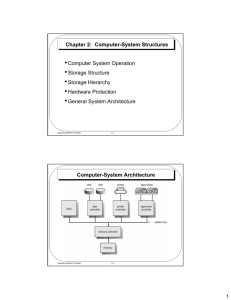
Operating Systems Designed and Presented by Dr. Ayman Elshenawy Elsefy Dept. of Systems & Computer Eng.. AL-AZHAR University Website : eaymanelshenawy.wordpress.com Email : eaymanelshenawy@Azhar.edu.eg eaymanelshenawy@yahoo.com Operating Systems 1.1 Operating Systems Reference Operating System Concepts, ABRAHAM SILBERSCHATZ Part 1: Overview of Operating system Chapter 1: Introduction What Operating Systems Do Computer-System Organization Computer-System Architecture Operating-System Structure Operating-System Operations Process Management Memory Management Storage Management Protection and Security Distributed Systems Special-Purpose Systems Computing Environments Open-Source Operating Systems Computer System Organization Computer system consists of: One or more CPU’s. A set of device controllers (disk drives, audio devices,…) connected through a common bus with a shared memory. The CPU and device controllers can execute concurrently competing for memory cycles. A memory controller synchronize access to the shared memory in ordered way. Computer System Structure divided into four components Users: People, machines, other computers Application & system programs – how system resources are used to solve the computing problems of the users (Word processors,…) Operating system: Controls and coordinates HW among various applications and users Hardware: basic computing resources ( CPU, memory, I/O devices) Computer System Structure Hardware: CPU, memory, and I/O devices provides the basic computing resources for the system. Application Programs: Word processors, Spreadsheets, compilers, and Web browsers. Define the ways in which these resources are used to solve users’ computing problems. Operating System: Support complex games, business applications, and everything in between. Controls the hardware and coordinates its use among the various application programs for the various users. Like a government, it performs no useful function by itself. It simply provides an environment within which other programs can do useful work. What is an Operating System? A program that: mange computer Hardware. The basis for Application programs. Intermediate between user applications and computer H.W. Mainframe OS: Are designed primarily to optimize HW utilization. Personal computer (PC) OS: Support complex games, business applications, and everything in between. Mobile computers: Provide an environment in which a user can easily interface with the computer to execute programs. OS are designed to be convenient, efficient, and some combination of the two. What is an Operating System? OS Consists of. Kernel A program run at all times on the computer. Systems programs are associated with the OS but are not part of the kernel (run as needed). Application programs, all programs not associated with the operation of the system.) OS goals: Execute user programs. Solve user problems in easy form. Make the computer system convenient to use. Use the computer hardware in an efficient manner. Operating Systems Role- User View Maximize Performance (ease of use), and resource utilization according to the interface being used. PC computer systems users need to: Maximize the performance Don’t care about resource utilization. Mainframe and Minicomputers: Maximize resource utilization. Dedicated systems (workstations) have dedicated resources but frequently use shared resources from servers, files , printers ( usability & resources Utilization) Mobile Devices: users are used touch screens embedded computers (No user interface): devices and automobiles (no user interaction, and no resource sharing) Operating Systems Role- System View OS as a Resource allocator: Manage computer resources (CPU time, memory space, file storage space, I/O devices, ….) to solve problems. OS acts as a manger for these resources. Solve conflict requests for resources, decide how to allocate them to specific programs and users ( efficiently and fairly). OS as a Control Program manages the execution of user programs prevent errors and improper use of the computer. Concerned with the operation and control of I/O devices. Computer-System Operation When the computer is powered on or rebooted it must have a bootstrap program (initial Program) to start working. Bootstrap Program: A simple program, stored in (ROM/EEPROM), known by firmware, within the computer HW. Initialize all the system, from CPU registers to device controllers to memory contents. Locate the OS Kernel and load it into the memory. Start providing services to the systems and users ( System Process or System Daemons) Know how to execute the first process, such as “init” in Unix. Waits for some event to occur Hardware Software Each Interrupt: I/O device sending signals to CPU. Interrupt: (special operation called a system call/ Monitor Call). computer design has its own interrupt mechanism, but several functions are common. Computer-System Operation What is happened when the CPU is interrupted? It