International Journal of Trend in Scientific Research and Development (IJTSRD)
Volume 3 Issue 6, October 2019 Available Online: www.ijtsrd.com e-ISSN: 2456 – 6470
Ethical Hacking
Mukesh. M1, Dr. S. Vengateshkumar2
1MCA
Student, 2Assistant Professor,
1,2Department of Computer Applications (PG),
1,2Dr. SNS Rajalakshmi College of Arts and Science, Coimbatore, Tamil Nadu, India
ABSTRACT
Today’s security is that the main downside and every one the work is finished
over the net mistreatment knowledge. whereas the information is out there,
there square measure many varieties of users who act with knowledge and a
few of them for his or her would like it all for his or her gaining data. There
square measure numerous techniques used for cover of information however
the hacker (or cracker) is a lot of intelligent to hack the security, there square
measure 2 classes of hackers they're completely different from one another on
the idea of their arrange. The one who has smart plans square measure
referred to as moral hackers as a result of the ethics to use their talent and
techniques of hacking to supply security to the organization. this idea
describes concerning the hacking, styles of hackers, rules of moral hacking and
also the blessings of the moral hacking.
How to cite this paper: Mukesh. M | Dr. S.
Vengateshkumar "Ethical Hacking"
Published
in
International Journal
of Trend in Scientific
Research
and
Development
(ijtsrd), ISSN: 24566470, Volume-3 |
IJTSRD29351
Issue-6,
October
2019,
pp.1212-1214,
URL:
https://www.ijtsrd.com/papers/ijtsrd29
351.pdf
KEYWORDS: Moral hackers, White hats, Malicious hackers, Grey hats
Copyright © 2019 by author(s) and
International Journal of Trend in Scientific
Research and Development Journal. This
is an Open Access article distributed
under the terms of
the
Creative
Commons Attribution
License
(CC
BY
4.0)
(http://creativecommons.org/licenses/by
/4.0)
INTRODUCTION
Security is that the major truth in today’s era wherever web
use is extremely quick and Brobdingnagian growing. each
organization has problems to secure their security
concerning sensitive and secret knowledge. Hacking is
finished by an individual WHO has the dangerous plans.
There square measure 2 styles of hackers, one WHO has
rights of securing knowledge whereas mistreatment hacking
and also the alternative WHO uses his data to interrupt
security to damage the organization. These hackers square
measure into 2 classes
1. Moral Hackers 2. Malicious Hackers
hackers WHO break their net Server and replaces their info
with porn, scan their e-mail, steal their master card info from
on-line looking web site, or implant software package which
will on the QT transmit their info to the open web. Cyber
Security is that the most talked topic and also the most
involved space in today’s web world.
Study on Cyber Security:
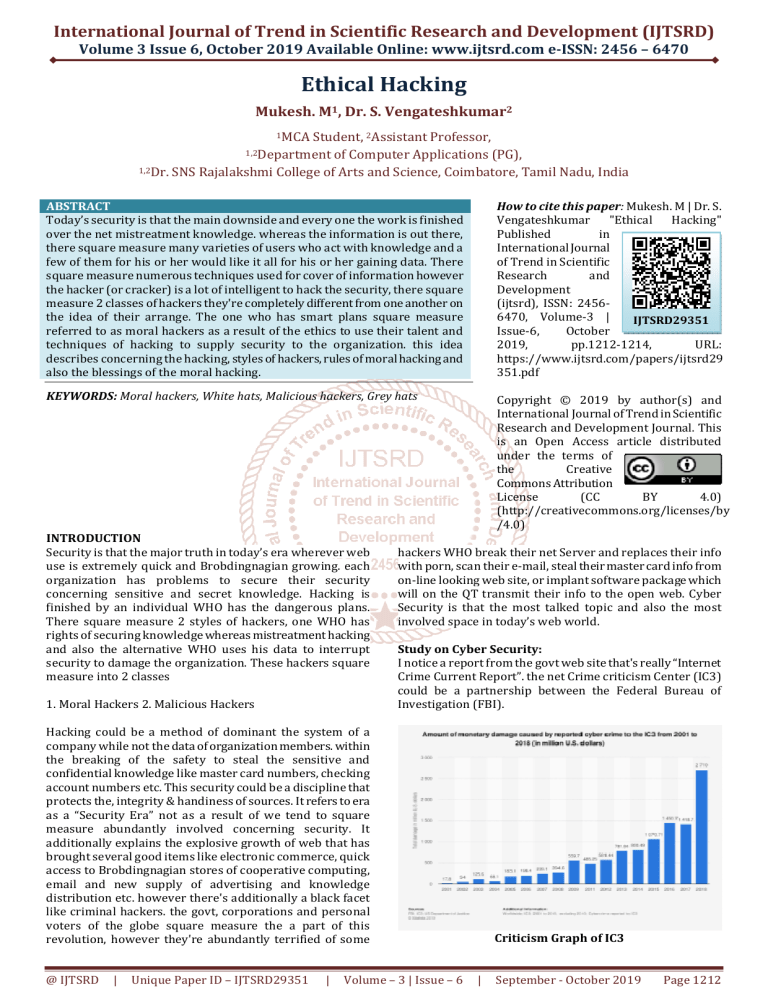
I notice a report from the govt web site that's really “Internet
Crime Current Report”. the net Crime criticism Center (IC3)
could be a partnership between the Federal Bureau of
Investigation (FBI).
