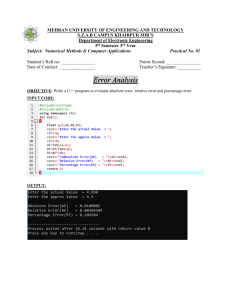
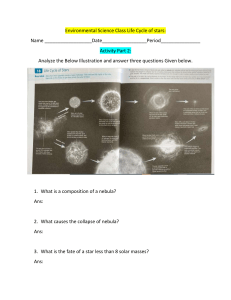
1. Processes in network identify each other by an abstract locator called ______ Port address 2. Which flag is used in the first step of connection termination phase of TCP? FIN 3. Which of the following is true regarding the characteristics of UDP? a. Implements mechanisms for reliable delivery b. Does not implement mechanisms for flow control. Only b is true 4. What mechanism in TCP involves preventing too much data from being injected into the network? Congestion control 5. In the original algorithm for adaptive retransmission in TCP, EstimatedRTT and TimeOut value is computed as _________(Assume α is the smoothing parameter, SampleRTT is the difference between these two times in receiving the current and previous acknowledgment ) EstimatedRTT = α×EstimatedRTT+(1−α)×SampleRTT , TimeOut = 2×EstimatedRTT 6. When the fast retransmit mechanism signals congestion, rather than drop the congestion window all the way back to one packet and run slow start, it is possible to use the ACKs that are still in the pipe to clock the sending of packets. This mechanism is called ____ Fast recovery 7. Congestion avoidance mechanism in which a single congestion bit is added to the packet header is called _____ DECbit 8. Consider the congestion window size for a TCP connection when a timeout occurs be 16 KB. The round trip time of the connection is 50 msec and the maximum segment size used is 2 KB. The size of the congestion window in terms of Maximum Segment Size(MSS) is _________. 8 MSS 9. Which application layer protocol runs in port number 53? DNS 10. The transport layer protocol which is used to improve the performance of connection-oriented web application is called ______ QUIC 11. The application layer protocol that helps in the transfer of flies from one computer to another is ___ FTP 12. An adaptive streaming protocol that enables high quality streaming of media content over the Internet is ____ DASH 13. A simple protocol to retrieve email from server with minimal error is ____ POP 3 14. Which of the following statement(s) is/ are not correct? I. TCP connections are full duplex II. TCP has no option for selective acknowledgment III. TCP connections are message streams Only II and III 15. What extra component is added with the TCP and UDP header fields to verify the message delivery between two end points? pseudoheader 1. What happened at time 20? Ans: timeout 2. What happened at time 10? Ans: duplicate acknowledgement,multiplicative decrease 3. When is the Congestion avoidance phase of slow start? Ans: 10-20,34-44,after 44 4. What congestion control mechanism is followed between time 10-20? Ans: Additive increase 5. What congestion control mechanism is followed at time 20? Ans: Slow start 6. The protocol value of UDP in IP header is ____ Ans: 17 7. What extra component is added with the TCP and UDP header fields to verify the message delivery between two end points? Ans: pseudoheader 8. The size of the source and destination port fields is ____ Ans: 2 bytes 9. The size of the sequence number and the advertised window fields in TCP header are ___ and ____ respectively. Ans: 4 bytes, 2 bytes 10. The algorithms used to establish TCP connection is called Ans: Three-way handshaking What is the congestion window size at 4th RTT? Ans: 16 Identify the time periods when TCP slow start is operating(more than one answer possible) Ans: 0-4,7-10 Identify the time periods when TCP congestion avoidance is operating (AIMD). Ans:4-6,10-14,15-17,6-9 At the 6th RTT, is the segment loss detected by_______ Ans:timeout What is the initial value of ssthreshold, before the first congestion avoidance interval? Ans: 16 What is the value of ssthreshold, after the first congestion avoidance interval? Ans: 9 What is the value of ssthreshold, after the second congestion avoidance interval? Ans: 6 At the 14th RTT, is the segment loss detected by Ans: duplicate ack Assuming a packet loss is detected after the 17th RTT by the receipt of a triple duplicate ACK, what will be the values of the congesion-window size and of ssthreshold? Ans: 4,4 1. TCP/IP model follows a. Connection oriented approach b. Connectionless approach c. Connection oriented over connectionless approach d. Connectionless over connection oriented approach 2. Flag bit used for establishing a connection is Ans: SYN 3. The client sends the following information to the server during the initiation of 3-way handshaking Ans: SYN, Sequence number=x 4. The sequence number of the TCP segment starts with ___ Ans: random number 5. One of the important part of the TCP message includes ________ a. b. c. d. Information about application which generated that message Information about machine which generated that message Information about user who generated that message Information about the status of that message 6. TCP segment is verified by ______________ a. b. c. d. The next network layer The previous application layer The receiving TCP layer The TCP layer of the next immediate router 7. The core protocol used in tcp is __ Ans: sliding window 8. TCP is also called as ______ Ans: byte-oriented protocol 9.