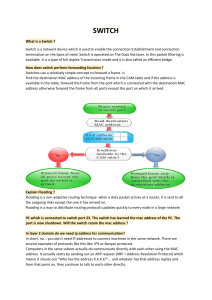
Network topologies: Point to point: - A connection between two computers, networks or other devices. If the connection fails the communication is disrupted Star: - Devices are connected to a central intermediate device. Easy to setup and maintain but it highly scalable Mesh: - In mesh topology, each end device can have multiple connections to other end devices. This configuration is highly resilient due to its allowance of multiples connection but is expensive Hybrid: - A combination of the other topologies 3 tier architecture: - Consists of 3 layers that provide isolation between devices, more security options and resilience. The separated layers are: Core: Routing layer connecting to servers and the internet Distribution: Separation between core and access layers and boundary control Access: Communication between and devices Collapsed architecture: - Similar to 3 tier, but has a different number of layers - Core and distribution layers are collapsed together to form a single layer - Advantages of the 3 tier architecture but a smaller network scale - - A mac address is the unique identity of a computer within a network while IP addresses are used to identify machines operating in different networks MAC: Media access control A MAC address is a unique hardware identifier attached to each network card A MAC address includes 2 parts: - A first three nodes represent the manufacturer’s identifier - The last three nodes represent a serial identifier - Can be written in different ways IPv4 consists of four octets IPv6 consists of six hexadecimal octets Subnet mask for class A,B and C: - /24 is class C, subnet mask is 255.255.255.0 - /16 is class B, subnet mask is 255.255.0.0 - /8 is Class A, subnet mask is 255.0.0.0 - The first IP address of each subnet is the network address and can’t be used for host or devices The last address of each subnet is the broadcast address Protocols - Protocols can be considered language of data transfer, to communicate two or more computers need to have the same protocol - Protocols are predefined sets of rules describing how something should work or behave - Protocols help maintain order among different technologies Types of protocols: - IP - DNS - DHCP - HTTP (Hypertext transfer protocol) - HTTPS (Hypertext transfer protocol secure) Wireless LAN components - AP (Access point): The component that allows end devices to connect to a network wirelessly - Wireless NIC adapter: Sends and receives information to the computer - IP that starts with 169.254 means you didn’t reach your dhcp server Common Network Protocols - DHCP - SMTP - SSH - ICMP - OSI is an educational model while TCP/IP is used as a practical model - TCP/IP and DOD are interchangeable OSI: Open system Interconnection - Defines a networking framework to implement protocols in layers - Was developed by the International Organization for Standardization (ISO) in 1974 - Divided into 7 layers: Application, presentation, session, transport, network, datalink, physical. Goes from the bottom up. - Upper layers - Application - Presentation - Session - Routers are layer 3 Switches are layer 2 Hubs are layer 1 Firewalls can be from layer 3 to layer 7 Network layer is the transport - Layers in the TCP/IP: Application, transport, internet, network access Application layer in TCP/IP is the first top 3 layers in OSI Transport layer is layer 3 in TCP/IP The transport layer is responsible for setting the port number and the communication type (TCP or UDP) UDP53 is port DNS TCP22 is port SSH - Half Duplex - Only one party can send or receive data at a moment, like a walkie talkie Full Duplex - Both parties can send and receive data at the same time, like cell phones - - - To connect network devices such as computers and switches, you can use media components such as an ethernet cable with an RJ-45 connector To transmit information over a distance that is greater 300m via a single cable without data loss you must use an optic fiber cable When connecting two networks of the same type you must use a crossover cable. This connection prevents collision between the transmitting and receiving points of the connected devices Which Wi-Fi standard used by AP devices supports both 2.4 GHz and 5 GHz wireless frequencies? 802.11n TCP is a 4 layer protocol used to establish a Telnet connection The TCP protocol uses the three way handshake process to establish a trusted connection between a server and a client Registered ports: Describes all ports between 1024 and 49151 The two common states of a network port are listening and established. Ports in both states can be identified when executing netstat -atb on windows computer - Switches are layer 2 by default - To see the MAC address table use the command “show mac address-table” - Fa = fast ethernet Switches have different methods of receiving and transmitting frames on the LAN - Store and forward: Buffers the entire frame upon receipt which enables the switch to support various port speeds. Provides error checking - Cut through switching: Faster than store and forward, only the first 6 bytes of the incoming frame are buffered. The switch forwards the frame immediately even before the frame is received and no error checking is done - Fragment Free switching: Buffers the first 64 bytes of the frame, including the MAC address data and the frame’s payload. - IOS uses a command line interface (CLI) to enable administrators and technicians to interact with the system Terminal software: - PuTTY - Tera Term - SecureCRT Cisco packet tracer allows a user to map a network Enables the testing of network configurations, trains users to work with network configuration - - Access Methods - Out of band: This method uses a dedicated management console cable that must be physically connected to the device Out of band management requires two items: 1. PC with terminal software 2. Console Cable - In band: Uses management protocols, such as SSH or Telnet which assess the