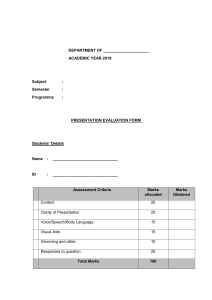
IS224: Advanced Database Systems
Faculty of Science, Technology and Environment
School of Computing, Information and Mathematical Sciences
Final Examination-Semester 2 2017
Face to Face and Online Mode
Duration of Exam: 3 hours + 10 minutes
Reading Time: 10 minutes | Writing Time: 3 hours
QUESTION BOOKLET
INSTRUCTIONS:
1. This exam has two sections:
Section A: 30 marks
Section B: 70 marks
2. Answer all questions.
3. There are 13 pages in this question booklet including this cover page.
4. All answers must be clearly written in the separate Answer Booklet provided.
5. There are 13 pages in the separate Answer Booklet provided.
6. This exam is worth 40% of your overall mark. The minimum mark to pass the final
exam is 16/40%.
Section A – Multiple Choice Questions (30 marks) (Each question has only one answer and is
worth 1 mark)
1.
A ____ distributed database system will support different DBMSs that may even support
different models running under different computer systems.
a.
b.
c.
d.
2.
fully heterogeneous
fully homogeneous
homogeneous
heterogeneous
If a DDBMS exhibits ______ transparency, the user does not need to know that the data
are partitioned-meaning the table’s rows and columns are split vertically or horizontally
and stored among multiple sites.
a. transaction
b. performance
c. distribution
d. heterogeneity
3.
The ____ guarantees that if a portion of a transaction operation cannot be committed; all
changes made at the other sites participating in the transaction will be undone to maintain
a consistent database state.
a.
b.
c.
d.
4.
NULL
BLANK
VOID
NO VALUE
The ___ function returns an error number describing the error in PHP code.
a.
b.
c.
d.
6.
two-phase commit protocol (2PC)
coordinator protocol
write-ahead protocol
When inserting a new record in a table, you must specify the keyword(s) ____ for any
fields in which you do not have a value
a.
b.
c.
d.
5.
DO-UNDO-REDO protocol
mysqli_error()
mysqli_errno()
mysqli_err()
mysqli_error_number()
The function ____ returns the fields in the current row into an indexed array.
a.
b.
c.
d.
mysqli_fetch_assoc()
mysqli_data_seek()
mysqli_fetch_row()
mysqli_fetch_row()
IS224 Final Exam
Page 2 of 13
Semester 2, 2017
7.
The list of records that is returned from a mysqli_query() is a called a ____.
a.
b.
c.
d.
8.
You must be logged in with the ____ account or have sufficient privileges to take away
privileges from another user account.
a.
b.
c.
d.
9.
recordset
resultset
result
result query
base
global
root
source
A(n) ____ has components and relationships but lacks manipulative ability.
a.
b.
c.
d.
entity
attribute
object
variable
10. The object ____ is the set of values that the object's attributes have at a given time.
a.
b.
c.
d.
state
method
message
type
11. An object’s ____ represents the public aspect, while the ____ represents the private
aspect.
a.
b.
c.
d.
method; protocol
protocol; implementation
message; method
instance variable; method
12. Which of the following does NOT describe an abstract data type?
a.
b.
c.
d.
The operations are user-defined
It does not allow direct access to its internal data representation.
It encapsulates its definition.
It allows direct access to its internal data representation.
13. What is typically the first step in a secure transaction?
a.
b.
c.
d.
Authentication
Authorization
Encryption
Decryption
IS224 Final Exam
Page 3 of 13
Semester 2, 2017
14. E-commerce styles CANNOT be classified as ____.
a.
b.
c.
d.
B2B
C2B
G2C
C2G
15. What is the biggest and fastest-growing segment of the e-commerce market?
a.
b.
c.
d.
