the steps taken in the cash disbursement system? ANS: Accounts payable reviews the documents related to a liability: purchase requisition, purchase order, receiving report, and vendor invoice. If proper, cash disbursements is authorized to make payment. Cash disbursements prepares the check, a separate person signs it, sends it to the vendor, and notifies accounts payable. At the end of the period, cash disbursements and accounts payable send summary information to general ledger. 7. How does the procedure for determining inventory requirements differ between a basic batch processing system and batch processing with real-time data input of sales and receipts of inventory? What about for the procedures used by the receiving department? ANS: A system which employs real-time data entry of sales will have the inventory levels updated more frequently. Thus, when a sale depletes the inventory level to the reorder point, the system will flag it for reorder more quickly than if it had to wait for a batch update of the inventory records. The sooner the item is ordered, the sooner it will be received. With respect to the real-time receipt of inventory, the inventory will be updated immediately to show the accurate amount which is on hand. Thus, a customer wishing to know how soon they may have an item shipped will receive more accurate information regarding the status of the firm’s inventory levels. Thus, the customer benefits from better stocking of inventory and better information regarding the inventory levels. The receiving departments uses real-time data entry; they enter the purchase order number and a receiving screen prompts the clerk for the quantities of goods received. This system should cause less discrepancies due to poor handwriting, carelessness, and loss of the receiving report form. 8. What are the key segregation of duties issues in purchasing and cash disbursements? ANS: The key segregation of duties issue in purchasing is the separation of inventory control from the warehouse. If the only inventory records were held in the same place as the goods themselves, theft would be easy to hide with changes in the inventory records. Within the cash disbursements function it is important to separate CD from both general ledger and accounts payable to prevent alteration of records. The CD clerk is different from the check signer. Check signer does not perform back reconciliation. 9. Supervision is extremely important in the receiving department. Two main reasons were given. What were they? Why are these important? ANS: Supervision is important in the receiving department to assure that received goods are properly counted and inspected and to prevent theft. The key issue is that goods received are what was ordered (blind copy of PO identifies what was ordered, not how many) in good condition and in the proper quantity. If insufficient or improper goods are received and the error was not identified in receiving, payment would be made for goods not received. If inadequate supervision occurs, goods could be stolen and the receiving report modified to cover the theft. 10. Why do companies devote resources to a purchasing department? Could not individual departments make their own purchases more efficiently? ANS: The purchasing function is extremely important to a business. The members of the department work closely with suppliers to assure that the goods ordered are appropriately selected, priced, and delivered. One of the tasks of purchasing is to monitor the performance of vendors and maintain an approved vendor list. After a requesting department submits a purchase requisition, purchasing prepares a purchase order. Hence the authorization occurs outside of purchasing separate from the processing of the purchase. Significant separation of duties is built into this system: the same party cannot authorize and initiate the transaction. Purchasing employees cannot initiate a purchase. This could be a problem if vendors try to influence the purchasing staff for favorable treatment. 11. What are the key authorization issues in purchasing and cash disbursements? ANS: Inventory control monitors inventory and authorizes restocking with a purchase requisition. Purchasing acts on the PR, it does not initiate the process. Accounts payable authorizes the cash disbursement. The cash disbursement function cannot produce checks on its own without authorization from accounts payable. 12. What are the steps taken in the purchasing system? ANS: Inventory control monitors inventory and authorizes restocking with a purchase requisition. A copy is retained and one is sent to accounts payable. Purchasing acts on the PR and prepares a purchase order. The original is sent to a vendor. Copies go to inventory control and accounts payable. A blind copy is sent to receiving and another is filed in purchasing. When the goods are received, the receiving staff count and inspect the goods. The blind PO tells what goods were ordered. The count is a significant control check. Receiving prepares a receiving report. One copy accompanies the goods to the storeroom. Other copies go to purchasing, inventory control, and accounts payable. Accounts payable reconciles the purchase requisition, purchase order and receiving report. When the vendor invoice arrives, it is examined thoroughly and reconciled and if all documents agree, the transaction is recorded in the purchases journal and the accounts payable subsidiary ledger. The information is filed until the time arises to make payment. The general ledger department receives a journal voucher from AP and a summary from inventory control. The inventory and accounts payable control accounts are updated. Chapter 6—The Expenditure Cycle Part II: Payroll Processing and Fixed Asset Procedures TRUE/FALSE 1. Time cards are used by cost accounting to allocate direct labor charges to work in process. ANS: F 2. The personnel department authorizes changes in employee pay rates. ANS: T 3. Most payroll systems for mid-size firms use real-time data processing. ANS: F 4. To improve internal control, paychecks should be distributed by the employee's supervisor. ANS: F 5. Employee paychecks should be drawn against a special checking account. ANS: T 6. Because a time clock is used, no supervision is required when employees enter and leave the work place. ANS: F 7. Inventory control performs the formal record keeping function for fixed assets. ANS: F 8. The depreciation schedule shows when assets are fully depreciated. ANS: T 9. Authorization to dispose of fixed assets should be issued by the user of the asset. ANS: F 10. Work-in-process records are updated by payroll personnel. ANS: F 11. Ideally, payroll checks are written on a special bank account used only for payroll. ANS: T 12. The supervisor is the best person to determine the existence of a “phantom employee” and should distribute paychecks. ANS: F 13. Payroll processing can be automated easily because accounting for payroll is very simple. ANS: F 14. Timekeeping is part of the personnel function. ANS: F 15. Fixed asset accounting systems include cost allocation and matching procedures that are not part of routine expenditure systems. ANS: T 16. Asset maintenance involves only the recording of depreciation charges. Physical improvements are always expensed. ANS: F 17. Fixed Asset Systems must keep track of the physical location of each asset to promote accountability. ANS: T 18. Time cards capture the total time an individual worker spends on each production job. ANS: F 19. Accounting conventions and IRS rules sometime specify the depreciation parameters to be used. ANS: T 20. The fixed asset disposal report authorizes the user department to dispose of a fixed asset. ANS: F MULTIPLE CHOICE 1. The document that captures the total amount of time that individual workers spend on each production job is called a a. time card b. job ticket c. personnel action form d. labor distribution form ANS: B 2. An important reconciliation in the payroll system is a. general ledger compares the labor distribution summary from cost accounting to the disbursement voucher from accounts payable b. personnel compares the number of employees authorized to receive a paycheck to the number of paychecks prepared c. production compares the number of hours reported on job tickets to the number of hours reported on time cards d. payroll compares the labor distribution summary to the hours reported on time cards ANS: A 3. Which internal control is not an important part of the payroll system? a. Supervisors verify the accuracy of employee time cards. b. Paychecks are distributed by an independent paymaster. c. Accounts payable verifies the accuracy of the payroll register before transferring payroll funds to the general checking accounting. d. General ledger reconciles the labor distribution summary and the payroll disbursement voucher. ANS: C 4. Which transaction is not processed in the Fixed Asset System? a. purchase of building b. improvement of equipment c. purchase of raw materials d. sale of company van ANS: C 5. Depreciation a. is calculated by the department that uses the fixed asset b. allocates the cost of the asset over its useful life c. is recorded weekly d. results in book value approximating fair market value ANS: B 6. Depreciation records include all of the following information about fixed assets except a. the economic benefit of purchasing the asset b. the cost of the asset c. the depreciation method being used d. the location of the asset ANS: A 7. Which control is not a part of the Fixed Asset System? a. formal analysis of the purchase request b. review of the assumptions used in the capital budgeting model c. development of an economic order quantity model d. estimates of anticipated cost savings ANS: C 8. Objectives of the Fixed Asset System do not include a. authorizing the acquisition of fixed assets b. recording depreciation expense c. computing gain and/or loss on disposal of fixed assets d. maintaining a record of the fair market value of all fixed assets ANS: D 9. Which of the following is not a characteristic of the Fixed Asset System? a. Acquisitions are routine transactions requiring general authorization. b. Retirements are reported on an authorized disposal report form. c. Acquisition cost is allocated over the expected life of the asset. d. Transfer of fixed assets among departments is recorded in the fixed asset subsidiary ledger. ANS: A 10. In the payroll subsystem, which function should distribute paychecks? a. personnel b. timekeeping c. paymaster d. payroll ANS: C 11. Where does the responsibility lie for reconciling the labor distribution summary and the payroll disbursement voucher? a. cash disbursements b. cost accounting c. personnel d. general ledger ANS: D 12. Which of the following statements is not true? a. Routine payroll processing begins with the submission of time cards. b. Payroll clerks must verify the hours reported on the time cards. c. Payroll reconciles personnel action forms with time cards and prepares paychecks. d. Cash disbursements signs paychecks and forwards them to the paymaster for distribution. ANS: B 13. In a manufacturing firm, employees use time cards and job tickets. Which of the following statements is not correct? a. Job tickets are prepared by employees for each job worked on, so an employee may have more that one job ticket on a given day. b. An individual employee will have only one time card. c. The time reported on job tickets should reconcile with the time reported on time cards. d. Paychecks should be prepared from the job tickets. ANS: D 14. Which department is responsible for approving changes in pay rates for employees? a. payroll b. treasurer c. personnel d. cash disbursements ANS: C 15. Which of the following situations represents a serious control weakness? a. Timekeeping is independent of the payroll department. b. Paychecks are distributed by the employees immediate supervisor. c. Time cards are reconciled with job tickets. d. Personnel is responsible for updating employee records, including creation of records for new hires. ANS: B 16. Why would an organization require the paymaster to deliver all unclaimed paychecks to the internal audit department? a. to detect a “phantom employee” for whom a check was produced b. to prevent an absent employee’s check from being lost c. to avoid paying absent employees for payday d. to prevent the paymaster from cashing unclaimed checks ANS: A 17. Which of the following is not a reasonable control for fixed assets? a. Proper authorization is required for acquisition and disposal of fixed assets. b. Fixed asset records show the location of each asset. c. Fully depreciated assets are immediately disposed of. d. Depreciation policies are in writing. ANS: C 18. Cost accounting updates work-in-process accounts from a. time cards b. the labor distribution summary c. job tickets d. personnel action forms ANS: C 19. Payroll uses time card data to do all of the following except a. prepare the payroll register b. update employee payroll records c. prepare the labor distribution summary d. prepare paychecks ANS: C 20. Payroll checks are typically drawn on a. the regular checking account b. a payroll imprest account c. a wages payable account d. petty cash ANS: B 21. The personnel action form provides authorization control by a. preventing paychecks for terminated employees b. verifying pay rates for employees c. informing payroll of new hires d. all of the above ANS: D 22. Accounting records that provide the audit trail for payroll include all of the following except a. time cards b. job tickets c. payroll register d. accounts payable register ANS: D 23. Personnel actions forms are used to do all of the following except a. activate new employees b. terminate employees c. record hours worked d. change pay rates ANS: C 24. The payroll department performs all of the following except a. prepares the payroll register b. distributes paychecks c. updates employee payroll records d. prepares paychecks ANS: B 25. The document that records the total amount of time spent on a production job is the a. time card b. job ticket c. labor distribution summary d. personnel action form ANS: C 26. A control technique that can reduce the risk of a terminated employee being paid is a. a security camera viewing the time clock b. the supervisor taking role during the shift c. paychecks being distributed by an independent paymaster d. reconciliation of time cards and job tickets ANS: C 27. Accounts payable a. signs paychecks b. prepares the payroll voucher c. reconciles time cards and employee records d. distributes paychecks to employees ANS: B 28. All of the following are processed by the Fixed Asset System except a. sale of unneeded equipment b. purchase of raw materials c. repair of production equipment d. purchase of a new plant ANS: B 29. The Fixed Asset System performs all of the following except a. determines the need for new assets b. maintains depreciation records c. records retirement and disposal of assets d. tracks the physical location of fixed assets ANS: A 30. The payroll department performs all of the following except a. prepares paychecks b. transfers adequate funds to the payroll imprest account c. updates employee payroll records d. prepares the payroll register ANS: B 31. Depreciation a. assures that assets are reported at fair market value b. is discretionary for many firms c. allocates the cost of an asset over its useful life d. is the responsibility of the department using the asset ANS: C 32. The Fixed Asset System is similar to the expenditure cycle except a. fixed asset transactions are non-routine and require special authorization and controls b. fixed assets are capitalized, not expensed c. both a and b d. none of the above ANS: C 33. Asset maintenance involves a. the recording of periodic depreciation b. adjusting the asset records to reflect the cost of physical improvements c. keeping track of the physical location of the assets d. all of the above ANS: D 34. The Fixed Asset Systems does all of the following except a. records acquisition of assets b. records improvements to assets c. estimates the fair market value of assets in service d. records the disposal of assets ANS: C 35. Asset disposal a. occurs as soon as an asset is fully depreciated b. requires no special authorization c. automatically initiates the purchase of a replacement asset d. must follow formal authorization procedures ANS: D SHORT ANSWER 1. Describe an internal control procedure that would prevent an employee from punching the time clock for another, absent employee. ANS: supervision of the time clock at the start of the shift 2. Why should the employee’s supervisor not distribute paychecks? ANS: A form of payroll fraud involves a supervisor submitting fraudulent time cards for nonexistent employees. The resulting paychecks, when returned to the supervisor are then cashed by the supervisor. 3. Describe an internal control procedure that would prevent a supervisor from stealing the unclaimed paychecks of employees who have been terminated. ANS: This type of fraud can be reduced or eliminated by using a paymaster to distribute paychecks to employees in person. Any uncollected paychecks are then returned to payroll. Also, mail final paychecks to terminated employees. 4. Why should employee paychecks be drawn against a special checking account? ANS: A separate imprest account is established for the exact amount of the payroll based on the payroll summary. When the paychecks are cashed, this account should clear leaving a zero balance. Any errors in checks (additional checks or abnormal amounts) would result in a non-zero balance in the imprest account and/or some paycheck would not clear. This will alert management to the problem so corrective action can be taken. 5. Why should employees clocking on and off the job be supervised. ANS: A form of payroll fraud involves employees clocking the time cards of absent employees. By supervising the clocking in and out process, this fraud can be reduced or eliminated. 6. What is a personnel action form? ANS: The personnel action form provides the payroll department with a list of currently active employees, so that any submission of time cards by supervisors for fictitious or ex-employees will not be processed. 7. In a manufacturing firm, employees typically fill out two different documents regarding their time worked. What are they? Why are there two? ANS: The two documents are the time card and the job ticket. Two are required because the time card records all the time worked by an employee during the period while the job ticket details the time by project. 8. List two types of authorization required in the Fixed Asset System. ANS: authorization to purchase the asset and to dispose of the asset 9. List four types of data that appear on a depreciation schedule. ANS: item description, depreciation method, useful life, date acquired, cost, salvage value, accumulated depreciation, depreciation expense per period, book value 10. Which documents prompt the fixed asset department to create a fixed asset record? ANS: the receiving report and the disbursement voucher 11. Describe an internal control that would prevent an employee from stealing a computer and then reporting it as scrapped. ANS: Supervisors must authorize the disposal of the computer. Unless so authorized, the record will continue to show that the employee is responsible for the computer. 12. Describe an internal control that would prevent the payment of insurance premiums on an automobile that is no longer owned by the company. ANS: Perform an annual physical inventory of fixed assets and adjust the records to reflect assets no longer on hand. Prepare reports about the disposal of assets. 13. Describe an internal control that would prevent the charging of depreciation expense to the maintenance department for a sweeper that is now located in and used by the engineering department. ANS: Prepare reports about the transfer of fixed assets. Perform an annual physical inventory and note the location of assets. Budget and then hold each department accountable for depreciation expense for assets located in each department. 14. Describe an internal control that would prevent the acquisition of office equipment which is not needed by the firm. ANS: A higher organizational level or other appropriate person authorizes fixed asset acquisitions; part of the authorization is showing that a need for the asset exists. 15. What negative consequences result when fixed asset records include assets that are no longer owned by the firm? ANS: On the financial statements, assets will be overstated and depreciation expense could be overstated. Assets on property tax returns will be overstated and too much tax will be paid. Insurance premiums will be paid on nonexistent assets. 16. Explain the purpose of each of the following documents used in the payroll system: the personnel action form, the job ticket, the time card. ANS: The personnel action form is a document which identifies employees who should receive a paycheck; reflects changes in pay rates, payroll deductions, and job classifications. The job ticket collects information on the time individual workers spend on each production job. The time card captures the total time that an employee is at work. 17. How do fixed asset systems differ from the expenditure cycle? ANS: The fixed asset system processes nonroutine transactions for a wider group of users in the organization than the expenditure cycle. Further, the expenditure cycle processes routine acquisitions of raw materials inventories for the production function and finished goods inventories for the sales function. The expenditure cycle transactions are oftentimes automatically approved by the system, while fixed asset transaction approvals typically demand individual attention due to the uniqueness of the transactions. 18. What is recorded by the asset maintenance part of the Fixed Asset System? ANS: periodic depreciation following an approved depreciation schedule and physical improvements to the asset to increase the subsidiary account and to adjust the depreciation schedule 19. How are the following carried out in the Fixed Asset System: authorization, supervision, independent verification? ANS: Independent authorization is required to acquire an asset and to formalize the depreciation schedule. Supervision must be exercised over the physical assets. Independent verification must confirm the location, existence, and condition of the assets. 20. Which department authorizes changes to employee pay rates? ANS: The personnel department via the personnel action form ESSAY 1. The Golf Club Company makes custom golf clubs. The manufacturing supervisor interviews people who have specialized manufacturing skills, and he informs payroll when an employee is hired. The employees use a time clock to record the hours they work. The employees are also required to keep a record of the time they spend working on each order. The supervisor approves all time cards. The accountant analyzes the job tickets and prepares a labor distribution summary. Payroll prepares the payroll register and paychecks. The supervisor distributes the paychecks to the employees. Payroll informs cash disbursement of the funds required to cover the entire payroll amount. The cash disbursements clerk ensures that there are adequate funds in the company's regular checking account to cover the payroll. Describe at least three internal control weaknesses; for each weakness suggest an improvement to internal control. ANS: WEAKNESS: The supervisor could be creating fictitious employees. The supervisor has too many incompatible duties; he hires workers, approves the time cards, and distributes the paychecks. IMPROVEMENT: Segregate duties. Personnel should hire employees and a paymaster should distribute paychecks. WEAKNESS: Employees could be paid for time they do not work; a co-worker could record an absent worker as present (punch the time clock). IMPROVEMENT: Supervise the time clock. Reconcile time cards and job time tickets. WEAKNESS: Payroll has authorization and transaction processing responsibilities. Payroll is authorizing the disbursement to fund the entire payroll. Accounts payable is not part of the system. IMPROVEMENT: Segregate duties; accounts payable should verify the accuracy of the payroll register and create a disbursement voucher. WEAKNESS: Payroll is funded through the general checking account. IMPROVEMENT: Paychecks should be written on a separate payroll account. 2. Describe how the Fixed Asset System differs from the expenditure cycle. ANS: The Fixed Asset System processes nonroutine transactions which are recorded as capital assets. The receiving department delivers fixed assets to the user/manager. The fixed asset department performs the record keeping function. The expenditure cycle processes routine transactions which are often debited to inventory or expensed. The receiving department delivers routine purchases to a central store or warehouse. Inventory Control performs the record keeping function for inventory purchases. 3. Three major tasks are handled by the Fixed Asset System. What is the purpose of each? What special control issues affect each? ANS: Asset acquisition handles the steps leading to the acquisition of new fixed assets: recognition of need, authorization and approval, possible capital investment analysis, and selection of supplier. Because of the value of fixed assets, special approvals are needed. Asset maintenance involves adjusting the subsidiary account balances for depreciation, and improvements and tracking location. Control involves accountability by keeping track of the physical location of each asset. Asset disposal handles the removal of assets from the subsidiary ledger when the asset is taken out of service. This requires special approval and preparation of a disposal report. 4. The Baccus Corp. manufactures medical equipment. This is a capital intensive industry and investments in fixed assets exceed $5 million a year. The minimum cost for production equipment is $75,000. When supervisors want new production machinery, they contact the plant manager. The plant manager approves or denies the request based on discussions with the production supervisor, the repair and maintenance supervisor, and the quality control supervisor. A purchase order is prepared by the purchasing department and sent to one of the three major suppliers of production machinery for medical equipment. The equipment is delivered immediately to the production floor and put into service. At the end of the month, the production supervisor informs the general ledger clerk about the receipt of the machinery. The general ledger clerk establishes an asset record for the machine. At the end of the year, the general ledger clerk computes straight-line depreciation based on a 10-year life with a 10 percent salvage value. Depreciation expense is recorded as a direct reduction of the asset cost. The repair department performs routine maintenance on all of the production equipment. Occasionally the repair department rebuilds a machine to extend its useful life. All of the costs associated with the repair department are charged to manufacturing overhead. When a machine becomes obsolete, production employees move it to a corner of the factory floor and break it down so that parts can be used in other machines. Production employees routinely remove parts for personal use. Some smaller machines have disappeared completely from the factory floor. The general ledger clerk takes a physical inventory every three years. About 75 percent of the fixed assets can be located and identified. Other assets have serial numbers that are inaccessible, so the item cannot be matched to a fixed asset record. Some fixed asset records cannot be traced to an actual item. Several machines that have been scrapped and are being used for spare parts were matched to fixed asset records. At the last inventory, the general ledger clerk did not make any adjustments to the fixed asset records explaining that 75 percent accuracy in the fixed asset physical inventory was excellent. Describe five internal control weaknesses and explain how to correct them. ANS: WEAKNESS: There is no written documentation of the approval for purchase. IMPROVEMENT: A formal capital investment analysis should be performed for purchases of fixed assets; the analysis should evaluate cost and benefits of the request. WEAKNESS: There is no process for obtaining competitive bids. IMPROVEMENT: Price bids should be obtained from the three suppliers before a purchase order is issued. WEAKNESS: Fixed assets are delivered directly to the factory floor. IMPROVEMENT: All purchases should go through the receiving department; the equipment should be inspected and a receiving report should be prepared. WEAKNESS: The production supervisor notifies the general ledger clerk about the receipt of fixed assets. IMPROVEMENT: The receiving department should send a copy of the receiving report to the fixed asset department so that fixed asset records can be updated and accountability for the asset established. WEAKNESS: The general ledger clerk is maintaining fixed asset records. IMPROVEMENT: The fixed asset department should maintain fixed asset records. WEAKNESS: Depreciation is computed using a standard method, asset life, and salvage value. IMPROVEMENT: Management should ensure that the depreciation method is appropriate. The asset life and salvage value should be determined individually for each fixed asset acquisition. WEAKNESS: Depreciation is recorded as a direct reduction of the asset cost. IMPROVEMENT: Depreciation should be recorded in an Accumulated Depreciation account for each asset. WEAKNESS: Costs to rebuild a machine is charged to manufacturing overhead. IMPROVEMENT: Costs to rebuild machines should be recorded as an increase to the cost of the asset. WEAKNESS: There is no authorization to scrap an obsolete machine. IMPROVEMENT: Obtain written authorization from management before a machine is scrapped. WEAKNESS: Employees remove equipment and equipment parts from the premises without authorization. IMPROVEMENT: Employees should receive written authorization before removing parts or equipment from the factory. WEAKNESS: The general ledger clerk is conducting the physical inventory and maintaining the record keeping. IMPROVEMENT: The general ledger clerk should not be taking the physical inventory count. Also, the physical count should occur more frequently. WEAKNESS: Fixed assets cannot be matched with records. IMPROVEMENT: Apply easily accessible labels to identify fixed assets. WEAKNESS: Fixed assets cannot be located and are not removed from the books. IMPROVEMENT: Fixed assets that cannot be located must be removed from the fixed asset records. WEAKNESS: Fixed assets that are scrapped remain on the books. IMPROVEMENT: Assets that are scrapped should be removed from the fixed asset records. WEAKNESS: The clerk regards 75% accuracy as excellent. IMPROVEMENT: Acceptance of 75% accuracy is poor. Any variation should be investigated and records updated. 5. Why does the payroll process lend itself to batch processing? ANS: Payroll lends itself to batch computerization because it is processed at fixed time intervals which permits some time lag. Processing the payroll file usually involves most employees each time it is processed, which is an efficient use of computer resources and can be accomplished with a single pass through the file. 6. Discuss the fundamental risk and control issues associated with fixed assets that are different from raw materials and finished goods. ANS: AUTHORIZATION CONTROLS. Because fixed assets are requested and employed by end-users asset acquisitions should be formal and explicitly authorized. Each material transaction should be initiated by a written request from the user or department. In the case of high-value items, there should be an independent approval process that evaluates the merits of the request on a cost-benefit basis. SUPERVISION CONTROLS. Because capital assets are widely distributed around the organization, they are more susceptible to theft and misappropriation than inventories that are secured in a warehouse. Therefore, management supervision is an important element in the physical security of fixed assets. Supervisors must ensure that fixed assets are being used in accordance with the organization’s policies and business practices. INDEPENDENT VERIFICATION CONTROLS. 1. Periodically, the internal auditor should review the asset acquisition and approval procedures to determine the reasonableness of key factors including: the useful life of the asset, the original financial cost, proposed cost savings as a result of acquiring the asset, the discount rate used, and the capital budgeting method used in justifying decisions to buy or dispose of assets. 2. The internal auditor should verify the location, condition, and fair value of the organization’s fixed assets against the fixed asset records in the subsidiary ledger. 3. The automatic depreciation charges calculated by the fixed asset system should be reviewed and verified for accuracy and completeness. System errors that miscalculate depreciation can result in the material misstatement of operating expenses, reported earnings, and asset values. Chapter 7—The Conversion Cycle TRUE/FALSE 1. The philosophy of customer satisfaction permeates the world-class firm. ANS: T 2. Reports generated by the cost accounting system include performance reports and budget reports. ANS: T 3. The cost accounting system authorizes the release of raw materials into production. ANS: F 4. Batch processing creates a homogeneous product through a continuous series of standard procedures. ANS: F 5. The bill of materials specifies the types and quantities of the raw materials and subassemblies used in producing a single unit of finished product. ANS: T 6. A purchase requisition authorizes the storekeeper to release materials to individuals or work centers in the production process. ANS: F 7. The SAP R/3 system organizes business processes into four categories: financial, logistics, human resources, and business process support. ANS: T 8. The objective of the Economic Order Quantity model is to reduce total inventory costs by minimizing carrying costs and ordering costs. ANS: T 9. The work-in-process file is the subsidiary ledger for the work-in-process control account. ANS: T 10. Move tickets authorize the storekeeper to release materials to work centers. ANS: F 11. An operating characteristic of modern manufacturing firms is that labor is replaced with capital so that the firm can be more efficient and therefore more competitive. ANS: T 12. Computer Integrated Manufacturing focuses on reducing the complexity of the physical manufacturing layout of the shop floor. ANS: F 13. The only objective of the Just-In-Time philosophy is to reduce inventory levels. ANS: F 14. Accounting in a world-class manufacturing environment emphasizes standard cost and variance analysis. ANS: F 15. Identifying cost drivers is an essential step in implementing the Just-In-Time philosophy. ANS: F 16. A world class information system produces very little paper. ANS: T 17. Internal control procedures are virtually identical in a world-class manufacturing environment and in a traditional manufacturing environment. ANS: F 18. In a world-class company, all activities, from acquisition of raw materials to selling the final product, form a “chain of customers.” ANS: T 19. The two subsystems of a traditional conversion cycle are the production system and the delivery system. ANS: F 20. Manufacturing resources planning (MRP II) has evolved into electronic resource planning (ERP). ANS: F MULTIPLE CHOICE 1. Which item does not describe a world-class company? a. the goal of a world-class company is to delight its customers b. customers in a world-class company are external departments only c. world-class companies work in cross-functional teams d. a world-class company has a flat organizational structure ANS: B 2. Which subsystem is not a part of the production system? a. b. c. d. directing the movement of work through the process determining raw material requirements authorizing work to be performed monitoring the flow of cost information related to production ANS: D 3. The purpose of the cost accounting system is to a. produce information for inventory valuation b. authorize release of raw materials c. direct the movement of work-in-process d. determine material requirements ANS: A 4. Which process creates a homogeneous product through a continuous series of standard procedures? a. batch process b. make-to-order process c. continuous process d. none of the above ANS: C 5. An example of a continuous process is the production of a. wedding invitations b. milk products c. jet aircraft d. all of the above ANS: B 6. All of the following are characteristics of batch processing except a. each item in the batch is similar b. batches are produced in accordance with detailed customer specifications c. batches are produced to replenish depleted inventory levels d. setting up and retooling is required for different batches ANS: B 7. When determining which items to produce, a firm must know a. last year’s production level b. raw material inventory levels c. the standard cost of the item d. the sales forecast ANS: D 8. The production schedule is a. the expected demand for the firm’s finished goods for a given year b. the formal plan and authority to begin production c. a description of the type and quantity of raw materials and subassemblies used to produce a single unit of finished product d. the sequence of operations during manufacturing ANS: B 9. A move ticket a. is the formal plan and authority to begin production b. specifies the materials and production required for each batch c. records the work done in each work center d. authorizes the storekeeper to release materials to work centers ANS: C 10. The internal control significance of the excess materials requisition is that it a. indicates the amount of material released to work centers b. identifies materials used in production that exceed the standard amount allowed c. indicates the standard quantities required for production d. documents the return to raw materials inventory of unused production materials ANS: B 11. Inventory control performs all of the following tasks except it a. provides production planning and control with the inventory status report of finished goods b. updates the raw material inventory records c. prepares a materials requisition for each production batch d. records the completed production as an increase to finished goods inventory ANS: C 12. The storekeeper releases raw materials based on the a. production schedule b. materials requisition c. work order d. bill of materials ANS: B 13. Which of the following is not an assumption of the Economic Order Quantity model? a. demand for the product is known with certainty b. total cost per year of placing orders is fixed c. lead time is known and is constant d. there are no quantity discounts ANS: B 14. Firms hold safety stock to compensate for a. mathematical weaknesses of the Economic Order Quantity model b. variations in lead time or daily demand c. fluctuations in carrying costs d. uncertainty in the estimation of ordering costs ANS: B 15. What is the economic order quantity if the annual demand is 10,000 units, set up cost of placing each order is $3 and the holding cost per unit per year is $2? a. 174 b. 123 c. 245 d. none of the above ANS: A 16. If the daily demand is 40 units and the lead time is 12 days, the reorder point is a. 52 units b. 48 units c. 480 units d. none of the above ANS: C 17. Which statement is not correct? a. general ledger creates a new cost record upon receipt of a work order from production planning and control b. cost accounting updates the cost record with data gathered from the materials requisition c. general ledger posts summary information about the manufacturing process based on a journal voucher prepared by cost accounting d. cost accounting computes variances and applies overhead to individual cost records ANS: A 18. Which of the following is not a category of critical success factors in most manufacturing companies? a. product quality b. customer service c. revenue generation d. resource management ANS: C 19. Computer integrated manufacturing groups all of the following technologies except a. robotics b. materials requirements planning c. automated storage and retrieval systems d. computer aided design ANS: B 20. The SAP R/3 system provides pre-defined modules to support business processes in the all of the following categories except a. human resources b. business process support c. strategic d. financial ANS: C 21. Which situation violates the segregation of functions control procedure? a. production planning and control is located apart from the work centers b. inventory control maintains custody of inventory items c. cost accounting has custody of and makes entries on cost records d. work centers record direct labor on job tickets ANS: B 22. All of the following are internal control procedures that should be in place in the conversion cycle except a. calculation and analysis of direct material and direct labor variances b. retention of excess materials by work centers c. physical count of inventory items on hand d. limited access to raw material and finished goods inventories ANS: B 23. Process simplification focuses on a. using Computer Numerical Controlled machines which stand alone within a traditional setting b. completely automating the manufacturing environment c. reducing the complexity of the physical manufacturing layout of the shop floor d. organizing the process into functional departments ANS: C 24. A manufacturing process that is organized into group technology cells utilizing no human labor is called a. islands of technology b. process simplification c. Computer Integrated Manufacturing d. traditional manufacturing ANS: C 25. An example of automation of manufacturing design is a. Computer Aided Engineering b. Automated Storage and Retrieval Systems c. Computer Numerical Control d. robotics ANS: A 26. An example of automation of manufacturing planning is a. Computer Aided Engineering b. Automated Storage and Retrieval Systems c. Materials Requirements Planning d. Computer Numerical Control ANS: C 27. Firms implement a Just-In-Time inventory approach to a. reduce investment in inventories b. determine the optimum inventory level using the EOQ model c. camouflage production problems d. ensure overproduction of inventory ANS: A 28. Characteristics of Just-In-Time manufacturing include all of the following except a. push manufacturing b. zero defects c. reduced setup time and small lot sizes d. reliable vendors ANS: A 29. The cost of poor quality includes all of the following except a. cost of rework b. warranty claims c. scheduling delays d. proceeds from the sale of scrap ANS: D 30. A flexible manufacturing system a. creates bottlenecks in the process b. leads to an “us” versus “them” attitude among workers c. shortens the physical distance between activities d. is organized along functional lines ANS: C 31. Deficiencies of the traditional cost accounting information system include all of the following except a. an emphasis on financial performance b. inaccurate cost allocations c. an emphasis on standard costs d. immediate feedback about deviations from the norm ANS: D 32. Which statement is not correct? a. an activity driver is a means to measure the activity used by the cost object b. cost object describes the work performed in a firm c. activities cause costs d. cost objects create a demand for activities ANS: B 33. Firms are adopting Activity Based Costing (ABC) because a. it facilitates the analysis of variances b. it more accurately allocates costs to products c. it recognizes the importance of direct labor as a component of total manufacturing cost d. the financial nature of the reports permits comparisons to be made among different types of products ANS: B 34. In traditional firms, information reporting a. provides financially oriented information relating to operations b. presents detailed information about activities c. shows the allocation of costs first to activities and then to cost objects d. identifies nonessential activities ANS: A 35. Types of information provided by Activity Based Costing include a. a description of the single activity driver used for overhead application b. the dollar value of the direct material usage variance c. identification of cost drivers d. details of the components of the single overhead cost pool ANS: C 36. Which statement is not correct? a. the benchmark approach compares key activities with similar activities in other firms b. critical success factors include product and process quality c. the ABC model includes two perspectives: an allocation of cost perspective and a process perspective d. in world-class manufacturing firms, quality control activities at the end of the process are essential ANS: D 37. All of the following are documents in batch process production systems except a. production schedule b. route sheet c. materials requisition d. purchase order ANS: D 38. Transaction authorization occurs in a traditional manufacturing environment in all of the following ways except a. production planning and control initiates production with a work order b. movement of the work through the production process follows the move ticket c. the sales department modifies work orders to match changes in demand d. the materials requisition authorizes the storekeeper to release materials to the work centers ANS: C 39. Manufacturing flexibility incorporates four characteristics. These include all of the following except a. high product quality b. high inventory levels c. automation of manufacturing processes d. physical reorganization of production facilities ANS: B 40. The stages of the automation continuum are (in order) a. traditional, computer-integrated manufacturing, islands of technology, process simplification b. process simplification, traditional, islands of technology, computer-integrated manufacturing c. traditional, islands of technology, process simplification, computer-integrated manufacturing d. traditional, process simplification, computer-integrated manufacturing, islands of technology ANS: C SHORT ANSWER 1. Which type of manufacturing creates a homogeneous product through a continuous series of standard procedures? ANS: continuous process manufacturing 2. What information is contained in the bill of materials (BOM)? ANS: The BOM specifies the types and quantities of raw materials and subassemblies used in producing a single unit of finished product. 