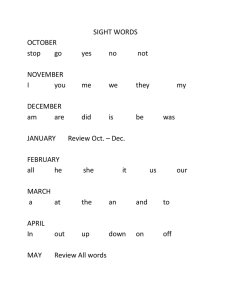
2015 TC Annual Index
advertisement

IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 0 2015 Index IEEE Transactions on Computers Vol. 64 This index covers all technical items — papers, correspondence, reviews, etc. — that appeared in this periodical during 2015, and items from previous years that were commented upon or corrected in 2015. Departments and other items may also be covered if they have been judged to have archival value. The Author Index contains the primary entry for each item, listed under the first author's name. The primary entry includes the coauthors’ names, the title of the paper or other item, and its location, specified by the publication abbreviation, year, month, and inclusive pagination. The Subject Index contains entries describing the item under all appropriate subject headings, plus the first author’s name, the publication abbreviation, month, and year, and inclusive pages. Note that the item title is found only under the primary entry in the Author Index. AUTHOR INDEX A Abdulrahman, E. A. H., and Reyhani-Masoleh, A., New Regular Radix-8 Scheme for Elliptic Curve Scalar Multiplication without Pre-Computation; TC Feb. 2015 438-451 Acacio, M.E., see Ros, A., TC June 2015 1534-1547 Adikari, J., see Rajapaksha, N., TC Sept. 2015 2708-2715 Ahmed, A.M., see Xia, F., TC July 2015 1857-1869 Ahn, J., Jin, S., and Huh, J., Fast Two-Level Address Translation for Virtualized Systems; TC Dec. 2015 3461-3474 Ahn, J., see Jin, S., TC Oct. 2015 2833-2846 Akbas, M.I., Erol-Kantarci, M., and Turgut, D., Localization for Wireless Sensor and Actor Networks with Meandering Mobility; TC April 2015 1015-1028 Al Ridhawi, Y., and Karmouch, A., QoS-Based Composition of Service Specific Overlay Networks; TC March 2015 832-846 Al-Qawasmeh, A.M., Pasricha, S., Maciejewski, A.A., and Siegel, H.J., Power and Thermal-Aware Workload Allocation in Heterogeneous Data Centers; TC Feb. 2015 477-491 Alawneh, S., Dragt, R., Peters, D., Daley, C., and Bruneau, S., Hyper-Real-Time Ice Simulation and Modeling Using GPGPU; TC Dec. 2015 3475-3487 Aldea, M., see Burns, A., TC May 2015 1241-1253 Alelaiwi, A., see Li, J., TC Dec. 2015 3569-3579 Alfaro, F.J., see Andujar-Munoz, F.J., TC Oct. 2015 2847-2861 Alizadeh, B., see Ghandali, S., TC June 2015 1579-1593 Alizadeh, B., Behnam, P., and Sadeghi-kohan, S., A Scalable Formal Debugging Approach with Auto-Correction Capability Based on Static Slicing and Dynamic Ranking for RTL Datapath Designs; TC June 2015 15641578 Alvarez, L., Vilanova, L., Gonzalez, M., Martorell, X., Navarro, N., and Ayguade, E., Hardware–Software Coherence Protocol for the Coexistence of Caches and Local Memories; TC Jan. 2015 152-165 Amaral, J. N., see Wang, A., TC Jan. 2015 233-246 Andujar-Munoz, F.J., Villar-Ortiz, J.A., Sanchez, J.L., Alfaro, F.J., and Duato, J., N-Dimensional Twin Torus Topology; TC Oct. 2015 2847-2861 Anyanwu, U. K., see Di Francesco, P., TC April 2015 912-924 Assi, C., see Gu, F., TC Aug. 2015 2353-2366 Athikulwongse, K., see Kim, D. H., TC Jan. 2015 112-125 Atienza, D., see Ranieri, J., TC Nov. 2015 3197-3209 Atiquzzaman, M., see Yaakob, N., TC June 2015 1594-1606 Au, M.H., see Yuen, T.H., TC Sept. 2015 2595-2608 Ayguade, E., see Alvarez, L., TC Jan. 2015 152-165 Azarderakhsh, R., see Jarvinen, K., TC Sept. 2015 2421-2432 Azimi, M., see Lee, J., TC Nov. 2015 3167-3180 Bagherzadeh, N., see Eghbal, A., TC Dec. 2015 3591-3604 Bahn, H., see Lee, E., TC May 2015 1349-1360 Baldoni, R., Bonomi, S., Platania, M., and Querzoni, L., Efficient Notification Ordering for Geo-Distributed Pub/Sub Systems; TC Oct. 2015 2796-2808 Bandyopadhyay, B., see Sarkar, S., TC Oct. 2015 2912-2925 Banerjee, T., Sahni, S., and Seetharaman, G., PC-TRIO: A Power Efficient TCAM Architecture for Packet Classifiers; TC April 2015 1104-1118 Banerjee-Mishra, T., and Sahni, S., Pubsub: An Efficient Publish/Subscribe System; TC April 2015 1119-1132 Banik, S., see Sarkar, S., TC June 2015 1647-1657 Bao, W., see Wang, J., TC Sept. 2015 2545-2558 Bao, Y., see Chen, T., TC May 2015 1442-1455 Bardhan, S., and Menasce, D.A., Predicting the Effect of Memory Contention in Multi-Core Computers Using Analytic Performance Models; TC Aug. 2015 2279-2292 Barnawi, A., see Yao, H., TC Dec. 2015 3515-3527 Barnawi, A., see Lukic, M., TC May 2015 1416-1428 Barnawi, A., see Gu, L., TC July 2015 2049-2059 Barnawi, A., see Zeng, D., TC July 2015 1819-1829 Barton, C., see Wang, A., TC Jan. 2015 233-246 Basak, A., see Wang, X., TC Aug. 2015 2226-2238 Bathen, L.A., see Gottscho, M., TC May 2015 1483-1496 Bayrak, A. G., Regazzoni, F., Novo, D., Brisk, P., Standaert, F.-X., and Ienne, P., Automatic Application of Power Analysis Countermeasures; TC Feb. 2015 329-341 Behnam, P., see Alizadeh, B., TC June 2015 1564-1578 Beldianu, S. F., and Ziavras, S. G., Performance-Energy Optimizations for Shared Vector Accelerators in Multicores; TC March 2015 805-817 Benini, L., see Dehyadegari, M., TC Aug. 2015 2132-2144 Bergmann, N.W., see Tang, Y., TC May 2015 1254-1267 Bernasconi, A., Ciriani, V., Trucco, G., and Villa, T., Using Flexibility in P-Circuits by Boolean Relations; TC Dec. 2015 3605-3618 Bertossi, A.A., Diodati, D., and Pinotti, C.M., Storage Placement in Path Networks; TC April 2015 1201-1207 Bhuiyan, M. Z. A., Wang, G., Cao, J., and Wu, J., Deploying Wireless Sensor Networks with Fault-Tolerance for Structural Health Monitoring; TC Feb. 2015 382-395 Bhuiyan, M.Z.A., Wang, G., and Vasilakos, A.V., Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks; TC July 2015 19681982 Bhunia, S., see Wang, X., TC Aug. 2015 2226-2238 Bian, K., see Chen, L., TC Oct. 2015 2968-2980 Bini, E., The Quadratic Utilization Upper Bound for Arbitrary Deadline RealTime Tasks; TC Feb. 2015 593-599 Bochard, N., see Lubicz, D., TC April 2015 1191-1200 Bonomi, S., see Baldoni, R., TC Oct. 2015 2796-2808 Boucheneb, H., see Randolph, A., TC April 2015 1074-1089 Boukerche, A., see Rezende, C., TC March 2015 614-626 Briceno, L.D., see Khemka, B., TC Aug. 2015 2394-2407 Brisk, P., see Bayrak, A. G., TC Feb. 2015 329-341 Brown, A.D., Furber, S.B., Reeve, J.S., Garside, J.D., Dugan, K.J., Plana, L.A., and Temple, S., SpiNNaker—Programming Model; TC June 2015 17691782 Bruck, J., see Lee, D.T., TC Dec. 2015 3376-3388 Bruneau, S., see Alawneh, S., TC Dec. 2015 3475-3487 Bu, K., see Liu, X., TC Nov. 2015 3265-3277 Bunescu, R., see DiTomaso, D., TC Dec. 2015 3555-3568 Burns, A., Gutierrez, M., Aldea, M., and Harbour, M.G., A Deadline-Floor Inheritance Protocol for EDF Scheduled Embedded Real-Time Systems with Resource Sharing; TC May 2015 1241-1253 B Badache, N., see Lasla, N., TC Aug. 2015 2103-2118 Bader, D.A., see Chai, Y., TC Nov. 2015 3304-3316 Baek, S., Lee, H.G., Nicopoulos, C., Lee, J., and Kim, J., Size-Aware Cache Management for Compressed Cache Architectures; TC Aug. 2015 23372352 C Cai, C., see Chen, D., TC March 2015 707-719 Cai, S., see Luo, C., TC July 2015 1830-1843 Cao, J., see Bhuiyan, M. Z. A., TC Feb. 2015 382-395 1 Cao, J., see Yang, L., TC Aug. 2015 2253-2266 Causapruno, G., Vacca, M., Graziano, M., and Zamboni, M., Interleaving in Systolic-Arrays: A Throughput Breakthrough; TC July 2015 1940-1953 Cha, S., see Jin, S., TC Oct. 2015 2833-2846 Chai, C., see Shih, Y., TC Nov. 2015 3079-3090 Chai, Y., Du, Z., Qin, X., and Bader, D.A., WEC: Improving Durability of SSD Cache Drives by Caching Write-Efficient Data; TC Nov. 2015 3304-3316 Chakraborty, C., see Sarkar, S., TC Oct. 2015 2912-2925 Chakraborty, D., Mancillas-Lopez, C., and Sarkar, P., STES: A Stream Cipher Based Low Cost Scheme for Securing Stored Data; TC Sept. 2015 26912707 Chakraborty, S., see Dietrich, B., TC Jan. 2015 260-273 Chan, A., see Liu, X., TC Nov. 2015 3265-3277 Chandler, H., see Shen, H., TC Oct. 2015 2953-2967 Chang, C., see Chen, L., TC Dec. 2015 3417-3429 Chang, C., Cheng, J., Huang, T., Huang, X., Lee, D., and Chen, C., Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching; TC Dec. 2015 3404-3416 Chang, E., Hsin, H.-K, Chao, C.-H., Lin, S.-Y., and Wu, A.-Y., Regional ACOBased Cascaded Adaptive Routing for Traffic Balancing in Mesh-Based Network-on-Chip Systems; TC March 2015 868-875 Chang, E., see Hsin, H., TC Aug. 2015 2119-2131 Chang, G., see Chen, C., TC June 2015 1622-1632 Chang, Y., see Tsao, C., TC Dec. 2015 3444-3460 Chang, Y.-H., see Wang, J., TC April 2015 925-940 Chantem, T., see Hong, S., TC July 2015 1983-1997 Chao, C.-H., see Chang, E., TC March 2015 868-875 Chatterjee, S., Karabina, K., and Menezes, A., Fault Attacks on Pairing-Based Protocols Revisited; TC June 2015 1707-1714 Chebira, A., see Ranieri, J., TC Nov. 2015 3197-3209 Chen, B., see Le, Y., TC Jan. 2015 19-31 Chen, C., see Chang, C., TC Dec. 2015 3404-3416 Chen, C., see Hsieh, J., TC Dec. 2015 3348-3361 Chen, C., see Zhu, X., TC Dec. 2015 3389-3403 Chen, C., see Wen, S., TC March 2015 640-653 Chen, C., Shih, H., Wu, C., Lin, C., Chiu, P., Sheu, S., and Chen, F.T., RRAM Defect Modeling and Failure Analysis Based on March Test and a Novel Squeeze-Search Scheme; TC Jan. 2015 180-190 Chen, C., Chang, G., and Hsieh, S., Conditional (t,k)-Diagnosis in Graphs by Using the Comparison Diagnosis Model; TC June 2015 1622-1632 Chen, C., see Li, D., TC Sept. 2015 2534-2544 Chen, D., Li, X., Wang, L., Khan, S. U., Wang, J., Zeng, K., and Cai, C., Fast and Scalable Multi-Way Analysis of Massive Neural Data; TC March 2015 707-719 Chen, F.T., see Chen, C., TC Jan. 2015 180-190 Chen, G., see Yu-Chun, C., TC Oct. 2015 2730-3740 Chen, G., see Zheng, Z., TC July 2015 2071-2083 Chen, H., see Qian, J., TC Dec. 2015 3500-3514 Chen, J., see Zhang, T., TC June 2015 1522-1533 Chen, J., see Lu, S., TC May 2015 1230-1240 Chen, J., see Menzel, M., TC May 2015 1336-1348 Chen, J., see Zhang, X., TC Aug. 2015 2293-2307 Chen, J., see Leu, J., TC Sept. 2015 2586-2594 Chen, J., see Liu, C., TC Sept. 2015 2609-2622 Chen, K., see Shen, H., TC Feb. 2015 518-532 Chen, K., and Shen, H., Maximizing P2P File Access Availability in Mobile Ad Hoc Networks though Replication for Efficient File Sharing; TC April 2015 1029-1042 Chen, L., Cui, A., and Chang, C., Design of Optimal Scan Tree Based on Compact Test Patterns for Test Time Reduction; TC Dec. 2015 3417-3429 Chen, L., see Wang, W., TC March 2015 698-706 Chen, L., see Li, C., TC March 2015 882-883 Chen, L., and Bian, K., The Telephone Coordination Game Revisited: From Random to Deterministic Algorithms; TC Oct. 2015 2968-2980 Chen, P., see Wang, C., TC May 2015 1296-1310 Chen, R., Qin, Z., Wang, Y., Liu, D., Shao, Z., and Guan, Y., On-Demand Block-Level Address Mapping in Large-Scale NAND Flash Storage Systems; TC June 2015 1729-1741 Chen, T., Guo, Q., Temam, O., Wu, Y., Bao, Y., Xu, Z., and Chen, Y., Statistical Performance Comparisons of Computers; TC May 2015 1442-1455 Chen, W., Xu, L., Li, G., and Xiang, Y., A Lightweight Virtualization Solution for Android Devices; TC Oct. 2015 2741-2751 Chen, X., see Li, J., TC Dec. 2015 3569-3579 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Chen, X., see Li, J., TC Feb. 2015 425-437 Chen, X., see Wang, J., TC Nov. 2015 3293-3303 Chen, Y., see Cui, Y., TC Jan. 2015 166-179 Chen, Y., see Chen, T., TC May 2015 1442-1455 Chen, Y., see Saifullah, A., TC May 2015 1361-1374 Chen, Y., see Wang, C., TC May 2015 1296-1310 Chen, Y., see Li, Q., TC Aug. 2015 2169-2181 Cheng, H., see Yang, L., TC Aug. 2015 2253-2266 Cheng, J., see Chang, C., TC Dec. 2015 3404-3416 Cheng, S., Ku, L., and Hsiu, P., Dynamic Antenna Management for Uplink Energy Efficiency on 802.11n Mobile Devices; TC Oct. 2015 2767-2780 Cheng, W., see Le, Y., TC Jan. 2015 19-31 Cheng, X., see Le, Y., TC Jan. 2015 19-31 Cheng, Y.-C., and Wang, P.-C., Packet Classification Using Dynamically Generated Decision Trees; TC Feb. 2015 582-586 Cheung, R.C., see Wang, C., TC May 2015 1296-1310 Chinneck, J.W., see Ibrahim, W., TC May 2015 1217-1229 Chiu, P., see Chen, C., TC Jan. 2015 180-190 Cho, B.Y., see Kim, K., TC Oct. 2015 2862-2874 Cho, S., see Maddah, R., TC March 2015 847-861 Choi, H., see Kim, D. H., TC Jan. 2015 112-125 Choi, J., see Park, H., TC March 2015 720-732 Chou, C., see Yu-Chun, C., TC Oct. 2015 2730-3740 Chung, C., see Wang, Z., TC Dec. 2015 3430-3443 Chung, J., and Kim, L., Bit-Width Optimization by Divide-and-Conquer for Fixed-Point Digital Signal Processing Systems; TC Nov. 2015 3091-3101 Chung, S. W., see Kim, J. M., TC Jan. 2015 286-292 Chung, S.W., see Kong, J., TC Sept. 2015 2460-2475 Cintra, M., see Ros, A., TC June 2015 1534-1547 Cintra, R.J., see Rajapaksha, N., TC Sept. 2015 2708-2715 Ciriani, V., see Bernasconi, A., TC Dec. 2015 3605-3618 Condo, C., Masera, G., and Montuschi, P., Unequal Error Protection of Memories in LDPC Decoders; TC Oct. 2015 2981-2993 Constantinides, G. A., see Jerez, J. L., TC Feb. 2015 303-315 Conti, M., see Sadiq, U., TC Aug. 2015 2308-2322 Cui, A., see Chen, L., TC Dec. 2015 3417-3429 Cui, T., Jin, C., and Kong, Z., On Compact Cauchy Matrices for SubstitutionPermutation Networks; TC July 2015 2098-2102 Cui, Y., Wang, Y., Chen, Y., and Shi, Y., Requester-Based Spin Lock: A Scalable and Energy Efficient Locking Scheme on Multicore Systems; TC Jan. 2015 166-179 D Dai, Y., see Levitin, G., TC April 2015 1043-1057 Daley, C., see Alawneh, S., TC Dec. 2015 3475-3487 Dang, C, see Guo, S., TC March 2015 747-762 Dargie, W., A Stochastic Model for Estimating the Power Consumption of a Processor; TC May 2015 1311-1322 DaSilva, L. A., see Di Francesco, P., TC April 2015 912-924 Datta, K., Sengupta, I., and Rahaman, H., A Post-Synthesis Optimization Technique for Reversible Circuits Exploiting Negative Control Lines; TC April 2015 1208-1214 Dehyadegari, M., Marongiu, A., Kakoee, M.R., Mohammadi, S., Yazdani, N., and Benini, L., Architecture Support for Tightly-Coupled Multi-Core Clusters with Shared-Memory HW Accelerators; TC Aug. 2015 2132-2144 Demmel, J., and Nguyen, H.D., Parallel Reproducible Summation; TC July 2015 2060-2070 Deniz, E., Sen, A., Kahne, B., and Holt, J., MINIME: Pattern-Aware Multicore Benchmark Synthesizer; TC Aug. 2015 2239-2252 Di, S., Kondo, D., and Wang, C., Optimization of Composite Cloud Service Processing with Virtual Machines; TC June 2015 1755-1768 Di Francesco, P., McGettrick, S., Anyanwu, U. K., OSullivan, J. C., MacKenzie, A. B., and DaSilva, L. A., A Split MAC Approach for SDR Platforms; TC April 2015 912-924 Dietrich, B., Goswami, D., Chakraborty, S., Guha, A., and Gries, M., Time Series Characterization of Gaming Workload for Runtime Power Management; TC Jan. 2015 260-273 Dimitrov, V., see Jarvinen, K., TC Sept. 2015 2421-2432 Dimitrov, V.S., see Rajapaksha, N., TC Sept. 2015 2708-2715 Ding, Z.J., see Wu, Y., TC Sept. 2015 2447-2459 Diodati, D., see Bertossi, A.A., TC April 2015 1201-1207 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 DiTomaso, D., Kodi, A.K., Louri, A., and Bunescu, R., Resilient and Power-Efficient Multi-Function Channel Buffers in Network-on-Chip Architectures; TC Dec. 2015 3555-3568 Dong, Z., see Salehin, K. M., TC Jan. 2015 205-218 Doroz, Y., Ozturk, E., and Sunar, B., Accelerating Fully Homomorphic Encryption in Hardware; TC June 2015 1509-1521 Doss, R., see Sundaresan, S., TC Oct. 2015 2994-3008 Dou, W., see Zhang, X., TC Aug. 2015 2293-2307 Dragt, R., see Alawneh, S., TC Dec. 2015 3475-3487 Du, A.Y., Smith, S.D., Yang, Z., Qiao, C., and Ramesh, R., Predicting Transient Downtime in Virtual Server Systems: An Efficient Sample Path Randomization Approach; TC Dec. 2015 3541-3554 Du, Z., see Chai, Y., TC Nov. 2015 3304-3316 Duato, J., see Andujar-Munoz, F.J., TC Oct. 2015 2847-2861 Duato, J., see Valero, A., TC July 