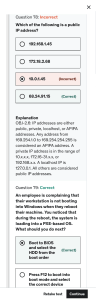
9/20/22, 1:21 PM CompTIA Network+ N10-008 Contents 1. Networking Fundamentals 1.1 Compare and contrast the Open Systems Interconnection (OSI) model layers and encapsulation concepts. 1.2 Explain the characteristics of network topologies and network types. 1.3 Summarise the types of cables and connectors and explain which is the appropriate type for a solution. 1.4 Given a scenario, configure a subnet and use appropriate IP addressing schemes. 1.5 Explain common ports and protocols, their application, and encrypted alternatives. 1.6 Explain the use and purpose of network services. 1.7 Explain basic corporate and datacenter network architecture. 1.8 Summarise cloud concepts and connectivity options. 2. Network Implementations 2.1 Compare and contrast various devices, their features, and their appropriate placement on the network. 2.2 Compare and contrast routing technologies and bandwidth management concepts. 2.3 Given a scenario, configure and deploy common Ethernet switching features. 2.4 Given a scenario, install and configure the appropriate wireless standards and technologies. 3.0 Network Operations 3.1 Given a scenario, use the appropriate statistics and sensors to ensure network availability. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 1/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 3.2 Explain the purpose of organisational documents and policies. 3.3 Explain high availability and disaster recovery concepts and summarise which is the best solution. 4.0 Network Security 4.1 Explain common security concepts. 4.2 Compare and contrast common types of attacks. 4.3 Given a scenario, apply network hardening techniques. 4.4 Compare and contrast remote access methods and security implications. 4.5 Explain the importance of physical security. 5.0 Network Troubleshooting 5.1 Explain the network troubleshooting methodology. 5.2 Given a scenario, troubleshoot common cable connectivity issues and select the appropriate tools. 5.3 Given a scenario, use the appropriate network software tools and commands. 5.4 Given a scenario, troubleshoot common wireless connectivity issues. 5.5 Given a scenario, troubleshoot general networking issues. 1. Networking Fundamentals 1.1 Compare and contrast the Open Systems Interconnection (OSI) model layers and encapsulation concepts. OSI model Layer 1 - Physical: Turns physical signals (light/electricity) into data/bits. Accounts for bit sync, https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 2/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 bit rate control, physical topologies & transmission mode (i.e. half/full duplex or simplex). Layer 1 devices include hubs, repeaters, modems & cables. Layer 2 - Data Link (MAC frames): Responsible for communication between physical devices that are directly connected, and encapsulates sender & receivers MAC address in frame headers. Functions include framing, physical addressing, error control, flow control & access control. Layer 2 devices include NIC's and switches. Layer 3 - Network (IP packets): Transmits data between hosts on different networks and handles packets and packet routing. Works with IP addresses. Layer 3 devices include routers. Layer 4 - Transport (Segments with port numbers): Responsible for end to end delivery of messages. Provides acknowledgement of of successful data transmission or re-transmits data if needed. Uses segmentation, and the data type is referred to as segments. Looks after flow & error control and adds source and destination port numbers to the segment header. The transport layer is managed by the OS. It is referred to as the heart of the OSI model. Layer 5 - Session: Responsible for the establishment, maintenance, and termination of connections. Mediates the communication between hosts and adds synchronisaton points to transmissions. Looks after full duplex/half duplex settings. Handled by network applications. Layer 6 - Presentation: Also referred to as the translation layer. Data is extracted to or from a format compatible with the adjacent layers. Handles translation (i.e. from ASCII to EBCDIC), encryption/decryption, and compression. Layer 7 - Application: Produces/displays data that is to be/has been transferred over the network. Usually https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 3/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 implemented via protocols rather than literal desktop applications. Data encapsulation and decapsulation within the OSI model context Ethernet frame header: Preamble > SFD (Start of Frame Delimiter) > Destination MAC Address > Source MAC address > Frame Length > Data > CRC (Cyclic Redundancy Check aka Checksum) Internet Protocol (IP) header: Version (IP Version) > Header Length > Priority and Type of Service > Packet Length > Identification > Flags > Fragmented Offset (for reassembly fragmented packets) > TTL > Protocol (TCP/UDP) > Source IP > Destination IP > Options TCP/UDP headers TCP: Source Port > Destination Port > Sequence Number > Acknowledgement Number > DO (Data Offset) > RSV (Reserved) > Flags (URG: Urgent > ACK: Acknowledgement > PSH: Push > RST: Reset > SYN: Synchronise > FIN: Finish) > Window > Checksum > Urgent > Options UDP: Source Port > Destination Port > Datagram Length > Checksum TCP flags: URG: Urgent > ACK: Acknowledgement > PSH: Push > RST: Reset > SYN: Synchronise > FIN: Finish Payload: Layer 2: (MAC) Frames > Layer 3: (IP) Packets > Layer 4: (Ports) Segments Maximum Transmission Unit (MTU): 1500 bytes unless using Jumbo Frames which can be up to 9000 bytes. 1.2 Explain the characteristics of network topologies and network types. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 4/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Mesh: Each host is physically connected with all other hosts on the network. Cabling requirements expand exponentially unscalable. Star/hub-and-spoke: Each host is physically connected with a central node such as a router, hub, or switch. Bus: All devices connected to a common half-duplex link that terminates at both ends. Ring: The same as bus topology, however all nodes connect to two other nodes, meaning that the common link does not terminate and forms a ring. Hybrid: The combination of two or more topologies. Network types and characteristics Peer-to-peer: Interconnected devices directly sharing resources with one another. Client-server: Centralised servers providing resources to multiple clients. LAN: Local Area Network MAN: Metropolitan Area Network WAN: Wide Area Network WLAN: Wireless Local Area Network PAN: Personal Area Network CAN: Campus Area Network SAN: Storage Area Network SDWAN: Software Defined Wide Area Network MPLS: Multiprotocol Label Switching mGRE: Multipoint Generic Routing Encapsulation Service related entry point Demarcation point: Physical network boundary point between telecom and private network. Smartjack: Network demarcation terminals that provide diagnostic capabilities. Virtual network concepts vSwitch: A virtual switch. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 5/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 vNIC: A virtual NIC. NFV: Network Function Virtualisation. The replacement of physical network devices with virtual versions. Hypervisor: Software that creates and runs virtual machines. Provider links Satellite: Self explanatory. DSL: Digital Subscriber Line - data over telephone lines. Cable: Data over coax/cable TV infrastructure. Leased line: A dedicated communication channel between two sites. Metro-optical: MAN over fibre. 