3. What is the difference between a materials requisition and a purchase requisition? ANS: A materials requisition authorizes the storekeeper to release materials and subassemblies to the production process. A purchase requisition authorizes the purchasing department to place an order with an external vendor to acquire goods or services. 4. List one authorization control in the traditional manufacturing environment. ANS: work orders prepared by production planning and control; move tickets signed by the foreman; materials requisitions and excess materials requisitions 5. Explain how Just-In-Time inventory affects setup time and lot size. ANS: In a Just-In-Time process, setup time should be reduced as much as possible, ideally to zero, and lot sizes should be very small to ensure a continuous flow of product through the process. 6. What is one benefit of the flexible production system? ANS: A flexible production system shortens the physical distance between activities, reducing setup time, processing time, handling costs, and inventories. 7. List two disadvantages of using a traditional cost accounting system. ANS: Cost allocations may be inaccurate; there is a time lag in reporting; information is reported in financial terms; there is an emphasis on standard cost. 8. In Activity Based Costing, what is the term used to refer to the work performed by a firm? ANS: an activity 9. In Activity Based Costing, the activity cost is assigned to the cost object by means of __________________________. ANS: an activity (or cost) driver 10. Explain benchmarking. ANS: When a process is benchmarked, key activities are compared to similar activities performed elsewhere in the firm or in other firms. 11. Provide a specific example of source data automation. ANS: bar coding, magnetic ink character recognition, electronic strip, optical character recognition 12. In a traditional manufacturing environment, cost accounting provides independent verification of what information? What are the benefits? ANS: Cost accounting reconciles materials and labor usage, from the materials requisitions and job tickets, with prescribed standards and identifies significant departures. Such variance analysis is important for control of the manufacturing process. 13. How are cost structures fundamentally different between the traditional and CIM environments? ANS: In the traditional manufacturing environment, direct labor is a much larger component of total manufacturing costs than in the CIM environment. Overhead, on the other hand, is a far more significant element of cost in advanced technology manufacturing. 14. What are the key segregation of duties issues in the conversion cycle? ANS: Inventory control must be separated from raw materials and finished goods custody. Cost accounting must be separate from the work centers. General ledger must be separate from other accounting functions. 15. Traditional accounting assumes that products cause costs. ABC assumes that _________________ cause costs. ANS: activities 16. Differentiate between essential and non-essential activities. ANS: Essential activities add value to the organization either through adding value to the customer or to the organization. Non-essential activities do not add value. 17. Name the underlying assumptions of the JIT method. ANS: Zero defects, zero setups, small lot sizes, zero inventories, zero lead times & reliable vendors, and team attitude. 18. What document signals the completion of the production process? ANS: The receipt by cost accounting of the last move ticket for a batch from the work center signals the completion of the production process. 19. What document triggers the beginning of the cost accounting process for a given production run? ANS: The work order from the production planning and control department triggers the cost accounting process. 20. Name five documents associated with batch production systems. ANS: Sales forecast, production schedule, bill of materials, route sheet, work order, move ticket, and materials requisition. ESSAY 1. What are the accounting implications when a firm moves toward world-class status? ANS: When a firm moves toward world-class status, changes will be required in accounting techniques, in information reporting, and in the integration of the information system. World-class companies will apply accounting techniques like Activity Based Costing to obtain improved cost information in order to make better decisions concerning pricing, product mix, and product and process design. Information will be developed to help managers understand and evaluate manufacturing activities, identify and eliminate nonessential activities, identify cost drivers, and establish links between performance measures and decision making. Finally, firms will implement information systems that integrate financial and nonfinancial information using software like the Manufacturing Resource Planning II. Firms will maintain an electronic link with external parties by implementing Electronic Data Interchange (EDI). 2. Contrast the treatment of inventories in the traditional manufacturing environment and the world-class manufacturing environment. ANS: In the traditional manufacturing environment, inventories are used to reduce or eliminate back orders. The goal in the traditional environment is to minimize the cost of holding inventory and the costs of ordering or manufacturing inventory. In a world-class manufacturing environment the Just-In-Time (JIT) inventory system is often implemented. Inventories are kept to the absolute minimum. Inventories arrive in small quantities from vendors several times per day. Inventory is “pulled” through the manufacturing process; there are no batches of partially completed products throughout the production process. The JIT inventory concept assumes: zero defects, zero setup time, small lot sizes, zero inventories, zero lead time, and reliable vendors. 3. Discuss the key segregation of duties that should exist in the traditional manufacturing environment. ANS: Production planning and control should be separate from the work centers. Inventory control, which maintains accounting records for raw materials (RM) and (FG) inventories should be kept separate from the materials storeroom and from the FG warehouse functions where these assets reside. The cost accounting function accounts for work in process and should be separate from the work centers in the production process. The general ledger (GL) function should be separate from departments keeping subsidiary account 4. What are the four categories of business processes as defined as modules by SAP R/3? Explain. ANS: Financial: The financial modules include the financial accounting module that collects financial data for both internal and external reporting, the controlling module for reporting and controlling costs, the fixed asset management module that supports the management of fixed, leased, and real corporate assets, and the ability to respond to interactive requests. Logistics: The logistics modules support manufacturing by means of an available-to-promise module to respond to customer inquiries, sales and distribution module to handle order entry and order status, a product planning module for forecasting, and additional modules for materials management, service calls, and plant maintenance. Human resources: This module supports management of employees including hiring, work scheduling, and payroll processing. Business process support: Two types of modules handle workflow and industry specific activities. 5. How can a world-class information system yield a paperless environment? ANS: Traditional paper flow can be essentially eliminated in a world-class information system environment. Savings occur by eliminating printing, handling, filing of paper documents, and data entry errors. Part of the benefit comes from source data automation using technologies such as bar coding (the familiar UPC code permits scanning which eliminates most errors). Thus, recording of materials is simplified. Magnetic monitoring of labor is possible to tally labor charges and movement of equipment and inventory. 6. How does MRP II (manufacturing resource planning) expand on MRP (materials requirements planning)? ANS: MRP is an older system that focused only on the materials requirements of the production process. It used work orders as a basis for a bill of materials and to determine inventory requirements prior to production. MRP II expands on this idea by identifying production need for all inputs–materials (as in MRP), labor, and equipment. In fact, MRP II provides planning, feedback, and control for coordinating all of the activities of a firm. 7. Name and explain the five categories of critical success factors. ANS: Product quality: The firm’s product must meet or exceed the customer’s expectations. Process quality: The amount of process variation that results in scrap or rework must be minimized. Customer service: The demands of customers for finished products must be met. Resource management: The firm must maximize the use of all resources in manufacturing. Flexibility: The firm must be willing to adjust to changes in demands in its environment. 8. MRP II integrates product design and the production process with order entry, accounting. and activity based costing. What are some of the benefits? ANS: The benefits include: improved customer service, reduced inventory investment, increased productivity, improved cash flow, assistance in achieving long-term strategic goals, help in managing changes and flexibility in the production process. 9. The Just-In-Time (JIT) approach to inventories is regarded as a great advance in inventory management. There are six assumptions that underlie JIT. Discuss three. ANS: Just-In-Time (JIT) manufacturing is a model which fosters inventory reduction and even elimination. It is based on the following assumptions: Zero defects are assumed for raw materials, WIP, and finished goods. The presence of excessive defects would require extra inventory as security. Zero setup time is desired because set-up time is not productive. Small lot sizes permit high machine utilization. Zero inventories reduce the investment that can be utilized elsewhere. Zero lead times and reliable vendors are required to have the materials available when needed. A team attitude is required of all employees. 10. The text discusses the “evils of inventory.” What are they? Why are they “evil?” ANS: Inventories cost money. They represent an investment. They need to be insured and stored, both of which cost money. Inventories can become obsolete over time. Inventories camouflage production problems–if a cushion exists, orders can be filled even if production is slowed or stopped due to difficulties. Willingness to maintain inventories can precipitate overproduction–if an organization is willing to have high stock, and if any incentives exist to produce–rewards etc., excess inventory may be produces without adequate demand. 11. Automation of manufacturing can be viewed as a progression beginning with the traditional manufacturing environment. What are the stages? What distinguishes them? ANS: Automation of the manufacturing process can be viewed as a gradual progression. The stages are: Traditional manufacturing which consists of many different types of machines that require a lot of setup time, each controlled by a single operator. The WIP follows a circuitous route through the different operations. Islands of technology in which stand alone islands employ computer numerical controlled (CNC) machines that can perform multiple operations with less human involvement–less set up time. Process simplification which reduces the complexity of the physical layout. Groups of CNC machines are arranged in cells to produce an entire part from start to finish. No human involvement in a cell. Computer integrated manufacturing (CIM)–a completely automated environment which employs automated storage and retrieval systems (AS/RS) and robotics. 12. How can a firm control against excessive quantities of raw materials being used in the manufacturing process. ANS: The use of standard costs provides a type of access control. By specifying the quantities of material authorized for each product, the firm limits usage. To obtain excess quantities requires special authorization and excess materials requisitions. 13. Explain the relationship between MRP, MRPII and ERP. ANS: Manufacturing resources planning (MRP II) is an extension of a simpler concept still in use called materials requirements planning (MRP). MRP is an automated version of a traditional production planning and control process. On the other hand, MRP II is a reengineering technique that integrates several business processes. MRP II is not confined to the management of inventory. It is both a system and a philosophy for coordinating the activities of the entire firm. As such, MRP II has evolved into the large suites of software called enterprise resource planning (ERP) systems. These huge commercial packages support the information needs of the entire organization, not just the manufacturing functions. An ERP can calculate resource requirements, schedule production, manage changes to product configurations, allow for future planned changes in products, and monitor shop floor production. In addition, the ERP provides order entry, cash receipts, procurement, and cash disbursement functions along with full financial and managerial reporting capability. 14. Explain how CAD can contribute to a firm’s move toward world-class status. ANS: Product design has been revolutionized through CAD technology. Advanced CAD systems can design both product and process simultaneously. Thus, aided by CAD, management can evaluate the technical feasibility of the product and determine its “manufacturability.” CAD technology greatly shortens the time frame between initial and final design. This allows firms to adjust their production quickly to changes in market demand. It also allows them to respond to customer requests for unique products. The CAD system’s EDI interface permits the world-class manufacturer to share its product design specifications with its vendors and customers. This communications link also allows the world-class manufacturer to receive product design specifications electronically from its customers and suppliers for its review. 15. Explain how CAM can contribute to a firm’s move toward world-class status. ANS: Computer-aided manufacturing (CAM) focuses on the shop floor and the use of computers to control the physical manufacturing process. The objective behind CAM is to replace labor through automation. CAM systems monitor and control the production process and routing through the use of process control, numerical control, and robotics equipment. A world-class manufacturer will derive several benefits from deploying a CAM system: improved process productivity, improved cost and time estimates, improved process monitoring, improved process quality, decreased setup times, and reduced labor costs. 16. Explain why traditional cost allocation methods fail in a CIM environment. ANS: Traditional accounting systems do not accurately trace costs to products and processes. One consequence of new technologies is a changed relationship between direct labor and overhead costs. In the traditional manufacturing environment, direct labor is a much larger component of total manufacturing costs than in the CIM environment. Overhead, on the other hand, is a far more significant element of cost in advanced technology manufacturing. In this setting, traditional cost accounting procedures are inadequate. For traditional allocations to be correct, a direct relationship between labor and technology needs to exist. In CIM, this relationship is diametric rather than complementary. When the cost pool is large and the allocation method ambiguous, any miscalculation in assigning labor is magnified many times in the calculation of overhead. 17. Explain how JIT can reduce inventory. ANS: Under the JIT approach, inventories arrive in small quantities from vendors several times per day “just in time” to go into production. JIT supports a pull manufacturing process. As production capacity upstream becomes available, the manufacturing process pulls small batches (or a single item) of product into the next work center. Rather than periodically taking in large batches, JIT promotes a continuous flow of production through the process pulled along by idle capacity. Unlike the traditional push process, JIT does not create batches of semi-finished inventories at bottlenecks. Chapter 8—General Ledger, Financial Reporting, and Management Reporting Systems TRUE/FALSE 1. The most common means of making entries in the general ledger is via the journal voucher. ANS: T 2. Individuals with access authority to general ledger accounts should not prepare journal vouchers. ANS: T 3. The journal voucher is the document that authorizes entries to be made to the general ledger. ANS: T 4. Each account in the chart of accounts has a separate record in the general ledger master file. ANS: T 5. The responsibility center file is primarily used by the Financial Reporting System. ANS: F 6. Management reporting is often called discretionary reporting because it is not mandated as is financial reporting. ANS: T 7. Primary recipients of financial statement information are internal management. ANS: F 8. The Management Reporting System is a nondiscretionary system. ANS: F 9. When evaluating decision alternatives, one option is to take no action. ANS: T 10. In most cases intangible decision criteria can be quantified. ANS: F 11. One benefit of the Management Reporting System is that it can alert management to delays in project implementation. ANS: T 12. Responsibility refers to an individual’s obligation to achieve desired results. ANS: T 13. A firm with a wide span of control tends to have relatively more layers of management. ANS: F 14. The control function entails evaluating a process against a standard and, if necessary, taking corrective action. ANS: T 15. Standards are the basis for evaluating actual performance. ANS: T 16. A report is said to have information content if it eliminates uncertainty associated with a problem facing the decision maker. ANS: F 17. An inventory out-of-stock report is an example of a programmed, on-demand report. ANS: T 18. A principle of responsibility accounting is that managers are responsible for controllable and uncontrollable costs. ANS: F 19. The manager of a cost center is responsible for cost control and revenue generation. ANS: F 20. Designing an effective management reporting system does not require an understanding of the information managers need to deal with the problems they face. ANS: F 21. The formalization of tasks principle suggests that management should structure the firm around the unique skills sets of key individuals. ANS: F 22. If a manager delegates responsibility to a subordinate, he or she must also grant the subordinate authority to make decisions. ANS: T 23. Operational control involves motivating managers at all levels to use resources, including materials, personnel, and financial assets, as productively as possible. ANS: F 24. The block code is the coding scheme most appropriate for a chart of accounts. ANS: T MULTIPLE CHOICE 1. The coding scheme most appropriate for a chart of accounts is a. sequential code b. block code c. group code d. mnemonic code ANS: B 2. A common use for sequential coding is a. creating the chart of accounts b. identifying inventory items c. identifying documents d. identifying fixed assets ANS: C 3. The most important advantage of sequential coding is that a. missing or unrecorded documents can be identified b. the code itself lacks informational content c. items cannot be inserted d. deletions affect the sequence ANS: A 4. When a firm wants its coding system to convey meaning without reference to any other document, it would choose a. an alphabetic code b. a mnemonic code c. a group code d. a block code ANS: B 5. The most important advantage of an alphabetic code is that a. meaning is readily conveyed to users b. sorting is simplified c. the capacity to represent items is increased d. missing documents can be identified ANS: C 6. Entries into the General Ledger System (GLS) can be made using information from a. the general journal b. a journal voucher which represents a summary of similar transactions c. a journal voucher which represents a single, unusual transaction d. all of the above ANS: D 7. Which statement is not correct? The general ledger master file a. is based on the firm’s chart of account b. contains a record for control accounts c. is an output of the Financial Reporting System (FRS) d. supplies information for management decision making ANS: C 8. What type of data is found in the general ledger master file? a. a chronological record of all transactions b. the balance of each account in the chart of accounts c. budget records for each account in the chart of accounts d. subsidiary details supporting a control account ANS: B 9. Which report is not an output of the Financial Reporting System (FRS)? a. variance analysis report b. statement of cash flows c. tax return d. comparative balance sheet ANS: A 10. Which steps in the Financial Accounting Process are in the correct sequence? a. record the transaction, post to the ledger, prepare the adjusted trial balance, enter adjusting entries, prepare financial statements b. record the transaction, prepare the unadjusted trial balance, record adjusting journal entries, record closing entries, prepare financial statements c. record the transaction, post to the ledger, record adjusting entries, prepare the unadjusted trial balance, prepare financial statements d. record the transaction, post to the ledger, prepare the adjusted trial balance, prepare financial statements, record closing entries ANS: D 11. Which statement is not correct? a. the post-closing trial balance reports the ending balance of each account in the general ledger b. one purpose of preparing the unadjusted trial balance is to ensure that debits equal credits c. financial statements are prepared based on the unadjusted trial balance d. the unadjusted trial balance reports control account balances but omits subsidiary ledger detail ANS: C 12. What account appears on the postclosing trial balance? a. income summary b. machinery c. rent expense d. interest income ANS: B 13. Financial statements are prepared from the a. b. c. d. trial balance adjusted trial balance general ledger general journal ANS: B 14. Risk exposures in the General Ledger and Financial Reporting Systems include all of the following except a. loss of the audit trail b. unauthorized access to the general ledger c. loss of physical assets d. general ledger account out of balance with the subsidiary account ANS: C 15. Which situation indicates an internal control risk in the General Ledger/Financial Reporting Systems (GL/FRS)? a. the employee who maintains the cash journal computes depreciation expense b. the cash receipts journal voucher is approved by the Treasurer c. the cash receipts journal vouchers are prenumbered and stored in a locked safe d. the employee who maintains the cash receipts journal records transactions in the accounts receivable subsidiary ledger ANS: D 16. With a limited work force and a desire to maintain strong internal control, which combination of duties performed by a single individual presents the least risk exposure? a. maintaining the inventory ledger and recording the inventory journal voucher in the general ledger b. recording the inventory journal voucher in the general ledger and maintaining custody of inventory c. maintaining the cash disbursements journal and recording direct labor costs applied to specific jobs d. preparing the accounts payable journal voucher and recording it in the general ledger ANS: C 17. The audit trail fulfills all of the following purposes except a. provides the ability to answer inquiries b. ensures the accuracy of the application software c. fulfills governmental regulations d. offers a means for preventing, detecting, and correcting errors ANS: B 18. Which best describes a batch process General Ledger System (GLS) a. paper documents are eliminated b. the general ledger master file is updated each night c. there is a time lag between transaction processing and posting to the general ledger d. no direct access or querying of the General Ledger is possible ANS: C 19. An advantage of a batch General Ledger System (GLS) is that a. separation between authorization and transaction processing is strictly enforced b. the general ledger master file is recreated with each update c. updates and reconciliation of transactions occur as a step within the transaction cycle d. errors and out-of-balance conditions are identified at the end of the month ANS: C 20. A characteristic of the Management Reporting System (MRS) is a. the MRS operates in conformity with generally accepted accounting principles b. it is a legal requirement that the MRS be installed and functioning properly c. the MRS is developed by implementing SEC requirements d. the MRS focuses on internal decision-making information ANS: D 21. Which statement is not true? a. authority refers to an individual’s obligation to achieve desired results b. if an employee is given the responsibility for a task, that employee should be given authority to make decisions within the limits of that task c. the level of detail provided to an employee is a function of the employee’s position with the firm d. all of the above are true ANS: A 22. Which statement is not true? The manager’s span of control a. is narrow for routine and repetitive tasks b. is related to the number of layers of management c. affects the amount of detail provided to a manager d. can affect employee morale and motivation ANS: A 23. Short-range planning involves a. setting goals and objectives of the firm b. planning the production schedule for the next quarter c. planning the growth of the firm d. deciding on the degree of diversification among the firm’s products ANS: B 24. Long-range planning involves a. planning the marketing and promotion for a product b. presenting department heads with budgetary goals for the next year c. preparing a work force utilization budget for the next quarter d. deciding the optimum size of the firm ANS: D 25. The level of management that makes tactical planning decisions is a. top management b. middle management c. operations management d. front-line management ANS: B 26. The decision to enter a new market is an example of a. strategic planning b. tactical planning c. management control d. operational control ANS: A 27. All of the following are elements of operational control decisions except a. determining the scope of the activity b. setting operating standards c. evaluating performance d. taking corrective action when necessary ANS: A 28. In contrast to tactical planning decisions, management control decisions, and operational control decisions, strategic planning decisions usually a. are more focused b. have a shorter time frame c. are unstructured d. have a high degree of certainty ANS: C 29. Which of the following management principles affects the management reporting system? a. formalization of tasks b. authorization c. span of control d. all of the above ANS: D 30. All of the following are elements of problem structure except a. certainty b. data c. procedures d. objectives ANS: A 31. All of the following are examples of programmed reports except a. cash flow reports for Division B b. year-to-date local income tax payments made by all employees living in City X and working in City Y c. inventory exception reports for Division G d. equipment utilization reports for Plant M ANS: B 32. A fundamental principle of responsibility accounting is that a. managers are accountable only for items they control b. a manager’s span of control should not exceed eight people c. structured reports should be prepared weekly d. the information flow is in one direction, top-down ANS: A 33. Which statement is not true? Responsibility accounting a. involves both a top-down and bottom-up flow of information b. acknowledges that some economic events cannot be traced to any manager c. creates a budget d. compares actual performance with budget ANS: B 34. What mechanism is used to convey to managers the standards by which their performance will be measured? a. the responsibility report b. the scheduled report c. the budget d. all of the above ANS: C 35. All of the following concepts encourage goal congruence except a. detailed information reporting at all management levels b. authority and responsibility c. formalization of tasks d. responsibility accounting ANS: A 36. Which of the following statements is NOT true? a. Sorting records that are coded alphabetically tends to be more difficult for users than sorting numeric sequences. b. Mnemonic coding requires the user to memorize codes. c. Sequential codes carry no information content beyond their order in the sequence. d. Mnemonic codes are limited in their ability to represent items within a class. ANS: B 37. Which file has as its primary purpose to present comparative financial reports on a historic basis? a. journal voucher history file b. budget master file c. responsibility file d. general ledger history file ANS: D 38. All of the following are characteristics of the strategic planning process except the a. emphasis on both the short and long run. b. review of the attributes and behavior of the organization’s competition. c. analysis of external economic factors. d. analysis of consumer demand. ANS: A 39. Which of the following performance measures can not result in dysfunctional behavior? a. price variance b. quotas c. ROI d. net income e. all of the above can result in dysfunctional behavior ANS: E 40. Which of the following best describes a profit center: a. authority to make decisions affecting the major determinants of profit, including the power to choose its markets and sources of supply. b. authority to make decisions affecting the major determinants of profit, including the power to choose its markets and sources of supply, and significant control over the amount of invested capital. c. authority to make decisions over the most significant costs of operations, including the power to choose the sources of supply. d. authority to provide specialized support to other units within the organization. e. responsibility for combining the raw materials, direct labor, and other factors of production into a final product. ANS: A SHORT ANSWER 1. List, in order, the steps in the Financial Accounting Process. 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. ANS: 1. Capture the transaction on source documents. 2. Record in special journals. 3. Post to subsidiary ledger. 4. Post to general ledger (using journal vouchers). 5. Prepare the unadjusted trial balance. 6. Make adjusting entries. 7. Journalize and post adjusting entries. 8. Prepare adjusted trial balance. 9. Prepare financial statements. 10. Journalize and post closing entries. 11. Prepare the post-closing trial balance. 2. List two duties that the general ledger clerk should not perform. ANS: make entries in special journals or subsidiary ledgers; prepare journal vouchers; maintain custody of physical assets 3. Explain the purpose and contents of the general ledger master file. ANS: The general ledger master file is the main file on the general ledger database. It is based on the firm’s chart of accounts. Each record is either a general ledger account (e.g., sales) or a control account (e.g., the accounts payable control) for one of the subsidiary ledgers. The general ledger master file contains the following for each account: the account number, description, account class (e.g., asset), the normal balance (debit or credit), beginning balance, total debits for period, total credits for period, and current balance. 4. Explain two types of coding schemes and give examples of their use. ANS: Sequential codes represent items in some sequential order. Prenumbered checks are one example. Block codes use sequential numbering in specific parts of the total code–all current assets begin with ‘1,’ fixed asset ‘2,’ etc. Traditional charts of accounts use block codes and start assets with 1, liabilities with 2, etc. Alphabetic codes are similar to numeric codes with increased options. A two character code AA has potential for 676 items (26 26) whereas a two digit code can accommodate only 100 (10 10). Mnemonic codes use letters with meaning. The postal state abbreviations are mnemonic. 5. Why do many firms no longer use a general journal? What has taken its place? ANS: Many firms have replaced a traditional general journal with a journal voucher system. Each entry is documented on a prenumbered journal voucher which contains additional information, such as authorization, which enhances control. A voucher may contain information on a number of related transactions. 6. What are the major exposures in the general ledger/financial reporting system? ANS: The primary exposures are: a defective or lost audit trail, unauthorized access, GL accounts out of balance with subsidiary ledger accounts, and incorrect account balances due to unauthorized or incorrect entries. 7. Why is the audit trail necessary? ANS: The audit trail is needed for several reasons: to provide the ability to answer inquiries from customers and suppliers, to reconstruct files if lost, to provide historical data to auditors, to satisfy government regulations, and for error control. 8. The _______________________________ principle suggests that management should structure the firm around the work it performs rather than around individuals with unique skills. ANS: formalization of tasks 9. Employees who are responsible for a task must have the __________________________ to make decisions within the limits of the responsibility delegated. ANS: authority 10. __________________________ refers to the number of subordinates directly under a manager’s control. ANS: Span of control 11. The difference between the actual performance and the standard is called the __________________________. ANS: variance 12. How does the Management by Exception principle affect the Management Reporting System? ANS: Reports should focus on differences between actual and expected numbers in key factors that are symptomatic of potential problems. Reports that provide unnecessary details about routine, in control items should be avoided. 13. For reports to be useful they must have information content. Describe a reporting objective which gives reports information content. ANS: Reports must reduce the level of uncertainty associated with a problem facing the decision maker, and must influence the behavior of the decision maker in a positive way. 14. What is information overload? How does it affect decision-making? ANS: Information overload refers to a situation in which a manager receives more information than can be assimilated. A natural response to this is to ignore information or select only some. In addition, intuition can displace logic. 