Dumpster Diving: Physical Security & Information Protection
advertisement

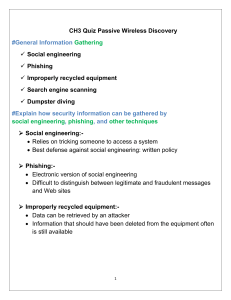
"Dumpster diving" is a form of physical social engineering where attackers sift through an organization's trash or discarded materials to gather sensitive information. While it may seem like a low-tech and simple process, dumpster diving can be highly effective for several reasons: Lack of Digital Security: In an age where cybersecurity measures are becoming more robust, physical security measures may not receive the same level of attention. Organizations might invest heavily in firewalls, encryption, and other digital security tools, but overlook the importance of securing physical documents and waste disposal. Rich Source of Information: Physical documents can contain a wealth of valuable information, such as printed emails, memos, invoices, customer records, passwords on sticky notes, and other confidential data. Attackers can piece together this information to gain insights into the organization's operations, internal structure, and potential weaknesses. Harder to Detect: Unlike cyber attacks, dumpster diving leaves little to no digital footprint, making it harder for organizations to detect or trace back to the attacker. It can be conducted covertly, with minimal risk of raising suspicion. Bypassing Digital Defenses: Even with strong digital defenses in place, some information may still be communicated or stored on physical documents. Dumpster diving allows attackers to bypass digital security measures and directly access this information. Preying on Human Error: Human error is a significant factor in security breaches. Employees might mistakenly discard sensitive documents, forget to shred them, or dispose of them improperly, providing an opportunity for attackers to exploit. Low Cost and Effort: Dumpster diving requires minimal resources and can be carried out by individuals with little technical expertise. This makes it an attractive method for attackers looking for quick and easy ways to gather information. Complementing Other Techniques: Dumpster diving can complement other social engineering techniques, such as impersonation, as attackers can use the information obtained from trash to make their deception more convincing. Targeting Specific Organizations: Attackers can target specific organizations or individuals by tailoring their dumpster diving efforts to suit their objectives. For example, they might focus on organizations known for handling sensitive data or those with weak physical security practices. To protect against dumpster diving and other physical social engineering attacks, organizations should: Educate employees about the importance of secure document disposal and the risks associated with improper handling of sensitive information. Implement strict physical security measures, such as using locked shredding bins for confidential documents and limiting access to sensitive areas. Establish clear policies for handling and disposing of sensitive information and ensure employees are trained to follow these policies. Encourage a culture of security awareness, where employees are vigilant about potential security risks, both digital and physical. By addressing the potential vulnerabilities associated with dumpster diving and other physical social engineering techniques, organizations can strengthen their overall security posture and protect sensitive information from falling into the wrong hands.