1.3 Summarise the types of cables and connectors and explain which is the appropriate type for a solution. Copper Twisted pair: Two wires are twisted together to reduce electromagnetic interference. Cat 5: 1Gbps, 1000BASE-T, 100MHz Cat 5e: 1Gbps, 1000BASE-T, 100MHz Cat 6: 1Gbps, 1000BASE-T, 250Mhz Cat 6a: 10Gbps, 10GBASE-T, 600Mhz Cat 7: 10Gbps, 10GBASE-T, 1Ghz Cat 8: 40Gbps, 40GBASE-T, 2Ghz Coaxial/RG-6: Single conductor Twinaxial: Two conductors Termination standards https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 6/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 TIA/EIA-568A: Green White > Green > Orange White > Blue > Blue White > Orange > Brown White > Brown TIA/EIA-568B: Orange White > Orange > Green White > Blue > Blue White > Green > Brown White > Brown Fibre: Data transmission by light. Single mode: Used for long range communication (<= 100KM). Uses laser beams. Multimode: Used for short range communication (<= 2KM). Typically uses LEDs. The core of the fibre is larger than the wavelength of light, the light splits as it travels and takes the form of multiple modes. Connector types LC (Local Connector): Rectangular and small. Has two fibres, one each for send and receive. Has clips similar to an RJ45. ST (Straight Tip): Round. Use bayonet connectors. SC (Subscriber Connector): Sometimes referred to as Square Connector. Unique, spring loaded locking mechanism. MT-RJ (Mechanical Transfer Registered Jack): Smallest fibre connector. Has two fibre connections. Similar looking mechanism to LC (Local Connector). APC (Angled Physical Contact): Has a slight angle, lower return loss. UPC (Ultra Physical Contact): Not angled. High return loss. RJ11: 6P2C, used for DSL & analogue telephone connections. RJ45: 8P8C F-type: Used with cable modems, DOCSIS, generally RG-6, threaded connector. Transceivers/media converters: Layer 1 devices. Convert network signals to different types i.e copper > https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 7/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 fibre, fibre > copper. Transceivers are defined by the capability to both transmit and receive data. Transceiver type SFP (Small Form-factor Pluggable): 1Gbps. SFP+ (Enhanced Small Form-factor Pluggable): 16Gbps. Same size as SFP. QSFP (Quad Small Form-factor Pluggable): Four channel SFP. 4Gbps. QSFP+ (Enhanced Quad Small Form-factor Pluggable): 40Gbps. Cable management Patch panel: Intermediate connector between hosts and switches. Fibre distribution panel: Used for accommodating fiber cable terminations, connections and patching. Punchdown block 66: Usually used for analogue voice. Left is patched to right. 110: Replaced 66 blocks. Supports Cat5 & Cat6 cables. Metal bites into insulator. Krone: European alternative to 110 block. BIX (Building Industry Cross Connect): Has been updated over the years, supports Cat6. Ethernet standards: Baseband - single frequency. Copper 10BASE-T: 10 Mbps. Two pair. Cat3 minimum. 100 meter max. 10BASE-TX: 100 Mbps. Two pair. Cat5 minimum. 100 meter max. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 8/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 1000BASE-T: 1 Gbps. Four pair. Cat5 minimum. 100 meter max. 10GBASE-T: 10 Gbps. Four pair. Cat6 minimum. 100 meter max. 40GBASE-T: 40 Gbps. Four pair. Cat8 minimum. 30 meters max. Fibre 100BASE-FX: 100 Mbps. Laser. 400 meters half-duplex, 2 kilometres fullduplex. 100BASE-SX: 100 Mbps. LED. 300 meters max. 1000BASE-SX: 1 Gbps. Short wavelength laser. 550 meters. 1000BASE-LX: 1 Gbps. Long wavelength laser. 5 kilometres. 10GBASE-SR: 10 Gbps. Multimode fibre. 400 meters. 10GBASE-LR: 10 Gbps. Single mode fibre. 10 kilometres. WDM (Bidirectional Wavelength Division Multiplexing): Bidirectional communication over a single strand of fibre for multiple types of signals. Uses different wavelengths for each carrier. CWDM (Coarse Wavelength Division Multiplexing): 10GBASE-LX4. DWDM (Division Wavelength Division Multiplexing): 160 signals, up to 1.6 Tbps. 1.4 Given a scenario, configure a subnet and use appropriate IP addressing schemes. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a s… 9/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Public vs. Private RFC1918: Defines private IP address ranges. 10.0.0.0 to 10.255.255.255. 16,777,216 addresses. 172.16.0.0 to 172.31.255.255. 1,048,576 addresses. 192.168.0.0 to 192.168.255.255. 65,536 addresses. Network Address Translation (NAT): The changing of an IP address as it progresses through a network, usually from private to public or vice versa. Port Address Translation (PAT): Translation of port numbers from source to destination and vice versa. IPv4 vs IPv6 Automatic Private IP Addressing (APIPA): Link local address. Automatically assigned. Unable to communicate with the router and therefore external networks. 169.254.1.0 to 169.254.254.255. Picked randomly from range/automatically assigned. Extended Unique Identifier (EUI-64): Extends the MAC address into a 64 bit value. The MAC address is split into two 3 byte halves. A value of 'FFFE' is placed in between these halves to make the address 64 bits in length. The 7th bit of the of the first half of the MAC address is flipped to distinguish the address as a local address rather than a globally unique address. Multicast: One to many of many communication (only those who want it). Unicast: One to one communication. Anycast: One to one of many communication (data is delivered only to the closest device with the correct anycast address). Broadcast: One to all communication. Link local: Same as APIPA. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 10/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Loopback: 127.0.0.1 - the address of the machine you're using. Default gateway: The IP address of the device which provides a gateway out of the network. The router. IPv4 subnetting: https://www.youtube.com/playlist? list=PLIFyRwBY_4bQUE4IB5c4VPRyDoLgOdExE Classless (variable length subnet mask): See CIDR notation. Classful A: Leading bits: 1 - 127. Subnet mask: 255.0.0.0. B: Leading bits: 128 - 191. Subnet mask: 255.255.0.0 C: Leading bits: 192 - 223. Subnet mask: 255.255.255.0 D: Leading bits: 224 - 239. Used for multicast. E: Leading bits: 240 - 254. Reserved. Classless Inter Domain Routing (CIDR): Ones on the left (network), zeroes on the right (host). IPv6 concepts: 128 bit address. First half of address (the first 64 bits) is typically associated with the subnet. The second half is created by combining 1. The first three bytes of the MAC address (with the 7th bit flipped), 2. FFFE, 3. The last 3 bytes of the MAC address. Tunnelling: 6to4 addressing allows sending of IPv6 traffic over an IPv4 network. 4to6 does the opposite. No NAT and requires router relays. Teredo (Windows)/Miredo (Linux/BSD/macOS) allow tunnelling of IPv6 through NATed IPv4 networks with no special routers needed. Dual stack: Running both IPv4 and IPv6 simultaneously. Shorthand notation: Leading zeroes are optional. Groups of zeroes can be removed and replaced with a double colon (this can only be done once per address). https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 11/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Router advertisement: IPv6 has no broadcast functionality and therefore no ARP. Instead, this is is managed by Neighbour Discovery Protocol (NDP) using multicast. Stateless address autoconfiguration (SLAAC): The automatic configuration of IP addresses (without a DHCP server). Virtual IP (VIP): An IP address not associated with a physical network adapter. Subinterfaces: One physical network interface handling multiple VLANs. 1.5 Explain common ports and protocols, their application, and encrypted alternatives. Protocols Ports Description File Transfer Protocol (FTP) 20/21 Transfers files. Secure Shell (SSH) 22 Facilitates secure, remote, shell access. Secure File Transfer Protocol 22 (SFTP) Provides secure file access, transfer, and management. Telnet 23 Unsecured bidirectional interactive text communication. 25 Allows for server to server email communication. 53 Decentralised database used to identify computers. Simple Mail Transfer Protocol (SMTP) Domain Name System (DNS) https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 12/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Dynamic Host Configuration Protocol (DHCP) 67/68 Automatically assigns IP addresses. Trivial File Transfer Protocol (TFTP) 69 Simple file transfer protocol. Hypertext Transfer Protocol (HTTP) 80 Transfers hypertext. Post Office Protocol v3 (POP3) 110 Provides basic mail transfer functionality. Network Time Protocol (NTP) 123 Synchronises clocks among network devices. 