15. Explain the phrase “span of control.” What are the implications for the management reporting system of this principle? ANS: A manager’s span of control is the number of subordinates he/she supervises directly. The broader a manager’s span of control, the more autonomy his/her subordinates enjoy–the less involved the manager is in their specific tasks. This impacts the MRS in terms of the level of detail a manager requires. If the span is wide, less detail; if narrow, more. 16. Explain the three types of responsibility centers. ANS: Cost centers are organizational units with responsibility for cost management. Profit centers have responsibility for both cost management and revenue generation. Investment centers have responsibility for cost management, revenue generation, and also the investment and use of assets. 17. Describe at least three characteristics of strategic planning decisions and their information requirements. ANS: have long time frames–create a need for information that supports forecasting, require summarized information–not encumbered by detail, tend to be nonrecurring–thus having little historical data in support involve a lot of uncertainty–i.e., are unstructured decisions are broad in scope–thus requiring broad based information often require significant external information–generated beyond the information system itself. 18. What three elements must be present for a problem to be “structured?” ANS: data, procedures, objectives 19. How does management by exception help to alleviate information overload by a manager? ANS: The principle of management by exception is that managers should limit their attention to potential problem areas rather than being involved with every activity or decision. Thus, only situations which are not proceeding as scheduled are highlighted by the reports and analyzed by the manager. Thus, the manager does not have to weed through multiple reports to find the situations which need attention. 20. What is a data warehouse? ANS: A data warehouse is a relational database management system that has been designed specifically to meet the needs of data mining. The warehouse is a central location that contains operational data about current events (within the past 24 hours) as well as events that have transpired over many years. ESSAY 1. List and explain the six basic files in the general ledger database. ANS: The general ledger master file is the main file on the general ledger database. It is based on the firm’s chart of accounts. Each record is either a separate general ledger account (e.g., sales) or a control account (e.g., the accounts payable control) for one of the subsidiary ledgers. The general ledger history file contains the same information for prior periods. The journal voucher file contains all of the journal vouchers processed in the current period. The journal voucher history file contains journal vouchers for past periods. The responsibility center file contains the revenues, expenses, and other data for individual responsibility centers. The budget master file contains budgeted amounts for responsibility centers. 2. Describe the three elements of problem structure. Contrast a structured problem to an unstructured problem. Describe which levels of management typically deal with structured problems and with unstructured problems. ANS: Problem structure has three elements: (1) Data–the values used to represent factors that are relevant to the problem; (2) Procedures–the sequence of steps or decision rules used in solving the problem; and (3) Objectives–the results the decision maker desires to attain by solving the problem. When all three elements of problem structure are known with certainty, the problem is structured. In unstructured problems the data requirements are uncertain, and/or the procedures are not specified, and/or the solution objectives have not been fully developed. In general, structured problems are handled at the operations level and partially structured problems are handled by operations, tactical, and strategic management. Usually, strategic management handles unstructured problems. 3. Many financial reports produced by organizations are nondiscretionary–publicly traded firms have no choice but to prepare income statements, tax returns, etc. Applications that are part of the management reporting system are discretionary–they are optional. How does this characteristic affect the system? ANS: Unlike nondiscretionary reports whose content, timing, even format are prescribed by regulatory or authoritative bodies, discretionary reports are whatever management feels is needed–in content, timing, format, and use. The MRS can be an important part of the firm’s internal control system. By summarizing activities, highlighting trends, and identifying exceptions from normal performance, reports can greatly enhance management’s understanding of operations. These can be whatever management feels is necessary to make good decisions. The expansion of the MRS must be guided by common sense. If too many reports are generated, information overload results. If the cost of the system exceeds the perceived benefits, the organization loses. 4. There are two basic types of management reports–programmed and ad hoc. Describe each and give examples. ANS: Programmed reports provide information to solve anticipated problems and make normal decisions. They include scheduled reports such as daily sales reports and on-demand reports generated by need such as inventory below reorder point (the report is generated when the inventory level fall to reorder–the report is demanded by the system based on the previously set inventory level). Ad hoc reports are the result of immediate need for information and may take the form of database queries on sales of a particular item mentioned in a news report. 5. Describe at least three attributes of an effective report. ANS: Effective reports tend to share several attributes: relevance–relevant data supports the manager’s decision needs, summarization–data should be at the appropriate level of summarization for the manager receiving it, exception orientation–this highlights what is not going as planned, accuracy–is the freedom from material errors, completeness–with no key pieces of information missing, timeliness–information that is reasonable complete and accurate in a reasonable time frame is more valuable than perfect information too late, conciseness–conciseness is a counter measure to information overload. 6. What is the implication for the Management Reporting System of an organization that implements the formalization of tasks principle? ANS: Information requirements are defined by a position, not by the person filling that position. When there is a personnel change, there should be no major changes in the information needed by the new employee; it will be essentially the same as that needed by the former employee. Internal control is strengthened because information is provided based on the requirements of the position (a need to know basis). 7. What are the reasons the companies use coding schemes in their accounting information systems? ANS: Companies use coding schemes in their AISs because codes concisely represent large amounts of complex information that would otherwise be unmanageable. They also provide a means of accountability over the completeness of the transactions processed and identify unique transactions and accounts within a file. In addition, coding supports the audit function by providing an effective audit trail. 8. Compare and contrast the relative advantages and disadvantages of sequential, block, group, alphabetic and mnemonic codes. ANS: Sequential codes are appropriate for items in either an ascending or descending sequence, such as the numbering of checks or source documents. An advantage is that during batch processing, any gaps detected in the sequence is a signal that a transaction may be missing. A disadvantage is that the codes carry little, if any, information other than the sequence order. Another disadvantage is that sequential codes are difficult to manage when items need to be added; the sequence needs either to be reordered or the items must be added to the end of the list. Block codes provide some remedies to sequential codes by restricting each class to a prespecified range. The first digit typically represents a class, whereas the following digits are sequential items which may be spaced in intervals in case of future additions. An example of block coding is a chart of accounts. A disadvantage of block coding is that the information content does not provide much meaning, i.e. an account number only means something if the chart of accounts is known. Group codes may be used to represent complex items or events involving two or more pieces of related data. The code is comprised of fields which possess specific meaning. The advantages of group codes over sequential and block codes are 1) they facilitate the representation of large amounts of diverse data, 2) they allow complex data structures to be represented in a hierarchical form that is logical and thus more easily remembered by humans, and 3) they permit detailed analysis and reporting both within an item class and across different classes of items. A disadvantage is that the codes may be overused to link classes which do not need to be linked, and thus creating a more complex coding system that is necessary. Alphabetic codes may be used sequentially or in block or group codes. An advantage is that a system which uses alphabetic codes can represent far more situations than a system with numeric codes given a specific field size. Some disadvantages are that sequentially assigned codes mostly have little meaning. Also, humans typically find alphabetic codes more difficult to sort than numeric data. Lastly, mnemonic codes are alphabetic characters in the form of acronyms, abbreviations or other combinations that convey meaning. The meaning aspect is its advantage. A disadvantage of mnemonic codes is that they are limited in their ability to represents items within a class i.e. names of all of American Express's customers. 9. Contrast the four decision types, strategic planning, tactical planning, management control and operational control, by the four decision characteristics, time frame, scope, level of details, recurrence, and certainty. ANS: Strategic planning decisions are 1) typically long-term in nature, 2) have a high impact on the firm, 3) require highly summarized information, 4) typically non-recurring problems/opportunities, and 5) uncertain in nature. Tactical planning decisions are 1) typically medium-term in nature, 2) have a limited impact on the firm, 3) require detailed information, 4) typically are periodically recurring problems/opportunities, and 5) highly certain in nature. Management control decisions are 1) typically medium-term in nature, 2) have a narrower impact on the firm, 3) require moderately summarized information, 4) typically are periodically recurring problems/opportunities, and 5) uncertain in nature. Operational control decisions are 1) typically short-term in nature, 2) have the narrowest impact on the firm, 3) require highly detailed information, 4) typically are periodically recurring problems/opportunities, and 5) highly certain in nature. Chapter 9—Database Management Systems TRUE/FALSE 1. The database approach to data management is sometimes called the flat file approach. ANS: F 2. The Database Management System provides a controlled environment for accessing the database. ANS: T 3. To the user, data processing procedures for routine transactions, such as entering sales orders, appear to be identical in the database environment and in the traditional environment. ANS: T 4. An important feature associated with the traditional approach to data management is the ability to produce ad hoc reports. ANS: F 5. The Data Definition Language is used to insert special database commands into application programs. ANS: F 6. There is more than one conceptual view of the database. ANS: F 7. In the database method of data management, access authority is maintained by systems programming. ANS: F 8. The physical database is an abstract representation of the database. ANS: F 9. A customer name and an unpaid balance is an example of a one-to-many relationship. ANS: F 10. In the relational model, a data element is called a relation. ANS: F 11. Data normalization groups data attributes into tables in accordance with specific design objectives. ANS: T 12. Under the database approach, data is viewed as proprietary or “owned” by users. ANS: F 13. The data dictionary describes all of the data elements in the database. ANS: T 14. A join builds a new table by creating links. ANS: F 15. The deletion anomaly is the least important of the problems affecting unnormalized databases. ANS: F 16. A deadlock is a phenomenon that prevents the processing of transactions. ANS: T 17. Timestamping is a control that is used to ensure database partitioning. ANS: F 18. A lockout is a software control that prevents multiple users from simultaneous access to data. ANS: T 19. Logical database design is the foundation of the conceptual design. ANS: F 20. An entity is any physical thing about which the organization wishes to capture data. ANS: F 21. An ER diagram is a graphical representation of a data model. ANS: T 22. The term occurrence is used to describe the number of attributes or fields pertaining to a specific entity. ANS: F 23. Cardinality describes the number of possible occurrences in one table that are associated with a single occurrence in a related table. ANS: T 24. A table in third normal form is free of partial dependencies, multiple dependencies, and transitive dependencies. ANS: F 25. Improperly normalized databases are associated with three types of anomalies: the update anomaly, the insertion anomaly, and the deletion anomaly. ANS: T MULTIPLE CHOICE 1. All of the following are basic data management tasks except a. data deletion b. data storage c. data attribution d. data retrieval ANS: C 2. The task of searching the database to locate a stored record for processing is called a. data deletion b. data storage c. data attribution d. data retrieval ANS: D 3. Which of the following is not a problem usually associated with the flat-file approach to data management? a. data redundancy b. restricting access to data to the primary user c. data storage d. currency of information ANS: B 4. Which characteristic is associated with the database approach to data management? a. data sharing b. multiple storage procedures c. data redundancy d. excessive storage costs ANS: A 5. Which characteristic is not associated with the database approach to data management? a. the ability to process data without the help of a programmer b. the ability to control access to the data c. constant production of backups d. the inability to determine what data is available ANS: D 6. The textbook refers to four interrelated components of the database concept. Which of the following is not one of the components? a. the Database Management System b. the Database Administrator c. the physical database d. the conceptual database ANS: D 7. Which of the following is not a responsibility of the Database Management System? a. provide an interface between the users and the physical database b. provide security against a natural disaster c. ensure that the internal schema and external schema are consistent d. authorize access to portions of the database ANS: C 8. A description of the physical arrangement of records in the database is a. the internal view b. the conceptual view c. the subschema d. the external view ANS: A 9. Which of the following may provide many distinct views of the database? a. the schema b. the internal view c. the user view d. the conceptual view ANS: C 10. Users access the database a. by direct query b. by developing operating software c. by constantly interacting with systems programmers d. all of the above ANS: A 11. The Data Definition Language a. identifies, for the Database Management System, the names and relationships of all data elements, records, and files that comprise the database b. inserts database commands into application programs to enable standard programs to interact with and manipulate the database c. permits users to process data in the database without the need for conventional programs d. describes every data element in the database ANS: A 12. The Data Manipulation Language a. defines the database to the Database Management System b. transfers data to the buffer area for manipulation c. enables application programs to interact with and manipulate the database d. describes every data element in the database ANS: C 13. Which statement is not correct? A query language like SQL a. is written in a fourth-generation language b. requires user familiarity with COBOL c. allows users to retrieve and modify data d. reduces reliance on programmers ANS: B 14. Which duty is not the responsibility of the Database Administrator? a. to develop and maintain the Data Dictionary b. to implement security controls c. to design application programs d. to design the subschema ANS: C 15. In a hierarchical model a. links between related records are implicit b. the way to access data is by following a predefined data path c. an owner (parent) record may own just one member (child) record d. a member (child) record may have more than one owner (parent) ANS: B 16. Which term is not associated with the relational database model? a. tuple b. attribute c. collision d. relation ANS: C 17. In the relational database model a. relationships are explicit b. the user perceives that files are linked using pointers c. data is represented on two-dimensional tables d. data is represented as a tree structure ANS: C 18. In the relational database model all of the following are true except a. data is presented to users as tables b. data can be extracted from specified rows from specified tables c. a new table can be built by joining two tables d. only one-to-many relationships can be supported ANS: D 19. In a relational database a. the user’s view of the physical database is the same as the physical database b. users perceive that they are manipulating a single table c. a virtual table exists in the form of rows and columns of a table stored on the disk d. a programming language (COBOL) is used to create a user’s view of the database ANS: B 20. The update anomaly in unnormalized databases a. occurs because of data redundancy b. complicates adding records to the database c. may result in the loss of important data d. often results in excessive record insertions ANS: A 21. The most serious problem with unnormalized databases is the a. update anomaly b. insertion anomaly c. deletion anomaly d. none of the above ANS: C 22. The deletion anomaly in unnormalized databases a. is easily detected by users b. may result in the loss of important data c. complicates adding records to the database d. requires the user to perform excessive updates ANS: B 23. Which statement is correct? a. in a normalized database, data about vendors occur in several locations b. the accountant is responsible for database normalization c. in a normalized database, deletion of a key record could result in the destruction of the audit trail d. connections between M:M tables is provided by a link table ANS: D 24. Which of the following is not a common form of conceptual database model? a. hierarchical b. network c. sequential d. relational ANS: C 25. Which of the following is a relational algebra function? a. restrict b. project c. join d. all are relational algebra functions ANS: D 26. Which statement is false? a. The DBMS is special software that is programmed to know which data elements each user is authorized to access. b. User programs send requests for data to the DBMS. c. During processing, the DBMS periodically makes backup copies of the physical database. d. The DBMS does not control access to the database. ANS: D 27. All of the following are elements of the DBMS which facilitate user access to the database except a. query language b. data access language c. data manipulation language d. data definition language ANS: B 28. Which of the following is a level of the database that is defined by the data definition language? a. user view b. schema c. internal view d. all are levels or views of the database ANS: D 29. An example of a distributed database is a. partitioned database b. centralized database c. networked database d. all are examples of distributed databases ANS: A 30. Data currency is preserved in a centralized database by a. partitioning the database b. using a lockout procedure c. replicating the database d. implementing concurrency controls ANS: B 31. Which procedure will prevent two end users from accessing the same data element at the same time? a. data redundancy b. data replication c. data lockout d. none of the above ANS: C 32. The advantages of a partitioned database include all of the following except a. user control is enhanced b. data transmission volume is increased c. response time is improved d. risk of destruction of entire database is reduced ANS: B 33. A replicated database is appropriate when a. there is minimal data sharing among information processing units b. there exists a high degree of data sharing and no primary user c. there is no risk of the deadlock phenomenon d. most data sharing consists of read-write transactions ANS: B 34. What control maintains complete, current, and consistent data at all information processing units? a. deadlock control b. replication control c. concurrency control d. gateway control ANS: C 35. Data concurrency a. is a security issue in partitioned databases b. is implemented using timestamping c. may result in data lockout d. occurs when a deadlock is triggered ANS: B 36. Entities are a. nouns that are depicted by rectangles on an entity relationship diagram b. data that describe the characteristics of properties of resources c. associations among elements d. sets of data needed to make a decision ANS: A 37. A user view a. presents the physical arrangement of records in a database for a particular user b. is the logical abstract structure of the database c. specifies the relationship of data elements in the database d. defines how a particular user sees the database ANS: D 38. All of the following are advantages of a partitioned database except a. increased user control by having the data stored locally b. deadlocks are eliminated c. transaction processing response time is improved d. partitioning can reduce losses in case of disaster ANS: B 39. Each of the following is a relational algebra function except a. join b. project c. link d. restrict ANS: C SHORT ANSWER Use the following words to complete the sentences. Database Administrator data redundancy query language sequential structure Data Dictionary Index Sequential Access Method schema subschema 1. _________________________ occurs when a specific file is reproduced for each user who needs access to the file. ANS: Data redundancy 2. The conceptual view of the database is often called ____________________. ANS: schema 3. The ____________________ allows users to retrieve and modify data easily. ANS: query language 4. The __________________________ authorizes access to the database. ANS: Database Administrator 5. The __________________________ describes every data element in the database. ANS: Data Dictionary 6. Describe a specific data element, entity, and record type in the expenditure cycle. ANS: data element: vendor’s name or account balance; entity: vendor; record type: purchase requisition, purchase order 7. What is the relationship between a database table and a user view? ANS: User views are derived database tables. A single table may contribute data to several different views On the other hand, simple views may be constructed from a single table. 8. How does the database approach solve the problem of data redundancy? ANS: Data redundancy is not a problem with the database approach because individual data elements need to be stored only once yet be available to multiple users. 9. Explain how linkages between relational tables are accomplished. ANS: Tables that are logically related in the data model need to be physically linked. The degree of association between the tables (i.e., 1:1, 1:M, or M:M) determines how the linking occurs. The key-assignment rules for linking tables are discussed below. Where a true 1:1 association exists between tables, either (or both) primary keys may be embedded as foreign keys in the related table. Where a 1:M (or 1:0,M) association exists, the primary key of the 1 side is embedded in the table of the M side. To represent the M:M association between tables, a link table needs to be created that has a combined (composite) key consisting of the primary keys of two related tables. 10. Explain the basic results that come from the restrict, project, and join functions. ANS: A restrict extracts selected rows from a table–records that satisfy prescribed conditions–to create a new table. A project extracts selected attributes (columns) from a table to create a new table. A join builds a new table, from two existing tables, by matching rows on a value of a common attribute. 11. Explain the purpose of an ER diagram in database design. ANS: The Entity Relationship (ER) diagram is the graphical representation technique used to depict a data model. Each entity in a ER diagram is named in the singular noun form such as Customer rather than Customers. The labeled line connecting two entities describes the nature of the association between them. This association is represented with a verb such as shipped, requests, or receives. The ER diagram also represents cardinality (the degree of association between two entities). Four basic forms of cardinality are possible: zero or one (0,1), one and only one (1,1), zero or many (0,M), and one or many (1,M). These are combined to represent logical associations between entities such as 1:1, 1:0,M, and M:M. 12. What are two types of distributed databases? ANS: Partitioned and replicated databases. 13. Describe an environment when a firm should use a partitioned database. ANS: A partitioned database approach works best in organizations that require minimal data sharing among its information processing units and when a primary user of the data can be identified. 14. Explain how to link tables in (1:1) association. Why may this be different in a (1:0,1) association? ANS: Where a true 1:1 association exists between tables, either (or both) primary keys may be embedded as foreign keys in the related table. On the other hand, when the lower cardinality value is zero (1:0,1) a more efficient table structure can be achieved by placing the one-side (1:) table’s primary key in the zero-or-one (:0,1) table as a foreign key. Assume that a company has 1000 employees but only 100 of them are sales staff. Assume also that each sales person is assigned a company car. Therefore, every occurrence in the Employee entity is associated with either zero or one occurrence in the Company Car entity. If we assigned the Company Car (:0,1) side primary to the Employee (:1) table as a foreign key then most of the foreign will have null (blank) values. While this approach would work, it could cause some technical problems during table searches. Correctly applying the key-assignment rule solves this problem because all Company Car records will have an employee assigned and no null values will occur. APPENDIX QUESTION 15. Why are the hierarchical and network models called navigational databases? ANS: These are called navigational models because traversing or searching them requires following a predefined path which is established through explicit linkages between related records. ESSAY 1. Give three examples that illustrate how cardinality reflects an organization’s underlying business rules. ANS: 1) When an organization decides to purchases the same items of inventory from different suppliers, the cardinality between the Supplier and Inventory tables is M:M. 2) When a the company purchases all items of a certain type from only one supplier, the cardinality between Supplier and Inventory tables is 1:M respectively. 3) A policy that a separate receiving report is prepared for the receipt of goods specified on a single purchase order will result in a 1:1 cardinality between the receiving report and purchase order tables. If, however, multiple purchase orders are combined on a single receiving report then the cardinality between these tables will be 1: M respectively. 2. Explain the three types of anomalies associated with database tables that have not been normalized. ANS: The update anomaly is the result of data redundancy. If a data element is stored in more than one place, it must be updated in all places. If this does not happen, the data are inconsistent. The insertion anomaly occurs when too much data is stored together–when vendor information is only stored with specific inventory items. Until items are purchased from a given vendor, the vendor cannot be added to the database. The deletion anomaly is the opposite of the insertion anomaly–if a vendor supplies only one item, and the firm discontinues that item, all information on the vendor is lost when vendor information is only stored with specific inventory items. 3. What are the four elements of the database approach? Explain the role of each. ANS: Users are the individuals in the organization who access the data in the database. This may happen via user programs or by direct query. The database management system is a set of programs that control access to the database and that manage the data resource through program development, backup and recovery functions, usage reporting, and access authorization. The database administrator is a function (which may involve part of one individual’s duties or an entire department) which manages the database resources through database planning, design, implementation, operation and maintenance, and growth and change. The physical database is the only physical form that the database has. It is comprised of magnetic spots on magnetic media. 4. Explain the three views of a database. ANS: The unique internal view of the database is the physical arrangement of records which describes the structure of data records, the linkages between files, and the physical arrangement and sequence of records in the file. The unique conceptual view (or schema) represents the database logically and abstractly. The many user views (or subschema) define the portion of a database that an individual user is authorized to access. 5. Explain a database lockout and the deadlock phenomenon. Contrast that to concurrency control and the timestamping technique. Describe the importance of these items in relation to database integrity. ANS: In a centralized database, a lockout is used to ensure data currency. A lockout prevents simultaneous access to individual data elements by different information processing units (IPU). When one IPU requests access to a data element, a lock is put on the file, record, or element. No other IPU can access the file, record, or element until the lock is released. In a partitioned database, lockouts are also used to ensure data currency. It is possible, however, for multiple sites to place locks on records that results in a deadlock condition which prevents transactions from processing. All transactions are in a “wait” state until the locks are removed. A deadlock cannot be resolved without outside intervention from the user’s application, the DBMS, or the operating system. In a replicated database, a large volume of data flows between sites, and temporary inconsistencies in the database may occur. Concurrency control ensures that transactions executed at each IPU are accurately reflected in the databases of all other sites. A popular method for concurrency control is to timestamp transactions. Transactions that may be in conflict are assigned a system-wide timestamp. Then, the identified transactions are processed in timestamp order. Both database lockouts and concurrency controls are designed to ensure that the transactions are completely processed and that all transactions are accurately reflected in the firm’s databases. Failure to implement these controls can result in transactions being lost, being partially processed, or with inconsistent databases. 6. What are the key control implications of the absence of database normalization? ANS: When considering the quality of the data in a database, accountants should be aware of the outcomes of typical anomalies. The update anomaly can yield conflicting data in the database. The insertion anomaly can result in unrecorded transactions. The deletion anomaly can cause loss of accounting information and destruction of the audit trail. 7. In a distributed data processing system, a database can be centralized or distributed. What are the options? Explain. ANS: In a distributed data processing system, a database can be centralized or distributed. When the database is centralized, the entire database is stored at a central site which processes requests from users at remote locations. Certain concerns arise when data processing is distributed. Questions arise with regard to data currency when multiple users have access to the database. Database lockout prevents more than one user from making changes at the same time. Distributed databases can be partitioned with parts stored at different sites, or replicated, with the entire database stored in multiple locations. When the database is partitioned, users have more control over data stored at local sites, transaction processing time is improved, and the potential of data loss is reduced. When the database is replicated, the entire database is stored at multiple locations. This works well when the primary use of the database is for querying. When transactions are processed at many sites, problems of database concurrency arise. 8. What are the characteristics of a properly designed relational database table? ANS: The characteristics of a properly designed relational database table are: a. All occurrences at the intersection of a row and column are a single value. b. The attribute values in any column must all be of the same class. c. Each column in a given table must be uniquely named. d. Each row in the table must be unique in at least one attribute which is considered the primary key. 9. Ownership of data in traditional legacy systems often leads to data redundancy. This in turn leads to several data management problems. What are they? How does the database approach solve them? ANS: Data redundancy causes significant data management problems in three areas: data storage, data updating, and currency of information. Data storage is a problem because if multiple users need the data, it must be collected and stored multiple times at multiple costs. When multiple users hold the same information, changes must be updated in all locations or data inconsistency results. Failure to update all occurrence of a data item can affect the currency of the information. With a database system, these problems are solved. There is no data redundancy since a data item is stored only once. Hence changes require only a single update, thus leading to current value. 10. What services are provided by a database management system? ANS: Database management systems typically provide the following services: a. program development which permits both programmers and end users to create applications to access the database; b. backup and recovery is built in therefore reducing likelihood of data loss; c. database usage reporting captures statistics on what data is being used, by whom, when; and especially d. database access is provided to authorized users. 11. Discuss the key factors to consider in determining how to partition a corporate database. ANS: The partitioned approach works best for organizations that require minimal data sharing among users at remote sites. To the extent that remote users share common data, the problems associated with the centralized approach will apply. The primary user must now manage requests for data from other sites. Selecting the optimum host location for the partitions to minimize data access problems requires an in-depth analysis of end-user data needs. 12. Distinguish between a database lockout and a deadlock. ANS: To achieve data currency, simultaneous access to individual data elements or records by multiple users needs to be prevented. The solution to this problem is a database lockout, which is a software control that prevents multiple simultaneous accesses to data. A deadlock occurs when multiple users seeking access to the same set of records lockout each other. As a result, the transactions of all users assume a “wait” state until the locks are removed. A deadlock is a permanent condition that must be resolved by special software that analyzes each deadlock condition to determine the best solution. 13. Replicated databases create considerable data redundancy, which is in conflict with the database concept. Explain the justification of this approach. ANS: The primary justification for a replicated database is to support read-only queries in situations involving a high degree of data sharing, but no primary user exists. With data replicated at every site, data access for query purposes is ensured, and lockouts and delays due to network traffic are minimized. A potential problem arises, however, when replicated databases need to be updated by transactions. Since each site processes only local transactions, the common data attributes that are replicated at each site will be updated by different transactions and thus, at any point in time, will have uniquely different values. System designers need to employ currency control techniques to ensure that transactions processed at different locations are accurately reflected in all the databases copies. APPENDIX QUESTION 14. Contrast the navigational databases with relational databases. What is the primary advantage of the relational model? ANS: The most apparent difference between the relational model and navigational models is the way that data associations are represented to the user. In navigational models, data are represented in tree structures or network structures. The navigational database models have explicit links, called pointers, between records. Data are accessed using defined data paths. The relational model portrays data in the form of two-dimensional tables. Users do not perceive any pointers linking the tables. At the conceptual level (logical view) and the external level (user’s view), data are represented only as tables. Relations between tables are formed by an attribute (data element) that is common to the tables. This attribute is a primary key in one table and a foreign key in the other. The relational model is more flexible than a navigational model. Users can obtain data from the database by using the primary key and a database query language. Typically users do not require assistance from programmers to obtain answers to ad hoc queries. Chapter 10—The REA Approach to Business Process Modeling TRUE/FALSE 1. According to the REA philosophy, information systems should support only the needs of accounting professionals. ANS: F 2. Many believe that the accounting profession should shift away from debits and credits toward providing information that assists decision-making. ANS: T 3. Modern managers need both financial and nonfinancial information that traditional GAAP-based accounting systems are incapable of providing. ANS: T 4. The REA model is an alternative accounting framework for modeling an organization’s critical resources, events, and accounts. ANS: F 5. In REA, resources are assets of the organization as shown on a traditional balance sheet. ANS: F 6. In REA, events can be operating, information, or decision/management events. ANS: T 7. REA agents are individuals and departments that participate in an economic event. ANS: T 8. In a relational database environment, the focus is on transaction events, not the accounting artifacts. ANS: T 9. Under the REA approach to database design, an entity relationship diagram is used to model the relationships between an organization’s critical resources, events, and agents. ANS: F 10. Operating events are activities that produce goods and services. ANS: T 11. Decision/management events are activities associated with recording, maintaining, and reporting information. ANS: F 12. Information events are activities that lead to decisions being made. ANS: F 13. Entity relationship diagrams include operating, information, and decision events. Only operating events are included in an REA model. ANS: T 14. A data flow diagram is a data modeling tool that enables organizations to view each business process in detail. ANS: F 15. The primary purpose of an ER diagram is to identify data attributes that represent the conceptual user views that must be supported by the base tables. ANS: T 16. The REA approach generates an information system with only one user view. ANS: F 17. Organizations that use REA produce financial statements and reports directly from the event-driven data, not from traditional ledgers and journals. ANS: T 18. The REA model may enhance efficiency and competitive advantage though often productivity may decline. ANS: F 19. User views are set by REA modeling. ANS: F 20. REA focuses on business activities within business processes. It is event-oriented. ANS: T MULTIPLE CHOICE 1. Economic resources possess all of the following characteristics except a. assets b. measure expected future receipts c. scarce d. under the organization’s control ANS: B 2. The REA approach leads to more efficient operations in all of the following ways except a. identifying non-value-added activities b. storage of both financial and nonfinancial data in the same database c. storage of detailed data to support a wider range of management decisions d. standardizing data forms for simplicity ANS: D 3. Which type of events are included in an REA model? a. operating b. decision c. management d. information ANS: A 4. Decision/management events involve decisions relating to all of the following except a. record keeping b. planning c. evaluation d. control ANS: A 5. Information events involve all of the following except a. acts of recording b. acts of updating c. acts of evaluating d. acts of maintaining ANS: C 6. The ‘R’ in REA stands for a. ratios b. relationships c. resources d. reserves ANS: C 7. The ‘E’ in REA stands for a. events b. estimates c. economics d. entities ANS: A 8. The ‘A’ in REA stands for a. assets b. apportionment c. allocation d. agents ANS: D 9. Which of the following is an example of a decision/management event? a. preparing cost estimates for a new product b. requesting a report c. preparing sales invoices d. preparing performance reports ANS: B 10. All of the following are examples of operating events except a. receiving raw materials from a supplier b. preparing a cash disbursement voucher for payment to the supplier c. paying for inventories received d. shipping product to a customer ANS: B 11. Which types of events are included in entity relationship diagrams? a. operating events b. information events c. decision events d. all of the above ANS: D 12. Which of the following represents the order of the steps in the preparation of an REA model? a. organize events in order, identify resources and agents, identify links, identify operating events, assign cardinalities b. identify operating events, identify resources and agents, identify links, assign cardinalities, organize events in order c. identify operating events, organize events in order, identify resources and agents, identify links, assign cardinalities d. identify resources and agents, identify operating events, organize events in order, identify links, assign cardinalities ANS: C 13. Which of the following statement is correct? a. The REA model requires that phenomena be characterized in a manner consistent with the development of a single user view. b. The REA model requires that phenomena be characterized in a manner consistent with the development of a selected user view. c. The REA model requires that phenomena be characterized in a manner consistent with the development of a unique user view. d. The REA model requires that phenomena be characterized in a manner consistent with the development of a multiple user view. ANS: D 14. Which of the following is not an advantage of using the REA model? a. greater efficiency b. increased productivity c. more relevant and timely information d. simpler database creation ANS: D 15. Which of the following is not correct? a. Operating events trigger information events. b. Information events trigger operating events. c. Decision/management events trigger operating events. d. Information events trigger decision/management events. ANS: B 16. When developing an REA model, events need to be organized in sequence of a. completion b. length c. ease of analysis d. occurrence ANS: D 17. In an REA model, events are described from the perspective of a. the organization b. the designer c. the user d. the customer ANS: A 18. Which of the following is not an example of an information event? a. updating inventory records after a sale b. requesting a report c. preparing cost estimates for new products d. preparing sales invoices ANS: B SHORT ANSWER 1. What is a user view? ANS: A user view is the set of data that a particular user needs to achieve his or her assigned tasks. For example, a production manager’s view may include finished goods inventory, free manufacturing capacity, and vendor performance. 