__________ is the address used to by the TCP to identify the target process. Ans: port number 10. The size of the source address in a UDP header is__ Ans:16 bits 11. _________is used to reassemble the message at the receiving end if the segments are received out of order. a. Sequence Number b. Advertised Window b. Sender Window c. Receiver Window 12. TCP uses _________ as error error detection a. check sum b. CRC c. Parity check d. LRC 13. ________ involves preventing too much data from being injected into the network, thereby causing switches or links to become overloaded. Ans: Congestion control 14. A TCP connection are likely to have different ____ Ans: RTT 15. The server which is willing to accept data is in ______ state Ans: passive open 16. _____ is a mechanism used to increase the congestion window rapidly from a cold start. Ans: slow start 17. In which method a single bit is added to the packet header to predict congestion . Ans: DECbit 18. In ____________ mail in the sender is not deleted after download a. b. c. d. IMAP POP3 SMTP ICMP 19. _________ is one of the FTP transfer parameter command a. STRU b. ALLO c. REST d. STOR 20. ________ allows a user to connect to a remote host and upload or download the files. a. TCP b. UDP c. FTP d. SMTP_ 21. ______ maintains the domain name system. a) distributed database system b) a single server c) a single computer d) none of the mentioned 22. _________contains all labels, from the most specific to the most general, that uniquely define the name of the host. a. Fully Qualified Domain Name(FQDN) b. Partially Qualified Domain Name(PQDN) c. Both FQDN and PQDN d. None of the above 23. The formal protocol that defines the Mail Transfer Agents( client and server) in the Internet is called _________ Ans:Simple Mail Transfer Protocol (SMTP). 24. The process of transferring a mail message occurs in the following order of phases : Ans: connection establishment, mail transfer, and connection termination. 25. The two modes of POP3 protocol are: 26. Ans: the delete mode and the keep mode. 27. _________ the standard mechanism provided by TCP/IP for copying a file from one host to another. Ans: FTP 28. 11. The two types of DNS message are: Ans: query and response Refer the Figure 1 to answer the questions number from 16 - 24)(12) 29. Identify the time periods when TCP slow start is operating. (2) 0 - 4, 7 – 10 30. Identify the time periods when TCP congestion avoidance is operating (AIMD).(3) 4 - 6, 10 - 14, 15 - 17 31. At the 6th RTT, is the segment loss detected by_______ (1) 32. What is the initial value of ssthreshold, before the first congestion avoidance interval? (1) 16 33. What is the value of ssthreshold, after the first congestion avoidance interval?(1) 9 34. At the 14th RTT, is the segment loss detected by________ (1) 35. What is the value of ssthreshold, after the second congestion avoidance interval? (1) 6 36. Assuming a packet loss is detected after the 17th RTT by the receipt of a triple duplicate ACK, what will be the values of the congesion-window size and of ssthreshold? (1) 4,4 37. Assuming a packet loss is detected after the 17th RTT by the receipt of a timeout , what will be the values of the congesion-window size and of ssthreshold?(1) 4,1 1/31/22, 2:22 PM Tutorial 1 Tutorial 1 Total points 20/20 The respondent's email (19z350@psgtech.ac.in) was recorded on submission of this form. If the network bandwidth = 10Mbps, what is the time taken to transmit one bit? 2/2 10^7 s 0.1 micro sec 0.1 s 10s Logical addressing is a service provided by ______ layer in OSI reference 1/1 model. network datalink transport physical https://docs.google.com/forms/d/e/1FAIpQLScVJrtrC4fGZbns8P2D8xbpHV5XeBdRTNsSwVAuCa77b6euZg/viewscore?viewscore=AE0zAgA-UknsJr9… 1/6 1/31/22, 2:22 PM Tutorial 1 The type of network that handles the interconnection of IT devices at the 1/1 surrounding of a single user is called _____________________ local area network metropolitan area network personal area network wide area network What is the propagation delay if the distance between the two points is 2/2 12,000 km? Assume the propagation speed to be 2.4 x 10^8 m/s in cable. 