143 Send, receives, and allows management of email on a remote server. 161/162 Gathers stats from network devices. Has notification functionality. Lightweight Directory Access Protocol (LDAP) 389 A protocol for accessing and maintaining distributed directory information services. Hypertext Transfer Protocol Secure (HTTPS) [Secure Sockets Layer (SSL)] 443 Self explanatory. Hypertext Transfer Protocol Secure (HTTPS) [Transport Layer Security (TLS)] 443 Self explanatory. Internet Message Access Protocol (IMAP) Simple Network Management Protocol (SNMP) Server Message Block (SMB) 445 Syslog 514 Windows file sharing protocol. A protocol for sending and receiving system https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 13/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 logs. SMTP TLS 587 Self explanatory. Lightweight Directory Access Protocol (over SSL) (LDAPS) 636 Self explanatory. IMAP over SSL 993 Self explanatory. POP3 over SSL 995 Self explanatory. Structured Query Language (SQL) Server 1433 Databases. SQLnet 1521 Databases. MySQL 3306 Databases. Remote Desktop Protocol (RDP) 3389 Microsoft's proprietary remote system access protocol. Session Initiation Protocol (SIP) 5060/5061 Used for VOIP. IP protocol types Internet Control Message Protocol (ICMP): A basic communication protocol, usually used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address. Ping uses ICMP. TCP: https://i.ibb.co/wznfjgr/jrbdgx5j7md51.jpg UDP: https://i.ibb.co/wznfjgr/jrbdgx5j7md51.jpg Generic Routing Encapsulation (GRE): Creates a tunnel between two IP endpoints, making them appear to be directly connected. No encryption. Internet Protocol Security (IPSec): A VPN protocol. Provides encryption and security of data over OSI layer 3. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 14/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Authentication Header (AH): Includes a hash of the IP packet and a shared key. Encapsulating Security Payload (ESP): Encrypts the packet. Adds a header, trailer, and an Integrity Check Value. Connectionless vs connection-oriented: The main differentiator between TCP & UDP. 1.6 Explain the use and purpose of network services. Dynamic Host Configuration Protocol (DHCP): Automatic assignment of IP addresses to devices on the local network. Confined to the local subnet. Uses the IPv4 broadcast domain. Stops at the router. Scope: A single configurable contiguous pool of IP addresses that can be leased to clients. Exclusion ranges: A configurable range of IPs that do not get leased to clients. Reservation: See static assignment. Dynamic assignment: The server has a pool of addresses to hand out, they get reclaimed after a lease period (if unused). Static assignment: Hosts get designated a static IP address by the DHCP server. Hosts are identified by MAC address. Lease time: DHCP addresses renew at the following times, in the following order - T1: 50% of the lease time; T2: 87.5% (7/8ths) of the lease time, from any DHCP server. T2 only takes effect if the original DHCP server is down. DHCP relay: Routers can be configured as DHCP relays in order to extend DHCP functionality beyond the local subnet. IP helper/UDP forwarding: See DHCP relay. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 15/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 DNS: Domain Name System. Used to translate domain names to IP addresses. Record types Address (A vs AAAA): A = IPv4 address; AAAA = IPv6 address. Canonical name (CNAME): Aliasing. Mail exchange (MX): Defines the host name for a mail server. Start of authority (SOA): Meta DNS info. Pointer (PTR): Provides info for reverse DNS lookups. Text (TXT): Human readable information. Commonly used for Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM). Service (SRV): A record pointing to other services on the domain (i.e. LDAP, VOIP). Name server (NS): Lists the nameservers associated with the domain. Global hierarchy Root DNS servers: 13 root server clusters. Internal vs external: Self explanatory: where are the DNS servers? Zone transfers: Zone transfers are used to copy a domain’s database from a primary server to a secondary server. Authoritative name servers: Cached responses are non-authoritative. Time to live (TTL): Configured on the authoritative server. Specifies how long a cache is valid in seconds. DNS caching: The storage of retrieved DNS results on a host. Reverse DNS: Provide the DNS server with an IP address and receive a Fully Qualified Domain Name (FQDN) in return. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 16/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Reverse lookup: dig -x 93.184.216.34. Provide the DNS server with an IP address and receive a Fully Qualified Domain Name (FQDN) in return. Forward lookup: dig www.example.com. Provide the DNS server with a FQDN. Receive an IP address in return. Recursive lookup: Single query from client. DNS servers communicate between each other to sort out the rest. Iterative lookup: The host initiates all queries. NTP: Network Time Protocol. Stratum: Measure of accuracy. Starts at 0, which would be an atomic clock. Stratum 1 would be a primary time server. A device that pull time from a Stratum 1 device would be a Stratum 2 device. Clients: A device that gets its NTP info from an NTP server. Server: A device that provides NTP info to NTP clients. 1.7 Explain basic corporate and datacenter network architecture. Three-tiered Core: Web servers, databases, server applications. Distribution/Aggregation: Manages communication between users and the core. Access/Edge: User facing infrastructure. Workstations, printers. Software defined networking: Replacing physical networking devices with virtual versions. Split into separate, functional layers. Application layer/management plane: End user facing management of the control layer. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 17/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Control layer: Manages the infrastructure layer/control plane. Contains internal resources such as routing tables, session tables, and NAT tables. Infrastructure layer/data plane: Does the "real" networking. Virtual switches, routers, and firewalls. Spine and leaf: Services connect to leaf switches, leaf switches connect to spine switches. Spine switches are fully meshed with leaf switches. Leaf switches do not connect to each other. Spine switches do not connect to each other. Top-of-rack switching: A conceptual hierarchical topology. Leaf switches are "on top" of hosts, etc. Traffic flows North-South: Traffic that is travelling in/out of the datacenter. East-West: Traffic between devices in the same datacenter. Network locations Branch office: Local. On-prem datacenter: A wholly self managed datacenter. Colocation: Your hardware in a datacenter managed by another company. Storage Area Networks (SAN): Appears as a local device to end users. Block level storage/access. Requires a lot bandwidth, may use an isolated network. Connection types Fibre Channel over Ethernet (FCoE): No special hardware required, integratable with FC setups. Fibre Channel (FC): A specialised high speed topology used for SANs. 2, 4, 8, and 16Gbps transfer rates. Requires a special FC switch. Internet Small Computer Systems Interface (iSCSI): SCSI over a network. