Mean value - Computing Science
advertisement

COMPUTING
SCIENCE
Mean value analysis for a class of PEPA models
N. Thomas
TECHNICAL REPORT SERIES
No. CS-TR-1128
December, 2008
TECHNICAL REPORT SERIES
No. CS-TR-1128
December, 2008
Mean value analysis for a class of PEPA models
Nigel Thomas
Abstract
In this paper a class of closed queueing network is modelled in the Markovian
process algebra PEPA and solved using the classical Mean Value Analysis (MVA).
This approach is attractive as it negates the need to derive the entire state space, and
so certain metrics from large models can be obtained with little computational effort.
The approach is illustrated with two numerical examples.
© 2008 University of Newcastle upon Tyne.
Printed and published by the University of Newcastle upon Tyne,
Computing Science, Claremont Tower, Claremont Road,
Newcastle upon Tyne, NE1 7RU, England.
Bibliographical details
THOMAS, N.
Mean value analysis for a class of PEPA models
[By] N. Thomas.
Newcastle upon Tyne: University of Newcastle upon Tyne: Computing Science, 2008.
(University of Newcastle upon Tyne, Computing Science, Technical Report Series, No. CS-TR-1128)
Added entries
UNIVERSITY OF NEWCASTLE UPON TYNE
Computing Science. Technical Report Series. CS-TR-1128
Abstract
In this paper a class of closed queueing network is modelled in the Markovian process algebra PEPA and solved
using the classical Mean Value Analysis (MVA). This approach is attractive as it negates the need to derive the
entire state space, and so certain metrics from large models can be obtained with little computational effort. The
approach is illustrated with two numerical examples.
About the author
Nigel Thomas joined the School of Computing Science in January 2004 from the University of Durham, where he
had been a lecturer since 1998. His research interests lie in performance modelling, in particular Markov
modelling through queueing theory and stochastic process algebra. Nigel was awarded a PhD in 1997 and an MSc
in 1991, both from the University of Newcastle upon Tyne.Nigel is currently Director of Postgraduate Teaching
within the School of Computing Science and Degree Programme Director for the MSc in Computing Science.
Suggested keywords
PERFORMANCE MODELLING,
MEAN VALUE ANALYSIS,
STOCHASTIC PROCESS ALGEBRA
Mean value analysis for a class of PEPA models
Nigel Thomas
∗
Abstract
In this paper a class of closed queueing network is modelled in the
Markovian process algebra PEPA and solved using the classical Mean
Value Analysis (MVA). This approach is attractive as it negates the need
to derive the entire state space, and so certain metrics from large models
can be obtained with little computational effort. The approach is illustrated with two numerical examples.
1
Introduction
There have been many attempts to find efficient solutions to large stochastic
process algebra models. Many of these have been based on concepts of decomposition originally derived for queueing networks [4]. Applying such approaches
to stochastic process algebra allows them to be understood in a more general
modelling framework. Recently, Thomas [11] showed that a fluid approximation in PEPA based on ordinary differential equations [5] is equivalent to a well
known asymptotic solution for a class of closed queueing network. Traditionally this asymptotic solution was used as a computationally cheap alternative
to mean value analysis [8] for very large populations. As such, it is clear that
the class of model considered in [11] is also amenable to solution by mean value
analysis.
Mean value analysis (MVA) is a method for deriving performance metrics
based on steady state averages directly from the queueing network specification,
without the need to derive any of the underlying Markov chain. As such it is relatively computationally efficient as long as the population size is not excessively
large.
This paper is organised as follows. In the next section a brief overview of
PEPA is given. The subsequent section then defines the class of model under
consideration and gives the MVA solution of this class. Two examples are then
used to illustrate the approach and to explore some numerical results. Finally
some conclusions are drawn and some further work discussed.
2
PEPA
A formal presentation of PEPA is given in [3], in this section a brief informal
summary is presented. PEPA, being a Markovian Process Algebra, only supports actions that occur with rates that are negative exponentially distributed.
