arrays," IEEE Trans. Comput., vol. C-27, pp. 325
advertisement

504
IEEE TRANSACTIONS ON COMPUTERS, VOL. C-32, NO. 5, MAY 1983
TABLE II
EXPERIMENTAL SUMMARY
DET.RI1TNISTTC AALYSIS
P
MCODLL- I CHF IC- E F' 1 F'2.
P3
EAN AND STEI. IDEVIATIOIN
MEAN AND SI-D.
0DEVIATI'rN
MEAN AND STO . DEVYIATI'N
MEAN AND STO. DEV I AT I'CN
MEAN 'ND rTDE.
DEVI Ii 'N
DEVIATI 'N
MEAN AND ST.
T
7'FATISTi'
It.L. ANAL Y I
A-,r
F P
I-.=
MCDUL I C'I'
. PE, .--
:3.
4.
5
--0,. 0173704
R NN=
C:. 0)I 6:-:,:5
F6 NFF
N
"00-l CI O 15'25"D F'OR ' NN=
"
C7'
51 6"".: 4 F R NN=
.7 6
1) '.
_O. 00(-)17
'lo-)14
f '.I1 4449 FOR NN=
0. C)"'2' 8
(-1.0- 1 5 7'44 FORF: NN=
C
.
u u-"'41
1 1
0 u 5-6364
FOR NN=
4
6
10
7
MEAN AND STO. L'L/I9TI6'N
0 0
'" " 4'":'
MEAN AND ;TDO I)EVl]
-' ()"'u)4) 6',7C 8:36. 0. 004141:-:1
IA'IN
MEAN AND -Tb I'EYIAEITIO'N
- .
'
i)I '!),::o
- - -2
MEAN AND TO DECI/flTD.E4I/TIC
I'
-I
4
MEAN AND -TD.
TODEVIAT1I-IN
C C030E.4C)'4
''
-C. CnoC1)
MEAN ANED c-TO. 1:'EY IATI'-N
-0. 0)''1
''.'041""-91
STATISTICAL ANALY"-. I'7
kNO D
LI C
MEAN ANED
MEAN AND
MEAN AND
MEAN AND
MEAN AND
O'I'-E F 1, F-'
S'TE.
STE.
STD.
FP3,
DE'VIAT I' IN
EDEVIATIO N
DEVIATION
DEVIATI 'N
,
15.
1 6'.
17.
' ''5'-'
--'),
C) 46
C
1 ?. C)11CC
1
C C'-P:- C) I
- 0.h!01
1
0 o0c009A67
-C.00011/47
C) 000''9'06
ol
014
-c.0
0 00098344'
FO R NN=
FOTIR NN=
OF NNF"'NN'I
4
FOR' NN=
O
FoFR NN=
F FR
F' 'R
FOR
'RD
NN=
NN=
NN=
NN=
STO.
STO. DEVIATION
FOR NN=
MEAN AND STD. DEVIATION
-C 000'1201
C. 00009'o' '5 FOR NN=
STATIST'IC AL ANALY .rI
MCIDLL I OlH 'I' E F I, F- FP 1-'
MEAN AND SJO DEVIATION
U Cu)0.0)'-O96
N
0.O"')0:R2'7559W' F`ORN,N=
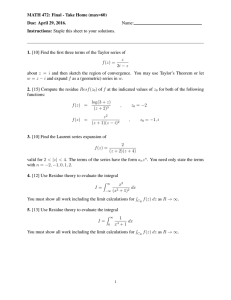
aF ERROR VA5IANCE IN RUTOCALE LGOMITTHM VS C'
cM
-
LL:
D
CZ
_
'fl
U:
,
Cc|
4
6
:
10
[3] G. A. Jullien, "Residue number scaling and other operations using ROM
arrays," IEEE Trans. Comput., vol. C-27, pp. 325-337, Apr. 1978.
[4] W. J. Jenkins, "A highly efficient residue-combinatorial architecture
for digital filters," Proc. IEEE (Lett.), vol. 66, pp. 700-702, June
1978.