B2C
B2B
C2C
Intra-business
16. ____ is a protocol used to implement secure communication channels between client and
server computers on the Internet
a.
b.
c.
d.
RSA
TCP/IP
HTTP
SSL
17. When you use a variable in a PHP program, you must be aware of the variable’s ____.
a.
b.
c.
d.
placement
scope
function
statement
18. With the ____________________ statement the program assure that the file is added to
the script only once and halts the processing of the web page and displays an error
message if the include file cannot be found.
a.
b.
c.
d.
require()
include()
include_once()
require_once()
19. The script in the dynamic data section of the Web page template will check the value of
the ____ array to determine which page to display, assuming the name being passed is
‘page’.
a.
b.
c.
d.
$_GET['page']
$_POST['page']
$_PAGE['page']
$SUBMIT['page']
IS224 Final Exam
Page 4 of 13
Semester 2, 2017
20. How many name=value pairs are in the following URL?
<ahref=”http://www.URL.com/TargetPage.php?firstName=Salsabil&l
astName=Nusair&occupation=lecturer “>Link Text</a>
a.
b.
c.
d.
one
two
three
four
21. Whenever you need to work with sessions in a PHP script, you must call the ____
function.
a. set_cookie()
b. session_start()
c. session_begin()
d. Start_session()
22. ____ is a collection of technologies used to access any type of data source and manage the
data through a common interface.
a.
b.
c.
d.
DAO
UDA
ODBC
OLE-DB
23. The ____ object is a specialized object that creates a read-only session with the database
to retrieve data sequentially (forward only) in a very fast manner.
a
b.
c.
d.
Command
DataReader
DataAdapter
DataSet
24. Based on Microsoft’s Component Object Model (COM), ____ is database middleware
that adds object-oriented functionality for access to relational and nonrelational data.
a.
b.
c.
d.
MS-DB
ODBC
COM-DB
OLE-DB
25. The XML metalanguage allows the definition of new ____, such as <ItemPrice>, to
describe the data elements used in an XML document.
a.
b.
c.
d.
tags
schemas
elements
DTDs
IS224 Final Exam
Page 5 of 13
Semester 2, 2017
26. A DBMS facilitates ____.
a.
b.
c.
d.
interpretation and presentation of data in useful formats
destruction of data and information to the right people at the right time
data presentation and data usage monitoring for adequate periods of time
automatic auditing of all data changes
27. What will be the result of combining a string with another data type in PHP
a.
b.
c.
d.
int
float
string
double
28. The ____ is responsible for ensuring database security and integrity.
a.
b.
c.
d.
database programmer
systems analyst
database security officer
data administrator
29. One of the important functions provided by the database ____ is to reserve the resources
that must be used by the database at run time
a.
b.
c.
d.
security component
initialization parameters
authorization manager
administrator
30. In the Oracle Enterprise Manager, a ____ is basically any object created by end users; for
example, tables, views, indexes, stored procedures, and triggers.
a.
b.
c.
d.
component
policy
database object
role
IS224 Final Exam
Page 6 of 13
Semester 2, 2017
Section B – Short and Long Answer Questions (70 Marks)
Question 31
(26 marks)
A. What is the primary difference between homogeneous and heterogeneous distributed
database management system (DDBMS)?
(2 marks)
B. Figure 1 below shows a distributed database environment. Using SQL statements
discuss the difference between Fragmentation and Local Mapping transparency.
(4 marks)
Figure 1
C. What aspects of an object are made public and what aspects are kept private?
(2 mark)
D. List the names of all attributes that belong to the "Magazine" class in figure 2 below.
(3 marks)
Figure 2
E. List and briefly explain one advantage of inheritance in object‐oriented database
system?
(2 marks)
IS224 Final Exam
Page 7 of 13
Semester 2, 2017
F. E-commerce data must be secured from the beginning of a transaction to its end.
Using a diagram illustrate an online purchasing scenario focusing on the principal
mechanisms used to protect the transaction.
