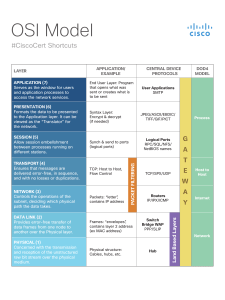
course|notes™ quick reference guide Network+ Guide to Networks, 8th Edition Welcome to Network+ Guide to Networks The CompTIA Network+ (N10-007) exam tests a student’s knowledge and skills needed to manage, troubleshoot, and configure a wired and wireless network. Successful candidates must understand basic network design and technologies, including network limitations and weaknesses. Network professionals must be able to maintain documentation, configure network devices and protocols, and manage security. In addition, the candidate should be familiar with enterprise technologies including virtualization, cloud computing, and mobile devices. Networking Concepts Network Infrastructure Network Operations VLAN 1 Trunk lines with traffic for VLAN 1, VLAN 2, and VLAN 3 Access ports Trunk ports VLAN 2 NETWORK ­Troubleshooting and Tools VLAN 1 Switch A Router Network ­Security Switch C Trunk line with traffic for VLAN 1, VLAN 2, and VLAN 3 Trunk ports Switch B VLAN 3 Access ports What’s new in the CompTIA Network+ (N10-007) certification exam? • • • • More emphasis on virtualization, cloud computing, remote access, and security Focus on practical skills, as well as Data link layer and Network layer technologies More coverage of emerging technologies such as IoT, NFC, and Ant+ Removal of legacy technologies 69378_isrt_ptg01_hires.indd 1 07/05/18 2:59 pm Networking Concepts IP Addressing IPv4 and IPv6 addresses are used to identify computers and networks. IPv4 addresses are 32-bit dotted decimal numbers and are categorized by classes based on the value of the first octet as in the following table: Networks are composed of many pieces that must all work together for proper operation. A network administrator must understand the components of a network including network protocols and ­addresses, network topologies and technologies, wired and wireless networks, and a variety of network services, including cloud services. An essential tool for bringing these many pieces together is the OSI model, which breaks network operations down into seven layers, explaining the role of each component and its interaction with other network components. The OSI model describes a seven-layer approach to networking from how applications should access network services to how bits are transmitted and received on the physical media. The seven layers and the job each layer performs are described in the following table: Application (7) Presentation (6) Session (5) Transport (4) Network (3) Data Link (2) Physical (1) Description Devices and Protocols Provides network services to applications Translates data formats, encryption, and compression Maintains connections between systems Transfers data between applications; reliability, and flow control Provides logical addressing and routing Provides physical addressing, frame formatting, and error detection Transmits and receives bits across the media DNS, DHCP, HTTP, FTP, and File sharing ASCII, EBCDIC, JPEG, TIF, and RDP First Octet Default Subnet Mask Hosts per Network A B C 0-127 128-191 192-223 255.0.0.0 255.255.0.0 255.255.255.0 16,277,214 65,534 254 Class D addresses are used for multicast applications and have a first-octet value of 224-239. Class E addresses are reserved for experimental use and have a first-octet value of 240-255. IPv4 addresses can be public or private. Private IP addresses can be used on any network but public IP addresses are issued by IANA and are used for Internet access. Users of private addresses must use NAT/PAT to gain access to the public Internet. IPv6 addresses are 128 bit numbers divided into 8 groups of 16 bits expressed as hexadecimal digits, for example: FE80:1234:5678:9ABC:DEF0:F00D:BEEF OSI Model Layer Name (Number) Class TCP and UDP Well-Known Ports TCP/IP network applications communicate using Transport layer protocol port numbers. TCP is a connection-oriented Transport layer protocol and uses a three-way handshake to establish a connection between two applications before data is transferred. UDP is a connectionless transport layer protocol that means that data is transferred between the applications without the requirement for a connection to be established. To configure and troubleshoot network communication, you should know the most commonly used port numbers. Login/logout, SQL, and NFS TCP and UDP IP, ICMP, ARP, and routers Ethernet, Frame Relay, ATM, switches, and NICs Cables, connectors, and hubs Network Topologies A network’s topology describes how devices are physically connected (physical topology) and how data moves from one device to another (logical topology). • Star—All devices are connected to a central device such as a switch. The most common topology used in LANs. • Ring—Data is passed along from one device to another in a ring formation. Token Ring and FDDI are common ring ­topologies. • Bus—Devices are connected by a length of cable, usually in daisy-chain fashion. A bus is sometimes used as a network backbone, connecting multiple network segments together. • Mesh—Most often used in WANs or WLANs, devices are ­connected to multiple other devices. Port # Application Transport Layer Protocol 20, 21 22 23 25 53 67, 68 69 80, 443 110 143 161 389 445 3389 FTP SSH Telnet SMTP DNS DHCP TFTP HTTP, HTTPS POP IMAP SNMP LDAP SMB RDP TCP TCP TCP TCP UDP UDP UDP TCP TCP TCP UDP TCP TCP TCP