Chapter 9 – Cryptography and Network
Security (William Stallings)
Public key cryptography
Basic Asymmetric Algorithms
Dr. Danish Mahmood
CS Dept., SZABIST
Islamabad.
traditional private/secret/single key
cryptography uses one key
shared by both sender and receiver
if this key is disclosed communications are
compromised
also is symmetric, parties are equal
hence does not protect sender from receiver
forging a message & claiming is sent by
sender
probably most significant advance in the
3000 year history of cryptography
uses two keys – a public & a private key
asymmetric since parties are not equal
uses clever application of number theoretic
concepts to function
complements rather than replaces private key
crypto
public-key/two-key/asymmetric
cryptography involves the use of two keys:
◦ a public-key, which may be known by anybody,
and can be used to encrypt messages, and verify
signatures
◦ a private-key, known only to the recipient, used
to decrypt messages, and sign (create) signatures
is asymmetric because
◦ those who encrypt messages or verify signatures
cannot decrypt messages or create signatures
Hashin
can classify uses into 3 categories:
◦ encryption/decryption (provide secrecy)
◦ digital signatures (provide authentication)
◦ key exchange (of session keys)
some algorithms are suitable for all uses,
others are specific to one
like private key schemes brute force exhaustive search attack is
always theoretically possible
but keys used are too large (>512bits)
security relies on a large enough difference in difficulty
between easy (en/decrypt) and hard (cryptanalyse) problems
more generally the hard problem is known, its just made too
hard to do in practise ---- NP HARD- NP COMPLETE
requires the use of very large numbers
hence is slow compared to private key schemes
Knapsack
Diffie-Hellman
RSA (Rivest-Shamir-Adleman)
El Gamal
Elliptic curve cryptosystem (ECC)
Digital Signature Algorithm (DSA)
Merkle-Hellman Knapsack
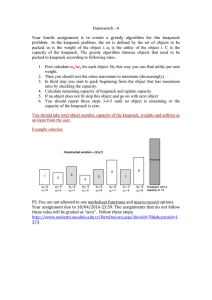
Thief (cash, gold, silver, household, platinum, diamond, crystal, copper)
He has a knapsack that can carry 20kg weight…
Now the problems is, what items he should be carrying / stealing.
(cash, gold, silver, household, appliances, diamond, crystal, copper)
(.5kg, .5kg, .5kg, 10kg, 7kg, .2kg, .5kh, 2kg)—one set--(1000, 3000, 1500. 5000, 2000, 10000, 5000, 3000)– 2nd set--This is a NP Complete hard problem…(nondeterministic polynomial) --- two
iterations,,, first we guess a solution, 2nd we check if our guess was correct.
Given a set of n weights W0,W1,...,Wn-1 and a sum S,
find ai {0,1} so that
S = a0W0+a1W1 + ... + an-1Wn-1
(technically, this is the subset sum problem)
Example
Value of items
◦ Weights (62,93,26,52,166,48,91,141)
◦ Problem: Find a subset that sums to S = 302
◦ Answer: 62 + 26 + 166 + 48 = 302
The (general) knapsack is NP-complete
The size of ba
NP is the set of decision problems solvable in polynomial
time by a non-deterministic Turing machine.
This definition is the basis for the abbreviation NP;
"nondeterministic, polynomial time."
The algorithm is based on the Turing machine which
consists of two phases,
◦ the first of which consists of a guess about the solution, which is
generated in a non-deterministic way,
◦ while the second phase consists of a deterministic algorithm that
verifies if the guess is a solution to the problem.
General knapsack (GK) is hard (NP hard) to solve
But superincreasing knapsack (SIK) is easy
SIK each weight greater than the sum of all
Example
previous weights
◦ Weights (2,3,7,14,30,57,120,251)
◦ Problem: Find subset that sums to S = 186
◦ Work from largest to smallest weight
◦ Answer: 120 + 57 + 7 + 2 = 186
1. Generate superincreasing knapsack
(SIK)
2. Convert SIK to “general” knapsack (GK)
3. Public Key: GK
4. Private Key: SIK and conversion factor
Goal…
o
o
o
Easy to encrypt with GK
With private key, easy to decrypt (solve SIK)
Without private key, Trudy has no choice but to try to solve GK
Element in
1+2+4+10+20+40< m--110
n *value mod m
31*31^-1mod(110)=1
62*31^-1mod(110)=2
…
General set Knapsack
SIK set knapsack
6 elements in every set
(31, 62, 14, 90, 70, 30)– GSK
(1,2,4,10,20,40)- SIK
123 4 5 6
1 2 4 10 20 40
100 1 0 0
Trapdoor: Convert SIK into “general” knapsack
using modular arithmetic
One-way: General knapsack easy to encrypt,
hard to solve; SIK easy to solve
This knapsack cryptosystem is insecure
◦ Broken in 1983 with Apple II computer
◦ The attack uses lattice reduction
“General knapsack” is not general enough!
◦ This special case of knapsack is easy to break