(8 marks)
G. Differentiate between symmetric and asymmetric key encryption algorithms?
(2 marks)
H. A key function of e-commerce web sites is their ability to process online payments
for products and/or services. List three technologies that aid in the processing of
electronic payments.
(3 marks)
IS224 Final Exam
Page 8 of 13
Semester 2, 2017
Question 32
(17 marks)
A. What special aspects must you take into account when introducing a DBMS into an
organization?
(3 marks)
B. Based on your experience gained from the IS224 lab exercises, Write the MySQL
command that will create a database named XMen.
(1 mark)
C. Suppose you are the DBA at X-Men Company. Write the MySQL command that
will create a full backup of the XMen database by generating a text file containing
the SQL commands that will create the XMen database together with current data in
the database. Name the text file Xavier.sql, you can store the file in any location of
your
choice.
Your
username
is
mutation,
with
no
password.
(2 marks)
D. A user Mystique remotely logins to MySQL database using putty successfully.
Mystique wants to use the database and executes the command: USE XMen.
Mystique sees the following error message
ERROR 1044 (42000): Access denied for user ' Mystique
'@' localhost ' to database 'XMen'
Why is Mystique seeing the above error message?
(1 mark)
E. Using necessary SQL commands, discuss how you will solve Mystique’s problem so
that she can use the XMen database?
(2 marks)
F. Mystique user has been disloyal to X-Men Company. Write the necessary SQL
command(s) that will remove all access that has been given to mystique user from
XMen database.
(2 marks)
G. A successful data administration strategy requires the continuous enforcement of
policies, procedures, and standards for correct data creation, usage and distribution
within a database. Using an example illustrate the distinction among policies,
standards, and procedures.
(3 marks)
H. In Oracle, what is a datafile?
IS224 Final Exam
(3 marks)
Page 9 of 13
Semester 2, 2017
Question 33
(17 marks)
A. What is the difference between static and dynamic web page?
(2 marks)
B. Explain the steps required to create an open database connectivity (ODBC) data
source name?
(3 marks)
C. Using a diagram illustrate the main components of ADO.NET framework.
(5 marks)
D. Explain why application programming interface (API) is more efficient and faster
than Common Gateway Interface (CGI).
(1 mark)
E. List three functionalities provided by Web application servers?
(3 marks)
F. One advantage of Java Database Connectivity (JDBC) over other database
middleware is that it requires no configuration on the client side. Explain
this advantage.
(1 mark)
G. List two disadvantage of using Extensible Markup Language (XML)?
IS224 Final Exam
Page 10 of 13
(2 marks)
Semester 2, 2017
Question 34
(10 marks)
A. Based on your experience gained from the IS224 lab exercises, Write the PHP script
that will create your database credentials using constants. Assume that it will be saved
in a file named db_credentials.php
(2 marks)
B. Write the code that will include the db_credentials.php file that defines the
database credentials in a file named db_connection.php. Assume both files are
located in the same directory.
(1 mark)
C. Write a function named db_connect that defines the database connection.
(2 marks)
D. Write a function named confirm_db_connect to test if the connection succeeded.
(2 marks)
E. SQL injection is a code injection technique that exploits security vulnerability within
the database layer of an application. This vulnerability can be found when user input is
incorrectly filtered for string literal escape characters embedded in SQL statements.
Write the missing code at line 7 to protect against SQL injection.
(2 marks)
1
2
3
4
5
6
7
8
<?php
// Often these are form values in $_POST
$menu_name = "Today's Widget Trivia";
$position = (int) 4;
$visible = (int) 1;
// Escape all strings
MISSING CODE
?>
F. In PHP what is the difference between $name and $$name?
IS224 Final Exam
Page 11 of 13
(1 mark)
Semester 2, 2017
ID#: _____________________
IS224: Advanced Database Systems
Final Examination – Semester 2, 2017
(Answer Booklet)
Total: 100 marks
Total Pages: 13 pages (including this cover page)
Total Questions: 34
Student ID: __________________________
First Name: __________________________
Surname:
Campus:
__________________________
__________________________
Seat Number: __________________________
Official Use Only
A
B
Total
IS224 Final Exam
Page 1 of 13
Semester 2, 2017
ID#: _____________________
Section A – Multiple Choice (30 marks) (Place a circle around the letter that you have chosen
as the answer to the respective multiple choice question.