∗ School
of Computing Science, Newcastle University, UK Nigel.Thomas@ncl.ac.uk
1
Specifications written in PEPA represent Markov processes and can be mapped
to a continuous time Markov chain (CTMC). Systems are specified in PEPA in
terms of activities and components. An activity (α, r) is described by the type of
the activity, α, and the rate of the associated negative exponential distribution,
r. This rate may be any positive real number, or given as unspecified using the
symbol ⊤. It is important to note that in this paper the unspecified rate is not
used.
The syntax for describing components is given as:
A | (α, r).P | P + Q | P/L | P
⊲
⊳
Q
L
def
A = P gives the constant A the behaviour of the component P . The component (α, r).P performs the activity of type α at rate r and then behaves like P .
The component P + Q behaves either like P or like Q, the resultant behaviour
being given by the first activity to complete.
The component P/L behaves exactly like P except that the activities in the
set L are concealed, their type is not visible and instead appears as the unknown
type τ .
⊳
Concurrent components can be synchronised, P ⊲
Q, such that activities in
L
the cooperation set L involve the participation of both components. In PEPA
the shared activity occurs at the slowest of the rates of the participants and if
a rate is unspecified in a component, the component is passive with respect to
⊳
activities of that type. The shorthand notation P ||Q is used to mean P ⊲
Q
∅
QN
and i=1 Pi is used to mean the parallel composition of the components Pi
where i takes the values 1 through to N , i.e. P1 || . . . ||PN .
In this paper we consider only models which are cyclic, that is, every deriva⊳
Q.
tive of components P and Q are reachable in the model description P ⊲
L
Necessary conditions for a cyclic model may be defined on the component and
model definitions without recourse to the entire state space of the model.
3
A class of closed queueing networks in PEPA
Now consider a model of a closed queueing network of N jobs circulating around
M service stations, denoted 1 to M ; each station is either a queueing station or
an infinite server station. There are Mq queueing stations. At each queueing
station, i, there is an associated queue (bounded at N ) operating a FCFS policy
and Ki servers which serve jobs at rate ri . At each infinite server station,
i, jobs experience a random delay with mean 1/ri . All services are negative
exponentially distributed. When a job completes a service of at a station i,
it will proceed to station j according to some routing probability pij . Let
M = {1, 2, . . . , M } be the set of all queueing stations.
In PEPA a queue station can be modelled as
def
QStationi = (servicei , ri ).QStationi , ∀i ∈ M
Note that ri is always specified as finite, and not ⊤. The infinite server stations
are not represented explicitly.
2
Each job will receive service from a sequence of stations determined by a set
of routing probabilities,
def
Jobi =
M
X
(servicei , pij ri ).Jobj , 1 ≤ i ≤ M
j=1
Where, 0 ≤ pij ≤ 1 and
M
X
pij = 1 , 1 ≤ i ≤ M
j=1
The entire system can then be represented as follows:
!
Y
⊳
QStationi [Ki ] ⊲
Job1 [N ]
L
(1)
∀i∈M
Where L is the set of all action types servicei where i ∈ M.
We now consider the arrival theorem, first derived independently by Sevcik
and Mitrani [9] and Lavenberg and Reiser [7], applied to this class of PEPA
model.
Theorem 3.1 Arrival Theorem. Consider a component Jobi evolving into
its successor derivative, Jobj in a system given by (1). The steady state distribution of the number of components behaving as Jobj at that moment is equal
to the steady state distribution of the number of components behaving as Jobj
in a system without the evolving job.
The arrival theorem is as profound as it is simple and seemingly intuitive.
It consequently gives rise to the well known mean value analysis, whereby the
average behaviour of a system of N components may be derived from the average behaviour of a system of N − 1 components. Therefore it is never necessary
to derive a solution to the full CTMC if we are only concerned with the average behaviour of systems of this kind. This follows from the following set of
relationships, derived following the pattern of Haverkort [2] pp. 241-245.
