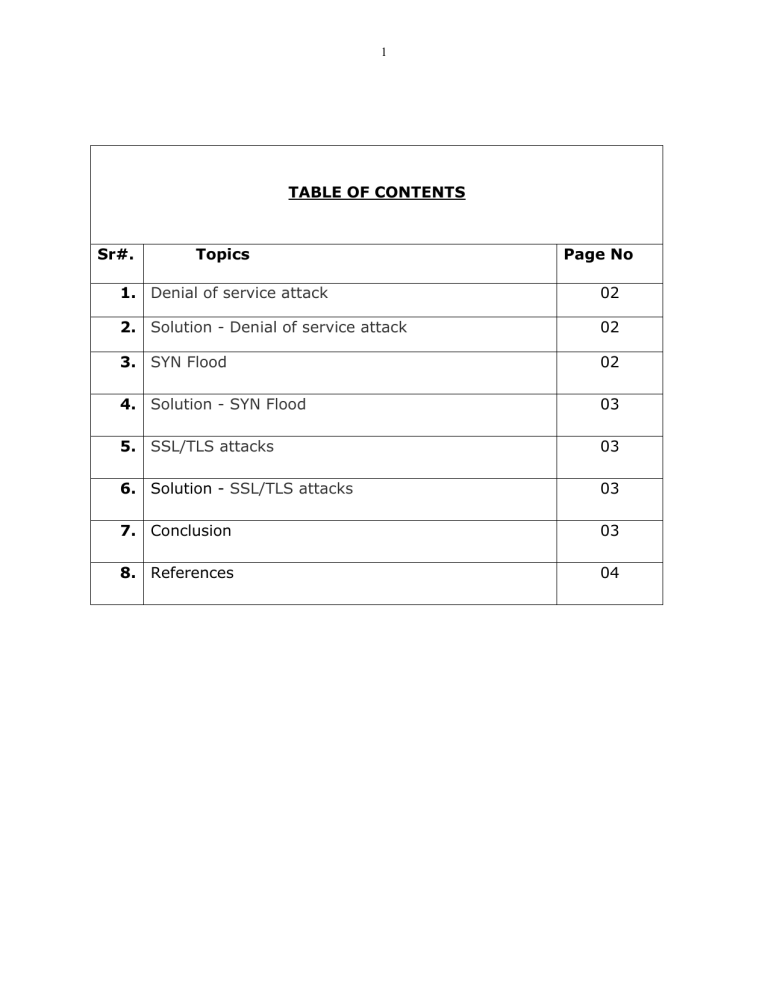
1 TABLE OF CONTENTS Sr#. Topics Page No 1. Denial of service attack 02 2. Solution - Denial of service attack 02 3. SYN Flood 02 4. Solution - SYN Flood 03 5. SSL/TLS attacks 03 6. Solution - SSL/TLS attacks 03 7. Conclusion 03 8. References 04 2 THE THREE THREATS THAT CAN BE DONE ON AIRPORT SECURITY NETWORK Following are the three threats and the solutions that can be done on Airport security network: 1. Denial of service attack: In this type of attack, the users of the network are deprived of the services provided by the computer network. These types of attack are very normal and are generally occurred in computer networks, which should be controlled in order for regular working of the network. Generally, large number of illegitimate requests are done which causes overloading of the computer network. Sometimes the service requested by the user is denied which is caused by large number of false requests. This type of threat can occur at computer network of the airports. Solution: One way of preventing denial of service attack is to develop a response plan, so that according to the problem, a solution should be provided. A full list of situations which can happen are created and a particular solution according to that situation can take place when the problem is encountered. 2. SYN Flood: A SYN Flood exploits the weakness in the TCP connection sequence, where a SYN request is used to start the connection with the host, which must be followed by SYN-ACK response from the host and then confirmed by ACK message from the requester. Now in SYN Flood scenario, the requester sends large number of SYN requests, but either does not respond to the host's SYNACK response. The host system continues to wait for the acknowledgement for each of these requests, resulting in denial of service. Solution: To prevent this type of attack, firewalls and proxies should be set up in the system, so that the system is free from virus or abruptions. We can also 3 reduce the time of SYN-RECEIVED timer, so that SYN requests don’t gets wasted and gets acknowledged on-time. 3. SSL/TLS attacks: Transport layer security keeps up the uprightness of information among worker and customer and gives validation to the two sides. In these type of attack, the aim is to intercept data that is sent over an encrypted connection. If the attack is successful, then the attacker can access the unencrypted information and can use it. This type of attack are common in airport security network. Solution: The arrangement of this assault is to utilize firewalls and executes legitimate security. The firewalls should ensure that the information that we are receiving should be 100% correct and valid. The information should not be changed during the transmission of message. Firewalls should ensure integrity. Conclusion: Organization reenactment instruments to look at the presentation of different lining calculations in easing the dispersed disavowal of administration assaults and in offering wanted types of assistance at Airport security. Recreation results demonstrated that carrying out lining calculations in network switches may give the ideal arrangement in ensuring security in instances of conveyed forswearing of administration assaults. Solutions are related with protocol itself, such as version rollback attack, which should take a long time to replace all SSL 3.0 with version 3.0. Others are easy to improve, as Martin’s attack to IMAP server, but people should aware the essential problem within that attack, not only stop the attacker, but also prevent the possibility in the future. Intrusion detection in the server side is a good method to prevent potential attack from man-in-the-middle attack and repeated attack. 4 References: Felix Lau Simon Fraser, University Burnaby, BC, Canada, Feb 2005. https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ca d=rja&uact=8&ved=2ahUKEwjLicCsg7LxAhXL6OAKHWEgCGAQFjALegQIHR 1 AD&url=https%3A%2F%2Fs2.ist.psu.edu%2Fpaper%2Fddos-chap-gujune-07.pdf&usg=AOvVaw34QK1_8HmNSIxFapuQAwbc Mehdi Ebady Manna and Angela Amphawan School of computing, University Utara Malaysia, Kedah, Malaysia, January 2012. https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ve d=2ahUKEwjD55bDhrLxAhXyB2MBHd1XAWAQFjADegQIBBAD&url=https%3 2 A%2F%2Farxiv.org%2Fpdf%2F1202.1761&usg=AOvVaw2hFDjXfGIQMiWw KwjciuIx Hong lei Zhang Department of Computer Science The University of Auckland, Dec 2007 https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ve d=2ahUKEwi1rIjsuv_uAhXEWc0KHdtnCqIQFjADegQIBRAD&url=https%3A% 3 2F%2Fwww.moheri.gov.om%2Fuserupload%2FPolicy%2FIT%2520Risk%25 20Management%2520Framework.pdf&usg=AOvVaw1lkFE2_0EKaDubBnSAs am8