INTRODUCTION TO INFORMATION
SECURITY
Compiled By :
Vaishali Soni
WHAT IS SECURITY?
In the context of computers, security generally means
three things:
Confidentiality
Integrity
When you ask for data, you get the “right” data
Availability
Access to systems or data is limited to authorized parties
The system or data is there when you want it
A computing system is said to be secure if it has all
three properties
Well, usually
Pillars of Security:
Confidentiality, Integrity, Availability
CONFIDENTIALITY(CIA)
: WHO IS AUTHORIZED?
INTEGRITY: IS DATA „GOOD?”
AVAILABILITY: CAN ONE ACCESS DATA WHENEVER
NEEDED?
Integrity
Confidentiality
S
Availability
S = secure
[cf. Barbara Edicott-Popovsky and Deborah Frincke, CSSE592/492, U. Washington]
BALANCING CIA
Payroll
Data
Biographical
Data
Integrity
Confidentiality
S
Sensitive
Data
Availability
S = secure
Need to balance CIA
Ex: Disconnect computer from
Internet to increase
confidentiality (availability
suffers, integrity suffers due to
lost updates)
Ex: Have extensive data checks
by different people/systems to
increase integrity (confidentiality
suffers as more people see data,
availability suffers due to locks
on data under verification)
Packet
Switch
Bridge
File
Server
Gateway
Other
Networks
[Barbara Edicott-Popovsky and Deborah Frincke, CSSE592/492, U. Washington]
Health
Data
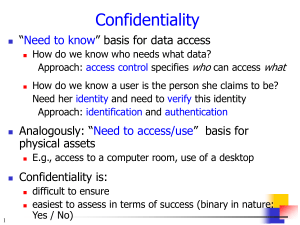
CONFIDENTIALITY
Use
the “need to know” basis for data access
How do we know who needs what data?
Approach: access control specifies who can access what
How do we know a user is the person she claims to be?
Need her identity and need to verify this identity
Approach: identification and authentication
Analogously:
“need to access/use” basis for access
to physical assets
E.g., access to a computer room, use of a desktop
Confidentiality
is:
Difficult to ensure
Easiest to assess in terms of success
Binary in nature: Yes / No
Integrity
INTEGRITY
vs. Confidentiality
Integrity - concerned with unauthorized modification of
assets (= resources)
Confidentiality - concered with access to assets
Integrity is more difficult to measure than confidentiality
Not binary – degrees of integrity
Context-dependent - means different things in different
contexts
Could mean any subset of these asset properties:
{ precision / accuracy / currency / consistency /
meaningfulness / usefulness / ...}
Types
of integrity—an example
A quotation from a politician
Preserve the quotation (data integrity) but mis-attribute
(origin integrity)
AVAILABILITY
We can say that an asset (resource) is available if:
Timely request response
Fair allocation of resources (no starvation!)
Fault tolerant (no total breakdown)
Easy to use in the intended way
Provides controlled concurrency (concurrency control, deadlock
control, ...)
[Pfleeger & Pfleeger]
VULNERABILITIES, THREATS, AND CONTROLS
Understanding
Vulnerabilities, Threats, and
Controls
Vulnerability = a weakness in a security system
Threat = circumstances that have a potential to cause harm
Controls = means and ways to block a threat, which tries to exploit
one or more vulnerabilities
Most of the class discusses various controls and their effectiveness
[Pfleeger & Pfleeger]
Attack
= exploitation of one or more vulnerabilities by a threat; tries to
defeat controls
Attack may be:
Successful
resulting in a breach of security, a system
penetration, etc.
Unsuccessful
when controls block a threat trying to exploit a
vulnerability
[Pfleeger & Pfleeger]
Examples
Fig. 1-1 (p.6)
New Orleans disaster (Hurricane Katrina):
What were city vulnerabilities, threats, and controls
SECURITY AND RELIABILITY
Security has a lot to do with reliability
A secure system is one you can rely on to (for example):
Keep your personal data confidential
Allow only authorized access or modifications to resources
Give you correct and meaningful results when you want
them
SOME TERMINOLOGY
Assets
Things we might want to protect, such as:
Hardware
Software
Data
Vulnerabilities
Weaknesses in a system that may be able to be exploited in
order to cause loss or harm
e.g., a file server that doesn't authenticate its users
SOME TERMINOLOGY
Threats
A loss or harm that might befall a system
e.g., users' personal files may be revealed to the public
There are four major categories of threats:
Interception
Interruption
Modification
Fabrication
When we design a system, we need to state a threat model
This is the set of threats we are undertaking to defend against
Whom do we want to stop from doing what?
SOME TERMINOLOGY
Attack
An action which exploits a vulnerability
e.g., telling the file server you are a different user in an
attempt to read or modify their files
Control
Removing or reducing a vulnerability
You control a vulnerability to prevent an attack and block a
threat.
How would you control the file server vulnerability?
Our goal: control vulnerabilities
KINDS OF THREATS
Kinds
Interception
an asset becomes lost, unavailable, or unusable
Modification
an unauthorized party (human or not) gains access to an asset
Interruption
of threats:
an unauthorized party changes the state of an asset
Fabrication
an unauthorized party counterfeits an asset
[Pfleeger & Pfleeger]