[5] C. H. Huang and F. J. Taylor, "High speed DFTs using residue numbers," in Proc. 1980 IEEE Int. Conf. Acoust., Speech, Signal Processing, Denver, CO, Apr. 1980, pp. 238-241.
[6] B. D. Tseng, G. A. Jullien, and W. C. Miller, "Implementation of FFT
structures using the residue number system," IEEE Trans. Comput.,
vol. C-28, Nov. 1979.
[7] F. J. Taylor, "Large moduli multipliers," in Proc. 1980 IEEE Int. Conf
Acoust., Speech, Signal Processing, Denver, CO, Apr. 1980.
[8] S. R. Logan, "A square-summing high speed multiplier," Comput.
Design, June 1971.
[9] H. Nussbaumer, "Digital filters using read-only memories," Electron.
Lett., vol. 11, 1976.
[10] S. M. Pollard, "Implementation of number-theoretic transforms,"
Electron. Lett., vol. 12, July 1976.
[l11 E. Johnson, "A digital quarter square multiplier," IEEE Trans. Com-
CC
LU
put., Mar. 1980.
C
P=
Fig. 3.
,
C0
so
=
[12] F. J. Taylor, "Large VLSI moduli multipliers," presented at the IEEE
Circuits and Syst. Conf., Houston, TX, Apr. 1980.
[131
, "An efficient residue to decimal coxverter," IEEE Trans. Circuits Syst., vol. CAS-28, Dec. 1981.
[14]
, "Large moduli multipliers for signal processing," in Proc. IEEE
Circuits and Syst. Conf., July 1981.
IC/Ml
{255,256,257}
Error variance
as a
function of the constant C.
Single Residue Error Correction in Residue Number Systems
VIJAYA RAMACHANDRAN
RNS multiplier can be designed to
10 MHz for VLSI multipliers).
run
at a 28.5 MHz rate (versus
REFERENCES
[1] N. S. Szabo and R. I. Tanaka, Residue Arithmetic and Its Application
to Computer Technology. New York: McGraw-Hill, 1967.
[2] W. K. Jenkins and B. J. Leon, "The use of residue number system in the
design of finite impulse response filters," IEEE Trans. Circuits Syst.,
vol. CAS-24, pp. 191-201, Apr. 1977.
Abstract-We present a new method to correct single errors in an n-residue
number system through the use of r redundant moduli. The method requires
r2n/rl + 2 recombinations of n residues in the worst case. This is of lower
complexity than any other known method.
Index Terms-Residue codes, single error correction.
Manuscript received February 20, 1981; revised May 1, 1982.
The author is with the Department of Electrical Engineering and Computer
Science, Princeton University, Princeton, NJ 08544.
0018-9340/83/0500-0504$01.00
1983 IEEE
505
IEEE TRANSACTIONS ON COMPUTERS, VOL. C-32, NO. 5, MAY 1983
I. INTRODUCTION
The residue number system was introduced more than 20 years ago
by Svoboda and Valach [6] and Garner [4] as an alternate method
for performing arithmetic operations on a computer. This system
consists of n relatively prime moduli mI, m2, * , m.. Any integer
X, 0 < X < M - 1 (M = l'lmi) is represented in this system by
the n-tuple (Xl, x2, , xn) where xi = X(mod mi), i = 1, 2,... , n.
It is trivial to check that, given X = (x1, x2, *, xn), Y = (Y1,Y2, ,
X + Y = (a1, a2, * , a.) and X Y = (b1, b2, *,
Yn), we can obtain
=
where
bn)
ai (xi + y,) (mod mi) and bi = xi y' (mod mi), i = 1,
2, **,m, provided 0 < X + Y, X Y < M- 1. This is often referred
to as carry-free addition and multiplication.
Any number X can be reconstructed from its residue representation
through the use of either the Chinese Remainder Theorem construction or the mixed radix method (Szabo and Tanaka [7]). We
refer to such a reconstruction of an integer from its residues as a
-
"recombination."
