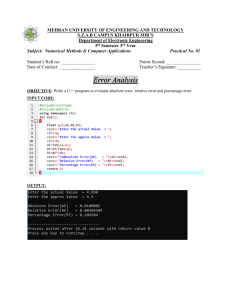
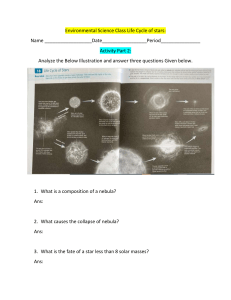
AIS Chapter 1 Multiple-Choice Questions 1. Which of the following is NOT a financial transaction? a. purchase of products b. cash receipts c. update valid vendor file d. sale of inventory 2. The following are subsystems of the Accounting Information System, EXCEPT a. Transaction Processing System. b. Human Resources System. c. General Ledger/Financial Reporting System. d. Management Reporting System. 3. Which of the following is NOT a purpose of the Transaction Processing System? a. managing and reporting on the status of financial investments b. converting economic events into financial transactions c. distributing essential information to operations personnel to support their daily operations d. recording financial transactions in the accounting records 4. The objectives of the data collection activity of the general model for Accounting Information Systems are to collect data that are a. relevant and redundant. b. efficient and objective. c. efficient and redundant. d. efficient and relevant. 5. Which of the following is NOT a characteristic of effective information? a. relevance b. accuracy c. summarization d. precision 6. Which of the following is NOT a database management task? a. retrieval b. storage c. summarization d. deletion 7. When viewed from the highest to most elemental level, the data hierarchy is a. attribute, record, file. b. record, attribute, key. c. file, record, attribute. d. file, record, key. e. key, record, file. 8. Which is NOT an accountant’s primary role in in- formation systems? a. system user b. system auditor c. system designer d. system programmer 9. Which of the following is NOT an objective of all information systems? a. support for the stewardship function of management b. support for management decision making c. support for the day-to-day operations of the firm d. all of the above are objectives 10. Which of the following best describes the activities of the materials management function? a. purchasing, receiving, and inventory control b. receiving, sales, distribution, and purchasing c. receiving, storage, purchasing, and accounts payable d. purchasing, receiving, and storage e. purchasing, storage, and distribution 11. Which of the following best describes the activities of the production function? a. maintenance, inventory control, and production planning b. production planning, quality control, manufacturing, and cost accounting c. quality control, production planning, manufacturing, and payroll d. maintenance, production planning, storage, and quality control e. manufacturing, quality control, and maintenance 12. Which of the following best describes the activities of the accounting function? a. inventory control, accounts payable, fixed assets, and payroll b. fixed assets, accounts payable, cash disbursements, and cost accounting c. purchasing, cash receipts, accounts payable, cash disbursements, and payroll d. inventory control, cash receipts, accounts payable, cash disbursements, and payroll e. inventory control, cost accounting, accounts payable, cash disbursements, and payroll 13. Which statement best describes the issue of distributed data processing (DDP)? a. The centralized and DDP approaches are mutually exclusive; an organization must choose one approach or the other. b. The philosophy and objective of the organization’s management will determine the extent of DDP in the firm. c. In a minimum DDP arrangement, only data input and output are distributed, leaving the tasks of data control, data conversion, database management, and data processing to be centrally managed. d. The greatest disadvantage of a totally distributed environment is that the distributed information processing unit locations are unable to communicate and coordinate their activities. e. Although hardware (such as computers, database storage, and input/output terminals) can be effectively distributed, the systems development and maintenance tasks must remain centralized for better control and efficiency. S—external user: stakeholder a. Internal Revenue Service S b. Inventory control manager c. Board of directors d. Customers e. Lending institutions f. Securities and Exchange Commission g. Stockholders h. Chief executive officer i. Suppliers j. Bondholders S INFORMATION SYSTEM CATEGORIZATION Classify the following items as either: TPS—transaction processing system FRS—financial reporting system MRS—management reporting system a. Variance reports b. Sales order capture c. Balance sheet d. Budgets e. Purchase order preparation f. Tax returns g. Sales summary by product line h. Cash disbursements preparation i. Annual report preparation j. Invoice preparation k. Cost-volume-profit analysis 14. Which of the following is a disadvantage of distributed data processing? a. End-user involvement in systems operation is decreased. b. Disruptions due to mainframe failures are increased. c. The potential for hardware and software incompatibility across the organization is increased. d. The time between project request and completion is increased. e. All of the above are disadvantages. CHAPTER 2 Multiple-Choice Questions 1. Which statement is NOT true? a. Business activities begin with the acquisition of materials, property, and labor in exchange for cash. b. The conversion cycle includes the task of determining raw materials requirements. c. Manufacturing firms have a conversion cycle but retail firms do not. d. A payroll check is an example of a product document of the payroll system. e. A journal voucher is actually a special source document. USERS OF INFORMATION Classify the following users of information as either: I—internal user T—external user: trading partner 2. A documentation tool that depicts the physical flow of information relating to a particular transaction through an organization is a a. system flowchart. b. program flowchart. c. decision table. d. work distribution analysis. e. systems survey. 3. Sequential file processing will not permit a. data to be edited on a separate computer run. b. the use of a database structure. c. data to be edited in an offline mode. d. batch processing to be initiated from a terminal. e. data to be edited on a real-time basis. 4. The production subsystem of the conversion cycle includes all of the following EXCEPT a. determining raw materials requirements. b. make or buy decisions on component parts. c. release of raw materials into production. d. scheduling the goods to be produced. 5. Which of the following files is a temporary file? a. transaction file b. master file c. reference file d. none of the above 6. A documentation tool used to represent the logi- cal elements of a system is a(n) a. programming flowchart. b. entity relationship diagram. c. system flowchart. d. data flow diagram. 7. Which of the following is NOT an advantage of real-time processing files over batch processing? a. shorter transaction processing time b. reduction of inventory stocks c. improved customer service d. all are advantages 8. Which statement is NOT correct? a. Legacy systems may process financially significant transactions. b. Some legacy systems use database technology. c. Mainframes are exclusive to legacy systems, while modern systems use only the client- server model. d. All the above are true. 9. Which statement is NOT correct? a. Indexed random files are dispersed throughout the storage device without regard for physical proximity with related records. b. Indexed random files use disk storage space efficiently. c. Indexed random files are efficient when processing a large portion of a file at one time. d. Indexed random files are easy to maintain in terms of adding records. 10. Which statement is NOT correct? The indexed sequential access method a. is used for very large files that need both direct access and batch processing. b. may use an overflow area for records. c. provides an exact physical address for each record. d. is appropriate for files that require few insertions or deletions. 11. Which statement is true about a hashing structure? a. The same address could be calculated for two records. b. Storage space is used efficiently. c. Records cannot be accessed rapidly. d. A separate index is required. 12. In a hashing structure a. two records can be stored at the same address. b. pointers are used to indicate the location of all records. c. pointers are used to indicate location of a record with the same address as another record. d. all locations on the disk are used for record storage. 13. An advantage of a physical address pointer is that a. it points directly to the actual disk storage location. b. it is easily recovered if it is inadvertently lost. c. it remains unchanged when disks are reorganized. d. all of the above are advantages of the physical address pointer. 14. Which of the following is NOT true of a turnaround document? a. They may reduce the number of errors made by external parties. b. They are commonly used by utility companies (gas, power, water). c. They are documents used by internal parties only. d. They are both input and output documents. 15. Which of the following is NOT a true statement? a. Transactions are recorded on source documents and are posted to journals. b. Transactions are recorded in journals and are posted to ledgers. c. Infrequent transactions are recorded in the general journal. d. Frequent transactions are recorded in special journals. 16. Which of the following is true of the relationship between subsidiary ledgers and general ledger accounts? a. The two contain different and unrelated data. b. All general ledger accounts have subsidiaries. c. The relationship between the two provides an audit trail from the financial statements to the source documents. d. The total of subsidiary ledger accounts usually exceeds the total in the related general ledger account. 17. Real-time systems might be appropriate for all of the following EXCEPT a. airline reservations. b. payroll. c. point-of-sale transactions. d. air traffic control systems. e. all of these applications typically utilize realtime processing. 18. is the system flowchart symbol for: a. on-page connector. b. off-page connector. c. home base. d. manual operation. e. document. 19. A chart of accounts would best be coded using a(n) ______________ coding scheme. a. alphabetic b. mnemonic c. block d. sequential 20. Which of the following statements is NOT true? a. Sorting records that are coded alphabetically tends to be more difficult for users than sorting numeric sequences. b. Mnemonic coding requires the user to memorize codes. c. Sequential codes carry no information content beyond their order in the sequence. d. Mnemonic codes are limited in their ability to represent items within a class. 21. A coding scheme in the form of acronyms and other combinations that convey meaning is a(n) a. sequential code. b. block code. c. alphabetic code. d. mnemonic code. CHAPTER 3 Multiple-Choice Questions 1. Management can expect various benefits to follow from implementing a system of strong internal control. Which of the following benefits is least likely to occur? a. reduction of cost of an external audit b. prevention of employee collusion to commit fraud c. availability of reliable data for decision-making purposes d. some assurance of compliance with the Foreign Corrupt Practices Act of 1977 e. some assurance that important documents and records are protected 2. Which of the following situations is NOT a segregation of duties violation? a. The treasurer has the authority to sign checks but gives the signature block to the assistant treasurer to run the check-signing machine. b. The warehouse clerk, who has custodial responsibility over inventory in the warehouse, selects the vendor and authorizes purchases when inventories are low. c. The sales manager has the responsibility to approve credit and the authority to write off accounts. d. The department time clerk is given the undistributed payroll checks to mail to absent employees. e. The accounting clerk who shares the recordkeeping responsibility for the accounts receivable subsidiary ledger performs the monthly reconciliation of the subsidiary ledger and the control account. 3. The underlying assumption of reasonable assurance regarding implementation of internal control means that a. auditor is reasonably assured that fraud has not occurred in the period. b. auditors are reasonably assured that employee carelessness can weaken an internal control structure. c. implementation of the control procedure should not have a significant adverse effect on efficiency or profitability. d. management assertions about control effectiveness should provide auditors with reasonable assurance. e. a control applies reasonably well to all forms of computer technology. 4. To conceal the theft of cash receipts from custom- ers in payment of their accounts, which of the fol- lowing journal entries should the bookkeeper make? DR a. Miscellaneous Expense b. Petty Cash Cash c. Cash d. Sales Returns CR Cash Cash Accounts Receivable Accounts Receivable e. None of the above 5. Which of the following controls would best prevent the lapping of accounts receivable? a. Segregate duties so that the clerk responsible for recording in the accounts receivable subsidiary ledger has no access to the general ledger. b. Request that customers review their monthly statements and report any unrecorded cash payments. c. Require customers to send payments directly to the company’s bank. d. Request that customers make checks payable to the company. 6. Providing timely information about transactions in sufficient detail to permit proper classification and financial reporting is an example of a. the control environment. b. risk assessment. c. information and communication. d. monitoring. 7. Ensuring that all material transactions processed by the information system are valid and in accordance with management’s objectives is an example of a. transaction authorization. b. supervision. c. accounting records. d. independent verification. 8. Which of the following is often called a compen- sating control? a. transaction authorization b. supervision c. accounting records d. independent verification 9. Which of the following is NOT an element of the fraud triangle? a. ethics b. justifiable reliance c. situational pressure d. opportunity 10. The fraud scheme that is similar to the ‘‘borrowing from Peter to pay Paul’’ scheme is a. expense account fraud. b. bribery. c. lapping. d. transaction fraud. CHAPTER 4 1. Which document is NOT prepared by the sales department? a. b. c. d. packing slip shipping notice bill of lading stock release 2. Which document triggers the update of the inventory subsidiary ledger? a. b. c. d. bill of lading stock release sales order shipping notice 3. Which function should the billing department NOT perform? a. record the sales in the sales journal b. send the ledger copy of the sales order to accounts receivable c. send the stock release document and the shipping notice to the billing department as proof of shipment d. send the stock release document to inventory control 4. When will a credit check approval most likely require specific authorization by the credit department? a. b. c. d. when verifying that the current transaction does not exceed the customer’s credit limit when verifying that the current transaction is with a valid customer when a valid customer places a materially large order when a valid customer returns goods 5. Which type of control is considered a compensating control? a. b. c. d. segregation of duties access control supervision accounting records 6. Which of the following is NOT an independent verification control? a. The shipping department verifies that the goods sent from the warehouse are correct in type and quantity. b. General ledger clerks reconcile journal vouchers that were independently prepared in various departments. c. The use of pre-numbered sales orders. d. The billing department reconciles the shipping notice with the sales invoice to ensure that customers are billed for only the quantities shipped. 7. Which function or department below records the decrease in inventory due to a sale? a. b. c. d. warehouse sales department billing department inventory control 8. Which situation indicates a weak internal control structure? a. b. c. d. the AR clerk authorizes the write off of bad debts the record-keeping clerk maintains both AR and AP subsidiary ledgers the inventory control clerk authorizes inventory purchases the AR clerk prepares customer statements every month 9. The bill of lading is prepared by the a. b. c. d. sales clerk. warehouse clerk. shipping clerk. billing clerk. 10. Which of following functions should be segregated? a. b. c. d. opening the mail and recording cash receipts in the journal authorizing credit and determining reorder quantities shipping goods and preparing the bill of lading providing information on inventory levels and reconciling the bank statement CHAPTER 5 1. Which document helps to ensure that the receiving clerks actually count the number of goods received? a. packing list b. blind copy of purchase order c. shipping notice d. invoice 2. When the goods are received and the receiving report has been prepared, which ledger may be updated? a. b. c. d. standard cost inventory ledger inventory subsidiary ledger general ledger accounts payable subsidiary ledger 3. Which statement is NOT correct for an expenditure system with proper internal controls? a. b. c. d. Cash disbursements maintain the check register. Accounts payable maintains the accounts payable subsidiary ledger. Accounts payable is responsible for paying invoices. Accounts payable is responsible for authorizing invoices. 4. Which duties should be segregated? a. b. c. d. matching purchase requisitions, receiving reports, and invoices and authorizing payment authorizing payment and maintaining the check register writing checks and maintaining the check register authorizing payment and maintaining the accounts payable subsidiary ledger 5. Which documents would an auditor most likely choose to examine closely to ascertain that all expenditures incurred during the accounting period have been recorded as a liability? a. b. c. d. invoices purchase orders purchase requisitions receiving reports 6. Which task must still require human intervention in an automated purchases/cash disbursements system? a. b. c. d. determination of inventory requirements preparation of a purchase order preparation of a receiving report preparation of a check register 7. Which one of the following departments does not have a copy of the purchase order? a. b. c. d. the purchasing department the receiving department accounts payable general ledger 8. Which document typically triggers the process of recording a liability? a. b. c. d. purchase requisition purchase order receiving report supplier’s invoice 9. Which of the following tasks should the cash disbursement clerk NOT perform? a. b. c. d. review the supporting documents for completeness and accuracy prepare checks approve the liability mark the supporting documents paid 10. Which of the following is true? a. b. c. d. The cash disbursement function is part of accounts payable. Cash disbursements is an independent accounting function. Cash disbursements is a treasury function. The cash disbursement function is part of the general ledger department. CHAPTER 6 1. The document that captures the total amount of time that individual workers spend on each production job is called a a. b. c. d. time card. job ticket. personnel action form. labor distribution form. 2. An important reconciliation in the payroll system is when a. the general ledger department compares the labor distribution summary from cost accounting to the disbursement voucher from accounts payable. b. the personnel department compares the number of employees authorized to receive a paycheck to the number of paychecks prepared. c. the production department compares the number of hours reported on job tickets to the number of hours reported on time cards. d. the payroll department compares the labor distribution summary to the hours reported on time cards. 3. Which internal control is not an important part of the payroll system? a. supervisors verify the accuracy of employee time cards b. paychecks are distributed by an independent paymaster c. the accounts payable department verifies the accuracy of the payroll register before transferring payroll funds to the general checking account d. the general ledger department reconciles the labor distribution summary and the payroll disbursement voucher 4. The department responsible for approving pay rate changes is a. b. c. d. payroll treasurer personnel cash disbursements 5. Which function should distribute paychecks? a. b. c. d. personnel timekeeping paymaster payroll 6. Which transaction is not processed in the fixed asset system? a. b. c. d. purchase of building repair of equipment purchase of raw materials sale of company van 7. Depreciation a. is calculated by the department that uses the fixed asset. b. allocates the cost of the asset over its useful life. c. is recorded weekly. d. results in book value approximating fair market value. 8. Depreciation records include all of the following information about fixed assets EXCEPT the a. b. c. d. economic benefit of purchasing the asset. cost of the asset. depreciation method being used. location of the asset. 9. Which control is not a part of the fixed asset system? a. b. c. d. formal analysis of the purchase request review of the assumptions used in the capital budgeting model development of an economic order quantity model estimates of anticipated cost savings 10. Objectives of the fixed asset system do NOT include a. b. c. d. authorizing the acquisition of fixed assets. recording depreciation expense. computing gain and/or loss on the disposal of fixed assets. maintaining a record of the fair market value of all fixed assets. 11. Which of the following is NOT a characteristic of the fixed asset system? a. b. c. d. acquisitions are routine transactions requiring general authorization retirements are reported on an authorized disposal report form acquisition cost is allocated over the expected life of the asset transfer of fixed assets among departments is recorded in the fixed asset subsidiary ledger CHAPTER 7 1. Which of the following is not an advantageous reason to reduce inventories? a. b. c. d. e. Inventories provide a competitive advantage. Inventories can invite overproduction. Inventories are expensive to maintain. Inventories may conceal problems. All of these are good reasons to reduce inventories. 2. The fundamental EOQ model a. b. c. d. e. provides for fluctuating lead times during reorder cycles. is relatively insensitive to errors in demand, procurement costs, and carrying costs. focuses on the trade-off between production costs and carrying costs. is stochastic in nature. is best used in conjunction with a periodic inventory system. 3. Refer to the equation for the EOQ in the text. Car Country, a local Ford dealer, sells 1,280 small SUVs each year. Keeping a car on the lot costs Car Country $200 per month, so the company prefers to order as few SUVs as is economically feasible. However, each time an order is placed, the company incurs total costs of $300. Of this $300, $240 is fixed and $60 is variable. Determine the company’s economic order quantity. a. b. c. d. e. 8 16 18 56 62 4. Which line segment represents the reorder lead time? a. b. c. d. e. AB AE AF BC AC 5. Which line segment identifies the quantity of safety stock maintained? a. AB b. AE c. AC d. BC e. EF 6. Which line segment represents the length of time to consume the total quantity of materials ordered? a. b. c. d. e. DE BC AC AE AD 7. Which of the following is NOT a principle of lean manufacturing? a. b. c. d. Products are pushed from the production end to the customer. All activities that do not add value and maximize the use of scarce resources must be eliminated. Achieve high inventory turnover rate. A lean manufacturing firm must have established and cooperative relationships with vendors. e. All of the above are lean manufacturing principles. 8. All of the following are problems with traditional accounting information EXCEPT: a. b. c. d. e. Managers in a JIT setting require immediate information. The measurement principle tends to ignore standards other than money. Variance analysis may yield insignificant values. The overhead component in a manufacturing company is usually very large. All of these are problems associated with traditional accounting information. 9. Which of the following is NOT a problem associated with standard cost accounting? a. Standard costing motivates management to produce large batches of products and build inventory. b. Applying standard costing leads to product cost distortions in a lean environment. c. Standard costing data are associated with excessive time lags that reduce its usefulness. d. The financial orientation of standard costing may promote bad decisions. e. All of the above are problems with standard costing. 10. Which one of the following statements is true? a. ERP evolved directly from MRP. b. ERP evolved into MRP and MRP evolved into MRP II. c. MRP II evolved from MRP and MRP II evolved into ERP. d. None of the above is true. CHAPTER 8 1. Sequential access means that a. b. c. d. data are stored on magnetic tape. the address of the location of data is found through the use of either an algorithm or an index. to read any record on the file, all of the preceding records must first be read. each record can be accessed in the same amount of time. 2. Which file has as its primary purpose to provide historical financial data for comparative financial reports? a. b. c. d. journal voucher history file budget master file responsibility file general ledger history file 3. Which of the following statements is true? a. Journal vouchers detailing transaction activity flow from various operational departments into the GLS, where they are independently reconciled and posted to the journal voucher history file. b. Journal vouchers summarizing transaction activity flow from the accounting department into the GLS, where they are independently reconciled and posted to the general ledger accounts. c. Journal vouchers summarizing transaction activity flow from various operational departments into the GLS, where they are independently reconciled and posted to the general ledger accounts. d. Journal vouchers summarizing transaction activity flow from various operational departments into the GLS, where they are independently reconciled and posted to the journal voucher history file. 4. Which of the following statements best describes a computer-based GL/FRS? a. b. c. d. Most firms derive little additional benefit from a real-time FRS. Batch processing is typically not appropriate for transaction processing of GLS. The sequential file approach is an inefficient use of technology. A batch system with direct access files recreates the entire database each time the file is updated. 5. Which of the following is NOT a potential exposure of the FRS? a. b. c. d. a defective audit trail general ledger accounts that are out of balance with subsidiary accounts unauthorized access to the check register unauthorized access to the general ledger 6. Which task should the general ledger perform? a. b. c. d. update the general ledger prepare journal vouchers have custody of physical assets have record-keeping responsibility for special journals of subsidiary ledgers 7. The Ozment Corporation uses a performance reporting system that shows online the data for each subordinate who reports to a supervisor. The data presented show the actual costs incurred during the period, the budgeted costs, and all variances from budget for that subordinate’s department. The name of this system of reporting is a. b. c. d. e. contribution accounting. responsibility accounting. flexible budgeting. program budgeting. cost-benefit accounting. 8. Which of the following is not a characteristic of the strategic planning process? a. b. c. d. e. emphasis on both the short and long run analysis of external economic factors review of the attributes and behavior of the organization’s competition analysis and review of departmental process analysis of consumer demand 9. The following are all output reports of the financial reporting system, EXCEPT a. b. c. d. variance analysis report. statement of cash flows. tax return. comparative balance sheet. 10. Which of the following budgeting processes is LEAST likely to motivate managers toward organizational goals? a. b. c. d. e. setting budget targets at attainable levels participation by subordinates in the budgetary process use of management by exception holding subordinates accountable for the items they control having top management set budget levels 11. Which of the following would normally be considered in a strategic plan? a. b. c. d. e. setting a target of 12 percent return on sales maintaining the image of the company as the industry leader setting a market price per share of stock outstanding distributing monthly reports for departmental variance analysis tightening credit terms for customers to 2/10, n/30 12. At what level of management is the long-range planning function most important? a. b. c. d. e. at top management levels at middle management levels at lower management levels for staff functions for line functions 13. Which of the following is the basic purpose of a responsibility accounting? a. b. c. d. e. variance analysis motivation authority budgeting pricing 14. Which statement below best describes a profit center? a. The authority to make decisions affecting the major determinants of profit, including the power to choose its markets and sources of supply. b. The authority to make decisions affecting the major determinants of profit, including the power to choose its markets, sources of supply, and significant control over the amount of invested capital. c. The authority to make decisions over the most significant costs of operations, including the power to choose the sources of supply. d. The authority to provide specialized support to other units within the organization. e. The responsibility for combining the raw materials, direct labor, and other factors of production into a final product. 15. Which statement below best describes an investment center? a. The authority to make decisions affecting the major determinants of profit, including the power to choose its markets and sources of supply. b. The authority to make decisions affecting the major determinants of profit, including the power to choose its markets and sources of supply, and significant control over the amount of invested capital. c. The authority to make decisions over the most significant costs of operations, including the power to choose the sources of supply. d. The authority to provide specialized support to other units within the organization. e. The responsibility for developing markets for and selling of the output of the organization. CHAPTER 9 1. The data attributes that a particular user has permission to access are defined by the a. b. c. d. e. operating system view. systems design view. database schema. user view. application program. 2. The database approach has several unique characteristics not found in traditional (flat-file) systems. Which of the following statements does not apply to the database model? a. Database systems have data independence; that is, the data and the programs are maintained separately except during processing. b. Database systems contain a data-definition language that helps describe each schema and subschema. c. The database administrator is the part of the software package that instructs the operating aspects of the program when data are retrieved. d. A primary goal of database systems is to minimize data redundancy. e. Database systems provide increased accessibility to data and flexibility in its usage. 3. One of the first steps in the creation of a relational database is to a. integrate accounting and nonfinancial data. b. plan for increased secondary storage capacity. c. order data-mining software that will facilitate data retrieval. d. create a data model of the key entities in the system. e. construct the physical user view using SQL. 4. Database currency is achieved by a. b. c. d. e. implementing partitioned databases at remote sites. employing data-cleansing techniques. ensuring that the database is secure from accidental entry. an external auditor’s reconciliation of reports from multiple sites. a database lockout that prevents multiple simultaneous access. 5. The installation of a database management system is likely to have the least impact on a. b. c. d. e. data redundancy. entity-wide sharing of common data. exclusive ownership of data. the logic needed to solve a problem in an application program. the internal controls over data access. 6. The functions of a database administrator are a. b. c. d. e. database planning, data input preparation, and database design. data input preparation, database design, and database operation. database design, database operation, and equipment operations. database design, database implementation, and database planning. database operations, database maintenance, and data input preparation. 7. A relational database system contains the following inventory data: part number, description, quantity on-hand, and reorder point. These individual items are called a. b. c. d. attributes. relations. associations. occurrences. 8. Which of the following is a characteristic of a relational database system? a. All data within the system are shared by all users to facilitate integration. b. Database processing follows explicit links that are contained within the records. c. User views limit access to the database. d. Transaction processing and data warehousing systems share a common database. 9. Partitioned databases are most effective when a. b. c. d. users in the system need to share common data. primary users of the data are clearly identifiable. read-only access is needed at each site. all of the above. 10. Database entities a. b. c. d. e. may contain zero or many occurrences. are represented as verbs in an ER diagram. may represent both physical assets and intangible phenomena. are often defined by common attributes that also define other entities. are unique to a specific user view. 11. A transitive dependency a. b. c. d. e. is a database condition that is resolved through special monitoring software. is a name given to one of the three anomalies that result from unnormalized database tables. can exist only in a table with a composite primary key. cannot exist in tables that are normalized at the 2NF level. is none of the above. 12. A partial dependency a. is the result of simultaneous user requests for the same data in a partitioned database environment. b. is a name given to one of the three anomalies that result from unnormalized database tables. c. can exist only in a table with a composite primary key. d. may exist in tables that are normalized at the 2NF level. e. is none of the above. 13. Repeating group data a. is a form of data redundancy common to replicated databases in a distributed database environment. b. is a name given to one of the three anomalies that result from unnormalized database tables. c. can exist only in a table with a composite primary key. d. cannot exist in tables that are normalized at the 2NF level. e. is none of the above. 14. The database model most likely to be used in the development of a modern (not legacy) system is a. b. c. d. e. hierarchical structured relational network navigational 15. Typical DBMS features include all of the following EXCEPT a. b. c. d. e. database interface design and development. backup and recovery. program development. database access. all of these are typical DBMS features. 16. Which of the following is least likely to be an attribute of an employee table in a normalized database? a. b. c. d. e. employee name employee address employee number employee supervisor’s name all of these would be attributes of the employee table in a normalized database. 17. The advantages to using a partitioned database approach include all of the following EXCEPT a. b. c. d. e. the possibility for the deadlock phenomenon is reduced. user control is increased. transaction processing time is decreased. the potential for wide-scale disaster is reduced. these are all advantages of partitioned databases. 18. Of the following, select the attribute that would be the best primary key in an inventory table. a. b. c. d. ITEM NAME ITEM LOCATION ITEM COST ITEM NUMBER e. ITEM SUPPLIER CHAPTER 10 1. The concept of duality means that an REA diagram must consist of a. b. c. d. e. two events—one of them economic and the other support. two agents—one of them internal and the other external. two resources—one increased and the other decreased by the same event. all of the above. none of the above. 2. Each economic event in an REA diagram is always a. b. c. d. e. linked to at least two resource entities. linked to two external agents. linked to two internal agents. linked to another economic event. linked to a support event. 3. Which of the following are characteristics of economic agents? a. b. c. d. They participate in economic events, but do not assume control of the resources. They participate in economic events, but not in support events. Internal agents are employees of the company whose system is being modeled. External agents are not employees of the company whose system is being modeled. e. All of the above describe agents. 4. Which of the following is true? a. b. c. d. e. REA diagram entities are arranged in constellations by entity class. ER diagrams present a static picture of the underlying business phenomena. Entity names in ER diagrams are always in the noun form. Events entity names in REA diagrams are in the verb form. All of the above are true statements. 5. Which of the following events would be LEAST likely to be modeled in an REA diagram? a. customer inquiries b. sales to a customer c. accounts payable d. cash e. all of these events would be modeled 6. Which of the following associations would most likely describe the relationship between an internal agent and an economic event? a. b. c. d. e. 1:M 1:1 M:M 0:M none of the above 7. Which of the following tables would most likely have a composite key? a. b. c. d. e. Take Order Ship Goods Inventory-Ship Link Cash none of the above 8. Which of the following associations requires a separate table in the database? a. b. c. d. 1:1 1:M M:M all of the above 9. When assigning foreign keys in a 1:1 association a. the primary key of each table should be embedded as a foreign key in the related table. b. the primary key on the 0,1 side of the relation should be embedded as the foreign key on the 1,1 side. c. the primary key on the 1,1 side of the relation should be embedded as the foreign key on the 0,1 side. d. a link table must be created to accept the foreign keys of both tables. e. none of the above is true. 10. When assigning foreign keys in a 1:M association a. the primary key of each table should be embedded as a foreign key in the related table. b. the primary key on the 0,M side of the relation should be embedded as the foreign key on the 1,1 side. c. the primary key on the 1,1 side of the relation should be embedded as the foreign key on the 0,M side. d. a link table must be created to accept the foreign keys of both tables. e. none of the above is true. CHAPTER 11 1. Closed database architecture is a. b. c. d. e. a control technique intended to prevent unauthorized access from trading partners. a limitation inherent in traditional information systems that prevents data sharing. a data warehouse control that prevents unclean data from entering the warehouse. a technique used to restrict access to data marts. a database structure that many of the leading ERPs use to support OLTP applications. 2. Each of the following is a necessary element for the successful warehousing of data EXCEPT a. b. c. d. e. cleansing extracted data. transforming data. modeling data. loading data. all of the above are necessary. 3. Which of the following is typically NOT part of an ERP’s OLAP applications? a. b. c. d. e. decision support systems information retrieval ad hoc reporting/analysis logistics what-if analysis 4. There are a number of risks that may be associated with ERP implementation. Which of the following was NOT stated as a risk in the chapter? a. A drop in firm performance after implementation because the firm looks and works differently than it did while using a legacy system. b. Implementing companies have found that staff members, employed by ERP consulting firms, do not have sufficient experience in implementing new systems. c. Implementing firms fail to select systems that properly support their business activities. d. The selected system does not adequately meet the adopting firm’s economic growth. e. ERPs are too large, complex, and generic for them to be well integrated into most company cultures. 