Configuring a WLAN Wireless LANs (WLANs) are an integral part of most wired networks, allowing mobile users access to a network without being tethered to a cable. There are five common 802.11 (Wi-Fi) standards as listed in the following table: Routing Routing moves packets from one network to another until the ­packet reaches the destination network. Routers work with IP ­addresses to determine the best path. Dynamic routing information is learned using routing protocols: • RIPv2, EIGRP—Distance vector routing protocols for small to medium-size private internetworks. • OSPF—A link-state routing protocol used for larger private internetworks. • BGP—A hybrid protocol used for Internet routing. Wi-Fi 802.11 Standards Standard Frequency Band Maximum Speed 802.11a 802.11b 802.11g 802.11n 802.11ac 5 GHz 2.4 GHz 2.4 GHz 2.4 or 5 GHz 5 GHz 54 Mbps 11 Mbps 54 Mbps 600 Mbps 6.93 Gbps Terms and components associated with Wi-Fi networks include: • Antenna—Antennas transmit and receive data and can be ­omnidirectional or unidirectional. • Channels—The range of frequencies on which a device transmits data. 2.4 GHz standards use 11 or 14 channels and 5 GHz standards use up to 25 channels. • Service set identifier (SSID)—The name of a WLAN; used by clients to connect to the network. Switching Switching moves data from one device to another. A switch ­receives incoming data from one of its ports and redirects it to one or more outgoing ports based on the destination MAC address. Switches can be configured to work with routers by using VLANs and trunking protocols such as 802.1q. 2 69378_isrt_ptg01_hires.indd 2 07/05/18 2:59 pm Network Infrastructure Virtualization Virtualization is a process that creates a software environment to emulate a computer’s hardware, BIOS, and networking components, allowing multiple virtual machines (VMs) to run on one physical computer and communicate across a virtual network. Some of the components of virtualization include: • Hypervisor—Creates and monitors the virtual hardware environment, allowing multiple VMs to share physical resources. A hypervisor can be type 1 or type 2. Type 1 hypervisors are used on production servers and run directly on the server hardware whereas type 2 hypervisors run on top of the host operating system and are most often used in testing and development environments. • Virtual switch—A network switch implemented within the hypervisor host. • Virtual NIC—A software implementation of a network interface card attached to a virtual machine. A virtual NIC connects to a virtual switch. • Virtual router/firewall—Software implementations of the hardware devices that allow secure communication between virtual networks and the virtual network and physical network. The infrastructure of a network is built upon the network devices used to connect computers; the media types used to make network connections; and the underlying network technologies, protocols, and topologies that make everything work together. Network+ candidates must know how network devices work and how data is moved from one device to another and from one network to another. They must be familiar with network cabling, Ethernet standards, virtualization, network storage, and how and where to use the network devices that communicate within and between LANs. Network Cabling Network cabling makes physical connections between network devices. Media types include copper and fiber-optic. • Copper cables—Includes coaxial and twisted-pair cabling. Coax cable types: RG-59 and RG-6. Twisted pair types: Cat3 through Cat7, can be shielded or unshielded, and can be PVC or plenum-rated. Connectors include RJ-11 and RJ-45 for UTP and BNC and F-type for coaxial. 110 blocks and 66 blocks are termination panels. Copper cables are terminated using the 568A or 568B wiring standard. • Fiber cables—Made of thin strands of glass, varieties include single-mode fiber (SMF) for longer distances using lasers and multimode fiber (MMF) for shorter distances using LEDs. Connectors include ST, LC, SC, and MTRJ. VM1 vNIC 1 VM2 vNIC 2 VM3 VM4 vNIC 3 vNIC 4 Host machine Ethernet Standards The base standard for Ethernet is IEEE 802.3 but there are many sections of the IEEE 802.3 standard that define operating details such as bandwidth and type of cabling. These standards are specified using the XBaseY naming convention, where X is the bandwidth rating, Base means baseband communication, and Y is the type of cabling used. Ethernet over twisted-pair cabling has a maximum segment length of 100 meters. Some fiber optic implementations can have segments up to 25 miles in length. Some of the most common XBaseY standards are described below: • 100BaseT—100 Mbps Ethernet over twisted-pair cabling. • 1000BaseT—1 Gbps Ethernet over twisted-pair cabling. • 10GBaseT—10 Gbps Ethernet over twisted-pair cabling. • 1000BaseLX—1 Gbps Ethernet over single-mode or multimode fiber. Up to 5000 meters. • 1000BaseSX—1 Gbps Ethernet over multimode fiber. Up to 500 meters. Virtual switch Hypervisor Physical NIC 1 Physical NIC 2 To physical network Network Storage There are two primary types of network storage used by both physical and virtual devices: • Storage Area Network (SAN)—Storage that uses a dedicated network connection, typically Fibre Channel, FCoE, iSCSI, or InfiniBand to connect computers directly to storage devices. • Network Attached