stops what it is doing and immediately. Execute the Interrupt Service Routine (ISR), using the memory address in Interrupt Vector Table (IVT) for each interrupt type. After executing of ISR, the CPU resumes the computation. Common Functions of Interrupts Interrupt transfers control to the ISR through the interrupt vector, which contains the addresses of all the service routines Interrupt architecture must save the address of the interrupted instruction Incoming interrupts are disabled while another interrupt is being processed to prevent a lost interrupt A trap is a software-generated interrupt caused either by an error or a user request An OS is interrupt driven Storage Structure –Main Memory The CPU can load instructions only from memory. Memory consists an array of words with addresses. The CPU execute programs that located in main memory (RAM): RAM is implemented in a semiconductor technology called dynamic random-access memory (DRAM).. too small to store all needed programs Volatile : loses its contents when power is turned off or otherwise lost Bootstrap program is typically stored in ROM or EEPROM. ROM used to store static programs that cannot be changed (game cartridges, manufacturers can distribute games that cannot be modified). EEPROM cannot be changed frequently and so contains mostly static programs (smartphones store their factory setting). The load instruction and store instruction moves a word from/to main memory and the internal register within the CPU. Computer Memory • Computers use many different types of memory to hold data and programs. ▪ Semi-conductor Memories ▪ magnetic disks, USB sticks, DVDs etc.) • Each type has its own characteristics and uses. • Common types of memory: ▪ ▪ ▪ ▪ read-only memory (ROM) flash memory (EEPROM) static random access memory (SRAM) dynamic random access memory (DRAM). Storage Structure –Secondary Memory An extension of main memory. Able to hold large quantities of data permanently. magnetic disk, Provides storage for both: Programs Data (system and application). until they are loaded into memory. Many programs then use the disk as both the source and the destination of their processing. Hence, the Disk management of disk storage is very important. Solid-state disks & Flash Memories: Are faster than magnetic disks Nonvolatile. If external power is interrupted, this solid-state disk’s controller copies the data from RAM to the magnetic disk. Memory Hierarchy • A computer have wide variety of storage systems (memory) can be organized in a hierarchy (memory hierarchy) Rang from fast, expensive internal registers, to slow, inexpensive Hard Magnetic Disks. • They are differ in speed, cost, size, volatility. • Registers are: • Matched in speed to the CPU • Consume a significant amount of power. • Only a small number of registers in a processor (More expensive). • Secondary storage: • such as hard magnetic disks. • Small cost per stored bit is in terms of money and electrical power. • Access time is very long when compared with registers. • Between the registers and secondary storage • There are a number of other forms of memory that bridge the gap between the two. Memory Hierarchy • The memory hierarchy can be characterized by a number of parameters: • Access Type: how physically the memory read/write is done (Random or Sequential). • Capacity measured in bytes or KB, MB, GB or TB. • Cycle time: the time elapsed from the start of a read operation to the start of a next read. • Latency: the time interval between the request for information and the access to the first bit of that information. • Bandwidth: the number of bits that can be accessed per second. • Cost of a memory is usually specified as dollars/MB • Total Cost = cost/MB * Memory Size. Storage-Device Hierarchy I/O Structure Device controller: a specific type of device. seven or more devices can be attached to the small computer-systems interface (SCSI- Small Computer System Interface) controller. Have some local buffer storage & a set of special-purpose registers. Transfer data between the I/O devices and its local buffer. Device Driver: Each OS has a device driver for each device controller. Understands the device controller provide Uniform interface for the device, loads the registers within the device controller. Computer-System Operation- I/O Operation To start an I/O operation: Interrupt Driven I/O The device driver loads the appropriate registers within the device controller. The device controller, examines the contents of these registers to determine what action to take (read a character from the KB). The controller starts the transfer of data from the device to its local buffer. After transferring data, the device controller informs the device driver via an interrupt that it has finished its operation. The device driver then returns control to the OS Interrupt Driven I/O is fine for moving small amount of data. It can produce high overhead. For bulk data or Disk I/O direct memory access (DMA) is used. Computer-System