5. Which statement is NOT true? a. In a typical two-tier client-server architecture, the server handles both application and database duties. b. Client computers are responsible for presenting data to the user and passing user input back to the server. c. Two-tier architecture is for local area network applications where the demand on the server is restricted to a relatively small population of users. d. The database and application functions are separated in the three-tier model. e. In three-tier client-server architectures, one tier is for user presentation, one is for database and applications access, and the third is for Internet access. 6. Which statement is NOT true? a. Drill-down capability is an OLAP feature of data mining tools available to the user. b. The data warehouse should be separate from operational systems. c. Denormalization of data involves dividing the data into very small tables that support detailed analysis. d. Some decisions supported by a data warehouse are not fundamentally different from those that are supported by traditional databases. e. Data cleansing involves transforming data into standard business terms with standard data values. 7. Which statement is LEAST accurate? a. Implementing an ERP system has more to do with changing the way an organization does business than it does with technology. b. The phased-in approach to ERP implementation is particularly suited to diversified organizations whose units do not share common processes and data. c. Because the primary reason for implementing an ERP is to standardize and integrate operations, diversified organizations whose units do not share common processes and data do not benefit and tend not to implement ERPs. d. To take full advantage of the ERP process, reengineering will need to occur. e. A common reason for ERP failure is that the ERP does not support one or more important business processes of the organization. 8. SAP, one of the leading ERP producers, makes several modules available to adopters. Which of the following is not a SAP module? a. b. c. d. e. Business Process Support Internet Development Support Logistics E-Commerce Support Human Resources 9. Auditors of ERP systems a. need not be concerned about segregation of duties because these systems possess strong computer controls. b. focus on output controls such as independent verification to reconcile batch totals. c. are concerned that managers fail to exercise adequate care in assigning permissions. d. do not see the data warehouse as an audit or control issue at all because financial records are not stored there. e. need not review access levels granted to users because these are determined when the system is configured and never change. 10. Which statement is most correct? a. b. c. d. e. SAP is more suited to service industries than manufacturing clients. J.D. Edwards’s ERP is designed to accept the best-practices modules of other vendors. Oracle evolved from a human resources system. PeopleSoft is the world’s leading supplier of software for information management. SoftBrands provides enterprise software for the hospitality and manufacturing sectors. CHAPTER 12 1. Which of the following statements is correct? a. b. c. d. e. TCP/IP is the basic protocol that permits communication between Internet sites. TCP/IP controls Web browsers that access the Web. TCP/IP is the document format used to produce Web pages. TCP/IP is used to transfer text files, programs, spreadsheets, and databases across the Internet. TCP/IP is a low-level encryption scheme used to secure transmissions in higher-level (HTTP) format. 2. Which of the following best describes a system of computers that connects the internal users of an organization distributed over a wide geographic area? a. LAN b. c. d. e. Internet decentralized network multidrop network intranet 3. Sniffer software is a. used by malicious Web sites to sniff data from cookies stored on the user’s hard drive. b. used by network administrators to analyze network traffic. c. used by bus topology intranets to sniff for carriers before transmitting a message to avoid data collisions. d. an illegal program downloaded from the Web to sniff passwords from the encrypted data of Internet customers. e. illegal software for decoding encrypted messages transmitted over a shared intranet channel. 4. Which of the following statements is true? a. b. c. d. e. Cookies were originally intended to facilitate advertising on the Web. Cookies always contain encrypted data. Cookies are text files and never contain encrypted data. Cookies contain the URLs of sites the user visits. Web browsers cannot function without cookies. 5. A message that is contrived to appear to be coming from a trusted or authorized source is called a. b. c. d. e. a denial of service attack. digital signature forging. Internet protocol spoofing. URL masquerading. a SYN-ACK packet. 6. A DDos attack a. is more intensive than a Dos attack because it emanates from single source. b. may take the form of either a SYN flood or smurf attack. c. is so named because it affects many victims simultaneously, which are distributed across the Internet. d. turns the target victim’s computers into zombies that are unable to access the Internet. e. none of the above is correct. 7. A ping signal is used to initiate a. b. c. d. e. URL masquerading. digital signature forging. Internet protocol spoofing. a smurf attack a SYN-ACK packet. 8. A digital signature a. b. c. d. e. is the encrypted mathematical value of the message sender’s name. is derived from the digest of a document that has been encrypted with the sender’s private key. is derived from the digest of a document that has been encrypted with the sender’s public key. is the computed digest of the sender’s digital certificate. allows digital messages to be sent over an analog telephone line. 9. Which of the following statements about the client-server model is correct? a. It is best suited to the token ring topology because the random-access method this topology uses detects data collisions. b. It distributes both data and processing tasks to the server node. The client-server model can use the bus or ring topology. c. It is most effective when used as a bus topology because its deterministic access method avoids collisions and prevents data loss during transmissions. d. It is more efficient than the bus or ring topologies because it transmits an entire file of records to the requesting node rather than only a single record. e. It is not used in conjunction with either the bus or ring topologies. 10. Which of the following statements is correct? a. A bridge is used to connect a LAN and a WAN. b. Packet switching combines the messages of multiple users into a packet for transmission. At the receiving end, the packet is disassembled into individual messages and distributed to the user. c. The decision to partition a database assumes that no identifiable primary user exists in the organization. d. Message switching is used to establish temporary connections between network devices for the duration of a communications session. e. A deadlock is a temporary phenomenon that disrupts transaction processing. It will resolve itself when the primary computer completes processing its transaction and releases the data the other nodes need. Quiz # 1 Identification Get the answer from the words/phrases below for the questions that follow. Wrong spelling is wrong. System Component Subsystem Transaction Accounts Agent Data Information Feedback Attribute Files Record Information System Accounting Information System Management Information System Transaction Processing System Financial Reporting System Management Reporting System Subsystem Interdependency External Users Internal Users System Decomposition Operations Management Middle management Top management Relevance Efficiency Timeliness Accuracy Completeness Summarizatio Operations Management1.Business organization is divided horizontally into several levels of activity. Business operations form the base of the pyramid and then followed by. System2.This is a group of two or more interrelated components or subsystems that serve a common purpose. Subsystem Interdependency 3.A system’s ability to achieve its goal depends on the effective functioning and harmonious interaction of its subsystems. If a vital subsystem fails or becomes defective and can no longer meet its specific objective, the overall system will fail to meet its objective. Information System 4.This is a set of formal procedures by which data are collected, processed into information, and distributed to users. Transaction 5.It is an event that affects or is of interest to the organization and is processed by the information system as a unit of work. Management Reporting System 6.This provides internal management with special-purpose financial reports and information needed for decision making such as budgets, variance reports, and responsibility reports. External Users 7.These users include creditors, stockholders, potential investors, regulatory agencies, tax authorities, suppliers, and customers. Information 8.This causes the user to take an action that he or she otherwise could not, or would not, have taken. Relevance 9.A fundamental task of the system designer is to analyze users' needs. This satisfies which rule of data collection? Feedback 10.This is a form of output that is sent back to the system as a source of data. True or False Write True if the statement if True, False if the statement is False. Wrong spelling is wrong. False 11.Backbone systems are general-purpose systems or systems customized to a specific industry. The users have standard business practices that permit the use of such system. False 12.Geographic location divides the organization into areas of specialized responsibility based on tasks. True 13.Receiving is the task of accepting the inventory. It includes counting and checking physical condition of items. False 14.Production planning is a primary manufacturing activity without which raw materials cannot be assembled to finish products. True 15.DDP involves reorganizing the IT function into small information processing units (IPUs) that are distributed to end users and placed under their control. True 16.The flat-file model describes an environment in which individual data files are not related to other files. End users in this environment own their data files rather than share them with other users. Thus, stand-alone applications rather than integrated systems perform data processing. False 17.The database model is a framework for modeling an organization’s critical resources, events, and agents and the relationships between them. True 18.ERP is an information system model that enables an organization to automate and integrate its key business processes. True 19.IT auditing is usually performed as part of a broader financial audit. False 20.The conceptual system is the medium and method for capturing and presenting the information. The computer professionals determine the most economical and effective technology for accomplishing the task. Quiz #2 - AIS 2213-4 I. Identification Supply the answer on the questions that follow from the words listed below. Wrong spelling is wrong. Asset maintenance Language Personnel Action Forms Blind copy File Transfer Protocol Point of sale systems Cardinality Insertion anomaly Purchase Order Computer-aided design Job tickets REA model Credit authorization Lean manufacturing Responsibility accounting Economic events Management by Exception Sales Journal Enterprise resource planning Materials requirements planning Smurf attack Entity relationship diagram eXtensible Business Reporting Online transaction processing Value chain analysis Voucher's payable system Purchase Order 1. This is prepared from purchase requisitions that are sorted by Vendor if necessary. Sales Journal 2. his is a special journal used for recording completed sales transactions.(1 Point) Credit Authorization 3.The credit department is organizationally and physically segregated from the sales department. When credit is approved, the sales department clerk pulls the various copies of the sales sales department. When credit is approved, the sales department clerk pulls the various copies of the sales orders from the pending file and releases them to the billing, warehouse, and shipping departments.(1 Point) Point of sale systems 4. This is used by businesses like grocery stores that exchange goods directly for cash in a transaction. Only cash, checks, and bank credit card sales are valid. The organization maintains no customer accounts receivable.(1 Point) Voucher's payable system 5.Under this system, the AP department uses cash disbursement vouchers and maintains a voucher register. After the AP clerk performs the three-way match, he or she prepares a cash disbursement voucher to approve payment.(1 Point) Blind copy 6.The purpose of this is to force the receiving clerk to count and inspect inventories prior to completing the receiving report. At times, receiving docks are very busy and receiving staff are under pressure to unload the delivery trucks and sign the bills of lading so the truck drivers can go on their way.(1 Point) Asset Maintenance 7. This involves adjusting the fixed asset subsidiary account balances as the assets (excluding land) depreciate over time or with usage.(1 Point) Personnel Action Forms 8.These documents identify employees authorized to receive a paycheck and are used to reflect changes in hourly pay rates, payroll deductions, and job classification.(1 Point) Job Tickets 9.This captures the time that individual workers spend on each production job. Cost accounting uses these documents to allocate direct labor charges to work-in-process (WIP) accounts.(1 Point) Lean manufacturing 10. This involves doing more with less, eliminating waste, and reducing production cycle time.(1 Point) Computer-aided design 11.Engineers use this to design better products faster. They increase engineers’ productivity, improve accuracy by automating repetitive design tasks, and allow firms to be more responsive to market demands.(1 Point) Materials requirements planning 12.These systems are limited in focus and geared toward determining how much raw materials are required to fulfill production orders.(1 Point) Responsibility accounting 13.This concept implies that every economic event that affects the organization is the responsibility of and can be traced to an individual manager.(1 Point) Management by Exception 14.This principle suggests that managers should limit their attention to potential problem areas rather than being involved with every activity or decision.(1 Point) eXtensible Business Reporting Language 15.This is the internet standard specifically designed for business reporting and information exchange. The objective is to facilitate the publication, exchange, and processing of financial and business information.(1 Point) Entity relationship diagram 16. This is a graphical representation used to depict the data model. Cardinality 17. It is the degree of association between two entities.(1 Point) Insertion anomaly 18. It is impossible to add data to the database because of the new data does not have a primary key.(1 Point) REA model 19. This is an accounting framework for modeling an organization’s critical resources, events, and agents and the relationships between them.(1 Point) Value chain analysis 20. This distinguishes between primary activities and support activities: primary activities create value; support activities assist in the achievement of the primary activities.(1 Point) Economic events 21. These are phenomena that effect changes (increases or decreases) in resources. Online transaction processing 22. Are those applications that operationally support the day-to-day activities of the business. If these applications fail, so does the business.(1 Point) Enterprise resource planning 23. The trend in information systems is toward implementing highly integrated, enterprise-oriented systems. These are not custom packages designed for a specific organization. Instead, they are generalized systems that incorporate the best business practices in use. Organizations mix and match precoded software components to assemble.(1 Point) Smurf Attack 24. Involves three parties: the perpetrator, the intermediary, and the victim. It is accomplished by exploiting an Internet maintenance tool called a ping, which is used to test the state of network congestion and determine whether a particular host computer is connected and available on the network.(1 Point) File Transfer Protocol 25. This is used to transfer text files, programs, spreadsheets, and databases across the Internet.(1 Point) ex II. True or False Write True if the statement of true, False if the statement is false. Wrong spelling is wrong. FALSE (IP SPOOFING) 26. Dos is a form of masquerading to gain unauthorized access to a Web server and/or to perpetrate an unlawful act without revealing one’s identity.(1 Point) True 27. Secure Electronic Transmission is an encryption scheme developed by a consortium of technology firms and banks (Netscape, Microsoft, IBM, Visa, MasterCard, and so on) to secure credit card transactions.(1 Point) FALSE (CORE APPLICATIONS) 28. Business analysis applications are also called online transaction processing (OLTP) applications.(1 Point) FALSE (baligtad - more to do with changing the way.... Than it does with technology) 29. Implementing an ERP system has more to do with technology than it does with changing the way an organization does business.(1 Point) True 30. The REA approach to modeling business processes helps managers focus on the key elements of economic events and identify the nonvalue-added activities that can be eliminated from operations. True 31. ER and REA diagrams differ visually in a significant way. Entities in ER diagrams are of one class, and their proximity to other entities is determined by their cardinality and by what is visually pleasing to keep the diagrams readable. Entities in an REA diagram, however, are divided into three classes and organized into constellations by class on the diagram. FALSE 32. Under the DDP approach, remote users send requests via terminals for data to the central site, which processes the requests and transmits the data back to the user. True 33. Multiple indexes can be used to create a cross-reference, called an inverted list, which allows even more flexible access to data. FALSE (Database usage reporting) 34. The database access feature captures statistics on what data are being used, when they are used, and who uses them. The database administrator (DBA) uses this information to help in assigning user authorization and in maintaining the database(1 Point) FALSE (There are two ways) 35. The only way users access the database is via user application programs. With this, data processing procedures (both batch and real-time) for transactions such as sales, cash receipts, and purchases are essentially the same as they would be in the flat-file environment.(1 Point) True 36. A cost center is an organizational unit with responsibility for cost management within budgetary limits. True 37. When all three elements are known with certainty, the problem is structured. Payroll calculation is an example of a structured problem.(1 Point) True 38. ABC is a method of allocating costs to products and services to facilitate better planning and control. It accomplishes this by assigning cost to activities based on their use of resources and assigning cost to cost objects based on their use of activities.(1 Point) FALSE 39. Upon receipt of the voucher packet, the AP clerk removes the liability by debiting the AP subsidiary account or by recording the check number and payment date in the voucher register. The voucher packet is filed in the open voucher file.(1 Point) FALSE 40. Upon receiving the goods from the warehouse, the shipping clerk reconciles the physical items with the stock release, the packing slip, and the shipping notice to verify that the order is correct. The ship goods function thus serves as an important independent verification control point and is the last opportunity to detect errors before shipment. The shipping clerk packages the goods, attaches the packing slip, completes the shipping notice, and prepares a remittance advise. AIS Master Reviewer 1 8 - Accounting Info System Test bank Accounting Information Systems (ACT INFO) Chapter 1—The Information System: An Accountant’s Perspective 12. A backbone system is completely finished, tested, and ready for implementation. TRUE/FALSE ANS: F 1. Information is a business resource. 13. The internal auditor represents the interests of third-party outsiders. ANS: T 2. An information system is an example of a natural system. ANS: F ANS: F 14. Information Technology (IT) audits can be performed by both internal and external auditors. ANS: T 3. Transaction processing systems convert nonfinancial transactions into financial transactions. 15. The single largest user of computer services is the personnel function. ANS: F 4. Information lacking reliability may still have value. ANS: F ANS: F 16. Increased control is one of the key advantages of distributed data processing. 5. A balance sheet prepared in conformity with GAAP is an example of discretionary reporting. ANS: F ANS: F 17. The flat-file approach is most often associated with so-called legacy systems. 6. The Management Reporting System provides the internal financial information needed to manage a business. ANS: T 7. Most of the inputs to the General Ledger System come from the Financial Reporting System. ANS: F 8. When preparing discretionary reports, organizations can choose what information to report and how to present it. ANS: T 9. Retrieval is the task of permanently removing obsolete or redundant records from the database. ANS: F ANS: T 18. In a flat-file system, files are easily shared by users. ANS: F 19. Legacy systems were eliminated in the effort to make systems Y2K compliant. ANS: F 20. One of the greatest disadvantages of database systems is that all data is always available to all users. ANS: F 21. Under SOX legislation auditors are no longer allowed to provide consulting services to audit clients. 10. Systems development represents 80 to 90 percent of the total cost of a computer system. ANS: T ANS: F 22. Under SOX legislation auditors are no loger allowed to provide consulting services to their clients. 11. The database administrator is responsible for the security and integrity of the database. ANS: T ANS: F They cannot provide such services to audit clients but may still provide them to non-audit clients 7 0 MULTIPLE CHOICE c. convenience 1. Which of the following is not a business resourc e? d. completeness a. raw material ANS: C b. labor 6. An example of a nonfinancial transaction is c. information a. sale of products d. all are business resources b. cash disbursement ANS: D c. log of customer calls 2. Which level of management is responsible for short-term planning and coordination of activities necessary to accomplish organizational objectives? d. purchase of inventory a. operations management 7. An example of a financial transaction is b. middle management a. the purchase of computer c. top management b. a supplier’s price list ANS: C c. a delivery schedule d. line management ANS: B d. an employee benefit brochure 3. Which level of management is responsible for controlling day-to-day operations? ANS: A 8. Which subsystem is not part of the Accounting Information System? a. top management a. Transaction Processing System b. middle management c. operations management b. Expert System d. executive management c. General Ledger/Financial Reporting System ANS: C d. Management Reporting System 4. The ability to achieve the goals of a system depends upon the effective functioning and harmonious interaction between its subsystems. This is called a. system decomposition ANS: B 9. The major difference between the Financial Reporting System (FRS) and the Management Reporting System (MRS) is the a. FRS provides information to internal and external users; the MRS provides information to internal users b. system redundancy c. backup system b. FRS provides discretionary information; the MRS provides nondiscretionary information d. subsystem interdependency ANS: D 5. The value of information for users is determined by all of the following but c. FRS reports are prepared using information provided by the General Ledger System; the MRS provides information to the General Ledger System d. FRS reports are prepared in flexible, nonstandardized formats; the MRS reports are prepared in standardized, formal formats a. reliability b. relevance 7 0 ANS: A b. the key 10. The purpose of the Transaction Processing System includes all of the following except c. the file d. the attribute a. converting economic events into financial transactions ANS: D b. recording financial transactions in the accounting records 15. In a database, a complete set of attributes for a single occurrence of an entity class is called c. distributing essential information to operations personnel to support their daily operatio ns a. a key d. measuring and reporting the status of financial resources and the changes in those resources c. a record b. a file d. a character ANS: D 11. The Transaction Processing System includes all of the following cycles except a. the revenue cycle ANS: C 16. Effective information has all of the following characteristics except a. relevance b. the administrative cycle b. completeness c. the expenditure cycle c. summarization d. the conversion cycle d. structure ANS: B 12. The primary input to the Transaction Processing System is ANS: D 17. Database management tasks do not include a. a financial transaction a. summarization b. an accounting record b. storage c. an accounting report c. retrieval d. a nonfinancial transaction d. deletion ANS: A ANS: A 13. When designing the data collection activity, which type of data should be avoided? 18. The author distinguishes between the Accounting Information System and the management Information System based on a. data that is relevant a. whether the transactions are financial or nonfinancial b. data that is efficient c. data that is redundant b. whether discretionary or nondiscretionary reports are prepared d. data that is accurate c. the end users of the reports ANS: C d. the organizational structure of the business 14. The most basic element of useful data in the database is ANS: A a. the record 7 0 19. Which activity is not part of the finance function? a. cash receipts b. separation of duties, such as record keeping and custody of physical resources c. generation of accurate and timely information b. portfolio management d. business segmentation by function c. credit ANS: B d. general ledger 24. In the distributed data processing approach ANS: D a. computer services are consolidated and managed as a shared organization resource 20. Market research and advertising are part of which business function? b. the computer service function is a cost center a. materials management c. the end users are billed using a charge-back system b. finance c. marketing d. computer services are organized into small information processing units under the control of end users d. production ANS: C ANS: D 21. Which function manages the financial resources of the firm through portfolio management, banking, credit evaluation, and cash receipts and disbursements? a. accounting 25. The data control group is responsible for a. performing the day-to-day processing of transactions b. security and integrity of the database b. finance c. liaison between the end user and data processing c. materials management d. providing safe storage for off-line data files d. distribution ANS: C ANS: B 26. Data processing does not involve 22. Which of the following is not part of the accounting function? a. data control a. managing the financial information resource of the firm b. computer operations c. system maintenance d. data conversion b. capturing and recording transactions in the database ANS: C c. distributing transaction information to operations personnel 27. Independent auditing is performed by d. managing the physical information system of the firm a. external auditors ANS: D c. licensed auditors 23. The term “accounting independence” refers to d. third-party accountants a. data integrity ANS: A 7 b. internal accountants 0 28. Which individual is least involved in new systems development? a. systems analyst d. confidence that all data is current ANS: B b. external auditor 33. Disadvantages of distributed data processing include all of the following except c. end user a. mismanagement of organizationwide resources d. data librarian b. hardware and software incompatibility ANS: D c. cost reductions 29. The objectives of all information systems include all of the following except d. difficulty in hiring qualified IT professionals a. support for the stewardship function of management ANS: C 34. Advantages of distributed data processing include each of the following except b. evaluating transaction data a. cost reductions c. support for the day-to-day operations of the firm d. support for management decision making b. better management of organization resources c. improved operational efficiency ANS: B d. increased user satisfaction 30. Which individuals may be involved in the Systems Development Life Cycle? ANS: B a. accountants 35. Disadvantages of the distributed data processing approach include all of the following except b. systems professionals c. end users a. possible mismanagement of organization resources d. all of the above b. redundancy of tasks ANS: D c. software incompatibility 31. An appraisal function housed within the organization that performs a wide range of services for management is d. system is not responsive to the user’s situation ANS: D 36. ERP packages include all of the following modules except a. internal auditing b. data control group a. human resources c. external auditing b. general ledger d. database administration c. inventory management ANS: A d. they include all of the above 32. Advantages of a database system include all of the following except ANS: D 37. All of the following are external end users except a. elimination of data redundancy b. open access to all data by all users a. cost accountants c. single update for changes in data b. creditors 7 0 c. stockholders 3. Transactions with trading partners include ____________________ and ____________________. d. tax authorities ANS: A ANS: sales, purchases 38. Useful information must possess all of the following characteristics except a. relevance 4. A system is a group of two or more interrelated components that ___________________________________. b. timelessness ANS: serve a common purpose c. accuracy d. completeness 5. The task of locating and transferring an existing record from the database for processing is called data ____________________. ANS: B ANS: retrieval 39. The objectives of an information system include each of the following except 6. Three ways that a business can be divided into segments are by __________________________, __________________________ and by __________________________. a. support for the stewardship responsibilities of management b. furthering the financial interests of shareholders ANS: geographic location, product lines, function 7. Three activities that are part of the finance function are __________________________, __________________________, and __________________________. c. support for management decision making d. support for the firm’s day-to-day operations ANS: B 40. Accountants play many roles relating to the accounting information system, including all of the following except ANS: portfolio management, treasury, credit, cash disbursements, cash receipts a. system users 8. Two distinct ways to structure the Data Processing Department are ____________________ and ____________________. b. system designers ANS: centralized, distributed c. system auditors 9. Two methods to acquire information systems are to __________________________ and to __________________________. d. system converters ANS: D ANS: develop customized systems, purchase commercial systems SHORT ANSWER 1. Entities outside the organization with a direct or indirect interest in the firm, such as stockholders, financial institutions, and government agencies, are called ____________________. ANS: stakeholders 10. Audits are conducted by ____________________, ____________________, and ____________________ auditors. ANS: internal, external, IT 11. Sales of products to customers, purchases of inventory from vendors, and cash disbursements are all example of __________________________. 2. The process of breaking a system into smaller subsystem parts is called ______________________________. ANS: financial transactions ANS: system decomposition 7 0 12. The three major subsystems of the AIS are _______________________________, ___________________________, and _______________________________. their audit clients. This is now prohibited from doing so under SOX legislation. ANS: the transaction processing system, the general ledger/financial reporting system, the management reporting system ANS: Reports used by management that the company is not obligated by law, regulation, or contract to provide. These are often used for internal problem-solving issues rather than by external constituents. 19. What is discretionary reporting? 13. The __________________________ and __________________________ standards that characterize the AIS clearly distinguish it from the MIS. ANS: legal, professional 20. Name the five characteristics of information? ANS: Relevance, accuracy, completeness, summarization, and timeliness. 14. The transaction processing system is comprised of three cycles: __________________________, __________________________, and __________________________. Chapter 2—Introduction to Transaction Processing ANS: revenue, expenditure, conversion 1. Processing more transactions at a lower unit cost makes batch processing more efficient than realtime systems. 15. The REA model identifies an organization’s ____________________, ____________________, and ____________________. TRUE/FALSE ANS: T 2. The process of acquiring raw materials is part of the conversion cycle. ANS: resources, events, agents. 16. Sarbanes-Oxley legislation requires that management designs and implements controls over the entire financial reporting process. What systems does this include? ANS: This includes the financial reporting system, the general ledger system, and the transaction processing systems that supply the data for financial reporting. 17. Why is it necessary to distinguish between AIS and MIS? ANS: Because of the highly integrative nature of modern information systems, management and auditors need a conceptual view of the information system that distinguishes key processes and areas of risk and legal responsibility from the other (nonlegally binding) aspects of the system. Without such a model, critical management and audit responsibilities under SOX may not be met. 18. How has SOX legislation impacted the consulting practices of public accounting firms? ANS: Prior to SOX, a gray area of overlap existed between assurance and consulting services. Auditors were once allowed to provide consulting services to 7 ANS: F 3. Directing work-in -process through its various stages of manufacturing is part of the conversion cycle. ANS: T 4. The top portion of the monthly bill from a credit card company is an example of a turn-around document. ANS: T 5. The general journal is used to record recurring transactions that are similar in nature. ANS: F 6. Document flowcharts are used to represent systems at different levels of detail. ANS: F 7. Data flow diagrams represent the physical system. ANS: F 0 ANS: F 8. Document flowcharts are often used to depict processes that are handled in batches. 20. An inverted triangle with the letter “N” represents a file in “name” order. ANS: T ANS: F 9. Program flowcharts depict the type of media being used (paper, magnetic tape, or disks) and terminals. 21. Real-time processing in systems that handle large volumes of transactions each day can create operational inefficiencies. ANS: F 10. System flowcharts represent the input sources, programs, and output products of a computer system. ANS: T ANS: T 22. Operational inefficiencies occur because accounts unique to many concurrent transactions need to be updated in real time. 11. Program flowcharts are used to describe the logic represented in system flowcharts. ANS: F ANS: T 12. Batch processing systems can store data on direct access storage devices. 23. Operational inefficiencies occur because accounts common to many concurrent transactions need to be ANS: T updated in real time. 13. Backups are automatically produced in a direct access file environment. ANS: T ANS: F 24. Batch processing of noncritical accounts improves operational efficiency. 14. The box symbol represents a temporary file. ANS: T ANS: F 25. Batch processing of accounts common to many concurrent transactions reduces operational efficiency. 15. Auditors may prepare program flowcharts to verify the correctness of program logic. ANS: F ANS: T MULTIPLE CHOICE 16. A control account is a general ledger account which is supported by a subsidiary ledger. 1. Which system is not part of the expenditure cycle? ANS: T a. cash disbursements 17. The most significant characteristic of direct access files is access speed. b. payroll c. production planning/control ANS: T d. purchases/accounts payable 18. Real time processing is used for routine transactions in large numbers. ANS: C ANS: F 2. Which system produces information used for inventory valuation, budgeting, cost control, 19. Batch processing is best used when timely information is needed because this method processes data performance reporting, and make-buy decisions? a. sales order processing efficiently. 7 0 b. purchases/accounts payable b. accounts receivable c. cash disbursements c. fixed assets d. cost accounting d. inventory ANS: D ANS: A 3. Which of the following is a turn-around document? 8. Subsidiary ledgers are used in manual accounting environments. What file is comparable to a a. remittance advice subsidiary ledger in a computerized environment? b. sales order a. archive file c. purchase order b. reference file d. payroll check c. transaction file ANS: A d. master file 4. The order of the entries made in the ledger is by ANS: D a. transaction number b. account number 9. A journal is used in manual accounting environments. What file is comparable to a journal in a c. date computerized environment? d. user a. archive file ANS: B b. reference file 5. The order of the entries made in the general journal is by c. transaction file d. master file a. date ANS: C b. account number 10. In a computerized environment, a list of authorized suppliers would be found in the c. user d. customer number a. master file ANS: A b. transaction file 6. In general a special journal would not be used to record c. reference file d. archive file a. sales ANS: C b. cash disbursements 11. Which of the following is an archive file? c. depreciation a. an accounts payable subsidiary ledger d. purchases b. a cash receipts file ANS: C 7. Which account is least likely to have a subsidiary ledger? a. sales 7 c. a sales journal d. a file of accounts receivable that have been written off 0 ANS: D a. depict logical tasks that are being performed, but not who is performing them 12. Which document is not a type of source document? b. illustrate the relationship between processes, and the documents that flow between them a. a sales order and trigger activities b. an employee time card c. a paycheck c. represent relationships between key elements of the computer system d. a sales return receipt d. describe the logic of the process ANS: C ANS: B 13. The most important purpose of a turn-around document is to a. serve as a source document 17. When determining the batch size, which consideration is the least important? a. achieving economies by grouping together large numbers of transactions b. inform a customer of the outstanding amount payable b. complying with legal mandates c. provide an audit trail for the external auditor c. providing control over the transaction process d. inform the bank of electronic funds deposits d. balancing the trade off between batch size and error detection ANS: A ANS: B 14. Which type of graphical documentation represents systems at different levels of detail? 