50s 100s 50ms 100ms The number of bits that can be transmitted over the network in a certain 1/1 period of time is called __________. round trip delay propagation delay bandwidth transmission delay https://docs.google.com/forms/d/e/1FAIpQLScVJrtrC4fGZbns8P2D8xbpHV5XeBdRTNsSwVAuCa77b6euZg/viewscore?viewscore=AE0zAgA-UknsJr9… 2/6 1/31/22, 2:22 PM Tutorial 1 SMTP is a protocol in ______ layer of TCP/IP model. 1/1 network application transport link The hiding of details behind well-defined interface is called __________ 1/1 layering decoding abstraction encapsulation The process of determining systematically how to forward messages towards the destination node based on its address is called __________ 1/1 Encoding Multiplexing Routing Linking https://docs.google.com/forms/d/e/1FAIpQLScVJrtrC4fGZbns8P2D8xbpHV5XeBdRTNsSwVAuCa77b6euZg/viewscore?viewscore=AE0zAgA-UknsJr9… 3/6 1/31/22, 2:22 PM Tutorial 1 ______ connector is used to connect coaxial cable. 1/1 BNC RJ45 SC connector ST connector For a noiseless channel, the Nyquist bit rate formula defines the 1/1 theoretical maximum bit rate is given by: Bit Rate = 2 x bandwidth x 1og(base 2) L . What does L stands for? number of signal levels used to represent data. data bits per signal level total number of data bits peak value of the signal levels The communication type where source node sends a message to all the 1/1 nodes is called _________ anycast unicast multicast broadcast https://docs.google.com/forms/d/e/1FAIpQLScVJrtrC4fGZbns8P2D8xbpHV5XeBdRTNsSwVAuCa77b6euZg/viewscore?viewscore=AE0zAgA-UknsJr9… 4/6 1/31/22, 2:22 PM Tutorial 1 _____ cable has a metal foil or braided mesh-covering that encases each 1/1 pair of insulated conductors. unshielded twisted pair shielded twisted pair optical coaxial _______ is the maximum value or strength of the signal over time 1/1 Frequency Time Phase Amplitude Consider a point-to-point link 50 km in length. At what bandwidth would 2/2 propagation delay(at a speed of 2x10^8 m/s) equal transmit delay for 100-byte packets? 3.2 kbps 2.5 Mbps 3.2 Mbps 2.5 kbps https://docs.google.com/forms/d/e/1FAIpQLScVJrtrC4fGZbns8P2D8xbpHV5XeBdRTNsSwVAuCa77b6euZg/viewscore?viewscore=AE0zAgA-UknsJr9… 5/6 1/31/22, 2:22 PM Tutorial 1 Consider a dial-up connection whose bandwidth is 56kbps with RTT of 2/2 87 micro seconds. The maximum number of bits in transit at a particular time. 3 6 5 4 If there are 5 nodes connected using bus topology then the number of 1/1 links is ___________ 2 4 5 6 This form was created inside of PSG College of Technology. Forms https://docs.google.com/forms/d/e/1FAIpQLScVJrtrC4fGZbns8P2D8xbpHV5XeBdRTNsSwVAuCa77b6euZg/viewscore?viewscore=AE0zAgA-UknsJr9… 6/6 1 mark qns: 1. A class of switches that connects Ethernet segments are called as _________ Ans: bridges 2. The protocol which is mainly used to deal with interconnection of different type is called __________ Ans: IP 3. The path taken by a packet in a network should have the following characteristics: Ans: loop free, respond to addition of new nodes, respond to failure of existing nodes. 4. If a connection has to be made by allocating dedicated resources it is called as ______ Ans: circuit-switching 5. Which of the following is a type of packet switched network Ans: datagram, virtual-circuit switched 6. _______________ is used to uniquely identify a connection to a switch. Ans: virtual circuit identifier (VCI) 7. In this approach, to establish a connection state by virtual circuit switching, the host sends messages/signal into the network to cause the state to be established. Ans: switched virtual circuit (SVC) 8. For the following network topology, what can be the content of virtual circuit table if the packet has to move from host A to host B Ans: 3,7,2,6 9. If all the information about network topology that is required to switch a packet across the network is provided by the source host then the type of switching is called Ans: source routing 10. The minimum size of IPv4 header is _______ Ans: 32 11. ___________ is the largest IP datagram that it can carry in a frame. Ans: maximum transmission unit (MTU), 12. The default value of TTL in IPv4 header is __________ Ans: 64 13. Header length in IPv4 header specifies the length of the header as ____ Ans: 32 bit word 14. Protocol to convert IP address to link-level address is ______ Ans: Address Resolution Protocol (ARP) 15. In ARP the value of Hardware type field if the link-level technology used is Ethernet and network protocol used is IPv4 is Ans: 1 16. The type of communication for an ARP request is _______ Ans: broadcast 17. The protocol used if the host system has to be configured to connect to a network automatically is called ______ Ans: DHCP 18. DHCP is derived from __________ protocol Ans: BOOTP 19. The error reporting protocol associated with IP is ____ Ans: Internet Control Message Protocol (ICMP) 20. Debugging tool that uses ICMP is Ans: ping, traceroute. 