2015 1884-1897 Dugan, K.J., see Brown, A.D., TC June 2015 1769-1782 Dutt, N., see Gottscho, M., TC May 2015 1483-1496 Dutta, A., see Saqib, F., TC Jan. 2015 280-285 E Easwaran, A., see Lee, J., TC April 2015 941-954 Ebergen, J., and Jamadagni, N., Radix-2 Division Algorithms with an OverRedundant Digit Set; TC Sept. 2015 2652-2663 Eeckhout, L., see Yu, Z., TC Nov. 2015 3153-3166 Eghbal, A., Yaghini, P.M., Bagherzadeh, N., and Khayambashi, M., Analytical Fault Tolerance Assessment and Metrics for TSV-Based 3D Network-onChip; TC Dec. 2015 3591-3604 El-Ghazawi, T., see Kayi, A., TC Feb. 2015 316-328 El-Razouk, H., Reyhani-Masoleh, A., and Gong, G., New Hardware Implementations of WG (29, 11) and WG- 16 Stream Ciphers Using Polynomial Basis; TC July 2015 2020-2035 Erol-Kantarci, M., see Akbas, M.I., TC April 2015 1015-1028 F Fan, B., see Xu, D., TC March 2015 682-697 Fan, H., see Han, J., TC March 2015 862-867 Feng, D., see Xia, W., TC April 2015 1162-1176 Feng, G., and Korkmaz, T., Finding Multi-Constrained Multiple Shortest Paths; TC Sept. 2015 2559-2572 Fernandez-Pascual, R., see Garcia-Guirado, A., TC April 2015 995-1014 Franchini, S., Gentile, A., Sorbello, F., Vassallo, G., and Vitabile, S., Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing; TC April 2015 955-970 Friese, R., see Khemka, B., TC Aug. 2015 2394-2407 Fu, H., see Xue, W., TC Aug. 2015 2382-2393 Fu, S., see Luo, J., TC Oct. 2015 3016-3021 Fu, X., see Yang, X., TC Jan. 2015 4-18 Fujita, M., see Ghandali, S., TC June 2015 1579-1593 Furber, S.B., see Brown, A.D., TC June 2015 1769-1782 G Gai, K., see Qiu, M., TC Dec. 2015 3528-3540 Gan, L., see Xue, W., TC Aug. 2015 2382-2393 Gao, Y., see Lu, G., TC May 2015 1389-1401 Garcia, H.J., and Markov, I.L., Simulation of Quantum Circuits via Stabilizer Frames; TC Aug. 2015 2323-2336 Garcia, J. M., see Garcia-Guirado, A., TC April 2015 995-1014 Garcia, J.M., see Ros, A., TC June 2015 1534-1547 Garcia-Guirado, A., Fernandez-Pascual, R., and Garcia, J. M., ICCI: In-Cache Coherence Information; TC April 2015 995-1014 Garside, J.D., see Brown, A.D., TC June 2015 1769-1782 Gaudet, M., see Wang, A., TC Jan. 2015 233-246 Gaudiot, J., see Kim, K., TC Oct. 2015 2862-2874 Gauthier, V., see Zhang, D., TC Feb. 2015 452-463 Gedik, B., see Schneider, S., TC Feb. 2015 504-517 Gentile, A., see Franchini, S., TC April 2015 955-970 George, C., and Vadhiyar, S., Fault Tolerance on Large Scale Systems using Adaptive Process Replication; TC Aug. 2015 2213-2225 + Check author entry for coauthors 2 Gerards, M.E., Hurink, J.L., and Kuper, J., On the Interplay between Global DVFS and Scheduling Tasks with Precedence Constraints; TC June 2015 1742-1754 Ghandali, S., Alizadeh, B., Fujita, M., and Navabi, Z., Automatic High-Level Data-Flow Synthesis and Optimization of Polynomial Datapaths Using Functional Decomposition; TC June 2015 1579-1593 Ghani, N., see Gu, F., TC Aug. 2015 2353-2366 Ghazaleh, N. A., see Kayaalp, M., TC Feb. 2015 533-546 Gholamian, S., see Kashif, H., TC April 2015 1177-1190 Ginosar, R., see Yavits, L., TC Feb. 2015 368-381 Goel, S.K., see Ingelsson, U., TC Dec. 2015 3335-3347 Gondal, I., see Rashid, M.M., TC July 2015 1998-2011 Gong, G., see El-Razouk, H., TC July 2015 2020-2035 Gonzalez, M., see Alvarez, L., TC Jan. 2015 152-165 Gorgin, S., and Jaberipur, G., Comment on “High Speed Parallel Decimal Multiplication With Redundant Internal Encodings”; TC Jan. 2015 293-294 Goswami, D., see Dietrich, B., TC Jan. 2015 260-273 Goswami, N., see Yu, Z., TC Nov. 2015 3153-3166 Gottscho, M., Bathen, L.A., Dutt, N., Nicolau, A., and Gupta, P., ViPZonE: Hardware Power Variability-Aware Virtual Memory Management for Energy Savings; TC May 2015 1483-1496 Grant, J.E., see Shen, H., TC June 2015 1715-1728 Graziano, M., see Causapruno, G., TC July 2015 1940-1953 Gries, M., see Dietrich, B., TC Jan. 2015 260-273 Groer, C., see Khemka, B., TC Aug. 2015 2394-2407 Grolleau, E., see Nguyen, T.H.C., TC July 2015 1805-1818 Gu, F., Shaban, K., Ghani, N., Khan, S., Naeini, M.R., Hayat, M.M., and Assi, C., Survivable Cloud Network Mapping for Disaster Recovery Support; TC Aug. 2015 2353-2366 Gu, L., Zeng, D., Barnawi, A., Guo, S., and Stojmenovic, I., Optimal Task Placement with QoS Constraints in Geo-Distributed Data Centers Using DVFS; TC July 2015 2049-2059 Guan, Y., see Chen, R., TC June 2015 1729-1741 Guha, A., see Dietrich, B., TC Jan. 2015 260-273 Gui, Y., see Zheng, Z., TC July 2015 2071-2083 Guizani, M., see Sun, Y., TC June 2015 1658-1669 Guneysu, T., Lyubashevsky, V., and Poppelmann, T., Lattice-Based Signatures: Optimization and Implementation on Reconfigurable Hardware; TC July 2015 1954-1967 Guo, J., see Lu, Y., TC Oct. 2015 2819-2832 Guo, M., see Lu, Y., TC Aug. 2015 2367-2381 Guo, Q., see Chen, T., TC May 2015 1442-1455 Guo, S., see Huang, H., TC Dec. 2015 3488-3499 Guo, S., see Yao, H., TC Dec. 2015 3515-3527 Guo, S., Dang, C, and Yang, Y., Joint Optimal Data Rate and Power Allocation in Lossy Mobile Ad Hoc Networks with Delay-Constrained Traffics; TC March 2015 747-762 Guo, S., see Yu, S., TC Jan. 2015 139-151 Guo, S., see Li, P., TC June 2015 1670-1679 Guo, S., see Wei, K., TC Oct. 2015 2809-2818 Guo, S., see Zeng, D., TC Nov. 2015 3128-3139 Guo, S., see Gu, L., TC July 2015 2049-2059 Guo, S., see Zeng, D., TC July 2015 1819-1829 Guo, X., see Zhou, J., TC Aug. 2015 2408-2414 Guo, Y., see Luo, J., TC Oct. 2015 3016-3021 Guo, Z., and Yang, Y., On Nonblocking Multicast Fat-Tree Data Center Networks with Server Redundancy; TC April 2015 1058-1073 Guo, Z., and Yang, Y., Exploring Server Redundancy in Nonblocking Multicast Data Center Networks; TC July 2015 1912-1926 Gupta, P., see Gottscho, M., TC May 2015 1483-1496 Gutierrez, M., see Burns, A., TC May 2015 1241-1253 H Ha, S., see Kang, S., TC July 2015 2036-2048 Ha, Y., see Jiang, G., TC Oct. 2015 2926-2939 Haghighi, M. S., see Wen, S., TC March 2015 640-653 Haghighi, M.S., Xiang, Y, Varadharajan, V, and Quinn, B., A Stochastic TimeDomain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks; TC March 2015 627-639 Hamdioui, S., Taouil, M., and Haron, N. Z., Testing Open Defects in Memristor-Based Memories; TC Jan. 2015 247-259 3 Han, J., and Fan, H., Shifted Polynomial Basis Multipliers Based on Subquadratic Toeplitz Matrix-Vector Product Approach for All Irreducible Pentanomials; TC March 2015 862-867 Han, J., see Liu, C., TC May 2015 1268-1281 Han, J., see Momeni, A., TC April 2015 984-994 Harbour, M.G., see Burns, A., TC May 2015 1241-1253 Haron, N. Z., see Hamdioui, S., TC Jan. 2015 247-259 Hasan, M.A., see Meloni, N., TC Aug. 2015 2204-2212 Hashizume, M., see Lu, S., TC May 2015 1230-1240 Hassan, M.M., see Li, J., TC Dec. 2015 3569-3579 Hayat, M.M., see Gu, F., TC Aug. 2015 2353-2366 He, B., see Lu, Y., TC Aug. 2015 2367-2381 He, W., see Luo, J., TC Oct. 2015 3016-3021 He, W., see Li, D., TC Sept. 2015 2534-2544 He, X., see Tan, Z., TC Sept. 2015 2519-2533 He, Y., see Li, Q., TC Aug. 2015 2169-2181 Healy, M. B., see Kim, D. H., TC Jan. 2015 112-125 Hilton, M.M., see Khemka, B., TC Aug. 2015 2394-2407 Hirzel, M., see Schneider, S., TC Feb. 2015 504-517 Holt, J., see Deniz, E., TC Aug. 2015 2239-2252 Hong, S., see Mahmood, T., TC June 2015 1694-1706 Hong, S., Chantem, T., and Hu, X.S., Local-Deadline Assignment for Distributed Real-Time Systems; TC July 2015 1983-1997 Hong, S., and Kim, S., A Low-Cost Mechanism Exploiting Narrow-Width Values for Tolerating Hard Faults in ALU; TC Sept. 2015 2433-2446 Hoon Yoo, S., see Lee, E., TC May 2015 1349-1360 Hossain, M. M., see Kim, D. H., TC Jan. 2015 112-125 Hsiaokuang Wu, E., see Yu-Chun, C., TC Oct. 2015 2730-3740 Hsieh, J., Chen, C., and Lin, H., Adaptive ECC Scheme for Hybrid SSD’s; TC Dec. 2015 3348-3361 Hsieh, J., and Kuan, Y., DCCS: Double Circular Caching Scheme for DRAM/ PRAM Hybrid Cache; TC Nov. 2015 3115-3127 Hsieh, J.-W., see Wang, J., TC April 2015 925-940 Hsieh, S., see Chen, C., TC June 2015 1622-1632 Hsieh, S.-Y., see Lee, C.-W., TC Jan. 2015 274-279 Hsin, H., Chang, E., Su, K., and Wu, A.A., Ant Colony Optimization-Based Adaptive Network-on-Chip Routing Framework Using Network Information Region; TC Aug. 2015 2119-2131 Hsin, H.-K, see Chang, E., TC March 2015 868-875 Hsiu, P., see Cheng, S., TC Oct. 2015 2767-2780 Hsu, A. C.-C., Wei, D. S., and Kuo, C.-C. J., Coexistence Wi-Fi MAC Design for Mitigating Interference Caused by Collocated Bluetooth; TC Feb. 2015 342-352 Hu, J., see Li, P., TC June 2015 1670-1679 Hu, J., see Zeng, D., TC Nov. 2015 3128-3139 Hu, J., see Tan, Z., TC Sept. 2015 2519-2533 Hu, X.S., see Hong, S., TC July 2015 1983-1997 Hu, Y., see Wang, W., TC March 2015 698-706 Hua, Y., see Xia, W., TC April 2015 1162-1176 Huang, C.-W., see Lee, C.-W., TC Jan. 2015 274-279 Huang, D., see Wang, Z., TC Dec. 2015 3430-3443 Huang, D., see Zhou, Z., TC Jan. 2015 126-138 Huang, H., Guo, S., Li, P., Ye, B., and Stojmenovic, I., Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network; TC Dec. 2015 3488-3499 Huang, H., see Yao, H., TC Dec. 2015 3515-3527 Huang, J., see Zhang, T., TC June 2015 1522-1533 Huang, J., Qin, X., Liang, X., and Xie, C., An Efficient I/O-Redirection-Based Reconstruction Scheme for Erasure-Coded Storage Clusters; TC Nov. 2015 3037-3050 Huang, J., see Sun, H., TC April 2015 1133-1148 Huang, P., see Tsao, C., TC Dec. 2015 3444-3460 Huang, P., Wang, C., and Xiao, L., RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks; TC April 2015 11491161 Huang, P.-C., see Wang, J., TC April 2015 925-940 Huang, T., see Chang, C., TC Dec. 2015 3404-3416 Huang, X., see Chang, C., TC Dec. 2015 3404-3416 Huang, X., see Li, J., TC Dec. 2015 3569-3579 Huang, X., see Wang, W., TC March 2015 698-706 Huang, X., see Wang, J., TC Nov. 2015 3293-3303 Huang, X., Liu, J.K., Tang, S., Xiang, Y., Liang, K., Xu, L., and Zhou, J., CostEffective Authentic and Anonymous Data Sharing with Forward Security; TC April 2015 971-983 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Huang, X., see Yuen, T.H., TC Sept. 2015 2595-2608 Huang, Y., see Zhang, T., TC June 2015 1522-1533 Huang, Z., Wang, C., Stojmenovic, M., and Nayak, A., Characterization of Cascading Failures in Interdependent Cyber-Physical Systems; TC Aug. 2015 2158-2168 Huh, J., see Ahn, J., TC Dec. 2015 3461-3474 Huh, J., see Jin, S., TC Oct. 2015 2833-2846 Hung, W.N.N., see Zhou, J., TC Aug. 2015 2408-2414 Hurink, J.L., see Gerards, M.E., TC June 2015 1742-1754 I Ibrahim, W., Shousha, M., and Chinneck, J.W., Accurate and Efficient Estimation of Logic Circuits Reliability Bounds; TC May 2015 1217-1229 Ienne, P., see Bayrak, A. G., TC Feb. 2015 329-341 Ikodinovic, I., Methodology for Cycle-Accurate DRAM Performance Analysis; TC July 2015 2084-2091 Imine, A., see Randolph, A., TC April 2015 1074-1089 Ingelsson, U., Goel, S.K., Larsson, E., and Marinissen, E.J., Abort-on-Fail Test Scheduling for Modular SOCs without and with Preemption; TC Dec. 2015 3335-3347 J Jaberipur, G., see Gorgin, S., TC Jan. 2015 293-294 Jamadagni, N., see Ebergen, J., TC Sept. 2015 2652-2663 Jamdagni, A., see Tan, Z., TC Sept. 2015 2519-2533 Jangjaimon, I., and Tzeng, N.-F., Effective Cost Reduction for Elastic Clouds under Spot Instance Pricing Through Adaptive Checkpointing; TC Feb. 2015 396-409 Jarray, A., and Karmouch, A., Cost-Efficient Mapping for Fault-Tolerant Virtual Networks; TC March 2015 668-681 Jarvinen, K., Dimitrov, V., and Azarderakhsh, R., A Generalization of Addition Chains and Fast Inversions in Binary Fields; TC Sept. 2015 2421-2432 Jawad, M., Muhammad Ali, S., Jorgenson, J.A., and Khan, S.U., JEM: Just in Time/Just Enough Energy Management Methodology for Computing Systems; TC June 2015 1798-1804 Jerez, J. L., Constantinides, G. A., and Kerrigan, E. C., A Low Complexity Scaling Method for the Lanczos Kernel in Fixed-Point Arithmetic; TC Feb. 2015 303-315 Jerger, N. E., see Ma, S., TC March 2015 763-777 Jessa, M., On the Quality of Random Sequences Produced with a Combined Random Bit Generator; TC March 2015 791-804 Ji, Y., see Yang, L., TC Aug. 2015 2253-2266 Jia, C., see Li, J., TC Feb. 2015 425-437 Jia, W., see Wen, S., TC March 2015 640-653 Jiang, C.J., see Wu, Y., TC Sept. 2015 2447-2459 Jiang, G., Wu, J., Ha, Y., Wang, Y., and Sun, J., Reconfiguring Three-Dimensional Processor Arrays for Fault-Tolerance: Hardness and Heuristic Algorithms; TC Oct. 2015 2926-2939 Jiang, H., see Liu, W., TC May 2015 1323-1335 Jiang, H., see Sun, H., TC April 2015 1133-1148 Jiang, H., see Xia, W., TC April 2015 1162-1176 Jiang, H., see Wu, S., TC Sept. 2015 2637-2651 Jiang, W., Ren, F., Shu, R., Wu, Y., and Lin, C., Sliding Mode Congestion Control for Data Center Ethernet Networks; TC Sept. 2015 2675-2690 Jie, Z., see Luo, C., TC July 2015 1830-1843 Jin, C., see Cui, T., TC July 2015 2098-2102 Jin, H., see Yu, Z., TC Nov. 2015 3153-3166 Jin, S., see Ahn, J., TC Dec. 2015 3461-3474 Jin, S., Ahn, J., Seol, J., Cha, S., Huh, J., and Maeng, S., H-SVM: HardwareAssisted Secure Virtual Machines under a Vulnerable Hypervisor; TC Oct. 2015 2833-2846 Jin, Z., see Liu, W., TC May 2015 1323-1335 John, L.K., see Yu, Z., TC Nov. 2015 3153-3166 Johnson, B.W., see Levitin, G., TC April 2015 1043-1057 Jong, C.C., see Low, J.Y.L., TC June 2015 1783-1797 Jorgenson, J.A., see Jawad, M., TC June 2015 1798-1804 Jou, J., see Lai, B. C., TC April 2015 884-898 Jung, M., see Kim, D. H., TC Jan. 2015 112-125 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 K Kahne, B., see Deniz, E., TC Aug. 2015 2239-2252 Kakoee, M.R., see Dehyadegari, M., TC Aug. 2015 2132-2144 Kamruzzaman, J., see Rashid, M.M., TC July 2015 1998-2011 Kang, S., Park, H., Kim, S., Oh, H., and Ha, S., Optimal Checkpoint Selection with Dual-Modular Redundancy Hardening; TC July 2015 2036-2048 Karabina, K., see Chatterjee, S., TC June 2015 1707-1714 Karafyllidis, I.G., see Mardiris, V.A., TC Sept. 2015 2476-2489 Karmouch, A., see Al Ridhawi, Y., TC March 2015 832-846 Karmouch, A., see Jarray, A., TC March 2015 668-681 Karri, R., see Rajendran, J., TC March 2015 733-746 Karri, R., see Rajendran, J., TC Feb. 2015 410-424 Kashif, H., Gholamian, S., and Patel, H., SLA: A Stage-Level Latency Analysisfor Real-Time Communicationin a Pipelined Resource Model; TC April 2015 1177-1190 Kavvadias, D.J., see Voyiatzis, I.K., TC Oct. 2015 2891-2901 Kayaalp, M., Schmitt, T., Nomani, J., Ponomarev, D., and Ghazaleh, N. A., Signature-Based Protection from Code Reuse Attacks; TC Feb. 2015 533-546 Kayi, A., Serres, O., and El-Ghazawi, T., Adaptive Cache Coherence Mechanisms with Producer–Consumer Sharing Optimization for Chip Multiprocessors; TC Feb. 2015 316-328 Kent, K.B., see Wang, Y., TC Sept. 2015 2716-2729 Kent, M., see Xu, D., TC Sept. 2015 2490-2505 Kerrigan, E. C., see Jerez, J. L., TC Feb. 2015 303-315 Khalil, I., see Yaakob, N., TC June 2015 1594-1606 Khalil, I., see Kumarage, H., TC Sept. 2015 2573-2585 Khan, S., see Gu, F., TC Aug. 2015 2353-2366 Khan, S. U., see Chen, D., TC March 2015 707-719 Khan, S.U., see Jawad, M., TC June 2015 1798-1804 Khan, S.U., see Menzel, M., TC May 2015 1336-1348 Khayambashi, M., see Eghbal, A., TC Dec. 2015 3591-3604 Khemka, B., Friese, R., Briceno, L.D., Siegel, H.J., Maciejewski, A.A., Koenig, G.A., Groer, C., Okonski, G., Hilton, M.M., Rambharos, R., and Poole, S., Utility Functions and Resource Management in an Oversubscribed Heterogeneous Computing Environment; TC Aug. 2015 2394-2407 Khorosh, I., see Kim, D. H., TC Jan. 2015 112-125 Kijkanjanarat, T., see Salehin, K. M., TC Jan. 2015 205-218 Kim, C., and Park, K.H., Credit-Based Runtime Placement of Virtual Machines on a Single NUMA System for QoS of Data Access Performance; TC June 2015 1633-1646 Kim, D. H., Athikulwongse, K., Healy, M. B., Hossain, M. M., Jung, M., Khorosh, I., Kumar, G., Lee, Y.