Operation- DMA Direct Memory Access (DMA) used for bulk data movement. After setting up buffers, pointers, and counters for the I/O device, the device controller transfers an entire block of data directly to or from its own buffer storage to memory, with no intervention by the CPU. Only one interrupt is generated per block, to tell the device driver that the operation has completed, While the device controller is performing these operations, the CPU is available to accomplish other work. Computer-System Architecture A computer system can be categorized according to the number of general-purpose processors (CPU’s) used. Single Processor system Multi Processor system Clustered system Single Processor System A system have One general-purpose CPU capable of executing an instruction sets, and user processes. Special-purpose CPU’s that run instruction sets and does not run user process (disk, keyboard, and graphics controllers); Special purpose CPU’s May: – Managed by the OS, For example, PCs contain a CPU in the keyboard to convert the keystrokes into codes to be sent to the CPU. – Not Managed by the OS: a low-level components built into the HW. The OS cannot communicate with it; they do their jobs autonomously. The use of special-purpose CPU is common and does not turn a single-processor system into a multiprocessor. If there is only one general-purpose CPU, then the system is a single-processor system. Multiple Processor System (Parallel systems) A system have two or more CPU in close communication. Sharing computer bus and sometimes clock, memory, I/O devices, mass storage, and power supplies. advantages: Increased throughput. more work done in less time. Low Cost than equivalent multiple single-processor systems. Increased reliability. the failure of one processor will not halt the system, only slow it down. Increase Addressable memory and computing power. Asymmetric multi-processor: each CPU is assigned to a specific task in a (master –slave relationship). A master CPU controls the system; the other CPU’s wait for the master instructions. Symmetric multiprocessing (SMP), in which each processor performs all tasks within the operating system. Symmetric Multiprocessing Architecture • N processes can run if there are N CPUs. • I/O must be controlled to ensure the data reach the appropriate CPU. • Ensure no CPU is idle while another is overloaded (inefficiencies). • Special hardware or software (written to allow only one master and multiple slaves) can be used to differentiate between symmetric and asymmetric multiprocessing. • Uniform memory access (UMA): access to any RAM from any CPU takes the same amount of time. • Non-uniform memory access (NUMA): some parts of memory may take longer to access than other parts. A Dual-Core Design • Include multiple computing cores on a single chip. In essence, these are multiprocessor chips. • They can be more efficient than multiple chips with single cores (on-chip communication is faster than between-chip communication). • appear to the operating system as N standard processors. Clustered Systems Like multiprocessor systems, but multiple systems working together composed of two or more individual systems or nodes—joined together. Usually sharing storage via a storage-area network (SAN) Provides a high-availability service which survives failures Asymmetric clustering has one machine in hot-standby mode Symmetric clustering has multiple nodes running applications, monitoring each other Some clusters are for high-performance computing (HPC) Applications must be written to use parallelization Operating system Structure – Multi Programming One of the most important aspects of OS. Reasons: A single program cannot, keep either the CPU or the I/O devices busy at all times. Single users frequently have multiple programs running. Multiprogramming: Increases CPU utilization by organizing jobs (code and data). The OS keeps several jobs in memory simultaneously. If main memory is too small to accommodate all jobs, Jobs are kept initially on the disk in a job pool (consists of all processes residing on disk awaiting allocation of main memory). The set of jobs in memory can be a subset of job pool. OS Structure – Multi Programming Eventually, the first job finishes waiting and gets the CPU back. As long as at least one job needs to execute, the CPU is never idle. do not provide for user interaction with the computer system. OS select one job and begins to execute it Job may have to wait for some task, (I/O operation), The OS simply switches to another job. When that job needs to wait, the CPU is switched to another job, and so on. In a non-multi programming system, the CPU would sit idle. Memory Layout for Multiprogrammed System OS Structure- Multi Tasking (Time Sharing) Time sharing is a logical extension of multiprogramming. In time-sharing systems, the CPU executes multiple jobs by switching among them, but the switches occur so frequently that the users can interact with each program while it is