Theorem 3.1 implies that the average time a component spends in behaviour
Jobj , Wj , where j ∈ M, is given by the average number of Jobj components
in a system with one fewer Jobi , ∀i, components in total, Lj (N − 1) and the
action rate of servicej , rj . If Lj (N − 1) + 1 ≤ Kj and j ∈ M then
Wj =
1
rj
(2)
Otherwise, if Lj (N − 1) + 1 > Kj and j ∈ M then
Wj =
Lj (N − 1) + 1
Kj rj
(3)
Clearly, if j ∈
/ M then Wj is a constant, given as Wj = 1/rj .
We now need to compute a quantity referred to as the visit count, denoted
as Vi . The visit count is the number of times an action of type servicei is
performed, relative to the number of times some reference action serviceI is
3
performed, where 1 ≤ I ≤ M .We can compute the visit count from the routing
probabilities pij . Define the probability that a component will evolve from Jobi
to Jobj , without revisiting Jobi , as follows:
Pij (σ) = pij +
X
pik Pkj (σ)
∀k∈σ
/
For convenience define the shorthand,
Pij = Pij ({i, j})
By definition, Pii = 1. Clearly the system is irreducible if
Pij > 0 ∀i, j , i 6= j
Now,
Vi =
PIi
, ∀i 6= I
PiI
and VI = 1.
Given the quantity Vj , we can now compute the average response time per
passage for queueing station j (j ∈ M). When Lj (N − 1) + 1 > Kj ,
Ŵj =
Vj Lj (N − 1) + 1
Kj rj
Clearly, for j ∈
/ M and Lj (N − 1) + 1 ≤ Kj ,
Ŵj =
Vj
rj
From Little’s theorem we know that
Lj (N ) = Xj (N )Wj (N ) = X(N )Vj Wj (N ) = X(N )Ŵj (N )
(4)
Where Xj (N ) is the observed rate of activity servicej when the population size
is N , and X(N ) is the sum of all possible Xj (N )′ s.
Summing (4) over all behaviours Jobi , i = 1, 2, . . . , M gives,
M
X
Lj (N ) = X(N )
PM
j=1
Ŵj = X(N )Ŵ = N
j=1
j=1
where Ŵ (N ) =
M
X
Ŵj (N ). Thus,
X(N ) =
N
Ŵ (N )
Hence, with Little’s law applied at node j,
Lj (N ) =
=
Xj (N )Wj (N ) = X(N )Vj Wj (N )
N
Ŵj (N )
Ŵ (N )
4
(5)
(6)
We are now in a position to calculate Lj (N ) for any value of N if we can
calculate Lj (1). A solitary Jobi component will never compete for cooperation
over the actions in L, and so will experience a delay of 1/ri in each derivative
Jobi . Hence, the average number of components behaving as Jobj when N = 1,
Lj (1) is given by the proportion of time a component spends in that behaviour.
Lj (1) =
rj
Vj
PM
(7)
Vi
i=1 ri
We now apply the following iterative solution.
1. Calculate Lj (1) for j = 1, 2, . . . M , using (7).
2. n = 2
3. Compute Wj (n) for j = 1, 2, . . . M , using (2) and (3) and Lj (n − 1) from
1 above.
PM
4. Compute W (n) = j=1 Wj (n).
5. Compute Lj (i) for j = 1, 2, . . . M , using (6) and W (n) from 4 above.
6. Increment n.
7. If n ≤ N return to step 3 else end.
Clearly this solution is not complicated to implement. For a system of M
nodes and N jobs it is necessary to compute 2.(M + 1)N distinct quantities.
Hence, this will only be costly when N is extremely large.