Hacking could be a method of dominant the system of a
company while not the data of organization members. within
the breaking of the safety to steal the sensitive and
confidential knowledge like master card numbers, checking
account numbers etc. This security could be a discipline that
protects the, integrity & handiness of sources. It refers to era
as a “Security Era” not as a result of we tend to square
measure abundantly involved concerning security. It
additionally explains the explosive growth of web that has
brought several good items like electronic commerce, quick
access to Brobdingnagian stores of cooperative computing,
email and new supply of advertising and knowledge
distribution etc. however there's additionally a black facet
like criminal hackers. the govt, corporations and personal
voters of the globe square measure the a part of this
revolution, however they're abundantly terrified of some
@ IJTSRD
|
Unique Paper ID – IJTSRD29351
|
Volume – 3 | Issue – 6
Criticism Graph of IC3
|
September - October 2019
Page 1212
International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470
The higher than graph shows that numbers of criticism were
improved at associate exponential rate. however once 2016
it's very little down in 2017 however enlarged in 2018 and is
nearly a similar within the remaining years. This shows that
however copious the safety is during this eon of pc world.
OUT HACKING:
Before knowing concerning the moral hacking, initial we
should always comprehend hacking that prying, as a result of
prying, the hacker continually needs to grasp abundant
concerning the data, liable upon the hacker’s surface.
Several of hacker’s square measure Hackers square measure
with the harmful pc data concerning software package also
as hardware. A hacker who relish the training of the small
print of pc systems. he's a pc fanatic and an honest computer
user in pc systems. The term hacking was outlined as “A one
who love the training the small print of pc systems.”
Moral hacking: moral hacking could be a method within
which the hacker has pure plans to interrupt the pc security
to avoid wasting the organization from some attacks. They
ne'er expose the facts and (information and knowledge) data
concerning the organizations. moral hackers are referred to
as “Red Teams”, or “Invasion Testing”.
Malevolent hacking: The misery uses of pc and network
resources. Malevolent hackers use software package
programs like Trojans, associated spyware to realize entry
into an organization’s network for thievery info. Its result’s
to fraud, loss of personal knowledge, and misery
transactions mistreatment credit or positive identification
numbers, commercialism of user’s personal details like
phone numbers, addresses, account numbers etc.
TYPE OF HACKERS:
The hackers square measure categorized styles of Hackers
Types of Hackers
Black Hat Hackers:
Their results square measure into the destroying activities.
they're referred to as around the bend.
White Hat Hackers:
These hackers square measure skilled hackers. They use
their talent for protecting purpose in strictly in associate
moral approach.
Gray Hat Hackers:
These hackers square measure one WHO square measure
mixture of each white hat and black hat hackers i.e. work
each for offense and defense functions.
LAW OF ETHICAL HACKING:
The hacker should follow the principles of moral
hacking. If they don’t follow the principles then it'd be a
defect for the organization.
Plan of execution: For the moral hackers, the time and
patience square measure a lot of vital.
@ IJTSRD
|
Unique Paper ID – IJTSRD29351
|
Ethical hacker should have clear plans to assist the
organization to not have an effect on them.
Privacy is that the major concern for the organization
purpose of view; so, the moral hacker should be
unbroken it non-public as a result of their misuse is
creating defect.