IS224 Final Exam
1
A
B
C
D
2
A
B
C
D
3
A
B
C
D
4
A
B
C
D
5
A
B
C
D
6
A
B
C
D
7
A
B
C
D
8
A
B
C
D
9
A
B
C
D
10
A
B
C
D
11
A
B
C
D
12
A
B
C
D
13
A
B
C
D
14
A
B
C
D
15
A
B
C
D
16
A
B
C
D
17
A
B
C
D
18
A
B
C
D
19
A
B
C
D
20
A
B
C
D
21
A
B
C
D
22
A
B
C
D
23
A
B
C
D
24
A
B
C
D
25
A
B
C
D
26
A
B
C
D
27
A
B
C
D
28
A
B
C
D
29
A
B
C
D
30
A
B
C
D
Page 2 of 13
Semester 2, 2017
ID#: _____________________
Section B – Short and Long Answer Questions (70 Marks)
Question 31
(26 marks)
A. What is the primary difference between homogeneous and heterogeneous distributed
database management system (DDBMS)?
(2 marks)
A homogeneous DDBMS integrates the same type of DBMS. For example, all DPs
will be using MySQL DBMS.
A heterogeneous integrates the different types of DBMSs. For example, one DP
could be created using MySQL and another using Oracle.
B. Figure 1 below shows a distributed database environment. Using SQL statements
discuss the difference between Fragmentation and Local Mapping transparency.
(4 marks)
Figure 3
Fragmentation transparency is the highest level of distribution transparency. At this
level, the user will not specify the fragment name or the physical location of the
fragment. If you want to extract all records from TableA (fragment A) and TableB
(fragment B), you may use the following SQL statement:
Select * from Table;
In this SQL statement, we do NOT specify the fragment name or location. The TP,
which will be installed at “Your Computer” knows the name and location of the two
DPs.
IS224 Final Exam
Page 3 of 13
Semester 2, 2017
ID#: _____________________
In Local Mapping transparency, we have to specify both, the location and name of the
fragments. The following SQL statement will be used in case the distributed database
supports only Local Mapping transparency:
Select * from DBServer1.TableA UNION Select * from DBServer2.TableB;
C. What aspects of an object are made public and what aspects are kept private?
(2 mark)
The class’s collection of messages or class protocol represents an object’s public
Aspect, that is, how it is known by other objects as well as end users.
The implementation of the object’s structure and methods constitutes the objects
Private aspect.
D. List the names of all attributes that belong to the "Magazine" class in figure 2 below.
(3 marks)
Figure 4
ItemID
ItemDesc
Volume
E. List and explain briefly one advantage of inheritance in object‐oriented database
system?
(2 marks)
Reusability: Properly defined classes can be used by other classes. This allows
common behavior and data to be shared by many classes.
Extensibility: Allows functionality to be enhanced.
IS224 Final Exam
Page 4 of 13
Semester 2, 2017
ID#: _____________________
F. E-commerce data must be secured from the beginning of a transaction to its end.
Using a diagram illustrate an online purchasing scenario focusing on the principal
mechanisms used to protect the transaction.
(8 marks)
G. Differentiate between symmetric and asymmetric key encryption algorithms?
(2 marks)
symmetric – uses a single key to encrypt and decrypt
asymmetric – use two keys. Public key to encrypt and private key to decrypt.
H.
A key function of e-commerce web sites is their ability to process online payments
for products and/or services. List three technologies that aid in the processing of
electronic payments.