-J., Lewis, D. L., Lin, T.-W., Liu, C., Panth, S., Pathak, M., Ren, M., Shen, G., Song, T., Woo, D. H., Zhao, X., Kim, J., Choi, H., Loh, G. H., Lee, H.-H. S., and Lim, S. K., Design and Analysis of 3D-MAPS (3D Massively Parallel Processor with Stacked Memory); TC Jan. 2015 112-125 Kim, H., see Lakshminarayana, N.B., TC Nov. 2015 3102-3114 Kim, H., see Lee, J., TC Nov. 2015 3167-3180 Kim, J., see Kim, D. H., TC Jan. 2015 112-125 Kim, J., see Baek, S., TC Aug. 2015 2337-2352 Kim, J. M., Kim, Y. G., and Chung, S. W., Stabilizing CPU Frequency and Voltage for Temperature-Aware DVFS in Mobile Devices; TC Jan. 2015 286-292 Kim, J.-S., see Lee, Y., TC Feb. 2015 569-581 Kim, K., Cho, B.Y., Ro, W.W., and Gaudiot, J., Network Variation and Fault Tolerant Performance Acceleration in Mobile Devices with Simultaneous Remote Execution; TC Oct. 2015 2862-2874 Kim, L., see Chung, J., TC Nov. 2015 3091-3101 Kim, S., see Mahmood, T., TC June 2015 1694-1706 Kim, S., see Kang, S., TC July 2015 2036-2048 Kim, S., see Lee, J., TC July 2015 1927-1939 Kim, S., see Hong, S., TC Sept. 2015 2433-2446 Kim, Y., Comments on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”; TC Dec. 2015 3619-3620 Kim, Y. G., see Kim, J. M., TC Jan. 2015 286-292 Kodi, A.K., see DiTomaso, D., TC Dec. 2015 3555-3568 Koenig, G.A., see Khemka, B., TC Aug. 2015 2394-2407 Kondo, D., see Di, S., TC June 2015 1755-1768 Kong, J., Koushanfar, F., and Chung, S.W., An Energy-Efficient Last-Level Cache Architecture for Process Variation-Tolerant 3D Microprocessors; TC Sept. 2015 2460-2475 Kong, Z., see Cui, T., TC July 2015 2098-2102 + Check author entry for coauthors 4 Korkmaz, T., see Feng, G., TC Sept. 2015 2559-2572 Kornerup, P., Reviewing High-Radix Signed-Digit Adders; TC May 2015 1502-1505 Koushanfar, F., see Kong, J., TC Sept. 2015 2460-2475 Ku, L., see Cheng, S., TC Oct. 2015 2767-2780 Kuan, Y., see Hsieh, J., TC Nov. 2015 3115-3127 Kumar, G., see Kim, D. H., TC Jan. 2015 112-125 Kumar, M., see Sadiq, U., TC Aug. 2015 2308-2322 Kumarage, H., see Yaakob, N., TC June 2015 1594-1606 Kumarage, H., Khalil, I., and Tari, Z., Granular Evaluation of Anomalies in Wireless Sensor Networks Using Dynamic Data Partitioning with an Entropy Criteria; TC Sept. 2015 2573-2585 Kuo, C.-C. J., see Hsu, A. C.-C., TC Feb. 2015 342-352 Kuo, H., see Lai, B. C., TC April 2015 884-898 Kuper, J., see Gerards, M.E., TC June 2015 1742-1754 L Lai, B. C., Kuo, H., and Jou, J., A Cache Hierarchy Aware Thread Mapping Methodology for GPGPUs; TC April 2015 884-898 Lakshminarayana, N.B., and Kim, H., Block-Precise Processors: Low-Power Processors with Reduced Operand Store Accesses and Result Broadcasts; TC Nov. 2015 3102-3114 Lam, K.-Y., see Wang, J., TC April 2015 925-940 Lama, P., and Zhou, X., Coordinated Power and Performance Guarantee with Fuzzy MIMO Control in Virtualized Server Clusters; TC Jan. 2015 97-111 Lan, C., see Zhou, J., TC Aug. 2015 2408-2414 Lan, Z., see Zheng, Z., TC May 2015 1402-1415 Larsson, E., see Ingelsson, U., TC Dec. 2015 3335-3347 Lasla, N., Younis, M.F., Ouadjaout, A., and Badache, N., An Effective AreaBased Localization Algorithm for Wireless Networks; TC Aug. 2015 21032118 Lastovetsky, A., see Zhong, Z., TC Sept. 2015 2506-2518 Le, Y., Ma, L., Cheng, W., Cheng, X., and Chen, B., A Time Fairness-Based MAC Algorithm for Throughput Maximization in 802.11 Networks; TC Jan. 2015 19-31 Le Traon, Y., see Xu, D., TC Sept. 2015 2490-2505 Lee, C.-W., Huang, C.-W., Pi, W.-H., and Hsieh, S.-Y., An Improved Approximation Ratio to the Partial-Terminal Steiner Tree Problem; TC Jan. 2015 274-279 Lee, D., see Chang, C., TC Dec. 2015 3404-3416 Lee, D., see Park, H., TC March 2015 720-732 Lee, D.T., and Bruck, J., Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits; TC Dec. 2015 3376-3388 Lee, E., Hoon Yoo, S., and Bahn, H., Design and Implementation of a Journaling File System for Phase-Change Memory; TC May 2015 1349-1360 Lee, H.-H. S., see Kim, D. H., TC Jan. 2015 112-125 Lee, H.G., see Baek, S., TC Aug. 2015 2337-2352 Lee, J., Woo, D.H., Kim, H., and Azimi, M., GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs; TC Nov. 2015 3167-3180 Lee, J., see Baek, S., TC Aug. 2015 2337-2352 Lee, J., Shin, K. G., Shin, I., and Easwaran, A., Composition of Schedulability Analyses for Real-Time Multiprocessor Systems; TC April 2015 941-954 Lee, J., and Kim, S., Filter Data Cache: An Energy-Efficient Small L0 Data Cache Architecture Driven byMiss Cost Reduction; TC July 2015 19271939 Lee, P.P., see Li, R., TC July 2015 1898-1911 Lee, P.P.C., see Zhu, Y., TC Aug. 2015 2145-2157 Lee, S.-W., see Lee, Y., TC Feb. 2015 569-581 Lee, Y., Kim, J.-S., Lee, S.-W., and Maeng, S., Zombie Chasing: Efficient Flash Management Considering Dirty Data in the Buffer Cache; TC Feb. 2015 569-581 Lee, Y.-J., see Kim, D. H., TC Jan. 2015 112-125 Leu, J., Chen, J., and Li, K., Hybrid Search Scheme for Social Networks Supported by Dynamic Weighted Distributed Label Clustering; TC Sept. 2015 2586-2594 Leung, V.C.M., see Zhu, C., TC July 2015 1844-1856 Levitin, G., Xing, L., Johnson, B.W., and Dai, Y., Mission Reliability, Cost and Time for Cold Standby Computing Systems with Periodic Backup; TC April 2015 1043-1057 Lewis, D. L., see Kim, D. H., TC Jan. 2015 112-125 Li, B., see Wang, Z., TC Dec. 2015 3430-3443 5 Li, C., Chen, L., Lu, R., and Li, H., Comment on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”; TC March 2015 882-883 Li, D., see Shang, Y., TC Nov. 2015 3237-3248 Li, D., and Wu, J., On Data Center Network Architectures for Interconnecting Dual-Port Servers; TC Nov. 2015 3210-3222 Li, D., Shang, Y., He, W., and Chen, C., EXR: Greening Data Center Network with Software Defined Exclusive Routing; TC Sept. 2015 2534-2544 Li, G., see Chen, W., TC Oct. 2015 2741-2751 Li, H., see Li, C., TC March 2015 882-883 Li, J., see Qiu, M., TC Dec. 2015 3528-3540 Li, J., Chen, X., Huang, X., Tang, S., Xiang, Y., Hassan, M.M., and Alelaiwi, A., Secure Distributed Deduplication Systems with Improved Reliability; TC Dec. 2015 3569-3579 Li, J., Chen, X., Jia, C., and Lou, W., Identity-Based Encryption with Outsourced Revocation in Cloud Computing; TC Feb. 2015 425-437 Li, J., see Li, J., TC Feb. 2015 425-437 Li, J., see Li, Q., TC Aug. 2015 2169-2181 Li, K., see Liu, X., TC Jan. 2015 87-96 Li, K., Tang, X., and Veeravalli, B., Scheduling Precedence Constrained Stochastic Tasks on Heterogeneous Cluster Systems; TC Jan. 2015 191-204 Li, K., see Li, K., TC Jan. 2015 191-204 Li, K., see Zhang, G., TC Jan. 2015 32-44 Li, K., see Wei, K., TC Oct. 2015 2809-2818 Li, K., see Luo, J., TC Oct. 2015 3016-3021 Li, K., see Mei, J., TC Nov. 2015 3064-3078 Li, K., see Mei, J., TC Nov. 2015 3064-3078 Li, K., see Leu, J., TC Sept. 2015 2586-2594 Li, K., see Yang, W., TC Sept. 2015 2623-2636 Li, K., see Yang, W., TC Sept. 2015 2623-2636 Li, P., see Huang, H., TC Dec. 2015 3488-3499 Li, P., Guo, S., and Hu, J., Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks; TC June 2015 1670-1679 Li, P., see Zeng, D., TC Nov. 2015 3128-3139 Li, Q., He, Y., Li, J., Shi, L., Chen, Y., and Xue, C.J., Compiler-Assisted Refresh Minimization for Volatile STT-RAM Cache; TC Aug. 2015 21692181 Li, R., Lin, J., and Lee, P.P., Enabling Concurrent Failure Recovery for Regenerating-Coding-Based Storage Systems: From Theory to Practice; TC July 2015 1898-1911 Li, S., see Lu, Y., TC Oct. 2015 2819-2832 Li, T., see Shen, H., TC Feb. 2015 353-367 Li, T., see Lu, S., TC May 2015 1230-1240 Li, T., see Yu, Z., TC Nov. 2015 3153-3166 Li, X., see Chen, D., TC March 2015 707-719 Li, X., see Wang, C., TC May 2015 1296-1310 Li, Z., see Shen, H., TC June 2015 1715-1728 Liang, K., see Huang, X., TC April 2015 971-983 Liang, W., see Xu, W., TC March 2015 600-613 Liang, W., see Ren, X., TC July 2015 1870-1883 Liang, X., see Huang, J., TC Nov. 2015 3037-3050 Liao, J., see Xue, W., TC Aug. 2015 2382-2393 Liao, X., see Liu, W., TC May 2015 1323-1335 Liaskos, C., and Tsioliaridou, A., A Promise of Realizable, Ultra-Scalable Communications at Nano-Scale:A Multi-Modal Nano-Machine Architecture; TC May 2015 1282-1295 Lim, K., see Won, Y., TC May 2015 1375-1388 Lim, S. K., see Kim, D. H., TC Jan. 2015 112-125 Lin, C, see Salehin, K. M., TC Jan. 2015 205-218 Lin, C., see Chen, C., TC Jan. 2015 180-190 Lin, C., see Jiang, W., TC Sept. 2015 2675-2690 Lin, H., see Hsieh, J., TC Dec. 2015 3348-3361 Lin, H., see Liu, W., TC May 2015 1323-1335 Lin, J., see Yang, X., TC Jan. 2015 4-18 Lin, J., see Zhu, Y., TC Aug. 2015 2145-2157 Lin, J., see Li, R., TC July 2015 1898-1911 Lin, L., see Zhou, S., TC Feb. 2015 547-555 Lin, S.-Y., see Chang, E., TC March 2015 868-875 Lin, T.-W., see Kim, D. H., TC Jan. 2015 112-125 Lin, T.-Y., Wu, K.-R., and Yin, G.-C., Channel-Hopping Scheme and ChannelDiverse Routing in Static Multi-Radio Multi-Hop Wireless Networks; TC Jan. 2015 71-86 Lin, X, see Xu, W., TC March 2015 600-613 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Lin, Y., see Shen, H., TC Feb. 2015 353-367 Lin, Z.-Y., see Yang, C.-N., TC Feb. 2015 492-503 Liu, A. X., see Liu, X., TC Jan. 2015 87-96 Liu, C., see Kim, D. H., TC Jan. 2015 112-125 Liu, C., Han, J., and Lombardi, F., An Analytical Framework for Evaluating the Error Characteristics of Approximate Adders; TC May 2015 1268-1281 Liu, C., see Zhang, X., TC Aug. 2015 2293-2307 Liu, C., Ranjan, R., Yang, C., Zhang, X., Wang, L., and Chen, J., MuR-DPA: Top-Down Levelled Multi-Replica Merkle Hash Tree Based Secure Public Auditing for Dynamic Big Data Storage on Cloud; TC Sept. 2015 26092622 Liu, D., see Chen, R., TC June 2015 1729-1741 Liu, F., Shu, P., and Lui, J.C., AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol; TC Nov. 2015 3051-3063 Liu, G., Shen, H., and Ward, L., An Efficient and Trustworthy P2P and Social Network Integrated File Sharing System; TC Jan. 2015 54-70 Liu, G., see Shen, H., TC Oct. 2015 2953-2967 Liu, J., see Shen, H., TC Feb. 2015 518-532 Liu, J., see Shen, H., TC Feb. 2015 518-532 Liu, J., see Shen, H., TC June 2015 1715-1728 Liu, J.K., see Huang, X., TC April 2015 971-983 Liu, J.K., see Yuen, T.H., TC Sept. 2015 2595-2608 Liu, L., Song, Y., Zhang, H., Ma, H., and Vasilakos, A. V., Physarum Optimization: A Biology-Inspired Algorithm for the Steiner Tree Problem in Networks; TC March 2015 818-831 Liu, L., see Wu, Y., TC Sept. 2015 2447-2459 Liu, R.P., see Tan, Z., TC Sept. 2015 2519-2533 Liu, W., see Wang, B., TC Feb. 2015 587-592 Liu, W., Jiang, H., Yang, Y., Liao, X., Lin, H., and Jin, Z., A Unified Framework for Line-Like Skeleton Extraction in 2D/3D Sensor Networks; TC May 2015 1323-1335 Liu, X., see Xu, D., TC March 2015 682-697 Liu, X., Li, K., Min, G., Shen, Y., Liu, A. X., and Qu, W., Completely Pinpointing the Missing RFID Tags in a Time-Efficient Way; TC Jan. 2015 87-96 Liu, X., see Yuan, D., TC Oct. 2015 2781-2795 Liu, X., see Zhang, G., TC May 2015 1456-1469 Liu, X., Xiao, B., Zhang, S., Bu, K., and Chan, A., STEP: A Time-Efficient Tag Searching Protocol in Large RFID Systems; TC Nov. 2015 3265-3277 Liu, Z. L., see Ma, S., TC March 2015 763-777 Loh, G. H., see Kim, D. H., TC Jan. 2015 112-125 Lombardi, F., see Namba, K., TC Oct. 2015 2902-2911 Lombardi, F., see Liu, C., TC May 2015 1268-1281 Lombardi, F., see Momeni, A., TC April 2015 984-994 Lombardi, F., see Namba, K., TC July 2015 2092-2097 Lopez, P., see Valero, A., TC July 2015 1884-1897 Lou, W., see Li, J., TC Feb. 2015 425-437 Loureiro, A. A., see Rezende, C., TC March 2015 614-626 Louri, A., see DiTomaso, D., TC Dec. 2015 3555-3568 Low, J.Y.L., and Jong, C.C., Unified Mitchell-Based Approximation for Efficient Logarithmic Conversion Circuit; TC June 2015 1783-1797 Lu, C., see Saifullah, A., TC May 2015 1361-1374 Lu, G., Zhan, J., Wang, H., Yuan, L., Gao, Y., Weng, C., and Qi, Y., PowerTracer: Tracing Requests in Multi-Tier Services to Reduce Energy Inefficiency; TC May 2015 1389-1401 Lu, P., see Wang, Y., TC Sept. 2015 2716-2729 Lu, R., see Li, C., TC March 2015 882-883 Lu, S., see Zhang, S., TC March 2015 654-667 Lu, S., Li, T., Hashizume, M., and Chen, J., Address Scrambling and Data Inversion Techniques for Yield Enhancement of NROM-Based ROMs; TC May 2015 1230-1240 Lu, Y., Shu, J., Guo, J., Li, S., and Mutlu, O., High-Performance and Lightweight Transaction Support in Flash-Based SSDs; TC Oct. 2015 2819-2832 Lu, Y., He, B., Tang, X., and Guo, M., Synergy of Dynamic Frequency Scaling and Demotion on DRAM Power Management: Models and Optimizations; TC Aug. 2015 2367-2381 Lu, Y., see Xue, W., TC Aug. 2015 2382-2393 Lubicz, D., and Bochard, N., Towards an Oscillator Based TRNG with a Certified Entropy Rate; TC April 2015 1191-1200 Lui, J.C., see Liu, F., TC Nov. 2015 3051-3063 Lukic, M., Barnawi, A., and Stojmenovic, I., Robot Coordination for EnergyBalanced Matching and Sequence Dispatch of Robots to Events; TC May 2015 1416-1428 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Luo, C., Cai, S., Wu, W., Jie, Z., and Su, K., CCLS: An Efficient Local Search Algorithm for Weighted Maximum Satisfiability; TC July 2015 1830-1843 Luo, J., see Zhang, B., TC June 2015 1548-1563 Luo, J., Guo, Y., Fu, S., Li, K., and He, W., Virtual Resource Allocation Based on Link Interference in Cayley Wireless Data Centers; TC Oct. 2015 30163021 Luo, Y., see Weng, C., TC May 2015 1470-1482 Luo, Z., see Xia, F., TC July 2015 1857-1869 Lyu, M. R., see Zheng, Z., TC Jan. 2015 219-232 Lyubashevsky, V., see Guneysu, T., TC July 2015 1954-1967 M Ma, H., see Liu, L., TC March 2015 818-831 Ma, K., see Zheng, W., TC Nov. 2015 3278-3292 Ma, L., see Le, Y., TC Jan. 2015 19-31 Ma, S., Wang, Z., Liu, Z. L., and Jerger, N. E., Leaving One Slot Empty: Flit Bubble Flow Control for Torus Cache-Coherent NoCs; TC March 2015 763-777 Maciejewski, A.A., see Al-Qawasmeh, A.M., TC Feb. 2015 477-491 Maciejewski, A.A., see Khemka, B., TC Aug. 2015 2394-2407 MacKenzie, A. B., see Di Francesco, P., TC April 2015 912-924 Madanayake, A., see Rajapaksha, N., TC Sept. 2015 2708-2715 Maddah, R., Melhem, R., and Cho, S., RDIS: Tolerating Many Stuck-At Faults in Resistive Memory; TC March 2015 847-861 Maeng, S., see Lee, Y., TC Feb. 2015 569-581 Maeng, S., see Jin, S., TC Oct. 2015 2833-2846 Maestro, J.A., see Pontarelli, S., TC May 2015 1497-1501 Mahmood, T., Hong, S., and Kim, S., Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho; TC June 2015 1694-1706 Maitra, S., see Sarkar, S., TC June 2015 1647-1657 Makris, Y., see Maniatakos, M., TC Sept. 2015 2664-2674 Mancillas-Lopez, C., see Chakraborty, D., TC Sept. 2015 2691-2707 Maniatakos, M., Michael, M., Tirumurti, C., and Makris, Y., Revisiting Vulnerability Analysis in Modern Microprocessors; TC Sept. 2015 2664-2674 Manoj P. D., S., Yu, H., and Wang, K., 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching; TC Nov. 2015 3022-3036 Mao, B., see Wu, S., TC Sept. 2015 2637-2651 Mardiris, V.A., Sirakoulis, G.C., and Karafyllidis, I.G., Automated Design Architecture for 1-D Cellular Automata Using Quantum Cellular Automata; TC Sept. 2015 2476-2489 Marinissen, E.J., see Ingelsson, U., TC Dec. 2015 3335-3347 Markov, I.L., see Garcia, H.J., TC Aug. 2015 2323-2336 Marongiu, A., see Dehyadegari, M., TC Aug. 2015 2132-2144 Martorell, X., see Alvarez, L., TC Jan. 2015 152-165 Masera, G., see Condo, C., TC Oct. 2015 2981-2993 Matula, D.W., Panu, M.T., and Zhang, J.Y., Multiplicative Division Employing Independent Factors; TC July 2015 2012-2019 McCartney, W.P., and Sridhar, N., Stackless Multi-Threading for Embedded Systems; TC Oct. 2015 2940-2952 McGettrick, S., see Di Francesco, P., TC April 2015 912-924 Mei, J., Li, K., Ouyang, A., and Li, K., A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing; TC Nov. 2015 30643078 Melhem, R., see Maddah, R., TC March 2015 847-861 Meloni, N., and Hasan, M.A., Efficient Double Bases for Scalar Multiplication; TC Aug. 2015 2204-2212 Menasce, D.A., see Bardhan, S., TC Aug. 2015 2279-2292 Menezes, A., see Chatterjee, S., TC June 2015 1707-1714 Menzel, M., Ranjan, R., Wang, L., Khan, S.U., and Chen, J., CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds; TC May 2015 1336-1348 Michael, M., see Maniatakos, M., TC Sept. 2015 2664-2674 Michael, M. M., see Wang, A., TC Jan. 2015 233-246 Min, G., see Liu, X., TC Jan. 2015 87-96 Min, J., see Won, Y., TC May 2015 1375-1388 Ming, Z., see Qiu, M., TC Dec. 2015 3528-3540 Misra, S., see Sarkar, S., TC Oct. 2015 2912-2925 Mitsunari, S., see Zavattoni, E., TC May 2015 1429-1441 Miyazaki, T., see Zeng, D., TC Nov. 2015 3128-3139 Mo, Z., see Yang, W., TC Sept. 2015 2623-2636 Mohammadi, S., see Dehyadegari, M., TC Aug. 2015 2132-2144 + Check author entry for coauthors 6 Momeni, A., Han, J., Montuschi, P., and Lombardi, F., Design and Analysis of Approximate Compressors for Multiplication; TC April 2015 984-994 Montuschi, P., Editorial from the New Editor in Chief; TC Jan. 2015 2 Montuschi, P., see Condo, C., TC Oct. 2015 2981-2993 Montuschi, P., see Momeni, A., TC April 2015 984-994 Morad, A., see Yavits, L., TC Feb. 2015 368-381 Moreno, F., see Rodriguez, A., TC Nov. 2015 3140-3152 Mouelhi, T., see Xu, D., TC Sept. 2015 2490-2505 Moulema, P.