18. In contrast to a real-time system, in a batch processing system a. data flow diagram a. there is a lag between the time when the economic event occurs and the financial records b. document flowchart c. system flowchart are updated d. program flowchart b. relatively more resources are required ANS: A 15. Data flow diagrams c. a greater resource commitment per unit of output is required a. depict logical tasks that are being performed, but not who is performing them d. processing takes place when the economic event occurs b. illustrate the relationship between processes, and the documents that flow between them ANS: A and trigger activities 19. In contrast to a batch processing system, in a real-time system c. represent relationships between key elements of the computer system a. a lag occurs between the time of the economic event and when the transaction is recorded d. describe in detail the logic of the process b. relatively fewer hardware, programming, and training resources are required ANS: A c. a lesser resource commitment per unit of output is required 16. Document flowcharts 7 0 d. processing takes place when the economic event occurs ANS: D b. turn-around document c. master document d. product document 20. The type of transaction most suitable for batch processing is ANS: C a. airline reservations 25. Which method of processing does not use the destructive update approach? b. credit authorization a. batch processing using direct access files c. payroll processing b. real-time processing d. adjustments to perpetual inventory c. batch processing using sequential files ANS: C 21. The type of transaction most suitable for realtime processing is a. recording fixed asset purchases d. all of the above use the destructive update approach ANS: C 26. Which symbol represents a data store? b. recording interest earned on long-term bonds 27. Which symbol represents a manual operation? c. adjusting prepaid insurance 28. Which symbol represents accounting records? d. recording a sale on account 29. Which symbol represents a document? ANS: D 22. Which step is not found in batch processing using sequential files? a. control totals 30. Which symbol represents a magnetic tape (sequential storage device)? 31. Which symbol represents a decision? 32. The characteristics that distinguish between batch and real-time systems include all of the following b. sort runs c. edit runs except d. immediate feedback of data entry errors a. time frame ANS: D 23. Both the revenue and the expenditure cycle can be viewed as having two key parts. These are b. resources used c. file format a. manual and computerized d. efficiency of processing b. physical and financial ANS: C c. input and output 33. A file that stores data used as a standard when processing transactions is d. batch and real-time a. a reference file ANS: B 24. All of the following can provide evidence of an economic event except b. a master file c. a transaction file d. an archive file a. source document 7 0 ANS: A c. accounts unique to many concurrent transactions need to be updated in real time. 34. Sequential storage means d. None of the above are true statements a. data is stored on tape ANS: B b. access is achieved through an index 39. Operational efficiencies can be improved by c. access is direct d. reading record 100 requires first reading records 1 to 99 a. updating accounts both common and unique to many concurrent transactions in real time. b. updating accounts both common and unique to many concurrent transactions in batch mode. ANS: D 35. Real-time processing would be most beneficial in handling a firm’s a. fixed asset records c. updating accounts unique to many concurrent transactions in real time and updating common accounts in batch mode. b. retained earning information d. None of the above are true statements c. merchandise inventory ANS: C d. depreciation records SHORT ANSWER ANS: C 1. List two of the three transaction cycles. 36. Which accounting application is least suited for batch processing? ANS: expenditure cycle, conversion cycle, revenue cycle a. general ledger 2. Documents that are created at the beginning of the transaction are called b. vendor payments __________________________. c. sales order processing ANS: source documents d. payroll ANS: C 37. Which accounting application is best suited for batch processing? 3. ______________________________________ are the two data processing approaches used in modern systems. ANS: Batch processing and real-time processing 4. Give a specific example of a turn-around document. a. general ledger b. vendor payments ANS: credit card, electricity, water, or telephone bill, etc. c. sales order processing d. payroll 5. Explain when it is appropriate to use special journals. ANS: D 38. Operational inefficiencies occur because a. accounts both common and unique to many concurrent transactions need to be updated in real time. ANS: Special journals are used to record large volumes of recurring transactions that are similar in nature. 6. What are the subsystems of the revenue cycle? ANS: sales order processing, cash receipts b. accounts common to many concurrent transactions need to be updated in real time. 7 0 7. What are the subsystems of the expenditure cycle? ANS: time lag, resource use, efficiency 16. Give one advantages of real-time data collection. ANS: purchasing, cash disbursements, payroll 8. Most organizations have replaced the general journal with a _______________________________. ANS: journal voucher system 9. Provide a specific example of a general ledger account and a corresponding subsidiary ledger. ANS: certain transaction errors can be prevented or detected and corrected at their source. 17. In one sentence, what does updating a master file record involve? ANS: Updating a master file record involves changing the value of one or more of its variable fields to reflect the effects of a transaction. ANS: accounts receivable control account and accounts receivable subsidiary, accounts payable control account and accounts payable subsidiary, inventory control and a subsidiary of specific inventory 18. What is destructive update? ANS: Destructive update involves replacing an old data value with a new value and thus destroying the original. items, fixed asset control account and a subsidiary of specific fixed assets, notes receivable/payable Chapter 3—Ethics, Fraud, and Internal Control and individual notes receivable and payable TRUE/FALSE 10. Name five documentation techniques? 1. The ethical principle of justice asserts that the benefits of the decision should be distributed fairly to those who share the risks. ANS: entity-relationship diagrams, data flow diagrams, document flowcharts, system flowcharts, program flowcharts ANS: T 2. The ethical principle of informed consent suggests that the decision should be implemented so as to minimize all of the risks and to avoid any unnecessary risks. 11. Why is the audit trail important? ANS: The audit trail is used to track transactions from the source document to the financial statements and vice versa. Accountants use the audit trail to correct errors, answer queries, and perform audits. ANS: F 12. List a method of data processing that uses the destructive update approach? ANS: batch method using direct access files or realtime processing 3. Employees should be made aware of the firm’s commitment to ethics. ANS: T 13. Only four symbols are used in data flow diagrams. What are they? 4. Business ethics is the analysis of the nature and social impact of computer technology, and the corresponding formulation and justification of policies for the ethical use of such technology. ANS: process, data store, data flow, entity ANS: F 14. Which flowchart depicts the relationship between processes and the documents that flow between them and trigger activities? 5. Para computer ethics is the exposure to stories and reports found in the popular media regarding the good or bad ramifications of computer technology. ANS: document flowcharts ANS: F 15. What are the three characteristics that are used to distinguish between batch and real-time systems. 7 6. Source code is an example of intellectual property. 0 ANS: T ANS: F 7. Copyright laws and computer industry standards have been developed jointly and rarely conflict. 19. A key modifying assumption in internal control is that the internal control system is the responsibility of management. ANS: F ANS: T 8. Business bankruptcy cases always involve fraudulent behavior. 20. Database management fraud includes altering, updating, and deleting an organization’s data. ANS: F ANS: F 9. Defalcation is another word for financial fraud. 10. The trend toward distributed data processing increases the exposure to fraud from remote locations. 21. While the Sarbanes-Oxley Act prohibits auditors from providing non-accounting services to their audit clients, they are not prohibited from performing such services for non-audit clients or privately held ANS: T companies. 11. The external auditor is responsible for establishing and maintaining the internal control system. ANS: T ANS: F ANS: T ANS: T 22. The Sarbanes-Oxley Act requires the audit committee to hire and oversee the external auditors. 12. Segregation of duties is an example of an internal control procedure. ANS: T 13. Controls in a computer-based information system are identical to controls in a manual system. ANS: F 14. Preventive controls are passive techniques designed to reduce fraud. 23. Section 404 requires that corporate management (including the CEO) certify their organization’s internal controls on a quarterly and annual basis. ANS: F 24. Section 302 requires the management of public companies to assess and formally report on the effectiveness of their organization’s internal controls. ANS: F ANS: T 15. Ethical issues and legal issues are essentially the same. 25. The objective of SAS 99 is to seamlessly blend the auditor’s consideration of fraud into all phases of the audit process. ANS: F ANS: T 16. Internal control systems are recommended but not required of firms subject to the Foreign Corrupt Practices Act. MULTIPLE CHOICE ANS: F 17. Operations fraud is the misuse or theft of the firm’s computer resources. 1. Which ethical principle states that the benefit from a decision must outweigh the risks, and that there is no alternative decision that provides the same or greater benefit with less risk? a. minimize risk ANS: T b. justice 18. The Foreign Corrupt Practices Act requires only that a firm keep good records. c. informed consent 7 0 d. proportionality a. is perpetrated at a level to which internal controls do not apply ANS: D b. involves misstating financial statements 2. Individuals who acquire some level of skill and knowledge in the field of computer ethics are involved in which level of computer ethics? c. involves the direct conversion of cash or other assets to the employee’s personal benefit a. para computer ethics d. involves misappropriating assets in a series of complex transactions involving third parties b. pop computer ethics ANS: C c. theoretical computer ethics d. practical computer ethics 7. Forces which may permit fraud to occur do not include ANS: A a. a gambling addiction 3. All of the following are issues of computer security except b. lack of segregation of duties a. releasing incorrect data to authorized individuals b. permitting computer operators unlimited access to the computer room c. permitting access to data by unauthorized individuals c. centralized decision making environment d. questionable integrity of employees ANS: C 8. Which of the following best describes lapping? d. providing correct data to unauthorized individuals ANS: B a. applying cash receipts to a different customer’s account in an attempt to conceal previous thefts of funds b. inflating bank balances by transferring money among different bank accounts 4. Which characteristic is not associated with software as intellectual property? c. expensing an asset that has been stolen a. uniqueness of the product d. creating a false transaction b. possibility of exact replication ANS: A c. automated monitoring to detect intruders 9. Operations fraud includes d. ease of dissemination ANS: C a. altering program logic to cause the application to process data incorrectly 5. For an action to be called fraudulent, all of the following conditions are required except b. misusing the firm’s computer resources a. poor judgment c. destroying or corrupting a program’s logic using a computer virus b. false representation c. intent to deceive d. creating illegal programs that can access data files to alter, delete, or insert values d. injury or loss ANS: B ANS: A 10. Who is responsible for establishing and maintaining the internal control system? 6. One characteristic of employee fraud is that the fraud a. the internal auditor 7 0 b. the accountant d. comparing the accounts receivable subsidiary ledger to the control account c. management ANS: A d. the external auditor ANS: C 15. A well-designed purchase order is an example of a 11. The concept of reasonable assurance suggests that a. preventive control a. the cost of an internal control should be less than the benefit it provides b. a well-designed system of internal controls will detect all fraudulent activity b. detective control c. corrective control d. none of the above ANS: A c. the objectives achieved by an internal control system vary depending on the data processing method 16. A physical inventory count is an example of a d. the effectiveness of internal controls is a function of the industry environment b. detective control a. preventive control c. corrective control ANS: A 12. Which of the following is not a limitation of the internal control system? a. errors are made due to employee fatigue b. fraud occurs because of collusion between two employees d. feedforward control ANS: B 17. The bank reconciliation uncovered a transposition error in the books. This is an example of a a. preventive control c. the industry is inherently risky d. management instructs the bookkeeper to make fraudulent journal entries b. detective control c. corrective control ANS: C d. none of the above 13. The most cost-effective type of internal control is ANS: B a. preventive control b. accounting control 18. In balancing the risks and benefits that are part of every ethical decision, managers receive guidance from each of the following except c. detective control a. justice d. corrective control b. self interest ANS: A c. risk minimization 14. Which of the following is a preventive control? d. proportionality a. credit check before approving a sale on account ANS: B b. bank reconciliation 19. Which of the following is not an element of the internal control environment? c. physical inventory count a. management philosophy and operating style 7 0 a. to avoid collusion between the programmer and the computer operator b. organizational structure of the firm c. well-designed documents and records d. the functioning of the board of directors and the audit committee ANS: C 20. Which of the following suggests a weakness in the internal control environment? a. the firm has an up-to-date organizational chart b. monthly reports comparing actual performance to budget are distributed to managers c. performance evaluations are prepared every three years b. to ensure that supervision is not required c. to prevent the record keeper from authorizing transactions d. to enable the firm to function more efficiently ANS: C 24. Segregation of duties in the computer-based information system includes a. separating the programmer from the computer operator b. preventing management override d. the audit committee meets quarterly with the external auditors c. separating the inventory process from the billing process ANS: C d. performing independent verifications by the computer operator 21. Which of the following indicates a strong internal control environment? ANS: A a. the internal audit group reports to the audit committee of the board of directors 25. Which of the following is not an internal control procedure? b. there is no segregation of duties between organization functions a. authorization b. management’s operating style c. there are questions about the integrity of management c. independent verification d. adverse business conditions exist in the industry d. accounting records ANS: A ANS: B 22. According to SAS 78, an effective accounting system performs all of the following except 26. The decision to extend credit beyond the normal credit limit is an example of a. independent verification a. identifies and records all valid financial transactions b. authorization b. records financial transactions in the appropriate accounting period c. segregation of functions d. supervision c. separates the duties of data entry and report generation ANS: B 27. When duties cannot be segregated, the most important internal control procedure is d. records all financial transactions promptly ANS: C a. supervision 23. Which of the following is the best reason to separate duties in a manual system? b. independent verification c. access controls 7 0 d. accounting records 32. The board of directors consists entirely of personal friends of the chief executive officer. This indicates a weakness in ANS: A 28. An accounting system that maintains an adequate audit trail is implementing which internal control procedure? a. the accounting system b. the control environment a. access controls c. control procedures b. segregation of functions d. this is not a weakness c. independent verification ANS: B d. accounting records 33. Computer fraud can take on many forms, including each of the following except ANS: D a. theft or illegal use of computer-readable information 29. Employee fraud involves three steps. Of the following, which is not involved? b. theft, misuse, or misappropriation of computer equipment a. concealing the crime to avoid detection b. stealing something of value c. theft, misuse, or misappropriation of assets by altering computer-readable records and files c. misstating financial statements d. theft, misuse, or misappropriation of printer supplies d. converting the asset to a usable form ANS: C ANS: D 30. Which of the following is not an example of independent verification? a. comparing fixed assets on hand to the accounting records b. performing a bank reconciliation c. comparing the accounts payable subsidiary ledger to the control account 34. When certain customers made cash payments to reduce their accounts receivable, the bookkeeper embezzled the cash and wrote off the accounts as uncollectible. Which control procedure would most likely prevent this irregularity? a. segregation of duties b. accounting records c. accounting system d. permitting authorized users only to access the accounting system d. access controls ANS: D ANS: A 31. The importance to the accounting profession of the Foreign Corrupt Practices Act of 1977 is that a. bribery will be eliminated b. management will not override the company’s internal controls 35. The office manager forgot to record in the accounting records the daily bank deposit. Which control procedure would most likely prevent or detect this error? a. segregation of duties b. independent verification c. firms are required to have an effective internal control system c. accounting records d. firms will not be exposed to lawsuits d. supervision ANS: C ANS: B 7 0 36. Business ethics involves c. management override a. how managers decide on what is right in conducting business d. stability of systems ANS: D b. how managers achieve what they decide is right for the business c. both a and b d. none of the above 41. Management can expect various benefits to follow from implementing a system of strong internal control. Which of the following benefits is least likely to occur? a. reduced cost of an external audit. ANS: C b. prevents employee collusion to commit fraud. 37. All of the following are conditions for fraud except c. availability of reliable data for decision-making purposes. a. false representation d. some assurance of compliance with the Foreign Corrupt Practices Act of 1977. b. injury or loss c. intent d. material reliance e. some assurance that important documents and records are protected. ANS: D ANS: B 38. The four principal types of fraud include all of the following except 42. Which of the following situations is not a segregation of duties violation? a. bribery a. The treasurer has the authority to sign checks but gives the signature block to the assistant treasurer to run the check-signing machine. b. gratuities c. conflict of interest b. The warehouse clerk, who has the custodial responsibility over inventory in the warehouse, selects the vendor and authorizes purchases when inventories are low. d. economic extortion ANS: B 39. The characteristics of useful information include a. summarization, relevance, timeliness, accuracy, and completeness b. relevance, summarization, accuracy, timelessness, and completeness c. timeliness, relevance, summarization, accuracy, and conciseness d. disaggregation, relevance, timeliness, accuracy, and completeness ANS: A c. The sales manager has the responsibility to approve credit and the authority to write off accounts. d. The department time clerk is given the undistributed payroll checks to mail to absent employees. e. The accounting clerk who shares the record keeping responsibility for the accounts receivable subsidiary ledger performs the monthly reconciliation of the subsidiary ledger and the control account. ANS: B 40. Internal control system have limitations. These include a. possibility of honest error 43. Which of the following is not an issue to be addressed in a business code of ethics required by the SEC? b. circumvention a. Conflicts of interest 7 0 b. Full and Fair Disclosures c. locking the warehouse c. Legal Compliance d. preparing a trial balance d. Internal Reporting of Code Violations e. counting inventory e. All of the above are issues to be addressed ANS: A. preventive; B. detective; C. preventive; D. detective; E. detective ANS: E SHORT ANSWER Use the internal control procedures listed below to complete the statements. 1. What are the main issues to be addressed in a business code of ethics required by the SEC? segregation of duties ANS: Conflicts of interest, Full and Fair Disclosures, Legal Compliance, Internal Reporting of Code Violations, Accountability 2. List the four broad objectives of the internal control system. specific authorization general authorization accounting records access controls independent verification ANS: safeguard assets, ensure the accuracy and reliability of accounting records, promote organizational efficiency, comply with management’s policies and procedures supervision 7. A clerk reorders 250 items when the inventory falls below 25 items. This is an example of __________________________. 3. Explain the purpose of the PCAOB ANS: The PCAOB is empowered to set auditing, quality control, and ethics standards; to inspect registered accounting firms; to conduct investigations; and to take disciplinary actions. ANS: general authorization 8. The internal audit department recalculates payroll for several employees each pay period. This is an example of __________________________. 4. What are the five internal control components described in the SAS 78 / COSO framework ANS: independent verification ANS: the control environment, risk assessment, information and communication, monitoring, and control activities 5. What are management responsibilities under section 302 and 404? ANS: Section 302 requires that corporate management (including the CEO) certify their organization’s internal controls on a quarterly and annual basis. Section 404 requires the management of public companies to assess and formally report on the effectiveness of their organization’s internal controls. 6. Identify to indicate whether each procedure is a preventive or detective control. 9. Locking petty cash in a safe is an example of __________________________. ANS: access controls 10. Approving a price reduction because goods are damaged is an example of __________________________. ANS: specific authorization 11. Using cameras to monitor the activities of cashiers is an example of __________________________. ANS: supervision a. authorizing a credit sale 12. Not permitting the computer programmer to enter the computer room is an example of _______________________________. b. preparing a bank reconciliation ANS: segregation of duties 7 0 13. Sequentially numbering all sales invoices is an example of __________________________. the stolen check. This is in effect a small scale Ponzi scheme. ANS: accounting records 20. What are the six broad classes of physical control activities defined by SAS 78? 14. What are the five conditions necessary for an act to be considered fraudulent? ANS: false representation, material fact, intent, justifiable reliance, and injury or loss ANS: Transaction authorization, segregation of duties, supervision, access controls, accounting records, independent verification Chapter 4—The Revenue Cycle 15. What is the objective of SAS 99? ANS: The objective of SAS 99 is to seamlessly blend the auditor’s consideration of fraud into all phases of the audit process. TRUE/FALSE 1. The packing slip is also known as the shipping notice. 16. Distinguish between exposure and risk. ANS: F ANS: Exposure is the absence or weakness of a control which increases the firm’s risk of financial loss or injury. Risk is the probability of incurring such a loss or injury. 2. The bill of lading is a legal contract between the buyer and the seller. 17. Explain the characteristics of management fraud. 3. Another name for the stock release form is the picking ticket. ANS: Management fraud typically occurs at levels above where the internal control system is effective. Financial statements are frequently modified to make the firm appear more healthy than it actually is. If any misappropriation of assets occurs, it is usually well hidden. ANS: F ANS: T 4. Warehouse stock records are the formal accounting records for inventory. ANS: F 5. The purpose of the invoice is to bill the customer. ANS: T 18. The text discusses many questions about personal traits of employees which might help uncover fraudulent activity. What are three? 6. In most large organizations, the journal voucher file has replaced the formal general journal. ANS: executives: with high personal debt, living beyond their means, engaged in habitual gambling, appear to abuse alcohol or drugs, appear to lack personal codes of ethics, appear to be unstable 19. Give two examples of employee fraud and explain how the theft might occur. ANS: T 7. The cash receipts journal is a special journal. ANS: T 8. In the revenue cycle, the internal control “limit access” applies to physical assets only. ANS: Charges to expense accounts: Cash could be stolen and charged to a miscellaneous expense account. Once the account is closed, detection would be more difficult. Lapping: This involves converting cash receipts to personal use. If a customer’s check is taken, his/her balance will not reflect a payment and will be detected when a statement is sent. In order to conceal this fraud, a later payment is used to cover 7 ANS: F 9. In real-time processing systems, routine credit authorizations are automated. ANS: T 10. In a computerized accounting system, segregation of functions refers to inventory control, accounts receivable, billing, and general ledger tasks. 0 ANS: F 11. A written customer purchase order is required to trigger the sales order system. d. three subsystems –sales order processing, credit authorization, and cash receipts ANS: B 2. The reconciliation that occurs in the shipping department is intended to ensure that ANS: F 12. Inventory control has physical custody of inventory. a. credit has been approved ANS: F 13. The principal source document in the sales order system is the sales order. ANS: T 14. Sales orders should be prenumbered documents. b. the customer is billed for the exact quantity shipped c. the goods shipped match the goods ordered d. inventory records are reduced for the goods shipped ANS: C ANS: T 3. The adjustment to accounting records to reflect the decrease in inventory due to a sale occurs in the 15. Integrated accounting systems automatically transfer data between modules. a. warehouse ANS: T 16. If a customer submits a written purchase order, there is no need to prepare a sales order. b. shipping department c. billing department ANS: F d. inventory control department 17. Sales return involves receiving, sales, credit, and billing departments, but not accounts receivable. ANS: D ANS: F 4. Which document triggers the revenue cycle? a. the sales order 18. A remittance advice is a form of turn-around document. b. the customer purchase order c. the sales invoice ANS: T 19. A bill of lading is a request for payment for shipping charges. d. the journal voucher ANS: F 5. Copies of the sales order can be used for all of the following except ANS: B 20. In point of sale systems, authorization takes the form of validation of credit card charges. a. purchase order ANS: T b. credit authorization MULTIPLE CHOICE c. shipping notice 1. The revenue cycle consists of d. packing slip a. one subsystem–order entry ANS: A b. two subsystems–sales order processing and cash receipts 6. The purpose of the sales invoice is to c. two subsystems –order entry and inventory control 7 a. record reduction of inventory 0 b. transfer goods from seller to shipper a. the customer purchase order is received c. bill the customer b. the backordered goods are shipped d. select items from inventory for shipment c. the original goods are shipped ANS: C d. customers are not billed for backorders because a backorder is a lost sale 7. The customer open order file is used to ANS: B a. respond to customer queries 12. Usually specific authorization is required for all of the following except b. fill the customer order c. ship the customer order a. sales on account which exceed the credit limit d. authorize customer credit b. sales of goods at the list price ANS: A c. a cash refund for goods returned without a receipt 8. The stock release copy of the sales order is not used to d. write off of an uncollectible account receivable ANS: B a. locate and pick the items from the warehouse shelves 13. Which of following functions should be segregated? b. record any out-of-stock items c. authorize the warehouse clerk to release custody of the inventory to shipping a. opening the mail and making the journal entry to record cash receipts b. authorizing credit and determining reorder quantities d. record the reduction of inventory ANS: D c. maintaining the subsidiary ledgers and handling customer queries 9. The shipping notice a. is mailed to the customer d. providing information on inventory levels and reconciling the bank statement b. is a formal contract between the seller and the shipping company ANS: A c. is always prepared by the shipping clerk 14. Which situation indicates a weak internal control structure? d. informs the billing department of the quantities shipped a. the mailroom clerk authorizes credit memos ANS: D b. the record keeping clerk maintains both accounts receivable and accounts payable 10. The billing department is not responsible for subsidiary ledgers a. updating the inventory subsidiary records c. the warehouse clerk obtains a signature before releasing goods for shipment b. recording the sale in the sales journal c. notifying accounts receivable of the sale d. the accounts receivable clerk prepares customer statements every month d. sending the invoice to the customer ANS: A ANS: A 11. Customers should be billed for backorders when 7 15. The most effective internal control procedure to prevent or detect the creation of fictitious credit 0 memoranda for sales returns is to a. all sales are profitable a. supervise the accounts receivable department b. all sales are recorded b. limit access to credit memoranda c. credit is authorized c. prenumber and sequence check all credit memoranda d. inventory to be shipped is not stolen ANS: A d. require management approval for all credit memoranda 20. Which control does not help to ensure that accurate records are kept of customer accounts and inventory? ANS: D 16. The accounts receivable clerk destroys all invoices for sales made to members of her family and does not record the sale in the accounts receivable subsidiary ledger. Which procedure will not detect this fraud? a. prenumber and sequence check all invoices a. reconcile accounts receivable control to accounts receivable subsidiary b. authorize credit c. segregate custody of inventory from record keeping b. reconcile the accounts receivable control to the accounts receivable subsidiary ledger d. segregate record keeping duties of general ledger from accounts receivable c. prepare monthly customer statements ANS: B d. reconcile total sales on account to the debits in the accounts receivable subsidiary ledger 21. Internal controls for handling sales returns and allowances do not include ANS: C a. computing bad debt expense using the percentage of credit sales 17. Which department is least likely to be involved in the revenue cycle? b. verifying that the goods have been returned c. authorizing the credit memo by management a. credit d. using the original sales invoice to prepare the sales returns slip b. accounts payable c. billing ANS: A d. shipping 22. The printer ran out of preprinted sales invoice forms and several sales invoices were not printed. The best internal control to detect this error is ANS: B 18. Which document is included with a shipment sent to a customer? a. sales invoice a. a batch total of sales invoices to be prepared compared to the actual number of sales invoices prepared b. stock release form b. sequentially numbered sales invoices c. packing slip d. shipping notice c. visual verification that all sales invoices were prepared ANS: C d. none of the above will detect this error 19. Good internal controls in the revenue cycle should ensure all of the following except ANS: A 23. Which department prepares the bill of lading? 7 0 a. sales ANS: D b. warehouse 28. A cash prelist is c. shipping a. a document that records sales returns and allowances d. credit b. a document returned by customers with their payments ANS: C 24. A remittance advice is a. used to increase (debit) an account receivable by the cash received b. is a turn-around document c. the source of information used to prepare monthly statements d. none of the above ANS: D c. is retained by the customer to show proof of payment 29. An advantage of real-time processing of sales is a. the cash cycle is lengthened d. none of the above b. current inventory information is available ANS: B 25. A weekly reconciliation of cash receipts would include comparing c. hard copy documents provide a permanent record of the transaction a. the cash prelist with bank deposit slips d. data entry errors are corrected at the end of each batch b. the cash prelist with remittance advices ANS: B c. bank deposit slips with remittance advices d. journal vouchers from accounts receivable and general ledger 30. Commercial accounting systems have fully integrated modules. The word “integrated” means that ANS: A a. segregation of duties is not possible 26. At which point is supervision most critical in the cash receipts system? b. transfer of information among modules occurs automatically a. accounts receivable c. batch processing is not an option b. general ledger d. separate entries are made in the general ledger accounts and the subsidiary ledgers c. mail room ANS: B d. cash receipts 31. The data processing method that can shorten the cash cycle is ANS: C 27. EDI trading partner agreements specify all of the following except a. selling price a. batch, sequential file processing b. batch, direct access file processing c. real-time file processing b. quantities to be sold d. none of the above c. payment terms ANS: C d. person to authorize transactions 7 0 32. Which of the following is not a risk exposure in a microcomputer accounting system? a. reliance on paper documentation is increased b. functions that are segregated in a manual environment may be combined in a microcomputer accounting system d. a memo prepared in the mailroom ANS: C 37. The revenue cycle utilizes all of the following files except a. credit memo file c. backup procedures require human intervention b. sales history file d. data are easily accessible c. shipping report file d. cost data reference file ANS: A 33. Which journal is not used in the revenue cycle? ANS: D 38. All of the following are advantages of real-time processing of sales except a. cash receipts journal b. sales journal a. The cash cycle is shortened c. purchases journal b. Paper work is reduced d. general journal c. Incorrect data entry is difficult to detect ANS: C d. Up-to-date information can provide a competitive advantage in the marketplace 34. Periodically, the general ledger department receives all of the following except ANS: C a. total increases to accounts receivable SHORT ANSWER b. total of all sales backorders 1. Distinguish between a packing slip, shipping notice, and a bill of lading. c. total of all sales ANS: The packing slip travels with the goods to the customer, and it describes the contents on the order. d. total decreases in inventory ANS: B 35. The credit department a. prepares credit memos when goods are returned b. approves credits to accounts receivable when payments are received c. authorizes the granting of credit to customers Upon filling the order, the shipping department sends the shipping notice to the billing department to notify them that the order has been filled and shipped. The shipping notice contains additional information that the packing slip may not contain, such as shipment date, carrier and freight charges. ANS: C The bill of lading is a formal contract between the seller and the transportation carrier; it shows legal ownership and responsibility for assets in transit. 36. Adjustments to accounts receivable for payments received from customers is based upon 2. State two specific functions or jobs that should be segregated in the sales processing system. a. the customer’s check ANS: sales order processing and credit approval; inventory control (record keeping) from warehouse (custody); and general ledger from accounts receivable subsidiary ledger d. none of the above b. the cash prelist c. the remittance advice that accompanies payment 7 0 3. State two specific functions or jobs that should be segregated in the cash receipts system. ANS: cash receipts (custody) from accounts receivable (record keeping); and general ledger from accounts receivable subsidiary ledger mail room (receiving cash) and accounts receivable subsidiary ledger 4. List two points in the sales processing system when authorization is required. ANS: credit check, sales returns policy, preparation of cash prelist 5. For the revenue cycle, state two specific independent verifications that should be performed. ANS: shipping verifies that the goods sent from the warehouse are correct in type and quantity; billing reconciles the shipping notice with the sales order to ensure that customers are billed only for the quantities shipped; general ledger reconciles journal vouchers submitted by the billing department (sales journal), inventory control (inventory subsidiary ledger), and cash receipts (cash receipts journal) treasurer determines that all cash received got to the bank 6. What task can the accounts receivable department engage in to verify that all checks sent by the customers have been appropriately deposited and recorded? ANS: The company should periodically, perhaps monthly, send an account summary to each customer listing invoices and amounts paid by check number and date. This form allows the customer to verify the accuracy of the records. If any payments are not recorded, they will notify the company of the discrepancy. These reports should not be handled by the accounts receivable clerk or the cashier. 7. What specific internal control procedure would prevent the sale of goods on account to a fictitious customer? ANS: credit check procedure that would prevent or detect this fraud. ANS: supervision (two people) when opening the mail; customer complaints when monthly statements mailed 9. A customer payment of $247 was correctly posted in the general ledger but was recorded as $274 in the customer’s account receivable. Describe a specific internal control procedure that would detect this error. ANS: reconcile the accounts receivable control account to the accounts receivable subsidiary ledger; compare control totals of cash received with total credits to A/R subsidiary ledger 10. Goods are shipped to a customer, but the shipping department does not notify billing and the customer never receives an invoice. Describe a specific internal control procedure that would detect this error. ANS: Billing department matches the stock release copy of the sales order (from shipping) to the invoice, ledger, and file copies of the sales order (sent directly to billing), and then mails the invoice to the customer. After a certain amount of time has passed, the billing department should investigate any unmatched invoice, ledger, and file copies of the sales order. 11. A clerk embezzles customer payments on account and covers up the theft by making an adjustment to the accounts receivable ledger. Describe a specific internal control procedure that would prevent this fraud. ANS: segregation of duties; do not let one person have custody of payments and the ability to make adjustments to the records; all adjustments to accounts receivable records must be authorized 12. A credit sale is made to a customer, even though the customer’s account is four months overdue. Describe a specific internal control procedure that would prevent this from happening. ANS: perform a credit check and require management approval for all sales to accounts that are overdue 13. What specific internal control procedure would prevent a customer from being billed for all 50 items ordered although only 40 items were shipped? 