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 18/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 1.8 Summarise cloud concepts and connectivity options. Deployment model Public: Available publicly over the internet. Private: Your own (virtualised) datacenter. Hybrid: A mixture of private and public. Community: Resources shared by several organisations. Service models Software as a Service (SaaS): On demand, externally hosted software. Infrastructure as a Service (IaaS): Self managed remote hardware. Platform as a Service (PaaS): Serverless. No management required, ready for development. Desktop as a Service (DaaS): PC becomes a thin client. Infrastructure as code: Using code to define and deploy remote infrastructure. Entire servers can be deployed and/or destroyed instantly. Automation/Orchestration: Saltstack, Ansible etc. Connectivity options Virtual Private Network (VPN): Site to site encrypted tunnelling. Private-direct connection to cloud provider: Virtual Private Cloud (VPC) endpoint to cloud provider. Multitenancy: Shared hosting. Elasticity: Rapid scaling of resources. Scalability: See elasticity. Security implications: Need to be adjusted according to the context. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 19/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 2. Network Implementations 2.1 Compare and contrast various devices, their features, and their appropriate placement on the network. Networking devices Layer 2 switch: Layer 2 device. Forwards packets based on destination MAC addresses. Layer 3 capable switch: Layer 3 device. Managed switch. Switch/router/firewall, all in one. Router: Layer 3 device. Routes traffics between IP subnets. Hub: Layer 1 device. Half duplex. Any incoming traffic is repeated out to all other ports. Access Point: Layer 2 device. Extends a wired network onto a wireless network. Bridge: Layer 2 device. A switch with not many ports (2 to 4). WLAN controller: Provides centralised management of WAPs. Load balancer: Distributes request load between multiple web servers. Provides redundancy and fault tolerance. Proxy server: Usually sits between users and the external network. Handles requests and responses on the users behalf. Cable modem: A modem that connects to a cable service over DOCSIS (Data Over Cable Service Interface Specification. DSL modem: Commonly ADSL. Uses telephone lines. Repeater: Layer 1 device. Receives a signal, amplifies, and forwards. Voice gateway https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 20/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Media converter: Layer 1 device. Converts between network mediums i.e. copper > fibre or vice versa. Intrusion Prevention System (IPS)/Intrusion Detection System (IDS): Analyses network traffic. IDS alerts when attacks occur, IPS prevents attacks. Firewall: Layer 2/3 devices. Filters traffic by port number, IP address, or application. VPN headend: A purpose built VPN gateway. Networked devices VOIP phone: Self explanatory. Printer: Self explanatory. Physical access control devices: Devices that control physical access to rooms etc. Card readers, biometric authenticators, pin pads. Cameras: Self explanatory. Heating, Ventilation, and Air-Conditioning (HVAC) sensors: Self explanatory. Internet of Things (IoT): The trend of connecting random things that don't need to be networked, to the internet. VLAN'd. Refrigerators: Self explanatory. Smart speakers: Self explanatory. Smart thermostats: Self explanatory. Smart doorbells: Self explanatory. Industrial control systems/Supervisory Control And Data Acquisition (SCADA): Control of factory/farm/warehouse/manufacturing equipment, commonly seen on https://computernewb.com/vncresolver/ 2.2 Compare and contrast routing technologies and bandwidth management concepts. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 21/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Routing Dynamic routing: Handle the updating of routing tables within routers by seeking other routers nearby while simultaneously advertising their own presence. Protocols: Determine the optimal routing path. Routing Internet Protocol (RIP): Distance vector routing protocol (takes the path with fewest hops). Enhanced Interior Gateway Routing Protocol (EIGRP): Distance vector routing protocol (takes the path with fewest hops). Open Shortest Path First (OSPF): Link state routing protocol. Takes bandwidth into account, will take the fastest route to destination disregarding the number of hops required. Border Gateway Protocol (BGP): Hybrid protocol. Uses distance vector + link state criteria, plus network policies and/or configured rule sets to determine the optimal path to destination. Link state vs distance vector vs hybrid: See above for explanation and examples. Static routing: You define where the next hop will be by manually editing the routing table. In routing tables, lower numbers in the metric column have higher priority. Administrative distance numbers also are prioritised with lower numbers first - administrative distances prioritise different routing protocols. Default route: Used if there are no valid options in the routing table. The gateway of https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 22/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 last resort. Exterior vs interior: In relation to the local network. Time To Live (TTL): A number attached to packets that reduces by 1 at every hop. When it reaches 0, the packet is destroyed. Prevents indefinite loops from occurring. Bandwidth management Traffic shaping: The prioritising of traffic according to protocol/application. Quality of Service (QoS): Same as traffic shaping. 2.3 Given a scenario, configure and deploy common Ethernet switching features. Virtual Local Area Network (VLAN): Segmentation of single physical networks into multiple logical networks. Voice VLAN: A separate VLAN for VOIP data that can be prioritised over general data. Port configurations: Port tagging/802.1Q: The addition of a tag to the L2 frame with VLAN info. Port aggregation: Link Aggregation Control Protocol (LACP): Used in the management of Link Aggregation/Port Bonding, which is aggregation of multiple switch ports in order to make them act as a single interface. Duplex: Full duplex Ethernet can send and receive data simultaneously. Half duplex Ethernet can send and receive data, but not at the same time. Simplex Ethernet can only send information in one direction. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 23/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Speed: Self explanatory? Ethernet/ports can be built to handle different speeds. 10/100/1,000/10,000 Flow control: Implemented when data is being transmitted faster than it can be accepted at the receiving end. A PAUSE frame is sent, halting the transmission of data for a specified amount of time (represented by a two-byte unsigned integer (aka up to 65535 seconds)). Port mirroring: Mirroring a copy of packets seen on one switch port (or entire VLAN), to a network monitoring connection on another switch port. Can be also be implemented on virtual hardware. Port security: Prevents unauthorised MAC addresses from accessing the switch. AKA MAC address whitelisting. Jumbo frames: The typical MTU of an Ethernet frame is 1,500 bytes. Jumbo Frame compatibility bumps this up to 9,000 bytes. Auto Medium Dependent interface crossover (MDIX): _Implements MDIX via software (so you don't need to use a crossover cable). Media Access Control (MAC) address tables: A table used internally by layer 2 devices, which links MAC addresses to physical ports/interfaces. Power over Ethernet (PoE)/Power over Ethernet plus (PoE+): Self explanatory. The + version increases the wattage. Spanning Tree Protocol: No TTL for Ethernet frames - only IP packets - so loops can occur in switches and other layer 2 devices. STP identifies whether a loop would be created with the devices current configuration. Carrier Sense Multiple Access with Collision Detection (CSMA/CD): On networks with multiple devices, CSMA/CD defers data transmission until no other devices are transmitting when a collision is detected. Jams all traffic and each device begins to retransmit after a random time. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 24/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Address Resolution Protocol (ARP): A protocol for retrieving MAC addresses via IP addresses. Neigbhour Discovery Protocol (NDP): IPv6 version of ARP. 2.4 Given a scenario, install and configure the appropriate wireless standards and technologies. 