-M., see Yang, X., TC Jan. 2015 4-18 Moyer, S., see Shen, H., TC Feb. 2015 518-532 Muhammad Ali, S., see Jawad, M., TC June 2015 1798-1804 Mukhopadhyay, D., see Rebeiro, C., TC March 2015 778-790 Mutlu, O., see Lu, Y., TC Oct. 2015 2819-2832 Myers, C.J., see Zheng, H., TC June 2015 1607-1621 N Naeini, M.R., see Gu, F., TC Aug. 2015 2353-2366 Namba, K., and Lombardi, F., Parallel Decodable Two-Level Unequal Burst Error Correcting Codes; TC Oct. 2015 2902-2911 Namba, K., and Lombardi, F., Non-Binary Orthogonal Latin Square Codes for a Multilevel Phase Charge Memory (PCM); TC July 2015 2092-2097 Nanda, P., see Tan, Z., TC Sept. 2015 2519-2533 Navabi, Z., see Ghandali, S., TC June 2015 1579-1593 Navarro, N., see Alvarez, L., TC Jan. 2015 152-165 Nayak, A., see Huang, Z., TC Aug. 2015 2158-2168 Nechma, T., and Zwolinski, M., Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs; TC April 2015 1090-1103 Negre, C., and Robert, J., New Parallel Approaches for Scalar Multiplication in Elliptic Curve over Fields of Small Characteristic; TC Oct. 2015 2875-2890 Nepal, S., see Zhang, X., TC Aug. 2015 2293-2307 Nguyen, H.D., see Demmel, J., TC July 2015 2060-2070 Nguyen, T.H.C., Richard, P., and Grolleau, E., An FPTAS for Response Time Analysis of Fixed Priority Real-Time Tasks with Resource Augmentation; TC July 2015 1805-1818 Nicolau, A., see Gottscho, M., TC May 2015 1483-1496 Nicopoulos, C., see Baek, S., TC Aug. 2015 2337-2352 Noh, S. H., see Park, H., TC March 2015 720-732 Nomani, J., see Kayaalp, M., TC Feb. 2015 533-546 Novo, D., see Bayrak, A. G., TC Feb. 2015 329-341 Nunez-Yanez, J.L., Adaptive Voltage Scaling with In-Situ Detectors in Commercial FPGAs; TC Jan. 2015 45-53 O Obaidat, M.S., see Sarkar, S., TC Oct. 2015 2912-2925 Oh, H., see Kang, S., TC July 2015 2036-2048 Ohmacht, M., see Wang, A., TC Jan. 2015 233-246 Okonski, G., see Khemka, B., TC Aug. 2015 2394-2407 Ortiz, P., see Saqib, F., TC Jan. 2015 280-285 Oshin, T.O., Poslad, S., and Zhang, Z., Energy-Efficient Real-Time Human Mobility State Classification Using Smartphones; TC June 2015 1680-1693 OSullivan, J. C., see Di Francesco, P., TC April 2015 912-924 Otoom, M., and Paul, J.M., Multiprocessor Capacity Metric and Analysis; TC Nov. 2015 3181-3196 Ottavi, M., see Pontarelli, S., TC May 2015 1497-1501 Ouadjaout, A., see Lasla, N., TC Aug. 2015 2103-2118 Ouyang, A., see Mei, J., TC Nov. 2015 3064-3078 Ozturk, E., see Doroz, Y., TC June 2015 1509-1521 P Pan, Y., see Zhang, T., TC June 2015 1522-1533 Pang, A., see Shih, Y., TC Nov. 2015 3079-3090 Panth, S., see Kim, D. H., TC Jan. 2015 112-125 Panu, M.T., see Matula, D.W., TC July 2015 2012-2019 Park, H., Choi, J., Lee, D., and Noh, S. H., iBuddy: Inverse Buddy for Enhancing Memory Allocation/Deallocation Performanceon Multi-Core Systems; TC March 2015 720-732 Park, H., see Kang, S., TC July 2015 2036-2048 Park, K.H., see Kim, C., TC June 2015 1633-1646 Pasricha, S., see Al-Qawasmeh, A.M., TC Feb. 2015 477-491 7 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Passarella, A., see Sadiq, U., TC Aug. 2015 2308-2322 Patel, H., see Kashif, H., TC April 2015 1177-1190 Pathak, M., see Kim, D. H., TC Jan. 2015 112-125 Pattichis, M. S., see Saqib, F., TC Jan. 2015 280-285 Paul, J.M., see Otoom, M., TC Nov. 2015 3181-3196 Pei, J., see Zhang, X., TC Aug. 2015 2293-2307 Peng, S.-L., see Yang, C.-N., TC Feb. 2015 492-503 Perez, L.J.D., see Zavattoni, E., TC May 2015 1429-1441 Peters, D., see Alawneh, S., TC Dec. 2015 3475-3487 Petit, S., see Valero, A., TC July 2015 1884-1897 Pi, W.-H., see Lee, C.-W., TC Jan. 2015 274-279 Pino, Y., see Rajendran, J., TC Feb. 2015 410-424 Pinotti, C.M., see Bertossi, A.A., TC April 2015 1201-1207 Plana, L.A., see Brown, A.D., TC June 2015 1769-1782 Platania, M., see Baldoni, R., TC Oct. 2015 2796-2808 Plusquellic, J., see Saqib, F., TC Jan. 2015 280-285 Pomeranz, I., Two-Dimensional Static Test Compaction for Functional Test Sequences; TC Oct. 2015 3009-3015 Pomeranz, I., Test Vector Omission for Fault Coverage Improvement of Functional Test Sequences; TC Nov. 2015 3317-3321 Pomeranz, I., Piecewise-Functional Broadside Tests Based on Reachable States; TC Aug. 2015 2415-2420 Ponomarev, D., see Kayaalp, M., TC Feb. 2015 533-546 Pontarelli, S., Reviriego, P., Ottavi, M., and Maestro, J.A., Low Delay Single Symbol Error Correction Codes Based on Reed Solomon Codes; TC May 2015 1497-1501 Poole, S., see Khemka, B., TC Aug. 2015 2394-2407 Poppelmann, T., see Guneysu, T., TC July 2015 1954-1967 Poslad, S., see Oshin, T.O., TC June 2015 1680-1693 Q Qi, Y., see Lu, G., TC May 2015 1389-1401 Qian, J., Zhu, Q., and Chen, H., Multi-Granularity Locality-Sensitive Bloom Filter; TC Dec. 2015 3500-3514 Qiao, C., see Du, A.Y., TC Dec. 2015 3541-3554 Qin, X., see Huang, J., TC Nov. 2015 3037-3050 Qin, X., see Chai, Y., TC Nov. 2015 3304-3316 Qin, X., see Sun, H., TC April 2015 1133-1148 Qin, Z., see Chen, R., TC June 2015 1729-1741 Qiu, M., Ming, Z., Li, J., Gai, K., and Zong, Z., Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm; TC Dec. 2015 35283540 Qu, W., see Liu, X., TC Jan. 2015 87-96 Que, X., see Yu, W., TC Feb. 2015 556-568 Querzoni, L., see Baldoni, R., TC Oct. 2015 2796-2808 Quinn, B., see Haghighi, M.S., TC March 2015 627-639 Quintero, A., see Randolph, A., TC April 2015 1074-1089 R Rahaman, H., see Datta, K., TC April 2015 1208-1214 Rajapaksha, N., Madanayake, A., Cintra, R.J., Adikari, J., and Dimitrov, V.S., VLSI Computational Architectures for the Arithmetic Cosine Transform; TC Sept. 2015 2708-2715 Rajendran, J., Karri, R., and Rose, G. S., Improving Tolerance to Variations in Memristor-Based Applications Using Parallel Memristors; TC March 2015 733-746 Rajendran, J., Zhang, H., Zhang, C., Rose, G. S., Pino, Y., Sinanoglu, O., and Karri, R., Fault Analysis-Based Logic Encryption; TC Feb. 2015 410-424 Rambharos, R., see Khemka, B., TC Aug. 2015 2394-2407 Ramesh, R., see Du, A.Y., TC Dec. 2015 3541-3554 Ramos, H. S., see Rezende, C., TC March 2015 614-626 Randolph, A., Boucheneb, H., Imine, A., and Quintero, A., On Synthesizing a Consistent Operational Transformation Approach; TC April 2015 10741089 Ranieri, J., Vincenzi, A., Chebira, A., Atienza, D., and Vetterli, M., Near-Optimal Thermal Monitoring Framework for Many-Core Systems-on-Chip; TC Nov. 2015 3197-3209 Ranjan, R., see Menzel, M., TC May 2015 1336-1348 Ranjan, R., see Xue, W., TC Aug. 2015 2382-2393 Ranjan, R., see Liu, C., TC Sept. 2015 2609-2622 + Check author entry for coauthors Rashid, M.M., Gondal, I., and Kamruzzaman, J., Mining Associated Patterns from Wireless Sensor Networks; TC July 2015 1998-2011 Ravi, S. S., see Xue, B., TC Feb. 2015 464-476 Rebeiro, C., and Mukhopadhyay, D., Micro-Architectural Analysis of TimeDriven Cache Attacks: Quest for the Ideal Implementation; TC March 2015 778-790 Reda, S., see Zhan, X., TC Aug. 2015 2267-2278 Reeve, J.S., see Brown, A.D., TC June 2015 1769-1782 Regazzoni, F., see Bayrak, A. G., TC Feb. 2015 329-341 Ren, F., see Jiang, W., TC Sept. 2015 2675-2690 Ren, M., see Kim, D. H., TC Jan. 2015 112-125 Ren, X., Liang, W., and Xu, W., Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling; TC July 2015 1870-1883 Reviriego, P., see Pontarelli, S., TC May 2015 1497-1501 Reyhani-Masoleh, A., see Abdulrahman, E. A. H., TC Feb. 2015 438-451 Reyhani-Masoleh, A., Comments on “Low-Latency Digit-Serial Systolic Double Basis Multiplier over GF (2 ) Using Subquadratic Toeplitz Matrix-Vector Product Approach”; TC April 2015 1215-1216 Reyhani-Masoleh, A., see El-Razouk, H., TC July 2015 2020-2035 Rezende, C., Boukerche, A., Ramos, H. S., and Loureiro, A. A., A Reactive and Scalable Unicast Solution for Video Streaming over VANETs; TC March 2015 614-626 Richard, P., see Nguyen, T.H.C., TC July 2015 1805-1818 Ro, W.W., see Kim, K., TC Oct. 2015 2862-2874 Robert, J., see Negre, C., TC Oct. 2015 2875-2890 Robertazzi, T.G., see Zhang, Z., TC Nov. 2015 3249-3264 Rodriguez, A., and Moreno, F., Evolutionary Computing and Particle Filtering: A Hardware-Based Motion Estimation System; TC Nov. 2015 3140-3152 Rodriguez, E., see Zheng, H., TC June 2015 1607-1621 Rodriguez-Henriquez, F., see Zavattoni, E., TC May 2015 1429-1441 Rojas-Cessa, R., see Salehin, K. M., TC Jan. 2015 205-218 Ros, A., Xekalakis, P., Cintra, M., Acacio, M.E., and Garcia, J.M., Adaptive Selection of Cache Indexing Bits for Removing Conflict Misses; TC June 2015 1534-1547 Rose, G. S., see Rajendran, J., TC March 2015 733-746 Rose, G. S., see Rajendran, J., TC Feb. 2015 410-424 Rotenberg, E., see Sheikh, R., TC Aug. 2015 2182-2203 Rychkov, V., see Zhong, Z., TC Sept. 2015 2506-2518 S Sadeghi-kohan, S., see Alizadeh, B., TC June 2015 1564-1578 Sadiq, U., Kumar, M., Passarella, A., and Conti, M., Service Composition in Opportunistic Networks: A Load and Mobility Aware Solution; TC Aug. 2015 2308-2322 Sahni, S., see Banerjee-Mishra, T., TC April 2015 1119-1132 Sahni, S., see Banerjee, T., TC April 2015 1104-1118 Sahuquillo, J., see Valero, A., TC July 2015 1884-1897 Saifullah, A., Xu, Y., Lu, C., and Chen, Y., End-to-End Communication Delay Analysis in Industrial Wireless Networks; TC May 2015 1361-1374 Salehin, K. M., Rojas-Cessa, R., Lin, C, Dong, Z., and Kijkanjanarat, T., Scheme to Measure Packet Processing Time of a Remote Host through Estimation of End-Link Capacity; TC Jan. 2015 205-218 Sanchez, J.L., see Andujar-Munoz, F.J., TC Oct. 2015 2847-2861 Sanchez-Ramirez, A.H., see Zavattoni, E., TC May 2015 1429-1441 Saqib, F., Dutta, A., Plusquellic, J., Ortiz, P., and Pattichis, M. S., Pipelined Decision Tree Classification Accelerator Implementation in FPGA (DTCAIF); TC Jan. 2015 280-285 Sarkar, P., see Chakraborty, D., TC Sept. 2015 2691-2707 Sarkar, S., Banik, S., and Maitra, S., Differential Fault Attack against Grain Family with Very Few Faults and Minimal Assumptions; TC June 2015 1647-1657 Sarkar, S., Misra, S., Bandyopadhyay, B., Chakraborty, C., and Obaidat, M.S., Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime; TC Oct. 2015 29122925 Schmitt, T., see Kayaalp, M., TC Feb. 2015 533-546 Schneider, S., Hirzel, M., Gedik, B., and Wu, K.-L., Safe Data Parallelism for General Streaming; TC Feb. 2015 504-517 Seetharaman, G., see Banerjee, T., TC April 2015 1104-1118 Sen, A., see Deniz, E., TC Aug. 2015 2239-2252 Sengupta, I., see Datta, K., TC April 2015 1208-1214 Seol, J., see Jin, S., TC Oct. 2015 2833-2846 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Serres, O., see Kayi, A., TC Feb. 2015 316-328 Shaban, K., see Gu, F., TC Aug. 2015 2353-2366 Shang, Y., Li, D., Zhu, J., and Xu, M., On the Network Power Effectiveness of Data Center Architectures; TC Nov. 2015 3237-3248 Shang, Y., see Li, D., TC Sept. 2015 2534-2544 Shao, Z., see Chen, R., TC June 2015 1729-1741 Sheikh, R., Tuck, J., and Rotenberg, E., Control-Flow Decoupling: An Approach for Timely, Non-Speculative Branching; TC Aug. 2015 2182-2203 Shen, G., see Kim, D. H., TC Jan. 2015 112-125 Shen, H., Liu, J., Chen, K., Liu, J., and Moyer, S., SCPS: A Social-Aware Distributed Cyber-Physical Human-Centric Search Engine; TC Feb. 2015 518-532 Shen, H., Lin, Y., and Li, T., Combining Efficiency, Fidelity, and Flexibility in Resource Information Services; TC Feb. 2015 353-367 Shen, H., see Liu, G., TC Jan. 2015 54-70 Shen, H., Li, Z., Liu, J., and Grant, J.E., Knowledge Sharing in the Online Social Network of Yahoo! Answers and Its Implications; TC June 2015 1715-1728 Shen, H., Liu, G., and Chandler, H., Swarm Intelligence Based File Replication and Consistency Maintenance in Structured P2P File Sharing Systems; TC Oct. 2015 2953-2967 Shen, H., see Chen, K., TC April 2015 1029-1042 Shen, X., see Zhang, B., TC June 2015 1548-1563 Shen, Y., see Liu, X., TC Jan. 2015 87-96 Sheu, S., see Chen, C., TC Jan. 2015 180-190 Shi, L., see Li, Q., TC Aug. 2015 2169-2181 Shi, Y., see Cui, Y., TC Jan. 2015 166-179 Shih, H., see Chen, C., TC Jan. 2015 180-190 Shih, Y., Pang, A., Tsai, M., and Chai, C., A Rewarding Framework for Network Resource Sharing in Co-Channel Hybrid Access Femtocell Networks; TC Nov. 2015 3079-3090 Shin, I., see Lee, J., TC April 2015 941-954 Shin, K. G., see Lee, J., TC April 2015 941-954 Shousha, M., see Ibrahim, W., TC May 2015 1217-1229 Shu, J., see Lu, Y., TC Oct. 2015 2819-2832 Shu, L., see Zhu, C., TC July 2015 1844-1856 Shu, P., see Liu, F., TC Nov. 2015 3051-3063 Shu, R., see Jiang, W., TC Sept. 2015 2675-2690 Shukla, S. K., see Xue, B., TC Feb. 2015 464-476 Siegel, H.J., see Al-Qawasmeh, A.M., TC Feb. 2015 477-491 Siegel, H.J., see Khemka, B., TC Aug. 2015 2394-2407 Silvera, R., see Wang, A., TC Jan. 2015 233-246 Sinanoglu, O., see Rajendran, J., TC Feb. 2015 410-424 Sirakoulis, G.C., see Mardiris, V.A., TC Sept. 2015 2476-2489 Smith, S.D., see Du, A.Y., TC Dec. 2015 3541-3554 Song, T., see Kim, D. H., TC Jan. 2015 112-125 Song, X., see Zhou, J., TC Aug. 2015 2408-2414 Song, Y., see Liu, L., TC March 2015 818-831 Sorbello, F., see Franchini, S., TC April 2015 955-970 Sousa, L., RNS Scalers for Extended 4-Moduli Sets; TC Dec. 2015 33223334 Sridhar, N., see McCartney, W.P., TC Oct. 2015 2940-2952 Standaert, F.