8. The clerk who opens the mail routinely steals remittances. Describe a specific internal control 7 0 ANS: billing should reconcile the shipping report with the sales order 14. What specific internal control procedure would prevent the shipping clerk from taking goods from the storeroom and sending them to someone who had not placed an order? ANS: shipping clerk should not have access to the storeroom 15. What specific internal control procedure would prevent an accounts receivable clerk from issuing a fictitious credit memo to a customer (who is also a relative) for goods that were “supposedly” returned from previous sales? ANS: credit memo should be authorized after verifying the return of goods based on evidence from the person who received the goods 3. The organization structure should be such that the perpetration of a fraud requires collusion between 2 or more individuals. 20. What is automation and why is it used? ANS: Automation involves using technology to improve the efficiency and effectiveness of a task. Automation of the revenue cycle is typically used to reduce overhead costs, make better credit granting decisions, and better collect outstanding accounts receivable. 21. What is the objective of re-engineering? ANS: The objective of re-engineering is to greatly reduce costs by identifying and eliminating non value-added tasks and also by streamlining necessary existing processes. 16. What specific internal control procedure would prevent an increase in sales returns since salesmen were placed on commission? 22. What are the key segregation of duties related to computer programs that process accounting transactions. ANS: customer credit should be verified by the credit department reduce commissions for sales returns ANS: Response: The tasks of design, maintenance, and operation of computer programs need to be segregated. The programmers who write the original computer programs should not also be responsible for making program changes. Both of these functions must also be separate from the daily task of operating the system. 17. What specific internal control procedure would detect the misplacement of a sales invoice after preparation and not mailed to the customer? The invoice was never found. ANS: all documents should be prenumbered 18. What function does the receiving department serve in the revenue cycle? ANS: The receiving department counts and inspects items which are returned by customers. The receiving department prepares a return slip of which a copy goes to the warehouse for restocking, and a copy goes to the sales order department so that a credit memo can be issued to the customer. 19. What are the three rules that ensure that no single employee or department processes a transaction in its entirety. 23. How is EDI more than technology? What unique control problems may it pose? ANS: EDI represents a unique business arrangement between the buyer and seller in which they agree, in advance, to the terms of their relationship on such items as selling price, quantities, delivery times, payment terms and methods of handling disputes. The terms of agreement are binding. One problem is ensuring that only valid transactions are processed. Another risk is that a non-trading partner will masquerade as a trading partner and access the firm's processing systems. 24. What makes point-of-sales systems different from revenue cycles of manufacturing firms? ANS: The three rules that ensure segregation of functions are: ANS: In point-of-sale systems, the customer literally has possession of the items purchased, thus the inventory is in hand. Typically, for manufacturing firms, the order is placed and the good is shipped to the customer at some later time period. Thus, updating inventory at the time of sale is necessary in 1. Transaction authorization should be separate from transaction processing 2. Asset custody should be separate from asset record keeping. 7 0 point-of-sale systems since the inventory is changing hands, while it is not necessary in manufacturing firms until the goods are actually shipped to the customer. 7. 25. Give three examples of Access Control in a Pointof-Sale (POS) system. 8. ANS: Lock on the cash drawer Internal cash register tape that can be accessed only by the manager Physical security over the inventory. The following are examples: Steel cables to secure expensive leather coats to the clothing rack. Locked showcases to display jewelry and costly electronic equipment. Magnetic tags attached to merchandise, which will sound an alarm when removed from the store. Note to Instructor: Some physical security devices could also be classified as supervision Chapter 5—The Expenditure Cycle Part I: Purchases and Cash Disbursements Procedures 10. 11. 12. 13. TRUE/FALSE 1. 9. 14. Purchasing decisions are authorized by inventory control. 15. ANS: T 2. 3. 4. 5. 6. The blind copy of the purchase order that goes to the receiving department contains no item descriptions. ANS: F Firms that wish to improve control over cash disbursements use a voucher system. ANS: T In a voucher system, the sum of all unpaid vouchers in the voucher register equals the firm’s total voucher payable balance. ANS: T The accounts payable department reconciles the accounts payable subsidiary ledger to the control account. ANS: F The use of inventory reorder points suggests the need to obtain specific authorization. ANS: F 7 16. 17. 18. 19. 20. 0 Proper segregation of duties requires that the responsibility approving a payment be separated from posting to the cash disbursements journal. ANS: T A major risk exposure in the expenditure cycle is that accounts payable may be overstated at the end of the accounting year. ANS: F When a trading partner agreement is in place, the traditional three way match may be eliminated. ANS: T Authorization of purchases in a merchandising firm occurs in the inventory control department. ANS: T A three way match involves a purchase order, a purchase requisition, and an invoice. ANS: F Authorization for a cash disbursement occurs in the cash disbursement department upon receipt of the supplier’s invoice. ANS: F An automated cash disbursements system can yield better cash management since payments are made on time. ANS: T Permitting warehouse staff to maintain the only inventory records violates separation of duties. ANS: T A purchasing system that employs electronic data interchange does not use a purchase order. ANS: F Inventory control should be located in the warehouse. ANS: F Inspection of shipments in the receiving department would be improved if the documentation showed the value of the inventory. ANS: F One reason for authorizing purchases is to enable efficient inventory management. ANS: T If accounts payable receives an invoice directly from the supplier it needs to be reconciled with the purchase order and receiving report. ANS: T Supervision in receiving is intended to reduce the theft of assets. ANS: T MULTIPLE CHOICE d. the quantity of items received 1. The purpose of the purchase requisition is to ANS: C a. order goods from vendors 6. The purchase order b. record receipt of goods from vendors a. is the source document to make an entry into the accounting records c. authorize the purchasing department to order goods b. indicates item description, quantity, and price d. bill for goods delivered c. is prepared by the inventory control department ANS: C d. is approved by the end-user department 2. The purpose of the receiving report is to ANS: B a. order goods from vendors 7. The reason that a blind copy of the purchase order is sent to receiving is to b. record receipt of goods from vendors a. inform receiving when a shipment is due c. authorize the purchasing department to order goods b. force a count of the items delivered d. bill for goods delivered c. inform receiving of the type, quantity, and price of items to be delivered ANS: B 3. All of the following departments have a copy of the purchase order except d. require that the goods delivered are inspected ANS: B a. the purchasing department 8. The receiving report is used to b. the receiving department a. accompany physical inventories to the storeroom or warehouse c. accounts payable b. advise the purchasing department of the dollar value of the goods delivered d. general ledger ANS: D 4. The purpose of the purchase order is to c. advise general ledger of the accounting entry to be made a. order goods from vendors d. advise the vendor that the goods arrived safely b. record receipt of goods from vendors ANS: A c. authorize the purchasing department to order goods 9. When a copy of the receiving report arrives in the purchasing department, it is used to d. approve payment for goods received a. adjust perpetual inventory records ANS: A b. record the physical transfer of inventory from receiving to the warehouse 5. The open purchase order file in the purchasing department is used to determine c. analyze the receiving department’s process a. the quality of items a vendor ships d. recognize the purchase order as closed b. the best vendor for a specific item ANS: D c. the orders that have not been received 10. The financial value of a purchase is determined by reviewing the 7 0 a. packing slip 15. Because of time delays between receiving inventory and making the journal entry b. purchase requisition a. liabilities are usually understated c. receiving report b. liabilities are usually overstated d. supplier’s invoice c. liabilities are usually correctly stated ANS: D d. none of the above 11. Which document is least important in determining the financial value of a purchase? ANS: A 16. Usually the open voucher payable file is organized by a. purchase requisition b. purchase order a. vendor c. receiving report b. payment due date d. supplier’s invoice c. purchase order number ANS: A d. transaction date 12. In a merchandising firm, authorization for the payment of inventory is the responsibility of ANS: B a. inventory control 17. Which of the following statements is not correct? b. purchasing a. the voucher system is used to improve control over cash disbursements c. accounts payable b. the sum of the paid vouchers represents the voucher payable liability of the firm d. cash disbursements ANS: C c. the voucher system permits the firm to consolidate payments of several invoices on one voucher 13. In a merchandising firm, authorization for the purchase of inventory is the responsibility of d. many firms replace accounts payable with a voucher payable system a. inventory control b. purchasing ANS: B c. accounts payable 18. In the expenditure cycle, general ledger does not d. cash disbursements a. post the journal voucher from the accounts payable department ANS: A 14. When purchasing inventory, which document usually triggers the recording of a liability? a. purchase requisition b. post the account summary from inventory control c. post the journal voucher from the purchasing department d. reconcile the inventory control account with the inventory subsidiary summary b. purchase order c. receiving report ANS: C d. supplier’s invoice 19. The documents in a voucher packet include all of the following except ANS: D 7 0 a. a check ANS: C b. a purchase order 24. Of the following duties, it is most important to separate c. a receiving report a. warehouse from stores d. a supplier’s invoice b. warehouse from inventory control ANS: A 20. To maintain a good credit rating and to optimize cash management, cash disbursements should arrive at the vendor’s place of business a. as soon as possible c. accounts payable and accounts receivable d. purchasing and accounts receivable ANS: B b. on the due date 25. In a firm with proper segregation of duties, adequate supervision is most critical in c. on the discount date a. purchasing d.by the end of the month b. receiving ANS: C c. accounts payable 21. The cash disbursement clerk performs all of the following tasks except d. general ledger ANS: B a. reviews the supporting documents for completeness and accuracy 26. The receiving department is not responsible to b. prepares checks a. inspect shipments received b. count items received from vendors c. signs checks d. marks the supporting documents paid c. order goods from vendors ANS: C d. safeguard goods until they are transferred to the warehouse 22. When a cash disbursement in payment of an accounts payable is recorded ANS: C b. the income statement is changed 27. The major risk exposures associated with the receiving department include all of the following except c. the cash account is unchanged a. goods are accepted without a physical count d. the liability account is decreased b. there is no inspection for goods damaged in shipment a. the liability account is increased ANS: D c. inventories are not secured on the receiving dock 23. Authorization for payment of an accounts payable liability is the responsibility of d. the audit trail is destroyed a. inventory control ANS: D b. purchasing c. accounts payable 28. When searching for unrecorded liabilities at the end of an accounting period, the accountant would search all of the files except d. cash disbursements a. the purchase requisition file 7 0 b. the cash receipts file b. all checks signed by check-signing equipment c. the purchase order file c. checks over a certain dollar amount manually signed by the treasurer d. the receiving report file ANS: B d. checks over a certain dollar amount manually signed by the cash disbursements clerk 29. In regards to the accounts payable department, which statement is not true? ANS: C 33. The document which will close the open purchase requisition file is the a. the purchase requisition shows that the transaction was authorized b. the purchase order proves that the purchase was required a. purchase order b. vendor invoice c. receiving report c. the receiving report provides evidence of the physical receipt of the goods d. none of the above d. the supplier’s invoice indicates the financial value of the transaction ANS: C ANS: B 34. Goods received are inspected and counted to 30. In a computerized system that uses an economic order quantity (EOQ) model and the perpetual inventory method, who determines when to reorder inventory? a. determine that the goods are in good condition a. the inventory control clerk b. determine the quantity of goods received c. preclude payment for goods not received or received in poor condition d. all of the above b. the purchasing department ANS: D c. the vendor d. the computer system 35. If a company uses a standard cost system, inventory records can be updated from the ANS: D a. vendor invoice 31. Firms can expect that proper use of a valid vendor file will result in all of the following benefits except b. purchase order a. purchasing agents will be discouraged from improperly ordering inventory from related parties d. purchase requisition b. purchases from fictitious vendors will be detected c. the most competitive price will be obtained d. the risk of purchasing agents receiving kickbacks and bribes will be reduced ANS: C c. receiving report ANS: C 36. If a company uses an actual cost system, inventory records can first be updated from the a. vendor invoice b. purchase order c. receiving report 32. In a real-time processing system with a high number of transactions, the best and most practical control over cash disbursements is to have d. purchase requisition ANS: A a. all checks manually signed by the treasurer 7 0 37. Copies of a purchase order are sent to all of the following except ANS: receiving report 3. a. inventory control List specific jobs that should be segregated in the purchases processing system. ANS: inventory control from warehouse, general ledger from accounts payable subsidiary ledger b. receiving c. general ledger 4. d. accounts payable ANS: C List specific jobs that should be segregated in the cash disbursements system. ANS: general ledger from accounts payable subsidiary ledger, accounts payable subsidiary ledger from cash disbursements 38. The receiving report a. is used to update the actual cost inventory ledger 5. b. accompanies the goods to the storeroom c. is sent to general ledger d. is returned to the vendor to acknowledge receipt of the goods ANS: B 39. A supplier invoice ANS: Accounts payable should compare the price on the purchase order to the price on the supplier’s invoice. Accounts payable should recalculate the math (extensions and additions) and check all other charges such as freight, tax, etc. 6. a. is included with the goods b. shows what was ordered even if all was not shipped Describe an internal control procedure that would detect that a vendor overcharged for goods delivered. Describe an internal control procedure that would prevent payment of a invoice for goods that were never delivered. ANS: Accounts payable should match every item on every invoice to a receiving report. c. is sent by vendor to accounts payable 7. d. none of the above ANS: C Describe an internal control procedure that would prevent issuing two checks in payment of the same invoice. a. part of accounts payable ANS: The supporting documents should be marked “paid” after the check is signed. A computerized system will tag the invoice number as paid. b. an independent accounting function 8. 40. The cash disbursement function is c. a treasury function d. part of the general ledger department ANS: C SHORT ANSWER 1. Which internally generated document should be compared to the supplier’s invoice to verify the price of an item? ANS: Receiving department employees have custody of the asset and record keeping responsibilities. Without proper supervision, employees may fail to count and inspect incoming shipments. Without proper supervision, shipments may disappear from the receiving dock before being transferred to the warehouse. 9. ANS: purchase order 2. Which internally generated document should be compared to the supplier’s invoice to verify the quantity being billed for? 7 Explain why supervision is so important in the receiving department. 0 What type of error or fraud might happen if the accounts payable ledger is not periodically reconciled to the control account in the general ledger? ANS: errors in A/P processing would go undetected, overstated payments produce debit balances in A/P. 10. What type of error or fraud might happen if suppliers’ invoices are not compared to purchase orders or to receiving reports before payment? ANS: payment at higher than anticipated prices, overpayment for goods not received 11. What internal accounting control(s) would be the most effective in preventing a storekeeper from taking inventory home at night? When shortages become apparent, he claims the goods were never received. ANS: receiving records items received on a receiving report, storekeeper initials receipt of goods 12. Why should the copy of a purchase order, which is sent to receiving, be a “blind” copy? ANS: to force workers in receiving to count and inspect the goods received 17. Explain why a three way match may not be required for transactions covered by a trading partner agreement. ANS: Under a trading partner agreement the parties contractually agree to terms of trade such as price, quantities to be shipped, discounts, and lead times. With these sources of potential discrepancy eliminated, financial information about purchases is known in advance and the vendor’s invoice provides no critical information that cannot be derived from the receiving report. Thus, a three way match is unnecessary. Chapter 6—The Expenditure Cycle Part II: Payroll Processing and Fixed Asset Procedures TRUE/FALSE 1. Time cards are used by cost accounting to allocate direct labor charges to work in process. ANS: F 13. What is(are) the purpose(s) of maintaining a valid vendor file? 2. The personnel department authorizes changes in employee pay rates. ANS: Inventories should only be acquired from valid vendors. This control procedure helps to deter the purchasing agent from buying inventories at excessive costs and receiving kickbacks or from buying from an entity in which the purchasing agent has a relationship, such a relative or a friend. ANS: T 3. Most payroll systems for mid-size firms use realtime data processing. ANS: F 14. Name two major benefits of automating the purchasing effort. 4. To improve internal control, paychecks should be distributed by the employee's supervisor. ANS: improved inventory control, better cash management, streamlining the purchasing effort ANS: F 15. What function or department typically initiates a purchase in a merchandising business? 5. Employee paychecks should be drawn against a special checking account. ANS: T ANS: Inventory control determines that the level of certain items warrants restocking and sends a purchase requisition to purchasing. 6. Because a time clock is used, no supervision is required when employees enter and leave the work place. 16. Where in the purchasing/cash disbursement functions is access control exercised? ANS: F ANS: physical control of inventory and cash, access to documents that control physical assets –such as purchase requisitions, purchase orders, receiving reports, etc. 7 7. Inventory control performs the formal record keeping function for fixed assets. ANS: F 8. The depreciation schedule shows when assets are fully depreciated. 0 ANS: T 9. Authorization to dispose of fixed assets should be issued by the user of the asset. 20. The fixed asset disposal report authorizes the user department to dispose of a fixed asset. ANS: F ANS: F MULTIPLE CHOICE 10. Work-in-process records are updated by payroll personnel. 1. The document that captures the total amount of time that individual workers spend on each production job is called a ANS: F 11. Ideally, payroll checks are written on a special bank account used only for payroll. a. time card b. job ticket ANS: T c. personnel action form 12. The supervisor is the best person to determine the existence of a “phantom employee” and should distribute paychecks. d. labor distribution form ANS: B 2. An important reconciliation in the payroll system is ANS: F 13. Payroll processing can be automated easily because accounting for payroll is very simple. a. general ledger compares the labor distribution summary from cost accounting to the disbursement voucher from accounts payable ANS: F 14. Timekeeping is part of the personnel function. ANS: F 15. Fixed asset accounting systems include cost allocation and matching procedures that are not part of routine expenditure systems. b. personnel compares the number of employees authorized to receive a paycheck c. production compares the number of hours reported on job tickets to the number of hours reported on time cards d. payroll compares the labor distribution summary to the hours reported on time cards ANS: T 16. Asset maintenance involves only the recording of depreciation charges. Physical improvements are always expensed. ANS: F ANS: A 3. Which internal control is not an important part of the payroll system? a. Supervisors verify the accuracy of employee time cards. 17. Fixed Asset Systems must keep track of the physical location of each asset to promote accountability. b. Paychecks are distributed by an independent paymaster. ANS: T 18. Time cards capture the total time an individual worker spends on each production job. ANS: F 19. Accounting conventions and IRS rules sometime specify the depreciation parameters to be used. ANS: T c. Accounts payable verifies the accuracy of the payroll register before transferring payroll funds to the general checking accounting. d. General ledger reconciles the labor distribution summary and the payroll disbursement voucher. ANS: C 4. Which transaction is not processed in the Fixed Asset System? 7 0 d. maintaining a record of the fair market value of all fixed assets a. purchase of building b. improvement of equipment ANS: D c. purchase of raw materials 9. Which of the following is not a characteristic of the Fixed Asset System? d. sale of company van ANS: C 5. Depreciation a. Acquisitions are routine transactions requiring general authorization. a. is calculated by the department that uses the fixed asset b. Retirements are reported on an authorized disposal report form. b. allocates the cost of the asset over its useful life c. Acquisition cost is allocated over the expected life of the asset. c. is recorded weekly d. results in book value approximating fair market value ANS: B 6. Depreciation records include all of the following information about fixed assets except a. the economic benefit of purchasing the asset d. Transfer of fixed assets among departments is recorded in the fixed asset subsidiary ledger. ANS: A 10. In the payroll subsystem, which function should distribute paychecks? a. personnel b. timekeeping b. the cost of the asset c. paymaster c. the depreciation method being used d. payroll d. the location of the asset ANS: C ANS: A 7. Which control is not a part of the Fixed Asset System? 11. Where does the responsibility lie for reconciling the labor distribution summary and the payroll disbursement voucher? a. formal analysis of the purchase request a. cash disbursements b. review of the assumptions used in the capital budgeting model b. cost accounting c. personnel c. development of an economic order quantity model d. general ledger d. estimates of anticipated cost savings ANS: D ANS: C 12. Which of the following statements is not true? 8. Objectives of the Fixed Asset System do not include a. Routine payroll processing begins with the submission of time cards. a. authorizing the acquisition of fixed assets b. Payroll clerks must verify the hours reported on the time cards. b. recording depreciation expense c. computing gain and/or loss on disposal of fixed assets 7 c. Payroll reconciles personnel action forms with time cards and prepares paychecks. 0 d. Cash disbursements signs paychecks and forwards them to the paymaster for distribution. b. to prevent an absent employee’s check from being lost ANS: B c. to avoid paying absent employees for payday 13. In a manufacturing firm, employees use time cards and job tickets. Which of the following statements is not correct? d. to prevent the paymaster from cashing unclaimed checks ANS: A a. Job tickets are prepared by employees for each job worked on, so an employee may have more that one job ticket on a given day. 17. Which of the following is not a reasonable control for fixed assets? b. An individual employee will have only one time card. a. Proper authorization is required for acquisition and disposal of fixed assets. c. The time reported on job tickets should reconcile with the time reported on time cards. b. Fixed asset records show the location of each asset. d. Paychecks should be prepared from the job tickets. c. Fully depreciated assets are immediately disposed of. ANS: D d. Depreciation policies are in writing. 14. Which department is responsible for approving changes in pay rates for employees? ANS: C a. payroll 18. Cost accounting updates work-in -process accounts from b. treasurer a. time cards c. personnel b. the labor distribution summary d. cash disbursements c. job tickets d. personnel action forms ANS: C 15. Which of the following situations represents a serious control weakness? a. Timekeeping is independent of the payroll department. ANS: C 19. Payroll uses time card data to do all of the following except a. prepare the payroll register b. Paychecks are distributed by the employees immediate supervisor. b. update employee payroll records c. prepare the labor distribution summary c. Time cards are reconciled with job tickets. d. Personnel is responsible for updating employee records, including creation of records for new hires. d. prepare paychecks ANS: C ANS: B 20. Payroll checks are typically drawn on 16. Why would an organization require the paymaster to deliver all unclaimed paychecks to the internal audit department? a. the regular checking account a. to detect a “phantom employee” for whom a check was produced c. a wages payable account b. a payroll imprest account d. petty cash 7 0 ANS: B d. personnel action form 21. The personnel action form provides authorization control by ANS: C a. preventing paychecks for terminated employees 26. A control technique that can reduce the risk of a terminated employee being paid is b. verifying pay rates for employees a. a security camera viewing the time clock c. informing payroll of new hires b. the supervisor taking role during the shift d. all of the above c. paychecks being distributed by an independent paymaster ANS: D 22. Accounting records that provide the audit trail for payroll include all of the following except d. reconciliation of time cards and job tickets ANS: C a. time cards 27. Accounts payable b. job tickets a. signs paychecks c. payroll register b. prepares the payroll voucher d. accounts payable register c. reconciles time cards and employee records ANS: D d. distributes paychecks to employees 23. Personnel actions forms are used to do all of the following except ANS: B a. activate new employees 28. All of the following are processed by the Fixed Asset System except b. terminate employees a. sale of unneeded equipment c. record hours worked b. purchase of raw materials d. change pay rates c. repair of production equipment ANS: C d. purchase of a new plant 24. The payroll department performs all of the following except ANS: B a. prepares the payroll register 29. The Fixed Asset System performs all of the following except b. distributes paychecks a. determines the need for new assets c. updates employee payroll records b. maintains depreciation records d. prepares paychecks c. records retirement and disposal of assets ANS: B d. tracks the physical location of fixed assets 25. The document that records the total amount of time spent on a production job is the ANS: A a. time card 30. The payroll department performs all of the following except b. job ticket a. prepares paychecks c. labor distribution summary 7 0 b. transfers adequate funds to the payroll imprest account c. updates employee payroll records 35. Asset disposal a. occurs as soon as an asset is fully depreciated b. requires no special authorization d. prepares the payroll register ANS: B c. automatically initiates the purchase of a replacement asset 31. Depreciation d. must follow formal authorization procedures a. assures that assets are reported at fair market value ANS: D SHORT ANSWER b. is discretionary for many firms 1. Describe an internal control procedure that would prevent an employee from punching the time clock c. allocates the cost of an asset over its useful life d. is the responsibility of the department using the asset for another, absent employee. ANS: C ANS: supervision of the time clock at the start of the shift 32. The Fixed Asset System is similar to the expenditure cycle except 2. Why should the employee’s supervisor not distribute paychecks? a. fixed asset transactions are non-routine and require special authorization and controls ANS: A form of payroll fraud involves a supervisor submitting fraudulent time cards for nonexistent employees. The resulting paychecks, when returned to the supervisor are then cashed by the supervisor. b. fixed assets are capitalized, not expensed c. both a and b 3. Describe an internal control procedure that would prevent a supervisor from stealing the unclaimed paychecks of employees who have been terminated. d. none of the above ANS: C 33. Asset maintenance involves a. the recording of periodic depreciation b. adjusting the asset records to reflect the cost of physical improvements c. keeping track of the physical location of the assets d. all of the above ANS: D 34. The Fixed Asset Systems does all of the following except a. records acquisition of assets b. records improvements to assets c. estimates the fair market value of assets in service d. records the disposal of assets ANS: This type of fraud can be reduced or eliminated by using a paymaster to distribute paychecks to employees in person. Any uncollected paychecks are then returned to payroll. Also, mail final paychecks to terminated employees. 4. Why should employee paychecks be drawn against a special checking account? ANS: A separate imprest account is established for the exact amount of the payroll based on the payroll summary. When the paychecks are cashed, this account should clear leaving a zero balance. Any errors in checks (additional checks or abnormal amounts) would result in a non-zero balance in the imprest account and/or some paycheck would not clear. This will alert management to the problem so corrective action can be taken. 5. Why should employees clocking on and off the job be supervised. ANS: C 7 0 ANS: A form of payroll fraud involves employees clocking the time cards of absent employees. Bysupervising the clocking in and out process, this fraud can be reduced or eliminated. 6. What is a personnel action form? ANS: The personnel action form provides the payroll department with a list of currently active employees, so that any submission of time cards by supervisors for fictitious or ex-employees will not be processed. 7. In a manufacturing firm, employees typically fill out two different documents regarding their time worked. What are they? Why are there two? ANS: The two documents are the time card and the job ticket. Two are required because the time card records all the time worked by an employee during the period while the job ticket details the time by project. 8. List two types of authorization required in the Fixed Asset System. longer on hand. Prepare reports about the disposal of assets. 13. Describe an internal control that would prevent the charging of depreciation expense to the maintenance department for a sweeper that is now located in and used by the engineering department. ANS: Prepare reports about the transfer of fixed assets. Perform an annual physical inventory and note the location of assets. Budget and then hold each department accountable for depreciation expense for assets located in each department. 14. Describe an internal control that would prevent the acquisition of office equipment which is not needed by the firm. ANS: A higher organizational level or other appropriate person authorizes fixed asset acquisitions; part of the authorization is showing that a need for the asset exists. 15. What negative consequences result when fixed asset records include assets that are no longer owned by the firm? ANS: authorization to purchase the asset and to dispose of the asset 9. List four types of data that appear on a depreciation schedule. ANS: item description, depreciation method, useful life, date acquired, cost, salvage value, accumulated depreciation, depreciation expense per period, book value 10. Which documents prompt the fixed asset department to create a fixed asset record? ANS: the receiving report and the disbursement voucher 11. Describe an internal control that would prevent an employee from stealing a computer and then reporting it as scrapped. ANS: Supervisors must authorize the disposal of the computer. Unless so authorized, the record will continue to show that the employee is responsible for the computer. 12. Describe an internal control that would prevent the payment of insurance premiums on an automobile that is no longer owned by the company. ANS: Perform an annual physical inventory of fixed assets and adjust the records to reflect assets no 7 ANS: On the financial statements, assets will be overstated and depreciation expense could be overstated. Assets on property tax returns will be overstated and too much tax will be paid. Insurance premiums will be paid on nonexistent assets. 16. Explain the purpose of each of the following documents used in the payroll system: the personnel action form, the job ticket, the time card. ANS: The personnel action form is a document which identifies employees who should receive a paycheck; reflects changes in pay rates, payroll deductions, and job classifications. The job ticket collects information on the time individual workers spend on each production job. The time card captures the total time that an employee is at work. 17. How do fixed asset systems differ from the expenditure cycle? ANS: The fixed asset system processes nonroutine transactions for a wider group of users in the organization than the expenditure cycle. Further, the expenditure cycle processes routine acquisitions of raw materials inventories for the production function and finished goods inventories for the sales function. The expenditure cycle transactions are oftentimes automatically approved by the system, 0 while fixed asset transaction approvals typically demand individual attention due to the uniqueness of the transactions. 18. What is recorded by the asset maintenance part of the Fixed Asset System? ANS: T 6. Because a time clock is used, no supervision is required when employees enter and leave the work place. ANS: F ANS: periodic depreciation following an approved depreciation schedule and physical improvements to the asset to increase the subsidiary account and to adjust the depreciation schedule 7. Inventory control performs the formal record keeping function for fixed assets. 19. How are the following carried out in the Fixed Asset System: authorization, supervision, independent verification? 8. The depreciation schedule shows when assets are fully depreciated. ANS: Independent authorization is required to acquire an asset and to formalize the depreciation schedule. ANS: F ANS: T 9. Authorization to dispose of fixed assets should be issued by the user of the asset. ANS: F Supervision must be exercised over the physical assets. Independent verification must confirm the location, existence, and condition of the assets. 20. Which department authorizes changes to employee pay rates? 10. Work-in-process records are updated by payroll personnel. ANS: F 11. Ideally, payroll checks are written on a special bank account used only for payroll. ANS: The personnel department via the personnel action form ANS: T Chapter 6—The Expenditure Cycle Part II: Payroll Processing and Fixed Asset Procedures 12. The supervisor is the best person to determine the existence of a “phantom employee” and should distribute paychecks. TRUE/FALSE ANS: F 1. Time cards are used by cost accounting to allocate direct labor charges to work in process. ANS: F 13. Payroll processing can be automated easily because accounting for payroll is very simple. ANS: F 2. The personnel department authorizes changes in employee pay rates. 14. Timekeeping is part of the personnel function. ANS: T ANS: F 3. Most payroll systems for mid-size firms use realtime data processing. 15. Fixed asset accounting systems include cost allocation and matching procedures that are not part of routine expenditure systems. ANS: F ANS: T 4. To improve internal control, paychecks should be distributed by the employee's supervisor. ANS: F 5. Employee paychecks should be drawn against a special checking account. 7 16. Asset maintenance involves only the recording of depreciation charges. Physical improvements are always expensed. ANS: F 0 17. Fixed Asset Systems must keep track of the physical location of each asset to promote accountability. a. Supervisors verify the accuracy of employee time cards. b. Paychecks are distributed by an independent paymaster. ANS: T 18. Time cards capture the total time an individual worker spends on each production job. ANS: F 19. Accounting conventions and IRS rules sometime specify the depreciation parameters to be used. c. Accounts payable verifies the accuracy of the payroll register before transferring payroll funds to the general checking accounting. d. General ledger reconciles the labor distribution summary and the payroll disbursement voucher. ANS: C ANS: T 20. The fixed asset disposal report authorizes the user department to dispose of a fixed asset. 4. Which transaction is not processed in the Fixed Asset System? a. purchase of building ANS: F b. improvement of equipment MULTIPLE CHOICE 1. The document that captures the total amount of time that individual workers spend on each production job is called a a. time card c. purchase of raw materials d. sale of company van ANS: C 5. Depreciation b. job ticket c. personnel action form a. is calculated by the department that uses the fixed asset d. labor distribution form b. allocates the cost of the asset over its useful life ANS: B c. is recorded weekly 2. An important reconciliation in the payroll system is d. results in book value approximating fair market value a. general ledger compares the labor distribution summary from cost accounting to the disbursement voucher from accounts payable ANS: B b. personnel compares the number of employees authorized to receive a paycheck to the number of paychecks prepared 6. Depreciation records include all of the following information about fixed assets except a. the economic benefit of purchasing the asset b. the cost of the asset c. production compares the number of hours reported on job tickets to the number of hours reported on time cards c. the depreciation method being used d. payroll compares the labor distribution summary to the hours reported on time cards ANS: A d. the location of the asset ANS: A 3. Which internal control is not an important part of the payroll system? 