2. What do the letters ‘R,’ ‘E,’ and ‘A’ stand for in the term “REA model”? ANS: resources, events, and agents 3. Explain the relationship between operating events, information events, and decision/management events. How is the relationship circular? ANS: One view could be that decision/management events trigger operating events which trigger information events which trigger decision/management events. 4. What questions help identify operating events? ANS: Operating events can be identified by asking the following questions: Who did it? What happened? When did it happen? Where did it happen? What was involved? How did it happen? 5. Define the following: economic resources, economic events, and economic agents. ANS: Economic resources are the assets of the firm–objects that are both scarce and under the control of the enterprise. Economic events are activities that effect changes in resources. These can be operating events, information events, and decision/management events. Economic agents are individuals and departments that participate in an economic event. 6. Classify each of the following events as operating, information, or decision/management: implement new controls, request a report, update inventory records, print a credit report, change a customer address, prepare a sales invoice, ship a product, receive raw materials, pay for inventory. ANS: d, d, i, i, i, i, o, o, o 7. How does the REA model categorize events? ANS: operating, information, decision/management 8. What are the activities that are distinguished in value chain analysis? ANS: Value chain analysis distinguishes between an organization’s primary activities and its support activities. Organizations must focus on using its resources to achieve organizational objectives. 9. List at least three operating events. ANS: taking a customer’s order, shipping the product to the customer, receiving raw materials from a vendor, paying for inventories 10. List at least three information events. ANS: recording new customer data, updating inventory records, preparing credit reports, preparing sales invoices 11. List at least three decision/management events. ANS: hiring a salesperson, requesting a report, implementing new control measures, purchasing new equipment 12. Define the following: operating event, information event, and decision/management event. ANS: Operating events are things that happen. Information events are what is recorded. Decision/management events are what actions result. 13. Distinguish between resources, events, and agents. ANS: Resources are assets under the control of the enterprise. Events are activities that affect the resources. Agents are individuals and departments that participate in events. 14. Why would a company adopt the REA approach to database design? ANS: The REA approach leads to the development of a database which collects data needed to support the information needs of all users, not just the financial information traditionally collected by accounting systems. ESSAY 1. List and explain the steps involved in preparing an REA model of a business process. ANS: The preparation of an REA model of a business process can be described in five steps: 1. Identify the operating events that are to be included in the model. These are the events that support the strategic objectives of the organization and about which we need to gather information. 2. Organize the operating events in order of occurrence. Events are described as a verb-object combination, from the perspective of the organization. 3. Identify the resources and agents involved in each operating event by answering “who,” “what,” and “when” questions. 4. Identify the links between the resources, events, and agents. 5. Assign the cardinalities of all the entity relationships. 2. What is the REA model? What does it mean for accountants? ANS: The REA model is an alternative accounting framework for modeling an organization’s critical resources, events, and agents, and the relationships between them. Both accounting and non-accounting data can be identified, captured and stored in a centralized database which can provide information to all users in the organization. 3. How does the REA approach improve efficiency? ANS: The REA approach can help improve operating efficiency in several ways. It can help managers identify non-value-added activities for elimination, reduce the need for multiple data collection, storage, and maintenance by storing both financial and nonfinancial data in the same database, and such storage permits a wider range of management decision-making. 4. How do the entity relationship (ER) and the REA models differ? ANS: Although the general appearance of ER and REA models are similar, the lines in the ER model which connect entities are intersected by diamonds which represent what occurs in the relationships. The events in the ER model are broader and include information events and decision events as well as the operating events included in the REA model. The primary purpose of the ER diagram is to identify the data attributes that represent the conceptual user views that must be supported by the base tables and is view oriented. The REA model focuses on operating events and is event-oriented. 5. Why is a database preferred to the flat file system of traditional accounting? What does REA add? ANS: Relational database tables have replaced the flat files that represent the traditional accounting records–journals, subsidiary ledgers, and general ledger. Data capture in flat file systems was designed to fill the accounting records. It rarely involved information of value to non-accounting users. By focusing on transaction events rather that accounting “numbers,” other users can benefit. In traditional systems, only financially oriented data is captured. Non-economic events are ignored. REA can provide improved operational efficiency by: identifying nonvalue-added activities that can be eliminated; reduce the need for multiple data collection, storage and maintenance processes by storing financial and nonfinancial data in the same central database; and storing financial and nonfinancial data about business events in detail form which support a wider range of management decisions. 6. Explain how a sales invoice table can be used to replace traditional accounting records. ANS: The sales invoice table may be used to replace some traditional accounting records. First, since it contains the total amount due for each invoice, summing the Invoice Amount field for all records in the table yields total sales (equivalent to the Sales Journal) for the period. The accounts receivable balance (AR -Subsidiary Ledger) for a particular customer is calculated by summing the Invoice Amount fields for all of the customer’s open invoices. Total accounts receivable (General Ledger, AR-Control) is the sum of all the open invoice records in the entire table 7. Explain how a Disbursement Voucher table can be used to replace traditional accounting records. ANS: The Disbursement Voucher table provides three important pieces of information that is traditionally contained in formal accounting records. First, it is a record of checks written in payment of trade accounts for the period and thus replaces the traditional Cash Disbursements Journal. Second, the sum of the open items (unpaid vouchers) for a particular vendor is equivalent to the Accounts Payable Subsidiary ledger for the vendor. Finally, the total of all unpaid vouchers in the table constitutes the company’s accounts payable (General Ledger) balance. 8. Discuss the limitations of transaction based systems ANS: While the system described in the pages above represents a marked improvement over the traditional flat-file approach, it has serious shortcomings. This system is event-based which allows the user to capture in great detail information related to economic events such as sales to customers and purchases from suppliers. A look at the database tables, however, shows that they are designed to capture only financially oriented data. Non financial data are not captured. Furthermore, non-economic events are ignored by this system. An example of a non-economic event is a customer that enters a place of business, browses, inquires about products, but does not buy. Information about such customer behavior may be very important to an organization. This type of event would, however, not be captured by an event-based system such as the one above. As we will see, REA is an event-based (or sometimes called a pattern-based) system. The distinction is more than semantic. REA systems are responsive to both economic and non-economic phenomena. Event-orientation permits the creation of a much richer database that can support the information needs of all users within the organization. 9. Discuss why adherence by accountants to a single, GAAP-based view is inappropriate. ANS: Modern managers need both financial and non-financial information in formats and at levels of aggregation that the traditional GAAP-based accounting systems architecture is generally incapable of providing. Information customers have shown quite clearly that they are willing to obtain the information they require elsewhere. The result has been a growing perception that accountants are not as useful as they once were. 10. Discuss how adopting a value chain perspective reveals advantages of adopting an REA approach to information system development. ANS: Decision-makers need to look at far more than the internal operations and functions of the organization. Value chain analysis distinguishes between primary activities–those that create value–and support activities–those that assist achievement of the primary activities. Through applying the analysis, an organization is able to look beyond itself and maximize its ability to create value by, for example, incorporating the needs of its customers within its products, or the flexibility of its suppliers in scheduling its production. It would be impossible to incorporate much of the value chain activities within a traditional information system. Those organizations that have applied value chain analysis have generally done so outside the accounting information system, providing such information separately to the decision-makers. Frequently, this would involve the establishment of other distinct information systems, such as marketing information systems, with all the resulting problems inherent in operating multiple information systems, including data duplication, data redundancy, and data inconsistency. It is fairly obvious that the adoption of a single information system framework that encompassed all this information, such as one based upon the REA approach, would be preferable. 11. Discuss the relationship between operating events, information events, and decision/management events. ANS: Operating events are the activities that produce goods and services, Information events are the activities that record, maintain, and report information, and Decision/Management events are the activities that lead to decisions being taken. These are linked in a circular fashion: Decision/Management events trigger Operating events. Operating events trigger Information events. Information events trigger Decision/Management events, and so on. In a manual information system, it is fairly easy to distinguish between these three classes of events. Unfortunately, the greater complexity of computerized information systems makes it much less clear where one class ends and another begins. Nevertheless, from the perspective of control and relevance to the item of interest, it is important that they are separately identified when an REA model is being developed. Chapter 11—Enterprise Resource Planning Systems TRUE/FALSE 1. The primary goal of installing an ERP system is reducing system maintenance costs. ANS: F 2. The recommended data architecture for an ERP includes separate operational and data warehouse databases. ANS: T 3. A closed database architecture shares data easily. ANS: F 4. ERP systems support a smooth and seamless flow of information across organizations. ANS: T 5. OLAP stands for on-line application processing. ANS: F 6. The primary goal of installing an ERP system is achieving business process reengineering to improve customer service, reduce production time, increase productivity, and improve decision-making. ANS: T 7. Day-to-day transactions are stored in the operational database. ANS: T 8. Data mining typically focuses on the operational databases. ANS: F 9. Companies are more likely to modify an ERP to accommodate the company than to modify company processes to accommodate the ERP. ANS: F 10. If a chosen ERP cannot handle a specific company process bolt-on software may be available. ANS: T 11. Core applications are also called OLAP. ANS: F 12. The client/server model is a form of network technology in which user computers, called clients, access ERP programs and data via a host computer called a server. ANS: T 13. A data warehouse is a relational or multi-dimensional database that may require hundreds of gigabytes of storage. ANS: T 14. Drill-down capability is an OLAP feature of data mining tools. ANS: T 15. Supply-chain management software is a type of program that supports efforts relative to moving goods from the raw material stage to the customer. ANS: T 16. In two-tier architecture, the database and application functions are separated. ANS: F 17. Slicing and dicing permits the disaggregation of data to reveal underlying details. ANS: F 18. Data entered into the data warehouse must be normalized. ANS: F 19. OLAP includes decision support, modeling, information retrieval, and what-if analysis. ANS: T 20. Efficient supply-chain management provides firms with a competitive advantage. ANS: T 21. The big-bang approach involves converting from old legacy systems to the new ERP in one implementation step. ANS: T 22. In a two-tier architecture approach is used primarily for wide area network (WAN) applications. ANS: F 23. Data cleansing is a step performed by external auditors to identify and repairing invalid data prior to the audit. ANS: F MULTIPLE CHOICE 1. Goals of ERP include all of the following except a. improved customer service b. improvements of legacy systems c. reduced production time d. increased production ANS: B 2. Core applications are a. sales and distribution b. business planning c. shop floor control and logistics d. all of the above ANS: D 3. Data warehousing processes does not include a. modeling data b. condensing data c. extracting data d. transforming data ANS: B 4. Which of the following is usually not part of an ERP’s core applications? a. OLTP applications b. sales and distribution applications c. business planning applications d. OLAP applications ANS: D 5. Which of the following is usually not part of an ERP’s OLAP applications? a. logistics b. decision support systems c. ad hoc analysis d. what-if analysis ANS: A 6. Which of the following statements is least likely to be true about a data warehouse? a. It is constructed for quick searching and ad hoc queries. b. It was an original part of all ERP systems. c. It contains data that are normally extracted periodically from the operating databases. d. It may be deployed by organizations that have not implemented an ERP. ANS: B 7. Which of the following statements is not true? a. In a typical two-tier client server system, the server handles both application and database duties. b. Client computers are responsible for presenting data to the user and passing user input back to the server. c. In three-tier client server architecture, one tier is for user presentations, one is for database and applications, and the third is for Internet access. d. The database and application functions are separate in the three-tier model. ANS: C 8. Which statements about data warehousing is not correct? a. The data warehouse should be separate from the operational system. b. Data cleansing is a process of transforming data into standard form. c. Drill-down is a data-mining tool available to users of OLAP. d. Normalization is an requirement of databases included in a data warehouse. ANS: D 9. Which statement about ERP installation is least accurate? a. For the ERP to be successful, process reengineering must occur. b. ERP fails because some important business process is not supported. c. When a business is diversified, little is gained from ERP installation. d. The phased-in approach is more suited to diversified businesses. ANS: C 10. Which statement is true? a. ERPs are infinitely scalable. b. Performance problems usually stem from technical problems, not business process reengineering. c. The better ERP can handle any problems an organization can have. d. ERP systems can be modified using bolt-on software. ANS: D 11. Auditors of ERP systems a. need not worry about segregation of duties. b. may feel that the data warehouse is too clean and free from errors. c. find independent verification easy. d. need not worry about system access since the ERP determines it. ANS: B 12. Legacy systems are a. old manual systems that are still in place. b. flat file mainframe systems developed before client-server computing became standard. c. stable database systems after debugging. d. advanced systems without a data warehouse. ANS: B 13. A data mart is a. another name for a data warehouse. b. a database that provides data to an organization’s customers. c. an enterprise resource planning system. d. a data warehouse created for a single function or department. ANS: D 14. Most ERPs are based on which network model? a. peer to peer b. client-server c. ring topology d. bus topology ANS: B 15. On-line transaction processing programs a. are bolt-on programs used with commercially available ERSs. b. are available in two models–two-tier and three-tier. c. handle large numbers of relatively simple transactions. d. allow users to analyze complex data relationships. ANS: C 16. Supply chain management software a. is typically under the control of external partners in the chain. b. links all of the partners in the chain, including vendors, carriers, third-party firms, and information systems providers. c. cannot be integrated into an overall ERP. d. none of the above ANS: B 17. The setup of a data warehouse includes a. modeling the data b. extracting data from operational databases c. cleansing the data d. all of the above ANS: D 18. Extracting data for a data warehouse a. cannot be done from flat files. b. should only involve active files. c. requires that the files be out of service. d. follows the cleansing of data. ANS: C 19. Data cleansing involves all of the following except a. filtering out or repairing invalid data b. summarizing data for ease of extraction c. transforming data into standard business terms d. formatting data from legacy systems ANS: B 20. Separating the data warehouse from the operations databases occurs for all of the following reasons except a. to make the management of the databases more economical b. to increase the efficiency of data mining processes c. to integrate legacy system data into a form that permits entity-wide analysis d. to permit the integration of data from diverse sources ANS: A SHORT ANSWER 1. Define ERP. ANS: Enterprise resource planning systems are multiple module systems designed to integrate the key processes in an organization–order entry, manufacturing, procurement, human resources, etc. 2. Define the term “core applications” and give some examples. ANS: Core applications are those applications that support the day-to-day activities of the business, e.g., sales, distribution, shop floor control, logistics. 3. Define OLAP and give some examples. ANS: On-line analytical processing (OLAP) includes decision support, modeling, information retrieval, ad hoc reporting and analysis, and what-if analysis, e.g., determining sales within each region, determining relationship of sales to certain promotions. 4. What is “bolt-on” software? ANS: Bolt-on software is software produced by third-party vendors which can be added onto an ERP to provide function not built into the ERP. 5. What is SCM software? ANS: Supply-chain management software is designed to manage the activities that get the product to the customer. This software typically handles procurement, production scheduling, order processing, inventory management, etc. 6. What is a data warehouse? ANS: A data warehouse is a relational or multi-dimensional database that serves as a central archive of inactive, completed data from both ERP and legacy systems. It is created to permit extensive access capability, including data mining. 7. What is the “Big-Bang” approach? ANS: The big-bang approach to conversion to an ERP is the approach which converts from old legacy systems to the new in one step that implements the ERP across the entire company. 8. Describe the two-tier client server model. ANS: In a two-tier architecture, the server handles both application and database duties. Some ERP vendors use this approach for local area network (LAN) applications. Client computers are responsible for presenting data to the user and passing user input back to the server. 9. What is the client-server model? ANS: The client-server model is a form of network topology in which the users computer or terminal (the client) accesses the ERPs programs and data via a host computer called the server. While the servers may be centralized, the clients are usually located at multiple locations throughout the enterprise. 10. What is scalability? ANS: System scalability refers to the ability of a system to grow as the organization itself grows. This can involve four factors: size, speed, workload, and transaction cost. 11. What is data mining? ANS: Data mining is the process of selecting, exploring, and modeling large amounts of data to uncover unknown relationships and patterns. 12. Why do ERP systems need bolt-on software? Give an example. ANS: Depending on the unique characteristics of a company, an ERP may not be designed to drive all processes needed, e.g., supply chain management software is a common bolt-on. 13. How can a firm acquire bolt-on software? What are the options? ANS: When a firm needs additional function not provided by the ERP, bolt-on applications may be available. These can often be obtained from third-party vendors with which the ERP provider has a partnership arrangement. The more risky alternative is to seek an independent source. 14. Why does data need to be “cleansed”? ANS: Data cleansing involves filtering out or repairing invalid data prior to its being stored in the data warehouse. It also involves standardizing the format. 15. What are the basic stages of the data warehousing process? ANS: modeling data for the data warehouse, extracting data from the operational databases, cleansing the extracted data, transforming data into the warehouse model, and loading the data into the data warehouse database 16. Describe the three-tier client server model. ANS: The database and application functions are separated in the three-tier model. This architecture is typical of large production ERP systems that use wide area networks (WANs) for connectivity. Satisfying a client requests requires two or more network connections. Initially, the client establishes communications with the application server. The application server then initiates a second connection to the database server. 17. Why must a data warehouse include both detail and summary data? ANS: Many decision makers need similar information and need it regularly. Prepared summary data and standard reports can take the pressure off the data warehouse and speed up the provision of regularly needed information. 18. How does a data warehouse help the external auditor perform the audit? ANS: One of the key procedures performed by the audit team is analytical review or procedures designed to gather evidence relating to assertions made by management in the financial statements. The functions available in searching a data warehouse make the examination of data to determine trends, etc., fairly easy, permitting the auditor to examine large quantities of data easily. 19. What is the closed database architecture? ANS: The closed database architecture is similar in concept to the basic flat-file model. Under this approach a database management system is used to provide minimal technological advantage over flat-file systems. The DBMS is little more than a private but powerful file system. Each function has a private database. 20. What is meant by the OLAP term - consolidation ANS: Consolidation is the aggregation or roll-up of data. For example, sales offices data can be rolled up to districts and districts rolled up to regions. 21. What is meant by the OLAP term - Drill-down? ANS: Drill-down permits the disaggregation of data to reveal the underlying details that explain certain phenomena. For example, the user can drill down from total sales returns for a period to identify the actual products returned and the reasons for their return. 22. What is meant by the OLAP term - Slicing and dicing? ANS: Slicing and dicing enables the user to examine data from different viewpoints. One slice of data might show sales within each region. Another slice might present sales by product across regions. Slicing and dicing is often performed along a time axis to depict trends and patterns. ESSAY 1. How are OLTP and OLAP different? Give examples of their use. ANS: On-line transaction processing (OLTP) involves large numbers of relatively simple day-to-day transactions. For example, this may involve order entry which collects data on customers and detail of sales. On-line analytical processing (OLAP) involves large amounts of data used to analyze relationships, involving aggregate data, that can be analyzed, compared, and dissected. 2. Why does the data warehouse need to be separate from the operational databases? ANS: The conclusion that a data warehouse must be maintained separately from the operational database reflects several issues. The transaction processing system needs a data structure that supports performance. A normalized database aids users be adds complexity that can yield performance inefficiency. Data mining systems need an organization that permits broad queries. The data warehouse permits the integration of data still maintained in legacy systems. And the complexities of modern business can benefit from the ability to analyze data extensively in ways not permitted in traditional databases. 3. If an auditor suspected an “unusual” relationship between a purchasing agent and certain suppliers, how could “drill-down” be used to collect data? ANS: Drill-down capability permits a user to repeatedly extract detailed data at increasing levels of detail. An auditor would be able to examine purchasing transactions to determine any pattern of purchases with the supplier in question that were approved by the purchasing agent and tie such transactions to other characteristics like price variations relative to other vendors at the same time. 4. Why must an organization expect the implementation of an ERP to disrupt operations? ANS: Successful implementation of an ERP requires that many business processes be reengineered. Once done, everything is different. If the organizational culture is not responsive to the changes, many problems can arise. 5. Scalability has several dimensions. What are they? What do they mean for ERP installation? ANS: Most organizations want to grow. When a new system of any type is installed, it should be expected to be able to handle a reasonable amount of growth. ERP systems are no different. Several dimensions of scalability can be considered. If size of the database doubles, access time may double. If system speed is increased, response time should decrease proportionately. If workload is increased, response time can be maintained by increasing hardware capacity accordingly. Transaction costs should not increase as capacity is increased. 6. Distinguish between the two-tier and three-tier client server model. Describe when each would be used? ANS: In a two-tier architecture, the server handles both application and database duties. Some ERP vendors use this approach for local area network (LAN) applications. Client computers are responsible for presenting data to the user and passing user input back to the server. In the three-tier model the database and application functions are separated. This architecture is typical of large production ERP systems that use wide area networks (WANs) for connectivity. Satisfying a client requests requires two or more network connections. Initially, the client establishes communications with the application server. The application server then initiates a second connection to the database server. 7. Data in a data warehouse are in a stable state. Explain how this can hamper data mining analysis? What can an organization do to alleviate this problem? ANS: Typically transaction data are loaded into the warehouse only when the activity on them has been completed–they are stable. Potentially important relationships between entities may, however, be absent from data that are captured in there stable state. For example, information about cancelled sales orders will probably not be reflected among the sales orders that have been shipped and paid for before they are placed in the warehouse. One way to reflect these dynamics is to extract the operations data in “slices of time”. These slices provide snapshots of business activity. 8. This chapter stressed the importance of data normalization when constructing a relational database. Why then is it important to de-normalize data in a data warehouse? ANS: Wherever possible, normalized tables pertaining to selected events should be consolidated into de-normalized tables. Because of the vast size of a data warehouse, inefficiency caused by joining normalized data can be very detrimental to the performance of the system. A three-way join between tables in a large data warehouse may take an unacceptably long time to complete and may be unnecessary. Since historical data are static in nature, nothing is gained by constructing normalized tables with dynamic links. 9. ERP implementations are at risk to extensive cost overuns. Discuss three of the more commonly experienced problems area. ANS: Training. Training costs are invariably higher than estimated because management focuses primarily on the cost of teaching employees the new software. This is only part of the needed training. Employees also need to learn new procedures, which is often overlooked during the budgeting process. System Testing and Integration. In theory, ERP is a holistic model in which one system drives the entire organization. The reality, however, is that many organizations use their ERP as a backbone system that is attached to legacy systems and other bolt-on systems, which support unique needs of the firm. Integrating these disparate systems with the ERP may involve writing special conversion programs or even modifying the internal code of the ERP. Integration and testing are done on a case-by-case basis; thus, the cost is extremely difficult to estimate in advance. Database Conversion. A new ERP system usually means a new database. Data conversion is the process of transferring data from the legacy system’s flat files to the ERP’s relational database. When the legacy system’s data are reliable, the conversion process may be accomplished through automated procedures. Even under ideal circumstances, however, a high degree of testing and manual reconciliation is necessary to ensure that the transfer was complete and accurate. More often, the data in the legacy system are not reliable (sometimes called dirty). Empty fields and corrupted data values cause conversion problems that demand human intervention and data rekeying. Also, and more importantly, the structure of the legacy data is likely to be incompatible with the reengineered processes of the new system. Depending on the extent of the process reengineering involved, the entire database may need to be converted through manual data entry procedures. Chapter 12—Electronic Commerce Systems TRUE/FALSE 1. Because of network protocols, users of networks built by different manufacturers are able to communicate and share data. ANS: T 2. Electronic commerce refers only to direct consumer marketing on the Internet. ANS: F 3. Business to consumer is the largest segment of Internet commerce. ANS: F 4. The phrase “.com” has become an Internet buzz word. It refers to a top-level domain name for communications organizations. ANS: F 5. The standard format for an e-mail address is DOMAIN NAME@USER NAME. ANS: F 6. The network paradox is that networks exist to provide user access to shared resources while one of its most important objectives is to control access. ANS: T 7. Business risk is the possibility of loss or injury that can reduce or eliminate an organization’s ability to achieve its objectives. ANS: T 8. IP spoofing is a form of masquerading to gain unauthorized access to a Web server. ANS: T 9. The rules that make it possible for users of networks to communicate are called protocols. ANS: T 10. A factor that contributes to computer crime is the reluctance of many organizations to prosecute criminals for fear of negative publicity. ANS: T 11. Cookies are files created by user computers and stored on Web servers. ANS: F 12. Sniffing is the unauthorized transmitting of information across an Intranet. ANS: F APPENDIX QUESTION 13. The client-server model can only be applied to ring and star topologies. ANS: F 14. The most popular topology for local area networks is the bus topology. ANS: T 15. A network topology is the physical arrangement of the components of the network. ANS: T 16. A bus topology is less costly to install than a ring topology. ANS: T 17. In a hierarchical topology, network nodes communicate with each other via a central host computer. ANS: T 18. Polling is one technique used to control data collisions. ANS: T 19. The most frequent use of EDI is in making vendor payments. ANS: F 20. EDI is the inter-company exchange of computer processible business information in standard format. ANS: T MULTIPLE CHOICE APPENDIX QUESTION 1. The primary difference between a LAN and a WAN is a. the geographical area covered by the network b. the transmission technology used c. the type of workstation used d. the size of the company ANS: A 2. To physically connect a workstation to a LAN requires a a. file server b. network interface card c. multiplexer d. bridge ANS: B 3. One advantage of network technology is a. bridges and gateways connect one workstation with another workstation b. the network interface card permits different networks to share data c. file servers permit software and data to be shared with other network users d. a universal topology facilitates the transfer of data among networks ANS: C 4. Which topology has a large central computer with direct connections to a periphery of smaller computers? Also in this topology, the central computer manages and controls data communications among the network nodes. a. star topology b. bus topology c. ring topology d. client/server topology ANS: A 5. In a star topology, when the central site fails a. individual workstations can communicate with each other b. individual workstations can function locally but cannot communicate with other workstations c. individual workstations cannot function locally and cannot communicate with other workstations d. the functions of the central site are taken over by a designated workstation ANS: B 6. Which of the following statements is correct? The client-server model a. is best suited to the token-ring topology because the random-access method used by this model detects data collisions. b. distributes both data and processing tasks to the server’s node. c. is most effective used with a bus topology. d. is more efficient than the bus or ring topologies. ANS: B 7. What do you call a system of computers that connects the internal users of an organization that is distributed over a wide geographic area? a. LAN b. decentralized network c. multidrop network d. Intranet ANS: D 8. Sniffer software is a. software used by malicious Web sites to sniff data from cookies stored on the user’s hard drive b. used by network administrators to analyze network traffic c. used by bus topology Intranets to sniff for a carrier before transmitting a message to avoid data collisions d. illegal programs downloaded from the Net to sniff passwords from the encrypted data of Internet customers ANS: B 9. In a ring topology a. all nodes are of equal status b. nodes manage private programs and databases locally c. shared resources are managed by a file server which is a node on the ring d. all of the above ANS: D 10. The client/server technology a. increases the amount of data that is transmitted between the central file and the network node b. eliminates the need for nodes to communicate with each other c. reduces the number of records that must be locked by having the file server perform record searches d. functions only with a ring and bus topology ANS: C 11. A star topology is appropriate a. for a wide area network with a mainframe for a central computer b. for centralized databases only c. for environments where network nodes routinely communicate with each other d. when the central database does not have to be concurrent with the nodes ANS: A 12. In a ring topology a. the network consists of a central computer which manages all communications between nodes b. has a host computer connected to several levels of subordinate computers c. all nodes are of equal status; responsibility for managing communications is distributed among the nodes d. information processing units rarely communicate with each other ANS: C 13. Which method does not manage or control data collisions that might occur on a network? a. multiplexing b. polling c. carrier sensing d. token passing ANS: A 14. Network protocols fulfill all of the following objectives except a. facilitate physical connection between network devices b. provide a basis for error checking and measuring network performance c. promote compatibility among network devices d. result in inflexible standards ANS: D 15. All of the following are true about the Open System Interface (OSI) protocol except a. within one node different layers communicate with other layers at that node b. one protocol is developed and applied to all the OSI layers c. specific layers are dedicated to hardware tasks and other layers are dedicated to software tasks d. layers at each node communicate logically with their counterpart layers across nodes ANS: B 16. Which of the following statements is correct? TCP/IP a. is the basic protocol that permits communication between Internet sites. b. controls Web browsers that access the WWW. c. is the file format used to produce Web pages. d. is a low-level encryption scheme used to secure transmissions in HTTP format. ANS: A 17. XBRL a. is the basic protocol that permits communication between Internet sites. b. controls Web browsers that access the Web. c. is the document format used to produce Web pages. d. was designed to provide the financial community with a standardized method for preparing e. is a low-level encryption scheme used to secure transmissions in higher-level (HTTP) format. ANS: D 18. FTP a. is the document format used to produce Web pages. b. controls Web browsers that access the Web. c. is used to connect to Usenet groups on the Internet d. is used to transfer text files, programs, spreadsheets, and databases across the Internet. e. is a low-level encryption scheme used to secure transmissions in higher-level () format. ANS: D 19. HTML a. is the document format used to produce Web pages. b. controls Web browsers that access the Web. c. is used to connect to Usenet groups on the Internet. d. is used to transfer text files, programs, spreadsheets, and databases across the Internet. e. is a low-level encryption scheme used to secure transmissions in higher-level () format. ANS: A 20. Which one of the following statements is correct? a. Cookies always contain encrypted data. b. Cookies are text files and never contain encrypted data. c. Cookies contain the URLs of sites visited by the user. d. Web browsers cannot function without cookies. ANS: C 21. A message that is made to look as though it is coming from a trusted source but is not is called a. a denial of service attack b. digital signature forging c. Internet protocol spoofing d. URL masquerading ANS: C 22. A digital signature is a. the encrypted mathematical value of the message sender’s name b. derived from the digest of a document that has been encrypted with the sender’s private key c. the computed digest of the sender’s digital certificate d. allows digital messages to be sent over analog telephone lines ANS: B 23. HTTP a. is the document format used to produce Web pages. b. controls Web browsers that access the Web. c. is used to connect to Usenet groups on the Internet d. is used to transfer text files, programs, spreadsheets, and databases across the Internet. e. is a low-level encryption scheme used to secure transmissions in higher-level () format. ANS: B 24. Which of the following statements is correct? a. Packet switching combines the messages of multiple users into a “packet” for transmission. At the receiving end, the packet is disassembled into the individual messages and distributed to the intended users. b. The decision to partition a database assumes that no identifiable primary user exists in the organization. c. Message switching is used to establish temporary connections between network devices for the duration of a communication session. d. A deadlock is a temporary phenomenon that disrupts transaction processing. It will resolve itself when the primary computer completes processing its transaction and releases the data needed by other users. ANS: C 25. NNTP a. is the document format used to produce Web pages. b. controls Web browsers that access the Web. c. is used to connect to Usenet groups on the Internet d. is used to transfer text files, programs, spreadsheets, and databases across the Internet. e. is a low-level encryption scheme used to secure transmissions in higher-level (HTTP) format. ANS: C SHORT ANSWER 1. What is packet switching? ANS: Packet switching is a transmission whereby messages are divided into small packets. Individual packets of the same message may take different routes to their destinations. Each packet contains address and sequencing codes so they can be reassembled into the original complete message at the receiving end. 2. What is an extranet? ANS: An extranet is a variant on Internet technology. This is a password-controlled network for private users rather than the general public. Extranets are used to provide access between trading partner internal databases. 