(3 marks)
digital cash
online credit card processing
Electronic wallets
IS224 Final Exam
Page 5 of 13
Semester 2, 2017
ID#: _____________________
Question 32
(17 marks)
A. What special aspects must you take into account when introducing a DBMS into an
organization?
(3 marks)
Technological aspects – DBMS software and hardware
Managerial aspects – Administrative function
Cultural aspects – Corporate resistance to change
B. Based on your experience gained from the IS224 lab exercises, Write the MySQL
command that will create a database named XMen.
(1 mark)
CREATE DATABASE XMen;
C. Suppose you are the DBA at X-Men Company. Write the MySQL command that
will create a full backup of the XMen database by generating a text file containing
the SQL commands that will create the XMen database together with current data in
the database. Name the text file Xavier.sql, you can store the file in any location of
your
choice.
Your
username
is
mutation,
with
no
password.
(2 marks)
mysqldump –u mutation -p XMen > Xavier.sql
D. A user Mystique remotely logins to MySQL database using putty successfully.
Mystique wants to use the database and executes the command: USE XMen.
Mystique sees the following error message
ERROR 1044 (42000): Access denied for user ' Mystique
'@' localhost ' to database 'XMen'
Why is Mystique seeing the above error message?
(1 mark)
That’s because Mystique does not have access to the database, that is, appropriately
privileges has not been granted to her.
E. Using necessary SQL commands, discuss how you will solve Mystique’s problem so
that she can use the XMen database?
(2 marks)
Mystique’s problem can be solved by giving her appropriate access to the XMen
database. Assuming that Mystique will have full access to the database, I’ll execute
the following commands to provide Sally access to XMen database.
GRANT ALL ON XMen.* TO ‘Mystique '@'localhost';
IS224 Final Exam
Page 6 of 13
Semester 2, 2017
ID#: _____________________
F. Mystique user has been disloyal to X-Men Company. Write the necessary SQL
command(s) that will remove all access that has been given to mystique user from
XMen database.
(2 marks)
REVOKE ALL ON XMen.* TO ‘mystique '@'localhost';
G. A successful data administration strategy requires the continuous enforcement of
policies, procedures, and standards for correct data creation, usage and distribution
within a database. Using an example illustrate the distinction among policies,
standards, and procedures.
(3 marks)
Any one of the following for each (consider other possible examples as well)
Policies:
o all users must have a password
o passwords must be changes every six months
Standards:
o A password must have a minimum of 8 characters
o A password must have a maximum of 12 characters.
o Social security numbers, names, birth dates cannot be used as
password.
Procedures:
o To create a password :
1. The user send the DBA a written request for the creation of an
account
2. The DBA approves the request and send it to the computer
operator.
3. The computer operator creates the account, assigns a temporary
password and sends the account information to end user.
4. The end user changes the temporary password
H. In Oracle, what is a datafile?
(3 marks)
o A datafile physically stores the databases data.
o Each datafile is associated with only one tablespace.
o Each datafile can reside in different directories on the hard disk or on
multiple hard disks
IS224 Final Exam
Page 7 of 13
Semester 2, 2017
ID#: _____________________
Question 33
(17 marks)
A. What is the difference between static and dynamic web page?
(2 marks)
Static page – contents remain same
Dynamic page – data changes to reflect current data or a page that is customized to
users preferences.
B. Explain the steps required to create an open database connectivity (ODBC) data
source name?
(3 marks)
An ODBC driver. You must identify the driver to use to connect to the data source.
A DSN name. This is a unique name by which the data source will be known to
ODBC and therefore, to the applications. ODBC offers two types of data sources:
User and System. User data sources are only available to the user. System data
sources are available to all users, including operating system services.
ODBC driver parameters. Most ODBC drivers require some specific parameters in
order to establish a connection to the database. For example if you are using a
DBMS server, you must provide the server name, the database name, and the user
name and password used to connect to the database.