II. SINGLE-ERROR CORRECTION SCHEMES
The earliest work on single-error detection and correction in residue
number systems was reported by Watson [8] and Watson and
Hastings [9]. In this method, two redundant moduli m,+1 and mn+2
(satisfying certain constraints) are added to an n-residue number
system, so that any number X is represented as (x I, x2, *- , xn, xn+ I,
xn+2). The method of correction is to compute the residues xn+ I and
Xn+2 of the number with respect to the two redundant moduli by base
extension [7]. The complexity of this operation is basically that of
reconstructing X from the nonredundant residues. The difference
between the two new residues and the corresponding old ones is
computed as A1 and A2. If both A1 and A2 are zero, no error has occurred; if exactly one of the two is nonzero, the corresponding old
residue is replaced by the new one; if both residues are nonzero, then
they are used to address an error-correction table, which has
0(2; (m,- 1)) entries.
Yau and Liu [ 10] use a modification of the above method in which
they replace the table lookup procedure by additional computation.
The authors append r redundant moduli to an n-residue system and
A I, lAm,, Amn-.l,,
**
compute the following sets: IAmn+,...,*,mn+
JAM 2, Am, . Here the elements of each set are computed by base extension, assuming a residue system containing all moduli except those
represented within the set. As in the method of Watson and Hastings
[9], if the first set has all zero entries, then there is no error, and if
exactly one element in the first set is nonzero, then the corresponding
residue is in error. If more than one element in the first set is nonzero,
then an iterative procedure checks the remaining sets to identify the
incorrect residue.
Barsi and Maestrini [1] use the concept of m, projections to obtain
an interesting method to correct single residue digit errors. Given
moduli mI, m2, , Mn, M = Ili=,, and an integerX in the range
[0, M), the integer Xi = X (mod M/mi) is defined as the m, projection
of X. The authors add r redundant moduli, r > 2, to the n-residue
number system, with MR > max (mi mj), i,j = 1, 2, * * *, n where
MR is the product of the redundant moduli. They prove that if a single
residue digit error occurs in the residue representation of any number
X in the above system, there will be only one m, projection of the
number represented by the new residues which lies in the range [0,
M). This number is obviously the number X, which was represented
by the residue digits before the error occurred. The error-correction
then involves finding the mi projection of the number for i
metJhod
= 1, 2, * , n + r until one such projection falls within the range [0,
M). Mandelbaum [5] has a method of similar complexity (n + r recombinations of n + r - 1 residues in the worst case), but his method
involves the isolation of certain high-order bits in the operands, which
requires either additional processing or additional hardware.
Barsi and Maestrini offer two other methods for error correction
2], [3]. The first method (which is also suggested by Mandelbaum
t5]) uses the concept of a product code where each residue is multiplied by a "generator" A, which then forms the code for the number.
=
-
The second method involves the use of a magnitude index along with
the residue representation. Both of these methods require additional
computation at each residue operation, which appears to be an excessive price to pay for the correction of an occasional error.
III. IMPROVED SCHEME FOR SINGLE-ERROR CORRECTION
It is a well-known result that any error in one residue digit can be
detected and corrected with the use of at least two redundant moduli.
in this section, we present a new proof of this result, and use it to derive
an error-correction method which is of lower complexity than any
previously reported in the literature.
Theorem: Let mlI, m2, * , mn, be n relatively prime moduli in increasing order of magnitude for an n-residue number system with M
= I,_ nm. Let mn+ 1, mn+2, * * *, mn+r be r additional relatively prime
moduli, all of which are greater than mn, so that a number x is represented by the (n + r)-tuple (xI, x, * *, xn+r). Then any error introduced in one residue digit xi, i = 1, 2, , n + r can be corrected,
provided that r > 2.
Proof: Let the kth residue be in error.