3. What is a URL? ANS: A URL is the address that defines the path to a facility or file on the Web. URLs are typed into the browser to access Web site homepages and individual Web pages, and can be embedded in Web pages to provide hypertext links to other pages. 4. What is an IP address? ANS: Every computer node and host attached to the Internet must have a unique Internet protocol (IP) address. For a message to be sent, the IP addresses of both the sending and the recipient nodes must be provided. 5. What is spoofing? ANS: Spoofing is a form of masquerading to gain unauthorized access to a Web server to perpetrate an unlawful act without revealing ones identity. 6. Name the three types of addresses used on the Internet. ANS: The three types of addresses used on the Internet are: e-mail addresses of individuals, Web site (URL) addresses of pages, and IP addresses of individual computers attached to the Internet. 7. What is XML? ANS: XML is a meta-language for describing markup languages. The term extensible means, that any markup language can be created using XML. This includes the creation of markup languages capable of storing data in relational form, where tags (formatting commands) are mapped to data values. 8. What is XBRL? ANS: XBRL (Extensible Business Reporting Language) is an XML-based language that was designed to provide the financial community with a standardized method for preparing, publishing and automatically exchanging financial information, including financial statements of publicly held companies. 9. What is XBRL Taxonomy? ANS: XBRL taxonomies are classification schemes that are compliant with the XBRL specifications, to accomplish a specific information exchange or reporting objectives. 10. Explain the parts of an e-mail address and give an example (your own?). ANS: The two parts of an e-mail address are the user name and the domain name. For example, hsavage@cc.ysu.edu is the address of Helen Savage at the computer center site at Youngstown State University. 11. Explain a denial of service attack. ANS: A denial of service attack is an assault on a Web server to prevent it from serving its users. The normal connecting on the Internet involves a three-way handshake: (1) from the originating server to the receiving server, (2) from the receiving server to the originating, and (3) from the originating server to the receiving. In a denial of service attack, step three is omitted by the attacking entity, and this locks up the receiving server and prevents either completing the connection or using their ports to respond to other inquiries. This is somewhat like a calling party on a phone being able to prevent the called party from breaking the connection, hence making the phone unusable. 12. What are cookies and why are they used? ANS: Cookies are files containing user information that are created by the Web server of the site being visited and are then stored on the visitor’s own computer hard drive. They can contain the addresses of sites visited by the user. If the site is revisited, the browser sends the cookie(s) to the Web server. This was originally intended to enhance efficiency. Many questions now exist about the use of cookies, especially with regard to user privacy and the security of user information such as passwords. 13. List at least five top-level domain names used in the United States. ANS: Among the top-level domain names used in the U.S. are: .com–a commercial entity .net–a network provider .org–an non-profit organization .edu–an educational or research entity .gov–a government entity APPENDIX QUESTION 14. When are networks connected with a bridge and with a gateway? ANS: Bridges connect LANs of the same type; gateways connect LANs of different manufacturers and different types. 15. Describe an advantage to the client/server topology. ANS: Client/server technology reduces the number of records that have to be locked and reduces the amount of data that is transmitted over the network. 16. Describe one primary advantage of polling as a network control method. ANS: Polling is noncontentious so data collisions are prevented. Firms can prioritize data communications by polling important nodes more frequently than less important nodes. 17. Describe one disadvantage to carrier sensing as a network control method. ANS: Collisions can occur when two messages are sent simultaneously. 18. Why is network control needed? What tasks are performed? ANS: Network control establishes a communication session between sender and receiver, manages the flow of data across the network, detects and resolves data collisions, and detects errors in data caused by line failure or signal degeneration. 19. Define WAN, LAN, and VAN. ANS: A WAN is a wide area network, a LAN is a local area network, and a VAN is a value-added network. 20. What are the five basic network architectures? ANS: The five basic network architectures are: star, hierarchical, ring, bus, and client/server. ESSAY APPENDIX QUESTION 1. Contrast a LAN and a WAN. Typically, who owns and maintains a WAN? ANS: A LAN is a local area network covering a limited geographic area (a room, a building, several buildings within a restricted geographic distance). Information processing units connected to a LAN are usually microcomputer-based workstations. Typically, LANs are privately owned and controlled. 2. Describe the basic differences between the star, ring, and bus topologies. ANS: The star topology is a configuration of IPUs with a large central computer (the host) at the hub (or center) that has connections to a number of smaller computers. Communication between nodes is managed from the host. The ring topology connects many computers of equal status. There is no host. Management of communication is distributed among the nodes. In the bus topology, all nodes are connected to a common cable, the bus. Communication and file transfer are controlled centrally by one or more server. 3. What security questions must be considered with regard to Internet commerce? ANS: Security questions that must be answered to safeguard Internet commerce relate to: private or confidential financial data stored on a host or server that could be accessed by unauthorized individuals, interception of private information sent between sites, such as credit card numbers, and the risk of destruction of data and programs by virus attacks and other malice. 4. What is the World Wide Web? ANS: The World Wide Web is an Internet facility that links user sites locally and around the world. It was originally developed to share scientific information over the Internet. Although the Web is the part of the Internet that is most familiar to average users, it is just a part. Other Internet tools include file transfer using FTP, remote connection to another computer using Telnet, and access to the menuing system Gopher. Its popularity is in part due to the ease of access that is provided by Internet browser software. The basic Web document is written in hypertext markup language that contains numerous links to other pages, thus permitting easy movement. 5. Discuss the three levels of Internet business models. ANS: How much benefit an organization gains from the Internet depends on how much of its function is used. Three levels of uses can be made: a. At the simplest level, the information level, the organization uses the Internet to display information about the company, its products, services, and business policies. In other words, it provides information only. b. At the transaction level, the organization uses the Internet to accept orders from customers and/or to place them with their suppliers. In other words, transactions occur. c. At the highest level, the distribution level, the organization uses the Internet to both sell and deliver digital products–online news, software, music, video, etc. 6. Define risk in an electronic commerce setting. ANS: The typical definition of business risk is the possibility of loss or injury that can reduce or eliminate an organization’s ability to achieve its objectives. In the area of e-commerce, risk relates to the loss, theft, or destruction of data and/or the use or generation of data or computer programs that financially or physically harm an organization. 7. Discuss the four areas of concern as they are related to e-commerce: data security, business policy, privacy, and business process integrity. ANS: Data security relates to the level of protection over stored and transmitted data–the security of internal databases and protection from unauthorized access by individuals inside and outside the organizations. Business policies relate to the need of consumers and trading partners to know a company’s policies regarding billing, payment, merchandise returns, shipping, products, and sales tax collection. Privacy refers to the level of confidentiality used by an organization in managing customer and trading partner data. Business process integrity relates to the accuracy, completeness, and consistency with which an organization processes its business transactions. 8. Define and contrast digital certificate and digital signature. ANS: A digital certificate is like an electronic identification card that is used in conjunction with a public key encryption system to verify the authenticity of the message sender. These are issued by certification authorities. A digital signature is an electronic authentication technique that ensures that the transmitted message originated with the authorized sender and that it was not tampered with after the signature was applied. 9. Explain the function of the two parts of the TCP/IP protocol. ANS: The two parts of the TCP/IP protocol are the transfer control protocol (TCP) and the Internet protocol (IP). This controls how the individual packets of data are formatted, transmitted, and received. The TCP supports the transport function of the OSI (Open System Interface) model that has been adopted by the International Standards Organization for the communication community. This ensures that the full message is received. The IP component provides the routing mechanism. It contains a network address and is used to route messages to their destinations. 10. What are network protocols? What functions do they perform? ANS: Network protocols are the rules and standards governing the design of hardware and software that permit users of networks manufactured by different vendors to communicate and share data. Protocols perform a number of different functions. a. They facilitate the physical connection between network devices. b. They synchronize the transfer of data between physical devices. c. They provide a basis for error checking and measuring network performance. d. They promote compatibility among network devices. e. They promote network designs that are flexible, expandable, and cost-effective. 11. List and briefly define the privacy conditions inherent to the Safe Harbor agreement ANS: Notice: Organizations must provide individuals with clear notice of, “the purposes for which it collects and uses information about them, the types of third parties to which it discloses the information, and how to contact the company with inquiries or complaints.” Choice: Before any data is collected, an organization must give its customers the opportunity to choose whether to share their sensitive information (e.g., data related to factors such as health, race, or religion). Onward Transfer: Unless they have the individual’s permission to do otherwise, organizations may share information only with those third parties that belong to the Safe Harbor Agreement or follow its principles. Security and Data Integrity: Organizations need to ensure that the data they maintain is accurate, complete, and current, and thus reliable, for use. They must also ensure the security of the information by protecting it against loss, misuse, unauthorized access, disclosure, alteration, and destruction. Access: Unless they would be unduly burdened or violate the rights of others, organizations must give individuals “access to personal data about themselves and provide an opportunity to correct, amend, or delete such data.” Enforcement: Organizations must “enforce compliance, provide recourse for individuals who believe their privacy rights have been violated, and impose sanctions on their employees and agents for non-compliance.” 12. Discuss three audit implications of XBRL ANS: Audit implications include: Taxonomy Creation. Taxonomy may be generated incorrectly, resulting in an incorrect mapping between data and taxonomy elements that could result in material misrepresentation of financial data. Controls must be designed and in place to ensure the correct generation of XBRL taxonomies. Validation of Instance Documents. As noted, once the mapping is complete and tags have been stored in the internal database, XBRL instance documents (reports) can be generated. Independent verification procedures need to be established to validate the instance documents to ensure that appropriate taxonomy and tags have been applied before posting to web server. Audit Scope and Timeframe. Currently, auditors are responsible for printed financial statements and other materials associated with the statements. What will be the impact on the scope of auditor responsibility as a consequence of real time distribution of financial statements across the Internet? Should auditors also be responsible for the accuracy of other related data that accompany XBRL financial statements, such as textual reports? 13. What is a Certification Authority and what are the implications for the accounting profession? ANS: A certification authority is independent and trusted third party empowered with responsibility to vouch for the identity of organizations and individuals engaging in Internet commerce. The question then becomes who vouches for the CA? How does one know that the CA who awarded a seal of authenticity to an individual is itself reputable and was meticulous in establishing his or her identity? These questions hold specific implication for the accounting profession. Since they enjoy a high degree of public confidence, public accounting firms are natural candidates for certification authorities. Chapter 13—Managing the Systems Development Life Cycle TRUE/FALSE 1. The majority of the cost of a system is incurred in the new systems development phase of the life cycle. ANS: F 2. According to the text, a stakeholder is an end user of a system. ANS: F 3. The objective of systems planning is to link systems projects to the strategic objectives of the firm. ANS: T 4. The Systems Development Life Cycle (SDLC) concept applies to specific applications and not to strategic systems planning. ANS: F 5. An accountant’s responsibility in the SDLC is to ensure that the system applies proper accounting conventions and rules and possesses adequate control. ANS: T 6. In the conceptual design phase of the Systems Development Life Cycle (SDLC), task force members are focused on selecting the new system design. ANS: F 7. When determining the operational feasibility of a new system, the expected ease of transition from the old system to the new system should be considered. ANS: T 8. One-time costs include operating and maintenance costs. ANS: F 9. When preparing a cost-benefit analysis, design costs incurred in the systems planning, systems analysis and conceptual design phases of the Systems Development Life Cycle are relevant costs. ANS: F 10. A tangible benefit can be measured and expressed in financial terms. ANS: T 11. Instead of implementing an application in a single “big-bang” release, modern systems are delivered in parts continuously and quickly ANS: T 12. When the nature of the project and the needs of the user permit, most organizations will seek a pre-coded commercial software package rather than develop a systems in-house. ANS: T 13. All of the steps in the Systems Development Life Cycle apply to software that is developed in-house and to commercial software. ANS: F 14. Mixing technologies from many vendors improves technical feasibility. ANS: F 15. The first step in the SDLC is to develop a systems strategy ANS: T 16. System maintenance is often viewed as the first phase of a new development cycle. ANS: T 17. Project initiation is the process by which systems proposals are assessed for consistency with the strategic systems plan and evaluated in terms of their feasibility and cost-benefit characteristics. ANS: T 18. When the nature of the project and the needs of the user permit, most organizations will create the system in-house rather than rely on a commercial package. ANS: F 19. Existing (maintained) applications are the prototypes for their new versions. ANS: T 20. Because of the robustness of modern technology, businesses today see infrequent changes in their IT systems and much longer system life spans. ANS: F MULTIPLE CHOICE 1. When studying the detailed feasibility of a new project a. prototyping does not affect the schedule feasibility analysis b. the need for user training will influence the schedule feasibility analysis c. protection from fraud and errors will influence the schedule feasibility analysis d. a cost-benefit review will affect the schedule feasibility analysis ANS: B 2. Protection from inadvertent disclosures of confidential information is part of the detailed a. operational feasibility study b. schedule feasibility study c. legal feasibility study d. economic feasibility study ANS: C 3. A cost-benefit analysis is a part of the detailed a. operational feasibility study b. schedule feasibility study c. legal feasibility study d. economic feasibility study ANS: D 4. Examples of one-time costs include all of the following except a. hardware acquisition b. insurance c. site preparation d. programming ANS: B 5. Examples of recurring costs include a. software acquisition b. data conversion c. personnel costs d. systems design ANS: C 6. Site preparation costs include all of the following except a. crane used to install equipment b. freight charges c. supplies d. reinforcement of the building floor ANS: C 7. The testing of individual program modules is a part of a. software acquisition costs b. systems design costs c. data conversion costs d. programming costs ANS: D 8. When implementing a new system, the costs associated with transferring data from one storage medium to another is an example of a. a recurring cost b. a data conversion cost c. a systems design cost d. a programming cost ANS: B 9. An example of a tangible benefit is a. increased customer satisfaction b. more current information c. reduced inventories d. faster response to competitor actions ANS: C 10. An example of an intangible benefit is a. expansion into other markets b. reduction in supplies and overhead c. more efficient operations d. reduced equipment maintenance ANS: C 11. A tangible benefit a. can be measured and expressed in financial terms b. might increase revenues c. might decrease costs d. all of the above ANS: D 12. Intangible benefits a. are easily measured b. are of relatively little importance in making information system decisions c. are sometimes estimated using customer satisfaction surveys d. when measured, do not lend themselves to manipulation ANS: C 13. Which technique is least likely to be used to quantify intangible benefits? a. opinion surveys b. simulation models c. professional judgment d. review of accounting transaction data ANS: D 14. The formal product of the systems evaluation and selection phase of the Systems Development Life Cycle is a. the report of systems analysis b. the systems selection report c. the detailed system design d. the systems plan ANS: B 15. One time costs include all of the following except a. site preparation b. insurance c. programming and testing d. data conversion ANS: B 16. Recurring costs include all of the following except a. data conversion b. software maintenance c. insurance d. supplies ANS: A 17. All of the following are reasons why new systems fail except a. the user is not involved in the development of the system b. system requirements are not clearly specified c. systems analysts rely on prototyping models d. system development techniques are ineffective ANS: C 18. The systems steering committee is responsible for all of the following except a. assigning priorities b. determining whether and when to terminate systems projects c. analyzing the technical feasibility of the project d. budgeting funds for systems development ANS: C 19. Strategic systems planning is important because the plan a. provides authorization control for the Systems Development Life Cycle b. will eliminate any crisis component in systems development c. provides a static goal to be attained within a five-year period d. all of the above ANS: A 20. Project feasibility includes all of the following except a. technical feasibility b. conceptual feasibility c. operational feasibility d. schedule feasibility ANS: B 21. The degree of compatibility between the firm’s existing procedures and personnel skills and the requirements of the new system is called a. technical feasibility b. operational feasibility c. schedule feasibility d. legal feasibility ANS: B 22. The ability of a system to protect individual privacy and confidentiality is an example of a. schedule feasibility b. operational feasibility c. legal feasibility d. economic feasibility ANS: C 23. The systems project proposal a. provides management with a basis for deciding whether or not to proceed with the project b. supplies an input to the project planning activity c. links the objectives of the proposed system to the system’s scheduling requirements d. prioritizes the proposal in relation to other system proposals ANS: A 24. Which step is not used to evaluate a systems proposal? An analysis of the project’s a. feasibility factors b. ability to eliminate nonessential activities and costs c. ability to provide a competitive advantage to the firm d. use of Computer Aided Software Engineering (CASE) tools in developing the system proposal ANS: D 25. Reasons that a new systems implementation may be unsuccessful include all of the following except a. organizational restructuring required by the new system results in displaced workers b. end users do not understand the strategic merits of the new system c. employees are not trained to use the system d. system development team members include representatives from end-user departments ANS: D 26. Typically a systems analysis a. results in a formal project schedule b. does not include a review of the current system c. identifies user needs and specifies system requirements d. is performed by the internal auditor ANS: C 27. A disadvantage of surveying the current system is a. it constrains the generation of ideas about the new system b. it highlights elements of the current system that are worth preserving c. it pinpoints the causes of the current problems d. all of the above are advantages of surveying the current system ANS: A 28. Systems analysis involves all of the following except a. gathering facts b. surveying the current system c. redesigning bottleneck activities d. reviewing key documents ANS: C 29. The systems analysis report does not a. identify user needs b. specify requirements for the new system c. formally state the goals and objectives of the system d. specify the system processing methods ANS: D 30. After the systems analysis phase of the System Development Life Cycle (SDLC) is complete, the company will have a formal systems analysis report on a. the conceptual design of the new system b. an evaluation of the new system c. users’ needs and requirements for the new system d. a comparison of alternative implementation procedures for the new system ANS: C 31. The accountant’s role in systems analysis includes all of the following except a. specify audit trail requirements b. prepare data gathering questionnaires c. suggest inclusion of advanced audit features d. ensure mandated procedures are part of the design ANS: B 32. The role of the steering committee includes a. designing the system outputs b. resolving conflicts that arise from a new system c. selecting the programming techniques to be used d. approving the accounting procedures to be implemented ANS: B 33. Project planning includes all of the following except a. specifying system objectives b. preparing a formal project proposal c. selecting hardware vendors d. producing a project schedule ANS: C 34. Aspects of project feasibility include all of the following except a. technical feasibility b. economic feasibility c. logistic feasibility d. schedule feasibility ANS: C 35. Which of the following is not a tool of systems analysts? a. observation b. task participation c. audit reports d. personal interviews ANS: C 36. When developing the conceptual design of a system, a. all similarities and differences between competing systems are highlighted b. structure diagrams are commonly used c. the format for input screens and source documents is decided d. inputs, processes, and outputs that distinguish one alternative from another are identified ANS: D 37. The role of the accountant/internal auditor in the conceptual design phase of the Systems Development Life Cycle includes all of the following except a. the accountant is responsible for designing the physical system b. the accountant is responsible to ensure that audit trails are preserved c. the internal auditor is responsible to confirm that embedded audit modules are included in the conceptual design d. the accountant is responsible to make sure that the accounting conventions that apply to the module are considered by the system designers ANS: A SHORT ANSWER 1. Why is it important that the systems professionals who design a project not perform the detailed feasibility study of the project? ANS: Objectivity is essential to the fair assessment of each project design. To ensure objectivity, an independent systems professional should perform the study. 2. List at least three one-time costs and three recurring costs in system development. ANS: One time costs include: hardware acquisition, site preparation, software acquisition, system design, programming and testing, data conversion, training. Recurring costs include: hardware maintenance, software maintenance, insurance, supplies, personnel costs. 3. ____________________ benefits can be measured and expressed in financial terms, while ____________________ benefits cannot be easily measured and/or quantified. ANS: Tangible, intangible 4. What is a systems selection report? ANS: A systems selection report is a formal document that consists of a revised feasibility study, a cost-benefit analysis, and a list and explanation of intangible benefits for each alternative design. The steering committee uses this report to select a system. 5. Why is the payback method often more useful than the net present value method for evaluating systems projects? ANS: Because of brief product life cycles and rapid advances in technology, the effective lives of information system tends to be short. Shorter payback projects are often desirable. 6. Contrast reactive and proactive management styles. ANS: Reactive management responds to problems only when they reach a crisis state and can no longer be ignored. In this situation, problem resolution is generally suboptimal. Proactive management is alert for early signs of problems and actively looks for ways to improve the organization’s systems. This allows adequate time for planning and implementing solutions. 7. Explain why accountants are interested in the legal feasibility of a new systems project. ANS: Legal feasibility identifies conflicts between the proposed system and the company’s ability to discharge its legal responsibilities. Accountants are often tasked with the legal requirements associated with developing the internal control system and securing information from inappropriate disclosure. 8. Explain an advantage of surveying the current system when preparing a systems analysis for a new systems project. ANS: An analysis of the current system: will identify what aspects of the current system should be retained will facilitate the conversion from the old to the new system may uncover causes of reported problems 9. What are two purposes of the systems project proposal? ANS: First, it summarizes the findings of the study conducted to this point into a general recommendation for a new or modified system. This enables management to evaluate the perceived problem along with the proposed system as a feasible solution. Second, the proposal outlines the linkage between the objectives of the proposed system and the business objectives of the firm. It shows that the proposed new system complements the strategic direction of the firm. 10. List two ways that a systems project can contribute to the strategic objectives of the firm. ANS: A new system can improve the operational performance by eliminating nonessential activities and costs, provide a method of differentiating the product or service from the competitors, and provide information that will help improve management decision-making. 11. List four types of facts that should be gathered during an analysis of a system. ANS: data sources; information users; data stores; processes; data flows; controls; transaction volumes; error rates; resource costs; bottlenecks; and redundant operations 12. What is the Internal Business Process Perspective? ANS: Metrics based on this perspective allow the manager to know how well their business is running, and whether its products and services conform to customer requirements. 13. What is the Learning and Growth Perspective? ANS: Learning and growth constitute the essential foundation for success of any organization. This perspective includes employee training and corporate cultural attitudes related to both individual and corporate self-improvement 14. When a company is doing financially well, why is the Customer Perspective measure important? ANS: These are leading indicators: if customers are not satisfied, they will eventually find other suppliers that will meet their needs. Poor performance from this perspective predicts of future decline, even though the current financial picture may look good. The Customer Perspective includes objective measurements such as customer retention rate, as well as more subjective criteria such as market research and customer satisfaction surveys. 15. Distinguish between escapable and inescapable costs. Give an example. ANS: Escapable costs are directly related to the system, and they cease to exist when the system ceases to exist. An example would be an annual software support fee for purchased software. If the system ceases to exist, the support for the software will no longer be necessary. Inescapable costs, on the other hand, represent costs which will not be eliminated if the system is scrapped. An example would be an overhead charge for office space in a building which is owned by the company. If the system ceases to exist, these costs will be allocated to the remaining departments. 16. Why is cost-benefit analysis more difficult for information systems than for many other types of investments organizations make? ANS: The benefits of information systems are oftentimes very difficult to assess. Many times the benefits are intangible, such as improved decision making capabilities. Also, maintenance costs may be difficult to predict. Most other investments that organizations make, i.e. purchase of a new piece of equipment, tend to have more tangible and estimable costs and benefits. 17. What does assessing user feedback involve? ANS: 1. recognizing the problem 2. defining the problem 3. specifying system objectives 4. determining project feasibility 5. preparing a formal project proposal ESSAY 1. Explain the five stages of the systems development life cycle? ANS: Systems Strategy. The first step in the SDLC is to develop a systems strategy, which requires an understanding the strategic business needs of the organization. This may be derived from the organization’s mission statement, an analysis of competitive pressures on the firm, and the nature of current and anticipated market conditions. These needs reflect the organizations current position relative to where it needs to be long term to maintain strategic advantage. Project Initiation. Project initiation is the process by which systems proposals are assessed for consistency with the strategic systems plan and evaluated in terms of their feasibility and cost-benefit characteristics. Alternative conceptual designs are considered and those selected enter the construct phase of the SDLC. In-House Development. As mentioned earlier, some organizations have such unique information needs that they can only be adequately met through internal development. The in-house development step includes analyzing user needs, designing processes and databases, creating user views, programming the applications, and testing and implementing the completed system. Commercial Packages. When the nature of the project and the needs of the user permit, most organizations will seek a pre-coded commercial software package rather than develop a new system from scratch. Maintenance and Support. Maintenance involves both acquiring and implementing the latest software versions of commercial packages and making in-house modifications to existing systems to accommodate changing user needs. Maintenance may be relatively trivial, such as modifying an application to produce a new report or more extensive, such as programming new functionality into a system. Another aspect of maintenance includes a establishing a user support infrastructure. This could include help desk services, providing user training and education classes, and documenting user feedback pertaining to problems and system errors. 2. What is the balanced scorecard? ANS: The balanced scorecard (BSC) is a management system that enables organizations to clarify their vision and strategy and translate them into action. It provides feedback both from internal business processes and external outcomes to continuously improve strategic performance. When fully deployed, the balanced scorecard transforms strategic planning from an academic exercise into operational tasks. 3. Define the feasibility measures that should be considered during project analysis and give an example of each. ANS: Technical feasibility is an assessment as to whether the system can be developed under existing technology or if new technology is needed. An example might be a situation where a firm wants to completely automate the sales process. A question would be-Is technology available that allows sales to be made without humans? Economic feasibility is an assessment as to the availability of funds to complete the project. A question would be-Is it cost feasible to purchase equipment to automate sales? Legal feasibility identifies any conflicts with the proposed system and the company’s ability to discharge its legal responsibilities. An example would be a firm that is proposing a new mail order sales processing system for selling wine. Operational feasibility shows the degree of compatibility between the firm’s existing procedures and personnel skills and the operational requirements of the new system. Do the firm have the right work force to operate the system? If not, can employees be trained? If not, can they be hired? Schedule feasibility pertains to whether the firm can implement the project within an acceptable time frame. An example would be a new ticket sales system for a sports team. The system would need to be implemented prior to the start of the new season. 