running. Time sharing requires an interactive computer system, which provides direct communication between the user and the system. The user gives instructions to the OS using input device (keyboard or mouse), and waits for an output device results. Allows many users to share the computer simultaneously. The system switches rapidly from one user to the next, Each user is given the impression that the entire computer system is dedicated to his use. Time Sharing Requirements Job Scheduling: If several jobs are ready to be brought into memory, and there is no enough room for all of them, then the system must choose among them. Memory Management: When the OS selects a job from the job pool, it loads that job into memory for execution. Having several programs in memory at the same time requires some form of memory management. if several jobs are ready to run at the same time, the system must choose among them. Making this decision is CPU scheduling. Running multiple jobs concurrently requires that they cant affect each other in all phases of the OS, including Process Scheduling, Disk Storage, and Memory Management. ensure reasonable response time through Swapping, in which processes are swapped in and out of main memory to the disk. Virtual Memory, enables users to run programs that are larger than actual physical memory (The execution of a process is not completely in memory) A file system that system resides on a collection of disks; hence, Disk Management must be provided. Provide a mechanism for protecting resources from inappropriate use. provide mechanisms for job synchronization and communication ,and it may ensure that jobs do not get stuck in a deadlock, forever waiting for one another. Operating-System Operations – Interrupt Driven Modern OS are interrupt driven, Waiting for something to happen. Events are almost always signalled by the occurrence of an interrupt or trap or an exception. Trap/Exception is a software-generated interrupt caused either by a specific request from a user program that an OS service be performed or by an error (div. by zero or invalid memory access, request for OS service, infinite loop). For each type of interrupt, separate segments of code in the operating system determine what action should be taken (ISR). An error in a user program could cause problems only for the one program running. An incorrect (or malicious) program cannot cause other programs to execute incorrectly. Dual Mode Operations OS must distinguish between the execution of: OS code ( Kernel mode or supervisor mode, system mode, or privileged mode) User-defined code( User mode ). Mode bit, is added to the hardware of the computer to indicate the current mode: kernel[0]: task that is executed on behalf of the OS. user[1]: task is executed on behalf of the user. When a user application requests a service from the OS (via a system call), it must transition from user to kernel. At system boot time, the hardware starts in kernel mode. The OS is then loaded and starts user applications in user mode. If a trap or interrupt occurs, the HW switches from user mode to kernel mode (changes the state of the mode bit to 0). Thus, whenever the OS gains control of the computer, it is in kernel mode. The system always switches to user mode (by setting the mode bit to 1) before passing control to a user program. Transition from User to Kernel Mode Timer Make the OS must maintains control over the CPU. Prevent a user program to get stuck in an infinite loop or to fail to call system services and never return control to the OS. Can interrupt the computer after a specified period fixed timer (1/60 second) or variable timer (from 1 millisecond to 1 second). The OS sets the counter before transfer the control to the user. Every clock pulse, the counter is decremented. When the counter reaches 0, an interrupt occurs (a 10-bit counter with a 1 ms clock allows interrupts from 1 ms to 1,024 ms, in steps of 1 ms). If the timer interrupts, control transfers automatically to the OS, which may treat the interrupt as a fatal error or may give the program more time. Clearly, instructions that modify the content of the timer are privileged. Process Management A process is a program in execution: A word-processing program being run by an individual user A system task (sending output to a printer). Process needs resources to accomplish its task (CPU, memory, I/O, files, Initialization data (such as file name for printing ) Process termination requires release of any reusable resources Single-threaded process has one program counter specifying location of next instruction to execute instructions sequentially, one at a time, until completion Multi-threaded process has one program counter per thread The OS is responsible for the following activities in connection with process management: Creating and deleting both user and system processes Suspending and resuming processes Providing mechanisms for process synchronization, process communication and deadlock handling Memory