HACKING PHASES:
Survey: It refers to assemble a lot of info as we will target
into perform associate attack. {the information the data the
data} is gathered concerning the target with none knowledge
of targeted company. It might be done by looking info on
web of associate worker of the targeted company who would
reveal and provides helpful info to the hacker.
Scanning: It refers to scan all the open also as closed ports
and even the familiar vulnerabilities on the targeted
machine. Gaining control: It is gained at OS level, system
level or maybe in a very network level.
It includes word cracking, buffer overflows, attacks etc.
Sustaining Access: It's wherever the hacker strives to retain
the management over the target with backdoors, root kits.
Compromised machines are used as Bots and Zombies for
additional attacks. White Hat Grey Hat.
Log clearing: it's referred to as Daily Chaining. To avoid the
exposed or caught, an honest hacker can leave no
impressions of his presence. So, he tries to write the system
and application logs.
Working of an Ethical Hacker:
The ethical hackers work involves below the mentioned
steps: Following the moral Hacking Orders: each moral
Hacker should follow some basic values. If he doesn't,
dangerous things will happen.
These ethics get unnoticed or forgotten once designing or
effecting moral hacking tests.
Working morally: The word ethical is outlined as
operating with high qualified rules and ethics. When you
square measure completing moral hacking tests against
your own systems or for somebody, everything you are
doing as associate moral hacker should be accepted and
should be support the organization’s goals. there'll be no
hidden plans square measure allowed.
Concerning Privacy: The data you fold with complete
respect, then all the data you create throughout your
testing of net application log files to clear-text
passwords should be unbroken safe.
Not well-off your systems: one in every of the most
errors is once individuals try and hack their own
systems, they are available up with booming their
systems. the most reason for this poor designing. These
tools square measure particularly handled if you wish to
run the tests on creating systems.
Implementing the plan: In moral hacking, Time and
reception square measure vital. Therefore, take care after
you do your own moral hacking tests.
BENEFITS OF ETHICAL HACKING:
The ethical hacking plays associate very important role
within the security eon. wherever the network users square
Volume – 3 | Issue – 6
|
September - October 2019
Page 1213
International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470
measure growing often and additionally the hackers who
square measure taking blessings of network.
The following blessings of moral hacking;
The fight against terrorist act and issues of safety.
Preventing malevolent hackers to realize the access of
crucial knowledge.
Ethical hackers believe the most effective shield systems
by them whereas inflicting no injury and afterwards
fixing the liabilities found.
Conclusion:
As the use of web rises, everybody depends upon it and
saves their (vital very vital important) and important
knowledge over the net. Basically, this is often an invitation
to the “crackers” realize access of data. the safety is that the
major downside for the organization. This illustrates the
importance of moral hackers. the aim of the organization
hires. Moral hackers WHO square measure well knowledge
and toughened person. Hackers observe flaws and
weaknesses in a very system or network and modify it in
keeping with the needs. There square measure 2 classes of
hackers referred to as the white-hat and also the black-hat
@ IJTSRD
|
Unique Paper ID – IJTSRD29351
|
WHO square measure solely differentiated by their plans
towards hacking. moral hackers of white-hat hackers aren't
accepted well by the society and square measure perceived
as general hackers who have malicious plans. (they square
measure they're) certified professionals who are appointed
by the organizations to stay their security under control that
is why they're vital for the society and businesses. Each
hacker utilizes sure tools, skills, and gadgets to hold out the
hacking method. If today’s security threats are going to be
greatly reduced.
References:
[1] Imaginary being, Sahil, Richet. "Ethical Hacking."
analysis Gate. N. p., 2015. Web. 14 Dec. 2018.
[2] Marsh, Devin. "Are ethical Hackers the most effective
declare Combating the Growing World of CyberCrime?" Jewlscholar.mtsu.edu. N. p., 2017. Web. 15 Dec.
2018.
[3] Munjal, Meenakshi N. "ETHICAL HACKING: A sway ON
SOCIETY." 7.1 (2013): 922-931. Web. 14 Dec. 2018.
[4] "Phases
of
Hacking
| Ethical Hacking."
Greycampus.com. Web. 14 Dec. 2018.
Volume – 3 | Issue – 6
|
September - October 2019
Page 1214