2 mark qns(as MCQs): 1. Advantages of having a switch in network: Ans: many hosts can be connected to a switch, connection can be made between two switches, network with switches is scalable, hosts connected with switch can transmit at full link speed. 2. Following are the characteristics of a datagram network: Ans: host can send packet anywhere at any time, each packet is treated independently, link failure many not be a serious problem, packets from a specific source to specific destination can take different paths, sender host need not know whether then network will be able to deliver the packet to the destination, no connection establishment phase 3. Which of the following are the characteristics of virtual circuit switching? Ans: if a link fails, new connection has to be established, if the switch fails, new connection has to be established, requires routing algorithm, per packet overhead is reduced when compared to the datagram model, has connection establishment phase, has to send tear-down signal/message to disconnect the connection 4. The following are the characteristics of IP protocol Ans: can build scalable network, can build heterogeneous network, uses logical addressing, uses datagram approach to forward packets, packets are sent in a connectionless manner, does not make any attempt to recover from failure, can deliver out-of-order packet, can deliver duplicate packet. 5. The following are the fields of IP header with the size of the fields in bits : Ans: Version number – 4 bits, Header length -4 bits, Type of service – 8 bits, length of the datagram – 16 bits, Time to live -8 bits, protocol – 8 bits, checksum -16 bits, source address – 32 bits, destination address – 32 bits, fragment identifier-16 bits, fragment flags – 3 bits, fragment offset – 13 bits (any 4 options can be given) 1. Nodes that support users and run application programs. Ans: Host 2. Byte string that identifies a node is called _______ Ans: Address 3. When an application uses the ___________service, the client and the server (residing in different end systems) send control packets to each other before sending packets with real data. Ans: connection-oriented 4. The internet’s connectionless service is ________ Ans: UDP 5. In __________ the resources needed for communication between the end-systems are reserved for the duration of the session. Ans: Circuit-Switched Networks 6. The hiding of details behind well-defined interface is called __________ Ans: abstraction 7. Which of the following is a valid IP address: Ans: 8. The range of System ports/ Well known ports is ____________ Ans: 0 – 1023 9. The number of bits that can be transmitted over the network in a certain period of time is called __________. Ans: bandwidth 10. The communication type where source node sends a message to a subset of nodes but not all nodes is called _________ Ans: multicast 11. If the switch run out of buffer space, some packets are dropped. This operating state is called _______ Ans: Congested. 12. Repeater belongs to __________ layer in a network model. Ans: Physical 13. The layer in the network model that handles routing among nodes within a packet-switched network is ______________ Ans: network 14. The type of network that handles the interconnection of IT devices at the surrounding of a single user is called _____________________ Ans: personal area network 15. If there are 10 nodes connected using bus topology then the number of links is ___________ Ans: 11 16. What is the propagation delay if the distance between the two points is 12,000 km? Assume the propagation speed to be 2.4 x 108 m/s in cable. Ans: 50ms 17. What is the transmission time for a 2.5-kbyte message (an e-mail) if the bandwidth of the network is 1 Gbps? Assume that the distance between the sender and the receiver is 12,000 km and that light travels at 2.4 x 108 mls. Ans: Transmission time = 0.020ms 18. Consider a dial-up connection whose bandwidth is 56kbps with RTT of 87 micro seconds. . The maximum number of bits in transit at a particular time. Ans: 5 19. Assume that Source S and Destination D are connected through an intermediate router R. How many times a packet has to visit the network layer and data link layer during a transmission from S to D? Network layer – 4 times, Data link layer – 4 times Network layer – 4 times, Data link layer – 6 times