devices remotely over the network IOS Modes - User EXEC Mode: Low level capabilities but is useful for basic operations. - Privileged EXEC Mode: Large number of monitoring commands and device configuration - Global configuration mode: The only mode that allows admins to change device configuration. Only accessible from the privileged EXEC mode. - Interface configuration mode: Allows you to change specific parameters within a switch or router - Enable command moves the user from user mode to privileged mode Cisco Device Components Volatile memory: When computer is rebooted, this memory is wiped out - RAM: Volatile memory that stores the system config - ROM: Non volatile memory responsible for the power on self test process and bootstrap which is the initial program responsible for booting the IOS - FLASH: Non volatile memory that stores the OS itself - NVRAM: Non volatile memory that stores the startup config file - TFTP: Trivial File Transfer Protocol, a simple file transfer protocol that allows clients to retrieve files from a remote host - FTP has username and password and TFTP doesn’t - ROMmon: Read only memory monitor, the purpose of this is to change the router’s behavior: - Determine how the router will boot - Apply option while booting - Set the console speed and band rate for terminal emulation session - MAC spoofing: When attackers change their physical PC address to conceal their true identity and be someone else - CAM table overflow: An attack that targets a switch’s MAC table. The goal is to flood the table with fake addresses which causes the switch to initiate fallback mode and act as a hub - Port security feature is used to restrict the number of MAC addresses that each board can learn - Port security feature has 3 protection modes: - Shutdown - Restrict - Protect - MAC address learning can be done in two ways, manual or sticky - Manual: Requires static configuration of each allowed MAC address and its assignment to an interface. Most secure method but is time consuming - Sticky: Allowed MAC addresses are learned dynamically and limited to the max number configured for the interface - Max allowed MAC addresses: Number can be changed - Err-Disabled: When a switch port is in this more, the port may have been disabled automatically by the switch OS due to a port security shutdown mode violation - Common triggers for Err-Disabled: - Duplex mismatch: This state occurs when two parties set for point to point communication are configured to use different duplex modes - Bad NIC: A faulty network interface card (NIC) - Broadcast storms: When a broadcast volume is too large for processing, the switches may become overwhelmed and trigger Err-Disabled mode Remote Access - Two common remote access protocols are used in switches: SSH and Telnet - - - SSH encrypts all data transferred between the user and end device, SSH uses RSA encryption and operates on TCP port 22 Telnet, usernames and passwords are sent in plain text on TCP port 23 RSA Encryption: Has two keys, public and private. Public is shared with everyone and the private is given only to specific persons. RSA ensures the confidentiality in the CIA triad Virtual Teletype (VTY): A CLI in network devices used to create remote access connections. VTY is virtual and doesn’t require hardware. Switches have 16 VTY lines (0-15) and routers have 5 VTY lines (0-4) Router is layer 3, switch is layer 2 Number systems: - Decimal: The most common numbering system goes from 0-9 - Known as base-10 numeral system - Binary: Uses 0 and 1 - Known as base-2 numeral system - Hexadecimal: Consists of 16 characters, uses number 0-9 and letter A-F - Known as base-16 numeral system - - - - Internet protocol (IP): A numerical label assigned to devices connected to a network used for host identification and communication IPv4 addresses consist of 32 bits and are divided into 4 octets each containing 8 bits IPv4 address consists of 2 parts, network and host defined by the subnet mask IPv4 communication types Unicast: One on one communication; A packet is sent directly from one device on the network to another device on the network. A single source communicates with a single destination Multicast: A single source communicates with multiple destinations Broadcast: When a packet is sent from one device on the network to all other devices on the network with the use of a generic broadcast address (255.255.255.255 or FF:FF:FF:FF:FF:FF) IPv4 link-local also known as an APIPA address: Used if the DHCP is not available or an IP is not statically configured, the OS will randomly generate a link local address Private IPs are non-unique addresses that can belong to one of three IP address ranges. They are used to create networks that do not communicate over the internet Public IPs are used for communication over the internet. These addresses must be unique, require a fee and be purchased from service providers - Private IP ranges: - IPv6 device communication types: - Unicast: 3 types of unicast: - Global Unicast: IPv6 global unicast addresses are similar to IPv4 public addresses, they are unique and can be routed via the internet -Link-Local: Addresses that enable communication between devices in the same local link (LAN) -Unique-Local: Similar to IPv4 private addresses with minor differences - Multicast: Addresses used to send IPv6 packets from a single host to multiple destinations Anycast: Refers to IPv6 unicast addresses that can be assigned to multiple devices IPv4 and IPv6 can coexist using protocols and tools created by IEFT which are known for dual stack, tunneling and translation Dual stack: Means that a devices runs both IPv4 and IPv6 protocols simultaneously, allowing both IP versions to coexist Tunneling: Used when IPv6 addresses are to be sent over IPv6 networks or vice versa. In this method the IPv6 is encapsulated within an IPv4 packet Translation: Allows IPv6 to communicated IPv5 enabled devices using techniques similar to those utilized by NAT IPv6 is 128 bits