Storage (NAS)—Shared storage accessible via the same network as the storage client. Uses standard file sharing protocols such as SMB and NFS. Network Devices WAN Technologies Network devices pass data from one device to another or from one network to another to get the data to its final destination; sometimes performing complex filtering and processing of data packets before they are forwarded. Some of the most common devices and their functions include: • Router—Manages traffic between two or more networks; ­forwards packets based on the network ID of the destination IP address. • Switch—Forwards data frames between devices based on MAC address. • Hub—Receives bit-level signals on one port and repeats the signals out all other ports. • Firewall—Performs routing functions and specialized filtering to block certain types of traffic based on IP addresses, ports, and packet contents. • Wireless access point—Accepts wireless signals from wireless clients and retransmits to the rest of the network. Used in an infrastructure mode wireless network. Advanced networking devices include multilayer switch, IDS/IPS, content filter, load balancer, proxy server, VoIP gateway and PBX, VPN concentrator, and RADIUS server. WAN technologies connect LANs together over long distances, primarily work at the Data Link layer, and include: • Frame relay—Uses packet-switching over SVCs or PVCs. • Leased line—Includes T1, T3, and OC-3 through OC-192 signaling rates. • MPLS—Carries multiple Layer 3 protocols over packetswitched networks using labels for routing and prioritization. • ATM—Uses fixed 53-byte packets called cells over virtual circuits. Other wired WAN technologies include ISDN, DSL, and Metro Ethernet; wireless WANs include WiMax, GSM/CDMA, LTE/4G, and satellite. WAN connections to the local network occur at the demarcation point and typically involve a smart jack and a CSU/DSU. Demarcation point Main office Demarcation point CSU/DSU CSU/DSU CSU/DSU with multiplexer CSU/DSU with multiplexer Customer responsibility Smart jack Smart jack Telco responsibility Branch office Customer responsibility 3 69378_isrt_ptg01_hires.indd 4 07/05/18 6:54 pm Network Operations Disaster recovery is the ability of a network to maintain operations in the event of a major disaster such as fire, flood, or extended power or network outage. Disaster recovery may involve these components: • Cold site—An alternate location where equipment and data can be moved and service restored within several days. • Warm site—An alternate location that is provisioned with some equipment and data, usually only requiring minor setup and data restoration before operations can be resumed; usually within a day. • Hot site—A fully operational alternate location with current data where service can be resumed within minutes or hours. • Backups—An integral component of a disaster recovery plan where data is backed up to an external media such as tapes or external drives. Types of backups include full, differential, and incremental. A snapshot is a type of backup where a copy of data or an entire system is made so the system can be fully restored back to the moment in time the snapshot was taken. Network administrators have a variety of tools, processes, and technologies available to help ensure a reliable and high-performance network. Network documentation makes troubleshooting and scaling a network easier through the use of diagrams, inventory management, labeling, and device configuration documentation and performance baselines. Network uptime is critical and high availability and disaster recovery must be a part of every network plan. In addition, network documentation must include the identification and execution of network policies and best practices. Network Documentation Network documentation includes both physical and logical network diagrams. Physical diagrams show the location of devices and cabling whereas logical diagrams show the overall network topology and logical addressing scheme. Standard symbols are used to indicate types of devices as in the following figure: Wireless access point Scanning and Monitoring A network administrator must continually monitor the network and its devices to ensure optimal operating conditions while also scanning for security vulnerabilities to prevent attacks. Some of the components and processes involved in this undertaking include: • Log reviewing—Most network devices and operating systems generate notifications and alerts of events that have been detected. Network and security devices usually send notifications to a Syslog server or a SIEM service, while Windows OSs use the Event Viewer. • SNMP monitoring—A TCP/IP based protocol used to collect performance metrics from multiple devices and send the data to a network management system for analysis and display. SNMP runs over UDP ports 161 and 162. SNMPv3 adds authentication and encryption for increased security. SNMP uses a Management Information Base (MIB) to store data gathered from network management agents. • Patch management—Network devices and OSs must be continually updated to fix bugs and vulnerabilities. A patch management system provides automatic updates and reporting to ensure all systems are up-to-date. Laptop Web server Internet Firewall Router Switch File server Printer Switch Workstation Additional types of documentation should include: • Rack diagrams—Show representations of physical devices such as routers, switches, and servers and their placement and connections in a standard equipment rack. • MDF/IDF documentation—The MDF is where a WAN provider’s connection is installed and serves as the interconnect between the IDFs. An IDF is where devices connect to patch panels and switches. Usually one or more IDFs per floor connect to the MDF. • Performance baselines—Include the percent utilization of the network, error statistics, CPU utilization on key servers, network service usage, and so forth. Baselines can be used to detect bottlenecks and malfunctioning devices. • Change management—Documents additions, removals, and configuration changes made to network devices and cabling. • Network configuration—Contains device type, model, and configuration details. Analyzing Metrics After data is collected from a network, many performance values must be analyzed to determine the network’s health. Network administrators often create a baseline that includes the percent utilization of the network, error statistics, CPU utilization on key servers, network service usage, and so forth. Baselines can be used to detect bottlenecks and malfunctioning devices. Error statistics might include the following: • Discarded packets—Packets that are discarded, or dropped, by the receiving device because the device was too busy, the packet was no longer relevant or had an error. • Error packets—Packets that are too small (runts), too large ­(giants), continually retransmit (jabber), or anomalous (ghosts). • Utilization and throughput—Measures what percentage of the network and computing bandwidth is being used and the amount of data that passes through the network in a given time period. Business Continuity and Disaster Recovery Business continuity depends on a business’s ability to ensure its network’s high availability. High availability typically involves: • Fault tolerance—The ability for a device to continue to operate after a component failure. • Load balancing—The ability to use two or more of the same devices or media pathways to share the processing or network traffic load. • NIC teaming—The use of two or more NICs in a single computer, with the NICs working together to provide increased bandwidth and fault tolerance. • Port aggregation—Two or more ports on a switch that are bonded together to provide higher bandwidth. • Clustering—Two or more servers working together to provide load balancing and fault tolerance. • Battery backup/UPS—The use of a battery backup and uninterruptible power supply (UPS) to provide power to a network device in the event of a power failure. Remote Access Most networks have provisions for users to access the network while working from home or while traveling. A number of remote access methods exist, with the most common being virtual private network (VPN). A VPN provides secure client-to-site or site-tosite communication using authentication and encryption. Common VPN protocols include IPSec, PPTP, and SSL. Other remote ­access protocols include remote desktop protocol (RDP), virtual network computing (VNC), SSH, and Telnet. 4 69378_isrt_ptg01_hires.indd 5 07/05/18 6:56 pm Network Security Access controls may include one or more of the following: • 802.1X—Also known as EAPoL, a port-based mechanism used to control access to wired or wireless clients by restricting ­access to the AP or switch port to only authenticated devices. • NAC—A policy-driven system used to determine the level and type of access granted to a device such as firewalls, routers, and switches. • Access control lists—A list of rules configured on a device that permits or denies traffic based on source and destination ­address, and network protocol. A lot of time is spent configuring a network to ensure that authorized users have access to network resources; perhaps more important is ensuring that unauthorized persons do not have access to the network. Network security is of paramount importance because so much important data is kept on networks, from social security numbers, to credit card information, to private health data. Network security involves concepts such as disaster recovery, encryption protocols, attacks and threats, malware, access controls, and physical security. A network technician’s understanding of security risks and countermeasures is of utmost importance on both wired and wireless networks. Wireless Security Wireless security requires special considerations because, unlike wired media, the network signals are unbounded and can therefore be captured by anybody with the appropriate radio receiver. To mitigate the problem, wireless networks should always be encrypted and may also require user or device authentication. Wireless encryption and authentication methods include: • WPA2—The strongest encryption standard; uses the AES or AES-CCMP encryption algorithm. WPA2-Enterprise or WPA2802.1X requires an authentication server. • WPA—Less secure than WPA2; uses TKIP-RC4 for ­encryption. • EAP (Extensible Authentication Protocol)— A framework for authentication protocols that use authentication and encryption. Common EAP variants include EAP-TLS, EAPoL, EAP-FAST, and PEAP. EAP can be used with smart cards, biometrics, and traditional username/password authentication methods. • MAC Filtering—A method that restricts access to the wireless