4
Example 1: A three node closed queueing network
Consider the following PEPA specification of a simple closed queueing network
def
N ode1
= (service1 , ξ).N ode1
N ode2
= (service2 , µ).N ode2
N ode3
= (service3 , η).N ode3
def
def
def
Request1
= (service1 , ξ).Request2
Request2
= (service2 , pµ).Request1 + (service2 , (1 − p)µ).Request3
Request3
= (service3 , η).Request1
def
def
The entire system is then specified as
(N ode1 [K1 ]||N ode2 [K2 ]||N ode3 [K3 ])
⊲
⊳
)
(
service1 ,service2
service3
Request1 [N ]
This system depicts a three node closed queueing network where all three
nodes are queueing stations. After completing service at node 1, all requests
5
proceed to node 2. Following service at node 2, a proportion of requests, p, will
return to node 1, whilst the remainder will be directed to node 3. All requests
completing service at node 3 will return to node 1.
In this example it is a simple matter to compute the visit count for each
node.
V1
= 1
V2
V3
= 1
= p
There are clearly many possible approaches to implementing the iterative
solution given above. For convenience this model has been solved in an Excel
spreadsheet. Solutions with population sizes of over 10000 have been derived
without any problems, although clearly a more efficient implementation is desirable for larger N when a range of parameter values are being considered.
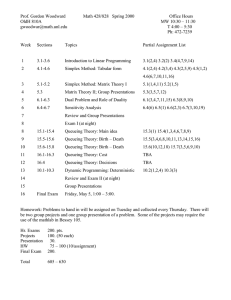
Figure 1 shows the average queue size at node 3 varied with population size
N for various values of p.
100
90
p=0.4
p=0.5
p=0.6
80
70
60
L3(N)
50
40
30
20
10
0
0
5
10 15 20 25 30 35 40 45 50 55 60 65 70 75 80 85 90 95 100
N
Figure 1: Average queue length at node 3 varied with population size (ξ = µ =
10, η = 5)
When p = 0.5 all three nodes have the same load, hence their queue sizes
will be equal, i.e. Li = N/3. Obviously, if p is less than 0.5 then it will have a
lower load than the other two nodes, hence it will have a smaller average queue
length. In fact, the average queue length at node 3 will tend to a fixed value
(L3 (N ) → 4 as N → ∞ when p = 0.4). Conversely, if p > 0.5 then the third
node will become the bottleneck of the system, and the majority of jobs will be
queueing there. In the case p = 0.6, the average queue length at node 3 will
tend to N − 10.
6
5
Example 2: A Secure Key Distribution Centre
Consider a model of the classic Needham-Schroeder key distribution protocol
(taken from [13]) specified as follows:
KDC
def
Alice0
def
Alice1
def
Alice2
def
Alice3
def
Alice4
def
Alice5
def
= (response, rp ).KDC
= (request, rq ).Alice1
= (response, rp ).Alice2
= (sendBob, rB ).Alice3
= (sendAlice, rA ).Alice4
= (conf irm, rc ).Alice5
= (usekey, ru ).Alice
The system is then defined as:
KDC[K] response
⊲
⊳ Alice0[N ]
Where, K is the number of KDC’s and N is the number of client pairs (Alices’s).
Clearly there is no branching, and so Vi = 1, ∀i. Furthermore there is only
one queueing station, so this is always the bottleneck of the system unless K is
large relative to N .
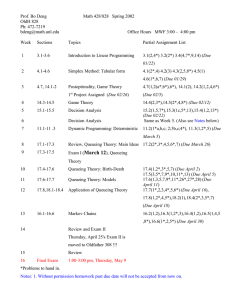
Figure 2 shows the average response time at the KDC, WKDC for this system
when there is one server for various service rates. Clearly, when the service rate
is smaller, the response time is larger and its rate of increase is larger.
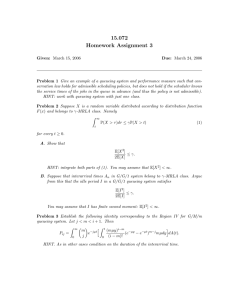
Figure 3 shows the average queue length at the KDC, LKDC for this system
when there is either one fast server or K slower servers. When the population
size is large (N > 30 in this case) the KDC becomes saturated and there is
consequently no difference in the service rate offered between the two cases
shown. However, when N is smaller, there will be periods where one or more
of the K servers will be idle, thus reducing the overall service capacity offered.