-X., see Bayrak, A. G., TC Feb. 2015 329-341 Stojmenovic, I., see Huang, H., TC Dec. 2015 3488-3499 Stojmenovic, I., see Yao, H., TC Dec. 2015 3515-3527 Stojmenovic, I., see Yu, S., TC Jan. 2015 139-151 Stojmenovic, I., see Lukic, M., TC May 2015 1416-1428 Stojmenovic, I., see Gu, L., TC July 2015 2049-2059 Stojmenovic, I., see Zeng, D., TC July 2015 1819-1829 Stojmenovic, M., see Huang, Z., TC Aug. 2015 2158-2168 Stoleru, R., see Won, M., TC Dec. 2015 3362-3375 Su, K., see Hsin, H., TC Aug. 2015 2119-2131 Su, K., see Luo, C., TC July 2015 1830-1843 Sun, H., Qin, X., Jiang, H., Huang, J., and Xie, C., RB-Explorer: An Accurate and Practical Approach to Write Amplification Measurement for SSDs; TC April 2015 1133-1148 Sun, J., see Jiang, G., TC Oct. 2015 2926-2939 Sun, Y., Wu, T., Zhao, G., and Guizani, M., Efficient Rule Engine for Smart Building Systems; TC June 2015 1658-1669 Sunar, B., see Wang, W., TC March 2015 698-706 Sunar, B., see Doroz, Y., TC June 2015 1509-1521 Sundaresan, S., Doss, R., and Zhou, W., Zero Knowledge Grouping Proof Protocol for RFID EPC C1G2 Tags; TC Oct. 2015 2994-3008 Susilo, W., see Yuen, T.H., TC Sept. 2015 2595-2608 + Check author entry for coauthors 8 T Tan, Z., Jamdagni, A., He, X., Nanda, P., Liu, R.P., and Hu, J., Detection of Denial-of-Service Attacks Based on Computer Vision Techniques; TC Sept. 2015 2519-2533 Tang, S., see Li, J., TC Dec. 2015 3569-3579 Tang, S., see Huang, X., TC April 2015 971-983 Tang, X., see Li, K., TC Jan. 2015 191-204 Tang, X., see Zheng, H., TC Oct. 2015 2752-2766 Tang, X., see Lu, Y., TC Aug. 2015 2367-2381 Tang, Y., and Bergmann, N.W., A Hardware Scheduler Based on Task Queues for FPGA-Based Embedded Real-Time Systems; TC May 2015 1254-1267 Taouil, M., see Hamdioui, S., TC Jan. 2015 247-259 Tari, Z., see Yaakob, N., TC June 2015 1594-1606 Tari, Z., see Kumarage, H., TC Sept. 2015 2573-2585 Temam, O., see Chen, T., TC May 2015 1442-1455 Temple, S., see Brown, A.D., TC June 2015 1769-1782 Teruya, T., see Zavattoni, E., TC May 2015 1429-1441 Thomas, L., see Xu, D., TC Sept. 2015 2490-2505 Thornton, M.A., Simulation and Implication Using a Transfer Function Model for Switching Logic; TC Dec. 2015 3580-3590 Tirumurti, C., see Maniatakos, M., TC Sept. 2015 2664-2674 Trucco, G., see Bernasconi, A., TC Dec. 2015 3605-3618 Tsai, M., see Shih, Y., TC Nov. 2015 3079-3090 Tsao, C., Chang, Y., Yang, M., and Huang, P., Efficient Victim Block Selection for Flash Storage Devices; TC Dec. 2015 3444-3460 Tsioliaridou, A., see Liaskos, C., TC May 2015 1282-1295 Tu, Y., see Xu, Z., TC Nov. 2015 3223-3236 Tuck, J., see Sheikh, R., TC Aug. 2015 2182-2203 Turgut, D., see Akbas, M.I., TC April 2015 1015-1028 Tzeng, N.-F., see Jangjaimon, I., TC Feb. 2015 396-409 V Vacca, M., see Causapruno, G., TC July 2015 1940-1953 Vadhiyar, S., see George, C., TC Aug. 2015 2213-2225 Valero, A., Sahuquillo, J., Petit, S., Lopez, P., and Duato, J., Design of Hybrid Second-Level Caches; TC July 2015 1884-1897 Varadharajan, V, see Haghighi, M.S., TC March 2015 627-639 Vasilakos, A. V., see Liu, L., TC March 2015 818-831 Vasilakos, A.V., see Bhuiyan, M.Z.A., TC July 2015 1968-1982 Vassallo, G., see Franchini, S., TC April 2015 955-970 Veeravalli, B., see Li, K., TC Jan. 2015 191-204 Vetterli, M., see Ranieri, J., TC Nov. 2015 3197-3209 Vilanova, L., see Alvarez, L., TC Jan. 2015 152-165 Villa, T., see Bernasconi, A., TC Dec. 2015 3605-3618 Villar-Ortiz, J.A., see Andujar-Munoz, F.J., TC Oct. 2015 2847-2861 Vincenzi, A., see Ranieri, J., TC Nov. 2015 3197-3209 Vitabile, S., see Franchini, S., TC April 2015 955-970 Voyiatzis, I.K., and Kavvadias, D.J., On the Generation of SIC Pairs in Optimal Time; TC Oct. 2015 2891-2901 W Wan, X., see Zhang, B., TC June 2015 1548-1563 Wang, A., Gaudet, M., Wu, P., Ohmacht, M., Amaral, J. N., Barton, C., Silvera, R., and Michael, M. M., Software Support and Evaluation of Hardware Transactional Memory on Blue Gene/Q; TC Jan. 2015 233-246 Wang, B., Xu, H., Liu, W., and Yang, L. T., The Optimal Node Placement for Long Belt Coverage in Wireless Networks; TC Feb. 2015 587-592 Wang, C., see Di, S., TC June 2015 1755-1768 Wang, C., Li, X., Zhang, J., Chen, P., Chen, Y., Zhou, X., and Cheung, R.C., Architecture Support for Task Out-of-Order Execution in MPSoCs; TC May 2015 1296-1310 Wang, C., see Huang, Z., TC Aug. 2015 2158-2168 Wang, C., see Huang, P., TC April 2015 1149-1161 Wang, D., see Zhou, S., TC Feb. 2015 547-555 Wang, G., see Bhuiyan, M. Z. A., TC Feb. 2015 382-395 Wang, G., see Bhuiyan, M.Z.A., TC July 2015 1968-1982 Wang, H., see Lu, G., TC May 2015 1389-1401 Wang, J., see Chen, D., TC March 2015 707-719 9 Wang, J., see Zhang, G., TC Jan. 2015 32-44 Wang, J., see Zhang, T., TC June 2015 1522-1533 Wang, J., Chen, X., Huang, X., You, I., and Xiang, Y., Verifiable Auditing for Outsourced Database in Cloud Computing; TC Nov. 2015 3293-3303 Wang, J., Lam, K.-Y., Chang, Y.-H., Hsieh, J.-W., and Huang, P.-C., BlockBased Multi-Version B -Tree for Flash-Based Embedded Database Systems; TC April 2015 925-940 Wang, J., Bao, W., Zhu, X., Yang, L.T., and Xiang, Y., FESTAL: Fault-Tolerant Elastic Scheduling Algorithm for Real-Time Tasks in Virtualized Clouds; TC Sept. 2015 2545-2558 Wang, K., see Manoj P. D., S., TC Nov. 2015 3022-3036 Wang, L., see Chen, D., TC March 2015 707-719 Wang, L., see Menzel, M., TC May 2015 1336-1348 Wang, L., see Xue, W., TC Aug. 2015 2382-2393 Wang, L., see Liu, C., TC Sept. 2015 2609-2622 Wang, P.-C., see Cheng, Y.-C., TC Feb. 2015 582-586 Wang, W., Hu, Y., Chen, L., Huang, X., and Sunar, B., Exploring the Feasibility of Fully Homomorphic Encryption; TC March 2015 698-706 Wang, X., see Zheng, W., TC Nov. 2015 3278-3292 Wang, X., see Xu, Z., TC Nov. 2015 3223-3236 Wang, X., Zheng, Y., Basak, A., and Bhunia, S., IIPS: Infrastructure IP for Secure SoC Design; TC Aug. 2015 2226-2238 Wang, X., see Xue, W., TC Aug. 2015 2382-2393 Wang, Y., see Yu, W., TC Feb. 2015 556-568 Wang, Y., see Cui, Y., TC Jan. 2015 166-179 Wang, Y., see Chen, R., TC June 2015 1729-1741 Wang, Y., see Jiang, G., TC Oct. 2015 2926-2939 Wang, Y., Lu, P., and Kent, K.B., WaFS: A Workflow-Aware File System for Effective Storage Utilization in the Cloud; TC Sept. 2015 2716-2729 Wang, Z., Huang, D., Zhu, Y., Li, B., and Chung, C., Efficient Attribute-Based Comparable Data Access Control; TC Dec. 2015 3430-3443 Wang, Z., see Ma, S., TC March 2015 763-777 Wang, Z., see Zhou, Z., TC Jan. 2015 126-138 Ward, L., see Liu, G., TC Jan. 2015 54-70 Wei, D. S., see Hsu, A. C.-C., TC Feb. 2015 342-352 Wei, K., Guo, S., Zeng, D., Xu, K., and Li, K., Exploiting Small World Properties for Message Forwarding in Delay Tolerant Networks; TC Oct. 2015 2809-2818 Wen, S., Haghighi, M. S., Chen, C., Xiang, Y., Zhou, W., and Jia, W., A Sword with Two Edges: Propagation Studies on Both Positive and Negative Information in Online Social Networks; TC March 2015 640-653 Weng, C., Zhan, J., and Luo, Y., TSAC: Enforcing Isolation ofVirtual Machines in Clouds; TC May 2015 1470-1482 Weng, C., see Lu, G., TC May 2015 1389-1401 Won, M., and Stoleru, R., A Hybrid Multicast Routing for Large Scale Sensor Networks with Holes; TC Dec. 2015 3362-3375 Won, Y., Lim, K., and Min, J., MUCH: Multithreaded Content-Based File Chunking; TC May 2015 1375-1388 Woo, D. H., see Kim, D. H., TC Jan. 2015 112-125 Woo, D.H., see Lee, J., TC Nov. 2015 3167-3180 Wu, A.-Y., see Chang, E., TC March 2015 868-875 Wu, A.A., see Hsin, H., TC Aug. 2015 2119-2131 Wu, C., see Chen, C., TC Jan. 2015 180-190 Wu, F., see Zheng, Z., TC July 2015 2071-2083 Wu, J., see Zhang, S., TC March 2015 654-667 Wu, J., see Bhuiyan, M. Z. A., TC Feb. 2015 382-395 Wu, J., see Jiang, G., TC Oct. 2015 2926-2939 Wu, J., see Li, D., TC Nov. 2015 3210-3222 Wu, J., see Yu, Z., TC Nov. 2015 3153-3166 Wu, K.-L., see Schneider, S., TC Feb. 2015 504-517 Wu, K.-R., see Lin, T.-Y., TC Jan. 2015 71-86 Wu, P., see Wang, A., TC Jan. 2015 233-246 Wu, S., Jiang, H., and Mao, B., Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers; TC Sept. 2015 2637-2651 Wu, T., see Sun, Y., TC June 2015 1658-1669 Wu, W., see Luo, C., TC July 2015 1830-1843 Wu, Y., see Chen, T., TC May 2015 1442-1455 Wu, Y., Yan, C.G., Liu, L., Ding, Z.J., and Jiang, C.J., An Adaptive Multilevel Indexing Method for Disaster Service Discovery; TC Sept. 2015 2447-2459 Wu, Y., see Jiang, W., TC Sept. 2015 2675-2690 Wu, Z.-L., see Zhou, J.-X., TC March 2015 876-881 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 X Xekalakis, P., see Ros, A., TC June 2015 1534-1547 Xia, F., Ahmed, A.M., Yang, L.T., and Luo, Z., Community-Based Event Dissemination with Optimal Load Balancing; TC July 2015 1857-1869 Xia, W., Jiang, H., Feng, D., and Hua, Y., Similarity and Locality Based Indexing for High Performance Data Deduplication; TC April 2015 11621176 Xiang, Y, see Haghighi, M.S., TC March 2015 627-639 Xiang, Y., see Li, J., TC Dec. 2015 3569-3579 Xiang, Y., see Zhu, X., TC Dec. 2015 3389-3403 Xiang, Y., see Wen, S., TC March 2015 640-653 Xiang, Y., see Chen, W., TC Oct. 2015 2741-2751 Xiang, Y., see Wang, J., TC Nov. 2015 3293-3303 Xiang, Y., see Zeng, D., TC Nov. 2015 3128-3139 Xiang, Y., see Huang, X., TC April 2015 971-983 Xiang, Y., see Wang, J., TC Sept. 2015 2545-2558 Xiao, B., see Liu, X., TC Nov. 2015 3265-3277 Xiao, L., see Huang, P., TC April 2015 1149-1161 Xie, C., see Huang, J., TC Nov. 2015 3037-3050 Xie, C., see Sun, H., TC April 2015 1133-1148 Xing, L., see Levitin, G., TC April 2015 1043-1057 Xiong, H., see Zhang, D., TC Feb. 2015 452-463 Xu, C., see Yu, W., TC Feb. 2015 556-568 Xu, C., see Yu, Z., TC Nov. 2015 3153-3166 Xu, D., Liu, X., and Fan, B., Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand; TC March 2015 682-697 Xu, D., Kent, M., Thomas, L., Mouelhi, T., and Le Traon, Y., Automated Model-Based Testing of Role-Based Access Control Using Predicate/Transition Nets; TC Sept. 2015 2490-2505 Xu, H., see Wang, B., TC Feb. 2015 587-592 Xu, K., see Wei, K., TC Oct. 2015 2809-2818 Xu, L., see Zhou, S., TC Feb. 2015 547-555 Xu, L., see Chen, W., TC Oct. 2015 2741-2751 Xu, L., see Huang, X., TC April 2015 971-983 Xu, M., see Shang, Y., TC Nov. 2015 3237-3248 Xu, W., Liang, W., and Lin, X, Approximation Algorithms for Min-Max Cycle Cover Problems; TC March 2015 600-613 Xu, W., see Ren, X., TC July 2015 1870-1883 Xu, Y., see Saifullah, A., TC May 2015 1361-1374 Xu, Y., see Zhu, Y., TC Aug. 2015 2145-2157 Xu, Y., see Xue, W., TC Aug. 2015 2382-2393 Xu, Z., see Chen, T., TC May 2015 1442-1455 Xu, Z., Tu, Y., and Wang, X., Online Energy Estimation of Relational Operations in Database Systems; TC Nov. 2015 3223-3236 Xue, B., Shukla, S. K., and Ravi, S. S., Optimization of Latency Insensitive Systems Through Back Pressure Minimization; TC Feb. 2015 464-476 Xue, C.J., see Li, Q., TC Aug. 2015 2169-2181 Xue, W., Yang, C., Fu, H., Wang, X., Xu, Y., Liao, J., Gan, L., Lu, Y., Ranjan, R., and Wang, L., Ultra-Scalable CPU-MIC Acceleration of Mesoscale Atmospheric Modeling on Tianhe-2; TC Aug. 2015 2382-2393 Y Yaakob, N., Khalil, I., Kumarage, H., Atiquzzaman, M., and Tari, Z., By-Passing Infected Areas in Wireless Sensor Networks Using BPR; TC June 2015 1594-1606 Yaghini, P.M., see Eghbal, A., TC Dec. 2015 3591-3604 Yan, C.G., see Wu, Y., TC Sept. 2015 2447-2459 Yang, C., see Zhang, X., TC Aug. 2015 2293-2307 Yang, C., see Xue, W., TC Aug. 2015 2382-2393 Yang, C., see Liu, C., TC Sept. 2015 2609-2622 Yang, C.-N., Lin, Z.-Y., and Peng, S.-L., Reducing Code Length of SecondOrder Spectral-Null Code; TC Feb. 2015 492-503 Yang, L., Cao, J., Cheng, H., and Ji, Y., Multi-User Computation Partitioning for Latency Sensitive Mobile Cloud Applications; TC Aug. 2015 2253-2266 Yang, L. T., see Zhang, D., TC Feb. 2015 452-463 Yang, L. T., see Wang, B., TC Feb. 2015 587-592 Yang, L.T., see Zhu, X., TC Dec. 2015 3389-3403 Yang, L.T., see Xia, F., TC July 2015 1857-1869 Yang, L.T., see Zhu, C., TC July 2015 1844-1856 Yang, L.T., see Wang, J., TC Sept. 2015 2545-2558 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Yang, M., see Tsao, C., TC Dec. 2015 3444-3460 Yang, S.-C., see Zhou, J.-X., TC March 2015 876-881 Yang, W., Li, K., Mo, Z., and Li, K., Performance Optimization Using Partitioned SpMV on GPUs and Multicore CPUs; TC Sept. 2015 2623-2636 Yang, X., Lin, J., Yu, W., Moulema, P.-M., Fu, X., and Zhao, W., A Novel En-Route Filtering Scheme Against False Data Injection Attacks in CyberPhysical Networked Systems; TC Jan. 2015 4-18 Yang, Y., see Guo, S., TC March 2015 747-762 Yang, Y., see Yuan, D., TC Oct. 2015 2781-2795 Yang, Y., see Liu, W., TC May 2015 1323-1335 Yang, Y., see Zhang, G., TC May 2015 1456-1469 Yang, Y., see Guo, Z., TC April 2015 1058-1073 Yang, Y., see Guo, Z., TC July 2015 1912-1926 Yang, Z., see Du, A.Y., TC Dec. 2015 3541-3554 Yao, H., Zeng, D., Huang, H., Guo, S., Barnawi, A., and Stojmenovic, I., Opportunistic Offloading of Deadline-Constrained Bulk Cellular Traffic in Vehicular DTNs; TC Dec. 2015 3515-3527 Yavits, L., Morad, A., and Ginosar, R., Computer Architecture with Associative Processor Replacing Last-Level Cache and SIMD Accelerator; TC Feb. 2015 368-381 Yazdani, N., see Dehyadegari, M., TC Aug. 2015 2132-2144 Ye, B., see Huang, H., TC Dec. 2015 3488-3499 Ye, D., and Zhang, M., A Self-Adaptive Strategy for Evolution of Cooperation in Distributed Networks; TC April 2015 899-911 Yin, G.-C., see Lin, T.-Y., TC Jan. 2015 71-86 You, I., see Wang, J., TC Nov. 2015 3293-3303 Younis, M.F., see Lasla, N., TC Aug. 2015 2103-2118 Yu, H., see Manoj P. D., S., TC Nov. 2015 3022-3036 Yu, L., see Zheng, Z., TC May 2015 1402-1415 Yu, S., Guo, S., and Stojmenovic, I., Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace; TC Jan. 2015 139-151 Yu, S., see Zeng, D., TC July 2015 1819-1829 Yu, W., Wang, Y., Que, X., and Xu, C., Virtual Shuffling for Efficient Data Movement in MapReduce; TC Feb. 2015 556-568 Yu, W., see Yang, X., TC Jan. 2015 4-18 Yu, Z., Eeckhout, L., Goswami, N., Li, T., John, L.K., Jin, H., Xu, C., and Wu, J., GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation; TC Nov. 2015 3153-3166 Yu-Chun, C., Chou, C., Hsiaokuang Wu, E., and Chen, G., A Cognitive TCP Design for a Cognitive Radio Network with an Unstable-Bandwidth Link; TC Oct. 2015 2730-3740 Yuan, D., Liu, X., and Yang, Y., Dynamic On-the-Fly Minimum Cost Benchmarking for Storing Generated Scientific Datasets in the Cloud; TC Oct. 2015 2781-2795 Yuan, K.-W., see Zhou, J.-X., TC March 2015 876-881 Yuan, L., see Lu, G., TC May 2015 1389-1401 Yuen, T.H., Liu, J.K., Au, M.H., Huang, X., Susilo, W., and Zhou, J., k-Times Attribute-Based Anonymous Access Control for Cloud Computing; TC Sept. 2015 2595-2608 Z Zamboni, M., see Causapruno, G., TC July 2015 1940-1953 Zavattoni, E., Perez, L.J.D., Mitsunari, S., Sanchez-Ramirez, A.H., Teruya, T., and Rodriguez-Henriquez, F., Software Implementation of an AttributeBased Encryption Scheme; TC May 2015 1429-1441 Zeng, D., see Yao, H., TC Dec. 2015 3515-3527 Zeng, D., see Wei, K., TC Oct. 2015 2809-2818 Zeng, D., Li, P., Guo, S., Miyazaki, T., Hu, J., and Xiang, Y., Energy Minimization in Multi-Task Software-Defined Sensor Networks; TC Nov. 2015 3128-3139 Zeng, D., see Gu, L., TC July 2015 2049-2059 Zeng, D., Guo, S., Barnawi, A., Yu, S., and Stojmenovic, I., An Improved Stochastic Modeling of Opportunistic Routing in Vehicular CPS; TC July 2015 1819-1829 Zeng, K., see Chen, D., TC March 2015 707-719 Zhan, J., see Weng, C., TC May 2015 1470-1482 Zhan, J., see Lu, G., TC May 2015 1389-1401 Zhan, X., and Reda, S., Power Budgeting Techniques for Data Centers; TC Aug. 2015 2267-2278 Zhang, B., Wan, X., Luo, J., and Shen, X., A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees; TC June 2015 1548-1563 + Check author entry for coauthors 10 Zhang, C., see Rajendran, J., TC Feb. 2015 410-424 Zhang, D., Xiong, H., Yang, L. T., and Gauthier, V., NextCell: Predicting Location Using Social Interplay from Cell Phone Traces; TC Feb. 2015 452-463 Zhang, D., see Zhang, D., TC Feb. 2015 452-463 Zhang, G., Li, K., Wang, J., and Zheng, W., Accelerate RDP RAID-6 Scaling by Reducing Disk I/Os and XOR Operations; TC Jan. 2015 32-44 Zhang, G., Liu, X., and Yang, Y., Time-Series Pattern Based Effective Noise Generation for Privacy Protection on Cloud; TC May 2015 1456-1469 Zhang, H., see Liu, L., TC March 2015 818-831 Zhang, H., see Rajendran, J., TC Feb. 2015 410-424 Zhang, J., see Wang, C., TC May 2015 1296-1310 Zhang, J.Y., see Matula, D.W., TC July 2015 2012-2019 Zhang, M., see Ye, D., TC April 2015 899-911 Zhang, S., Wu, J., and Lu, S., Collaborative Mobile Charging; TC March 2015 654-667 Zhang, S., see Liu, X., TC Nov. 2015 3265-3277 Zhang, T., Wang, J., Huang, J., Huang, Y., Chen, J., and Pan, Y., AdaptiveAcceleration Data Center TCP; TC June 2015 1522-1533 Zhang, X., Dou, W., Pei, J., Nepal, S., Yang, C., Liu, C., and Chen, J., Proximity-Aware Local-Recoding Anonymization with MapReduce for Scalable Big Data Privacy Preservation in Cloud; TC Aug. 2015 2293-2307 Zhang, X., see Liu, C., TC Sept. 2015 2609-2622 Zhang, Y., see Zheng, H., TC June 2015 1607-1621 Zhang, Z., see Oshin, T.O., TC June 2015 1680-1693 Zhang, Z., see Zheng, H., TC June 2015 1607-1621 Zhang, Z., and Robertazzi, T.G., Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors; TC Nov. 2015 3249-3264 Zhao, G., see Sun, Y., TC June 2015 1658-1669 Zhao, W., see Yang, X., TC Jan. 2015 4-18 Zhao, X., see Kim, D. H., TC Jan. 2015 112-125 Zheng, H., Zhang, Z., Myers, C.J., Rodriguez, E., and Zhang, Y., Compositional Model Checking of Concurrent Systems; TC June 2015 1607-1621 Zheng, H., and Tang, X., Analysis of Server Provisioning for Distributed Interactive Applications; TC Oct. 2015 2752-2766 Zheng, W., see Zhang, G., TC Jan. 2015 32-44 Zheng, W., Ma, K., and Wang, X., TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage; TC Nov. 2015 32783292 Zheng, Y., see Wang, X., TC Aug. 2015 2226-2238 Zheng, Z., and Lyu, M. R., Selecting an Optimal Fault Tolerance Strategy for Reliable Service-Oriented Systems with Local and Global Constraints; TC Jan. 2015 219-232 Zheng, Z., Yu, L., and Lan, Z., Reliability-Aware Speedup Models for Parallel Applications with Coordinated Checkpointing/Restart; TC May 2015 14021415 Zheng, Z., Gui, Y., Wu, F., and Chen, G., STAR: Strategy-Proof Double Auctions for Multi-Cloud, Multi-Tenant Bandwidth Reservation; TC July 2015 2071-2083 Zhong, Z., Rychkov, V., and Lastovetsky, A., Data Partitioning on Multicore and Multi-GPU Platforms Using Functional Performance Models; TC Sept. 2015 2506-2518 Zhou, J., Lan, C., Hung, W.N.N., Guo, X., and Song, X., A Quantitative Characterization of Cross Coverage; TC Aug. 2015 2408-2414 Zhou, J., see Huang, X., TC April 2015 971-983 Zhou, J., see Yuen, T.H., TC Sept. 2015 2595-2608 Zhou, J.