In the absence of an error, any n of the n + r residues of x can be
used to reconstruct x. The number of ways this can be done is
(n+r)
|n
Since there is an error in the kth residue, the original x can be reconstructed using any n residues from the n + r - I residues xl, x2,
Xk-l, Xk+ I,*.* Xn+r. Hence, the number of different ways we
can reconstruct the correct value of x in the presence of an error in
the kth residue is (+
n
)
Any reconstruction of x using the kth residue results in an incorrect
value. The important result we prove is the following:
Lemma: Of the (
) ways in which we can reconstruct an
n-I
incorrect value using the kth residue (which has become changed by
an error), no two reconstructions produce the same value, call it x',
with0<x' < M- 1.
Before we prove the lemma, we point out that the proof of the
theorem follows immediately from the lemma. For r
!
2, n+r
)
> n + 1 > 2. Hence, at least two sets of n residues will give the correct
value of x (which, of course, will satisfy 0 < x < M - 1), while from
the lemma, we know that no two sets of n residues will give an incorrect value for x, say x', with 0 < x' < M - 1. Hence, the theorem
is proved.
Proof of Lemma: Assume that there do exist two sets of n residues using the kth residue which produce the same value x', with 0
< x' < M - 1. Let us denote these two sets by S1 and S2. Then SI
u S2 contains at least n + 1 residues. Let us choose n + 1 residues
in this set, say,xi I, xi2,. ., xin,1 where k = il for some 1, 1 - 1, 2, * *,
n + 1. Clearly, we havexi, = x' (mod mi,), I = 1, 2, * *, n + 1. Hence,
these n + 1 residues together produce the reconstructed integer x'.
However, these n + 1 residues, before one of them was changed
by an error, represented an integer x in the range 0 S x < M - 1. It
is a well-known result [7] that the introduction of a single error in a
redundant residue system causes the reconstructed integer to lie
outside the original range. Hence, the original assumption that there
do exist two sets of n residues using the kth residue which produce
x', 0 < x' < M - 1 is false, and the lemma is proved.
From the theorem, we have the following result. In the presence
of a single error in an n + r redundant residue number system,
-
1) (n+r
sets of n residues give back the correct result x,
506
IEEE TRANSACTIONS ON COMPUTERS, VOL.
and
2) of the remaining kl
n-I
J sets of n residues, some results will
lie outside the permitted range, but no two results which lie within
the range will have the same value.
We use this result to devise a single-error correction scheme which
requires, in the worst case, r2n/rl + 2 recombinations of n residues.
The idea behind the scheme is to recombine sets of n residues in such
a way that each residue is left out at least twice. Since exactly one
residue is in error, we ensure that the faulty residue is left out twice,
and hence we reconstruct twice the correct value x. The theorem
ensures us that two reconstructions of the same value x, 0 < x < M
- 1 guarantee that x is the correct value.
We also prove that the result is optimal in the following sense.
Any single-error correction scheme that attempts to correct by the
method of the previous paragraph requires at least (2n/r) + 2 recombinations of n residues.
Proof: At each recombination, we choose n residues from n +
r residues. Hence, at each recombination, we leave out r residues.
After s recombinations, we leave out sr residues. Since any residue
may be in error, we must leave out a total of at least 2(n + r) residues
to guarantee that each residue is left out twice. Hence, we require sr
. 2(n + r), i.e., the number of recombinations s > (2n/r) + 2.
IV. ERROR-CORRECTION SCHEME
Assume that r divides n.
In the first recombination, we choose the n residues rI, r2
, rn
and recombine to obtain x1.
In the second recombination, we replace r1 by rn+X recombine to
obtain x2. We then restore the original n residues r,, r2, , rn.
In the third recombination, we replace r2 by rn+2, r3 by rn+3, * ,
rr by rn+r, and recombine to obtain X3. We then restore the original
residues.
At this stage, each redundant residue rn+ , rn+2, , rn+r has been
left out twice, and some of the other residues have been left out once.
The remaining recombinations are made so that the residues rI, r2,
* , rn are each left out twice, too. This is accomplished as follows.
In the fourth recombination, we replace rr+ by rn+ 1,rr+2 by rn+2,
* * , r2r by rn+r to obtain X4. We then restore the original residues.