7 7. Which control is not a part of the Fixed Asset System? a. formal analysis of the purchase request 0 b. cost accounting b. review of the assumptions used in the capital budgeting model c. personnel c. development of an economic order quantity model d. general ledger ANS: D d. estimates of anticipated cost savings ANS: C 12. Which of the following statements is not true? 8. Objectives of the Fixed Asset System do not include a. Routine payroll processing begins with the submission of time cards. a. authorizing the acquisition of fixed assets b. Payroll clerks must verify the hours reported on the time cards. b. recording depreciation expense c. computing gain and/or loss on disposal of fixed assets d. maintaining a record of the fair market value of all fixed assets ANS: D 9. Which of the following is not a characteristic of the Fixed Asset System? c. Payroll reconciles personnel action forms with time cards and prepares paychecks. d. Cash disbursements signs paychecks and forwards them to the paymaster for distribution. ANS: B 13. In a manufacturing firm, employees use time cards and job tickets. Which of the following statements is not correct? a. Job tickets are prepared by employees for each job worked on, so an employee may have more that one job ticket on a given day. a. Acquisitions are routine transactions requiring general authorization. b. Retirements are reported on an authorized disposal report form. c. Acquisition cost is allocated over the expected life of the asset. d. Transfer of fixed assets among departments is recorded in the fixed asset subsidiary ledger. b. An individual employee will have only one time card. c. The time reported on job tickets should reconcile with the time reported on time cards. d. Paychecks should be prepared from the job tickets. ANS: A 10. In the payroll subsystem, which function should distribute paychecks? a. personnel ANS: D 14. Which department is responsible for approving changes in pay rates for employees? a. payroll b. timekeeping b. treasurer c. paymaster c. personnel d. payroll d. cash disbursements ANS: C 11. Where does the responsibility lie for reconciling the labor distribution summary and the payroll disbursement voucher? ANS: C 15. Which of the following situations represents a serious control weakness? a. Timekeeping is independent of the payroll department. a. cash disbursements 7 0 b. Paychecks are distributed by the employees immediate supervisor. b. update employee payroll records c. prepare the labor distribution summary c. Time cards are reconciled with job tickets. d. prepare paychecks d. Personnel is responsible for updating employee records, including creation of records for new hires. ANS: C ANS: B 20. Payroll checks are typically drawn on 16. Why would an organization require the paymaster to deliver all unclaimed paychecks to the internal audit department? a. the regular checking account b. a payroll imprest account c. a wages payable account a. to detect a “phantom employee” for whom a check was produced d. petty cash ANS: B b. to prevent an absent employee’s check from being lost 21. The personnel action form provides authorization control by c. to avoid paying absent employees for payday d. to prevent the paymaster from cashing unclaimed checks ANS: A a. preventing paychecks for terminated employees b. verifying pay rates for employees c. informing payroll of new hires 17. Which of the following is not a reasonable control for fixed assets? d. all of the above a. Proper authorization is required for acquisition and disposal of fixed assets. b. Fixed asset records show the location of each asset. ANS: D 22. Accounting records that provide the audit trail for payroll include all of the following except a. time cards c. Fully depreciated assets are immediately disposed of. b. job tickets c. payroll register d. Depreciation policies are in writing. d. accounts payable register ANS: C ANS: D 18. Cost accounting updates work-in -process accounts from 23. Personnel actions forms are used to do all of the following except a. time cards a. activate new employees b. the labor distribution summary b. terminate employees c. job tickets c. record hours worked d. personnel action forms d. change pay rates ANS: C ANS: C 19. Payroll uses time card data to do all of the following except 24. The payroll department performs all of the following except a. prepare the payroll register a. prepares the payroll register 7 0 b. distributes paychecks a. determines the need for new assets c. updates employee payroll records b. maintains depreciation records d. prepares paychecks c. records retirement and disposal of assets ANS: B d. tracks the physical location of fixed assets 25. The document that records the total amount of time spent on a production job is the ANS: A a. time card 30. The payroll department performs all of the following except b. job ticket a. prepares paychecks c. labor distribution summary b. transfers adequate funds to the payroll imprest account d. personnel action form c. updates employee payroll records ANS: C 26. A control technique that can reduce the risk of a terminated employee being paid is d. prepares the payroll register ANS: B a. a security camera viewing the time clock 31. Depreciation b. the supervisor taking role during the shift a. assures that assets are reported at fair market value c. paychecks being distributed by an independent paymaster b. is discretionary for many firms d. reconciliation of time cards and job tickets c. allocates the cost of an asset over its useful life ANS: C d. is the responsibility of the department using the asset 27. Accounts payable ANS: C a. signs paychecks 32. The Fixed Asset System is similar to the expenditure cycle except b. prepares the payroll voucher c. reconciles time cards and employee records d. distributes paychecks to employees a. fixed asset transactions are non-routine and require special authorization and controls ANS: B b. fixed assets are capitalized, not expensed 28. All of the following are processed by the Fixed Asset System except c. both a and b a. sale of unneeded equipment ANS: C b. purchase of raw materials 33. Asset maintenance involves c. repair of production equipment a. the recording of periodic depreciation d. purchase of a new plant b. adjusting the asset records to reflect the cost of physical improvements ANS: B d. none of the above c. keeping track of the physical location of the assets 29. The Fixed Asset System performs all of the following except d. all of the above 7 0 ANS: D ANS: F 34. The Fixed Asset Systems does all of the following except 7. The SAP R/3 system organizes business processes into four categories: financial, logistics, human resources, and business process support. a. records acquisition of assets ANS: T b. records improvements to assets d. records the disposal of assets 8. The objective of the Economic Order Quantity model is to reduce total inventory costs by minimizing carrying costs and ordering costs. ANS: C ANS: T 35. Asset disposal 9. The work-in-process file is the subsidiary ledger for the work-in -process control account. c. estimates the fair market value of assets in service a. occurs as soon as an asset is fully depreciated ANS: T b. requires no special authorization 10. Move tickets authorize the storekeeper to release materials to work centers. c. automatically initiates the purchase of a replacement asset ANS: F d. must follow formal authorization procedures 11. An operating characteristic of modern manufacturing firms is that labor is replaced with capital so that the firm can be more efficient and therefore more competitive. ANS: D Chapter 7—The Conversion Cycle TRUE/FALSE ANS: T 1. The philosophy of customer satisfaction permeates the world-class firm. 12. Computer Integrated Manufacturing focuses on reducing the complexity of the physical manufacturing layout of the shop floor. ANS: T 2. Reports generated by the cost accounting system include performance reports and budget reports. ANS: T 3. The cost accounting system authorizes the release of raw materials into production. ANS: F 13. The only objective of the Just-In-Time philosophy is to reduce inventory levels. ANS: F ANS: F 14. Accounting in a world-class manufacturing environment emphasizes standard cost and variance analysis. 4. Batch processing creates a homogeneous product through a continuous series of standard procedures. ANS: F ANS: F 15. Identifying cost drivers is an essential step in implementing the Just-In-Time philosophy. 5. The bill of materials specifies the types and quantities of the raw materials and subassemblies used in producing a single unit of finished product. ANS: F ANS: T 6. A purchase requisition authorizes the storekeeper to release materials to individuals or work centers in the production process. 7 16. A world class information system produces very little paper. ANS: T 0 17. Internal control procedures are virtually identical in a world-class manufacturing environment and in a traditional manufacturing environment. b. authorize release of raw materials c. direct the movement of work-in-process d. determine material requirements ANS: F ANS: A 18. In a world-class company, all activities, from acquisition of raw materials to selling the final product, form a “chain of customers.” 4. Which process creates a homogeneous product through a continuous series of standard procedures? ANS: T a. batch process 19. The two subsystems of a traditional conversion cycle are the production system and the delivery system. b. make-to-order process ANS: F d. none of the above 20. Manufacturing resources planning (MRP II) has evolved into electronic resource planning (ERP). ANS: C c. continuous process ANS: F 5. An example of a continuous process is the production of MULTIPLE CHOICE a. wedding invitations 1. Which item does not describe a world-class company? b. milk products c. jet aircraft a. the goal of a world-class company is to delight its customers b. customers in a world-class company are external departments only c. world-class companies work in cross-functional teams d. all of the above ANS: B 6. All of the following are characteristics of batch processing except a. each item in the batch is similar d. a world-class company has a flat organizational structure b. batches are produced in accordance with detailed customer specifications ANS: B c. batches are produced to replenish depleted inventory levels 2. Which subsystem is not a part of the production system? a. directing the movement of work through the process d. setting up and retooling is required for different batches ANS: B b. determining raw material requirements 7. When determining which items to produce, a firm must know c. authorizing work to be performed a. last year’s production level d. monitoring the flow of cost information related to production b. raw material inventory levels ANS: D c. the standard cost of the item 3. The purpose of the cost accounting system is to d. the sales forecast a. produce information for inventory valuation ANS: D 7 0 8. The production schedule is ANS: C a. the expected demand for the firm’s finished goods for a given year 12. The storekeeper releases raw materials based on the b. the formal plan and authority to begin production a. production schedule c. a description of the type and quantity of raw materials and subassemblies used to produce a single unit of finished product b. materials requisition d. the sequence of operations during manufacturing d. bill of materials c. work order ANS: B ANS: B 9. A move ticket 13. Which of the following is not an assumption of the Economic Order Quantity model? a. is the formal plan and authority to begin production a. demand for the product is known with certainty b. specifies the materials and production required for each batch b. total cost per year of placing orders is fixed c. records the work done in each work center d. there are no quantity discounts d. authorizes the storekeeper to release materials to work centers ANS: B c. lead time is known and is constant 14. Firms hold safety stock to compensate for ANS: C 10. The internal control significance of the excess materials requisition is that it a. indicates the amount of material released to work centers a. mathematical weaknesses of the Economic Order Quantity model b. variations in lead time or daily demand c. fluctuations in carrying costs d. uncertainty in the estimation of ordering costs b. identifies materials used in production that exceed the standard amount allowed ANS: B c. indicates the standard quantities required for production d. documents the return to raw materials inventory of unused production materials 15. What is the economic order quantity if the annual demand is 10,000 units, set up cost of placing each order is $3 and the holding cost per unit per year is $2? ANS: B a. 174 11. Inventory control performs all of the following tasks except it b. 123 a. provides production planning and control with the inventory status report of finished goods c. 245 d. none of the above ANS: A b. updates the raw material inventory records 16. If the daily demand is 40 units and the lead time is 12 days, the reorder point is c. prepares a materials requisition for each production batch d. records the completed production as an increase to finished goods inventory 7 a. 52 units b. 48 units 0 c. 480 units d. financial d. none of the above ANS: C ANS: C 21. Which situation violates the segregation of functions control procedure? 17. Which statement is not correct? a. general ledger creates a new cost record upon receipt of a work order from production planning and control b. cost accounting updates the cost record with data gathered from the materials requisition c. general ledger posts summary information about the manufacturing process based on a journal voucher prepared by cost accounting d. cost accounting computes variances and applies overhead to individual cost records ANS: A a. production planning and control is located apart from the work centers b. inventory control maintains custody of inventory items c. cost accounting has custody of and makes entries on cost records d. work centers record direct labor on job tickets ANS: B 22. All of the following are internal control procedures that should be in place in the conversion cycle except a. calculation and analysis of direct material and direct labor variances 18. Which of the following is not a category of critical success factors in most manufacturing companies? b. retention of excess materials by work centers a. product quality c. physical count of inventory items on hand b. customer service c. revenue generation d. limited access to raw material and finished goods inventories d. resource management ANS: B ANS: C 23. Process simplification focuses on 19. Computer integrated manufacturing groups all of the following technologies except a. using Computer Numerical Controlled machines which stand alone within a traditional setting a. robotics b. completely automating the manufacturing environment b. materials requirements planning c. reducing the complexity of the physical manufacturing layout of the shop floor c. automated storage and retrieval systems d. computer aided design d. organizing the process into functional departments ANS: B 20. The SAP R/3 system provides pre-defined modules to support business processes in the all of the following categories except ANS: C a. human resources 24. A manufacturing process that is organized into group technology cells utilizing no human labor is called b. business process support a. islands of technology c. strategic b. process simplification c. Computer Integrated Manufacturing 7 0 d. traditional manufacturing b. warranty claims ANS: C c. scheduling delays 25. An example of automation of manufacturing design is d. proceeds from the sale of scrap ANS: D a. Computer Aided Engineering 30. A flexible manufacturing system b. Automated Storage and Retrieval Systems a. creates bottlenecks in the process c. Computer Numerical Control d. robotics b. leads to an “us” versus “them” attitude among workers ANS: A c. shortens the physical distance between activities 26. An example of automation of manufacturing planning is d. is organized along functional lines ANS: C a. Computer Aided Engineering 31. Deficiencies of the traditional cost accounting information system include all of the following except b. Automated Storage and Retrieval Systems c. Materials Requirements Planning a. an emphasis on financial performance d. Computer Numerical Control b. inaccurate cost allocations ANS: C c. an emphasis on standard costs 27. Firms implement a Just-In-Time inventory approach to d. immediate feedback about deviations from the norm a. reduce investment in inventories b. determine the optimum inventory level using the EOQ model ANS: D 32. Which statement is not correct? a. an activity driver is a means to measure the activity used by the cost object c. camouflage production problems d. ensure overproduction of inventory b. cost object describes the work performed in a firm ANS: A c. activities cause costs 28. Characteristics of Just-In-Time manufacturing include all of the following except d. cost objects create a demand for activities a. push manufacturing ANS: B b. zero defects 33. Firms are adopting Activity Based Costing (ABC) because c. reduced setup time and small lot sizes a. it facilitates the analysis of variances d. reliable vendors b. it more accurately allocates costs to products ANS: A c. it recognizes the importance of direct labor as a component of total manufacturing cost 29. The cost of poor quality includes all of the following except d. the financial nature of the reports permits comparisons to be made among different types of products a. cost of rework 7 0 34. In traditional firms, information reporting 38. Transaction authorization occurs in a traditional manufacturing environment in all of the following ways except a. provides financially oriented information relating to operations a. production planning and control initiates production with a work order ANS: B b. presents detailed information about activities c. shows the allocation of costs first to activities and then to cost objects d. identifies nonessential activities b. movement of the work through the production process follows the move ticket c. the sales department modifies work orders to match changes in demand ANS: A d. the materials requisition authorizes the storekeeper to release materials to the work centers 35. Types of information provided by Activity Based Costing include ANS: C a. a description of the single activity driver used for overhead application 39. Manufacturing flexibility incorporates four characteristics. These include all of the following except b. the dollar value of the direct material usage variance a. high product quality c. identification of cost drivers b. high inventory levels d. details of the components of the single overhead cost pool c. automation of manufacturing processes ANS: C ANS: B 36. Which statement is not correct? 40. The stages of the automation continuum are (in order) a. the benchmark approach compares key activities with similar activities in other firms b. critical success factors include product and process quality d. physical reorganization of production facilities a. traditional, computer-integrated manufacturing, islands of technology, process simplification b. process simplification, traditional, islands of technology, computer-integrated manufacturing c. the ABC model includes two perspectives: an allocation of cost perspective and a process perspective c. traditional, islands of technology, process simplification, computer-integrated manufacturing d. in world-class manufacturing firms, quality control activities at the end of the process are essential d. traditional, process simplification, computerintegrated manufacturing, islands of technology ANS: D ANS: C 37. All of the following are documents in batch process production systems except Chapter 8—General Ledger, Financial Reporting, and Management Reporting Systems a. production schedule TRUE/FALSE b. route sheet c. materials requisition 1. The most common means of making entries in the general ledger is via the journal voucher. d. purchase order ANS: T ANS: D 7 0 2. Individuals with access authority to general ledger accounts should not prepare journal vouchers. ANS: T 3. The journal voucher is the document that authorizes entries to be made to the general ledger. ANS: T 4. Each account in the chart of accounts has a separate record in the general ledger master file. ANS: T 5. The responsibility center file is primarily used by the Financial Reporting System. ANS: F 14. The control function entails evaluating a process against a standard and, if necessary, taking corrective action. ANS: T 15. Standards are the basis for evaluating actual performance. ANS: T 16. A report is said to have information content if it eliminates uncertainty associated with a problem facing the decision maker. ANS: F ANS: F 6. Management reporting is often called discretionary reporting because it is not mandated as is financial reporting. ANS: T 7. Primary recipients of financial statement information are internal management. 17. An inventory out-of-stock report is an example of a programmed, on-demand report. ANS: T 18. A principle of responsibility accounting is that managers are responsible for controllable and uncontrollable costs. ANS: F 19. The manager of a cost center is responsible for cost control and revenue generation. ANS: F 8. The Management Reporting System is a nondiscretionary system. ANS: F 9. When evaluating decision alternatives, one option is to take no action. 20. Designing an effective management reporting system does not require an understanding of the information managers need to deal with the problems they face. ANS: T ANS: F ANS: F 10. In most cases intangible decision criteria can be quantified. ANS: F 11. One benefit of the Management Reporting System is that it can alert management to delays in project implementation. ANS: T 21. The formalization of tasks principle suggests that management should structure the firm around the unique skills sets of key individuals. ANS: F 22. If a manager delegates responsibility to a subordinate, he or she must also grant the subordinate authority to make decisions. ANS: T 12. Responsibility refers to an individual’s obligation to achieve desired results. ANS: T 13. A firm with a wide span of control tends to have relatively more layers of management. 7 23. Operational control involves motivating managers at all levels to use resources, including materials, personnel, and financial assets, as productively as possible. 0 ANS: F 24. The block code is the coding scheme most appropriate for a chart of accounts. 5. The most important advantage of an alphabetic code is that a. meaning is readily conveyed to users ANS: T b. sorting is simplified MULTIPLE CHOICE c. the capacity to represent items is increased 1. The coding scheme most appropriate for a chart of accounts is d. missing documents can be identified a. sequential code ANS: C b. block code 6. Entries into the General Ledger System (GLS) can be made using information from c. group code a. the general journal d. mnemonic code b. a journal voucher which represents a summary of similar transactions ANS: B 2. A common use for sequential coding is c. a journal voucher which represents a single, unusual transaction a. creating the chart of accounts d. all of the above b. identifying inventory items ANS: D c. identifying documents d. identifying fixed assets 7. Which statement is not correct? The general ledger master file ANS: C a. is based on the firm’s chart of account 3. The most important advantage of sequential coding is that b. contains a record for control accounts c.is an output of the Financial Reporting System (FRS) a. missing or unrecorded documents can be identified b. the code itself lacks informational content d. supplies information for management decision making c. items cannot be inserted ANS: C d. deletions affect the sequence 8. What type of data is found in the general ledger master file? ANS: A a. a chronological record of all transactions 4. When a firm wants its coding system to convey meaning without reference to any other document, it would choose b. the balance of each account in the chart of accounts a. an alphabetic code c. budget records for each account in the chart of accounts b. a mnemonic code d. subsidiary details supporting a control account c. a group code ANS: B d. a block code 9. Which report is not an output of the Financial Reporting System (FRS)? ANS: B 7 0 a. variance analysis report a. trial balance b. statement of cash flows b. adjusted trial balance c. tax return c. general ledger d. comparative balance sheet d. general journal ANS: A ANS: B 10. Which steps in the Financial Accounting Process are in the correct sequence? 14. Risk exposures in the General Ledger and Financial Reporting Systems include all of the following except a. record the transaction, post to the ledger, prepare the adjusted trial balance, enter adjusting entries, prepare financial statements a. loss of the audit trail b. unauthorized access to the general ledger b. record the transaction, prepare the unadjusted trial balance, record adjusting journal entries, record closing entries, prepare financial statements c. loss of physical assets c. record the transaction, post to the ledger, record adjusting entries, prepare the unadjusted trial balance, prepare financial statements ANS: C d. record the transaction, post to the ledger, prepare the adjusted trial balance, prepare financial statements, record closing entries d. general ledger account out of balance with the subsidiary account 15. Which situation indicates an internal control risk in the General Ledger/Financial Reporting Systems (GL/FRS)? a. the employee who maintains the cash journal computes depreciation expense ANS: D 11. Which statement is not correct? a. the post-closing trial balance reports the ending balance of each account in the general ledger b. one purpose of preparing the unadjusted trial balance is to ensure that debits equal credits c. financial statements are prepared based on the unadjusted trial balance d. the unadjusted trial balance reports control account balances but omits subsidiary ledger detail ANS: C 12. What account appears on the postclosing trial balance? a. income summary b. the cash receipts journal voucher is approved by the Treasurer c. the cash receipts journal vouchers are prenumbered and stored in a locked safe d. the employee who maintains the cash receipts journal records transactions in the accounts receivable subsidiary ledger ANS: D 16. With a limited work force and a desire to maintain strong internal control, which combination of duties performed by a single individual presents the least risk exposure? a. maintaining the inventory ledger and recording the inventory journal voucher in the general ledger b. recording the inventory journal voucher in the general ledger and maintaining custody of inventory b. machinery c. rent expense c. maintaining the cash disbursements journal and recording direct labor costs applied to specific jobs d. interest income ANS: B d. preparing the accounts payable journal voucher and recording it in the general ledger 13. Financial statements are prepared from the 7 0 ANS: C 17. The audit trail fulfills all of the following purposes except d. the MRS focuses on internal decision-making information ANS: D a. provides the ability to answer inquiries 21. Which statement is not true? b. ensures the accuracy of the application software a. authority refers to an individual’s obligation to achieve desired results c. fulfills governmental regulations b. if an employee is given the responsibility for a task, that employee should be given authority to make decisions within the limits of that task d. offers a means for preventing, detecting, and correcting errors ANS: B 18. Which best describes a batch process General Ledger System (GLS) c. the level of detail provided to an employee is a function of the employee’s position with the firm d. all of the above are true a. paper documents are eliminated ANS: A b. the general ledger master file is updated each night 22. Which statement is not true? The manager’s span of control c. there is a time lag between transaction processing and posting to the general ledger a. is narrow for routine and repetitive tasks d. no direct access or querying of the General Ledger is possible ANS: C 19. An advantage of a batch General Ledger System (GLS) is that a. separation between authorization and transaction processing is strictly enforced b. the general ledger master file is recreated with each update b. is related to the number of layers of management c. affects the amount of detail provided to a manager d. can affect employee morale and motivation ANS: A 23. Short-range planning involves a. setting goals and objectives of the firm b. planning the production schedule for the next quarter c. updates and reconciliation of transactions occur as a step within the transaction cycle c. planning the growth of the firm d. errors and out-of-balance conditions are identified at the end of the month d. deciding on the degree of diversification among the firm’s products ANS: C ANS: B 20. A characteristic of the Management Reporting System (MRS) is 24. Long-range planning involves a. the MRS operates in conformity with generally accepted accounting principles b. it is a legal requirement that the MRS be installed and functioning properly c. the MRS is developed by implementing SEC requirements a. planning the marketing and promotion for a product b. presenting department heads with budgetary goals for the next year c. preparing a work force utilization budget for the next quarter d. deciding the optimum size of the firm 7 0 ANS: D c. span of control 25. The level of management that makes tactical planning decisions is d. all of the above ANS: D a. top management b. middle management 30. All of the following are elements of problem structure except c. operations management a. certainty d. front-line management b. data ANS: B c. procedures 26. The decision to enter a new market is an example of d. objectives ANS: A a. strategic planning b. tactical planning 31. All of the following are examples of programmed reports except c. management control a. cash flow reports for Division B d. operational control b. year-to-date local income tax payments made by all employees living in City X and working in City Y ANS: A 27. All of the following are elements of operational control decisions except c. inventory exception reports for Division G d. equipment utilization reports for Plant M a. determining the scope of the activity ANS: B b. setting operating standards 32. A fundamental principle of responsibility accounting is that c. evaluating performance a. managers are accountable only for items they control d. taking corrective action when necessary ANS: A b. a manager’s span of control should not exceed eight people 28. In contrast to tactical planning decisions, management control decisions, and operational control decisions, strategic planning decisions usually c. structured reports should be prepared weekly d. the information flow is in one direction, top-down a. are more focused ANS: A b. have a shorter time frame 33. Which statement is not true? Responsibility accounting c. are unstructured a. involves both a top-down and bottom-up flow of information d. have a high degree of certainty ANS: C 29. Which of the following management principles affects the management reporting system? b. acknowledges that some economic events cannot be traced to any manager c. creates a budget a. formalization of tasks d. compares actual performance with budget b. authorization ANS: B 7 0 34. What mechanism is used to convey to managers the standards by which their performance will be measured? a. the responsibility report a. emphasis on both the short and long run. b. review of the attributes and behavior of the organization’s competition. c. analysis of external economic factors. b. the scheduled report d. analysis of consumer demand. c. the budget ANS: A d. all of the above 39. Which of the following performance measures can not result in dysfunctional behavior? ANS: C a. price variance 35. All of the following concepts encourage goal congruence except b. quotas a. detailed information reporting at all management levels c. ROI b. authority and responsibility d. net income c. formalization of tasks e. all of the above can result in dysfunctional behavior d. responsibility accounting ANS: E ANS: A 36. Which of the following statements is NOT true? 40. Which of the following best describes a profit center: a. Sorting records that are coded alphabetically tends to be more difficult for users than sorting numeric sequences. a. authority to make decisions affecting the major determinants of profit, including the power to choose its markets and sources of supply. b. Mnemonic coding requires the user to memorize codes. b. authority to make decisions affecting the major determinants of profit, including the power to choose its markets and sources of supply, and significant control over the amount of invested capital. c. Sequential codes carry no information content beyond their order in the sequence. d. Mnemonic codes are limited in their ability to represent items within a class. ANS: B c. authority to make decisions over the most significant costs of operations, including the power to choose the sources of supply. 37. Which file has as its primary purpose to present comparative financial reports on a historic basis? d. authority to provide specialized support to other units within the organization. a. journal voucher history file b. budget master file e. responsibility for combining the raw materials, direct labor, and other factors of production into a final product. c. responsibility file ANS: A d. general ledger history file ANS: D 38. All of the following are characteristics of the strategic planning process except the 7 0 Ch01 - chapter 1 Accounting Information Systems (ACC 3202) ACCOUNTING INFORMATION SYSTEMS/2e TURNER / WEICKGENANNT Test Bank: CHAPTER 1: Introduction to AIS 1NOTE: All new or adjusted questions are in red. New questions are identified by the letter A as part of the question number; adjusted questions are identified by the letter X as part of the question number. End of Chapter Questions: 1. When a company receives returned goods from a customer, the business process to accept the return would most likely be a(n): A. Administrative process B. Conversion process C. Expenditure process D. Revenue process 2. Which of the following is least likely to be an output of the accounting information system? A. A check B. A report C. An invoice D. A bar code 3. Which of the following is not true of the supply chain? A. The supply chain includes vendors. B. The supply chain excludes customers. C. The supply chain includes information flows. D. The supply chain include secondary suppliers. 4. Which of the following is not an objective of IT enablement? A. Increased accuracy of data B. Reduced cost C. Reduced security problems D. Increased efficiency 5. The correct order of the computer data hierarchy is: A. Byte, bit, record, field, file, database B. Bit, byte, record, field, file, database C. Bit, byte, field, record, file, database D. Bit, byte, field, record, database, file 6. The process of searching for identifiable patterns in data is called: A. Sequential processing B. Data warehousing C. Data mining D. Real-time processing 7. An IT enabled system for purchasing that is an “invoice-less” system is called a(n): A. Automated matching system B. Evaluated receipt settlement 1-1 9 0 C. E-payables D. Point of sale system 8. The COSO report written for the purpose of assisting managers in the challenge of managing risk in their organization is entitled: A. Internal Control – Integrated Framework B. Enterprise Risk Management – Integrated Framework C. Corporate Governance Guidance D. IT Governance Guidance 9. Accountants have some form of use of the AIS in all but which role? A. User B. Programmer C. Auditor D. Designer 10. Which of the following is not true of unethical behavior? A. The only category of unethical behavior for accountants is inflating revenue. B. Accountants are often pressured to help commit or coverup unethical behavior. C. Hacking is an unethical behavior that accountants should be concerned about. D. An accounting information system can be used to cover up unethical behavior. ANSWERS TO QUESTIONS 1 - 10 (FROM THE TEXTBOOK) 1. D 6. C 2. D 7. B 3. B 8. A 4. C 9. B 5. C 10. A TEST BANK – CHAPTER 1 – MULTIPLE CHOICE 11. A prescribed sequence of work steps preformed in order to produce a desired result for the organization is called a(n): A. Accounting Information System B. Business Process C. Financial Transaction D. Capital Transaction Process 12. The process that must identify the transactions to be recorded, capture all the important details of the transactions, properly process the transaction details, and provide reports is termed the: A. Revenue Process B. Expenditure Process C. Accounting Information System D. Business Process 13. An accounting information system serves many functions - which of the following is NOT one of those functions? A. Capture the details of a transaction B. Implement the start of a transaction C. Provide reports of transactions D. Process the transactions details into appropriate accounts 1-2 9 0 14. The proper order of activity in an accounting information system would be as follows: A. Capture, Record, Process, Report B. Process, Record, Capture, Report C. Capture, Process, Report, Record D. Record, Capture, Process, Report 15. Which of the following is not one of the general types of business processes identified by the textbook? A. Revenue Processes B. Expenditure Processes C. Conversion Processes D. Human Resource Processes 16. Which of the following statements, related to business processes, is false? A. Each business process has a direct effect on the financial status of the organization. B. A business process is initiated by a particular kind of event. C. A business process has a well-defined beginning and end. D. Each business process is usually completed in a relatively short period. 17. Which of the following is least likely to be part of an accounting information system function? A. Record the accounting data in the appropriate records B. Generation of data to be part of the information system. C. Process the detailed accounting data. D. Report the summarized accounting data. 18. Work steps that are internal controls within the business process would include: A. Using an electronic register to record all sales transactions. B. Combining both manual and computer based records. C. Reconciling a cash register at the end of each day. D. Preparation of internal reports to monitor the performance of a specific department. 19. Five different components of the accounting information system were presented in the textbook. Which of the following is not one of those components? A. Work steps within a business process intended to capture accounting data as the business process occurs. B. Work steps that are internal controls within the business process to safeguard assets and to ensure the accuracy and completeness of the data. C. Work steps that generate both internal and external reports. D. Work steps to assure that all business processes are recorded using computer-based procedures. 20. Output from an accounting information system would include: A. Checks to vendors B. Invoices from vendors C. Customer statements D. Purchase orders 21. The entities, processes, and information flows that involve the movement of materials, funds, and related information through the full logistics process, from the acquisition of raw materials to the delivery of the finished produces to the end use is a set of linked activities referred to as: A. Management Information System B. Supply Chain C. Accounting Information System 1-3 9 0 D. Logistics Management 22. The organization and control of all materials, funds, and related information in the logistics process, from the acquisition of raw materials to the delivery of finished products to the end user is referred to as: A. Supply Chain Management B. Management Information System C. Logistics Management D. IT Enablement 23. When discussing the supply chain: A. Any concern about vendors would relate only to those vendors with which a company has direct contact. B. Service providers would not be part of the supply chain. C. Concern would not extend beyond the point where the product is shipped to a customer. D. An entity may not be able to directly control all of the interrelated activities within the supply chain. 24. Using IT systems to enhance efficiency and effectiveness of internal or supply chain processes is called: A. Information Technology Enablement B. Information Systems Control C. Information Technology Process Engineering D. Information Technology Business Processes 25. The purposeful and organized changing of business processes to make them more efficient is referred to as: A. Information Technology Engineering B. Information Systems Management C. Business Process Reengineering D. Business Process Supply Chain 26. The use of BPR (Business Process Reengineerin) is a two-fold: (1) Aligns business processes with the IT systems used to recorded processes and, (2): A. Improves the efficiency and effectiveness of these processes. B. Reduces the cost of these processes. C. Enhances the usefulness of these processes. D. Increases the accuracy of the process. 