-X., Wu, Z.-L., Yang, S.-C., and Yuan, K.-W., Symmetric Property and Reliability of Balanced Hypercube; TC March 2015 876-881 -Diagnosability of Star Graph Zhou, S., Lin, L., Xu, L., and Wang, D., The Networks; TC Feb. 2015 547-555 Zhou, W., see Wen, S., TC March 2015 640-653 Zhou, W., see Sundaresan, S., TC Oct. 2015 2994-3008 Zhou, X., see Lama, P., TC Jan. 2015 97-111 Zhou, X., see Wang, C., TC May 2015 1296-1310 Zhou, Z., Huang, D., and Wang, Z., Efficient Privacy-Preserving Ciphertext-Policy Attribute Based-Encryption and Broadcast Encryption; TC Jan. 2015 126-138 Zhu, C., Leung, V.C.M., Yang, L.T., and Shu, L., Collaborative Location-Based Sleep Scheduling for Wireless Sensor Networks Integratedwith Mobile Cloud Computing; TC July 2015 1844-1856 Zhu, J., see Shang, Y., TC Nov. 2015 3237-3248 Zhu, Q., see Qian, J., TC Dec. 2015 3500-3514 Zhu, X., Chen, C., Yang, L.T., and Xiang, Y., ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds; TC Dec. 2015 3389-3403 Zhu, X., see Wang, J., TC Sept. 2015 2545-2558 11 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Zhu, Y., see Wang, Z., TC Dec. 2015 3430-3443 Zhu, Y., Lin, J., Lee, P.P.C., and Xu, Y., Boosting Degraded Reads in Heterogeneous Erasure-Coded Storage Systems; TC Aug. 2015 2145-2157 Ziavras, S. G., see Beldianu, S. F., TC March 2015 805-817 Zomaya, A.Y., In Memoriam [Ivan Stojmenovic]; TC Jan. 2015 3 Zong, Z., see Qiu, M., TC Dec. 2015 3528-3540 Zwolinski, M., see Nechma, T., TC April 2015 1090-1103 SUBJECT INDEX 3G 3G mobile communication Network Variation and Fault Tolerant Performance Acceleration in Mobile Devices with Simultaneous Remote Execution. Kim, K., +, TC Oct. 2015 2862-2874 A Acceleration GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation. Yu, Z., +, TC Nov. 2015 3153-3166 Accelerometers Energy-Efficient Real-Time Human Mobility State Classification Using Smartphones. Oshin, T.O., +, TC June 2015 1680-1693 Access control A Rewarding Framework for Network Resource Sharing in Co-Channel Hybrid Access Femtocell Networks. Shih, Y., +, TC Nov. 2015 3079-3090 A Split MAC Approach for SDR Platforms. Di Francesco, P., +, TC April 2015 912-924 A Stochastic Time-Domain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks. Haghighi, M.S., +, TC March 2015 627-639 A Time Fairness-Based MAC Algorithm for Throughput Maximization in 802.11 Networks. Le, Y., +, TC Jan. 2015 19-31 Coexistence Wi-Fi MAC Design for Mitigating Interference Caused by Collocated Bluetooth. Hsu, A. C.-C., +, TC Feb. 2015 342-352 Completely Pinpointing the Missing RFID Tags in a Time-Efficient Way. Liu, X., +, TC Jan. 2015 87-96 Efficient Attribute-Based Comparable Data Access Control. Wang, Z., +, TC Dec. 2015 3430-3443 Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Actuators Efficient Rule Engine for Smart Building Systems. Sun, Y., +, TC June 2015 1658-1669 Adaptive systems Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 Adders An Analytical Framework for Evaluating the Error Characteristics of Approximate Adders. Liu, C., +, TC May 2015 1268-1281 Bit-Width Optimization by Divide-and-Conquer for Fixed-Point Digital Signal Processing Systems. Chung, J., +, TC Nov. 2015 3091-3101 Reviewing High-Radix Signed-Digit Adders. Kornerup, P., TC May 2015 1502-1505 Aerospace computing Mission Reliability, Cost and Time for Cold Standby Computing Systems with Periodic Backup. Levitin, G., +, TC April 2015 1043-1057 Agent-based modeling ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds. Zhu, X., +, TC Dec. 2015 3389-3403 Air conditioning Power and Thermal-Aware Workload Allocation in Heterogeneous Data Centers. Al-Qawasmeh, A.M., +, TC Feb. 2015 477-491 Air traffic control Mission Reliability, Cost and Time for Cold Standby Computing Systems with Periodic Backup. Levitin, G., +, TC April 2015 1043-1057 + Check author entry for coauthors Algebra Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Algorithm design and analysis RNS Scalers for Extended 4-Moduli Sets. Sousa, L., TC Dec. 2015 33223334 Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits. Lee, D.T., +, TC Dec. 2015 3376-3388 Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching. Chang, C., +, TC Dec. 2015 3404-3416 Bit-Width Optimization by Divide-and-Conquer for Fixed-Point Digital Signal Processing Systems. Chung, J., +, TC Nov. 2015 3091-3101 DCCS: Double Circular Caching Scheme for DRAM/PRAM Hybrid Cache. Hsieh, J., +, TC Nov. 2015 3115-3127 Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors. Zhang, Z., +, TC Nov. 2015 3249-3264 Analytic hierarchy process CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Android (operating system) A Lightweight Virtualization Solution for Android Devices. Chen, W., +, TC Oct. 2015 2741-2751 Ant colony optimization Ant Colony Optimization-Based Adaptive Network-on-Chip Routing Framework Using Network Information Region. Hsin, H., +, TC Aug. 2015 2119-2131 Regional ACO-Based Cascaded Adaptive Routing for Traffic Balancing in Mesh-Based Network-on-Chip Systems. Chang, E., +, TC March 2015 868-875 Antenna arrays Dynamic Antenna Management for Uplink Energy Efficiency on 802.11n Mobile Devices. Cheng, S., +, TC Oct. 2015 2767-2780 Application program interfaces Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 ViPZonE: Hardware Power Variability-Aware Virtual Memory Management for Energy Savings. Gottscho, M., +, TC May 2015 1483-1496 Application specific integrated circuits A Generalization of Addition Chains and Fast Inversions in Binary Fields. Jarvinen, K., +, TC Sept. 2015 2421-2432 Accelerating Fully Homomorphic Encryption in Hardware. Doroz, Y., +, TC June 2015 1509-1521 New Hardware Implementations of WG (29, 11) and WG- 16 Stream Ciphers and Using Polynomial Basis. El-Razouk, H., +, TC July 2015 20202035 Towards an Oscillator Based TRNG with a Certified Entropy Rate. Lubicz, D., +, TC April 2015 1191-1200 Approximation theory An Analytical Framework for Evaluating the Error Characteristics of Approximate Adders. Liu, C., +, TC May 2015 1268-1281 An Improved Approximation Ratio to the Partial-Terminal Steiner Tree Problem. Lee, C.-W., +, TC Jan. 2015 274-279 Approximation Algorithms for Min-Max Cycle Cover Problems. Xu, W., +, TC March 2015 600-613 Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 Multiplicative Division Employing Independent Factors. Matula, D.W., +, TC July 2015 2012-2019 Unified Mitchell-Based Approximation for Efficient Logarithmic Conversion Circuit. Low, J.Y.L., +, TC June 2015 1783-1797 Associative processing Computer Architecture with Associative Processor Replacing Last-Level Cache and SIMD Accelerator. Yavits, L., +, TC Feb. 2015 368-381 Authentication Comments on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”. Kim, Y., TC Dec. 2015 3619-3620 Authorization k-Times Attribute-Based Anonymous Access Control for Cloud Computing. Yuen, T.H., +, TC Sept. 2015 2595-2608 Automated Model-Based Testing of Role-Based Access Control Using Predicate/Transition Nets. Xu, D., +, TC Sept. 2015 2490-2505 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 12 H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor. Jin, S., +, TC Oct. 2015 2833-2846 Automatic test pattern generation On the Generation of SIC Pairs in Optimal Time. Voyiatzis, I.K., +, TC Oct. 2015 2891-2901 Automobiles Multiprocessor Capacity Metric and Analysis. Otoom, M., +, TC Nov. 2015 3181-3196 Autoregressive moving average processes Time Series Characterization of Gaming Workload for Runtime Power Management. Dietrich, B., +, TC Jan. 2015 260-273 Building management systems Efficient Rule Engine for Smart Building Systems. Sun, Y., +, TC June 2015 1658-1669 Built-in self test Address Scrambling and Data Inversion Techniques for Yield Enhancement of NROM-Based ROMs. Lu, S., +, TC May 2015 1230-1240 On the Generation of SIC Pairs in Optimal Time. Voyiatzis, I.K., +, TC Oct. 2015 2891-2901 Business continuity Survivable Cloud Network Mapping for Disaster Recovery Support. Gu, F., +, TC Aug. 2015 2353-2366 B C Bandwidth AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol. Liu, F., +, TC Nov. 2015 3051-3063 An Efficient I/O-Redirection-Based Reconstruction Scheme for Erasure-Coded Storage Clusters. Huang, J., +, TC Nov. 2015 3037-3050 STAR: Strategy-Proof Double Auctions for Multi-Cloud, Multi-Tenant Bandwidth Reservation. Zheng, Z., +, TC July 2015 2071-2083 Batteries TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage. Zheng, W., +, TC Nov. 2015 3278-3292 Bayes methods Accurate and Efficient Estimation of Logic Circuits Reliability Bounds. Ibrahim, W., +, TC May 2015 1217-1229 SCPS: A Social-Aware Distributed Cyber-Physical Human-Centric Search Engine. Shen, H., +, TC Feb. 2015 518-532 Benchmark testing GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation. Yu, Z., +, TC Nov. 2015 3153-3166 Software Support and Evaluation of Hardware Transactional Memory on Blue Gene/Q. Wang, A., +, TC Jan. 2015 233-246 Test Vector Omission for Fault Coverage Improvement of Functional Test Sequences. Pomeranz, I., TC Nov. 2015 3317-3321 Bidirectional control ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds. Zhu, X., +, TC Dec. 2015 3389-3403 Big Data MuR-DPA: Top-Down Levelled Multi-Replica Merkle Hash Tree Based Secure Public Auditing for Dynamic Big Data Storage on Cloud. Liu, C., +, TC Sept. 2015 2609-2622 Proximity-Aware Local-Recoding Anonymization with MapReduce for Scalable Big Data Privacy Preservation in Cloud. Zhang, X., +, TC Aug. 2015 2293-2307 Bioinformatics Multi-Granularity Locality-Sensitive Bloom Filter. Qian, J., +, TC Dec. 2015 3500-3514 Bit error rate Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 Blogs A Generalization of Addition Chains and Fast Inversions in Binary Fields. Jarvinen, K., +, TC Sept. 2015 2421-2432 Bluetooth Coexistence Wi-Fi MAC Design for Mitigating Interference Caused by Collocated Bluetooth. Hsu, A. C.-C., +, TC Feb. 2015 342-352 Body area networks Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 Boolean functions Using Flexibility in P-Circuits by Boolean Relations. Bernasconi, A., +, TC Dec. 2015 3605-3618 Brain models Fast and Scalable Multi-Way Analysis of Massive Neural Data. Chen, D., +, TC March 2015 707-719 Buffer storage Leaving One Slot Empty: Flit Bubble Flow Control for Torus Cache-Coherent NoCs. Ma, S., +, TC March 2015 763-777 Resilient and Power-Efficient Multi-Function Channel Buffers in Networkon-Chip Architectures. DiTomaso, D., +, TC Dec. 2015 3555-3568 Cache storage A Cache Hierarchy Aware Thread Mapping Methodology for GPGPUs. Lai, B. C., +, TC April 2015 884-898 Adaptive Cache Coherence Mechanisms with Producer–Consumer Sharing Optimization for Chip Multiprocessors. Kayi, A., +, TC Feb. 2015 316-328 Adaptive Selection of Cache Indexing Bits for Removing Conflict Misses. Ros, A., +, TC June 2015 1534-1547 An Energy-Efficient Last-Level Cache Architecture for Process VariationTolerant 3D Microprocessors. Kong, J., +, TC Sept. 2015 2460-2475 Compiler-Assisted Refresh Minimization for Volatile STT-RAM Cache. Li, Q., +, TC Aug. 2015 2169-2181 Computer Architecture with Associative Processor Replacing Last-Level Cache and SIMD Accelerator. Yavits, L., +, TC Feb. 2015 368-381 Design of Hybrid Second-Level Caches. Valero, A., +, TC July 2015 18841897 Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 Filter Data Cache: An Energy-Efficient Small L0 Data Cache Architecture Driven byMiss Cost Reduction. Lee, J., +, TC July 2015 1927-1939 Hardware–Software Coherence Protocol for the Coexistence of Caches and Local Memories. Alvarez, L., +, TC Jan. 2015 152-165 ICCI: In-Cache Coherence Information. Garcia-Guirado, A., +, TC April 2015 995-1014 Leaving One Slot Empty: Flit Bubble Flow Control for Torus Cache-Coherent NoCs. Ma, S., +, TC March 2015 763-777 Micro-Architectural Analysis of Time-Driven Cache Attacks: Quest for the Ideal Implementation. Rebeiro, C., +, TC March 2015 778-790 On-Demand Block-Level Address Mapping in Large-Scale NAND Flash Storage Systems. Chen, R., +, TC June 2015 1729-1741 Size-Aware Cache Management for Compressed Cache Architectures. Baek, S., +, TC Aug. 2015 2337-2352 TSAC: Enforcing Isolation ofVirtual Machines in Clouds. Weng, C., +, TC May 2015 1470-1482 Zombie Chasing: Efficient Flash Management Considering Dirty Data in the Buffer Cache. Lee, Y., +, TC Feb. 2015 569-581 Calibration Adaptive Voltage Scaling with In-Situ Detectors in Commercial FPGAs. Nunez-Yanez, J.L., TC Jan. 2015 45-53 Carry logic Reviewing High-Radix Signed-Digit Adders. Kornerup, P., TC May 2015 1502-1505 Cellular automata Automated Design Architecture for 1-D Cellular Automata Using Quantum Cellular Automata. Mardiris, V.A., +, TC Sept. 2015 2476-2489 Cellular radio NextCell: Predicting Location Using Social Interplay from Cell Phone Traces. Zhang, D., +, TC Feb. 2015 452-463 Cellular networks Opportunistic Offloading of Deadline-Constrained Bulk Cellular Traffic in Vehicular DTNs. Yao, H., +, TC Dec. 2015 3515-3527 Central Processing Unit Online Energy Estimation of Relational Operations in Database Systems. Xu, Z., +, TC Nov. 2015 3223-3236 Channel allocation RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Channel coding Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching. Chang, C., +, TC Dec. 2015 3404-3416 + Check author entry for coauthors 13 Checkpointing Design and Implementation of a Journaling File System for Phase-Change Memory. Lee, E., +, TC May 2015 1349-1360 Effective Cost Reduction for Elastic Clouds under