Management All data in memory before and after processing All instructions in memory in order to execute Memory management determines what is in memory when Optimizing CPU utilization and computer response to users Memory management activities Keeping track of which memory locations are currently being used and by whom. Deciding which processes (or parts there of) and data to move into and out of memory Allocating and reallocating memory space as needed Storage Management OS provides uniform, logical view of information storage Abstracts physical properties to logical storage unit - file Each medium is controlled by device (i.e., disk drive, tape drive) Varying properties include access speed, capacity, datatransfer rate, access method (sequential or random) File-System management Mass storage management Cashing I/O Systems File System Management Is one of the most visible components of an OS. Computers can store information on several types of physical media ( Magnetic disk, optical disk, and magnetic tape). Each of these media has its own characteristics and physical organization (access speed, capacity, data-transfer rate, and access method (sequential or random)). Each medium is controlled by a device, such as a disk drive or tape drive. A file is: a collection of related information defined by its creator. represent programs and data. Data files may be numeric, alphabetic, alphanumeric, or binary. Files may be free-form (for example, text files), or they may be formatted rigidly (for example, fixed fields). organized into directories to make them easier to use. File System Management When multiple users have access to files, it may be desirable to control by whom and in what ways (for example, read, write, append) files may be accessed. The operating system is responsible for the following activities in connection with file management: Creating and deleting files and directories Manipulate files and directories ( Open, Close , Append , Rename, Print, ….) Mapping files onto secondary storage. Backing up files on stable (nonvolatile) storage media. Mass-Storage Management Main memory are small to hold all data and program and data in main memory are lost when the power is off. Secondary storage are used as a backup for the main memory. Most programs (compilers, assemblers, and word processors) are stored on a disk until loaded into memory and then use the disk as both the source and destination of their processing. The OS is responsible for Free-space management, Storage allocation and Disk scheduling. Files usually organized into directories, Access control systems determines who can access what Some storage need not be fast Tertiary storage includes optical storage, magnetic tape Still must be managed – by OS or applications Varies between WORM (write-once, read-many-times) and RW (read-write) Caching Caching is an important principle of computer systems. Information is normally kept in some storage system (such as main memory). As it is used, it is copied into a faster storage system. When we need a particular piece of information: Check whether it is in the cache. If it is, we use the information directly from the cache; if it is not, we use the information from the source, putting a copy in the cache under the assumption that we will need it again soon. Without this cache, the CPU would have to wait several cycles while an instruction was fetched from main memory. Careful selection of the cache size and of a replacement policy can result in greatly increased performance. Performance of Various Levels of Storage Migration of Integer A from Disk to Register Movement between levels of storage hierarchy can be explicit or implicit I/O Subsystem One purpose of OS is to hide difficulties of HW devices from the user I/O subsystem responsible for Memory management of I/O including: Buffering (storing data temporarily while it is being transferred), Caching (storing parts of data in faster storage for performance), Spooling (the overlapping of output of one job with input of other jobs) General device-driver interface Drivers for specific hardware devices Only the device driver knows the specialization of the specific device to which it is assigned. Protection and Security Protection – a mechanism for controlling access of processes or users to resources defined by the OS memory-addressing hardware ensures that a process can execute only within its own address space. Device-control registers are not accessible to users, an unprotected resource cannot defend against use (or misuse) by an unauthorized or incompetent user. Security – defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service OS generally must distinguish among users, to determine who can do what User identities (user IDs ) name and associated number, one per user User ID then associated with all files, processes of that user to determine access control Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file Privilege escalation allows user to change to effective