27. The smallest unit of information in a computer system can have only one of two values, zero or one, and is referred to as a(n): A. Field B. Record C. Byte D. Bit 28. A unit of storage that represents one character is referred to as a: A. Byte B. Bit C. Bat D. Field 29. A set of related fields is referred to as a: A. File B. Record C. Byte D. Binary Digit 1-4 9 0 30. Each record is made up of related: A. Files B. Bytes C. Name D. Fields 31. A collection of data stored on a computer in a form that allows the data to be easily accessed, retrieved, manipulated, and stored is referred to as a(n): A. Accounting Information System B. Information Technology C. Database D. Master File 32. A collection of data stored in several small two-dimensional tables that can be joined together in many varying ways to represent many different kinds of relationships among the data is referred to as a(n): A. Database B. Master File C. Relational Database D. Relation Based Accounting Software 33. Accounting software traditionally uses two different types of files. The file type that is relatively permanent and used to maintain the detailed data for each major process is a(n): A. General Ledger B. Master File C. Transaction File D. Subsidiary File 34. Accounting software traditionally uses two different types of files. The file type that is the set of relatively temporary records that will be process to update the permanent file is referred to as a(n): A. Master File B. General File C. Transaction File D. Subsidiary File 35. The chart of accounts would be a good example of a: A. Transaction File B. Master File C. Field D. Record 36. The organization of files in a computer system normally uses one of two different access methods. The access method where the files store records in sequence, with one record stored immediately after another, is referred to as: A. Chronological Access B. Sequential Access C. Random Access D. Numerical Access 37. The organization of files in a computer system normally uses one of two different access methods. The access method where the files are not stored in sequence, one record not stored immediately after another, is referred to 1-5 9 0 as: A. B. C. D. Indexed Access Batch Access Sequential Access Random Access 38. There are two modes of processing transactions in accounting systems. The mode that requires all similar transactions be grouped together and be processed at the same time, is referred to as: A. Batch Processing B. Online Processing C. Real-time Processing D. Sequential Processing 39. There are two modes of processing transactions in accounting systems. The mode that will record transactions, one at a time, is referred to as: A. Batch Processing B. Online Processing C. Real-Time Processing D. Sequential Processing 40. A type of online processing where a transaction is processed immediately so that the output is available immediately is termed: A. Virtual Processing B. Sequential Processing C. Real-Time Processing D. Batch Processing 41. An integrated collection of enterprise-wide data that includes five to ten fiscal years of non-volatile data, used to support management in decision making and planning is referred to as: A. Operational Database B. Relational Database C. Data Storage D. Data Warehouse 42. This type of database contains the data that are continually updated as transactions are processed and includes data for the current fiscal year and supports day-to-day operations is referred to as a(n): A. Data Warehouse B. Data Storage C. Relational Database D. Operational Database 43. The data in the data warehouse are said to be enterprise-wide because: A. The data relate to all areas of the business. B. The data are pulled from each of the operational databases and maintained in the data warehouse for many fiscal periods. C. All areas of the business are able to access the data warehouse. D. All transactions across the all areas of the business are recorded in the data warehouse. 44. The process of searching data within the data warehouse for identifiable patterns that can be used to predict future behavior is referred to as: A. Data mining B. Data digging 1-6 9 0 C. Data housing D. Data querying 45. Two or more computers linked together to share information and / or resources is referred to as a(n): A. Computer Intranet B. Computer Internet C. Computer System D. Computer Network 46. This type of computer network is one that spans a relatively small area - often confined to a single building or group of buildings, and are intended to connect computers within an organization. A. Local Area Network B. Land Arena Network C. Extranet D. Internet 47. The global computer network, or “information super highway”, is the: A. WAN B. Intranet C. Internet D. LAN 48. A company’s private network, accessible only to the employees of that company is the: A. WAN B. Intranet C. Internet D. LAN 49. This computer network is similar to a company’s intranet except that it does allow access to selected outsiders, such as buyers, suppliers, distributors, and wholesalers. A. Ultranet B. Internet C. Extranet D. LAN 49A. A contemporary type of computer infrastructure that is used by an increasing number of companies involves the use of shared services, software, and / or data stored on servers at a remote location, which are accessible over a network, is referred to as: A. Database B. Cloud Computing C. Internet D. Relational Internet 50. The use of electronic means to enhance business processes is termed: A. E-business B. Electronic data interchange C. Point of sale system D. E-commerce 51. The intercompany, computer-to-computer transfer of business documents in a standard business format is called: A. E-business B. E-commerce 1-7 9 0 C. Local area network D. Electronic data interchange 52. Which of the following is NOT one of the three components of electronic data interchange? A. Commerce - encompasses all forms of electronic trading. B. Intercompany - two or more companies conducting business electronically. C. Standard business format - necessary so that the various companies can interact and trade electronically. D. Computer to computer - indicates that each company’s computers are connected via a network. 53. This term refers to a system of hardware and software that captures retail sales transactions by standard bar coding. A. E-business B. Electronic data interchange C. Point of sale system D. E-commerce 54. When a point of sale system is used and a customer checks out through a cash register, which of the following processes occur? A. Net income is computed B. Inventory values are updated C. Accounts payable balances are updated D. Replacement inventory is purchased 55. A system of computer hardware and software in which the software matches an invoice to its related purchase order and receiving report is called: A. Point of sale system B. Electronic data interchange C. Automated matching D. Evaluated receipt settlement 56. An invoice-less system in which computer hardware and software complete an invoice-less match that is a comparison of the purchase order with the goods received is termed: A. Evaluated receipt settlement B. Automated matching C. Electronic invoice presentation and payment D. Enterprise resource planning 57. This system enables a vendor to present an invoice to its trading partner via the internet, eliminating the paper, printing, and postage costs of traditional paper invoicing. A. Evaluated receipt settlement B. Electronic invoice presentation and payment C. Automated matching D. Electronic data interchange 58. A multi-module software system designed to manage all aspects of an enterprise usually broken down into modules such as financials, sales, human resources, and manufacturing, is referred to as a(n): A. Electronic data system B. Electronic data interchange C. Enterprise resource planning D. Electronic resource program 1-8 9 0 59X. Management has the responsibility, and the ability, to take action to reduce risks or to lessen the impact al nearly all risks an organization faces. The steps taken by management to lessen the risk or reduce the impact of the risk, are referred to as: A. Programs B. Risk assessment C. Information evaluation D. Controls 60. Which of the following groups of professionals within an organization have a history of designing and implementing the controls to lessen risks? A. Management B. Accountants C. Human Resources D. Lawyers 61. Which of the following is not one of broad categories of controls? A. The risk that assets will be stolen or misused. B. The risk of errors in accounting data or information. C. The risk of loss due to a natural disaster. D. The risk of fraudulent activity by employees. 62. Which of the following is not a risk inherent in an IT system? A. Computer security breaches. B. Computers being stolen. C. Erroneous input of data. D. Hardware or software failure. 63X. A comprehensive report on enterprise risk management was issued by this organization. A. American Accounting Association B. New York Stock Exchange C. Institute of Internal Auditors D. Committee on Sponsoring Organizations 64. A process, effected by an entity’s board of directors, management and other personnel, applied in strategy setting and across the enterprise, designed to identify potential events that may effect the entity, and manage risk to be withing its risk appetite, to provide reasonable assurance regarding the achievement of entity objectives is referred to as: A. Enterprise resource planning B. Enterprise risk management C. IT system control structure D. Corporate governance structure 65. In order to achieve the objective of managing risk, management should establish control structures that include, at a minimum: A. Accounting internal controls. B. Accounting internal controls, IT controls, corporate governance, enterprise risk management, and IT governance. C. IT controls, IT governance, corporate governance, and accounting internal controls. D. IT controls and accounting internal controls. 1-9 9 0 66. The company’s development and adherence to this should reduce the opportunities for managements or employees to conduct fraud. A. Code of ethics B. Internal control structure C. Application controls D. Corporate governance 67X. The COSO report, Internal Controls – Integrated Framework, identified interrelated components of internal control. Which of the following is not one of those components? A. Monitoring B. Risk assessment C. Control activities D. Enterprise risk management 68. IT controls can be divided into two categories. Which of the following is a correct statement of one of those categories? A. Application controls apply overall to the IT accounting system. B. Application controls apply to the prevention of erroneous or incomplete input or processing of data. C. Application controls are used specifically in accounting applications to control inputs, processing, and output. D. Application controls are used to prohibit fraudulent financial reporting. 69. An elaborate system of checks and balances, whereby a company’s leadership is held accountable for building shareholder value and creating confidence in the financial reporting processes, is referred to as: A. Enterprise risk management B. Corporate governance C. Application controls D. Internal control structure 70. The purpose of this 2002 act was to improve financial reporting and reinforce the importance of corporate ethics. A. Foreign Corrupt Practices Act B. Sarbanes-Oxley Act C. Securities and Exchange Act D. Treadway Act 71. Which of the following is not one of the corporate functions interrelated within the corporate governance system? A. Management Oversight B. Ethical Conduct C. Risk Assessment D. Financial Stewardship 72. The proper management, control, and use of IT systems are known as: A. IT Governance B. IT Controls C. IT Risk Management D. IT Code of Ethics 73. Accountants have several possible roles related to accounting information systems. Which of the following is not normally one of those roles? A. Auditor of an AIS B. User of the AIS C. Programmer of the AIS 1-10 9 0 D. Design of the AIS 74. There are many reasons for accountants to become aware of potential unethical behaviors. Which of the following is not one of the reasons identified by the authors? A. Accountants are responsible for identifying unethical and illegal activities. B. Accounts assist in developing and implementing internal control structures that should decrease the chance of unethical actions. C. Accountants are often pressured to assist in, or cover up, unethical actions. D. Accountants deal with assets or records that could easily tempt accountants to engage in unethical behavior. ANSWERS TO TEST BANK – CHAPTER 1 – MULTIPLE CHOICE: 11. B 24. A 37. D 12. C 25. C 38. A 13. B 26. A 39. B 14. A 27. D 40. C 15. D 28. A 41. D 16. A 29. B 42. D 17. B 30. D 43. B 18. C 31. C 44. A 19. D 32. C 45. D 20. B 33. B 46. A 21. B 34. C 47. C 22. A 35. B 48. B 23. D 36. B 49. C 49A. B 50. 51. 52. 53. 54. 55. 56. 57. 58. 59X. 60. 61. 62. A D A C B C A B C D B C B 63X. D 64. B 65. C 66. A 67X. D 68. C 69. B 70. B 71. C 72. A 73. C 74. A TEST BANK – CHAPTER 1 – TRUE/FALSE: 75. A business process has a well-defined beginning and end. TRUE 76. Each business process has a direct effect on the financial status of an organization. FALSE: The process could have an indirect effect. 77. Few accounting information systems rely on computer hardware and software to track business processes. FALSE: Most accounting information systems rely on computer hardware and software. 78. The rethinking and redesigning that occur during business process reengineering are aided by the use of information technology. TRUE 79. There are very few business processes that have the potential to be improved by IT enablement. FALSE 80. Business process reengineering should leverage the capabilities of information technology to improve the efficiency of business processes. TRUE 81. It is important for accountants to have some understanding of basic computer terminology. TRUE 82. When files are organized as sequential access, and the user needs to access record number 250, the previous 249 1-11 9 0 records will be read by the computer before reading record number 250. TRUE 83. When files are organized as sequential access, the sequence is normally based on one key record in each file. FALSE: the key is a field – not a record 84. Batch processing is best suited to applications that have large volumes of similar transactions that can be processed as regular intervals. TRUE 85. Online processing is the opposite of real-time processing. FALSE: Online processing is the opposite of batch processing. 86. Batch processing is best suited to sequential access files. TRUE 87. Online processing is best suited to sequential access files. FALSE: random access files, not sequential access files. 88. Online processing is best suited to situations were there is a large volume of records but only a few records are needed to process any individual transaction. TRUE 89. Each time a new transaction is completed, parts of the data warehouse must be updated. FALSE: parts of the operational database must be updated. 90. Data in the data warehouse are called nonvolatile because they do not change rapidly in the same way that operational data change. TRUE 91. A system of local area networks connected over any distance via other net work connections is called a WAN, or wide area network. TRUE 92. E-business is a type of e-commerce. FALSE: e-commerce is a type of e-business 93. The “intercompany” component of electronic data interchange means that two or more companies are conducting business electronically. TRUE 94. In order to have an automated matching system it is necessary to have access to paper copies of purchase orders and invoices. FALSE: All of the related files need to be online. 95. When automated matching is used, the system will not approve an invoice for payment unless the items and quantities match with the packing slip and the prices match the purchase order prices. TRUE 96. The evaluated receipt settlement system is an IT enabled system that reduces the time and cost of processing customer payments. 1-12 9 0 FALSE: processing vendor payments. 97. ERP systems are based on a relational database system. TRUE 98. Traditional accounting software is much more comprehensive and encompassing that ERP software. FALSE 99. Before ERP software systems, modules such as human resources were in separate software but well integrated with the accounting software. FALSE: were NOT well integrated. 100. Although accountants are heavily involved in the creation, implementation, and monitoring of the control structure, management has the ultimate responsibility to establish a control environment. TRUE 101. Once a company has decided on the control processes needed, it is not necessary to have an ongoing assessment of risks. FALSE: it is necessary to have an ongoing assessment of risks. 102. A code of ethics should reduce opportunities for employees to conduct fraud if management emphasizes the cost and disciplines or discharges those who violate it. TRUE 103. IT systems are to be chosen and implemented to support the attainment of strategies and objectives. TRUE 104. It is likely that an accountant will select a career path, within accounting, that will not in some way, involve the use of an accounting information system. FALSE 105. An auditor cannot make informed decisions necessary to complete the audit without an understanding of the accounting information system. TRUE 106. The accounting information system is often the tool used to commit or cover up unethical behavior. TRUE ANSWERS TO TEST BANK – CHAPTER 1 – TRUE/FALSE: 75. True 82. True 89. False 76. False 83. False 90. True 77. False 84. True 91. True 78. True 85. False 92. False 79. False 86. True 93. True 80. True 87. False 94. False 81. True 88. True 95. True 96. False 97. True 98. False 99. False 100. True 101. False 102. True 1-13 9 0 103. 104. 105. 106. True False True True Hall 5e TB Ch03 - AIS Accountancy Chapter 3—Ethics, Fraud, and Internal Control TRUE/FALSE 1. The ethical principle of justice asserts that the benefits of the decision should be distributed fairly to those who share the risks. ANS: T 2. The ethical principle of informed consent suggests that the decision should be implemented so as to minimize all of the risks and to avoid any unnecessary risks. ANS: F 3. Employees should be made aware of the firm’s commitment to ethics. ANS: T 4. Business ethics is the analysis of the nature and social impact of computer technology, and the corresponding formulation and justification of policies for the ethical use of such technology. ANS: F 5. Para computer ethics is the exposure to stories and reports found in the popular media regarding the good or bad ramifications of computer technology. ANS: F 6. Source code is an example of intellectual property. ANS: T 7. Copyright laws and computer industry standards have been developed jointly and rarely conflict. ANS: F 8. Business bankruptcy cases always involve fraudulent behavior. ANS: F 9. Defalcation is another word for financial fraud. ANS: T 10. The trend toward distributed data processing increases the exposure to fraud from remote locations. ANS: T 11. The external auditor is responsible for establishing and maintaining the internal control system. ANS: F 1 0 12. Segregation of duties is an example of an internal control procedure. ANS: T 13. Controls in a computer-based information system are identical to controls in a manual system. ANS: F 14. Preventive controls are passive techniques designed to reduce fraud. ANS: T 15. Ethical issues and legal issues are essentially the same. ANS: F 16. Internal control systems are recommended but not required of firms subject to the Foreign Corrupt Practices Act. ANS: F 17. Operations fraud is the misuse or theft of the firm’s computer resources. ANS: T 18. The Foreign Corrupt Practices Act requires only that a firm keep good records. ANS: F 19. A key modifying assumption in internal control is that the internal control system is the responsibility of management. ANS: T 20. Database management fraud includes altering, updating, and deleting an organization’s data. ANS: F 21. While the Sarbanes-Oxley Act prohibits auditors from providing non-accounting services to their audit clients, they are not prohibited from performing such services for non-audit clients or privately held companies. ANS: T 22. The Sarbanes-Oxley Act requires the audit committee to hire and oversee the external auditors. ANS: T 23. Section 404 requires that corporate management (including the CEO) certify their organization’s internal controls on a quarterly and annual basis. 1 0 ANS: F 24. Section 302 requires the management of public companies to assess and formally report on the effectiveness of their organization’s internal controls. ANS: F 25. The objective of SAS 99 is to seamlessly blend the auditor’s consideration of fraud into all phases of the audit process. ANS: T MULTIPLE CHOICE 1. Which ethical principle states that the benefit from a decision must outweigh the risks, and that there is no alternative decision that provides the same or greater benefit with less risk? a minimize risk . b justice . c informed consent . d proportionality . ANS: D 2. Individuals who acquire some level of skill and knowledge in the field of computer ethics are involved in which level of computer ethics? a para computer ethics . b pop computer ethics . c theoretical computer ethics . d practical computer ethics . ANS: A 3. All of the following are issues of computer security except a releasing incorrect data to authorized individuals . b permitting computer operators unlimited access to the computer room . c permitting access to data by unauthorized individuals . d providing correct data to unauthorized individuals . 1 0 ANS: B 4. Which characteristic is not associated with software as intellectual property? a uniqueness of the product . b possibility of exact replication . c automated monitoring to detect intruders . d ease of dissemination . ANS: C 5. For an action to be called fraudulent, all of the following conditions are required except a poor judgment . b false representation . c intent to deceive . d injury or loss . ANS: A 6. One characteristic of employee fraud is that the fraud a is perpetrated at a level to which internal controls do not apply . b involves misstating financial statements . c involves the direct conversion of cash or other assets to the employee’s personal benefit . d involves misappropriating assets in a series of complex transactions involving third . parties ANS: C 7. Forces which may permit fraud to occur do not include a a gambling addiction . b lack of segregation of duties . c centralized decision making environment . d questionable integrity of employees . 1 0 ANS: C 8. Which of the following best describes lapping? a applying cash receipts to a different customer’s account in an attempt to conceal previous . thefts of funds b inflating bank balances by transferring money among different bank accounts . c expensing an asset that has been stolen . d creating a false transaction . ANS: A 9. Operations fraud includes a altering program logic to cause the application to process data incorrectly . b misusing the firm’s computer resources . c destroying or corrupting a program’s logic using a computer virus . d creating illegal programs that can access data files to alter, delete, or insert values . ANS: B 10. Who is responsible for establishing and maintaining the internal control system? a the internal auditor . b the accountant . c management . d the external auditor . ANS: C 11. The concept of reasonable assurance suggests that a the cost of an internal control should be less than the benefit it provides . b a well-designed system of internal controls will detect all fraudulent activity . c the objectives achieved by an internal control system vary depending on the data . processing method d the effectiveness of internal controls is a function of the industry environment . 1 0 ANS: A 12. Which of the following is not a limitation of the internal control system? a errors are made due to employee fatigue . b fraud occurs because of collusion between two employees . c the industry is inherently risky . d management instructs the bookkeeper to make fraudulent journal entries . ANS: C 13. The most cost-effective type of internal control is a preventive control . b accounting control . c detective control . d corrective control . ANS: A 14. Which of the following is a preventive control? a credit check before approving a sale on account . b bank reconciliation . c physical inventory count . d comparing the accounts receivable subsidiary ledger to the control account . ANS: A 15. A well-designed purchase order is an example of a a preventive control . b detective control . c corrective control . d none of the above . 1 0 ANS: A 16. A physical inventory count is an example of a a preventive control . b detective control . c corrective control . d feedforward control . ANS: B 17. The bank reconciliation uncovered a transposition error in the books. This is an example of a a preventive control . b detective control . c corrective control . d none of the above . ANS: B 18. In balancing the risks and benefits that are part of every ethical decision, managers receive guidance from each of the following except a justice . b self interest . c risk minimization . d proportionality . ANS: B 19. Which of the following is not an element of the internal control environment? a management philosophy and operating style . b organizational structure of the firm . c well-designed documents and records . d the functioning of the board of directors and the audit committee 1 0 . ANS: C 20. Which of the following suggests a weakness in the internal control environment? a the firm has an up-to-date organizational chart . b monthly reports comparing actual performance to budget are distributed to managers . c performance evaluations are prepared every three years . d the audit committee meets quarterly with the external auditors . ANS: C 21. Which of the following indicates a strong internal control environment? a the internal audit group reports to the audit committee of the board of directors . b there is no segregation of duties between organization functions . c there are questions about the integrity of management . d adverse business conditions exist in the industry . ANS: A 22. According to SAS 78, an effective accounting system performs all of the following except a identifies and records all valid financial transactions . b records financial transactions in the appropriate accounting period . c separates the duties of data entry and report generation . d records all financial transactions promptly . ANS: C 23. Which of the following is the best reason to separate duties in a manual system? a to avoid collusion between the programmer and the computer operator . b to ensure that supervision is not required . c to prevent the record keeper from authorizing transactions . d to enable the firm to function more efficiently 1 0 . ANS: C 24. Segregation of duties in the computer-based information system includes a separating the programmer from the computer operator . b preventing management override . c separating the inventory process from the billing process . d performing independent verifications by the computer operator . ANS: A 25. Which of the following is not an internal control procedure? a authorization . b management’s operating style . c independent verification . d accounting records . ANS: B 26. The decision to extend credit beyond the normal credit limit is an example of a independent verification . b authorization . c segregation of functions . d supervision . ANS: B 27. When duties cannot be segregated, the most important internal control procedure is a supervision . b independent verification . c access controls . d accounting records 1 0 . ANS: A 28. An accounting system that maintains an adequate audit trail is implementing which internal control procedure? a access controls . b segregation of functions . c independent verification . d accounting records . ANS: D 29. Employee fraud involves three steps. Of the following, which is not involved? a concealing the crime to avoid detection . b stealing something of value . c misstating financial statements . d converting the asset to a usable form . ANS: C 30. Which of the following is not an example of independent verification? a comparing fixed assets on hand to the accounting records . b performing a bank reconciliation . c comparing the accounts payable subsidiary ledger to the control account . d permitting authorized users only to access the accounting system . ANS: D 31. The importance to the accounting profession of the Foreign Corrupt Practices Act of 1977 is that a bribery will be eliminated . b management will not override the company’s internal controls . c firms are required to have an effective internal control system . 1 0 d firms will not be exposed to lawsuits . ANS: C 32. The board of directors consists entirely of personal friends of the chief executive officer. This indicates a weakness in a the accounting system . b the control environment . c control procedures . d this is not a weakness . ANS: B 33. Computer fraud can take on many forms, including each of the following except a theft or illegal use of computer-readable information . b theft, misuse, or misappropriation of computer equipment . c theft, misuse, or misappropriation of assets by altering computer-readable records and . files d theft, misuse, or misappropriation of printer supplies . ANS: D 34. When certain customers made cash payments to reduce their accounts receivable, the bookkeeper embezzled the cash and wrote off the accounts as uncollectible. Which control procedure would most likely prevent this irregularity? a segregation of duties . b accounting records . c accounting system . d access controls . ANS: A 35. The office manager forgot to record in the accounting records the daily bank deposit. Which control procedure would most likely prevent or detect this error? a segregation of duties . 1 0 b independent verification . c accounting records . d supervision . ANS: B 36. Business ethics involves a how managers decide on what is right in conducting business . b how managers achieve what they decide is right for the business . c both a and b . d none of the above . ANS: C 37. All of the following are conditions for fraud except a false representation . b injury or loss . c intent . d material reliance . ANS: D 38. The four principal types of fraud include all of the following except a bribery . b gratuities . c conflict of interest . d economic extortion . ANS: B 39. The characteristics of useful information include a summarization, relevance, timeliness, accuracy, and completeness . 1 0 b relevance, summarization, accuracy, timelessness, and completeness . c timeliness, relevance, summarization, accuracy, and conciseness . d disaggregation, relevance, timeliness, accuracy, and completeness . ANS: A 40. Internal control system have limitations. These include a possibility of honest error . b circumvention . c management override . d stability of systems . ANS: D 41. Management can expect various benefits to follow from implementing a system of strong internal control. Which of the following benefits is least likely to occur? a reduced cost of an external audit. . b prevents employee collusion to commit fraud. . c availability of reliable data for decision-making purposes. . d some assurance of compliance with the Foreign Corrupt Practices Act of 1977. . e some assurance that important documents and records are protected. . ANS: B 42. Which of the following situations is not a segregation of duties violation? a The treasurer has the authority to sign checks but gives the signature block to the . assistant treasurer to run the check-signing machine. b The warehouse clerk, who has the custodial responsibility over inventory in the . warehouse, selects the vendor and authorizes purchases when inventories are low. c The sales manager has the responsibility to approve credit and the authority to write off . accounts. d The department time clerk is given the undistributed payroll checks to mail to absent . employees. e The accounting clerk who shares the record keeping responsibility for the accounts . receivable subsidiary ledger performs the monthly reconciliation of the subsidiary ledger and the control account. 1 0 ANS: B 43. Which of the following is not an issue to be addressed in a business code of ethics required by the SEC? a Conflicts of interest . b Full and Fair Disclosures . c Legal Compliance . d Internal Reporting of Code Violations . e All of the above are issues to be addressed . ANS: E SHORT ANSWER 1. What are the main issues to be addressed in a business code of ethics required by the SEC? ANS: Conflicts of interest, Full and Fair Disclosures, Legal Compliance, Internal Reporting of Code Violations, Accountability 2. List the four broad objectives of the internal control system. ANS: safeguard assets, ensure the accuracy and reliability of accounting records, promote organizational efficiency, comply with management’s policies and procedures 3. Explain the purpose of the PCAOB ANS: The PCAOB is empowered to set auditing, quality control, and ethics standards; to inspect registered accounting firms; to conduct investigations; and to take disciplinary actions. 4. What are the five internal control components described in the SAS 78 / COSO framework ANS: the control environment, risk assessment, information and communication, monitoring, and control activities 5. What are management responsibilities under section 302 and 404? ANS: Section 302 requires that corporate management (including the CEO) certify their organization’s internal controls on a quarterly and annual basis. Section 404 requires the management of public companies to assess and formally report on the effectiveness of their organization’s internal controls. 1 0 6. Identify to indicate whether each procedure is a preventive or detective control. a authorizing a credit sale . b preparing a bank reconciliation . Preventive Detective Preventive Detective c locking the warehouse . Preventive Detective d preparing a trial balance . e counting inventory . Preventive Detective Preventive Detective ANS: A. preventive; B. detective; C. preventive; D. detective; E. detective Use the internal control procedures listed below to complete the statements. segregation of duties general authorization access controls supervision specific authorization accounting records independent verification 7. A clerk reorders 250 items when the inventory falls below 25 items. This is an example of __________________________. ANS: general authorization 8. The internal audit department recalculates payroll for several employees each pay period. This is an example of __________________________. ANS: independent verification 9. Locking petty cash in a safe is an example of __________________________. ANS: access controls 10. Approving a price reduction because goods are damaged is an example of __________________________. ANS: specific authorization 11. Using cameras to monitor the activities of cashiers is an example of __________________________. 1 0 ANS: supervision 12. Not permitting the computer programmer to enter the computer room is an example of _______________________________. ANS: segregation of duties 13. Sequentially numbering all sales invoices is an example of __________________________. ANS: accounting records 14. What are the five conditions necessary for an act to be considered fraudulent? ANS: false representation, material fact, intent, justifiable reliance, and injury or loss 15. What is the objective of SAS 99? ANS: The objective of SAS 99 is to seamlessly blend the auditor’s consideration of fraud into all phases of the audit process. 16. Distinguish between exposure and risk. ANS: Exposure is the absence or weakness of a control which increases the firm’s risk of financial loss or injury. Risk is the probability of incurring such a loss or injury. 17. Explain the characteristics of management fraud. ANS: Management fraud typically occurs at levels above where the internal control system is effective. Financial statements are frequently modified to make the firm appear more healthy than it actually is. If any misappropriation of assets occurs, it is usually well hidden. 18. The text discusses many questions about personal traits of employees which might help uncover fraudulent activity. What are three? ANS: executives: with high personal debt, living beyond their means, engaged in habitual gambling, appear to abuse alcohol or drugs, appear to lack personal codes of ethics, appear to be unstable 19. Give two examples of employee fraud and explain how the theft might occur. ANS: Charges to expense accounts: Cash could be stolen and charged to a miscellaneous expense account. Once the account is closed, detection would be more difficult. 1 0 Lapping: This involves converting cash receipts to personal use. If a customer’s check is taken, his/her balance will not reflect a payment and will be detected when a statement is sent. In order to conceal this fraud, a later payment is used to cover the stolen check. This is in effect a small scale Ponzi scheme. 20. What are the six broad classes of physical control activities defined by SAS 78? ANS: Transaction authorization, segregation of duties, supervision, access controls, accounting records, independent verification ESSAY 1. The text describes six internal control activities. List four of them and provide a specific example of each one. ANS: Control Activity Authorization Example general (purchase of inventory when level drops) or specific (credit approval beyond normal limit) Segregation of functions separate authorization from processing separate custody of assets from record keeping Supervision required when separation of duties is not possible, such as opening the mail (cash receipts) Accounting records maintain an adequate audit trail Access controls Independent verification maintain physical security bank reconciliation, physical inventory count 2. Contrast management fraud with employee fraud. ANS: Employee fraud is usually designed to directly convert cash or other assets to the employee’s personal benefit. Management fraud involves less of a direct benefit to the perpetrator. Management fraud may involve an attempt to misstate financial performance in order to gain additional compensation or to earn a promotion. Management fraud may also involve an attempt to misstate financial performance in order to increase the price of the company’s stock or to reduce the cost of debt. 3. Discuss the importance of the Foreign Corrupt Practices Act of 1977 to the accounting profession. ANS: The Foreign Corrupt Practices Act of 1977 (FCPA) is a law that requires all companies registered with the Securities and Exchange Commission to: keep records that fairly and reasonably reflect the transactions of the firm and its financial position 1 0 maintain a system of internal control that provides reasonable assurance that the organization’s objectives are met As a result of the Foreign Corrupt Practices Act of 1977, management devotes substantial time to developing and maintaining the internal control structure because failure to do so violates the FCPA and could lead to heavy fines and imprisonment. Accountants are key participants in establishing and maintaining the internal control structure. Therefore, it is accountants who are instrumental in ensuring that the firm is in compliance with the Foreign Corrupt Practices Act of 1977. 4. Why are the computer ethics issues of privacy, security, and property ownership of interest to accountants? ANS: Privacy is a concern because the nature of computer data files makes it possible for unauthorized individuals to obtain information without it being recognized as “missing” from its original location. Security is a concern because its absence makes control from a privacy viewpoint questionable. In addition lack of security may permit unauthorized changes to data, therefore distorting information that is reported. Property ownership raises issues of legitimacy of organizational software, valuation of assets, and questions of lost revenues. 5. According to common law, there are five conditions that must be present for an act to be deemed fraudulent. Name and explain each. ANS: In order for an act to be deemed fraudulent under common law, it must possess the following characteristics: false representation, meaning some misrepresentation or omission must have occurred, material facts, meaning that the facts must influence someone’s actions, intent, meaning there must have been the intention to deceive others, justifiable reliance, meaning it did affect someone’s decision, and injury or loss must have occurred. 6. Management fraud is regarded as more serious than employee fraud. Three special characteristics have been discussed for management fraud. What are they? Explain. ANS: It usually occurs at levels above the normal internal control system. There is typically an intent to present a better picture of the business than is valid, often to deceive creditors and/or shareholders. If assets are misappropriated, the route is quite devious involving a maze of business transactions. 