In the fifth recombination, we replace r2r+l by rn+ 1, r2r+2 by rn+2,
* r3r by rn+r to obtain X5. We then restore the original residues.
We proceed in this manner until the (n/r) + 2nd recombination
in which we replace rn -r+ 1 by rn+ 1, rn.r+2 by r+2,2* , rn by rn+r to
obtain x(nfr)+2. We then restore the original n residues. At this stage,
each of the residues r1, r2, * * *, rn has been left out exactly once. In
the next n/r recombinations, we will leave out each of rl, r2, .., rn
another time, taking care, however, that we never choose the same
set of n residues twice in our (2n/r) + 2 trials.
In the (n/r) + 3rd recombination, we replace r2 by rn+ 1, r3 by rn+2,
*, rr+I by rn+r to obtain X(n/r)+3. We then restore the original
residues.
In the (n/r) + 4th recombination, we replace rr+2 by rn+ , rr+3 by
rn+2, *. , r2r+ by rn+r to obtain X(nfr)+4. We then restore the original
residues.
We proceed in this manner until the last recombination in which
we replace rn_r+2 by rn+ , rn .r+3 by rn+2, * *, rn by rn+r- 1, and rI
by rn+r to obtain X(2nfr)+2. It is clear that at this stage, every residue
has been left out twice.
At each recombination, we check if the reconstructed integer xi
lies in the range 0 < xi < M - 1. If xi does not lie in the range, then
we discard it. If it does lie in the range, we check if it equals any other
reconstructed xj, which was not discarded. The procedure can be
stopped any time a match is obtained, at which point xi gives the
correct value of x. It is clear that, in the presence of at most one error,
a match will have to be obtained after the (2n/r) + 2 steps outlined
above.
The above method is designed for the case when r divides n. In it,
we made a shift in the residues to be replaced in the (n/r) + 3rd re-
C-32, NO. 5, MAY 1983
combination so that we do not choose the same n residues twice in the
(2n/r) + 2 trials. When r does not divide n, we can simply cycle
around the n residues to correct a single error without taking this
precaution. The resulting procedure requires at most r2n/rl + 2
recombinations of n residues to correct a single error. We illustrate
this by two examples, one for the case when r divides n, and the other
for the case when r does not divide n.
Example 1:
6, r
=3
+2
6.
l= (r, r2, r3, r4, r5, r6)
(r7, r2, r3, r4, r5, r6)
X3 = (r7, r2, r9, r4, r5, r6)
X4 = (ri, r2, r3, r7, r8, r9)
X5 = (ri, r7, r8, r9, r5, r6)
X=
X6
=
(rs, r2, r3, r4, r7, r8).
Example 2:
n
=7, r = 3,
+ 2 = 7.
x= (ri, r2, r3, r4, r5, r6, r7)
X2= (r8, r2, r3, r4, r5, r6, r7)
X3= (r1, rg, rio, r4, r5, r6, r7)
X4 = (rj, r2, r3, r8, r9, r1o, r7)
(rg, rIo, r3, r4, r5, r6, r8)
X6 = (rI, r2, r8, rg, r0o, r6, r7)
X5 =
X7= (rj, r2, r3, r4, r5, r8, r9).
Note, also, that for r > 2n, three recombinations are sufficient to
obtain the correct answer.
V. COMPARISON TO OTHER METHODS
We established in the previous section that the worst case number
of recombinations of n residues required to correct a single error using
the method presented there is r2n/rl + 2. This is a clear improvement
over other known methods. It is not possible to make a direct comparison of our method to the method of Watson and Hastings [9] since
that method trades computation with a very large storage space for
the error-correction table. However, the method of Yau and Liu [10],
which is basically Watson's method with the error-correction table
replaced by computation, requires in the worst case rn/21 + 1 recombinations, each of at least n moduli. On the other hand, the
methods of Mandelbaum [5] and Barsi and Maestrini [1] require n
+ r recombinations of n + r - 1 residues in the worst case. As we
mentioned earlier, other methods require additional processing of
residues at each residue operation, and the total increase in computation time introduced by such correction schemes would depend on
the frequency of errors.