ID with more rights Kernel Data Structure (OS Implementation) An array: A simple data structure in which each element can be accessed directly. Example, main memory is constructed as an array. If the data item being stored is larger than one byte, ( use multiple bytes number × item size) Variable item Sizes, ????? Linked Lists: the most fundamental data structures in computer science. Each item must be accessed in a particular order. Represents a collection of data values as a sequence. In a singly linked list, each item points to its successor Double linked list, a given item can refer either to its predecessor or to its successor, Circular linked list, the last element in the list refers to the first element, rather than to null, Kernel Data Structure (OS Implementation) Kernel Data Structure (OS Implementation) Stack: A stack is a sequentially ordered data structure that uses the last in, first out (LIFO) principle for adding and removing items The operations for inserting and removing items from a stack are known as push and pop, respectively. Example: OS uses a stack when invoking function calls. Parameters, local variables, and the return address are pushed onto the stack when a function is called; returning from the function call pops those items off the stack. A queue, A sequentially ordered data structure that uses the first in, first out (FIFO) principle. Example: Jobs that are sent to a printer are typically printed in the order in which they were submitted. Tasks that are waiting to be run on an available CPU are often organized in queues. Kernel Data Structure (OS Implementation) Tree: A data structure that can be used to represent data hierarchically linked through parent–child relationships. A parent may have an unlimited number of children (two children for binary tree). Linux uses a balanced binary search tree as part its CPU-scheduling algorithm. Hash Function: A hash function takes data as its input, performs a numeric operation on this data, and returns a numeric value. This numeric value can then be used as an index into a table (typically an array) to quickly retrieve the data. a user enters his user name and password. The hash function is used to retrieve the password. Kernel Data Structure (OS Implementation) Bitmap: A bitmap is a string of n binary digits that can be used to represent the status of n items. Example, suppose we have several resources, and the availability of each resource is indicated by the value of a binary digit: 0 means that the resource is available, while 1 indicates that it is unavailable (or viceversa). The value of the ith position in the bitmap is associated with the ith resource. As an example, consider the bitmap shown below: » 001011101 A medium-sized disk drive might be divided into several thousand individual units, called disk blocks. A bitmap can be used to indicate the availability of each disk block. Distributed Computing – Computer Network Collection of separate, networked together possibly heterogeneous, systems Network is a communications path Networks vary by the protocols used, the distances between nodes, and the transport media, their performance and reliability. – Local Area Network (LAN) room, floor , building. – Wide Area Network (WAN) building, cities , countries – Metropolitan Area Network (MAN) building within a city A network OS provides: File sharing across the network and that includes a communication scheme that allows different processes on different computers to exchange messages. Different OS communicate closely enough to provide the illusion that only a single operating system controls the network. Special-Purpose Systems - RTOS Real-time embedded systems: Embedded computers is a HW device with special purpose OS (car engines and manufacturing robots, microwave ovens, …). Have a specific task. It’s OS provides limited functions It may use a general PC with standard OS to run a special App. Have little or no user interface. HW device with App Specific Integrated Circuits (ASIC) A real-time system is often used as a control device in a dedicated application. Sensors The bring data to the computer. computer must analyze the data and possibly adjust controls to modify the sensor inputs. Special-Purpose Systems – Multimedia Systems Most OS’s are designed to handle: Conventional data (text files, programs, word documents, and spreadsheets) Multimedia data (audio and video files, video frames). These data must be delivered (streamed) according to certain time restrictions ( 30 f/s). Multimedia systems: A wide range of applications that include audio files such as MP3, DVD movies, video conferencing, and short video clips of movie, live webcasts (broadcasting over the Web) of speeches or sporting events and even live webcams. Includes a combination of audio and video. For example, a movie may consist of separate audio and video tracks. Exist in desktop PC’s. PDAs and cellular telephones. Special-Purpose Systems - Handheld systems Personal digital assistants (PDAs), and cellular telephones use special-purpose embedded OS. Developers of handheld systems and applications face many challenges due to the limited size of these devices: Size, most handheld devices have small amounts of memory, slow processors, and small display. CPU’s for most handheld devices run at a fraction of the speed of a CPU in a PC (consume less power, have no large battery). A lack of physical space limits input methods to small KB, handwriting recognition, or small screen-based KB’s. The small display screens limit output options (3 inch square). Web clipping, only a small subset of a Web page is delivered and displayed on the handheld device. use wireless technology, such as Bluetooth, allowing remote access to e-mail and Web browsing. Computing Environments How computer-system organization and major OS’s components are used in a variety of computing environments. Traditional Computing Client server computing Peer to Peer computing Web Based Computing Computing Environments Traditional Computing ( an office) Consists of PCs connected to a network, with servers providing file and print services. Remote access desktop. Terminals attached to mainframes. Portability was achieved by use of Laptop computers. Web technology resizes the boundary. Portals, provide Web accessibility to their internal servers. Network computers are essentially terminals that understand Web-based computing. Handheld PDAs can also connect to wireless networks to use the company’s Web portal Home computers serve up Web pages and run networks that include printers, client PCs, and servers. Firewalls to protect their networks from security warms. Computing Environments : Mobile Computing Refers to computing on handheld smartphones and tablet computers. Portable and lightweight, Rich functionality that is either unavailable or impractical on a desktop or laptop computer. Are used for e-mail, web browsing ,playing music and video, reading digital books, taking photos, and recording HD Video, playing games. Developers are now designing mobile APPS: Use GPS chips, accelerometers, and gyroscopes. An embedded GPS chip allows a mobile device to use satellites to determine its precise location on earth. GPS is useful in designing navigation applications (telling users which way to walk or drive or perhaps directing them to nearby services, such as restaurants). An accelerometer allows a mobile device to detect its orientation with respect to the ground and to detect certain other forces, such as tilting and shaking. Two OS dominate mobile computing: Apple iOS (run on Apple iPhone and iPad mobile devices.) Computing Environments : Distributed Systems A distributed system is a collection of physically separate, possibly heterogeneous, computer systems that are networked to provide users with access to the various resources that the system maintains. Increases computation speed, functionality, data availability, and reliability. Some OS generalize network access as a form of file access, with the details of networking contained in the network interface’s device driver. Others make users specifically invoke network functions. Generally, systems contain a mix of the two modes—for example FTP. Computing Environments : Client-Server Computing A set of PC’s connected to a centralized systems. The centralized system acts as computer servers or file servers to satisfy requests generated by client systems. compute-server system: Provides an interface to a client that can send a request to perform an action (read data); the server executes the action and sends back results to the client. (A server running a database that responds to client requests for data). The file-server system: Provides a file-system interface where clients can create, update, read, and delete files ( Web server delivers files to clients running Web browsers). Computing Environments: Peer to Peer Computing All nodes are identical, and each of them can act as client or server, depend on it have a request or provide a service. Services can be provided by several nodes distributed throughout the network, in client server model a server has a bottleneck. Once a node has joined the network, it can begin providing services to and requesting services from—other nodes in the network. ➢ When a node joins a network, it registers its service with a centralized lookup service on the network. Any node desiring a specific service first contacts this centralized lookup service to determine which node provides the service. ➢ A client peer broadcasting a request for the service to all other nodes in the network. The node (or nodes) providing that service responds to the peer making the request. Computing Environments (Cont.) Web Based Computing Web computing has increased the emphasis on networking. Devices that were not previously networked now include wired or wireless access. Devices that were networked now have faster network connectivity, provided by either improved networking technology, optimized