7. Four principal types of corruption are discussed. Name all four and explain at least two. ANS: Corruption involves an executive, manager, or employee of a business working in collusion with an outsider. The four principal types of corruption are: bribery, illegal gratuities, conflicts of interest, and economic extortion. 1 0 Bribery involves giving, offering, soliciting, or receiving things of value to influence an official in the performance of his or her lawful duties. An illegal gratuity involves giving. receiving, offering, or soliciting something of value because of an official act that has been taken. A conflict of interest occurs when an employee acts on behalf of a third party during the discharge of his or her duties or has self-interest in the activity being performed. Economic extortion is the use (or threat) of force (including economic sanctions) by an individual or organization to obtain something of value. 8. Misappropriation of assets can involve various schemes: charges to expense accounts, lapping, and transaction fraud. Explain each and give an example. ANS: Charges to expense accounts involve fictitious charges to such accounts as miscellaneous expense to offset theft of an asset. Because the expense account is closed to revenue at the end of the period, the period in which it could be detected is short. Lapping is a technique whereby an early theft is covered up by a later one, i.e., with the moves “lapping” over each other. The simplest example involves taking a customer’s payment. A later payment is then credited to the first customer’s account, not the second. And on it goes. This requires some control over billing to avoid tipping off the last customer. Transaction fraud involves deleting, altering, or adding false transactions to divert assets to the perpetrator. For example, if an employee leaves the business and the supervisor fails to notify payroll and continues to clock the employee in and out, a fraudulent paycheck would be produced. If, in addition, the supervisor distributes the paycheck, it can be kept, and cashed. 9. Computer fraud is easiest at the data collection stage. Why? ANS: Computer fraud is easiest at the data collection stage because much of what occurs after the data collection or input stage is not visible to human eyes. Once entered, the system will presume that the input is legitimate and will process it as all others. 10. Explain why collusion between employees and management in the commission of a fraud is difficult to both prevent and detect. ANS: Collusion among employees in the commission of a fraud is difficult to both prevent and detect. This is particularly true when the collusion is between managers and their subordinate employees. Management plays a key role in the internal control structure of an organization. They are relied upon to prevent and detect fraud among their subordinates. When they participate in fraud with the employees over whom they are supposed to provide oversight, the organization’s control structure is weakened, or completely circumvented, and the company becomes more vulnerable to losses. 11. Since all fraud involves some form of financial misstatement, how is Fraudulent Statement fraud different? 1 0 ANS: Fraudulent statements are associated with management fraud. While all fraud involves some form of financial misstatement, to meet the definition under this class of fraud scheme, the statement itself must bring direct or indirect financial benefit to the perpetrator. In other words, the statement is not simply a vehicle for obscuring or covering a fraudulent act. For example, misstating the cash account balance to cover the theft of cash does not fall under this class of fraud scheme. On the other hand, understating liabilities to present a more favorable financial picture of the organization to drive up stock prices does qualify. 12. Explain the problems associated with lack of auditor independence. ANS: Auditing firms who are also engaged by their clients to perform non-accounting activities such as actuarial services, internal audit outsourcing services, and consulting lack independence. They are essentially auditing their own work. This risk is that as auditors they will not bring to management’s attention detected problems that may adversely affect their consulting fees. For example, Enron’s auditors – Arthur Andersen – were also their internal auditor’s and their management consultants. 13. Explain the problems associated with lack of director independence ANS: Many boards of directors are comprised of individuals who are not independent. Examples of lack of independence are directors who: have a personal relationship by serving on the boards of other directors companies; have a business trading relationship as key customers or suppliers of the company; have a financial relationship as primary stockholders or have received personal loans from the company; have an operational relationship as employees of the company. 14. Explain the problems associated with Questionable Executive Compensation Schemes ANS: A survey by Thompson Financial revealed the strong belief that executives have abused stock-based compensation. The consensus is that fewer stock options should be offered than currently is the practice. Excessive use of short-term stock options to compensate directors and executives may result in short term thinking and strategies aimed at driving up stock prices at the expense of the firm’s longterm health. In extreme cases, financial statement misrepresentation has been the vehicle to achieve the stock price needed to exercise the option. 15. Explain the problems associated with inappropriate accounting practices. ANS: The use of inappropriate accounting techniques is a characteristic common to many financial statement fraud schemes. Enron made elaborate use of Special Purpose Entities (SPE) to hide liabilities through off balance sheet accounting. WorldCom management transferred transmission line costs from current expense accounts to capital accounts. This allowed them to defer some operating expenses and report higher earnings. Also, they reduced the book value of hard assets of MCI by $3.4 billion and increased goodwill by the same amount. Had the assets been left at book value, they would have been charged against earnings over four years. Goodwill, on the other hand, was amortized over much longer period. 16. Explain the purpose of the PCAOB. ANS: 1 0 b relevance, summarization, accuracy, timelessness, and completeness . c timeliness, relevance, summarization, accuracy, and conciseness . d disaggregation, relevance, timeliness, accuracy, and completeness . ANS: A 40. Internal control system have limitations. These include a possibility of honest error . b circumvention . c management override . d stability of systems . ANS: D 41. Management can expect various benefits to follow from implementing a system of strong internal control. Which of the following benefits is least likely to occur? a reduced cost of an external audit. . b prevents employee collusion to commit fraud. . 1 0 c availability of reliable data for decision-making purposes. . d some assurance of compliance with the Foreign Corrupt Practices Act of 1977. . e some assurance that important documents and records are protected. . ANS: B 42. Which of the following situations is not a segregation of duties violation? a The treasurer has the authority to sign checks but gives the signature block to the . assistant treasurer to run the check-signing machine. b The warehouse clerk, who has the custodial responsibility over inventory in the . warehouse, selects the vendor and authorizes purchases when inventories are low. c The sales manager has the responsibility to approve credit and the authority to write off . accounts. d The department time clerk is given the undistributed payroll checks to mail to absent . employees. e The accounting clerk who shares the record keeping responsibility for the accounts . receivable subsidiary ledger performs the monthly reconciliation of the subsidiary ledger and the control account. 1 0 Chapter 9 Interim Financial Reporting PROBLEM 1: TRUE OR FALSE 1 FALSE 6. FALSE . 2 TRUE 7. FALSE . 3 FALSE 8. TRUE . 4 TRUE 9. FALSE . 5 FALSE 10. TRUE . PROBLEM 2: FOR CLASSROOM DISCUSSION 1. D 2. A 3. B 4. B 5. B 6. C 7. A 8. Solution: Revenue Cost of goods sold Gross profit Other operating expenses Loss on inventory write-down (2.2M – 2.8M) Interest income (2M x 12% x 3/12) Profit 9,000,000 (5,000,000) 4,000,000 (2,800,000) (600,000) 60,000 660,000 Other comprehensive income: Unrealized loss on FVOCI [450K – (500K + 60K)] Comprehensive income 0 (110,000) 550,000 0 9. Solution: Revenue Cost of goods sold Gross profit Other operating expenses Property tax expense (1.2M x 1/4) Depreciation expense [(1.2M / 5) x 3/12] Insurance expense Profit 7,000,000 (3,000,000) 4,000,000 (2,800,000) (300,000) (60,000) (15,000) 825,000 Other comprehensive income: Revaluation increase (4.4M - 3.8M) Comprehensive income 600,000 1,425,000 10. Solution: Revenue Cost of goods sold Gross profit Other operating expenses Salaries expense (2.8M x 3/12) Impairment loss Profit from continuing operations Discontinued operations Profit for the year 9,000,000 (3,000,000) 6,000,000 (2,800,000) (700,000) (500,000) 2,000,000 (700,000) 1,300,000 11. Solution: 1,200,000 (300,000) 900,000 30% 270,000 Estimated annual profit before tax Less: Operating loss carryforward Total Multiply by: Estimated annual income tax expense Divide by: Estimated annual profit before tax Weighted average income tax rate 1,200,000 22.50% Profit before tax - 1st quarter Multiply by: Weighted ave. tax rate Income tax expense 350,000 22.50% 78,750 0 0 PROBLEM 3: EXERCISES 1. Solution: Revenue Cost of goods sold Gross profit Other operating expenses Property tax expense Impairment loss Loss 9,000,000 (5,000,000) 4,000,000 (2,800,000) (250,000) (600,000) 350,000 The write-up is not recognized because there are no write-downs in the past. 2. Solution: Revenue Cost of goods sold Gross profit Other operating expenses Insurance expense (60K x 3/24) Commission expense Unrealized gain (1.45M - 1.5M) Profit from continuing operations Discontinued operations (2.8M - 3M) + 800K Profit for the year Other comprehensive income: Comprehensive income 3. 9,000,000 (5,000,000) 4,000,000 (2,800,000) (7,500) (80,000) (50,000) 1,062,500 (1,000,000) 62,500 62,500 Solution: Revenue Cost of goods sold Gross profit Other operating expenses Employee benefits Depreciation expense (see solution below) Interest income (1.2M x 10% x 3/12) Profit for the year 9,000,000 (5,000,000) 4,000,000 (2,800,000) (450,000) (45,000) 30,000 735,000 By trial and error, the depreciation method used by Puppy is determined to be the SYD method. Trial and error: 0 0 Historical cost (squeeze) Accumulated depreciation Carrying amount - 1/1/x1 1,000,000 (540,000) 460,000 Historical cost Residual value Depreciable amount 1,000,000 (100,000) 900,000 Depreciation - 1st yr. (900K x 5/15) Depreciation - 2nd yr. (900K x 4/15) Accumulated depreciation - 1/1/x1 300,000 240,000 540,000 Depreciation - 20x1 (900K x 3/15) Multiply by: Depreciation - 1st qtr. 180,000 3/12 45,000 4. Solution: Estimated annual profit before tax Less: Operating loss carryforward (300K / 30%) 1,200,000 (1,000,000 ) 200,000 30% 60,000 1,200,000 5.00% Total Multiply by: Estimated annual income tax expense Divide by: Estimated annual profit before tax Weighted average income tax rate Profit before tax - 1st quarter Multiply by: Weighted ave. tax rate Income tax expense 350,000 5.00% 17,500 5. Solution: Estimated annual profit before tax Less: Operating loss carryforward Total Multiply by: Estimated annual income tax expense Divide by: Estimated annual profit before tax Weighted average income tax rate 800,000 (100,000) 700,000 30% 210,000 800,000 26.25% Profit before tax - 1st quarter Multiply by: Weighted ave. tax rate Income tax expense 280,000 26.25% 73,500 PROBLEM 4: MULTIPLE CHOICE – THEORY 1 6. C D . 2 7. B C . 8. C 3 A 0 0 . 4 . 5 . D D 9. C 10. A PROBLEM 5: MULTIPLE CHOICE – COMPUTATIONAL 1. B 70,000 loss recognized immediately; (100,000 x ¼) = 25,000 insurance expense allocated to the quarter 2. C Solution: Depreciation expense (60,000 x 6/12) 30,000 Salaries expense - bonus (120,000 x 6/12) 60,000 Total expense for the semi-annual period 90,000 3. B Solution: Property tax (180,000 x 1/4) Costs benefitting the remainder of the year (300,000 x 1/3) Total expense for the 2nd quarter 4. C 45,000 100,000 145,00 0 5. B (-20,000 - 30,000 + 90,000) = 40,000 6. C (200,000 x 25%) = 50,000 7. C – The entire write-down of 900,000 is recognized in the 2 quarter. nd 8. D 9. C 10. B Solution: 1,200,000 Estimated annual profit before tax Less: Operating loss carryforward (120K / 30%) Total (400,000) 800,000 0 0 30% 240,000 1,200,000 20.00% Multiply by: Estimated annual income tax expense Divide by: Estimated annual profit before tax Weighted average income tax rate 1st Qtr. Profits before taxes Multiply by: Weighted ave. tax rate Income tax expense 350,00 0 20.00% 70,000 2nd Qtr. 3rd Qtr. 200,000 400,000 20.00% 40,000 20.00% 80,000 0 0 Accounting Information Systems, 7e—Test Bank, Chapter 4 Chapter 4—The Revenue Cycle TRUE/FALSE 1. The packing slip is also known as the shipping notice. ANS: F PTS: 1 2. The bill of lading is a legal contract between the buyer and the seller. ANS: F PTS: 1 3. Another name for the stock release form is the picking ticket. ANS: T PTS: 1 4. Warehouse stock records are the formal accounting records for inventory. ANS: F PTS: 1 5. The purpose of the invoice is to bill the customer. ANS: T PTS: 1 6. In most large organizations, the journal voucher file has replaced the formal general journal. ANS: T PTS: 1 7. The cash receipts journal is a special journal. ANS: T PTS: 1 8. In the revenue cycle, the internal control “limit access” applies to physical assets only. ANS: F PTS: 1 9. In real-time processing systems, routine credit authorizations are automated. ANS: T PTS: 1 10. In a computerized accounting system, segregation of functions refers to inventory control, accounts receivable, billing, and general ledger tasks. ANS: F PTS: 1 11. A written customer purchase order is required to trigger the sales order system. 1 ANS: F PTS: 1 12. Inventory control has physical custody of inventory. ANS: F PTS: 1 13. The principal source document in the sales order system is the sales order. ANS: T PTS: 1 14. Sales orders should be prenumbered documents. ANS: T PTS: 1 15. Integrated accounting systems automatically transfer data between modules. ANS: T PTS: 1 16. If a customer submits a written purchase order, there is no need to prepare a sales order. ANS: F PTS: 1 17. Sales return involves receiving, sales, credit, and billing departments, but not accounts receivable. ANS: F PTS: 1 18. A remittance advice is a form of turn-around document. ANS: T PTS: 1 19. A bill of lading is a request for payment for shipping charges. ANS: F PTS: 1 20. In point of sale systems, authorization takes the form of validation of credit card charges. ANS: T PTS: 1 21. The warehouse is responsible for updating the inventory subsidiary ledger. ANS: F PTS: 1 22. In a manual system, the billing department is responsible for recording the sale in the sales journal. ANS: T PTS: 1 23. The stock release document is prepared by the shipping department to provide evidence that the goods have been released to the customer. ANS: F PTS: 1 24. The accounts receivable clerk is responsible for updating the AR Control accounts to reflect each customer sale. ANS: F PTS: 1 25. When customer payments are received, the mailroom clerk sends the checks to the cash receipts clerk and the remittance advices to the AR clerk. ANS: T PTS: 1 26. Physical controls are imbedded in computer systems to control access to data. ANS: F PTS: 1 27. Process controls are controls over the logic of the application. ANS: T PTS: 1 28. In a basic technology revenue cycle system, a robust passwold control policy should be implemented. ANS: T PTS: 1 29. In an integrated cash receipts system, the cash receipts clerk reconciles the checks and the remittance advices and prepares deposit slips. ANS: T PTS: 1 30. Multilevel security employs programmed techniques that permit simultaneous access to a central system by many users with different access privileges but allows them to obtaining information for which they lack authorization. ANS: F PTS: 1 31. Application integrity is achieved through the systems development and program change processes. ANS: T MULTIPLE CHOICE PTS: 1 1. The revenue cycle consists of a. one subsystem–order entry b. two subsystems–sales order processing and cash receipts c. two subsystems–order entry and inventory control d. three subsystems–sales order processing, credit authorization, and cash receipts ANS: B PTS: 1 2. The reconciliation that occurs in the shipping department is intended to ensure that a. credit has been approved b. the customer is billed for the exact quantity shipped c. the goods shipped match the goods ordered d. inventory records are reduced for the goods shipped ANS: C PTS: 1 3. The adjustment to accounting records to reflect the decrease in inventory due to a sale occurs in the a. warehouse b. shipping department c. billing department d. inventory control department ANS: D PTS: 1 4. Which document triggers the revenue cycle? a. the sales order b. the customer purchase order c. the sales invoice d. the journal voucher ANS: B PTS: 1 5. Copies of the sales order can be used for all of the following except a. purchase order b. credit authorization c. shipping notice d. packing slip ANS: A PTS: 1 6. The purpose of the sales invoice is to a. record reduction of inventory b. transfer goods from seller to shipper c. bill the customer d. select items from inventory for shipment ANS: C PTS: 1 7. The customer open order file is used to a. respond to customer queries b. fill the customer order c. ship the customer order d. authorize customer credit ANS: A PTS: 1 8. The stock release copy of the sales order is not used to a. locate and pick the items from the warehouse shelves b. record any out-of-stock items c. authorize the warehouse clerk to release custody of the inventory to shipping d. record the reduction of inventory ANS: D PTS: 1 9. The shipping notice a. is mailed to the customer b. is a formal contract between the seller and the shipping company c. is always prepared by the shipping clerk d. informs the billing department of the quantities shipped ANS: D PTS: 1 10. The billing department is not responsible for a. updating the inventory subsidiary records b. recording the sale in the sales journal c. notifying accounts receivable of the sale d. sending the invoice to the customer ANS: A PTS: 1 11. Customers should be billed for back-orders when a. the customer purchase order is received b. the backordered goods are shipped c. the original goods are shipped d. customers are not billed for backorders because a backorder is a lost sale ANS: B PTS: 1 12. Usually specific authorization is required for all of the following except a. sales on account which exceed the credit limit b. sales of goods at the list price c. a cash refund for goods returned without a receipt d. write off of an uncollectible account receivable ANS: B PTS: 1 13. Which of following functions should be segregated? a. opening the mail and making the journal entry to record cash receipts b. authorizing credit and determining reorder quantities c. maintaining the subsidiary ledgers and handling customer queries d. providing information on inventory levels and reconciling the bank statement ANS: A PTS: 1 14. Which situation indicates a weak internal control structure? a. the mailroom clerk authorizes credit memos b. the record keeping clerk maintains both accounts receivable and accounts payable subsidiary ledgers c. the warehouse clerk obtains a signature before releasing goods for shipment d. the accounts receivable clerk prepares customer statements every month ANS: A PTS: 1 15. The most effective internal control procedure to prevent or detect the creation of fictitious credit memoranda for sales returns is to a. supervise the accounts receivable department b. limit access to credit memoranda c. prenumber and sequence check all credit memoranda d. require management approval for all credit memoranda ANS: D PTS: 1 16. The accounts receivable clerk destroys all invoices for sales made to members of her family and does not record the sale in the accounts receivable subsidiary ledger. Which procedure will not detect this fraud? a. prenumber and sequence check all invoices b. reconcile the accounts receivable control to the accounts receivable subsidiary ledger c. prepare monthly customer statements d. reconcile total sales on account to the debits in the accounts receivable subsidiary ledger ANS: C PTS: 1 17. Which department is least likely to be involved in the revenue cycle? a. credit b. accounts payable c. billing d. shipping ANS: B PTS: 1 18. Which document is included with a shipment sent to a customer? a. sales invoice b. stock release form c. packing slip d. shipping notice ANS: C PTS: 1 19. Good internal controls in the revenue cycle should ensure all of the following except a. all sales are profitable b. all sales are recorded c. credit is authorized d. inventory to be shipped is not stolen ANS: A PTS: 1 20. Which control does not help to ensure that accurate records are kept of customer accounts and inventory? a. reconcile accounts receivable control to accounts receivable subsidiary b. authorize credit c. segregate custody of inventory from record keeping d. segregate record keeping duties of general ledger from accounts receivable ANS: B PTS: 1 21. Internal controls for handling sales returns and allowances do not include a. computing bad debt expense using the percentage of credit sales b. verifying that the goods have been returned c. authorizing the credit memo by management d. using the original sales invoice to prepare the sales returns slip ANS: A PTS: 1 22. The printer ran out of preprinted sales invoice forms and several sales invoices were not printed. The best internal control to detect this error is a. a batch total of sales invoices to be prepared compared to the actual number of sales invoices prepared b. sequentially numbered sales invoices c. visual verification that all sales invoices were prepared d. none of the above will detect this error ANS: A PTS: 1 23. Which department prepares the bill of lading? a. sales b. warehouse c. shipping d. credit ANS: C PTS: 1 24. A remittance advice is a. used to increase (debit) an account receivable by the cash received b. is a turn-around document c. is retained by the customer to show proof of payment d. none of the above ANS: B PTS: 1 25. A weekly reconciliation of cash receipts would include comparing a. the cash prelist with bank deposit slips b. the cash prelist with remittance advices c. bank deposit slips with remittance advices d. journal vouchers from accounts receivable and general ledger ANS: A PTS: 1 26. At which point is supervision most critical in the cash receipts system? a. accounts receivable b. general ledger c. mail room d. cash receipts ANS: C PTS: 1 27. EDI trading partner agreements specify all of the following except a. selling price b. quantities to be sold c. payment terms d. person to authorize transactions ANS: D PTS: 1 28. A cash prelist is a. a document that records sales returns and allowances b. a document returned by customers with their payments c. the source of information used to prepare monthly statements d. none of the above ANS: D PTS: 1 29. An advantage of real-time processing of sales is a. the cash cycle is lengthened b. current inventory information is available c. hard copy documents provide a permanent record of the transaction d. data entry errors are corrected at the end of each batch ANS: B PTS: 1 30. Commercial accounting systems have fully integrated modules. The word “integrated” means that a. segregation of duties is not possible b. transfer of information among modules occurs automatically c. batch processing is not an option d. separate entries are made in the general ledger accounts and the subsidiary ledgers ANS: B PTS: 1 31. The data processing method that can shorten the cash cycle is a. batch, sequential file processing b. batch, direct access file processing c. real-time file processing d. none of the above ANS: C PTS: 1 32. Which of the following is not a risk exposure in a PC accounting system? a. reliance on paper documentation is increased b. functions that are segregated in a manual environment may be combined in a microcomputer accounting system c. backup procedures require human intervention d. data are easily accessible ANS: A PTS: 1 33. Which journal is not used in the revenue cycle? a. cash receipts journal b. sales journal c. purchases journal d. general journal ANS: C PTS: 1 34. Periodically, the general ledger department receives all of the following except a. total increases to accounts receivable b. total of all sales backorders c. total of all sales d. total decreases in inventory ANS: B PTS: 1 35. The credit department a. prepares credit memos when goods are returned b. approves credits to accounts receivable when payments are received c. authorizes the granting of credit to customers d. none of the above ANS: C PTS: 1 36. Adjustments to accounts receivable for payments received from customers is based upon a. the customer’s check b. the cash prelist c. the remittance advice that accompanies payment d. a memo prepared in the mailroom ANS: C PTS: 1 37. The revenue cycle utilizes all of the following files except a. credit memo file b. sales history file c. shipping report file d. cost data reference file ANS: D PTS: 1 38. All of the following are advantages of real-time processing of sales except a. The cash cycle is shortened b. Paper work is reduced c. Incorrect data entry is difficult to detect d. Up-to-date information can provide a competitive advantage in the marketplace ANS: C PTS: 1 39. Which document is NOT prepared by the sales department? a. packing slip b. shipping notice c. bill of lading d. stock release ANS: C PTS: 1 40. Which type of control is considered a compensating control? a. segregation of duties b. access control c. supervision d. accounting records ANS: C PTS: 1 41. Which of the following is NOT a common method for achieving multilevel security? a. Access control list b. Application integrity c. Role based access control d. All of the above ANS: B PTS: 1 42. In an integrated cash receipts system, which of the following is not a task of the mail room clerk? a. Prepare deposit slips b. Open envelopes c. Prepare remittance list d. Make bank deposit ANS: D PTS: 1 SHORT ANSWER 1. Distinguish between a packing slip, shipping notice, and a bill of lading. ANS: The packing slip travels with the goods to the customer, and it describes the contents on the order. Upon filling the order, the shipping department sends the shipping notice to the billing department to notify them that the order has been filled and shipped. The shipping notice contains additional information that the packing slip may not contain, such as shipment date, carrier and freight charges. The bill of lading is a formal contract between the seller and the transportation carrier; it shows legal ownership and responsibility for assets in transit. PTS: 1 2. State two specific functions or jobs that should be segregated in the sales processing system. ANS: sales order processing and credit approval; inventory control (record keeping) from warehouse (custody); and general ledger from accounts receivable subsidiary ledger PTS: 1 3. State two specific functions or jobs that should be segregated in the cash receipts system. ANS: cash receipts (custody) from accounts receivable (record keeping); and general ledger from accounts receivable subsidiary ledger; mail room (receiving cash) and accounts receivable subsidiary ledger PTS: 1 4. List two points in the sales processing system when authorization is required. ANS: credit check, sales returns policy, preparation of cash prelist PTS: 1 5. For the revenue cycle, state two specific independent verifications that should be performed. ANS: Shipping verifies that the goods sent from the warehouse are correct in type and quantity. Billing reconciles the shipping notice with the sales order to ensure that customers are billed only for the quantities shipped. General ledger reconciles journal vouchers submitted by the billing department (sales journal), inventory control (inventory subsidiary ledger), and cash receipts (cash receipts journal). Treasurer determines that all cash received got to the bank. PTS: 1 6. What task can the accounts receivable department engage in to verify that all checks sent by customers have been appropriately deposited and recorded? ANS: The company should periodically, perhaps monthly, send an account summary to each customer listing invoices and amounts paid by check number and date. This form allows the customer to verify the accuracy of the records. If any payments are not recorded, they will notify the company of the discrepancy. These reports should not be handled by the accounts receivable clerk or the cashier. PTS: 1 7. What specific internal control procedure would prevent the sale of goods on account to a fictitious customer? ANS: credit check PTS: 1 8. The clerk who opens the mail routinely steals remittances and checks. Describe a specific internal control procedure that would prevent or detect this fraud. ANS: supervision (two people) when opening the mail; customer complaints when monthly statements mailed PTS: 1 9. A customer payment of $247 was correctly posted in the general ledger but was recorded as $274 in the customer’s account receivable. Describe a specific internal control procedure that would detect this error. ANS: Reconcile the accounts receivable control account to the accounts receivable subsidiary ledger; compare control totals of cash received with total credits to A/R subsidiary ledger. PTS: 1 10. Goods are shipped to a customer, but the shipping department does not notify billing and the customer never receives an invoice. Describe a specific internal control procedure that would detect this error. ANS: Billing department matches the stock release copy of the sales order (from shipping) to the invoice, ledger, and file copies of the sales order (sent directly to billing), and then mails the invoice to the customer. After a certain amount of time has passed, the billing department should investigate any unmatched invoice, ledger, and file copies of the sales order. PTS: 1 11. A clerk embezzles customer payments on account and covers up the theft by making an adjustment to the accounts receivable ledger. Describe a specific internal control procedure that would prevent this fraud. ANS: segregation of duties; do not let one person have custody of payments and the ability to make adjustments to the records; all adjustments to accounts receivable records must be authorized PTS: 1 12. A credit sale is made to a customer, even though the customer’s account is four months overdue. Describe a specific internal control procedure that would prevent this from happening. ANS: Perform a credit check and require management approval for all sales to accounts that are overdue. PTS: 1 13. What specific internal control procedure would prevent a customer from being billed for all 50 items ordered although only 40 items were shipped? ANS: Billing should reconcile the shipping report with the sales order. PTS: 1 14. What specific internal control procedure would prevent the shipping clerk from taking goods from the storeroom and sending them to someone who had not placed an order? ANS: Shipping clerk should not have access to the storeroom. PTS: 1 15. What specific internal control procedure would prevent an accounts receivable clerk from issuing a fictitious credit memo to a customer (who is also a relative) for goods that were “supposedly” returned from previous sales? ANS: Credit memo should be authorized after verifying the return of goods based on evidence from the person who received the goods. PTS: 1 16. What specific internal control procedure would prevent an increase in sales returns since salesmen were placed on commission? ANS: Customer credit should be verified by the credit department; reduce commissions for sales returns. PTS: 1 17. What specific internal control procedure would detect the misplacement of a sales invoice after preparation and not mailed to the customer? The invoice was never found. ANS: All documents should be prenumbered. PTS: 1 18. What function does the receiving department serve in the revenue cycle? ANS: The receiving department counts and inspects items which are returned by customers. The receiving department prepares a return slip of which a copy goes to the warehouse for restocking, and a copy goes to the sales order department so that a credit memo can be issued to the customer. PTS: 1 19. What are the three rules that ensure that no single employee or department processes a transaction in its entirety. ANS: The three rules that ensure segregation of functions are: 1. Transaction authorization should be separate from transaction processing. 2. Asset custody should be separate from asset record keeping. 3. The organization structure should be such that the perpetration of a fraud requires collusion between 2 or more individuals. PTS: 1 20. What is automation and why is it used? ANS: Automation involves using technology to improve the efficiency and effectiveness of a task. Automation of the revenue cycle is typically used to reduce overhead costs, make better credit granting decisions, and better collect outstanding accounts receivable. PTS: 1 21. What is the objective of re-engineering? ANS: The objective of re-engineering is to greatly reduce costs by identifying and eliminating non value- added tasks and also by streamlining necessary existing processes. PTS: 1 22. What are the key segregation of duties related to computer programs that process accounting transactions? ANS: The tasks of design, maintenance, and operation of computer programs need to be segregated. The programmers who write the original computer programs should not also be responsible for making program changes. Both of these functions must also be separate from the daily task of operating the system. PTS: 1 23. How is EDI more than technology? What unique control problems may it pose? ANS: EDI represents a unique business arrangement between the buyer and seller in which they agree, in advance, to the terms of their relationship on such items as selling price, quantities, delivery times, payment terms and methods of handling disputes. The terms of agreement are binding. One problem is ensuring that only valid transactions are processed. Another risk is that a non-trading partner will masquerade as a trading partner and access the firm's processing systems. PTS: 1 24. What makes point-of-sale systems different from revenue cycles of manufacturing firms? ANS: In point-of-sale systems, the customer literally has possession of the items purchased, thus the inventory is in hand. Typically, for manufacturing firms, the order is placed and the good is shipped to the customer at some later time period. Thus, updating inventory at the time of sale is necessary in point-of-sale systems since the inventory is changing hands, while it is not necessary in manufacturing firms until the goods are actually shipped to the customer. Also, POS systems are used extensively in grocery stores, department stores, and other types of retail organizations. Generally, only cash, checks, and bank credit card sales are valid. Unlike manufacturing firms, the organization maintains no customer accounts receivable. Unlike some manufacturing firms, inventory is kept on the store’s shelves, not in a separate warehouse. The customers personally pick the items they wish to buy and carry them to the checkout location, where the transaction begins. Shipping, packing, bills of lading, etc. are not relevant to POS systems. PTS: 1 25. Give three examples of Access Control in a Point-of-Sale (POS) system. ANS: Lock on the cash drawer Internal cash register tape that can be accessed only by the manager Physical security over the inventory, for example: steel cables to secure expensive leather coats to the clothing rack; locked showcases to display jewelry and costly electronic equipment; magnetic tags attached to merchandise that will sound an alarm when removed from the store. Note to Instructor: Some physical security devices could also be classified as supervision. PTS: 1 26. Describe the key tasks in the sales order process. ANS: Sales order procedures include the tasks involved in receiving and processing a customer order, filling the order and shipping products to the customer, billing the customer at the proper time, and correctly accounting for the transaction. PTS: 1 27. What is the purpose(s) of the stock release document? ANS: The stock release document (also called the picking ticket) is sent to the warehouse to identify the items of inventory that have been sold and must be located and picked from the warehouse shelves. It also provides formal authorization for warehouse personnel to release the specified items. PTS: 1 28. What is the role of the shipping notice? ANS: The shipping notice triggers the billing process. When the goods are shipped the shipping notice is forwarded to the billing function as evidence that the customer’s order was filled and shipped. This document conveys pertinent new facts such as the date of shipment, the items and quantities actually shipped, the name of the carrier, and freight charges. PTS: 1 29. What is a bill of lading? ANS: The bill of lading is a formal contract between the seller and the shipping company (carrier) to transport the goods to the customer. This document establishes legal ownership and responsibility for assets in transit. PTS: 1 30. What is the purpose of the credit memo? ANS: This document is the authorization for the customer to receive credit for the merchandise returned. A credit memo may be similar in appearance to a sales order. Some systems may actually use a copy of the sales order marked credit memo. PTS: 1 31. How is application integrity achieved? ANS: Application integrity is achieved through the systems development and program change processes. PTS: 1 32. What is multilevel security? ANS: Multilevel security employs programmed techniques that permit simultaneous access to a central system by many users with different access privileges but prevents them from obtaining information for which they lack authorization. PTS: 1 33. What does EDI technology do? ANS: EDI technology was devised to expedite routine transactions between manufacturers and wholesalers, and between wholesalers and retailers. PTS: 1 ESSAY 1. When Clipper Mail Order Co. receives telephone and fax orders, the billing department prepares an invoice. The invoice is mailed immediately. A copy of the invoice serves as a shipping notice. The shipping department removes inventory from the warehouse and prepares the shipment. When the order is complete, the goods are shipped. The clerk checks the customer’s credit before recording the sale in the general journal and the account receivable subsidiary ledger. The receptionist opens the mail and lists all payments. The receptionist also handles all customer complaints and prepares sales return forms for defective merchandise. The cashier records all cash receipts in the general journal and makes the appropriate entry in the accounts receivable subsidiary ledger. The cashier prepares the daily bank deposit. Describe at least four internal control weaknesses at Clipper Mail Order Co. ANS: no sales order is prepared; credit should be checked before shipping the items; invoices are mailed before the goods are shipped; shipping has access to the warehouse; record keeping duties are not segregated (general ledger from subsidiary ledger); only one person opens the mail; sales return forms are not authorized by management; custody and record keeping duties are not separated; the cashier has custody of cash, makes journal entries, and maintains A/R ledger; Cashier has custody of cash and handles customer complaints (e.g., about unrecorded payments). PTS: 1 2. How may an employee embezzle funds by issuing an unauthorized sales credit memo if the appropriate segregation of functions and authorization controls were not in place? ANS: An employee who has access to incoming payments, either cash or check, as well as the authorization to issue credit memos may pocket the cash or check of a payment for goods received. This employee could then issue a credit memo to this person’s account so that the customer does not show a balance due. PTS: 1 3. For each of the following documents, describe its purpose, the functional area preparing it, and the key data included: sales order, bill of lading, credit memo. ANS: A sales order is used to collect information needed to initiate the sales process. It can be a copy of the customer’s purchase order prepared by the customer or a document prepared by a member of the sales staff in response to mail, phone or personal contact with the customer. It contains information about the customer, the type and quantity of merchandise being requested, price information, shipping information, etc. The bill of lading is prepared by the shipping