4. Explain the role of accountants in the conceptual design stage. ANS: Accountants are responsible for the logical information flows in a new system. Alternate systems considered must be properly controlled, audit trails must be preserved, accounting conventions and legal requirements must be met. The auditability of a new system depends in part on its design characteristics. 5. Contrast the feasibility study performed in the systems analysis phase of the Systems Development Life Cycle (SDLC) with the study performed in the systems selection phase of the SDLC. ANS: A preliminary feasibility study for the project as a whole is performed in the systems analysis phase of the SDLC. Five aspects to project feasibility are considered: technical feasibility, economic feasibility, legal feasibility, operational feasibility, and schedule feasibility. The preliminary analysis is based largely on the judgment and intuition of the systems professionals. In the systems selection phase of the SDLC, the same five feasibility factors are considered for the specific system features that have been conceptualized and for each conceptual design alternative. The economic feasibility study in the detailed analysis includes a cost-benefit analysis for each alternative. 6. Explain why the Systems Development Life Cycle is of interest to accountants. What is the accountant’s role in the Systems Development Life Cycle? ANS: The information system requires a significant financial investment. Accountants are concerned that the capital investment involved in acquiring an information system is properly handled. Also, the information system gathers the data used to prepare financial statements. Accountants must be certain that the information system is applying accounting principles properly and that the system itself has adequate internal controls. Any deficiencies in the information system could result in misstated financial statements. Accountants have three roles in the Systems Development Life Cycle. Accountants are users of the information system and as such must be able to communicate their needs to the systems designers. These needs include audit trail requirements, depreciation models, and other accounting techniques. Accountants are members of the SDLC development team and are expected to provide information about the requirements of the system including security needs. Finally, accountants are auditors of the information system and determine what audit features should be designed into the system. 7. What are three problems that account for most system failures? ANS: Most system failures can be traced to three problems: a. poorly specified system requirements, due to communication problems between users and systems professionals, the iterative nature of the process, and the need to rework parts of the system; b. ineffective development techniques for presenting, documenting, and modifying systems specifications; and c. lack of user involvement during critical development stages. 8. What is Industry analysis and why do managers do it. ANS: Industry Analysis provides management with an analysis of the driving forces that affect their industry and their organization’s performance. Such analysis offers a fact-based perspective on the industry’s important trends, significant risks, and potential opportunities that may impact the business’s performance. 9. Why is the announcement of a new systems project so critical to project success? ANS: Change is threatening to many individuals. A new system can be perceived as putting jobs at risk in the name of “efficiency,” as a threat to organizational structure, and as requiring job skills that some users fear they lack. The announcement of a new system must include upper management support and an explanation of the business rationale for the system and the expected benefits for ultimate users. 10. Contrast the preliminary project feasibility study with the feasibility study performed in the systems evaluation and selection phase of the SDLC. ANS: A preliminary feasibility study for the project as a whole is performed in the systems needs analysis phase of the SDLC. Five aspects to project feasibility are considered: technical feasibility, economic feasibility, legal feasibility, operational feasibility, and schedule feasibility. The preliminary analysis is based largely on the judgment and intuition of the systems professionals. In the systems evaluation and selection phase of the SDLC, the same five feasibility factors are considered for the specific system features that have been conceptualized and for each conceptual design alternative. The economic feasibility study includes a cost-benefit analysis for each alternative. 11. Part of systems planning is a project feasibility study. Several feasibility issues can be raised. What are they? Explain the key concerns. ANS: The key feasibility issues include: technical, economic, legal, operational, and schedule. Technical feasibility relates to whether the proposed system can be developed with existing technology or requires new. Economic feasibility relates to cost questions. Legal feasibility relates to the firm’s ability to discharge is legal responsibilities under the proposed system. Operational feasibility concerns the compatibility of the new and old systems, including personnel issues. Schedule feasibility relates to meet target deadlines. 12. Explain the role of accountants in the conceptual design stage. ANS: Accountants are responsible for the logical information flows in a new system. Alternate systems considered must be properly controlled, audit trails must be preserved, accounting conventions and legal requirements must be met. The auditability of a new system depends in part on its design characteristics. 13. Classify each of the following as either a one-time or recurring costs: training personnel initial programming and testing system design-one hardware costs software maintenance costs site preparation rent for facilities data conversion from old system to new system insurance costs installation of original equipment hardware upgrades ANS: training personnel-one-time initial programming and testing-one-time system design-one-time hardware costs-one-time software maintenance costs-recurring site preparation-one-time rent for facilities-recurring data conversion from old system to new system-one-time insurance costs-recurring installation of original equipment-one-time hardware upgrades-recurring 14. What is competency analysis and why do managers do it. ANS: Competency Analysis provides a complete picture of the organization’s effectiveness as seen via four strategic filters: Resources, Infrastructure, Products/Services and Customers. By assessing these factors, an organization can develop an accurate view of its relative strengths, weaknesses and core competencies. The analysis helps in developing strategic options, which are based on an understanding of the future environment and firm’s core competencies. Strategic opportunities may include market entry options or new product development options. Chapter 14—Construct, Deliver, and Maintain Systems Projects TRUE/FALSE 1. The detailed design phase of the Systems Development Life Cycle is a linear process with each of five steps occurring once and in its proper sequence. ANS: F 2. In a Computer Aided Software Engineering (CASE) environment, the most important use of a data flow diagram is to present a graphic display of the system. ANS: F 3. During maintenance of a system developed using Computer Aided Software Engineering (CASE) tools, changes to the system are made directly through the data flow diagram. ANS: T 4. The Computer Aided Software Engineering (CASE) coding model transforms the structure diagram into computer code. ANS: T 5. If system development is conducted properly, most system maintenance costs can be eliminated. ANS: F 6. The context level data flow diagram is a physical input to the lower CASE models that automatically produce program code. ANS: F 7. The design and programming of modern systems follows one of two basic approaches: the structured approach and the object-oriented approach. ANS: T 8. The concept of reusability is central to the structured approach to systems design. ANS: F 9. In the object-oriented approach to systems design, a vendor is an example of an attribute. ANS: F 10. In the object-oriented approach to systems design, an instance is a logical grouping of individual objects which share the same attributes and operations. ANS: F 11. In the object-oriented approach to systems design, when an operation is performed on an object, an attribute will always be changed. ANS: F 12. In the object-oriented approach to systems design, inheritance means that each object instance inherits the attributes and operations of the class to which it belongs. ANS: T 13. In the object-oriented approach to systems design, it is possible for an object class to inherit attributes and operations of another object class. ANS: T 14. The entity relationship diagram is used to represent object-oriented designs. ANS: T 15. Office automation is more complex than accounting packages. ANS: F 16. In-house developed systems are less reliable than commercial software. ANS: T 17. Output of the Management Reporting System may vary considerably among companies. ANS: T 18. Output reporting includes both paper and electronic reports. ANS: T 19. Information as to which databases are required for a new system can be obtained from the entity relationship diagram. ANS: T 20. A point-of-sale terminal is an example of electronic data input from source documents. ANS: F 21. Correctly designed, processing modules are tightly coupled and have strong cohesion. ANS: F 22. A system walkthrough occurs after the system is implemented. ANS: F 23. The detailed design report is the “blueprint” which guides programmers and database administrators in constructing the physical system. ANS: T 24. When a program module is tested, both good and bad data are included with the test transactions. ANS: T 25. Instruction for the filling out of paper input forms should always be printed on a separate instruction sheet. ANS: F 26. Program modules with weak cohesion are more complex and difficult to maintain. ANS: T 27. If individual modules are thoroughly tested, it is not necessary to test the whole system. ANS: F MULTIPLE CHOICE 1. Which statement is not true? a. prototypes do not include internal control features b. a prototype is an inexpensive, simplified model of a system c. a throwaway prototype is discarded after the requirements are established d. systems designers always discard prototypes and do not develop them into finished systems ANS: D 2. Which statement is not true? Computer Aided Software Engineering (CASE) technology a. is commercially available software b. reduces the productivity but increases the quality of the work of systems professionals c. expedites the System Development Life Cycle d. consists of upper and lower tools ANS: B 3. The central repository of the Computer Aided Software Engineering (CASE) system contains a. the program code b. user prototype screens c. data flow diagrams d. all of the above ANS: D 4. Which is not a level of a data flow diagram? a. conceptual level b. context level c. intermediate level d. elementary level ANS: A 5. Which level of a data flow diagram is used to produce program code and database tables? a. context level b. elementary level c. intermediate level d. prototype level ANS: B 6. In a Computer Aided Software Engineering (CASE) environment, a structure diagram a. presents an overview model of the primary transactions processed b. graphically depicts the iceberg effect c. presents a model of the program code that constitutes the physical system d. is prepared by the systems analyst ANS: C 7. An advantage of the Computer Aided Software Engineering (CASE) model tool, which transforms the structure diagram into machine language, is a. it facilitates the auditors review of the system b. it ensures that firm will use a specific CASE tool and vendor c. it forces all system changes to be made through the data flow diagrams d. it reduces the analysis required in designing the system ANS: C 8. When maintaining a system that was developed using Computer Aided Software Engineering (CASE) tools, a. the programmer must thoroughly review the program code b. changes should be made directly to the structure diagram c. significantly less time is required compared to maintenance activities for a system developed without using Computer Aided Software Engineering (CASE) tools d. the need for testing the modified application is eliminated ANS: C 9. Which of the following is an advantage of the Computer Aided Software Engineering (CASE) approach? a. the ability to easily revise the model during the development stage b. the requirement that all program code and documentation be regenerated for each module c. the cost of software engineering programs d. user involvement is restricted to final stages of development ANS: A 10. Which of the following is a disadvantage of the Computer Aided Software Engineering (CASE) approach? a. source code produced by CASE tools is less efficient than code written by a skilled programmer b. alternative designs cannot be reviewed prior to implementation c. system users are reluctant to become involved with the CASE approach d. maintenance costs are increased ANS: A 11. Which statement is not correct? The structured design approach a. is a top-down approach b. is documented by data flow diagrams and structure diagrams c. assembles reusable modules rather than creating systems from scratch d. starts with an abstract description of the system and redefines it to produce a more detailed description of the system ANS: C 12. The benefits of the object-oriented approach to systems design include all of the following except a. this approach does not require input from accountants and auditors b. development time is reduced c. a standard module once tested does not have to be retested until changes are made d. system maintenance activities are simplified ANS: A 13. In the object-oriented systems design approach, the employee pay rate is an example of a. an object b. an attribute c. an operation d. a class ANS: B 14. Ms. Andrews is a customer of the Edsell Company. In the object-oriented design approach a. Ms. Andrews is an instance in the object class accounts receivable b. the amount Ms. Andrews owes the Edsell Company is an operation c. determining the amount past due is an attribute d. the object class accounts receivable inherits all the attributes of Ms. Andrews ANS: A 15. In the object-oriented systems design approach, a. objects possess two characteristics–attributes and instances b. an instance is a logical grouping of individual objects c. inheritance means that each object instance inherits the attributes and operations of the class to which it belongs d. operations performed on objects always change attributes ANS: C 16. Which statement is not correct? In the object-oriented design approach a. a single change to an attribute or operation in one object class is automatically changed for all the object instances and subclasses that inherit the attribute b. each module can inherit from other modules the attributes and operations it requires c. the entity relationship diagram is used to create a program which can be used in other systems d. the control module must be recreated for each program ANS: D 17. Evaluators of the detailed feasibility study should not include a. the internal auditor b. the project manager c. a user representative d. the system designer ANS: D 18. A commercial software system that is completely finished, tested, and ready for implementation is called a a. backbone system b. vendor-supported system c. benchmark system d. turnkey system ANS: D 19. Which of the following is not an advantage of commercial software? Commercial software a. can be installed faster than a custom system b. can be easily modified to the user’s exact specifications c. is significantly less expensive than a system developed in-house d. is less likely to have errors than an equivalent system developed in-house ANS: B 20. Which step is least likely to occur when choosing a commercial software package? a. a detailed review of the source code b. contact with user groups c. preparation of a request for proposal d. comparison of the results of a benchmark problem ANS: A 21. The output of the detailed design phase of the Systems Development Life Cycle (SDLC) is a a. fully documented system report b. systems selection report c. detailed system design report d. systems analysis report ANS: C 22. The detailed design report contains all of the following except a. input screen formats b. alternative conceptual designs c. report layouts d. process logic ANS: B 23. When each element of information supports the user’s decision or task, the output is said to possess a. completeness b. summarization c. conciseness d. relevance ANS: D 24. There is often a conflict between the attributes of a. timeliness and conciseness b. accuracy and timeliness c. relevance and summarization d. completeness and exceptions orientation ANS: B 25. A report of accounts that are past due has many information attributes. The most important attribute is a. summarization b. timeliness c. conciseness d. exception orientation ANS: D 26. When hardcopy forms are used as the source for electronic data input, a. a paper audit trail is maintained b. economies of scale in data collection are avoided c. input errors are reduced d. a point-of-sale terminal is required ANS: A 27. The most important design element for a hardcopy form that is used for electronic data input is that a. the form is a standard size b. the source document and the input screen are identical c. instructions use active voice d. sufficient copies of the form are prepared ANS: B 28. Which is not true of direct data input forms? a. errors caused by transcription are reduced b. calculations are automatically performed on intelligent forms c. many data entry errors are detected and corrected immediately d. workers who use direct data input forms must be highly trained and skilled ANS: D 29. Which statement is not true? a. loosely coupled modules are independent of other modules b. cohesive modules perform a single, well-defined task c. maintenance of a module with weak cohesion is simple d. an error made in a tightly coupled module will affect other modules ANS: C 30. Translating the system modules into pseudocode a. occurs in the implementation phase of the Systems Development Life Cycle b. expresses the detailed logic of the module in programming language c. discourages end users from becoming actively involved in designing the system d. permits individuals with few technical skills to understand the logic of the module ANS: D 31. Which statement is not true? A systems design walkthrough a. is conducted by a quality assurance group b. occurs just after system implementation c. simulates the operation of the system in order to uncover errors and omissions d. reduces costs by reducing the amount of reprogramming ANS: B 32. System documentation is designed for all of the following groups except a. systems designers and programmers b. end users c. accountants d. all of the above require systems documentation ANS: D 33. Which type of documentation shows the detailed relationship of input files, programs, and output files? a. structure diagrams b. overview diagram c. system flowchart d. program flowchart ANS: C 34. Typical contents of a run manual include all of the following except a. run schedule b. logic flowchart c. file requirements d. explanation of error messages ANS: B 35. Computer operators should have access to all of the following types of documentation except a. a list of users who receive output b. a program code listing c. a list of all master files used in the system d. a list of required hardware devices ANS: B 36. Which task is not essential during a data conversion procedure? a. decomposing the system b. validating the database c. reconciliation of new and old databases d. backing up the original files ANS: A 37. When converting to a new system, which cutover method is the most conservative? a. cold turkey cutover b. phased cutover c. parallel operation cutover d. data coupling cutover ANS: C 38. What is not true about data modeling? a. b. c. d. Relationships are the degree of association between two entities. Attributes are data that describe the characteristics or properties of entities. Entities are resources, events, or agents involved in the business. Modeling is the task of formalizing the data requirements of the business process as a physical model. ANS: D SHORT ANSWER 1. Using Computer Aided Software Engineering (CASE) tools, the structure diagram can be transformed into machine code. Describe a disadvantage associated with this procedure. ANS: Auditors need to review program code, and machine code is more difficult to review than source code. Also, this approach usually commits the company to a particular CASE tool and vendor while source code is accepted by most CASE tools. 2. Using Computer Aided Software Engineering (CASE) tools, the structure diagram can be transformed into machine code. Describe an advantage associated with this procedure. ANS: Programmers are forced to make all changes through the data flow diagrams. The CASE tool will then modify the structure diagram and rewrite the machine code automatically. This ensures that the systems documentation always agrees with the computer code. 3. What is prototyping? Why is it used in systems development? ANS: Prototyping is a technique for providing users with a preliminary working version of the new system that users can test. This leads to better understanding of user needs and system requirements. When used in the early stages of the SDLC, prototyping is an effective tool for establishing user requirements. 4. A bottom-up method to design a new system by assembling reusable modules is called __________________________. ANS: object-oriented design 5. Contrast the structured and object-oriented approaches to conceptual systems design. Which is more common? ANS: The structured approach develops each new system from scratch from the top down. Object-oriented design builds systems from the bottom up through the assembly of reusable modules rather than creating each system from scratch. The structured approach dominates modern system design while the object-oriented approach is still an emerging concept. 6. What is meant by “object-oriented design?” What does it mean for systems design? ANS: Object-oriented design refers to a “building block” approach to system design which develops systems from reusable standard components, called objects. This approach avoids starting from scratch for each new system. This saves time and expense for development, maintenance, and testing of systems. An example of an object is inventory. Each object possesses two characteristics: attributes (part number, description, quantity on hand, . . .) and operations (reorder, replace, review quantity, . . . ) 7. List three advantages and one disadvantage of commercial software. ANS: Advantages include very quick implementation time, relatively inexpensive software, and reliable, tested software. Disadvantages include not being able to customize the system and difficulty in modifying the software. 8. What is the purpose of the Request for Proposal (RFP)? ANS: The purpose of the RFP is to obtain proposals on supplying commercial software packages from various vendors. Each prospective vendor is sent an RFP explaining the nature of the problem, the objectives of the system, and the deadline for proposal submission. The RFP includes a format for responses to facilitate a comparison of the proposals from different vendors. 9. Explain how a benchmark problem is used to measure the performance of two different commercial software packages. ANS: Each prospective vendor is given the same data and task to perform (usually important transactions or tasks performed by key components of the proposed system). The results of the benchmark problem are compared for speed, accuracy, and efficiency. 10. Contrast the structured and object-oriented approaches to conceptual systems design. Which is more common? ANS: The structured approach develops each new system from scratch from the top down. Object-oriented design builds systems from the bottom up through the assembly of reusable modules rather than creating each system from scratch. The structured approach dominates modern system design while the object-oriented approach is still an emerging concept. 11. List three characteristics that should be considered when designing a hardcopy input form. ANS: handling, storage, number of copies, form size 12. List two techniques of forms design that encourage efficient and effective data collection. ANS: zones and embedded instructions 13. What is the importance of the base case? ANS: A base case is test data that documents how the system performed at a point in time, and it provides a reference point for analyzing the effects of future system changes. The base case also eases the burden of recreating test data. 14. Describe a risk associated with the phased cutover procedure for data conversion. ANS: Incompatibilities may exist between the new subsystems and the yet-to-be replaced old subsystems. 15. List the attributes of output views. ANS: relevance, summarization, exception orientation, timeliness, accuracy, completeness, conciseness 16. What are embedded instructions? Why do they matter? ANS: Embedded instructions are placed directly on the form in the zone to which they pertain. When contained in the form, they cannot be lost; when in the relevant zone there is less confusion. 17. What are the two methods of electronic input? How do they differ? ANS: The two basic types of electronic input are input from source documents and direct input. The former involves the collection of data on paper that is then transcribed. The latter involves direct capture of data in electronic form. There is no physical record of the input. 18. Describe the Cold Turkey (or Big Bang) approach to system cutover. ANS: Under the cold turkey cutover approach (also called the “Big Bang” approach), the firm switches to the new system and simultaneously terminates the old system. When implementing simple systems, this is often the easiest and least costly approach. With more complex systems, it is the riskiest. 19. Discuss the advantage of the parallel operation cutover approach. ANS: Parallel operation cutover involves running the old system and the new system simultaneously for a period of time. The advantage of parallel cutover is the reduction in risk. By running two systems, the user can reconcile outputs to identify errors and debug errors before running the new system solo. 20. What is the objective of a post-implementation review? ANS: The objective post-implementation review is to measure the success of the system and of the process after the dust has settled. ESSAY 1. Describe at least four advantages and two disadvantages of the Computer Aided Software Engineering (CASE) approach. ANS: Advantages of the CASE approach include: reduced system complexity increased flexibility in making revisions to the system model creation, comparison, and review of alternative system designs quicker development process prototyping promotes user involvement reusable program code and documentation reduced maintenance costs Disadvantages of the CASE approach include: cost of the CASE tools time and cost involved with developing CASE expertise CASE products are incompatible with one another inefficient source code generated by CASE tools encourages skilled programmers to modify the code which results in discrepancies between the data flow diagram and the program code 2. CASE tools develop systems without the intermediate step of writing human readable source code. This can pose some concerns for accountants. What are they? ANS: The absence of human readable source code has implications for accountants, auditors, and management. The first is one of control. Source code has traditionally been part of system documentation. Auditors often design test procedures based on the source code. Without it, testing is hampered. In addition, the absence of source code may tie the firm to the CASE tools and vendor, limiting management’s choice. 3. Discuss the appropriate steps to take when selecting a commercial software package. ANS: When selecting a commercial software package, the first step is to prepare a needs analysis, as detailed as the user’s technical background permits. The second step is to send out a request for proposal, explaining to the vendor the nature of the problem, the objectives of the system, and the deadline for proposal submission. The third step is to identify and capture facts about each vendor’s system. These facts come from vendor presentations (including a technical demonstration), comparing the results of a benchmark problem, obtaining information about vendor support, and contacting user groups. The final step is to evaluate the findings and make a selection. A weighted factor matrix is used to analyze the qualitative variables, and the results are reported as a performance/cost index. 4. The Studebaker Company is evaluating two proposals for a commercial software package. Three relevant factors were identified and weighted. Then the evaluation team assigned raw scores from 1 to 5 to each factor for each vendor. Proposal One will cost $70,000 and Proposal Two will cost $65,000. Weight Proposal One Proposal Two Vendor support 30 4 5 Ease of use 30 5 4 Range of capabilities 40 5 3 Determine a composite score and a performance/cost index for both proposals. Which proposal is the more economically feasible choice? ANS: The composite score is 470 for Proposal One and 390 for Proposal Two. The performance/cost index is 6.7 for Proposal One and 6.0 for Proposal Two. Based on this analysis, Proposal One is the more economically feasible proposal. 5. Discuss the advantages and disadvantages of the three methods of converting to a new system: cold turkey cutover, phased cutover, and parallel operation cutover. ANS: Cold turkey–This is the fastest, quickest and least expensive cutover method. It is also the most risky. If the system does not function properly, there is no backup system to rely on. Phased cutover–The phased cutover avoids the risk of total system failure because the conversion occurs one module at a time. The disadvantage of this method is the potential incompatibilities between new modules that have been implemented and old modules that have not yet been phased out. Parallel operation cutover–This is the most time consuming and costly of the three methods, but it also provides the greatest security. The old system is not terminated until the new system is tested for accuracy. 6. What issues must be considered in designing hardcopy documents? ANS: The issues to be considered in designing hardcopy documents relate to the physical operations of the business. Handling: designers must take into account moisture, manipulation, temperature, etc. Storage: where, why, environment, time. Number of copies: how many are needed, where will they be stored, etc. Forms distribution sheets can help determine the number of copies needed. Form size: should be standard unless special circumstances are involved. 7. What is the role of test data? What is a base case? ANS: Test data is hypothetical data with known results. The test data is run through the system to verify the processing occurs correctly. Test data should test all aspects of the new system including error capture. When a thorough set of test data is developed, it is saved to document system performance at the time of testing. This is the base case. It can therefore be compared to results of test data after system modification. 8. Correctly designed modules possess two attributes. Name and explain each. ANS: Coupling measures the degree of interaction or exchange of data between modules. A loosely coupled module is independent of the others. Modules with a great deal of interaction are tightly coupled. Cohesion refers to the number of tasks a module performs. Strong cohesion means that each module performs a single, well-defined task. Chapter 15—IT Controls Part I: Sarbanes-Oxley and IT Governance TRUE/FALSE 1. Corporate management (including the CEO) must certify monthly and annually their organization’s internal controls over financial reporting. ANS: F 2. Both the SEC and the PCAOB requires management to use the COBIT framework for assessing internal control adequacy. ANS: F 3. Both the SEC and the PCAOB requires management to use the COSO framework for assessing internal control adequacy. ANS: F 4. A qualified opinion on management’s assessment of internal controls over the financial reporting system necessitates a qualified opinion on the financial statements? ANS: F 5. The same internal control objectives apply to manual and computer-based information systems. ANS: T 6. To fulfill the segregation of duties control objective, computer processing functions (like authorization of credit and billing) are separated. ANS: F 7. To ensure sound internal control, program coding and program processing should be separated. ANS: T 8. Some systems professionals have unrestricted access to the organization's programs and data. ANS: T 9. Application controls apply to a wide range of exposures that threaten the integrity of all programs processed within the computer environment. ANS: F 10. The Database Administrator should be separated from systems development. ANS: T 11. A disaster recovery plan is a comprehensive statement of all actions to be taken after a disaster. ANS: T 12. IT auditing is a small part of most external and internal audits. ANS: F 13. Assurance services is an emerging field that goes beyond the auditor’s traditional attestation function. ANS: T 14. An IT auditor expresses an opinion on the fairness of the financial statements. ANS: F 15. External auditing is an independent appraisal function established within an organization to examine and evaluate its activities as a service to the organization. ANS: F 16. External auditors can cooperate with and use evidence gathered by internal audit departments that are organizationally independent and that report to the Audit Committee of the Board of Directors. ANS: T 17. Tests of controls determine whether the database contents fairly reflect the organization's transactions. ANS: F 18. Audit risk is the probability that the auditor will render an unqualified opinion on financial statements that are materially misstated. ANS: T 19. A strong internal control system will reduce the amount of substantive testing that must be performed. ANS: T 20. Substantive testing techniques provide information about the accuracy and completeness of an application's processes. ANS: F MULTIPLE CHOICE 1. Which of the following is NOT an implication of section 302 of the Sarbanes-Oxley Act? a. Auditors must determine, whether changes in internal control has, or is likely to, materially affect internal control over financial reporting. b. Auditors must interview management regarding significant changes in the design or operation of internal control that occurred since the last audit. c. Corporate management (including the CEO) must certify monthly and annually their organization’s internal controls over financial reporting. d. Management must disclose any material changes in the company’s internal controls that have occurred during the most recent fiscal quarter. ANS: C 2. Which of the following is NOT a requirement in management’s report on the effectiveness of internal controls over financial reporting? a. A statement of management’s responsibility for establishing and maintaining adequate internal control user satisfaction. b. A statement that the organizations internal auditors has issued an attestation report on management’s assessment of the companies internal controls. c. A statement identifying the framework used by management to conduct their assessment of internal controls. d. An explicit written conclusion as to the effectiveness of internal control over financial reporting. ANS: B 3. In a computer-based information system, which of the following duties needs to be separated? a. program coding from program operations b. program operations from program maintenance c. program maintenance from program coding d. all of the above duties should be separated ANS: D 4. Supervision in a computerized environment is more complex than in a manual environment for all of the following reasons except a. rapid turnover of systems professionals complicates management's task of assessing the competence and honesty of prospective employees b. many systems professionals have direct and unrestricted access to the organization's programs and data c. rapid changes in technology make staffing the systems environment challenging d. systems professionals and their supervisors work at the same physical location ANS: D 5. Adequate backups will protect against all of the following except a. natural disasters such as fires b. unauthorized access c. data corruption caused by program errors d. system crashes ANS: B 6. Which is the most critical segregation of duties in the centralized computer services function? a. systems development from data processing b. data operations from data librarian c. data preparation from data control d. data control from data librarian ANS: A 7. Systems development is separated from data processing activities because failure to do so a. weakens database access security b. allows programmers access to make unauthorized changes to applications during execution c. results in inadequate documentation d. results in master files being inadvertently erased ANS: B 8. Which organizational structure is most likely to result in good documentation procedures? a. separate systems development from systems maintenance b. separate systems analysis from application programming c. separate systems development from data processing d. separate database administrator from data processing ANS: A 9. All of the following are control risks associated with the distributed data processing structure except a. lack of separation of duties b. system incompatibilities c. system interdependency d. lack of documentation standards ANS: C 10. Which of the following is not an essential feature of a disaster recovery plan? a. off-site storage of backups b. computer services function c. second site backup d. critical applications identified ANS: B 11. A second site backup agreement between two or more firms with compatible computer facilities to assist each other with data processing needs in an emergency is called a. internally provided backup b. recovery operations center c. empty shell d. mutual aid pact ANS: D 12. The major disadvantage of an empty shell solution as a second site backup is a. the host site may be unwilling to disrupt its processing needs to process the critical applications of the disaster stricken company b. intense competition for shell resources during a widespread disaster c. maintenance of excess hardware capacity d. the control of the shell site is an administrative drain on the company ANS: B 13. An advantage of a recovery operations center is that a. this is an inexpensive solution b. the initial recovery period is very quick c. the company has sole control over the administration of the center d. none of the above are advantages of the recovery operations center ANS: B 14. For most companies, which of the following is the least critical application for disaster recovery purposes? a. b. c. d. month-end adjustments accounts receivable accounts payable order entry/billing ANS: A 15. The least important item to store off-site in case of an emergency is a. backups of systems software b. backups of application software c. documentation and blank forms d. results of the latest test of the disaster recovery program ANS: D 16. Some companies separate systems analysis from programming/program maintenance. All of the following are control weaknesses that may occur with this organizational structure except a. systems documentation is inadequate because of pressures to begin coding a new program before documenting the current program b. illegal lines of code are hidden among legitimate code and a fraud is covered up for a long period of time c. a new systems analyst has difficulty in understanding the logic of the program d. inadequate systems documentation is prepared because this provides a sense of job security to the programmer ANS: C 17. All of the following are recommended features