network implementation code, or both. The implementation of Web-based computing has given rise to new categories of devices, such as load balancers, which distribute network connections among a pool of similar servers. Computing Environments (Cont.) Virtualization Virtualization is a technology that allows operating systems to run as applications within other operating systems. Virtualization is one member of a class of software that also includes emulation. Computing Environments (Cont.) Cloud Computing Cloud computing is a type of computing that delivers computing, storage, and even applications as a service across a network. In some ways, it’s a logical extension of virtualization, because it uses virtualization as a base for its functionality. Example, the Amazon Elastic Compute Cloud (EC2) facility has thousands of servers, millions of virtual machines, and petabytes of storage available for use by anyone on the Internet. Users pay per month based on how much of those resources they use. Computing Environments (Cont.) Computing Environments (Cont.) Cloud Computing Public cloud—a cloud available via the Internet to anyone willing to pay for the services Private cloud—a cloud run by a company for that company’s own use Hybrid cloud—a cloud that includes both public and private cloud components Software as a service (SaaS)—one or more applications (such as word processors or spreadsheets) available via the Internet Platform as a service (PaaS)—a software stack ready for application use via the Internet (for example, a database server) Infrastructure as a service (IaaS)—servers or storage available over the Internet (for example, storage available for making backup copies of production data) Open-Source Operating Systems Computer and software companies eventually sought to limit the use of their software to authorized computers and customers by releasing only the binary files compiled from the source code, rather than the source code itself ( to save their ideas from their competitors). Counter to the copy protection and Digital Rights Management (DRM) movement Started by Free Software Foundation (FSF) (encouraging the free exchange of software source code and the free use of that software), which has “copy left” GNU Public License (GPL) Source code can be compiled and deployed to a binary code format to be executed on a system, Reverse Engineering is to reach to the source code from the binary code. Open-Source Operating Systems Open-source OS are those made available in source-code format (Linux is the most famous) rather than as compiled binary code (Closed source) Microsoft Windows is a well-known example of the opposite closed source approach. Benefits : learning operating systems by examining the actual source code. OS can be modified and compiled again (excellent learning tool). Large community of interested programmers who contribute to the code by helping to debug it, analyze it, provide support, and suggest changes. more secure than closed-source code because many more eyes are viewing the code. Any bug can be founded and fixed faster. Linux Operating Systems As an example of an open-source OS. Produced many tools, including compilers, editors, and utilities. Linus Torvalds, released a rudimentary UNIX-like kernel using the GNU compilers and tools and invited contributions worldwide programmers to download the source code, modify it, and submit changes to Torvalds. Releasing updates once a week allowed this so-called Linux operating system to grow rapidly, enhanced by several thousand programmers. The resulting GNU/Linux operating system has hundreds numbers of unique distributions, or custom builds, of the system. Major distributions include RedHat, SUSE, Fedora, Debian, Slackware, and Ubuntu. Distributions vary in function, utility, installed applications, hardware support, user interface, and purpose. For example, RedHat Enterprise Linux is geared to large commercial use. PCLinuxOS is a LiveCD , LiveDVD—an operating system that can be booted and run from a CD-ROM without being installed on a system’s hard disk. Linux Operating Systems Ubuntu Linux. Ubuntu is a popular Linux distribution that comes in a variety of types, including those tuned for desktops, servers, and students. The following steps outline a way to explore the Ubuntu kernel source code on systems that support the free “VMware Player” tool: 1. Download the player from http://www.vmware.com/download/player/ and install it on your system. 2. Download a virtual machine containing Ubuntu. are available from VMware at http://www.vmware.com/appliances/. 3. Boot the virtual machine within VMware Player. 4. Get the source code of the kernel release of interest, such as 2.6, by executing wget http://www.kernel.org/pub/linux/kernel/v2.6/linux2.6.18.1.tar.bz2 within the Ubuntu virtual machine. Uncompress and untar the downloaded file via tar xjf linux2.6.18.1.tar.bz2. Explore the source code of the Ubuntu kernel, which is now in ./linux2.6.18.1. End of Chapter 1