C. Using a diagram illustrate the main components of ADO.NET framework.
(5 marks)
IS224 Final Exam
Page 8 of 13
Semester 2, 2017
ID#: _____________________
D. Explain why application programming interface (API) is more efficient and faster
than Common Gateway Interface (CGI).
(1 mark)
APIs are more efficient than CGI because they are implemented as shared code or as
dynamic-link libraries (DLLs). That means the API is treated as part of the web
server program that is dynamically invoked when needed.
E. List three functionalities provided by Web application servers?
(3 marks)
Any 3 from below:
Connect to and query the BD form a Web page.
Present database data in a Webpage using various formats
Create dynamic Web search pages
Create Web pages to insert, update ,and delete DB data
Enforce referential integrity in the application program logic
Use simple and nested queries and programming logic to represent business
rules.
F. One advantage of Java Database Connectivity (JDBC) over other database
middleware is that it requires no configuration on the client side. Explain
this advantage.
(1 mark)
The JDBC driver is automatically downloaded and installed as part of the Java
applet download. Because Java is a Web-based technology, applications can
connect to a database directly using a simple URL. Once the URL is invoked, the
Java architecture comes into place, the necessary applets are downloaded to the
client (including the JDBC database driver and all configuration information), and
then the applets are executed securely in the client’s runtime environment.
G. List two disadvantage of using Extensible Markup Language (XML)?
IS224 Final Exam
Page 9 of 13
(2 marks)
Semester 2, 2017
ID#: _____________________
Question 34
(10 marks)
G. Based on your experience gained from the IS224 lab exercises, Write the PHP script
that will create your database credentials using constants. Assume that it will be saved
in a file named db_credentials.php
(2 marks)
<?php
define("DB_SERVER", "localhost");
define("DB_USER", "Sxxxxxxxx");
define("DB_PASS", "secretpassword");
define("DB_NAME", "Sxxxxxxxx");
?>
H. Write the code that will include the db_credentials.php file that defines the
database credentials in a file named db_connection.php. Assume both files are
located in the same directory.
(1 mark)
require_once('db_credentials.php');
I. Write a function named db_connect that defines the database connection.
(2 marks)
<?php
function db_connect() {
$connection = mysqli_connect(DB_SERVER,
DB_PASS, DB_NAME);
confirm_db_connect();
return $connection;
}
?>
DB_USER,
J. Write a function named confirm_db_connect to test if the connection succeeded.
(2 marks)
function confirm_db_connect() {
if(mysqli_connect_errno()) {
$msg = "Database connection failed: ";
$msg .= mysqli_connect_error();
$msg .= " (" . mysqli_connect_errno() . ")";
exit($msg);
}
}
K. SQL injection is a code injection technique that exploits security vulnerability within
the database layer of an application. This vulnerability can be found when user input is
incorrectly filtered for string literal escape characters embedded in SQL statements.
Write the missing code at line 7 to protect against SQL injection.
(2 marks)
IS224 Final Exam
Page 10 of 13
Semester 2, 2017
ID#: _____________________
1
2
3
4
5
6
7
8
<?php
// Often these are form values in $_POST
$menu_name = "Today's Widget Trivia";
$position = (int) 4;
$visible = (int) 1;
// Escape all strings
MISSING CODE
?>
$menu_name = mysqli_real_escape_string($connection,
$menu_name);
L. In PHP what is the difference between $name and $$name?
(1 mark)
$name is variable whereas $$name is reference variable/ variable-variable
For example
<?php
$a = "hello";
$hello = "Hello everyone.";
echo $a ."<br />";
echo $hello."<br />";
echo $$a."<br />";
?>
//$$a value = Hello everyone
IS224 Final Exam
Page 11 of 13
Semester 2, 2017
ID#: _____________________
[BLANK PAGE]
IS224 Final Exam
Page 12 of 13
Semester 2, 2017