clerk. It is a formal contract between the seller and the carrier who will transport the goods to the customer. It contains information about the carrier, the customer, descriptions of the package(s) being shipped, declared value of the goods, and information on freight charges, including how much and who will pay. A credit memo is a document authorizing issuance of credit to a customer for returned goods. It is prepared in the sales department after receipt of a return slip from receiving. It shows the customer’s name, reason for the return, a list of items and prices, and the total amount of credit. Many credit memos require additional authorization. PTS: 1 4. What features of a reengineered cash receipts system contribute to improved control and reduced costs? What complicates the process? ANS: A reengineered cash receipts system can include automated mail processing that opens envelopes and separates checks and remittance advices in a manner that limits access of the mail room clerk to the checks. Software can be used to read the amount of payment and compare to the amount due, verify that the check has been signed, etc. “Good” transactions continue through processing, exceptions are handled separately. Checks are sent to the cash receipts department for deposit, listings of transactions are sent to accounts receivable, cash receipts, and general ledger departments. This process is complicated when the organization receives many partial payments, single payments covering multiple invoices, or encounters many clerical errors on the part of customers. PTS: 1 5. What role does each of the following departments play in the sales order processing subsystem: sales, credit, and shipping? Be complete. ANS: The sales department receives the order information from the customer, either by mail, phone, or in person. Information is captured on a sales order form which includes customer name, account number, name, number and description of items ordered, quantities and unit prices plus taxes, shipping info, discounts, freight terms. This form is usually prepared in multiple copies that are used for credit approval, packing, stock release, shipping, and billing. The credit department provides transaction authorization by approving the customer for a credit sale and returns and allowances. The shipping department receives information from the sales department in the form of packing slip and shipping notice. When the goods arrive from the warehouse, the documents are reconciled with the stock release papers. The goods are packed and labeled. The packing slip is included. The shipping notice is sent to billing. A bill of lading is prepared to accompany the shipment. PTS: 1 6. With regard to segregation of duties, rule one is that transaction authorization and transaction processing should be separated. What does this require in the revenue cycle? ANS: Within the revenue cycle, the credit department is separate from the rest of the process. Hence, the authorization of the transaction (granting of credit) is independent. If other people, e.g., sales staff, were able to authorize credit sales, there would be the temptation to approve sales to any customer, even those known to not be credit worthy. PTS: 1 7. With regard to segregation of duties, rule two is that asset custody and record keeping should be separated. What does this require in the revenue cycle? ANS: In the revenue cycle, the warehouse has custody of physical assets while accounting (especially general ledger and inventory control) maintains the records. Also, in the cash receipts subsystem, cash receipts has custody of the asset (cash) while general ledger and accounts receivable keep the records. PTS: 1 8. What role does each of the following departments play in the cash receipts subsystem: mail room, cash receipts, accounts receivable, and general ledger? Be complete. ANS: The mail room receives the customer’s payment–usually a check accompanied by a document called a remittance advice (which may be a copy of the invoice sent to the customer). Mail clerks separate the two, prepare a cash prelist or remittance list which lists all the payments received and sends the checks to the cashier and remittance advices to accounts receivable. In cash receipts someone (e.g., cashier) restrictively endorses the checks and records the payments in the cash receipts journal. A deposit slip is prepared which accompanies the checks to the bank. The accounts receivable department posts from the remittance advices to the customer accounts in the AR subsidiary ledger. The general ledger department records cash receipts to the cash and AR control accounts based on the list from the mailroom and the summary report of posting from A/R. PTS: 1 PTS: 1 9. A customer payment of $247 was correctly posted in the general ledger but was recorded as $274 in the customer’s account receivable. Describe a specific internal control procedure that would detect this error. ANS: Reconcile the accounts receivable control account to the accounts receivable subsidiary ledger; compare control totals of cash received with total credits to A/R subsidiary ledger. PTS: 1 10. Goods are shipped to a customer, but the shipping department does not notify billing and the customer never receives an invoice. Describe a specific internal control procedure that would detect this error. ANS: Billing department matches the stock release copy of the sales order (from shipping) to the invoice, ledger, and file copies of the sales order (sent directly to billing), and then mails the invoice to the customer. After a certain amount of time has passed, the billing department should investigate any unmatched invoice, ledger, and file copies of the sales order. PTS: 1 11. A clerk embezzles customer payments on account and covers up the theft by making an adjustment to the accounts receivable ledger. Describe a specific internal control procedure that would prevent this fraud. ANS: segregation of duties; do not let one person have custody of payments and the ability to make adjustments to the records; all adjustments to accounts receivable records must be authorized PTS: 1 12. A credit sale is made to a customer, even though the customer’s account is four months overdue. Describe a specific internal control procedure that would prevent this from happening. ANS: Perform a credit check and require management approval for all sales to accounts that are overdue. PTS: 1 13. What specific internal control procedure would prevent a customer from being billed for all 50 items ordered although only 40 items were shipped? ANS: Billing should reconcile the shipping report with the sales order. PTS: 1 Chapter 5—The Expenditure Cycle Part I: Purchases and Cash Disbursements Procedures TRUE/FALSE 1. Purchasing decisions are authorized by inventory control. ANS: T 2. The blind copy of the purchase order that goes to the receiving department contains no item descriptions. ANS: F 3. Firms that wish to improve control over cash disbursements use a voucher system. ANS: T 4. In a voucher system, the sum of all unpaid vouchers in the voucher register equals the firm’s total voucher payable balance. ANS: T 5. The accounts payable department reconciles the accounts payable subsidiary ledger to the control account. ANS: F 6. The use of inventory reorder points suggests the need to obtain specific authorization. ANS: F 7. Proper segregation of duties requires that the responsibility approving a payment be separated from posting to the cash disbursements journal. ANS: T 8. A major risk exposure in the expenditure cycle is that accounts payable may be overstated at the end of the accounting year. ANS: F 9. When a trading partner agreement is in place, the traditional three way match may be eliminated. ANS: T 10. Authorization of purchases in a merchandising firm occurs in the inventory control department. ANS: T 11. A three way match involves a purchase order, a purchase requisition, and an invoice. 12. 13. 14. 15. 16. 17. 18. 19. 20. ANS: F Authorization for a cash disbursement occurs in the cash disbursement department upon receipt of the supplier’s invoice. ANS: F An automated cash disbursements system can yield better cash management since payments are made on time. ANS: T Permitting warehouse staff to maintain the only inventory records violates separation of duties. ANS: T A purchasing system that employs electronic data interchange does not use a purchase order. ANS: F Inventory control should be located in the warehouse. ANS: F Inspection of shipments in the receiving department would be improved if the documentation showed the value of the inventory. ANS: F One reason for authorizing purchases is to enable efficient inventory management. ANS: T If accounts payable receives an invoice directly from the supplier it needs to be reconciled with the purchase order and receiving report. ANS: T Supervision in receiving is intended to reduce the theft of assets. ANS: T MULTIPLE CHOICE 1. The purpose of the purchase requisition is to a. order goods from vendors b. record receipt of goods from vendors c. authorize the purchasing department to order goods d. bill for goods delivered ANS: C 2. The purpose of the receiving report is to d. bill for goods delivered ANS: B 3. All of the following departments have a copy of the purchase order except a. the purchasing department b. the receiving department c. accounts payable d. general ledger ANS: D 4. The purpose of the purchase order is to a. order goods from vendors b. record receipt of goods from vendors c. authorize the purchasing department to order goods d. approve payment for goods received ANS: A 5. The open purchase order file in the purchasing department is used to determine a. the quality of items a vendor ships b. the best vendor for a specific item c. the orders that have not been received d. the quantity of items received ANS: C 6. The purchase order a. is the source document to make an entry into the accounting records b. indicates item description, quantity, and price c. is prepared by the inventory control department d. is approved by the end-user department ANS: B 7. The reason that a blind copy of the purchase order is sent to receiving is to a. inform receiving when a shipment is due b. force a count of the items delivered c. inform receiving of the type, quantity, and price of items to be delivered d. require that the goods delivered are inspected ANS: B 8. The receiving report is used to a. accompany physical inventories to the storeroom or warehouse b. advise the purchasing department of the dollar value of the goods delivered c. advise general ledger of the accounting entry to be made d. advise the vendor that the goods arrived safely ANS: A 9. When a copy of the receiving report arrives in the purchasing department, it is used to d. recognize the purchase order as closed ANS: D 10. The financial value of a purchase is determined by reviewing the a. packing slip b. purchase requisition c. receiving report d. supplier’s invoice ANS: D 11. Which document is least important in determining the financial value of a purchase? a. purchase requisition b. purchase order c. receiving report d. supplier’s invoice ANS: A 12. In a merchandising firm, authorization for the payment of inventory is the responsibility of a. inventory control b. purchasing c. accounts payable d. cash disbursements ANS: C 13. In a merchandising firm, authorization for the purchase of inventory is the responsibility of a. inventory control b. purchasing c. accounts payable d. cash disbursements ANS: A 14. When purchasing inventory, which document usually triggers the recording of a liability? a. purchase requisition b. purchase order c. receiving report d. supplier’s invoice ANS: D 15. Because of time delays between receiving inventory and making the journal entry a. liabilities are usually understated b. liabilities are usually overstated c. liabilities are usually correctly stated d. none of the above ANS: A 16. Usually the open voucher payable file is organized by d. transaction date ANS: B 17. Which of the following statements is not correct? a. the voucher system is used to improve control over cash disbursements b. the sum of the paid vouchers represents the voucher payable liability of the firm c. the voucher system permits the firm to consolidate payments of several invoices on one voucher d. many firms replace accounts payable with a voucher payable system ANS: B 18. In the expenditure cycle, general ledger does not a. post the journal voucher from the accounts payable department b. post the account summary from inventory control c. post the journal voucher from the purchasing department d. reconcile the inventory control account with the inventory subsidiary summary ANS: C 19. The documents in a voucher packet include all of the following except a. a check b. a purchase order c. a receiving report d. a supplier’s invoice ANS: A 20. To maintain a good credit rating and to optimize cash management, cash disbursements should arrive at the vendor’s place of business a. as soon as possible b. on the due date c. on the discount date d. by the end of the month ANS: C 21. The cash disbursement clerk performs all of the following tasks except a. reviews the supporting documents for completeness and accuracy b. prepares checks c. signs checks d. marks the supporting documents paid ANS: C 22. When a cash disbursement in payment of an accounts payable is recorded a. the liability account is increased b. the income statement is changed c. the cash account is unchanged d. the liability account is decreased ANS: D Chapter 6—The Expenditure Cycle Part II: Payroll Processing and Fixed Asset Procedures TRUE/FALSE 1. Time cards are used by cost accounting to allocate direct labor charges to work in process. ANS: F 2. The personnel department authorizes changes in employee pay rates. ANS: T 3. Most payroll systems for mid-size firms use real-time data processing. ANS: F 4. To improve internal control, paychecks should be distributed by the employee's supervisor. ANS: F 5. Employee paychecks should be drawn against a special checking account. ANS: T 6. Because a time clock is used, no supervision is required when employees enter and leave the work place. ANS: F 7. Inventory control performs the formal record keeping function for fixed assets. ANS: F 8. The depreciation schedule shows when assets are fully depreciated. ANS: T 9. Authorization to dispose of fixed assets should be issued by the user of the asset. ANS: F 10. Work-in-process records are updated by payroll personnel. ANS: F 11. Ideally, payroll checks are written on a special bank account used only for payroll. ANS: T 12. The supervisor is the best person to determine the existence of a “phantom employee” and should distribute paychecks. ANS: F 13. Payroll processing can be automated easily because accounting for payroll is very simple. ANS: F 14. Timekeeping is part of the personnel function. ANS: F 15. Fixed asset accounting systems include cost allocation and matching procedures that are not part of routine expenditure systems. ANS: T 16. Asset maintenance involves only the recording of depreciation charges. Physical improvements are always expensed. ANS: F 17. Fixed Asset Systems must keep track of the physical location of each asset to promote accountability. ANS: T 18. Time cards capture the total time an individual worker spends on each production job. ANS: F 19. Accounting conventions and IRS rules sometime specify the depreciation parameters to be used. ANS: T 20. The fixed asset disposal report authorizes the user department to dispose of a fixed asset. ANS: F MULTIPLE CHOICE 1. The document that captures the total amount of time that individual workers spend on each production job is called a a time card . b job ticket . c personnel action form . d labor distribution form . ANS: B 2. An important reconciliation in the payroll system is a general ledger compares the labor distribution summary from cost accounting to the . disbursement voucher from accounts payable b personnel compares the number of employees authorized to receive a paycheck to the . number of paychecks prepared c production compares the number of hours reported on job tickets to the number of hours . reported on time cards d payroll compares the labor distribution summary to the hours reported on time cards . ANS: A 3. Which internal control is not an important part of the payroll system? a Supervisors verify the accuracy of employee time cards. . b Paychecks are distributed by an independent paymaster. . c Accounts payable verifies the accuracy of the payroll register before transferring payroll . funds to the general checking accounting. d General ledger reconciles the labor distribution summary and the payroll disbursement . voucher. ANS: C 4. Which transaction is not processed in the Fixed Asset System? a purchase of building . b improvement of equipment . c purchase of raw materials . d sale of company van . ANS: C 5. Depreciation a is calculated by the department that uses the fixed asset . b allocates the cost of the asset over its useful life . c is recorded weekly . d results in book value approximating fair market value . ANS: B 6. Depreciation records include all of the following information about fixed assets except a the economic benefit of purchasing the asset . b the cost of the asset . c the depreciation method being used . d the location of the asset . ANS: A 7. Which control is not a part of the Fixed Asset System? a formal analysis of the purchase request . b review of the assumptions used in the capital budgeting model . c development of an economic order quantity model . d estimates of anticipated cost savings . ANS: C 8. Objectives of the Fixed Asset System do not include a authorizing the acquisition of fixed assets . b recording depreciation expense . c computing gain and/or loss on disposal of fixed assets . d maintaining a record of the fair market value of all fixed assets . ANS: D 9. Which of the following is not a characteristic of the Fixed Asset System? a Acquisitions are routine transactions requiring general authorization. . b Retirements are reported on an authorized disposal report form. . c Acquisition cost is allocated over the expected life of the asset. . d Transfer of fixed assets among departments is recorded in the fixed asset subsidiary . ledger. ANS: A 10. In the payroll subsystem, which function should distribute paychecks? a personnel . b timekeeping . c paymaster . d payroll . ANS: C 11. Where does the responsibility lie for reconciling the labor distribution summary and the payroll disbursement voucher? a cash disbursements . b cost accounting . c personnel . d general ledger . ANS: D 12. Which of the following statements is not true? a Routine payroll processing begins with the submission of time cards. . b Payroll clerks must verify the hours reported on the time cards. . c Payroll reconciles personnel action forms with time cards and prepares paychecks. . d Cash disbursements signs paychecks and forwards them to the paymaster for distribution. . ANS: B 13. In a manufacturing firm, employees use time cards and job tickets. Which of the following statements is not correct? a Job tickets are prepared by employees for each job worked on, so an employee may have . more that one job ticket on a given day. b An individual employee will have only one time card. . c The time reported on job tickets should reconcile with the time reported on time cards. . d Paychecks should be prepared from the job tickets. . ANS: D 14. Which department is responsible for approving changes in pay rates for employees? a payroll . b treasurer . c personnel . d cash disbursements . ANS: C 15. Which of the following situations represents a serious control weakness? a Timekeeping is independent of the payroll department. . b Paychecks are distributed by the employees immediate supervisor. . c Time cards are reconciled with job tickets. . d Personnel is responsible for updating employee records, including creation of records for . new hires. ANS: B 16. Why would an organization require the paymaster to deliver all unclaimed paychecks to the internal audit department? a to detect a “phantom employee” for whom a check was produced . b to prevent an absent employee’s check from being lost . c to avoid paying absent employees for payday . d to prevent the paymaster from cashing unclaimed checks . ANS: A 17. Which of the following is not a reasonable control for fixed assets? a Proper authorization is required for acquisition and disposal of fixed assets. . b Fixed asset records show the location of each asset. . c Fully depreciated assets are immediately disposed of. . d Depreciation policies are in writing. . ANS: C 18. Cost accounting updates work-in-process accounts from a time cards . b the labor distribution summary . c job tickets . d personnel action forms . ANS: C 19. Payroll uses time card data to do all of the following except a prepare the payroll register . b update employee payroll records . c prepare the labor distribution summary . d prepare paychecks . ANS: C 20. Payroll checks are typically drawn on a the regular checking account . b a payroll imprest account . c a wages payable account . d petty cash . ANS: B 21. The personnel action form provides authorization control by a preventing paychecks for terminated employees . b verifying pay rates for employees . c informing payroll of new hires . d all of the above . ANS: D 22. Accounting records that provide the audit trail for payroll include all of the following except a time cards . b job tickets . c payroll register . d accounts payable register . ANS: D 23. Personnel actions forms are used to do all of the following except a activate new employees . b terminate employees . c record hours worked . d change pay rates . ANS: C 24. The payroll department performs all of the following except a prepares the payroll register . b distributes paychecks . c updates employee payroll records . d prepares paychecks . ANS: B 25. The document that records the total amount of time spent on a production job is the a time card . b job ticket . c labor distribution summary . d personnel action form . ANS: C 26. A control technique that can reduce the risk of a terminated employee being paid is a a security camera viewing the time clock . b the supervisor taking role during the shift . c paychecks being distributed by an independent paymaster . d reconciliation of time cards and job tickets . ANS: C 27. Accounts payable a signs paychecks . b prepares the payroll voucher . c reconciles time cards and employee records . d distributes paychecks to employees . ANS: B 28. All of the following are processed by the Fixed Asset System except a sale of unneeded equipment . b purchase of raw materials . c repair of production equipment . d purchase of a new plant . ANS: B 29. The Fixed Asset System performs all of the following except a determines the need for new assets . b maintains depreciation records . c records retirement and disposal of assets . d tracks the physical location of fixed assets . ANS: A 30. The payroll department performs all of the following except a prepares paychecks . b transfers adequate funds to the payroll imprest account . c updates employee payroll records . d prepares the payroll register . ANS: B 31. Depreciation a assures that assets are reported at fair market value . b is discretionary for many firms . c allocates the cost of an asset over its useful life . d is the responsibility of the department using the asset . ANS: C 32. The Fixed Asset System is similar to the expenditure cycle except a fixed asset transactions are non-routine and require special authorization and controls . b fixed assets are capitalized, not expensed . c both a and b . d none of the above . ANS: C 33. Asset maintenance involves a the recording of periodic depreciation . b adjusting the asset records to reflect the cost of physical improvements . c keeping track of the physical location of the assets . d all of the above . ANS: D 34. The Fixed Asset Systems does all of the following except a records acquisition of assets . b records improvements to assets . c estimates the fair market value of assets in service . d records the disposal of assets . ANS: C 35. Asset disposal a occurs as soon as an asset is fully depreciated . b requires no special authorization . c automatically initiates the purchase of a replacement asset . d must follow formal authorization procedures . ANS: D SHORT ANSWER 1. Describe an internal control procedure that would prevent an employee from punching the time clock for another, absent employee. ANS: supervision of the time clock at the start of the shift 2. Why should the employee’s supervisor not distribute paychecks? ANS: A form of payroll fraud involves a supervisor submitting fraudulent time cards for nonexistent employees. The resulting paychecks, when returned to the supervisor are then cashed by the supervisor. 3. Describe an internal control procedure that would prevent a supervisor from stealing the unclaimed paychecks of employees who have been terminated. ANS: This type of fraud can be reduced or eliminated by using a paymaster to distribute paychecks to employees in person. Any uncollected paychecks are then returned to payroll. Also, mail final paychecks to terminated employees. 4. Why should employee paychecks be drawn against a special checking account? ANS: A separate imprest account is established for the exact amount of the payroll based on the payroll summary. When the paychecks are cashed, this account should clear leaving a zero balance. Any errors in checks (additional checks or abnormal amounts) would result in a non-zero balance in the imprest account and/or some paycheck would not clear. This will alert management to the problem so corrective action can be taken. 5. Why should employees clocking on and off the job be supervised. ANS: A form of payroll fraud involves employees clocking the time cards of absent employees. By supervising the clocking in and out process, this fraud can be reduced or eliminated. 6. What is a personnel action form? ANS: The personnel action form provides the payroll department with a list of currently active employees, so that any submission of time cards by supervisors for fictitious or ex-employees will not be processed. 7. In a manufacturing firm, employees typically fill out two different documents regarding their time worked. What are they? Why are there two? ANS: The two documents are the time card and the job ticket. Two are required because the time card records all the time worked by an employee during the period while the job ticket details the time by project. 8. List two types of authorization required in the Fixed Asset System. ANS: authorization to purchase the asset and to dispose of the asset 9. List four types of data that appear on a depreciation schedule. ANS: item description, depreciation method, useful life, date acquired, cost, salvage value, accumulated depreciation, depreciation expense per period, book value 10. Which documents prompt the fixed asset department to create a fixed asset record? ANS: the receiving report and the disbursement voucher 11. Describe an internal control that would prevent an employee from stealing a computer and then reporting it as scrapped. ANS: Supervisors must authorize the disposal of the computer. Unless so authorized, the record will continue to show that the employee is responsible for the computer. 12. Describe an internal control that would prevent the payment of insurance premiums on an automobile that is no longer owned by the company. ANS: Perform an annual physical inventory of fixed assets and adjust the records to reflect assets no longer on hand. Prepare reports about the disposal of assets. 13. Describe an internal control that would prevent the charging of depreciation expense to the maintenance department for a sweeper that is now located in and used by the engineering department. ANS: Prepare reports about the transfer of fixed assets. Perform an annual physical inventory and note the location of assets. Budget and then hold each department accountable for depreciation expense for assets located in each department. 14. Describe an internal control that would prevent the acquisition of office equipment which is not needed by the firm. ANS: A higher organizational level or other appropriate person authorizes fixed asset acquisitions; part of the authorization is showing that a need for the asset exists. 15. What negative consequences result when fixed asset records include assets that are no longer owned by the firm? ANS: On the financial statements, assets will be overstated and depreciation expense could be overstated. Assets on property tax returns will be overstated and too much tax will be paid. Insurance premiums will be paid on nonexistent assets. 16. Explain the purpose of each of the following documents used in the payroll system: the personnel action form, the job ticket, the time card. ANS: The personnel action form is a document which identifies employees who should receive a paycheck; reflects changes in pay rates, payroll deductions, and job classifications. The job ticket collects information on the time individual workers spend on each production job. The time card captures the total time that an employee is at work. 17. How do fixed asset systems differ from the expenditure cycle? ANS: The fixed asset system processes nonroutine transactions for a wider group of users in the organization than the expenditure cycle. Further, the expenditure cycle processes routine acquisitions of raw materials inventories for the production function and finished goods inventories for the sales function. The expenditure cycle transactions are oftentimes automatically approved by the system, while fixed asset transaction approvals typically demand individual attention due to the uniqueness of the transactions. 18. What is recorded by the asset maintenance part of the Fixed Asset System? ANS: periodic depreciation following an approved depreciation schedule and physical improvements to the asset to increase the subsidiary account and to adjust the depreciation schedule 19. How are the following carried out in the Fixed Asset System: authorization, supervision, independent verification? ANS: Independent authorization is required to acquire an asset and to formalize the depreciation schedule. Supervision must be exercised over the physical assets. Independent verification must confirm the location, existence, and condition of the assets. 20. Which department authorizes changes to employee pay rates? ANS: The personnel department via the personnel action form ESSAY 1. The Golf Club Company makes custom golf clubs. The manufacturing supervisor interviews people who have specialized manufacturing skills, and he informs payroll when an employee is hired. The employees use a time clock to record the hours they work. The employees are also required to keep a record of the time they spend working on each order. The supervisor approves all time cards. The accountant analyzes the job tickets and prepares a labor distribution summary. Payroll prepares the payroll register and paychecks. The supervisor distributes the paychecks to the employees. Payroll informs cash disbursement of the funds required to cover the entire payroll amount. The cash disbursements clerk ensures that there are adequate funds in the company's regular checking account to cover the payroll. Describe at least three internal control weaknesses; for each weakness suggest an improvement to internal control. ANS: WEAKNESS: The supervisor could be creating fictitious employees. The supervisor has too many incompatible duties; he hires workers, approves the time cards, and distributes the paychecks. IMPROVEMENT: Segregate duties. Personnel should hire employees and a paymaster should distribute paychecks. WEAKNESS: Employees could be paid for time they do not work; a co-worker could record an absent worker as present (punch the time clock). IMPROVEMENT: Supervise the time clock. Reconcile time cards and job time tickets. WEAKNESS: Payroll has authorization and transaction processing responsibilities. Payroll is authorizing the disbursement to fund the entire payroll. Accounts payable is not part of the system. IMPROVEMENT: Segregate duties; accounts payable should verify the accuracy of the payroll register and create a disbursement voucher. WEAKNESS: Payroll is funded through the general checking account. IMPROVEMENT: Paychecks should be written on a separate payroll account. 2. Describe how the Fixed Asset System differs from the expenditure cycle. ANS: The Fixed Asset System processes nonroutine transactions which are recorded as capital assets. The receiving department delivers fixed assets to the user/manager. The fixed asset department performs the record keeping function. The expenditure cycle processes routine transactions which are often debited to inventory or expensed. The receiving department delivers routine purchases to a central store or warehouse. Inventory Control performs the record keeping function for inventory purchases. 3. Three major tasks are handled by the Fixed Asset System. What is the purpose of each? What special control issues affect each? ANS: Asset acquisition handles the steps leading to the acquisition of new fixed assets: recognition of need, authorization and approval, possible capital investment analysis, and selection of supplier. Because of the value of fixed assets, special approvals are needed. Asset maintenance involves adjusting the subsidiary account balances for depreciation, and improvements and tracking location. Control involves accountability by keeping track of the physical location of each asset. Asset disposal handles the removal of assets from the subsidiary ledger when the asset is taken out of service. This requires special approval and preparation of a disposal report. 4. The Baccus Corp. manufactures medical equipment. This is a capital intensive industry and investments in fixed assets exceed $5 million a year. The minimum cost for production equipment is $75,000. When supervisors want new production machinery, they contact the plant manager. The plant manager approves or denies the request based on discussions with the production supervisor, the repair and maintenance supervisor, and the quality control supervisor. A purchase order is prepared by the purchasing department and sent to one of the three major suppliers of production machinery for medical equipment. The equipment is delivered immediately to the production floor and put into service. At the end of the month, the production supervisor informs the general ledger clerk about the receipt of the machinery. The general ledger clerk establishes an asset record for the machine. At the end of the year, the general ledger clerk computes straight-line depreciation based on a 10-year life with a 10 percent salvage value. Depreciation expense is recorded as a direct reduction of the asset cost. The repair department performs routine maintenance on all of the production equipment. Occasionally the repair department rebuilds a machine to extend its useful life. All of the costs associated with the repair department are charged to manufacturing overhead. When a machine becomes obsolete, production employees move it to a corner of the factory floor and break it down so that parts can be used in other machines. Production employees routinely remove parts for personal use. Some smaller machines have disappeared completely from the factory floor. The general ledger clerk takes a physical inventory every three years. About 75 percent of the fixed assets can be located and identified. Other assets have serial numbers that are inaccessible, so the item cannot be matched to a fixed asset record. Some fixed asset records cannot be traced to an actual item. Several machines that have been scrapped and are being used for spare parts were matched to fixed asset records. At the last inventory, the general ledger clerk did not make any adjustments to the fixed asset records explaining that 75 percent accuracy in the fixed asset physical inventory was excellent. Describe five internal control weaknesses and explain how to correct them. ANS: WEAKNESS: There is no written documentation of the approval for purchase. IMPROVEMENT: A formal capital investment analysis should be performed for purchases of fixed assets; the analysis should evaluate cost and benefits of the request. WEAKNESS: There is no process for obtaining competitive bids. IMPROVEMENT: Price bids should be obtained from the three suppliers before a purchase order is issued. WEAKNESS: Fixed assets are delivered directly to the factory floor. IMPROVEMENT: All purchases should go through the receiving department; the equipment should be inspected and a receiving report should be prepared. WEAKNESS: The production supervisor notifies the general ledger clerk about the receipt of fixed assets. IMPROVEMENT: The receiving department should send a copy of the receiving report to the fixed asset department so that fixed asset records can be updated and accountability for the asset established. WEAKNESS: The general ledger clerk is maintaining fixed asset records. IMPROVEMENT: The fixed asset department should maintain fixed asset records. WEAKNESS: Depreciation is computed using a standard method, asset life, and salvage value. IMPROVEMENT: Management should ensure that the depreciation method is appropriate. The asset life and salvage value should be determined individually for each fixed asset acquisition. WEAKNESS: Depreciation is recorded as a direct reduction of the asset cost. IMPROVEMENT: Depreciation should be recorded in an Accumulated Depreciation account for each asset. WEAKNESS: Costs to rebuild a machine is charged to manufacturing overhead. IMPROVEMENT: Costs to rebuild machines should be recorded as an increase to the cost of the asset. WEAKNESS: There is no authorization to scrap an obsolete machine. IMPROVEMENT: Obtain written authorization from management before a machine is scrapped. WEAKNESS: Employees remove equipment and equipment parts from the premises without authorization. IMPROVEMENT: Employees should receive written authorization before removing parts or equipment from the factory. WEAKNESS: The general ledger clerk is conducting the physical inventory and maintaining the record keeping. IMPROVEMENT: The general ledger clerk should not be taking the physical inventory count. Also, the physical count should occur more frequently. WEAKNESS: Fixed assets cannot be matched with records. IMPROVEMENT: Apply easily accessible labels to identify fixed assets. WEAKNESS: Fixed assets cannot be located and are not removed from the books. IMPROVEMENT: Fixed assets that cannot be located must be removed from the fixed asset records. WEAKNESS: Fixed assets that are scrapped remain on the books. IMPROVEMENT: Assets that are scrapped should be removed from the fixed asset records. WEAKNESS: The clerk regards 75% accuracy as excellent. IMPROVEMENT: Acceptance of 75% accuracy is poor. Any variation should be investigated and records updated. 5. Why does the payroll process lend itself to batch processing? ANS: Payroll lends itself to batch computerization because it is processed at fixed time intervals which permits some time lag. Processing the payroll file usually involves most employees each time it is processed, which is an efficient use of computer resources and can be accomplished with a single pass through the file. 6. Discuss the fundamental risk and control issues associated with fixed assets that are different from raw materials and finished goods. ANS: AUTHORIZATION CONTROLS. Because fixed assets are requested and employed by end-users asset acquisitions should be formal and explicitly authorized. Each material transaction should be initiated by a written request from the user or department. In the case of high-value items, there should be an independent approval process that evaluates the merits of the request on a cost-benefit basis. SUPERVISION CONTROLS. Because capital assets are widely distributed around the organization, they are more susceptible to theft and misappropriation than inventories that are secured in a warehouse. Therefore, management supervision is an important element in the physical security of fixed assets. Supervisors must ensure that fixed assets are being used in accordance with the organization’s policies and business practices. INDEPENDENT VERIFICATION CONTROLS. 1. Periodically, the internal auditor should review the asset acquisition and approval procedures to determine the reasonableness of key factors including: the useful life of the asset, the original financial cost, proposed cost savings as a result of acquiring the asset, the discount rate used, and the capital budgeting method used in justifying decisions to buy or dispose of assets. 2. The internal auditor should verify the location, condition, and fair value of the organization’s fixed assets against the fixed asset records in the subsidiary ledger. 3. The automatic depreciation charges calculated by the fixed asset system should be reviewed and verified for accuracy and completeness. System errors that miscalculate depreciation can result in the material misstatement of operating expenses, reported earnings, and asset values.