Of the methods mentioned above, the one proposed by Yau and
Liu [ 10] has the lowest complexity. From the results of the previous
section, we see that, for n > 4 and for sufficiently large r, our method
requires a fewer number of recombinations than theirs. Further, each
recombination in our method uses exactly n residues, while their
method uses n + r - 2 residues in all but one of the rn/21 + 1 recombinations. Also, each recombination in their method is accompanied by at least two base extensions, which require additional
computation. Our method requires exactly r2n/rl + 1 recombinations of n moduli, along with a few comparisons.
To summarize, we have presented in this paper a new method to
correct single errors in residue number systems. This method is of
507
IEEE TRANSACTIONS ON COMPUTERS, VOL. C-32, NO. 5, MAY 1983
lower complexity than any known method presented so far, and it will
find use in computer organizations which use the residue system.
ACKNOWLEDGMENT
This work has benefited from discussions with Prof. B. Arden and
Prof. R. Lipton. I would like to thank them for their help and for their
comments on the first version of this paper.
REFERENCES
[1] F. Barsi and P. Maestrini, "Error correcting properties of redundant
residue number systems," IEEE Trans. Comput., vol. C-22, pp.
307-315, Mar. 1973.
, "Error detection and correction by product codes in residue
[2]
number systems," IEEE Trans. Comput., vol. C-23, pp.915-924, Sept.
1974.
[3]
, "Arithmetic codes in residue number systems with magnitude
index," IEEE Trans. Comput., vol. C-27, pp. 1185-1188, Dec. 1978.
[4] H. L. Garner, "The residue number system," IRE Trans. Electron.
Comput., vol. EC-8, pp. 140-147, June 1959.
[5] D. Mandelbaum, "Error correction in residue arithmetic," IEEE Trans.
Comput., vol. C-21, pp. 538-545, June 1972.
[6] A. Svoboda and M. Valach, "Operatorove obvody" (operational circuits), in Stroje na Zpracovani Informaci, Sbornik III, Nakl. CSAV,
Praha, 1955. Translation: Liaison Office, Wright-Patterson AFB,
OH.
[7] N. S. Szabo and R. I. Tanaka, Residue Arithmetic and Its Application
to Computer Technology. New York: McGraw-Hill, 1967.
[81 R. W. Watson, "Error detection and correction and other residue interacting operations in a redundant residue number system," Ph.D.
dissertation, Univ. California, Berkeley, 1965.
[9] R. W. Watson and C. W. Hastings, "Self-checked computation using
residue arithmetic," Proc. IEEE, vol. 54, pp. 1920-1931, Dec. 1966.
[10] S. S.-S. Yau and Y.-C. Liu, "Error correction in redundant residue
number systems," IEEE Trans. Comput., vol. C-22, pp. 5-11, Jan.
1973.
erant computers. Two forms of TSC checkers for m/n codes have been
suggested so far. The first form of an m/n code checker [2] is composed of three TSC subcheckers, namely, an m/n to 1/(n/m) code
translator, a 1 /(n/m) to a k/2k code translator, and finally, a k/2k
TSC checker. An m/n code checker of the second form [5] consists
of an m/n to 1/z (z = 4, 5, 6) code translator, a 1/z to 2/4 code
translator, and finally, a 2/4 to 1/2 code translator. z = 4 for m/(2m
+ 1) codes, z = 5 for 2/n codes, and z = 6 for any other m/n code. It
has been shown in [5] that an m/n TSC checker of the second form
requires less hardware and a smaller test set. A saving in logic complexity and testing complexity of 70-97 percent is reported in [5] in
all cases except for n = 2m and m = 1.