Spot Instance Pricing Through Adaptive Checkpointing. Jangjaimon, I., +, TC Feb. 2015 396-409 Fault Tolerance on Large Scale Systems using Adaptive Process Replication. George, C., +, TC Aug. 2015 2213-2225 Reliability-Aware Speedup Models for Parallel Applications with Coordinated Checkpointing/Restart. Zheng, Z., +, TC May 2015 1402-1415 Circuit CAD Piecewise-Functional Broadside Tests Based on Reachable States. Pomeranz, I., TC Aug. 2015 2415-2420 Circuit faults Analytical Fault Tolerance Assessment and Metrics for TSV-Based 3D Network-on-Chip. Eghbal, A., +, TC Dec. 2015 3591-3604 Design of Optimal Scan Tree Based on Compact Test Patterns for Test Time Reduction. Chen, L., +, TC Dec. 2015 3417-3429 Resilient and Power-Efficient Multi-Function Channel Buffers in Networkon-Chip Architectures. DiTomaso, D., +, TC Dec. 2015 3555-3568 Test Vector Omission for Fault Coverage Improvement of Functional Test Sequences. Pomeranz, I., TC Nov. 2015 3317-3321 Circuit optimization Performance-Energy Optimizations for Shared Vector Accelerators in Multicores. Beldianu, S. F., +, TC March 2015 805-817 Circuit simulation Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs. Nechma, T., +, TC April 2015 1090-1103 Closed loop systems Adaptive Voltage Scaling with In-Situ Detectors in Commercial FPGAs. Nunez-Yanez, J.L., TC Jan. 2015 45-53 Cloud computing k-Times Attribute-Based Anonymous Access Control for Cloud Computing. Yuen, T.H., +, TC Sept. 2015 2595-2608 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing. Mei, J., +, TC Nov. 2015 3064-3078 ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds. Zhu, X., +, TC Dec. 2015 3389-3403 CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Collaborative Location-Based Sleep Scheduling for Wireless Sensor Networks Integratedwith Mobile Cloud Computing. Zhu, C., +, TC July 2015 1844-1856 Cost-Effective Authentic and Anonymous Data Sharing with Forward Security. Huang, X., +, TC April 2015 971-983 Dynamic On-the-Fly Minimum Cost Benchmarking for Storing Generated Scientific Datasets in the Cloud. Yuan, D., +, TC Oct. 2015 2781-2795 Effective Cost Reduction for Elastic Clouds under Spot Instance Pricing Through Adaptive Checkpointing. Jangjaimon, I., +, TC Feb. 2015 396-409 FESTAL: Fault-Tolerant Elastic Scheduling Algorithm for Real-Time Tasks in Virtualized Clouds. Wang, J., +, TC Sept. 2015 2545-2558 H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor. Jin, S., +, TC Oct. 2015 2833-2846 Identity-Based Encryption with Outsourced Revocation in Cloud Computing. Li, J., +, TC Feb. 2015 425-437 Multi-User Computation Partitioning for Latency Sensitive Mobile Cloud Applications. Yang, L., +, TC Aug. 2015 2253-2266 MuR-DPA: Top-Down Levelled Multi-Replica Merkle Hash Tree Based Secure Public Auditing for Dynamic Big Data Storage on Cloud. Liu, C., +, TC Sept. 2015 2609-2622 On Nonblocking Multicast Fat-Tree Data Center Networks with Server Redundancy. Guo, Z., +, TC April 2015 1058-1073 Optimal Task Placement with QoS Constraints in Geo-Distributed Data Centers Using DVFS. Gu, L., +, TC July 2015 2049-2059 Optimization of Composite Cloud Service Processing with Virtual Machines. Di, S., +, TC June 2015 1755-1768 Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm. Qiu, M., +, TC Dec. 2015 3528-3540 Power Budgeting Techniques for Data Centers. Zhan, X., +, TC Aug. 2015 2267-2278 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Predicting Transient Downtime in Virtual Server Systems: An Efficient Sample Path Randomization Approach. Du, A.Y., +, TC Dec. 2015 3541-3554 Proximity-Aware Local-Recoding Anonymization with MapReduce for Scalable Big Data Privacy Preservation in Cloud. Zhang, X., +, TC Aug. 2015 2293-2307 Secure Distributed Deduplication Systems with Improved Reliability. Li, J., +, TC Dec. 2015 3569-3579 STAR: Strategy-Proof Double Auctions for Multi-Cloud, Multi-Tenant Bandwidth Reservation. Zheng, Z., +, TC July 2015 2071-2083 Survivable Cloud Network Mapping for Disaster Recovery Support. Gu, F., +, TC Aug. 2015 2353-2366 Time-Series Pattern Based Effective Noise Generation for Privacy Protection on Cloud. Zhang, G., +, TC May 2015 1456-1469 TSAC: Enforcing Isolation ofVirtual Machines in Clouds. Weng, C., +, TC May 2015 1470-1482 WaFS: A Workflow-Aware File System for Effective Storage Utilization in the Cloud. Wang, Y., +, TC Sept. 2015 2716-2729 CMOS integrated circuits New Hardware Implementations of WG (29, 11) and WG- 16 Stream Ciphers Using Polynomial Basis. El-Razouk, H., +, TC July 2015 2020-2035 CMOS logic circuits Interleaving in Systolic-Arrays: A Throughput Breakthrough. Causapruno, G., +, TC July 2015 1940-1953 Cognitive radio A Cognitive TCP Design for a Cognitive Radio Network with an UnstableBandwidth Link. Yu-Chun, C., +, TC Oct. 2015 2730-3740 Collaboration Energy Minimization in Multi-Task Software-Defined Sensor Networks. Zeng, D., +, TC Nov. 2015 3128-3139 Compaction Test Vector Omission for Fault Coverage Improvement of Functional Test Sequences. Pomeranz, I., TC Nov. 2015 3317-3321 Complex networks Characterization of Cascading Failures in Interdependent Cyber-Physical Systems. Huang, Z., +, TC Aug. 2015 2158-2168 Complexity theory RNS Scalers for Extended 4-Moduli Sets. Sousa, L., TC Dec. 2015 33223334 Computability CCLS: An Efficient Local Search Algorithm for Weighted Maximum Satisfiability. Luo, C., +, TC July 2015 1830-1843 Differential Fault Attack against Grain Family with Very Few Faults and Minimal Assumptions. Sarkar, S., +, TC June 2015 1647-1657 Computational complexity Shifted Polynomial Basis Multipliers Based on Subquadratic Toeplitz Matrix-Vector Product Approach for All Irreducible Pentanomials. Han, J., +, TC March 2015 862-867 A Low Complexity Scaling Method for the Lanczos Kernel in Fixed-Point Arithmetic. Jerez, J. L., +, TC Feb. 2015 303-315 A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees. Zhang, B., +, TC June 2015 1548-1563 An FPTAS for Response Time Analysis of Fixed Priority Real-Time Tasks with Resource Augmentation. Nguyen, T.H.C., +, TC July 2015 1805-1818 Analysis of Server Provisioning for Distributed Interactive Applications. Zheng, H., +, TC Oct. 2015 2752-2766 CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Comments on “Low-Latency Digit-Serial Systolic Double Basis Multiplier over GF (2 ) Using Subquadratic Toeplitz Matrix-Vector Product Approach”. Reyhani-Masoleh, A., TC April 2015 1215-1216 Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Cost-Efficient Mapping for Fault-Tolerant Virtual Networks. Jarray, A., +, TC March 2015 668-681 Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 Efficient Rule Engine for Smart Building Systems. Sun, Y., +, TC June 2015 1658-1669 Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Fast and Scalable Multi-Way Analysis of Massive Neural Data. Chen, D., +, TC March 2015 707-719 Mining Associated Patterns from Wireless Sensor Networks. Rashid, M.M., +, TC July 2015 1998-2011 Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 Physarum Optimization: A Biology-Inspired Algorithm for the Steiner Tree Problem in Networks. Liu, L., +, TC March 2015 818-831 Reconfiguring Three-Dimensional Processor Arrays for Fault-Tolerance: Hardness and Heuristic Algorithms. Jiang, G., +, TC Oct. 2015 2926-2939 Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 Synergy of Dynamic Frequency Scaling and Demotion on DRAM Power Management: Models and Optimizations. Lu, Y., +, TC Aug. 2015 23672381 Test Vector Omission for Fault Coverage Improvement of Functional Test Sequences. Pomeranz, I., TC Nov. 2015 3317-3321 VLSI Computational Architectures for the Arithmetic Cosine Transform. Rajapaksha, N., +, TC Sept. 2015 2708-2715 Computational geometry An Effective Area-Based Localization Algorithm for Wireless Networks. Lasla, N., +, TC Aug. 2015 2103-2118 Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Computational modeling A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing. Mei, J., +, TC Nov. 2015 3064-3078 GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation. Yu, Z., +, TC Nov. 2015 3153-3166 GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs. Lee, J., +, TC Nov. 2015 3167-3180 Hyper-Real-Time Ice Simulation and Modeling Using GPGPU. Alawneh, S., +, TC Dec. 2015 3475-3487 Multiprocessor Capacity Metric and Analysis. Otoom, M., +, TC Nov. 2015 3181-3196 Near-Optimal Thermal Monitoring Framework for Many-Core Systems-onChip. Ranieri, J., +, TC Nov. 2015 3197-3209 Predicting Transient Downtime in Virtual Server Systems: An Efficient Sample Path Randomization Approach. Du, A.Y., +, TC Dec. 2015 3541-3554 Simulation and Implication Using a Transfer Function Model for Switching Logic. Thornton, M.A., TC Dec. 2015 3580-3590 Test Vector Omission for Fault Coverage Improvement of Functional Test Sequences. Pomeranz, I., TC Nov. 2015 3317-3321 Computer architecture RNS Scalers for Extended 4-Moduli Sets. Sousa, L., TC Dec. 2015 33223334 Control-Flow Decoupling: An Approach for Timely, Non-Speculative Branching. Sheikh, R., +, TC Aug. 2015 2182-2203 DCCS: Double Circular Caching Scheme for DRAM/PRAM Hybrid Cache. Hsieh, J., +, TC Nov. 2015 3115-3127 Design of Optimal Scan Tree Based on Compact Test Patterns for Test Time Reduction. Chen, L., +, TC Dec. 2015 3417-3429 Efficient Victim Block Selection for Flash Storage Devices. Tsao, C., +, TC Dec. 2015 3444-3460 GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation. Yu, Z., +, TC Nov. 2015 3153-3166 On the Network Power Effectiveness of Data Center Architectures. Shang, Y., +, TC Nov. 2015 3237-3248 Statistical Performance Comparisons of Computers. Chen, T., +, TC May 2015 1442-1455 Using Flexibility in P-Circuits by Boolean Relations. Bernasconi, A., +, TC Dec. 2015 3605-3618 Computer centers PowerTracer: Tracing Requests in Multi-Tier Services to Reduce Energy Inefficiency. Lu, G., +, TC May 2015 1389-1401 Adaptive-Acceleration Data Center TCP. Zhang, T., +, TC June 2015 15221533 Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand. Xu, D., +, TC March 2015 682-697 Exploring Server Redundancy in Nonblocking Multicast Data Center Networks. Guo, Z., +, TC July 2015 1912-1926 EXR: Greening Data Center Network with Software Defined Exclusive Routing. Li, D., +, TC Sept. 2015 2534-2544 + Check author entry for coauthors 14 On Nonblocking Multicast Fat-Tree Data Center Networks with Server Redundancy. Guo, Z., +, TC April 2015 1058-1073 Optimal Task Placement with QoS Constraints in Geo-Distributed Data Centers Using DVFS. Gu, L., +, TC July 2015 2049-2059 Power and Thermal-Aware Workload Allocation in Heterogeneous Data Centers. Al-Qawasmeh, A.M., +, TC Feb. 2015 477-491 Power Budgeting Techniques for Data Centers. Zhan, X., +, TC Aug. 2015 2267-2278 Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers. Wu, S., +, TC Sept. 2015 2637-2651 Sliding Mode Congestion Control for Data Center Ethernet Networks. Jiang, W., +, TC Sept. 2015 2675-2690 Virtual Resource Allocation Based on Link Interference in Cayley Wireless Data Centers. Luo, J., +, TC Oct. 2015 3016-3021 Computer games Time Series Characterization of Gaming Workload for Runtime Power Management. Dietrich, B., +, TC Jan. 2015 260-273 Computer network management Dynamic Antenna Management for Uplink Energy Efficiency on 802.11n Mobile Devices. Cheng, S., +, TC Oct. 2015 2767-2780 Sliding Mode Congestion Control for Data Center Ethernet Networks. Jiang, W., +, TC Sept. 2015 2675-2690 Computer network performance evaluation Community-Based Event Dissemination with Optimal Load Balancing. Xia, F., +, TC July 2015 1857-1869 Network Variation and Fault Tolerant Performance Acceleration in Mobile Devices with Simultaneous Remote Execution. Kim, K., +, TC Oct. 2015 2862-2874 Computer network security An Efficient and Trustworthy P2P and Social Network Integrated File Sharing System. Liu, G., +, TC Jan. 2015 54-70 Detection of Denial-of-Service Attacks Based on Computer Vision Techniques. Tan, Z., +, TC Sept. 2015 2519-2533 Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace. Yu, S., +, TC Jan. 2015 139-151 Computer networks Cost-Efficient Mapping for Fault-Tolerant Virtual Networks. Jarray, A., +, TC March 2015 668-681 EXR: Greening Data Center Network with Software Defined Exclusive Routing. Li, D., +, TC Sept. 2015 2534-2544 Computer science Using Flexibility in P-Circuits by Boolean Relations. Bernasconi, A., +, TC Dec. 2015 3605-3618 Computer vision Detection of Denial-of-Service Attacks Based on Computer Vision Techniques. Tan, Z., +, TC Sept. 2015 2519-2533 Computerized instrumentation Deploying Wireless Sensor Networks with Fault-Tolerance for Structural Health Monitoring. Bhuiyan, M. Z. A., +, TC Feb. 2015 382-395 Computers A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing. Mei, J., +, TC Nov. 2015 3064-3078 Concurrency (computers) Compositional Model Checking of Concurrent Systems. Zheng, H., +, TC June 2015 1607-1621 Software Support and Evaluation of Hardware Transactional Memory on Blue Gene/Q. Wang, A., +, TC Jan. 2015 233-246 Condition monitoring Deploying Wireless Sensor Networks with Fault-Tolerance for Structural Health Monitoring. Bhuiyan, M. Z. A., +, TC Feb. 2015 382-395 Content-addressable storage Adaptive Selection of Cache Indexing Bits for Removing Conflict Misses. Ros, A., +, TC June 2015 1534-1547 PC-TRIO: A Power Efficient TCAM Architecture for Packet Classifiers. Banerjee, T., +, TC April 2015 1104-1118 Cooling TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage. Zheng, W., +, TC Nov. 2015 3278-3292 Cooperative communication Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 15 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Coprocessors Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Performance-Energy Optimizations for Shared Vector Accelerators in Multicores. Beldianu, S. F., +, TC March 2015 805-817 Correlation methods Detection of Denial-of-Service Attacks Based on Computer Vision Techniques. Tan, Z., +, TC Sept. 2015 2519-2533 Cost function Dynamic On-the-Fly Minimum Cost Benchmarking for Storing Generated Scientific Datasets in the Cloud. Yuan, D., +, TC Oct. 2015 2781-2795 Effective Cost Reduction for Elastic Clouds under Spot Instance Pricing Through Adaptive Checkpointing. Jangjaimon, I., +, TC Feb. 2015 396-409 Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand. Xu, D., +, TC March 2015 682-697 Using Flexibility in P-Circuits by Boolean Relations. Bernasconi, A., +, TC Dec. 2015 3605-3618 Crosstalk Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching. Chang, C., +, TC Dec. 2015 3404-3416 Cryptographic protocols Fault Attacks on Pairing-Based Protocols Revisited. Chatterjee, S., +, TC June 2015 1707-1714 Zero Knowledge Grouping Proof Protocol for RFID EPC C1G2 Tags. Sundaresan, S., +, TC Oct. 2015 2994-3008 Cryptography STES: A Stream Cipher Based Low Cost Scheme for Securing Stored Data. Chakraborty, D., +, TC Sept. 2015 2691-2707 A Generalization of Addition Chains and Fast Inversions in Binary Fields. Jarvinen, K., +, TC Sept. 2015 2421-2432 Accelerating Fully Homomorphic Encryption in Hardware. Doroz, Y., +, TC June 2015 1509-1521 Automatic Application of Power Analysis Countermeasures. Bayrak, A. G., +, TC Feb. 2015 329-341 Differential Fault Attack against Grain Family with Very Few Faults and Minimal Assumptions. Sarkar, S., +, TC June 2015 1647-1657 Efficient Privacy-Preserving Ciphertext-Policy Attribute Based-Encryption and Broadcast Encryption. Zhou, Z., +, TC Jan. 2015 126-138 Exploring the Feasibility of Fully Homomorphic Encryption. Wang, W., +, TC March 2015 698-706 Fault Analysis-Based Logic