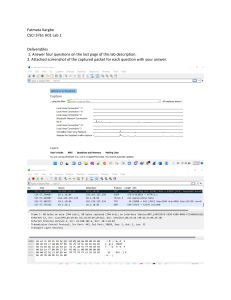
ENGI 53809 - Project Sheridan College Institute of Technology and Advanced Learning Faculty of Applied Science and Technology Course Project Requirements Wireshark is an open-source network protocol analysis software program, widely considered the industry standard. A global organization of network specialists and software developers supports Wireshark and continues to make updates for new network technologies and encryption methods. 1. Using the Wireshark protocol analyser, capture all packets generated in response to your web request to www.sheridancollege.ca and all packet to an internet request using one of the apps you are using in your PC (e.g Outlook, WhatsApp, search app, MS Teams or any other app that accesses the internet directly, not web-based) In your report document, paste a screenshot of Wireshark and the first 10 packets of each of the two internet requests above (web request to Sheridan and another internet request), then research and explain (to your best knowledge) the contents of those 20 packets. Do you find any alien packets not related to these two requests in the 10 packets you grabbed about each? If so, what do you think that packet is about? 2. Run Wireshark and start a new capture (capturing network packets). Do your normal computing tasks for one hour (studying, messaging, checking email, searching the web... etc.) then analyse the captured traffic. List the protocols used in your capture, then research the internet about the types of services and apps that are using each of these protocols. Add the list of protocols to your report along with the list of possible services/apps using each of the protocols. Can you identify what exact services/apps accessed the internet during this hour? If so, add that list to your solution 3. Research and report about: How can a network administrator use Wireshark to troubleshoot network problems? 4. Research and report about: How can cybersecurity specialists use Wireshark to examine security issues across a network? Hints and resources: • You may use more than one NIC (e.g. WiFi and Ethernet) in your capture • Have a look at “Wireshark Tutorial for Beginners” at https://www.youtube.com/watch?v=TkCSr30UojM • Tutorial: How to use Wireshark https://www.varonis.com/blog/how-to-use-wireshark • Be free to do further research about internet traffic and report on your findings. SUBMISSION: Compile your report in a word document following APA style 7th edition (https://extras.apa.org/apastyle/basics-7e), save the document as PDF and submit it by the due date ENGI 53809 - Project RUBRIC Unsatisfactory (040%) Requirements • are met 50% Completed less than 50% of the requirements Satisfactory (40-60%) Good (80%) Excellent (100%) • • • Requirements were met and exceeded Completed 50-60% of the requirements Completed 70-90% of the requirements Research and solution Standards 30% • No signs of good research were seen in your report • Some signs of • Good research was proper research were done and references seen in your report Clarity and writeup • The report is not clear enough to readers • The report is readable but missing proper formatting OR contains language errors • The report is • The report is readable, the writeup excellent, with clear is good signs of exceptional efforts Delivery • 10% • • Delivered on time, in proper format • Some details can be improved • Completed most of the requirements • Delivered on time 10% Not delivered in correct format Late (subtract 10% per day) • Proper research was done, extensive list of references • Completed between 90-100% of the requirements. • Delivered on time, and in correct format