of a fire protection system for a computer center except a. clearly marked exits b. an elaborate water sprinkler system c. manual fire extinguishers in strategic locations d. automatic and manual alarms in strategic locations ANS: B 18. Which concept is not an integral part of an audit? a. evaluating internal controls b. preparing financial statements c. expressing an opinion d. analyzing financial data ANS: B 19. Which statement is not true? a. Auditors must maintain independence. b. IT auditors attest to the integrity of the computer system. c. IT auditing is independent of the general financial audit. d. IT auditing can be performed by both external and internal auditors. ANS: C 20. Typically, internal auditors perform all of the following tasks except a. IT audits b. evaluation of operational efficiency c. review of compliance with legal obligations d. internal auditors perform all of the above tasks ANS: D 21. The fundamental difference between internal and external auditing is that a. internal auditors represent the interests of management and external auditors represent outsiders b. internal auditors perform IT audits and external auditors perform financial statement audits c. internal auditors focus on financial statement audits and external auditors focus on operational audits and financial statement audits d. external auditors assist internal auditors but internal auditors cannot assist external auditors ANS: A 22. Internal auditors assist external auditors with financial audits to a. reduce audit fees b. ensure independence c. represent the interests of management d. the statement is not true; internal auditors are not permitted to assist external auditors with financial audits ANS: A 23. Which statement is not correct? a. Auditors gather evidence using tests of controls and substantive tests. b. The most important element in determining the level of materiality is the mathematical formula. c. Auditors express an opinion in their audit report. d. Auditors compare evidence to established criteria. ANS: B 24. All of the following are steps in an IT audit except a. substantive testing b. tests of controls c. post-audit testing d. audit planning ANS: C 25. When planning the audit, information is gathered by all of the following methods except a. completing questionnaires b. interviewing management c. observing activities d. confirming accounts receivable ANS: D 26. Substantive tests include a. examining the safety deposit box for stock certificates b. reviewing systems documentation c. completing questionnaires d. observation ANS: A 27. Tests of controls include a. confirming accounts receivable b. counting inventory c. completing questionnaires d. counting cash ANS: C 28. All of the following are components of audit risk except a. control risk b. legal risk c. detection risk d. inherent risk ANS: B 29. Control risk is a. the probability that the auditor will render an unqualified opinion on financial statements that are materially misstated b. associated with the unique characteristics of the business or industry of the client c. the likelihood that the control structure is flawed because controls are either absent or inadequate to prevent or detect errors in the accounts d. the risk that auditors are willing to take that errors not detected or prevented by the control structure will also not be detected by the auditor ANS: C 30. All of the following tests of controls will provide evidence about the physical security of the computer center except a. review of fire marshal records b. review of the test of the backup power supply c. verification of the second site backup location d. observation of procedures surrounding visitor access to the computer center ANS: C 31. All of the following tests of controls will provide evidence about the adequacy of the disaster recovery plan except a. inspection of the second site backup b. analysis of the fire detection system at the primary site c. review of the critical applications list d. composition of the disaster recovery team ANS: B 32. Which of the following is true? a. In the CBIS environment, auditors gather evidence relating only to the contents of databases, not the reliability of the computer system. b. Conducting an audit is a systematic and logical process that applies to all forms of information systems. c. Substantive tests establish whether internal controls are functioning properly. d. IT auditors prepare the audit report if the system is computerized. ANS: B 33. Inherent risk a. b. c. d. exists because all control structures are flawed in some ways. is the likelihood that material misstatements exist in the financial statements of the firm. is associated with the unique characteristics of the business or industry of the client. is the likelihood that the auditor will not find material misstatements. ANS: C 34. Attestation services require all of the following except a. written assertions and a practitioner’s written report b. the engagement is designed to conduct risk assessment of the client’s systems to verify their degree of SOX compliance c. the formal establishment of measurements criteria d. the engagement is limited to examination, review, and application of agreed-upon procedures ANS: B 35. The financial statement of an organization reflects a set of management assertions about the financial health of the business. All of the following described types of assertions except a. that all of the assets and equities on the balance sheet exist b. that all employees are properly trained to carry out their assigned duties c. that all transactions on the income statement actually occurred d. that all allocated amounts such as depreciation are calculated on a systematic and rational basis ANS: B SHORT ANSWER 1. Which of the following statements is true? a. Both the SEC and the PCAOB requires the use of the COSO framework b. Both the SEC and the PCAOB requires the COBIT framework c. The SEC recommends COBIT and the PCAOB recommends COSO d. Any framework can be used that encompass all of COSO’s general themes ANS: Both c and d above are true. 2. COSO identifies two broad groupings of information system controls. What are they? ANS: general; application 3. The Sarbanes-Oxley Act contains many sections. Which sections are the focus of this chapter? ANS: The chapter concentrate on internal control and audit responsibilities pursuant to Sections 302 and 404. 4. What control framework is recommended by the PCAOB? ANS: The PCAOB’s Auditing Standard No. 2 endorses the use of COSO as the framework for control assessment. 5. What are the objectives of application controls? ANS: The objectives of application controls are to ensure the validity, completeness, and accuracy financial transactions. 6. Define general controls. ANS: General controls apply to all systems. They are not application specific. General controls include controls over IT governance, the IT infrastructure, security and access to operating systems and databases, application acquisition and development, and program changes. 7. Discuss the key features of Section 302 of the Sarbanes-Oxley Act. ANS: Section 302 requires that corporate management (including the CEO) certify quarterly and annually their organization’s internal controls over financial reporting. The certifying officers are required to: a. have designed internal controls b. they must disclose any material changes in the company’s internal controls that have occurred during the most recent fiscal quarter. 8. What the three primary CBIS functions that must be separated? ANS: Programming should be separated from computer operations Programming maintenance should be separated from new systems development. End users should be separate from systems design. 9. List three pairs of system functions that should be separated in the centralized computer services organization. Describe a risk exposure if the functions are not separated. Functions to Separate Risk Exposure __________________________ __________________________ __________________________ __________________________ __________________________ __________________________ ANS: separate systems development from data processing operations (unauthorized changes to application programs during execution), separate database administrator from systems development (unauthorized access to database files), separate new systems development from systems maintenance (writing fraudulent code and keeping it concealed during maintenance), separate data library from computer operations (loss of files or erasing current files) 10. For disaster recovery purposes, what criteria are used to identify an application or data as critical? ANS: Critical application and files are those that impact the short-run survival of the firm. Critical items impact cash flows, legal obligations, and customer relations. 11. Describe the components of a disaster recovery plan. ANS: Every disaster recovery plan should: designate a second site backup identify critical applications prepare backup and off-site storage procedures create a disaster recovery team test the disaster recovery plan 12. What is a mirrored data center? ANS: Duplicating programs and data onto a computer at a separate location. Mirroring is performed for backup purposes. 13. Why is supervisory control more elaborate in the CBIS environment than in the manual environment? ANS: The required skills of systems professionals lead to high rates of turnover. Systems professionals work in areas that permit direct and unrestricted access to the organizations programs and data. Management is unable to adequately observe employees in the CBIS environment. 14. What are some control implications of the distributed data processing model? ANS: Control issues of the DDP model include incompatibility of hardware and software purchased without coordination, redundancy of work with different units duplicating effort, incompatible duties because of consolidation in small units, difficulty acquiring qualified personnel, and lack of standards. 15. What is program fraud? ANS: Program fraud involves making unauthorized changes to parts of a program for the purpose of committing an illegal act. 16. The distributed data processing approach carries some control implications of which accountants should be aware. Discuss two. ANS: Incompatibility of hardware and software, selected by users working independently, can result in system incompatibility that can affect communication. When individuals in different parts of the organization “do their own thing,” there can be significant redundancy between units. When user areas handle their own computer services functions, there may be a tendency to consolidate incompatible activities. Small units may lack the ability to evaluate systems professionals and to provide adequate opportunities and may therefore have difficulty acquiring qualified professionals. As the number of units handling systems tasks, there is an increasing chance that the systems will lack standards. 17. __________________________ are intentional mistakes while __________________________ are unintentional mistakes. ANS: Irregularities, Errors 18. Explain the relationship between internal controls and substantive testing. ANS: The stronger the internal controls, the less substantive testing must be performed. 19. Discuss the interrelationship of tests of controls, audit objectives, exposures, and existing controls. ANS: During the risk analysis phase of the audit, the auditor develops an understanding of the exposures that threaten the firm and about the existing controls. Based on that understanding, the auditor develops audit objectives. From the audit objectives the auditor designs and performs tests of controls. 20. Distinguish between errors and irregularities. Which do you think concern the auditors the most? ANS: Errors are unintentional mistakes; while irregularities are intentional misrepresentations to perpetrate a fraud or mislead the users of financial statements. Errors are a concern if they are numerous or sizable enough to cause the financial statements to be materially misstated. Processes which involve human actions will contain some amount of human error. Computer processes should only contain errors if the programs are erroneous, or if systems operating procedures are not being closely and competently followed. Errors are typically much easier to uncover than misrepresentations, thus auditors typically are more concerned whether they have uncovered any and all irregularities. 21. Describe two tests that an auditor would perform to ensure that the disaster recovery plan is adequate. ANS: review second site backup plan, critical application list, and off-site backups of critical libraries, applications and data files; ensure that backup supplies, source documents and documentation are located off-site; review which employees are members of disaster recovery team 22. Distinguish between inherent risk and control risk. How do internal controls and detection risk fit in? ANS: Inherent risk is associated with the unique characteristics of the business or industry of the client. Firms in declining industries are considered to have more inherent risk than firms in stable or thriving industries. Control risk is the likelihood that the control structure is flawed because internal controls are either absent or inadequate to prevent or detect errors in the accounts. Internal controls may be present in firms with inherent risk, yet the financial statements may be materially misstated due to circumstances outside the control of the firm, such as a customer with unpaid bills on the verge of bankruptcy. Detection risk is the risk that auditors are willing to accept that errors are not detected or prevented by the control structure. Typically, detection risk will be lower for firms with higher inherent risk and control risk. 23. Contrast internal and external auditing. ANS: Internal auditing is an independent appraisal function established within an organization to examine and evaluate its activities as a service to the organization. External auditing is often called "independent auditing" because it is done by certified public accountants who are independent of the organization being audited. This independence is necessary since the external auditors represent the interests of third-party stakeholders such as shareholders, creditors, and government agencies. 24. What are the components of audit risk? ANS: Inherent risk is associated with the unique characteristics of the business itself; control risk is the likelihood that the control structure is flawed because controls are absent or inadequate; and detection risk is the risk that auditors are willing to take that errors will not be detected by the audit. 25. How do the tests of controls affect substantive tests? ANS: Tests of controls are used by the auditor to measure the strength of the internal control structure. The stronger the internal controls, the lower the control risk, and the less substantive testing the auditor must do. 26. What is an auditor looking for when testing computer center controls? ANS: When testing computer center controls, the auditor is trying to determine that the physical security controls are adequate to protect the organization from physical exposures, that insurance coverage on equipment is adequate, that operator documentation is adequate to deal with operations and failures, and that the disaster recovery plan is adequate and feasible. 27. Define and contrast attestation services and assurance services. ANS: Attest services are engagements in which a practitioner is engaged to issue, or does issue, a written communication that expresses a conclusion about the reliability of a written assertion that is the responsibility of another party, e.g., the financial statements prepared by an organization. Assurance services are professional services that are designed to improve the quality of information, both financial and non-financial, used by decision makers. The domain of assurance services is intentionally unbounded. ESSAY 1. Discuss the key features of Section 404 of the Sarbanes-Oxley Act ANS: Section 404 requires the management of public companies to assess the effectiveness of their organization’s internal controls over financial reporting and provide an annual report addressing the following points: 1) A statement of management’s responsibility for establishing and maintaining adequate internal control. 2) An assessment of the effectiveness of the company’s internal controls over financial reporting. 3) A statement that the organizations external auditors has issued an attestation report on management’s assessment of the companies internal controls. 4) An explicit written conclusion as to the effectiveness of internal control over financial reporting. 6) A statement identifying the framework used by management to conduct their assessment of internal controls. 2. Section 404 requires management to make a statement identifying the control framework used to conduct their assessment of internal controls. Discuss the options in selecting a control framework. ANS: The SEC has made specific reference to the Committee of the Sponsoring Organizations of the Treadway Commission (COSO) as a recommended control framework. Furthermore, the PCAOB’s Auditing Standard No. 2 endorses the use of COSO as the framework for control assessment. Although other suitable frameworks have been published, according to Standard No. 2, any framework used should encompass all of COSO’s general themes. 3. Explain how general controls impact transaction integrity and the financial reporting process. ANS: Consider an organization with poor database security controls. In such a situation, even data processed by systems with adequate built in application controls may be at risk. An individual who can circumvent database security, may then change, steal, or corrupt stored transaction data. Thus, general controls are needed to support the functioning of application controls, and both are needed to ensure accurate financial reporting. 4. Prior to SOX, external auditors were required to be familiar with the client organization’s internal controls, but not test them. Explain. ANS: Auditors had the option of not relying on internal controls in the conduct of an audit and therefore did not need to test them. Instead auditors could focus primarily of substantive tests. Under SOX, management is required to make specific assertions regarding the effectiveness of internal controls. To attest to the validity of these assertions, auditors are required to test the controls. 5. Does a qualified opinion on managements assessment of internal controls over the financial reporting system necessitate a qualified opinion on the financial statements? Explain. ANS: No. Auditors are permitted to simultaneously render a qualified opinion on management’s assessment of internal controls and an unqualified opinion on the financial statements. In other words, it is technically possible for auditors to find internal controls over financial reporting to be weak, but conclude through substantive tests that the weaknesses did not cause the financial statements to be materially misrepresented. 6. The PCAOB’s standard No. 2 specifically requires auditors to understand transaction flows in designing their test of controls. What steps does this entail? ANS: This involves: 1. Selecting the financial accounts that have material implications for financial reporting. 2. Identify the application controls related to those accounts. As previously noted, the 3. Identify the general that support the application controls. The sum of these controls, both application and general, constitute the relevant internal controls over financial reporting that need to be reviewed. 7. What fraud detection responsibilities (if any) are imposed on auditors by SOX. ANS: Standard No. 2 places new responsibility on auditors to detect fraudulent activity. The standard emphasizes the importance of controls designed to prevent or detect fraud that could lead to material misstatement of the financial statements. Management is responsible for implementing such controls and auditors are expressly required to test them. 8. Describe how a Corporate Computer Services Function can overcome some of the problems associated with distributed data processing. ANS: The Corporate Computer Services Function may provide the following technical advice and expertise to distributed data processing units: central testing of commercial software and hardware; installation of new software; trouble-shooting hardware and software problems; technical training; firm-wide standard setting for the systems area; and performance evaluation of systems professionals. 9. Discuss the advantages and disadvantages of the second site backup options. ANS: Second site backups include mutual aid pacts, empty shell, recovery operations center, and internally provided backups. Mutual Aid Pacts Advantages Inexpensive Disadvantages May encounter reluctance to share facilities during an emergency Empty Shell Advantages Disadvantages Inexpensive Extended time lag between disaster and initial recovery May encounter competition among users for shell resources Recovery Operations Center Advantages Rapid initial recovery Disadvantages Expensive Internally Provided Backups Advantages Controlled by the firm Compatibility of hardware and software Rapid initial recovery Disadvantages Expense of maintaining excess capacity year round 10. Internal control in a computerized environment can be divided into two broad categories. What are they? Explain each. ANS: Internal controls can be divided into two broad categories. General controls apply to all or most of a system to minimize exposures that threaten the integrity of the applications being processed. These include operating system controls, data management controls, organizational structure controls, system development controls, system maintenance controls, computer center security, Internet and Intranet controls, EDI controls, and PC controls. Application controls focus on exposures related to specific parts of the system: payroll, accounts receivable, etc. 11. Auditors examine the physical environment of the computer center as part of their audit. Many characteristics of computer centers are of interest to auditors. What are they? Discuss. ANS: The characteristics of computer centers that are of interest of auditors include: physical location because it affects the risk of disaster–it should be away from man-made and natural hazards; construction of the computer center should be sound; access to the computer center should be controlled; air-conditioning should be adequate given the heat generated by electronic equipment and the failure that can result from over-heating; fire suppression systems are critical; and adequate power supply is needed to ensure service. 12. Explain why certain duties that are deemed incompatible in a manual system may be combined in a CBIS environment? Give an example. ANS: In a CBIS environment it would be inefficient and contrary to the objectives of automation to separate such tasks and processing and recoding a transaction among several different application programs merely to emulate a manual control model. Further, the reason for separating tasks is to control against the negative behavior of humans; in a CBIS the computer performs the tasks not humans. 13. Compare and contrast the following disaster recovery options: mutual aid pact, empty shell, recovery operations center, and internally provided backup. Rank them from most risky to least risky, as well as most costly to least costly. ANS: A mutual aid pact requires two or more organizations to agree and trust one another to aid each other with their data processing needs in the event of a disaster. This method is the lowest cost, but also somewhat risky for two reasons. First, the host company must be trusted to scale back its own processing in order to process the transactions of the disaster-stricken company. Second, the two or more firms must not be affected by the same disaster or the plan fails. The next lowest cost method is internally provided backup. With this method, organizations with multiple data processing centers may invest in internal excess capacity and support themselves in the case of disaster in one data processing center. This method is not as risky as the mutual aid pact because reliance on another organization is not a factor. In terms of cost, the next highest method is the empty shell where two or more organizations buy or lease space for a data processing center. The space is made ready for computer installation; however, no computer equipment is installed. This method requires lease or mortgage payments, as well as payment for air conditioning and raised floors. The risk of this method is that the hardware, software, and technicians may be difficult, if not impossible, to have available in the case of a natural disaster. Further, if multiple members' systems crash simultaneously, an allocation problem exists. The method with lowest risk and also the highest cost is the recovery operations center. This method takes the empty shell concept one step further - the computer equipment is actually purchased and software may even be installed. Assuming that this site is far enough away from the disaster-stricken area not to be affected by the disaster, this method can be a very good safeguard. 14. What is a disaster recovery plan? What are the key features? ANS: A disaster recovery plan is a comprehensive statement of all actions to be taken before, during, and after a disaster, along with documented, tested procedures that will ensure the continuity of operations. The essential features are: providing second site backup, identifying critical applications, backup and off-site storage procedures, creating a disaster recovery team, and testing the disaster recovery plan. Chapter 16—IT Controls Part II: Security and Access TRUE/FALSE 1. In a computerized environment, the audit trail log must be printed onto paper documents. ANS: F 2. Disguising message packets to look as if they came from another user and to gain access to the host’s network is called spooling. ANS: F 3. Access controls take on increased importance in a computerized environment because all of the records may be found in one place. ANS: T 4. Computer viruses usually spread throughout the system before being detected. ANS: T 5. A worm is software program that replicates itself in areas of idle memory until the system fails. ANS: T 6. Viruses rarely attach themselves to executable files. ANS: F 7. Subschemas are used to authorize user access privileges to specific data elements. ANS: F 8. A recovery module suspends all data processing while the system reconciles its journal files against the database. ANS: F 9. The Database Management System controls program files. ANS: F 10. Operating system controls are of interest to system professionals but should not concern accountants and auditors. ANS: F 11. The most frequent victims of program viruses are microcomputers. ANS: T 12. Access controls protect databases against destruction, loss or misuse through unauthorized access. ANS: T 13. Operating system integrity is not of concern to accountants because only hardware risks are involved. ANS: F 14. Audit trails in computerized systems are comprised of two types of audit logs: detailed logs of individual keystrokes and event-oriented logs. ANS: T 15. In a telecommunications environment, line errors can be detected by using an echo check. ANS: T 16. Firewalls are special materials used to insulate computer facilities ANS: F 17. The message authentication code is calculated by the sender and the receiver of a data transmission. ANS: T 18. The request-response technique should detect if a data communication transmission has been diverted. ANS: T 19. Electronic data interchange translation software interfaces with the sending firm and the value added network. ANS: F 20. A value added network can detect and reject transactions by unauthorized trading partners. ANS: T 21. Electronic data interchange customers may be given access to the vendor's data files. ANS: T 22. The audit trail for electronic data interchange transactions is stored on magnetic media. ANS: T 23. A firewall is a hardware partition designed to protect networks from power surges. ANS: F 24. To preserve audit trails in a CBIS environment, transaction logs are permanent records of transactions. ANS: T 25. Examining programmer authority tables for information about who has access to Data Definition Language commands will provide evidence about who is responsible for creating subschemas. ANS: T MULTIPLE CHOICE 1. The operating system performs all of the following tasks except a. translates third-generation languages into machine language b. assigns memory to applications c. authorizes user access d. schedules job processing ANS: C 2. Which of the following is considered an unintentional threat to the integrity of the operating system? a. a hacker gaining access to the system because of a security flaw b. a hardware flaw that causes the system to crash c. a virus that formats the hard drive d. the systems programmer accessing individual user files ANS: B 3. A software program that replicates itself in areas of idle memory until the system fails is called a a. Trojan horse b. worm c. logic bomb d. none of the above ANS: B 4. A software program that allows access to a system without going through the normal logon procedures is called a a. logic bomb b. Trojan horse c. worm d. back door ANS: D 5. All of the following will reduce the exposure to computer viruses except a. install antivirus software b. install factory-sealed application software c. assign and control user passwords d. install public-domain software from reputable bulletin boards ANS: D 6. Which backup technique is most appropriate for sequential batch systems? a. grandfather-father-son approach b. staggered backup approach c. direct backup d. remote site, intermittent backup ANS: A 7. When creating and controlling backups for a sequential batch system, a. the number of backup versions retained depends on the amount of data in the file b. off-site backups are not required c. backup files can never be used for scratch files d. the more significant the data, the greater the number of backup versions ANS: D 8. Hackers can disguise their message packets to look as if they came from an authorized user and gain access to the host’s network using a technique called a. spoofing. b. spooling. c. dual-homed. d. screening. ANS: A 9. In a direct access file system a. backups are created using the grandfather-father-son approach b. processing a transaction file against a maser file creates a backup file c. files are backed up immediately before an update run d. if the master file is destroyed, it cannot be reconstructed ANS: C 10. Which of the following is not an access control in a database system? a. antivirus software b. database authorization table c. passwords d. voice prints ANS: A 11. Which is not a biometric device? a. password b. retina prints c. voice prints d. signature characteristics ANS: A 12. Which of the following is not a basic database backup and recovery feature? a. checkpoint b. backup database c. transaction log d. database authority table ANS: D 13. All of the following are objectives of operating system control except a. protecting the OS from users b. protesting users from each other c. protecting users from themselves d. protecting the environment from users ANS: D 14. Passwords are secret codes that users enter to gain access to systems. Security can be compromised by all of the following except a. failure to change passwords on a regular basis b. using obscure passwords unknown to others c. recording passwords in obvious places d. selecting passwords that can be easily detected by computer criminals ANS: B 15. Audit trails cannot be used to a. detect unauthorized access to systems b. facilitate reconstruction of events c. reduce the need for other forms of security d. promote personal accountability ANS: C 16. Which control will not reduce the likelihood of data loss due to a line error? a. echo check b. encryption c. vertical parity bit d. horizontal parity bit ANS: B 17. Which method will render useless data captured by unauthorized receivers? a. echo check b. parity bit c. public key encryption d. message sequencing ANS: C 18. Which method is most likely to detect unauthorized access to the system? a. message transaction log b. data encryption standard c. vertical parity check d. request-response technique ANS: A 19. All of the following techniques are used to validate electronic data interchange transactions except a. value added networks can compare passwords to a valid customer file before message transmission b. prior to converting the message, the translation software of the receiving company can compare the password against a validation file in the firm's database c. the recipient's application software can validate the password prior to processing d. the recipient's application software can validate the password after the transaction has been processed ANS: D 20. In an electronic data interchange environment, customers routinely access a. b. c. d. the vendor's price list file the vendor's accounts payable file the vendor's open purchase order file none of the above ANS: A 21. All of the following tests of controls will provide evidence that adequate computer virus control techniques are in place and functioning except a. verifying that only authorized software is used on company computers b. reviewing system maintenance records c. confirming that antivirus software is in use d. examining the password policy including a review of the authority table ANS: B 22. Audit objectives for the database management include all of the following except a. verifying that the security group monitors and reports on fault tolerance violations b. confirming that backup procedures are adequate c. ensuring that authorized users access only those files they need to perform their duties d. verifying that unauthorized users cannot access data files ANS: A 23. All of the following tests of controls will provide evidence that access to the data files is limited except a. inspecting biometric controls b. reconciling program version numbers c. comparing job descriptions with access privileges stored in the authority table d. attempting to retrieve unauthorized data via inference queries ANS: B 24. Audit objectives for communications controls include all of the following except a. detection and correction of message loss due to equipment failure b. prevention and detection of illegal access to communication channels c. procedures that render intercepted messages useless d. all of the above ANS: D 25. When auditors examine and test the call-back feature, they are testing which audit objective? a. incompatible functions have been segregated b. application programs are protected from unauthorized access c. physical security measures are adequate to protect the organization from natural disaster d. illegal access to the system is prevented and detected ANS: D 26. In an Electronic Data Interchange (EDI) environment, when the auditor compares the terms of the trading partner agreement against the access privileges stated in the database authority table, the auditor is testing which audit objective? a. all EDI transactions are authorized b. unauthorized trading partners cannot gain access to database records c. authorized trading partners have access only to approved data d. a complete audit trail is maintained ANS: C 27. Audit objectives in the Electronic Data Interchange (EDI) environment include all of the following except a. all EDI transactions are authorized b. unauthorized trading partners cannot gain access to database records c. a complete audit trail of EDI transactions is maintained d. backup procedures are in place and functioning properly ANS: D 28. In determining whether a system is adequately protected from attacks by computer viruses, all of the following policies are relevant except a. the policy on the purchase of software only from reputable vendors b. the policy that all software upgrades are checked for viruses before they are implemented c. the policy that current versions of antivirus software should be available to all users d. the policy that permits users to take files home to work on them ANS: D 29. Which of the following is not a test of access controls? a. biometric controls b. encryption controls c. backup controls d. inference controls ANS: C 30. In an electronic data interchange environment, customers routinely a. access the vendor's accounts receivable file with read/write authority b. access the vendor's price list file with read/write authority c. access the vendor's inventory file with read-only authority d. access the vendor's open purchase order file with read-only authority ANS: C 31. In an electronic data interchange environment, the audit trail a. is a printout of all incoming and outgoing transactions b. is an electronic log of all transactions received, translated, and processed by the system c. is a computer resource authority table d. consists of pointers and indexes within the database ANS: B 32. All of the following are designed to control exposures from subversive threats except a. firewalls b. one-time passwords c. field interrogation d. data encryption ANS: C 33. Many techniques exist to reduce the likelihood and effects of data communication hardware failure. One of these is a. hardware access procedures b. antivirus software c. parity checks d. data encryption ANS: C 34. Which of the following deal with transaction legitimacy? a. transaction authorization and validation b. access controls c. EDI audit trail d. all of the above ANS: D 35. Firewalls are a. special materials used to insulate computer facilities b. a system that enforces access control between two networks c. special software used to screen Internet access d. none of the above ANS: B 36. The database attributes that individual users have permission to access are defined in a. operating system. b. user manual. c. database schema. d. user view. e. application listing. ANS: D 37. An integrated group of programs that supports the applications and facilitates their access to specified resources is called a (an) a. operating system. b. database management system. c. utility system d. facility system. e. object system. ANS: A SHORT ANSWER 1. Briefly define an operating system. ANS: An integrated group of programs that supports the applications and facilitates their access to specified resources. 2. What is a virus? ANS: A virus is a program that attaches itself to another legitimate program in order to penetrate the operating system. 3. Describe one benefit of using a call-back device. ANS: Access to the system is achieved when the call-back device makes contact with an authorized user. This reduces the chance of an intruder gaining access to the system from an unauthorized remote location. 4. Contrast the Private Encryption Standard approach with the Public Key Encryption approach to controlling access to telecommunication messages. ANS: In the Private Encryption Standard approach, both the sender and the receiver use the same key to encode and decode the message. In the Public Key Encryption approach all senders receive a copy of the key used to send messages; the receiver is the only one with access to the key to decode the message. 5. List three methods of controlling unauthorized access to telecommunication messages. ANS: call-back devices, data encryption, message sequence numbering, message authentication codes, message transaction logs, and request-response technique 6. Describe two ways that passwords are used to authorize and validate messages in the electronic data interchange environment. ANS: value-added networks use passwords to detect unauthorized transactions before they are transmitted to recipients; the recipient of the message can validate the password prior to translating the message; the recipient of the message can validate the password prior to processing the transaction 7. Explain how transactions are audited in an electronic data interchange environment. ANS: Firms using electronic data interchange maintain an electronic log of each transaction as it moves from receipt to translation to communication of the message. This transaction log restores the audit trail that was lost because no source documents exist. Verification of the entries in the log is part of the audit process. 