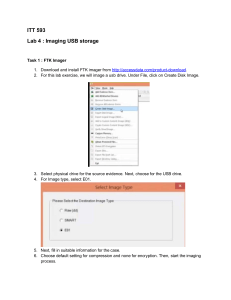
Digital Forensics FTK Introduction to FTK using the Case of George and Martha In this Lab activity, you will use AccessData FTK to extract and analysis the image of a image-bit-stream file. Complete the following steps to acquire the image file and start a documented investigation of the image contents. 1. The image of the disk has been created already as ftk-demo1-image.1 2. Copy this file 3. Verify the copy by using the checksum verification value in the text file 4. Start FTK 5. You will be presented with the following warning messages for the evaluation version of FTK. Click ok button for each message. Figure 1: Warning message on KFF Hash Library Figure 2: Warning message for missing dongle Page 1 of 18 Digital Forensics FTK Figure 3: Warning message on limit of file items allowed 6. Now we will create a new case by clicking the Ok button in the following dialog window: Figure 4: Start-up Dialog Window Enter the following information for the new case: Page 2 of 18 Digital Forensics FTK Figure 5: New Case Dialog Information 7. For the next few windows, just press the Next button. Have a read of the information but do not change any options. A screen captured copy of each window is presented here for your convenience. Page 3 of 18 Digital Forensics Figure 6: Case Log Options – Default options 7.1 What is the format is the ftp.log file 7.2 What is a log file used for? 7.3 What kind of events can be recorded in a log file? 7.4 How can you add comments to a log file? Page 4 of 18 FTK Digital Forensics Figure 7: Processes options – Default settings 7.5 How many bits in a MD5 and SH1 key? 7.6 What is the function of the KFF utility? 7.7 How can we check if a file is compressed? 7.8 Why does data need to be indexed? 7.9 What is a thumbnail? 7.10 What other types of databases can be used to store lists of files? 7.11 What is data carving? Page 5 of 18 FTK Digital Forensics FTK Figure 8: The Refine Case – Default dialog box 7.12 What are the options for excluding certain kinds of data? 7.13 What is difference Slack Space and Free Space? 7.14 What utility compares file hashes against a reference database to eliminate known files? 7.15 What is difference between File Status and File Type? Page 6 of 18 Digital Forensics FTK 8. We will now import the image file contents by selecting the Add Evidence button and selecting Acquire Image Drive option in dialog box. Figure 9: Adding evidence dialog box 9. Now select the image file by navigating to the correct folder on your pen drive and selecting the ftk-demo1-image.1 file. The other file in the folder is a text file containing the correct MD5 checksum value. Check if image file MD5 checksums matches the generated MD5 of your copied file. MD5 value of copied file: MD5 value in text file: Page 7 of 18 Digital Forensics Figure 10: Selecting the file to analysis Figure 11: Selecting the time zone Page 8 of 18 FTK Digital Forensics FTK 10. Once the file is selected, the system will ask for the location of any files or reports to be stored. Use the default folder where the image is stored and press the Finish button. FTK will perform several steps of cataloguing data and indexing of data in the image file. The cataloguing process organises and lists each file in its own section for any follow up analysis. The indexing feature creates a database of every word in the image with its exact location, providing instant lookup for any keywords of interest to the investigation. Figure 12: Location of created files and reports for this investigation Page 9 of 18 Digital Forensics FTK Figure 13: Snapshot of Adding evidence files to system from image 11. When the cataloguing and indexing is finished, FTK opens an Overview Tab option and displays several other tab options, like Explore, Graphics, etc. Figure 14: FTK Overview Tab Display Page 10 of 18 Digital Forensics FTK Figure 15: FTK Overview Tab Display (enlarged) 12. Click on the Explore tab option. In the pane at the upper left (the tree view) click to expand the folders tree and then select the List all descendants option by clicking the box (see figure 16) When you are navigating between the Explorer, Graphic and E-Mail tabs in the FTK window, only the folder’s contents are displayed. If you click a folder in the upper-left pane, the folder’s contents are displayed in the lower pane. The List all descendants option enables you to view all files, regardless of which folder they are in and you can scroll through all files at once. Page 11 of 18 Digital Forensics FTK Figure 16 Viewing all files 13. Navigate through each file in the lower pane by clicking the file name one at a time. The upper-right pane displays any text data contained in the files. Read through the text that is displayed so see what information is contained on the disk. Figure 17: Looking at file contents Page 12 of 18 Digital Forensics FTK 14. Non-text based files will appear as Hex (see below). Figure 18: Viewing a graphics file 15. When you have located a file containing information you think is important, click the check box to the left of the file name and continue searching and selecting additional files of interest as you find them. Figure 19: Marking files for further analysis Page 13 of 18 Digital Forensics FTK 16. After you have selected all the files of interest, create a Bookmark by selecting the tools option in the menu. In the Create New Bookmark dialog box, type a bookmark name and any comments, then click the All Checked Items button, the Include in Report check box and the Export Files check box, (see figure 18). The purpose of the bookmark in FTK is to provide a mechanism for inclusion of items in a report. Figure 20: Creating a bookmark 17. Once the files have been bookmarked, select the Report Wizard in the File menu. In the Case Information dialog box enter the relevant data (see figure 20). Make a copy of the Case Log. What information does it give you? Page 14 of 18 Digital Forensics FTK Figure 21: Case Information in Report Wizard 18. Several windows will appear, just click Next until you reach the Finish button. This will complete the process of extracting data of interest to the investigation. 19. The Report Wizard will prompt you asking if you would like to view the report. This will allow you to see the report in a web browser window. Click the various options to view the report contents. Page 15 of 18 Digital Forensics Figure 22: Report Location Page 16 of 18 FTK Digital Forensics FTK Figure 23: The report displayed using a web browser 20. Now that you know how to use the FTK tool to analyse the disk image, investigate the contents of the files and build up a picture of the evidence. The case report goes something like this. The manager of a small business, Steve Billings has concerns with two of his employees. Two weeks ago, Martha Heiser, the shipping clerk began a one-week emergency leave from the company without informing anyone where she was going or how to contact her. She has not returned from her leave. Also, a supervisor in the Accounts Payable Department, George Montgomery has been missing from work for the last week and no one knows why. Steve searches Martha’s desk and notices travel brochures for foreign tours. When he searches George’s desk, he sees paper notes about a Switz supplier that Steve once used and he found a floppy disk with the former supplier’s name on the label. Steve asks you to examine the disk and see if it contains any information that may explain what has happened. Page 17 of 18 Digital Forensics You need to provide a solution: 1. provide all the answers raised during various steps. 2. What is your analysis or final findings for this case. Page 18 of 18 FTK