Hence, for smaller N , a single fast server will out perform multiple slower servers
with the same overall capacity.
6
Conclusions and further work
This paper demonstrates the solution of a class of PEPA models using classical
Mean Value Analysis [8]. This gives a relatively computationally cheap method
for solving large models without need to derive the state space of the underlying
Markov chain. Clearly the approach is limited in both the metrics that can be
derived and also the class of model that is considered. The former limitation is
a feature of mean value analysis. However, the class of model could be extended
in a number of ways. Mean value analysis applies to multiple classes of jobs in
closed queueing network. Therefore it should be straightforward to define a class
of model with different groups of components, each with potentially different
action rates and routing probabilities. Furthermore, it should also be possible
to consider that the same group of component may compete for a resource
7
11
10
9
rp=1
8
rp=2
7
rp=4
6
WKDC
5
4
3
2
1
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
N
Figure 2: Average response time at the KDC varied with population size (rq =
rB = rA = rc = 1, ru = 1.1, K = 1)
12
10
K=4, rp=1
8
K=1, rp=4
LKDC
6
4
2
0
1
3
5
7
9
11
13
15
17
19
21
23
25
27
29
31
N
Figure 3: Average queue length at KDC varied with population size (rq = rB =
rA = rc = 1, ru = 1.1)
(queueing station) over more than one action type in more than one derivative.
These possibilities are left for further exploration, since as yet we do not have
applications for such solutions.
8
Acknowledgements
The example of the Key Distribution Centre is based on earlier work by Zhao
and Thomas [13] and the author would like to acknowledge the contribution of
Yishi Zhao in inspiring this current work.
References
[1] G. Clark and S. Gilmore and J. Hillston and N. Thomas, Experiences with
the PEPA Performance Modelling Tools, IEE Proceedings - Software, pp.
11-19, 146(1), 1999.
[2] B. Haverkort, Performance of Computer Communication Systems: A model
Based Approach, Wiley, 1998.
[3] J. Hillston, A Compositional Approach to Performance Modelling, Cambridge University Press, 1996.
[4] J. Hillston, Exploiting Structure in Solution: Decomposing Compositional
Models, in: E. Brinksma et al, Lectures on Formal Methods and Performance Analysis, LNCS 2090, Springer-Verlag, 2003.
[5] J. Hillston, Fluid flow approximation of PEPA models, in: Proceedings of
QEST’05, pp. 33-43, IEEE Computer Society, 2005.
[6] I. Mitrani, Probabilistic Modelling, Cambridge University Press, 1998.
[7] S. Lavenberg and M. Reiser, Stationary state space probabilities at arrival
instants for closed queueing networks with multiple types of customers,
Journal of Applied Probability, 17)(4), pp. 1048-1061, 1980.
[8] M. Reiser and S. Lavenberg, Mean value analysis of closed multichain
queueing networks, JACM, 22(4), pp. 313-322, 1980.
[9] K. Sevcik and I. Mitrani, The distribution of queueing network states at
input and output instants, JACM, 28(2), pp. 358-371, 1981.
[10] W. Stallings, Cryptography and Network Security: Principles and Practice,
Prentice Hall, 1999.
[11] N. Thomas, Using ODEs from PEPA models to derive asymptotic solutions
for a class of closed queueing networks, Technical Report CS-TR-1129,
School of Computing Science, Newcastle University, 2008.
[12] N. Thomas and Y. Zhao, Fluid flow analysis of a model of a secure key distribution centre, in: Proceedings 24th Annual UK Performance Engineering
Workshop, Imperial College London, 2008.
[13] Y. Zhao and N. Thomas, Approximate solution of a PEPA model of a
key distribution centre, in: Performance Evaluation - Metrics, Models and
Benchmarks: SPEC International Performance Evaluation Workshop, pp.
44-57, LNCS 5119, Springer-Verlag, 2008.
9