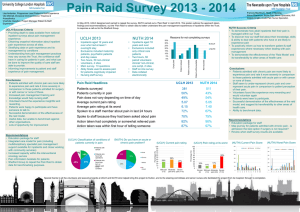
Acceptable Use A User may use NUTH COMPUTING FACILITIES for the purpose of interworking with other Users and Trust Systems and with attached networks, which are reachable via NHS.net. All use of NUTH COMPUTING FACILITIES is subject to acceptance and understanding of the Trust Internet Security Policy and its associated policies (embedded below – refer to section 10). The Data Protection and Information Security Policies embedded below provide guidance on personal data use within the Trust including alignment to the Data Protection Act 2018 including Data Protection Officer details. Information Security Policy Data Protection Policy Newcastle Internet Security Policy If you have any data protection issues please find our Trust Privacy Notice link below for further information: https://www.newcastle-hospitals.org.uk/about-us/freedom-of-information_how-we-use-information_staff-privacy-notice.aspx Subject to the following paragraphs, NUTH COMPUTING FACILITIES may be used for any legal activity that is in furtherance of the aims and policies of the Trust. Unacceptable Use NUTH COMPUTING FACILITIES may not be used for any of the following: The creation or transmission (other than for properly supervised and lawful research purposes) of any offensive, obscene or indecent images, data or other material, or any data capable of being resolved into obscene or indecent images or material; The creation or transmission of material which is designed or likely to cause annoyance, inconvenience or needless anxiety; The transmission of unsolicited commercial or advertising material either to other users, or to users connected to other networks; Deliberate unauthorised access to facilities or services accessible via NUTH COMPUTING FACILITIES; Corrupting or destroying other users' data; Continuing to use an item of networking software or hardware after being requested that use cease because it is causing disruption to the correct functioning of NUTH COMPUTING FACILITIES or NHS.net Other misuse of NUTH COMPUTING FACILITIES or networked resources, such as the introduction of "viruses", “worms” or other malicious software. Users must not attach non-authorised equipment to the Trust network. Authorised equipment should only be connected by the Trust IT department. The creation or transmission of defamatory material; The transmission of material such that this infringes the copyright of another person; Deliberate activities with any of the following characteristics: Wasting staff effort or networked resources, including time on end systems accessible via NUTH COMPUTING FACILITIES and the effort of staff involved in the support of those systems; Violating the privacy of other users; Disrupting the work of other users; Using NUTH COMPUTING FACILITIES in a way that denies service to other users (for example, deliberate or reckless overloading of access links or of switching equipment); Where NUTH COMPUTING FACILITIES are being used to access another network, any abuse of the acceptable use policy of that network will be regarded as unacceptable use of NUTH COMPUTING FACILITIES. Third Party Access It is not permitted to provide access to NUTH COMPUTING FACILITIES for third parties without the prior agreement of the Trust IT Network and Infrastructure Manager. It is intended that such use be regulated by the Trust IT Department. Compliance It is the responsibility of the User to take all reasonable steps to ensure compliance with the conditions set out in this Policy document, and to ensure that unacceptable use of NUTH COMPUTING FACILITIES does not occur. The discharge of this responsibility must include informing those with access to NUTH COMPUTING FACILITIES of their obligations. In this respect. Where necessary, service may be withdrawn from the User. This may take one of two forms. An indefinite withdrawal of service, should a violation of these conditions persist after appropriate warnings have been given. Such a withdrawal of service would only be made on the authority of the IT Security Manager. Restoration would be made only when the IT Security Manager was satisfied that the appropriate steps had been taken at the involved to ensure acceptable behaviour in future. A suspension of service, should a violation of these conditions cause serious degradation of the service to other users of NUTH COMPUTING FACILITIES. Such a suspension would be made on the judgement of IT Network and Infrastructure Manager, and service would be restored when the cause of the degradation of service to others had been removed. Where violation of these conditions is illegal or unlawful, or results in loss or damage to NUTH COMPUTING FACILITIES resources or the resources of third parties accessible via NUTH COMPUTING FACILITIES, the matter may be referred for legal action. All Internet and e-mail facility users are required to read and sign the following declaration: I have seen and read a copy of the Newcastle-upon-Tyne Hospitals Internet Policy. I understand the terms of the Policy and agree to abide by them. I understand that security software may record the use I make of patient information, e-mail facilities and the Internet, which may include logging the content of e-mails and attachments and the addresses of any web sites and noting what file transfers I make. I have no objection to any monitoring of the use I make of any NHS establishment IT equipment. I understand that any violation of this policy could result in escalation my employer and removal from site.