This note presents a new design method of three-level TSC's for
m/(2m ± 1) codes. Reddy in [4] has presented two-level TSC's for
the same class of codes. A two-level TSC according to [4] is composed
of an mr/(2m ± 1) to 1/(2m i I /m) code translator, realized by one
level of AND gates, and a 1/(2m ± 1 /m) to 1/2 code translator realized by two OR gates only. Our three-level TSC checker is composed
of an mr/(2m + 1) to 1/z code translator realized by two levels of
gates where z is a function of m given by (4) below, and a 1/z to 1/2
code translator realized by two OR gates also as in (4). It is shown that
our three-level TSC's require less hardware and a smaller test set
compared to those in [4] at the expense of an extra gate level. Also,
our checkers compare very favorably to those in [5], although the
latter require seven levels of gates. Actually, for m = 3, 4, our
three-level TSC's are the best known.
In the following, we present the design procedure for m/(2m + 1)
codes. The dual of a checker of mr/(2m - 1) codes will be a checker
for m/(2m + 1) codes.
II. DESIGN PROCEDURE
The key factor of our design procedure for a three-level m/(2m
-1) TSC checker is the partitioning of the 2m - 1 input variables
into m blocks Al, A2, * *, A, such that the blocks Al,A2, * Amcontain two variables each, and the block Am has one variable. Let
ni, i = 1, 2, , m denote the number of variables in block Ai. Obviously, n I + n2 + * * + nm = 2m - 1. Let, also, ki denote the number
of variables in Ai that are equal to 1. Then kI + k2 + + km = m
for all input codewords from a m/(2m - 1) code. The input codewords are partitioned into classes, each class denoted by (k1, k2, * ,
ki ) and containing all input codewords that have ki l's in class Ai,
i= 1,2,- -,m.
We define, next, the majority functions T(ki > ji),ji < ni to have
the value of I if and only if the condition inside the parentheses is true.
Obviously, the functions T(ki > 1), i = 1, 2, , m - 1 are implemented each by a two-input OR gate and the T(ki > 2)functions i
= 1, 2, , m- 1 by two-input AND gates.
We define also the product functions PJli2. im ji < n, i = 1, 2,
* , m as
(1)
piJ02*jm = T(kI > ji)T(k2 > i2) ... T(km > im).
Let B be the set of all product functions that correspond to the classes
of all input codewords, i.e.,
B=IPjlj2...jimliI + j2 + *+ jm = m}
(2)
and let $B1, BIuI be a proper partition on B, called product separation
partition. The formation of this partition is the most important phase
of our design procedure and is covered in the next section. It is the
proper partitioning of the product functions into the two blocks B1
and B11 that ensures totally self-checking capabilities.
Lastly, we define the two outputfunctionsf and g on B1 and BlI,
respectively, as follows:
f EP1lj2.m
-
-
Fast and Efficient Totally Self-Checking Checkers for m-out-of(2m ± 1) Codes
C. HALATSIS, N. GAITANIS, AND M. SIGALA
Abstract-This note is concerned with the design of fast totally self-checking
checkers for m-out-of-(2m ± 1) codes. The new method uses only three levels
of gates, and is based on the partitioning of the input lines into m blocks of two
lines per block except for the last block. A first level of two-input AND and OR
gates realizes the majority functions T(k; > 1) and T(k; > 2). These are
combined through AND gates of a second level into the so-called product
functions Pj,j.. b one for each class of input codewords that have jl, j2.
jm l's in the corresponding blocks of the input lines. Finally, two OR gates (third
level) partition the product functions into two. The property of totally selfchecking operation is achieved through the proper partitioning of the product
functions into two classes. This note presents a systematic method of such
partitioning. Also, the note determines the cost of these checkers and compares
them to previous designs.
...
Index Terms-m-out-of-n codes, totally self-checking checkers.
I. INTRODUCTION
The problem of designing totally self-checking (TCS) checkers for
mr-out-of-n (m/n) codes has received considerable attention [1] - [5]
because of the importance of such circuits in the design of fault-tolManuscript received January 1, 1981; revised August 2, 1982.
The authors are with the Digital Systems Laboratory, Computer Center,
NRC "Democritos," Aghia Paraskevi Attikis, Athens, Greece.
0018-9340/83/0500-0507$01.00 ©0 1983 IEEE
-
B1
BIl
(3)