802.11 Standards: 802.11 == WiFi a: 1999, 5GHz, 54Mbps, 20MHz. b: 1999, 2.4GHz, 11Mbps, 20MHz. g: 2003, 2.4GHz, 54Mbps, 20MHz. n (WiFi 4): 2009, 2.4GHz/5GHz, 150Mbps/600MBps, 4 x MIMO, 20/40/80MHz. ac (WiFi 5): 2014, 5GHz, 857Mbps/6.9Gbps, 8 x DL MU-MIMO, 20/40/80/80+80/160MHz. ax (WiFi 6): 2021, 2.4GHz/5GHz, 1201Mbps/9.6Gbps, 8 x bi-directional MU-MIMO, 20/40/80/80+80/160MHz. Frequencies and range 2.4GHz: Better range. 5GHz: More bandwidth. Channels: Groups of frequencies, some overlap. Channel width can be 20MHz, 40MHz, 80MHz, or 160MHz. Channel bonding: Combining two adjacent wireless channels to increase bandwidth/throughput. SSID (Service Set Identifier) Basic service set: MAC address of SSID. Extended service set: One SSID across multiple WAPs. Independent basic service set (ad-hoc): No AP required. Antenna types Omni: Signal is distributed on all sides. Common. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 25/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Directional: Signal is distributed in a single direction. Provides increased signal distance. Encryption standards WiFi Protected Access (WPA): 2002. Replaced WEP. Every packet gets a 128 bit encryption key. WiFi Protected Access 2 (WPA2): 2004. WiFi Protected Access 3 (WPA3): 2018. Cellular technologies Code Division Multiple Access (CDMA): Each call used a different code, which were used to filter the calls on the receiving side. Global System for Mobile Communications (GSM): Had 90% of the market and worldwide coverage. Used multiplexing. 3G: 1998. Several Mbps. 4G/LTE: 150Mbps. LTE Advanced (LTE-A) increased this to 300Mbps. 5G: 2020. 100 - 900Mbps. Will eventually reach 10Gbps. Multiple Input, Multiple Output (MIMO) and Multi User MIMO (MU-MIMO): MIMO enables multiple streams of traffic to be transmitted. MU-MIMO enables dedicated streams per device(?). 3.0 Network Operations 3.1 Given a scenario, use the appropriate statistics and sensors to ensure network availability. Performance metrics/sensors Device/chassis https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 26/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Temperature: Self explanatory. CPU usage: Self explanatory. Memory: Self explanatory. Network metrics Bandwidth: The rate of data transfer. Latency: Delay between request and response. Jitter: Time between frames i.e. in video calls. SNMP: Simple Network Management Protocol is an Internet Standard protocol used to monitor and manage the network devices connected over an IP. Different devices like routers, switches, firewalls, load balancers, servers, CCTV cameras, and wireless devices communicate using SNMP. Traps: Network device self monitors/gathers its own SNMP data (rather than having to be constantly be polled by a remote workstation). The data on the device is sent to a remote workstation when a certain event occurs, or when data gathered reaches a certain threshold. Object Identifiers (OIDs): Object Identifier. This is the data contained within the MIBs. Management Information Bases (MIBs): A database of statistics contained within network infrastructure/devices. Network device logs Log reviews Traffic logs Audit logs Syslog: A standard protocol for message logging. Logs from multiple sources are consolidated and organised. Logging levels/severity levels: Not all logs have the same priority i.e. debug and general information vs high level critical alerts. Configurable. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 27/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Interface statistics/status Link state (up/down) Speed/duplex Send/receive traffic Cyclic Redundancy Checks (CRCs) Protocol packet and byte counts Interface errors or alerts CRC errors: Cyclic Redundancy Check error - occur when Ethernet frames are corrupted. Giants: A frame larger than 1518 bytes (unless using jumbo frames, which can be up to 9000 bytes). Runts: An Ethernet frame smaller than the minimum size (64 bytes). Encapsulation errors: Occur when Ethernet frames that use incompatible encapsulation methods are transferred between devices. Environmental factors and sensors: Self explanatory. Temperature: Self explanatory. Humidity: Self explanatory. Electrical: Self explanatory. Flooding: Self explanatory. Baselines: A standard level of performance for a network used as something to compare to when trying to identify errors or other patterns in network performance. NetFlow data: A standard statistics collection method that involves a probe (a device within the network) and collector (a device that receives the information from the probe). Uptime/downtime: A useful data point for troubleshooting. Defines whether a service/interface is up or down (and for how long). https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 28/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 3.2 Explain the purpose of organisational documents and policies. Plans and procedures Change management: A formal plan regarding how to make a change to network. Incident response plan: A formal plan regarding what to do if a certain type of incident occurs i.e. security incident. Disaster recovery plan: A formal plan regarding what to do if a disaster occurs. System life cycle: A plan for physical asset disposal. Standard operating procedures: Documentation for standard procedures such as infrastructure downtime, software upgrades etc. Hardening and security policies Password policy: The policy defining minimum password requirements. Acceptable use policy: Defines acceptable use of company assets. Bring your own device (BYOD) policy: Defines whether or not employees can bring/use their own device rather than a device provided by the company. Remote access policy: Documents security methods required to be in place when requiring internal resources from a remote location. Onboarding and offboarding policy: Policies defining how onboarding new employees and terminating current employees should take place. Security policy: Details all of the policies and procedures regarding security. Contains many other policies. Data loss prevention: Policies defining how sensitive data is transferred to/from/within a network. Common documentation https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 29/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Physical network diagram: A diagram showing all network devices and how they are interconnected. Floor plan: Shows the wired and wireless networks within a building, including access points and cabling. Rack diagram: A logical diagram showing the devices and layout of a rack. Intermediate Distribution Frame (IDF)/Main Distribution Frame (MDF) documentation: The documenting of the layout of IDFs/MDFs. Logical network diagram: A diagram showing the devices and layout of a network. Wiring diagram: Self explanatory. Site survey report Audit and assessment report: A report, following an audit, to validate existing security policies. Baseline configurations: A measure of "performance" over time. Ambiguous. Common agreements Non Disclosure Agreement (NDA): Agreement between parties that certain information will remain undisclosed. Service Level Agreement (SLA): The minimum terms for services provided between parties (usually between customers and service providers). Memorandum Of Understanding (MOU): Expresses a convergence of will between two or more parties, indicating an intended common line of action. Not a contract. 3.3 Explain high availability and disaster recovery concepts and summarise which is the best solution. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 30/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Load balancing: Service load is shared among components. If a component fails or the load is too high, the service is able distributed from the remaining components. Multipathing: Multiple NICs in a server, each connecting to their own router/switch to provide redundancy. NIC teaming: Multiple NICs in a server, however the server as a whole appears as a single NIC. Redundant hardware/clusters: Having more than one of each component in the network (i.e. switches, routers, firewalls), so that if one device fails, an alternate can be switched to (usually automatically). Switches Routers Firewalls Facilities and infrastructure support Uninterruptible Power Supply (UPS): A battery that sits between equipment and the mains power, allowing devices to stay powered for a short time if there is a blackout. Power Distribution Units (PDUs): A device with multiple power outlets. Some have network connectivity. Generator: Self explanatory. HVAC: Self explanatory. Fire suppression: Self explanatory. Redundancy and High Availability (HA) concepts Cold site: An empty building/warehouse. Warm site: A datacenter with empty racks. BYO hardware. Hot site: A (managed?) datacenter used for backups, usually with a 1:1 copy of hardware and data as the main hardware/data. Cloud site: Using a cloud provider for typical datacenter services.. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 31/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Active-active vs active-passive: Having two devices synchronised, for redundancy. AA: two devices, synchronised, used simultaneously; AP: two devices, synchronised, with only one device in use at a time. Multiple ISPs/diverse paths: Multiple paths to and from a destination. Involves advanced dynamic routing protocols. Virtual Router Redundancy Protocol (VRRP)/First Hop Redundancy Protocol (FHRP): VRRP: A virtual IP that points to the router. If the router fails, the IP shifts to the next available router. The host/workstation uses the same IP to reach the router and to it, it appears nothing has changed. FHRP: Configuration of multiple routers to provide redundancy for the first hop. If a router fails, functionality is provided by an alternate default gateway. Meant Time to Repair (MTR): How long is required to fix a certain issue? Mean Time Between Failure (MTBF): Self explanatory. Recovery Point Objective (RPO): How much data needs to be available, before the service/system can be classified as "normal" or "available" or "back up and running". Network device backup/restore: Self explanatory. State: The state of the network device. Configuration: The configuration of the network device. 4.0 Network Security https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 32/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 4.1 Explain common security concepts. Confidentiality, Integrity, Availability (CIA) Confidentiality: Ensuring information is only available to certain people. Integrity: Ensuring data is transferred/stored unmodified. Availability: Ensuring access to information is available. Threats: People who have the ability to exploit systems. Internal: Threats from people who are authorised/have access to systems (i.e. employees). External: Threats from people who are not authorised/do not have access to the system (i.e. not employees). Vulnerabilities Common Vulnerabilities and Exposures (CVEs): A database of known exploits and vulnerabilities. Zero days: Yet to be published vulnerabilities. Exploits: Taking advantage of vulnerabilities. Least privilege: Granting all users the minimal amount of privileges needed to do their job properly. Role-based access: People are granted a set of permissions according to their position in the organisation i.e. manager, team leader etc. Zero trust: Every device, for every user, has to be authorised and approved before gaining access to internal resources (every time). Defense in depth Network segmentation enforcement: Seperation of networks, to ensure that no single person is able to access the whole network and all devices on it. Screened subnet/DMZ: A portion of the network configured for public access. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 33/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Separation of duties: Ensuring that no single person has "all" of the (security relevant) knowledge. Network Access Control (NAC): IEEE 802.1X. RADIUS/EAP. No network communication until authorised and authenticated (logged-in). Honeypot: Something designed to attract bad actors. Authentication methods Multifactor: Multiple methods of authentication required. Terminal Access Controller Access Control System Plus (TACACS+): An old remote authentication protocol. Generally used for network devices. Single Sign On (SSO): Single sign-on is an authentication scheme that allows a user to log in with a single ID to any of several related, yet independent, software systems. True single sign-on allows the user to log in once and access services without re-entering authentication factors. Remote Authentication Dial In User Service (RADIUS): Provides a centralised server-based database of user authentication details. Versatile. LDAP: A protocol for reading and writing directories over a network. Kerberos: Authenticate once, trusted by the entire system. Local authentication: Authentication credentials are stored on the local device. Manual and cumbersome but reliable. 802.1X: See Network Access Control (NAC). Extensible Authentication Protocol (EAP): An authentication framework, comes in many flavours, tightly integrated with IEEE 802.1X. Risk management Security risk assessments https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 34/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Threat assessment: Researching potential threats. Vulnerability assessment: Minimally invasive tests to compare your system/network with a set of known vulnerabilities. Penetration testing: Attempting to actively exploit any vulnerabilities within a system/network. Posture assessment: Ensuring a set of requirements are met before a device is authorised to interact with the network. Business risk assessments Process assessment Vendor assessment: Assessing the risk of data sharing with vendors/service providers. Security Information and Event Management (SIEM): A centralised (documentation) database in which all security events and information is recorded. 4.2 Compare and contrast common types of attacks. Technology based Denial of Service (DOS)/Distributed Denial of Service (DDOS): Forcing a service to fail, usually by overloading a server with traffic. Botnet/command and control: A botnet is a system being maliciously controlled. They are controlled from centralised servers called command & control servers. On path attack/Man In The Middle (MITM): An attacker sits between a user and a web service, intercepting traffic. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 35/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 DNS poisoning: If you can modify the DNS server, or the client host file, or send fake DNS responses, you can redirect traffic to wherever you like (rather than from where it was originally requested). VLAN hopping: Hopping onto an alternate VLAN on a network segmented by VLANs.i Done by either pretending to be a trunk connection, or encapsulating a second VLAN tag within the "actual/legitimate" VLAN tag (double tagging). ARP spoofing: Hijacking the ARP procedure in order to have a certain device appear as another device on the local network. Synonymous with IP spoofing. Rogue DHCP: A malicious DHCP server, overriding the legitimate DHCP server. DHCP snooping can be activated at the switch to prevent this. Rogue AP: Unauthorised WAP. Can be used for MITM attacks. Evil twin: A malicious wireless access point with a similar SSID to a legitimate network. Ransomware: Software that encrypts your files. The distributor of the software usually requests payment to unencrypt the data. Password attacks Bruteforce: A known hash is compared with the hashes of many possible iterations of passwords, until a hash is found. Dictionary: The same as a bruteforce/hash attack, but uses words from the dictionary rather than every single possible iteration of characters. MAC spoofing: MAC addresses can be changed. IP spoofing: See ARP spoofing. Deauthentication: A DoS attack which prevents users from connecting to a wireless network. aircrack-ng. Malware: Malicious software. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 36/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Human and environmental Social engineering Phishing: The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers. Tailgating: When an authorised person allows an unauthorised person to access a restricted (physical) location i.e. through a locked door. Piggybacking: The same as tailgating, but with permission from the authorised person. Shoulder surfing: Someone looking at your monitor over your shoulder. 4.3 Given a scenario, apply network hardening techniques. Best practices Secure SNMP: SNMPv1 & SNMPv2 do not use encryption. Use SNMPv3. Router Advertisement (RA) Guard: IPv6 routers periodically announce their presence. A malicious actor could pretend to be a router, opening up vulnerabilities. Switches can limit RA messages to certain devices. Port security: A MAC address whitelist for switches. Only authorised devices are given access to the network. Dynamic ARP inspection: Inspection of ARP packets to prevent ARP poisoning at the switch level. Control plane policing: Protection of the control plane in switches via firewall utilities and rate limiting. Private VLANs: The limiting or prevention of access between devices on a VLAN. Used often in public https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 37/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 networks. Disable unneeded switchports: It's best practice to administratively disable unused interfaces/switch ports. Disable unneeded network devices: Self explanatory. Change default passwords: Self explanatory. Password complexity/length: Self explanatory. Enable DHCP snooping: DHCP is inherently insecure and unencrypted. Switches can use DHCP snooping to essentially act as a DHCP firewall, managing the DHCP connections. Change default VLAN: Separate user traffic from administrative traffic. Patch and firmware management: Self explanatory. Keep firmware updated. Access Control List (ACL): Allow or disallow network traffic based on things such as source IP, destination IP, port number, time of day, application etc. Role-based access: Define network access permissions based on role in the workplace. Firewall rules Explicit deny: Explicitly denying traffic based on certain criteria (see ACL above). Implicit deny: If traffic isn't explicitly allowed, it's implicitly denied. Wireless security MAC filtering: Traffic filtering based on MAC address. Self explanatory. Not that secure because MAC addresses can be changed. Antenna placement: Limit who can connect to a network by limiting number of WAPs and placing them strategically. Power levels: Limit transmission signal strength to minimum viable amount. RSSI (receive)/EIRP (transmit). https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 38/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Wireless client isolation: Devices connected to a wireless network are isolated and cannot interact with each other. Guest network isolation: A network which can reach the internet, but no access to internal resources. Preshared keys (PSKs): A key that can be distributed, that is used to access a wireless network (rather than using a password). Extensible Authentication Protocol (EAP): An authentication framework with different implementations. Typically, users authenticate against a database with credentials individual to them (i.e. RADIUS). Geofencing: Restricting access to a wireless network depending on the users physical location. Captive portal: A portal requiring authentication before full network access is granted. IoT access considerations: It's best practice to put IoT devices on a separate network. 4.4 Compare and contrast remote access methods and security implications. Site to site VPN: Direct network connectivity between sites in different locations. Client to site VPN: Access to a network, from remote device/client. Traffic is encrypted. Clientless VPN: Connecting to a VPN without client side software i.e. via a web browser. Split tunnel vs full tunnel: Full tunnel: all traffic flows through the VPN endpoint; Split tunnel: only traffic destined for the private network connected to the VPN will travel through the VPN connnection - regular internet traffic will not use the VPN connection. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 39/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Remote desktop connection: Access a desktop environment remotely. VNC/RDP. Remote desktop gateway: A centralised gateway, requiring authentication, granting access to multiple remote desktop connections. SSH: Encrypted remote shell access. Virtual Network Computing (VNC): A remote desktop protocol. Virtual desktop: A desktop where the hardware is in a different physical location to the user/workstation. In band vs out of band management: Out of band management is an alternate way to interface with network devices that does not require an internet connection i.e. via a serial cable. 4.5 Explain the importance of physical security. Detection methods Camera: Self explanatory. Motion detection: Self explanatory. Asset tags: The attachment of serialised tags to your devices. Tamper detection: Sensors that detect whether hardware has been tampered with i.e. case opened in UEFI. Prevention methods Employee training: Train your employees to snitch on imposters. Access control hardware: Self explanatory. Badge readers: Self explanatory. Biometrics: Self explanatory. Locking racks: Self explanatory. Locking cabinets: Self explanatory. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 40/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Access control vestibule: Multiple doors in a row, only one can be unlocked at a time, prevents tailgating. Smart lockers: AusPost Parcel Lockers. Asset disposal Factory reset/wipe configuration: Self explanatory. Sanitise devices for disposal: Self explanatory. 5.0 Network Troubleshooting 5.1 Explain the network troubleshooting methodology. Identify the problem Gather information Question users Identify symptoms Determine if anything has changed Duplicate the problem, if possible Approach multiple problems individually Establish a theory of probably cause Question the obvious Consider multiple approaches Top to bottom/bottom to top OSI model Divide and conquer Test the theory to determine the cause If the theory is confirmed, determine the next steps to resolve the problem If the theory is not confirmed reestablish a new theory https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 41/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Establish a plan of action to resolve the problem and identify potential effects Implement the solution or escalate as necessary Verify full system functionality and, if applicable, implement preventative measures Document findings, actions, outcomes, and lessons learned 5.2 Given a scenario, troubleshoot common cable connectivity issues and select the appropriate tools. Specifications and limitations Throughput: Maximum data rate. Speed: Maximum data rate. Distance: Maximum distance of cable type. Cable considerations Shielded and unshielded: Shielding prevents electromagnetic interferences. S = shielded, U = unshielded, F = foil shielding Plenum and riser-rated: Plenum rated cable doesn't use PVC (or uses less toxic PVC), so as the be safer if a fire occurs. Cable application Rollover cable/console cable: DB9 connectors. Usually used for configuring network devices (these days). Crossover cable: Used to communicate directly between NICs (without having a router between devices). PoE: Power over Ethernet. Common issues Attenuation: The diminishing of signal strength over distance. Interference: Self explanatory. EMI. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 42/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Decibel loss: See attenuation. Incorrect pinout: Self explanatory. A cable tester can diagnose pinout issues. Bad ports: Refers to physical (RJ45) ports/interfaces. Open/short: Open circuit/short circuit. LED status indicators: Indicate connectivity. Incorrect transceivers: Important to match single mode/multi mode receivers when using fibre. Different light wavelengths also use different transceivers. Duplexing issues: TX & RX should be set to the same duplex configuration to prevent issues. TX/RX reversed: Self explanatory. Dirty optical cables: Self explanatory. Common tools Cable crimper: Crimps connectors to twisted pair cables. Punchdown tool: Used for punching down cables into wiring blocks. Tone generator: Generates a tone at one end of a wire, to help identify where the other end of the wire terminates. Loopback adapter: Loop an output back into an input on the same device. Used for testing physical ports. Optical Time Domain Reflectometer (OTDR): Use to estimate cable lengths, check impedance and identify breaks or splices in the cable. Multimeter: Used to check voltage. Cable tester: Tests a cable to make sure its able to transmit data and that the pinout is correct. Wire map Tap: Used to duplicate packet capture - similar to a hub. Fusion splicers: Allows two separate fibre cables to be connected together permanently. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 43/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Spectrum analysers: Analyses wireless frequency spectrums. Snips/cutters: Self explanatory. 5.3 Given a scenario, use the appropriate network software tools and commands. Software tools WiFi analyser: Provides the ability to capture and analyse WiFi network info/packets. Protocol analyser/packet capture: WireShark. Bandwidth speed tester: Speed test websites. Port scanner: Software to scan a network for IP addresses and open ports. nmap. iperf: Bandwidth tester. NetFlow analysers: Allows the gathering of network/traffic statistics from NetFlow probes that have been installed on the network. Trivial File Transfer Protocol (TFTP) server: A bare minimum file transfer protocol. Terminal emulator: Self explanatory. IP scanner: Software to scan a network for IP addresses and open ports. nmap. Command line tool ping: Test reachability via ICMP and shows round-trip time. ipconfig/ifconfig/ip: IP/interface information. nslookup/dig: Lookup information from DNS servers. nslookup has been deprecated in favour of dig. traceroute/tracert: Determines the route a packet takes to a destination. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 44/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 arp: Used to grab MAC addresses known by the local machine. 'arp -a' to view the ARP cache. netstat: Displays local TCP connections, routing tables, and other statistics. hostname: Shows the FQDN and IP address of the device in use. route: Shows the devices routing table. netstat -r on macOS. telnet: Unencrypted text based remote communication. Useful for checking whether a port is open. tcpdump: Used to capture packets. nmap: Port scanner. Basic network platform commands show interface: Show the interfaces on a device. show config: Show the device configuration. show route: Show the devices routing table. 5.4 Given a scenario, troubleshoot common wireless connectivity issues. Specifications and limitations Throughput: Maximum data rate. Speed: Maximum data rate. Distance: Receivers distance from the access point. Received Signal Strength Indication (RSSI) signal strength: The strength of the received signal. Effective Isotropic Radiated Power (EIRP)/power settings: The strength of the transmitted signal. Considerations Antennas Placement: Where are the antennas? https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 45/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Type: Is it omnidirectional or unidirectional? Polarisation: The orientation of the antenna in relation to the earth i.e. horizontal or vertical. TX & RX should have the same orientation. Channel utilisation: If there are many users on a single wireless channel, traffic congestion can occur. AP association time: The time it takes for a device to associate with an access point. Site survey: Determine the wireless equipment and usage in a certain area. Common issues Interference: Channel overlap: If a channel on one access point overlaps with the bandwidth being used on another wireless device in the same area, interference will occur. Antenna cable attenuation/signal loss: Attenuation that occurs between the wireless access point and the switch or other device. RF attenuation/signal loss: The further away you are from the antenna, the weaker the signal will become. Wrong SSID: Self explanatory. Incorrect passphrase: Self explanatory. Encryption protocol mismatch: Self explanatory. Insufficient wireless coverage: Self explanatory. Captive portal issues: Occur when user reaches data limit, or exceeds allowed timeframe. Client disassociation issues: A DOS attack that prevents legitimate users from connecting to wireless networks. 5.5 Given a scenario, troubleshoot general networking issues. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 46/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 Considerations Device configuration review: Self explanatory. Routing tables: If set incorrectly, traffic won't be routed properly. Interface status: Individual interfaces have their own settings and statuses. VLAN assignment: Is the device connected to the right VLAN? Network performance baselines: Gathering information about the baseline network performance can help identify trends and issues in network performance. Common issues Collisions: Two devices trying to communicate at the same time. Occurs by default on half-duplex networks/devices such as hubs. Broadcast storm: Large numbers of broadcasts can cause performance issues. Duplicate MAC address: Will cause issues. Unlikely to occur. Duplicate IP address: Usually occur only when IP addresses have been set statically, or when there are multiple DHCP servers on the same LAN. Multicast flooding: If multicast is incorrectly configured, multicast will flood all devices i.e. like a broadcast. Asymmetrical routing: When packets take a different route on their transmitting/receiving paths. Can cause issues with NAT & firewalls. Switching loops: When switches create a loop on the network that constantly sends traffic back and forth between two switches (i.e. causing an infinite loop). No TTL with Layer 2 communications to prevent this.. Routing loops: A loop between routers: Router A has the next hop set to Router B, and Router B has the next https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 47/48 9/20/22, 1:21 PM CompTIA Network+ N10-008 hop set to Router A. Rogue DHCP server: DHCP is insecure, anyone can spin up a DHCP server and start handing out IPs. IP settings issues Incorrect gateway Incorrect subnet mask Incorrect IP address Incorrect DNS Missing route: No next hop or default hop is set in the routing table. Low optical link budget: Lack of light on fibre connections. Occurs when distances are too great, or when there is an issue with the connectors. Certificate issues: Certs may be expired, or the certificate may be linked to the wrong domain name. Certs will be invalid if the date & time is wrong on your system. Hardware failure: Self explanatory. Host-based/network-based firewall settings: Self explanatory. Blocked services, ports, or addresses: Self explanatory. Incorrect VLAN: Self explanatory. DNS issues: No URLs will resolve. NTP issues: If times are wrong, or unsynchronised between client & server, many things will fail. BYOD challenges: Difficult to secure. Use MDM. Licensed feature issues: Software licences may not be maintained during nuke & paves. Network performance issues: Many factors. https://duncanbennie.com/comptia-network-n10-008-study-notes/html/CompTIA Network+ N10-008.html#5.0 Network Troubleshooting-5.4 Given a … 48/48