8. Describe are some typical problems with passwords? ANS: users failing to remember passwords; failure to change passwords frequently; displaying passwords where others can see them; using simple, easy-to-guess passwords 9. Discuss the key features of the one-time password technique: ANS: The one-time password was designed to overcome the problems associated with reusable passwords. The user’s password changes continuously. This technology employs a credit card-sized smart card that contains a microprocessor programmed with an algorithm that generates, and electronically displays, a new and unique password every 60 seconds. The card works in conjunction with special authentication software located on a mainframe or network server computer. Each user’s card is synchronized to the authentication software, so that at any point in time both the smart card and the network software are generating the same password for the same user. 10. Describe two tests of controls that would provide evidence that the database management system is protected against unauthorized access attempts. ANS: compare job descriptions with authority tables; verify that database administration employees have exclusive responsibility for creating authority tables and designing user subschemas; evaluate biometric and inference controls 11. What is event monitoring? ANS: Event monitoring summarizes key activities related to system resources. Event logs typically record the IDs of all users accessing the system; the time and duration of a user’s session; programs that were executed during a session; and the files, databases, printers, and other resources accessed. 12. What are the auditor's concerns in testing EDI controls? ANS: When testing EDI controls, the auditor's primary concerns are related to ascertaining that EDI transactions are authorized, validated, and in compliance with organization policy, that no unauthorized organizations gain access to records, that authorized trading partners have access only to approved data, and that adequate controls are in place to maintain a complete audit trail. 13. What is a database authorization table? ANS: The database authorization table contains rules that limit the actions a user can take. Each user is granted certain privileges that are coded in the authority table, which is used to verify the user’s action requests. 14. What is a user-defined procedure? ANS: A user-defined procedure allows the user to create a personal security program or routine to provide more positive user identification than a password can. For example, in addition to a password, the security procedure asks a series of personal questions (such as the user’s mother’s maiden name), which only the legitimate user is likely to know. 15. What are biometric devices? ANS: Biometric devices measure various personal characteristics such as fingerprints, voiceprints, retina prints, or signature characteristics. These user characteristics are digitized and stored permanently in a database security file or on an identification card that the user carries. When an individual attempts to access the database, a special scanning device captures his or her biometric characteristics, which it compares with the profile data stored internally or on the ID card. If the data do not match, access is denied. ESSAY 1. What are the three security objectives of audit trails? Explain. ANS: Audit trails support system security objectives in three ways. By detecting unauthorized access to the system, the audit trail protects the system from outsiders trying to breach system controls. By monitoring system performance, changes in the system may be detected. The audit trail can also contribute to reconstructing events such as system failures, security breaches, and processing errors. In addition, the ability to monitor user activity can support increased personal accountability. 2. What is an operating system? What does it do? What are operating system control objectives? ANS: An operating system is a computer’s control program. It controls user sharing of applications and resources such as processors, memory, databases, and peripherals such as printers. Common PC operating systems include Windows 2000, Windows NT, and Linux. An operating system carries out three primary functions: translating high level languages into machine language using modules called compilers and interpreters; allocating computer resources to users, workgroups, and applications; and managing job scheduling and multiprogramming. Operating systems have five basic control objectives: 1. to protect itself from users, 2. to protect users from each other, 3. to protect users from themselves, 4. to protect it from itself, and 5. to protect itself from its environment. 3. Discus three sources of exposure (threats) to the operating system. ANS: 1. Privileged personnel who abuse their authority. Systems administrators and systems programmers require unlimited access to the operating system to perform maintenance and to recover from system failures. Such individuals may use this authority to access users’ programs and data files. 2. Individuals both internal and external to the organization who browse the operating system to identify and exploit security flaws. 3. Individuals who intentionally (or accidentally) insert computer viruses or other forms of destructive programs into the operating system. 4. There are many techniques for breaching operating system controls. Discuss three. ANS: Browsing involves searching through areas of main memory for password information. Masquerading is a technique where a user is made to believe that he/she has accessed the operating system and therefore enters passwords, etc., that can later be used for unauthorized access. A virus is a program that attaches itself to legitimate software to penetrate the operating system. Most are destructive. A worm is software that replicates itself in memory. A logic bomb is a destructive program triggered by some "logical" condition–a matching date, e.g., Michelangelo's birthday. 5. A formal log-on procedure is the operating system’s first line of defense. Explain this works. ANS: When the user logs on, he or she is presented with a dialog box requesting the user’s ID and password. The system compares the ID and password to a database of valid users. If the system finds a match, then the log-on attempt is authenticated. If, however, the password or ID is entered incorrectly, the log-on attempt fails and a message is returned to the user. The message should not reveal whether the password or the ID caused the failure. The system should allow the user to reenter the log-on information. After a specified number of attempts (usually no more than five), the system should lock out the user from the system. 6. Explain the concept of discretionary access privileges. ANS: In centralized systems system administrator usually determines who is granted access to specific resources and maintains the access control list. In distributed systems, however, resources may be controlled (owned) by end users. Resource owners in this setting may be granted discretionary access privileges, which allow them to grant access privileges to other users. For example, the controller, who is the owner of the general ledger, may grant read-only privileges to a manager in the budgeting department. The accounts payable manager, however, may be granted both read and write permissions to the ledger. Any attempt by the budgeting manager to add, delete, or change the general ledger will be denied. The use of discretionary access control needs to be closely supervised to prevent security breaches because of its liberal use. 7. One purpose of a database system is the easy sharing of data. But this ease of sharing can also jeopardize security. Discuss at least three forms of access control designed to reduce this risk. ANS: Many types of access control are possible. A user view is a subset of a database that limits a user’s “view” or access to the database. The database authorization table contains rules that limit what a user can do, i.e., read, insert, modify, delete. A user-defined procedure adds additional queries to user access to prevent others from accessing in a specific user’s place. To protect the data in a database, many systems use data encryption to make it unreadable by intruders. A newer technique uses biometric devices to authenticate users. 8. Explain how the one-time password approach works. ANS: Under this approach, the user’s password changes continuously. To access the operating system, the user must provide both a secret reusable personal identification number (PIN) and the current one-time only password for that point in time. One technology employs a credit-card-sized device (smart card) that contains a microprocessor programmed with an algorithm that generates, and visually displays, a new and unique password every 60 seconds. The card works in conjunction with special authentication software located on a mainframe host or network server computer. At any point in time both the smart card and the network software are generating the same password for the same user. To access the network, the user enters the PIN followed by the current password displayed on the card. The password can be used one time only. 9. Network communication poses some special types of risk for a business. What are the two broad areas of concern? Explain. ANS: Two general types of risk exist when networks communicate with each other–risks from subversive threats and risks from equipment failure. Subversive threats include interception of information transmitted between sender and receiver, computer hackers gaining unauthorized access to the organization’s network, and denial-of-service attacks from remote locations on the Internet. Methods for controlling these risks include firewalls, encryption, digital signatures, digital certificates, message transaction logs, and call-back devices. Equipment failure can be the result of line errors. The problems can be minimized with the help of echo checks, parity checks, and good backup control. 10. What is EDI? How does its use affect the audit trail? ANS: Electronic data interchange is an arrangement which links the computer systems of two trading partners to expedite sales/purchases. The buying company’s purchasing system creates and transmits a purchase order electronically in an agreed format, either directly or through a value-added network. The selling company receives the information, and it is converted electronically into a sales order. The absence of paper documents in an EDI transaction disrupts the traditional audit trail. This can be compensated for through the use of transaction logs which can be reconciled. Chapter 17—IT Controls Part III: Systems Development, Program Changes, and Application Controls TRUE/FALSE 1. Programs in their compiled state are very susceptible to the threat of unauthorized modification. ANS: F 2. Maintenance access to systems increases the risk that logic will be corrupted either by the accident or intent to defraud. ANS: T 3. Source program library controls should prevent and detect unauthorized access to application programs. ANS: T 4. A check digit is a method of detecting data coding errors. ANS: T 5. Input controls are intended to detect errors in transaction data after processing. ANS: F 6. A header label is an internal, machine-readable label. ANS: T 7. The user test and acceptance procedure is the last point at which the user can determine the system’s acceptability prior to it going into service. ANS: T 8. A run-to-run control is an example of an output control. ANS: F 9. Shredding computer printouts is an example of an output control. ANS: T 10. In a CBIS environment, all input controls are implemented after data is input. ANS: F 11. Achieving batch control objectives requires grouping similar types of input transactions (such as sales orders) together in batches and then controlling the batches throughout data processing. ANS: T 12. The "white box" tests of program controls are also known as auditing through the computer. ANS: T 13. The presence of a SPLMS effectively guarantees program integrity. ANS: F 14. When using the test data method, the presence of multiple error messages indicates a flaw in the preparation of test transactions. ANS: F 15. The Base Case System Evaluation is a variation of the test data method. ANS: T 16. Tracing is a method used to verify the logical operations executed by a computer application. ANS: T 17. Generalized audit software packages are used to assist the auditor in performing substantive tests. ANS: T 18. The results of a parallel simulation are compared to the results of a production run in order to judge the quality of the application processes and controls. ANS: T 19. Firms with an independent internal audit staff may conduct tests of the system development life cycle on an ongoing basis. ANS: T 20. The programmer’s authority table will specify the libraries a programmer may access. ANS: T 21. Use of the integrated test facility poses no threat to organizational data files. ANS: F MULTIPLE CHOICE 1. Which statement is not correct? The audit trail in a computerized environment a. consists of records that are stored sequentially in an audit file b. traces transactions from their source to their final disposition c. is a function of the quality and integrity of the application programs d. may take the form of pointers, indexes, and embedded keys ANS: A 2. Which control is not associated with new systems development activities? a. reconciling program version numbers b. program testing c. user involvement d. internal audit participation ANS: A 3. Routine maintenance activities require all of the following controls except a. documentation updates b. testing c. formal authorization d. internal audit approval ANS: D 4. Which statement is correct? a. compiled programs are very susceptible to unauthorized modification b. the source program library stores application programs in source code form c. modifications are made to programs in machine code language d. the source program library management system increases operating efficiency ANS: B 5. Which control is not a part of the source program library management system? a. using passwords to limit access to application programs b. assigning a test name to all programs undergoing maintenance c. combining access to the development and maintenance test libraries d. assigning version numbers to programs to record program modifications ANS: C 6. Which control ensures that production files cannot be accessed without specific permission? a. Database Management System b. Recovery Operations Function c. Source Program Library Management System d. Computer Services Function ANS: C 7. Program testing a. involves individual modules only, not the full system b. requires creation of meaningful test data c. need not be repeated once the system is implemented d. is primarily concerned with usability ANS: B 8. The correct purchase order number, 123456, was incorrectly recorded as shown in the solutions. All of the following are transcription errors except a. 1234567 b. 12345 c. 124356 d. 123454 ANS: C 9. Which of the following is correct? a. check digits should be used for all data codes b. check digits are always placed at the end of a data code c. check digits do not affect processing efficiency d. check digits are designed to detect transcription and transposition errors ANS: D 10. Which statement is not correct? The goal of batch controls is to ensure that during processing a. transactions are not omitted b. transactions are not added c. transactions are free from clerical errors d. an audit trail is created ANS: C 11. An example of a hash total is a. total payroll checks–$12,315 b. total number of employees–10 c. sum of the social security numbers–12,555,437,251 d. none of the above ANS: C 12. Which statement is not true? A batch control record a. contains a transaction code b. records the record count c. contains a hash total d. control figures in the record may be adjusted during processing e. All the above are true ANS: E 13. Which of the following is not an example of a processing control? a. hash total. b. record count. c. batch total. d. check digit ANS: D 14. Which of the following is an example of input control test? a. sequence check b. zero value check c. spooling check d. range check ANS: D 15. Which input control check would detect a payment made to a nonexistent vendor? a. missing data check b. numeric/alphabetic check c. range check d. validity check ANS: D 16. The employee entered "40" in the "hours worked per day" field. Which check would detect this unintentional error? a. numeric/alphabetic data check b. sign check c. limit check d. missing data check ANS: C 17. An inventory record indicates that 12 items of a specific product are on hand. A customer purchased two of the items, but when recording the order, the data entry clerk mistakenly entered 20 items sold. Which check could detect this error? a. numeric/alphabetic data checks b. limit check c. range check d. reasonableness check ANS: B 18. Which check is not an input control? a. reasonableness check b. validity check. c. spooling check d. missing data check ANS: C 19. A computer operator was in a hurry and accidentally used the wrong master file to process a transaction file. As a result, the accounts receivable master file was erased. Which control would prevent this from happening? a. header label check b. expiration date check c. version check d. validity check ANS: A 20. Run-to-run control totals can be used for all of the following except a. to ensure that all data input is validated b. to ensure that only transactions of a similar type are being processed c. to ensure the records are in sequence and are not missing d. to ensure that no transaction is omitted ANS: A 21. Methods used to maintain an audit trail in a computerized environment include all of the following except a. transaction logs b. Transaction Listings. c. data encryption d. log of automatic transactions ANS: C 22. Risk exposures associated with creating an output file as an intermediate step in the printing process (spooling) include all of the following actions by a computer criminal except a. gaining access to the output file and changing critical data values b. using a remote printer and incurring operating inefficiencies c. making a copy of the output file and using the copy to produce illegal output reports d. printing an extra hardcopy of the output file ANS: B 23. Which statement is not correct? a. only successful transactions are recorded on a transaction log b. unsuccessful transactions are recorded in an error file c. a transaction log is a temporary file d. a hardcopy transaction listing is provided to users ANS: C 24. Input controls include all of the following except a. check digits b. Limit check. c. spooling check d. missing data check ANS: C 25. Which of the following is an example of an input error correction technique? a. immediate correction b. rejection of batch c. creation of error file d. all are examples of input error correction techniques ANS: D 26. Which test of controls will provide evidence that the system as originally implemented was free from material errors and free from fraud? Review of the documentation indicates that a. a cost-benefit analysis was conducted b. the detailed design was an appropriate solution to the user's problem c. tests were conducted at the individual module and total system levels prior to implementation d. problems detected during the conversion period were corrected in the maintenance phase ANS: C 27. Which statement is not true? a. An audit objective for systems maintenance is to detect unauthorized access to application databases. b. An audit objective for systems maintenance is to ensure that applications are free from errors. c. An audit objective for systems maintenance is to verify that user requests for maintenance reconcile to program version numbers. d. An audit objective for systems maintenance is to ensure that the production libraries are protected from unauthorized access. ANS: A 28. When the auditor reconciles the program version numbers, which audit objective is being tested? a. protect applications from unauthorized changes b. ensure applications are free from error c. protect production libraries from unauthorized access d. ensure incompatible functions have been identified and segregated ANS: A 29. When auditors do not rely on a detailed knowledge of the application's internal logic, they are performing a. black box tests of program controls b. white box tests of program controls c. substantive testing d. intuitive testing ANS: A 30. All of the following concepts are associated with the black box approach to auditing computer applications except a. the application need not be removed from service and tested directly b. auditors do not rely on a detailed knowledge of the application's internal logic c. the auditor reconciles previously produced output results with production input transactions d. this approach is used for complex transactions that receive input from many sources ANS: D 31. Which test is not an example of a white box test? a. determining the fair value of inventory b. ensuring that passwords are valid c. verifying that all pay rates are within a specified range d. reconciling control totals ANS: A 32. When analyzing the results of the test data method, the auditor would spend the least amount of time reviewing a. the test transactions b. error reports c. updated master files d. output reports ANS: A 33. All of the following are advantages of the test data technique except a. auditors need minimal computer expertise to use this method b. this method causes minimal disruption to the firm's operations c. the test data is easily compiled d. the auditor obtains explicit evidence concerning application functions ANS: C 34. All of the following are disadvantages of the test data technique except a. the test data technique requires extensive computer expertise on the part of the auditor b. the auditor cannot be sure that the application being tested is a copy of the current application used by computer services personnel c. the auditor cannot be sure that the application being tested is the same application used throughout the entire year d. preparation of the test data is time-consuming ANS: A 35. All of the following statements are true about the integrated test facility (ITF) except a. production reports are affected by ITF transactions b. ITF databases contain "dummy" records integrated with legitimate records c. ITF permits ongoing application auditing d. ITF does not disrupt operations or require the intervention of computer services personnel ANS: A 36. Which statement is not true? Embedded audit modules a. can be turned on and off by the auditor. b. reduce operating efficiency. c. may lose their viability in an environment where programs are modified frequently. d. identify transactions to be analyzed using white box tests. ANS: D 37. Generalized audit software packages perform all of the following tasks except a. recalculate data fields b. compare files and identify differences c. stratify statistical samples d. analyze results and form opinions ANS: D SHORT ANSWER 1. Contrast the source program library (SPL) management system to the database management system (DBMS). ANS: The SPL software manages program files and the DBMS manages data files. 2. Describe two methods used to control the source program library. ANS: passwords, separation of development programs from maintenance programs, program management reports, program version numbers, controlling maintenance commands 3. New system development activity controls must focus on the authorization, development, and implementation of new systems and its maintenance. Discuss at least five control activities that are found in an effective system development life cycle. ANS: System authorization activities assure that all systems are properly authorized to ensure their economic justification and feasibility. User specification activities should not be stifled by technical issues. Users can provide written description of the logical needs that must be satisfied by the system. Technical design activities must lead to specifications that meet user needs. Documentation is both a control and evidence of control. Internal audit involvement should occur throughout the process to assure that the system will serve user needs. Program testing is to verify that data is processed as intended. 4. What are the three broad categories of application controls? ANS: input, processing, and output controls 5. How does privacy relate to output control? ANS: If the privacy of certain types of output, e.g., sensitive information about clients or customers, a firm could be legally exposed. 6. What are the three categories of processing control? ANS: Batch controls, run-to-run controls, and audit trail controls. 7. What control issue is related to reentering corrected error records into a batch processing system? What are the two methods for doing this? ANS: Errors detected during processing require careful handling, since these records may already be partially processed. Simply resubmitting the corrected records at the data input stage may result in processing portions of these transactions twice. Two methods are: (1) reverse the effects of the partially processed transactions and resubmit the corrected records to the data input stage. The second method is to reinsert corrected records into the processing stage at which the error was detected. 8. Output controls ensure that output is not lost, misdirected, or corrupted and that privacy is not violated. What are some output exposures or situations where output is at risk? ANS: output spooling, delayed printing, waste, report distribution 9. Input controls are programmed procedures (routines) that perform tests on transaction data to ensure they are free from errors. Name four input controls and describe what they test ANS: 1. numeric-alphabetic checks look for the correct type of character content in a field, numbers or letters; 2. limit checks verify that values are within preset limits; 3. range checks verify the values fall with in an acceptable range 4. reasonableness check determines if a value in one field, which has already passed a limit check and a range check, is reasonable when considered along with data in other fields of the record. 10. A __________________________ fraud affects a large number of victims but the harm to each appears to be very small. ANS: salami 11. Describe a test of controls that would provide evidence that only authorized program maintenance is occurring. ANS: reconcile program version numbers, confirm maintenance authorizations 12. Auditors do not rely on detailed knowledge of the application's internal logic when they use the __________________________ approach to auditing computer applications. ANS: black box or auditing around the computer 13. Describe parallel simulation. ANS: The auditor writes a program that simulates the application under review. The simulation is used to reprocess production transactions that were previously processed by the production application. The results of the simulation are compared to the results of the original production run. 14. What is meant by auditing around the computer versus auditing through the computer? Why is this so important? ANS: Auditing around the computer involves black box testing in which the auditors do not rely on a detailed knowledge of the application's internal logic. Input is reconciled with corresponding output. Auditing through the computer involves obtaining an in-depth understanding of the internal logic of the computer application. As transactions become increasingly automated, the inputs and outputs may become decreasingly visible. Thus, the importance of understanding the programming components of the system is crucial. 15. What is an embedded audit module? ANS: EAM techniques use one or more specially programmed modules embedded in a host application to select and record predetermined types of transactions for subsequent analysis. This method allows material transactions to be captured throughout the audit period. The auditor's substantive testing task is thus made easier since they do not have to identify significant transactions for substantive testing. 16. What are the audit’s objectives relating to systems development? ANS: The auditor’s objectives are to ensure that (1) systems development activities are applied consistently and in accordance with management’s policies to all systems development projects; (2) the system as originally implemented was free from material errors and fraud; (3) the system was judged necessary and justified at various checkpoints throughout the SDLC; and (4) system documentation is sufficiently accurate and complete to facilitate audit and maintenance activities. ESSAY 1. Outline the six controllable activities that relate to new systems development ANS: Systems Authorization Activities: All systems should be properly authorized to ensure their economic justification and feasibility. This requires a formal environment in which users submit requests to systems professionals in written form. User Specification Activities: Users need to be actively involved in the systems development process. Users should create a detailed written description of their needs. It should describe the user’s view of the problem, not that of the systems professionals. Technical Design Activities: The technical design activities translate user specifications into a set of detailed technical specifications for a system that meets the user’s needs. The scope of these activities includes systems analysis, feasibility analysis, and detailed systems design. Internal Audit Participation: To meet the governance-related expectations of management under SOX, an organization’s internal audit department needs to be independent, objective, and technically qualified. As such, the internal auditor can play an important role in the control of systems development activities. Program Testing: All program modules must be thoroughly tested before they are implemented. This involves creating hypothetical master files and transactions files that are processed by the modules being tested. The results of the tests are then compared against predetermined results to identify programming and logic errors. User Test and Acceptance Procedures: Prior to system implementation, the individual modules of the system need to be formally and rigorously tested as a whole. The test team should comprise of user personnel, systems professionals, and internal auditors. The details of the tests performed and their results need to be formally documented and analyzed. Once the test team is satisfied that the system meets its stated requirements, the system can be transferred to the user. 2. Explain the three methods used to correct errors in data entry. ANS: Immediate Correction. In the direct data validation approach, error detection and correction take place during data entry. When an error or illogical relationship is entered, the system should halt the data entry procedure until the error is corrected. Creation of an Error File. In the delayed data validation approach, errors are flagged and placed in an error file. Records with errors will not be processed until the error is investigated and corrected. Rejection of the Entire Batch. Some errors are associated with the entire batch and are not attributable to individual records. An example of this is a control total that does not balance. The entire batch is placed in the error file and will be reprocessed when the error is corrected. 3. The presence of an audit trail is critical to the integrity of the accounting information system. Discuss three of the techniques used to preserve the audit trail. ANS: Transaction logs list all transactions successfully processed by the system and serve as journals, permanent records. Transactions that were not processed successfully should be recorded in an error file. After processing transactions, a paper transaction listing should be produced and used by appropriate users to reconcile input. Logs and listings of automatic transactions should be produced for transactions received or initiated internally by the system. Error listing should document all errors and be sent to appropriate users to support error correction. 4. Define each of the following input controls and give an example of how they may be used: a. Missing data check b. Numeric/alphabetic data check c. Limit check d. Range check e. Reasonableness check f. Validity check ANS: Missing data check. Some programming languages are restrictive as to the justification (right or left) of data within the field. If data are not properly justified or if a character is missing (has been replaced with a blank), the value in the field will be improperly processed. For example, the presence of blanks in a numeric data field may cause a system failure. When the control routine detects a blank where it expects to see a data value, the error is flagged. Numeric-alphabetic check. This control identifies when data in a particular field are in the wrong form. For example, a customer’s account balance should not contain alphabetic data and the presence of it will cause a data processing error. Therefore, if alphabetic data are detected, the error record flag is set. Limit check. Limit checks are used to identify field values that exceed an authorized limit. For example, assume the firm’s policy is that no employee works more than 44 hours per week. The payroll system input control program can test the hours-worked field in the weekly payroll records for values greater than 44. Range check. Many times data have upper and lower limits to their acceptable values. For example, if the range of pay rates for hourly employees in a firm is between 8 and 20 dollars, this control can examine the pay rate field of all payroll records to ensure that they fall within this range. Reasonableness check. The test determines if a value in one field, which has already passed a limit check and a range check, is reasonable when considered along with data in other fields of the record. For example, assume that an employee’s pay rate of 18 dollars per hour falls within an acceptable range. This rate is excessive, however, when compared to the employee’s job skill code of 693; employees in this skill class should not earn more than 12 dollars per hour. Validity check. A validity check compares actual field values against known acceptable values. For example, this control may be used to verify such things as valid vendor codes, state abbreviations, or employee job skill codes. If the value in the field does not match one of the acceptable values, the record is flagged as an error. 5. After data is entered into the system, it is processed. Processing control exists to make sure that the correct things happen during processing. Discuss processing controls. ANS: Processing controls take three forms–batch controls, run-to-run controls, and audit trail controls. Batch controls are used to manage the flow of high volumes of transactions through batch processing systems. The objective of batch control is to reconcile output produced by the system with the input originally entered into the system. This provides assurance that: _ All records in the batch are processed. _ No records are processed more than once. _ An audit trail of transactions is created from input through processing to the output stage of the system. Run-to-run controls use batch figures and new balances to monitor the batch as it goes through the system–i.e. from run-to-run. These are to assure that no transactions are lost and that all are processed completely. Audit trail controls are designed to document the movement of transactions through the system. The most common techniques include the use of transaction logs and transaction listings, unique transaction identifiers, logs and listings of automatic transactions, and error listings. 6. If input and processing controls are adequate, why are output controls needed? ANS: Output controls are designed to ensure that system output is not lost, misdirected, or corrupted and that privacy is not violated. Great risk exists if checks are misdirected, lost, or stolen. Certain types of data must be kept private–trade secrets, patents pending, customer records, etc. 7. Describe and contrast the test data method with the integrated test facility. ANS: In the test data method, a specially prepared set of input data is processed; the results of the test are compared to predetermined expectations. To use the test data method, a copy of the current version of the application must be obtained. The auditor will review printed reports, transaction listings, error reports, and master files to evaluate application logic and control effectiveness. The test data approach results in minimal disruption to the organization's operations and requires little computer expertise on the part of auditors. The integrated test facility (ITF) is an automated approach that permits auditors to test an application's logic and controls during its normal operation. ITF databases contain test records integrated with legitimate records. During normal operations, test transactions are entered into the stream of regular production transactions and are processed against the test records. The ITF transactions are not included with the production reports but are reported separately to the auditor for evaluation. The auditor compares ITF results against expected results. In contrast to the test data approach, the ITF technique promotes ongoing application auditing and does not interfere with the normal work of computer services employees. In the test data approach, there is a risk that the auditor might perform the tests on a version of the application other than the production version; this cannot happen in the ITF approach. Both versions are relatively costly to implement. The major risk with the ITF approach is that ITF data could become combined with live data and the reports would be misstated; this cannot happen in the test data approach. 8. Contrast Embedded Audit Modules with Generalized Audit Software. ANS: Both techniques permit auditors to access, organize, and select data in support of the substantive phase of the audit. The Embedded Audit Module (EAM) technique embeds special audit modules into applications. The EAM captures specific transactions for auditor review. EAMs reduce operational efficiency and are not appropriate for environments with a high level of program maintenance. Generalized Audit Software (GAS) permits auditors to electronically access audit files and to perform a variety of audit procedures. For example the GAS can recalculate, stratify, compare, format, and print the contents of files. The EAM is an internal program that is designed and programmed into the application. The GAS is an external package that does not affect operational efficiency of the program. GASs are easy to use, require little IT background on the part of the user, are hardware independent, can be used without the assistance of computer service employees, and are not application-specific. On the other hand, EAMs are programmed into a specific application by computer service professionals. 9. What is the purpose of the auditor's review of SDLC documentation? ANS: In reviewing the SDLC documentation, the auditor seeks to determine that completed projects now in use reflect compliance with SDLC policies including: proper authorization of the project by users and computer service management, a preliminary feasibility study showed that the project had merit, that a detailed analysis of user needs was conducted, that a cost-benefit analysis was performed, that the project can be demonstrated to solve the users' problem, and that the system was thoroughly tested. 10. Microcomputers have traditionally been difficult to control, leaving auditors with special problems in verifying physical controls. Discuss what an auditor's objectives might be in testing microcomputer controls. ANS: The auditor must investigate several things: 1) that adequate supervision and operating procedures exist to compensate for the lack of segregation of duties that occur when users are functioning also as programmers and operators; 2) that access to hardware, data and software is limited to authorized personnel; 3) that backup procedures are in place and implemented to prevent data and program loss; and 4) that procedures for systems selection and acquisition assure high quality, error free, applications. This is far from an ideal situation. 11. Contrast the "black box" approach to IT auditing and the "white box" approach. Which is preferred? ANS: The black box approach is not concerned with the application's internal workings. The auditor examines documentation of the system, interviews personnel, and bases the evaluation on the logical consistency between input and output. This method is often referred to as "auditing-around-the-computer" because there is no examination of data as it is processed. The white box approach, also called "auditing-through-the-computer," relies on knowledge of the internal workings of the systems and actually tests the application in action with test data having known results. Several white box techniques are available. These include the test data method, base case evaluation, tracing, the integrated test facility, and parallel simulation. This method makes the computer a tool of the audit as well as its target.