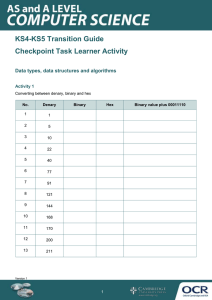
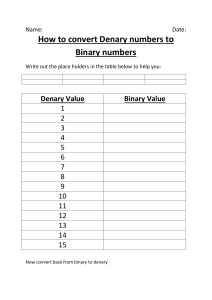
END OF SECOND SEMESTER ASSESSMENET TEST YEAR 7 COMPUTING NAME_________________________________________________________DATE________________ Answer All Questions 1. Many computer systems have an input device and an output device.(8mk) (a) (i) State what is meant by an input device. (ii) Give an example of an input device. (b) (i) State what is meant by an output device. (ii) Give an example of an output device. 2. Choose the most suitable input device for each of the following applications. A different device must be given in each case.(7mk) 3. Eight types of sensor are shown on the left and eight potential sensor applications on the right. Draw lines to connect each sensor to an appropriate application. Only one application can be assigned to each sensor.(8mk) 4. A security system uses three different types of sensor to detect intruders.(3mk) a Name three types of sensor that could be used. 5. Explain the differences between primary memory and secondary storage.(4mk) b In the following table, tick (✓) which description refers to RAM and which refers to ROM. (6mk) 6. (a) Give the denary value of each of the three 12-bit binary values.(6mk) (i) 000000001100 ..................................................................................................................................... (ii) 000011000110 ..................................................................................................................................... (iii) 010011000001 ..................................................................................................................................... (b) Write down the two digits used in the binary number system.(2mk) (c) Write down the eight extra digits used in the decimal system that are not used in binary.(4mk) 7. An electronic guessing game compares denary integer values input by a user with pre-stored values. The pre-stored values are held in 10-bit binary format. (a) Convert the binary values in the table to denary.(6mk) 8. (a) Complete this binary addition: 00101101+ 00100101(show your working) (2mk) (b)Convert all the numbers in the sum in question (a) to decimal. (2mk) 9. a Explain what is meant by a cookie.(2mk) b. Name three types of cookie(3mk) c. Give three uses of cookies.(3mk) 10.Explain what is meant by the following three types of malware. (6mk) i Trojan horse: ii Adware: iii Ransomware: 11.a Explain what is meant by anti-spyware.(2mk) b. Give one similarity and two differences between phishing and pharming.(4mk) Similarity : Difference 1 Difference 2 12.When using the internet it is easy to accidently give your personal details to others. Give two examples of personal data.(2mk) (b) Describe ways of protecting your personal data when using the internet.(4mk) 13.Ocean City is a port which handles a large number of shipping containers. Containers are automatically transferred between ships, storage areas and lorries at the port. The whole system is operated by robots. Discuss the benefits and drawbacks of using robots in this type of operation. (4mk)