network to devices with specific MAC addresses. Since MAC addresses can be spoofed, it should not be used as the sole security method. Physical Security If someone has physical access to a device, it is not secure. ­Network devices and servers must be installed in a secure location with strict rules governing who has access to the location, and with well-defined procedures for enforcing those rules and detecting if a breach has occurred. To summarize: the two tenets of physical security are prevention and detection. Common prevention methods include: • Badges and Smart cards—A security badge may simply contain information a security guard can use to verify a person’s identify, such as a photo, name, and title. Most, however, are smart cards that have digital data encoded on them that specifies which doors a person can open by swiping the card through a reader or by using a proximity sensor. • Biometrics—Biometric sensors authenticate a person using unique traits such as fingerprint, iris pattern, or facial recognition. • Key fob—A small handheld device, often placed on a key ring that contains identifying and access information for a user. In the event of a security breach or attempted breach, detection methods must be in place: • Motion detection—Detects movement in a room or ­ outdoor space that can generate an alarm, notification, or ­countermeasures. • Video surveillance—Creates a video log of all activity for ­real-time monitoring or archival purposes. • Asset tracking tags—Small tags placed on items that generate a signal that can be picked up by a reader when an item enters or exits a room or building. • Tamper detection—Detects whether a device has been physically opened or otherwise tampered with. Common Network Attacks Networks face varied and numerous threats from hackers and malware. Network administrators must know what threats they face to properly secure a network. Some of the more common network attacks include the following: • Denial of service (DoS)—A network attack that attempts to prevent legitimate users from accessing a network or service; usually works by consuming excessive network or server resources. A distributed DoS (DDoS) is a coordinated attack that comes from multiple sources. Distributed reflective DoS (DRDoS) attacks use spoofing to hide the source identity. • Brute force—An attempt to guess a password or encryption key using numerous character combinations. • Social engineering—An attack that uses a person’s trust or naiveté to gain access to a system. • Man-in-the-middle—An attack that captures secure transmissions between two parties without either party’s knowledge. • Ransomware—A program that locks a user’s data or computer system until a ransom is paid. • DNS poisoning—An attack in which the hacker redirects traffic to the attacker’s web server by altering DNS records. Authentication and Access Controls System and data security is founded on two components: ­Authentication verifies someone’s identity and access controls allow or deny an authenticated user access to a system or data. There are a variety of authentication methods including: • Kerberos—Used with Windows Active Directory and supported on other systems, it uses the concept of keys to validate identity and tickets to grant access. • RADIUS—A centralized authentication, authorization, and accounting (AAA) service commonly used for remote access, wireless networks, and network device access. • TACACS+—Another AAA service, developed by Cisco, typically used for network device access control. • Certificates—A digital document that contains identifying information and usually an encryption key for identity verification and secure communication. Commonly used by HTTPS and SSL in a public key infrastructure (PKI). • Multifactor authentication (MFA)—Combines two or more authentication methods, such as a user name plus password and biometrics. Network Device Hardening Network hardening attempts to reduce network and system vulnerabilities, thereby stopping or detecting attacks before they are exploited. Some technologies and techniques for network hardening include: • Anti-malware software—Install software that detects and sometimes removes malware such as viruses, worms, rootkits, spyware, and adware. • Credentials—Change default administrator credentials on OSs and network devices. Use strong passwords. • Software updates—Keep software and device firmware up-todate and apply patches in a timely manner. • Services and ports—Disable unnecessary network services and TCP/UDP ports. Disable unused physical switch and router ports. 