Network layer – 2 times, Data link layer – 4 times Network layer – 3 times, Data link layer – 4 times 20. The OSI layers that is resent only at the end hosts are Ans: transport,session,presentation,application PSG COLLEGE OF TECHNOLOGY, COIMBATORE - 641 004 DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING BE CSE, SEM V CONTINUOUS ASSESSMENT TEST 1 Date: 13/09/2021 19Z504 COMPUTER NETWORKS Time: 75 min. Maximum Marks: 50 INSTRUCTIONS: 1. Answer ALL questions. Each question carries 10 Marks. Answer the following: 1. Consider a network that uses one switch. We need to send two packets of size is 10000. Transmission time for each packet is 500 μs. Two hosts are connected via a packet switch with 107 bits per second links. Each link has a propagation delay of 20 μs. The switch begins forwarding a packet 35 μs after it receives the same. If 20000 bits of data are to be transmitted between the two hosts using a packet size of 10000 bits, what is the time elapsed between the transmission of the first bit of data and the reception of the last bit of the data. (10) 2. Discuss about the OSI reference model of computer networks with neat sketch. (10) 3. Given the data word 1010001101 and the divisor 110101.Show the generation of the codeword at the sender site and Show the checking of the codeword at the receiver site using CRC technique. (10) 6 4. Frames of 1000 bits are sent over a 10 bps duplex link between two hosts. The propagation time is 25ms. Frames are to be transmitted into this link to maximally pack them in transit (within the link).What is the minimum number of bits that will be required to represent the sequence numbers distinctly? (Assume that no time gap needs to be given between transmissions of two frames). (i) If receiver window size is one (ii) If receiver window size is equal to sender window size 5. What is meant by Hidden Terminal and Exposed node Problems? How to solve it? Illustrate with the suitable examples. (10) PSG COLLEGE OF TECHNOLOGY, COIMBATORE - 641 004 DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING BE CSE, SEM V CONTINUOUS ASSESSMENT TEST 3 Date: 18/11/2021 19Z504 COMPUTER NETWORKS Time: 60 min. Maximum Marks: 35 PART B Answer the following (2x10=20 marks) 1. i.Describe the purpose of the sequence number in TCP (6 marks) ii. Suppose Host A sends two TCP segments back to back to Host B over a TCP connection. The first segment has sequence number 80; the second has sequence number 110. a. Suppose that the first segment is lost but the second segment arrives at B. In the acknowledgment that Host B send to Host A, what will be the acknowledgment number? b. How much data is in the first segment?(4 marks) 2. What is DHCP and describe how it works?(10 marks) PSG COLLEGE OF TECHNOLOGY, COIMBATORE - 641 004 DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING BE CSE, SEM V CONTINUOUS ASSESSMENT TEST 2 Date: 21/10/2021 19Z504 COMPUTER NETWORKS Time: 60 min. Maximum Marks: 50 1. A router maintains the following routing table and it can deliver the packets directly to hosts through interfaces and can forward the packet to the routers Rn (n =2, 3, &4). (10) With the following destination IP addresses, what does the router do? (a) 128.96.171.91 (b) 128.96.167.152 (c) 128.96.163.153 (d) 128.96.169.193 (e) 128.96.165.122 2. Consider a message from TCP layer contains 1044 bytes of data without including the header. It is passed to network layer’s IP protocol for delivery across 3 networks with MTUs 1024 and 500 and 200. Show the values of all the Flag bits and offset field of IP header and the size of each data packet (without header) when it passes though each network and reach the destination host. (Assume all IP and TCP headers are 20 bytes). (10) 3. (i) For the network given in the Figure 1, give the datagram forwarding table (both initial and final) for each node. The links are labeled with relative costs; your table should forward each packet via the lowest-cost path to its destination using distance vector routing. (10) Figure 1 (ii) Consider the figure 2. Initially both the node A and B know how to reach node C. But suddenly the link B to C goes down. What will happen in distance routing and also discuss how to overcome that problem? (5) A 1 1 B C Figure 2 4. Consider a traditional Class C address space like 192.168.1.0/24and an organization wants to formsubnets for four departments, with hosts as follows: A) CSE: 75 hosts B) EEE: 50 hosts C) Civil: 25 hosts D) ECE: 20 hosts Design the subblocks and show the first and last address of each subblocks (using slash notation). Find out how many addresses are still available after these allocations (15)