5 69378_isrt_ptg01_hires.indd 7 07/05/18 6:57 pm Network Troubleshooting and Tools • • Troubleshooting a network is as much an art as it is a science. There is no substitute for practice and experience, but there is a methodology you should follow that will help with troubleshooting not only networks, but most problems you encounter in life. In addition, you need to be familiar with the various tools, both software and hardware, that are commonly used to troubleshoot networks. The successful network troubleshooter will draw upon a variety of skills, technologies, and techniques to solve the problems encountered on increasingly complex LANs and internetworks. Troubleshoot Wireless Connections Wireless networks pose unique problems compared to wired networks since there is no tangible media to inspect and test. Some of the more common problems and wireless signal characteristics that can affect signal quality include: • Interference—Signal quality can be adversely affected by other radio signals using the same frequencies as a WLAN. • Overlapping channels—Nearby WLANs using the same or adjacent channels degrade signal quality. • Power level—The transmitter power can be increased or ­decreased to provide the best wireless signal coverage. • Rogue access point—An unauthorized access point (AP) can degrade signal quality or pose as a valid AP to steal data or gain unauthorized access to another network. • Antenna type—Using the proper antenna type (unidirectional or omnidirectional) for a given scenario is critical for a strong signal. • AP placement—A site survey must be done to determine the best placement for access points. Environmental factors such as concrete walls, reflective materials on windows, and metals studs can all affect signal quality. Keep in mind signal phenomena: reflection (bounce), diffraction, and scattering. • Mismatches—The wireless client must use the same ­encryption protocol and passphrase as the AP and the correct SSID (SSIDs are case sensitive). Troubleshooting Methodology CompTIA defines a seven-step approach to network troubleshooting as follows: 1. Identify the problem 2. Establish a theory of probable cause 3. Test the theory to determine cause 4. Establish a plan of action 5. Implement the solution or escalate as necessary 6. Verify system functionality 7. Document findings, actions, and outcomes Using Troubleshooting Tools Some of the tools needed to troubleshoot a network are built right into the operating system in the form of command-line tools as described in the following table: Command Description ipconfig ping tracert nslookup arp pathping netstat nmap View IP address configuration Verify host connectivity View path to a device Perform DNS lookups View arp cache Verifies path and connectivity Displays TCP/IP connection information Scans a network for open ports and provides application and OS information about hosts Troubleshoot Network Issues Numerous things that can go wrong with a network, ranging from misconfigured devices to hardware failures. Network technicians must be able to recognize the signs and symptoms of some of the most common reasons for network failure so they can quickly identify and resolve them. The following list describes some common reasons for network errors or failures: • Incorrect IP configuration—Occurs when the IP address, subnet mask or default gateway of a device doesn’t match the network configuration. Most often occurs with static addresses. Use ipconfig to verify. • Blocked ports—Misconfigured firewalls can result in ports ­being blocked that applications require. Ports can also be blocked by incorrect ACL settings on routers. • Duplicate IP—Most often occurs when addresses are assigned statically or if the DHCP server is malfunctioning. Use ipconfig to verify or examine the DHCP server lease data. • Misconfigured DHCP—If the DHCP server has incorrect scope data or options, all devices on the network that use dynamic addresses will be affected. Check for exhausted DHCP scope. In addition, protect against rogue DHCP servers using DHCP snooping on switches. You may also need to use a variety of other tools and equipment to install, troubleshoot, and test a network: Tool Description Protocol analyzer Multimeter Cable tester Spectrum analyzer Tone generator Light meter TDR/OTDR Capture and view packets; also called a sniffer Test electrical properties Check patch cables and cable terminations Assesses the quality of a wireless signal Verifies cable location and continuity Measures light power for fiber optic cabling Measures copper/fiber cable length EMI/RFI—Electromagnetic or radio frequency interference generated by motors, fluorescent lights, power lines, and large machinery and electronic equipment. Attenuation—The weakening of the signal as it travels across the length of the media. Attenuation can be a problem if the media exceeds the maximum length. Troubleshoot Wired Connections Copper cables must be properly terminated by installing an RJ-45 plug or by punching down the ends into an RJ-45 jack or a 110 block patch panel. Improper termination or incorrect installation can cause a variety of problems including the following: • Open—A problem that occurs when a circuit does not exist such as when a wire breaks or is not making contact with a conductor. • Short—A problem that occurs when two wires that should not touch, come into contact with each other. • Crosstalk—Interference caused by the electromagnetic field of one wire traveling to an adjacent wire. Near end crosstalk (NEXT) occurs near the transmitter and far end crosstalk (FEXT) occurs near the receiver. © 2019 Cengage Learning ALL RIGHTS RESERVED. No part of this work covered by the copyright herein may be reproduced, transmitted, stored, or used in any form or by any means graphic, electronic, or mechanical, including but not limited to photocopying, recording, scanning, digitizing, taping, Web distribution, information networks, or information storage and retrieval systems, except as permitted under Section 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the publisher. 6 69378_isrt_ptg01_hires.indd 9 07/05/18 6:58 pm