Encryption. Rajendran, J., +, TC Feb. 2015 410-424 Lattice-Based Signatures: Optimization and Implementation on Reconfigurable Hardware. Guneysu, T., +, TC July 2015 1954-1967 New Hardware Implementations of WG (29, 11) and WG- 16 Stream Ciphers Using Polynomial Basis. El-Razouk, H., +, TC July 2015 2020-2035 On Compact Cauchy Matrices for Substitution-Permutation Networks. Cui, T., +, TC July 2015 2098-2102 Secure Distributed Deduplication Systems with Improved Reliability. Li, J., +, TC Dec. 2015 3569-3579 Software Implementation of an Attribute-Based Encryption Scheme. Zavattoni, E., +, TC May 2015 1429-1441 Towards an Oscillator Based TRNG with a Certified Entropy Rate. Lubicz, D., +, TC April 2015 1191-1200 D Data analysis Cost-Effective Authentic and Anonymous Data Sharing with Forward Security. Huang, X., +, TC April 2015 971-983 Fast and Scalable Multi-Way Analysis of Massive Neural Data. Chen, D., +, TC March 2015 707-719 Mining Associated Patterns from Wireless Sensor Networks. Rashid, M.M., +, TC July 2015 1998-2011 Data communication AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol. Liu, F., +, TC Nov. 2015 3051-3063 Joint Optimal Data Rate and Power Allocation in Lossy Mobile Ad Hoc Networks with Delay-Constrained Traffics. Guo, S., +, TC March 2015 747-762 + Check author entry for coauthors Data compression Size-Aware Cache Management for Compressed Cache Architectures. Baek, S., +, TC Aug. 2015 2337-2352 Data flow computing Automatic High-Level Data-Flow Synthesis and Optimization of Polynomial Datapaths Using Functional Decomposition. Ghandali, S., +, TC June 2015 1579-1593 Data handling CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Data Partitioning on Multicore and Multi-GPU Platforms Using Functional Performance Models. Zhong, Z., +, TC Sept. 2015 2506-2518 Enabling Concurrent Failure Recovery for Regenerating-Coding-Based Storage Systems: From Theory to Practice. Li, R., +, TC July 2015 1898-1911 Data mining Detection of Denial-of-Service Attacks Based on Computer Vision Techniques. Tan, Z., +, TC Sept. 2015 2519-2533 Mining Associated Patterns from Wireless Sensor Networks. Rashid, M.M., +, TC July 2015 1998-2011 Data models Hyper-Real-Time Ice Simulation and Modeling Using GPGPU. Alawneh, S., +, TC Dec. 2015 3475-3487 Data privacy Efficient Privacy-Preserving Ciphertext-Policy Attribute Based-Encryption and Broadcast Encryption. Zhou, Z., +, TC Jan. 2015 126-138 Proximity-Aware Local-Recoding Anonymization with MapReduce for Scalable Big Data Privacy Preservation in Cloud. Zhang, X., +, TC Aug. 2015 2293-2307 Time-Series Pattern Based Effective Noise Generation for Privacy Protection on Cloud. Zhang, G., +, TC May 2015 1456-1469 Data protection Automatic Application of Power Analysis Countermeasures. Bayrak, A. G., +, TC Feb. 2015 329-341 Data structures Pubsub: An Efficient Publish/Subscribe System. Banerjee-Mishra, T., +, TC April 2015 1119-1132 Data transfer DCCS: Double Circular Caching Scheme for DRAM/PRAM Hybrid Cache. Hsieh, J., +, TC Nov. 2015 3115-3127 Database indexing Similarity and Locality Based Indexing for High Performance Data Deduplication. Xia, W., +, TC April 2015 1162-1176 Database management systems Block-Based Multi-Version B -Tree for Flash-Based Embedded Database Systems. Wang, J., +, TC April 2015 925-940 Databases Verifiable Auditing for Outsourced Database in Cloud Computing. Wang, J., +, TC Nov. 2015 3293-3303 DC-DC power converters JEM: Just in Time/Just Enough Energy Management Methodology for Computing Systems. Jawad, M., +, TC June 2015 1798-1804 Decision making Utility Functions and Resource Management in an Oversubscribed Heterogeneous Computing Environment. Khemka, B., +, TC Aug. 2015 2394-2407 Decision support systems CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Decision trees Packet Classification Using Dynamically Generated Decision Trees. Cheng, Y.-C., +, TC Feb. 2015 582-586 Pipelined Decision Tree Classification Accelerator Implementation in FPGA (DT-CAIF). Saqib, F., +, TC Jan. 2015 280-285 Decoding Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching. Chang, C., +, TC Dec. 2015 3404-3416 Reducing Code Length of Second-Order Spectral-Null Code. Yang, C.-N., +, TC Feb. 2015 492-503 Unequal Error Protection of Memories in LDPC Decoders. Condo, C., +, TC Oct. 2015 2981-2993 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Delay lines Adaptive Voltage Scaling with In-Situ Detectors in Commercial FPGAs. Nunez-Yanez, J.L., TC Jan. 2015 45-53 Delay tolerant networks Exploiting Small World Properties for Message Forwarding in Delay Tolerant Networks. Wei, K., +, TC Oct. 2015 2809-2818 Delays Joint Optimal Data Rate and Power Allocation in Lossy Mobile Ad Hoc Networks with Delay-Constrained Traffics. Guo, S., +, TC March 2015 747-762 Multi-User Computation Partitioning for Latency Sensitive Mobile Cloud Applications. Yang, L., +, TC Aug. 2015 2253-2266 On Data Center Network Architectures for Interconnecting Dual-Port Servers. Li, D., +, TC Nov. 2015 3210-3222 Design for testability Testing Open Defects in Memristor-Based Memories. Hamdioui, S., +, TC Jan. 2015 247-259 Digital arithmetic A Low-Cost Mechanism Exploiting Narrow-Width Values for Tolerating Hard Faults in ALU. Hong, S., +, TC Sept. 2015 2433-2446 Comment on “High Speed Parallel Decimal Multiplication With Redundant Internal Encodings”. Gorgin, S., +, TC Jan. 2015 293-294 Radix-2 Division Algorithms with an Over-Redundant Digit Set. Ebergen, J., +, TC Sept. 2015 2652-2663 Simulation of Quantum Circuits via Stabilizer Frames. Garcia, H.J., +, TC Aug. 2015 2323-2336 Unified Mitchell-Based Approximation for Efficient Logarithmic Conversion Circuit. Low, J.Y.L., +, TC June 2015 1783-1797 Digital circuits A Low-Cost Mechanism Exploiting Narrow-Width Values for Tolerating Hard Faults in ALU. Hong, S., +, TC Sept. 2015 2433-2446 Digital communication A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees. Zhang, B., +, TC June 2015 1548-1563 Digital signal processing Bit-Width Optimization by Divide-and-Conquer for Fixed-Point Digital Signal Processing Systems. Chung, J., +, TC Nov. 2015 3091-3101 Digital signatures Cost-Effective Authentic and Anonymous Data Sharing with Forward Security. Huang, X., +, TC April 2015 971-983 Lattice-Based Signatures: Optimization and Implementation on Reconfigurable Hardware. Guneysu, T., +, TC July 2015 1954-1967 Signature-Based Protection from Code Reuse Attacks. Kayaalp, M., +, TC Feb. 2015 533-546 Digital storage Boosting Degraded Reads in Heterogeneous Erasure-Coded Storage Systems. Zhu, Y., +, TC Aug. 2015 2145-2157 Parallel Decodable Two-Level Unequal Burst Error Correcting Codes. Namba, K., +, TC Oct. 2015 2902-2911 Directed graphs Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 Scheduling Precedence Constrained Stochastic Tasks on Heterogeneous Cluster Systems. Li, K., +, TC Jan. 2015 191-204 Virtual Resource Allocation Based on Link Interference in Cayley Wireless Data Centers. Luo, J., +, TC Oct. 2015 3016-3021 Discrete cosine transforms VLSI Computational Architectures for the Arithmetic Cosine Transform. Rajapaksha, N., +, TC Sept. 2015 2708-2715 Distributed algorithms A Self-Adaptive Strategy for Evolution of Cooperation in Distributed Networks. Ye, D., +, TC April 2015 899-911 Physarum Optimization: A Biology-Inspired Algorithm for the Steiner Tree Problem in Networks. Liu, L., +, TC March 2015 818-831 The Telephone Coordination Game Revisited: From Random to Deterministic Algorithms. Chen, L., +, TC Oct. 2015 2968-2980 Distributed databases Secure Distributed Deduplication Systems with Improved Reliability. Li, J., +, TC Dec. 2015 3569-3579 Distributed processing Analysis of Server Provisioning for Distributed Interactive Applications. Zheng, H., +, TC Oct. 2015 2752-2766 + Check author entry for coauthors 16 Enabling Concurrent Failure Recovery for Regenerating-Coding-Based Storage Systems: From Theory to Practice. Li, R., +, TC July 2015 1898-1911 Local-Deadline Assignment for Distributed Real-Time Systems. Hong, S., +, TC July 2015 1983-1997 Proximity-Aware Local-Recoding Anonymization with MapReduce for Scalable Big Data Privacy Preservation in Cloud. Zhang, X., +, TC Aug. 2015 2293-2307 SCPS: A Social-Aware Distributed Cyber-Physical Human-Centric Search Engine. Shen, H., +, TC Feb. 2015 518-532 Utility Functions and Resource Management in an Oversubscribed Heterogeneous Computing Environment. Khemka, B., +, TC Aug. 2015 2394-2407 Diversity reception Channel-Hopping Scheme and Channel-Diverse Routing in Static MultiRadio Multi-Hop Wireless Networks. Lin, T.-Y., +, TC Jan. 2015 71-86 DRAM chips Design of Hybrid Second-Level Caches. Valero, A., +, TC July 2015 18841897 Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 Low Delay Single Symbol Error Correction Codes Based on Reed Solomon Codes. Pontarelli, S., +, TC May 2015 1497-1501 Methodology for Cycle-Accurate DRAM Performance Analysis. Ikodinovic, I., TC July 2015 2084-2091 Synergy of Dynamic Frequency Scaling and Demotion on DRAM Power Management: Models and Optimizations. Lu, Y., +, TC Aug. 2015 23672381 ViPZonE: Hardware Power Variability-Aware Virtual Memory Management for Energy Savings. Gottscho, M., +, TC May 2015 1483-1496 Drives WEC: Improving Durability of SSD Cache Drives by Caching Write-Efficient Data. Chai, Y., +, TC Nov. 2015 3304-3316 Dynamic programming Power Budgeting Techniques for Data Centers. Zhan, X., +, TC Aug. 2015 2267-2278 Dynamic range RNS Scalers for Extended 4-Moduli Sets. Sousa, L., TC Dec. 2015 33223334 Dynamic scheduling ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds. Zhu, X., +, TC Dec. 2015 3389-3403 E Economics A Rewarding Framework for Network Resource Sharing in Co-Channel Hybrid Access Femtocell Networks. Shih, Y., +, TC Nov. 2015 3079-3090 Electroencephalography Fast and Scalable Multi-Way Analysis of Massive Neural Data. Chen, D., +, TC March 2015 707-719 Electronic commerce STAR: Strategy-Proof Double Auctions for Multi-Cloud, Multi-Tenant Bandwidth Reservation. Zheng, Z., +, TC July 2015 2071-2083 Electronic data interchange Boosting Degraded Reads in Heterogeneous Erasure-Coded Storage Systems. Zhu, Y., +, TC Aug. 2015 2145-2157 Ultra-Scalable CPU-MIC Acceleration of Mesoscale Atmospheric Modeling on Tianhe-2. Xue, W., +, TC Aug. 2015 2382-2393 Electronic design automation Automated Design Architecture for 1-D Cellular Automata Using Quantum Cellular Automata. Mardiris, V.A., +, TC Sept. 2015 2476-2489 Electronic mail WEC: Improving Durability of SSD Cache Drives by Caching Write-Efficient Data. Chai, Y., +, TC Nov. 2015 3304-3316 Electronic messaging Exploiting Small World Properties for Message Forwarding in Delay Tolerant Networks. Wei, K., +, TC Oct. 2015 2809-2818 Electrostatic discharges TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage. Zheng, W., +, TC Nov. 2015 3278-3292 17 Embedded systems A Deadline-Floor Inheritance Protocol for EDF Scheduled Embedded RealTime Systems with Resource Sharing. Burns, A., +, TC May 2015 12411253 A Hardware Scheduler Based on Task Queues for FPGA-Based Embedded Real-Time Systems. Tang, Y., +, TC May 2015 1254-1267 A Low Complexity Scaling Method for the Lanczos Kernel in Fixed-Point Arithmetic. Jerez, J. L., +, TC Feb. 2015 303-315 Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Architecture Support for Tightly-Coupled Multi-Core Clusters with SharedMemory HW Accelerators. Dehyadegari, M., +, TC Aug. 2015 2132-2144 Block-Based Multi-Version B -Tree for Flash-Based Embedded Database Systems. Wang, J., +, TC April 2015 925-940 Energy-Efficient Real-Time Human Mobility State Classification Using Smartphones. Oshin, T.O., +, TC June 2015 1680-1693 High-Performance and Lightweight Transaction Support in Flash-Based SSDs. Lu, Y., +, TC Oct. 2015 2819-2832 IIPS: Infrastructure IP for Secure SoC Design. Wang, X., +, TC Aug. 2015 2226-2238 Stackless Multi-Threading for Embedded Systems. McCartney, W.P., +, TC Oct. 2015 2940-2952 The Quadratic Utilization Upper Bound for Arbitrary Deadline Real-Time Tasks. Bini, E., TC Feb. 2015 593-599 Emergency management An Adaptive Multilevel Indexing Method for Disaster Service Discovery. Wu, Y., +, TC Sept. 2015 2447-2459 Encoding Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching. Chang, C., +, TC Dec. 2015 3404-3416 Boosting Degraded Reads in Heterogeneous Erasure-Coded Storage Systems. Zhu, Y., +, TC Aug. 2015 2145-2157 Encryption Efficient Attribute-Based Comparable Data Access Control. Wang, Z., +, TC Dec. 2015 3430-3443 Verifiable Auditing for Outsourced Database in Cloud Computing. Wang, J., +, TC Nov. 2015 3293-3303 Energy conservation PowerTracer: Tracing Requests in Multi-Tier Services to Reduce Energy Inefficiency. Lu, G., +, TC May 2015 1389-1401 An Energy-Efficient Last-Level Cache Architecture for Process VariationTolerant 3D Microprocessors. Kong, J., +, TC Sept. 2015 2460-2475 Control-Flow Decoupling: An Approach for Timely, Non-Speculative Branching. Sheikh, R., +, TC Aug. 2015 2182-2203 Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand. Xu, D., +, TC March 2015 682-697 Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 EXR: Greening Data Center Network with Software Defined Exclusive Routing. Li, D., +, TC Sept. 2015 2534-2544 Filter Data Cache: An Energy-Efficient Small L0 Data Cache Architecture Driven byMiss Cost Reduction. Lee, J., +, TC July 2015 1927-1939 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Requester-Based Spin Lock: A Scalable and Energy Efficient Locking Scheme on Multicore Systems. Cui, Y., +, TC Jan. 2015 166-179 ViPZonE: Hardware Power Variability-Aware Virtual Memory Management for Energy Savings. Gottscho, M., +, TC May 2015 1483-1496 Energy consumption AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol. Liu, F., +, TC Nov. 2015 3051-3063 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing. Mei, J., +, TC Nov. 2015 3064-3078 Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand. Xu, D., +, TC March 2015 682-697 Filter Data Cache: An Energy-Efficient Small L0 Data Cache Architecture Driven byMiss Cost Reduction. Lee, J., +, TC July 2015 1927-1939 ICCI: In-Cache Coherence Information. Garcia-Guirado, A., +, TC April 2015 995-1014 Online Energy Estimation of Relational Operations in Database Systems. Xu, Z., +, TC Nov. 2015 3223-3236 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Synergy of Dynamic Frequency Scaling and Demotion on DRAM Power Management: Models and Optimizations. Lu, Y., +, TC Aug. 2015 23672381 Energy harvesting Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 Entropy Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace. Yu, S., +, TC Jan. 2015 139-151 Granular Evaluation of Anomalies in Wireless Sensor Networks Using Dynamic Data Partitioning with an Entropy Criteria. Kumarage, H., +, TC Sept. 2015 2573-2585 Environmental monitoring (geophysics) Localization for Wireless Sensor and Actor Networks with Meandering Mobility. Akbas, M.I., +, TC April 2015 1015-1028 Environmental science computing Ultra-Scalable CPU-MIC Acceleration of Mesoscale Atmospheric Modeling on Tianhe-2. Xue, W., +, TC Aug. 2015 2382-2393 Error correction codes Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 Low Delay Single Symbol Error Correction Codes Based on Reed Solomon Codes. Pontarelli, S., +, TC May 2015 1497-1501 Parallel Decodable Two-Level Unequal Burst Error Correcting Codes. Namba, K., +, TC Oct. 2015 2902-2911 Simulation of Quantum Circuits via Stabilizer Frames. Garcia, H.J., +, TC Aug. 2015 2323-2336 Unequal Error Protection of Memories in LDPC Decoders. Condo, C., +, TC Oct. 2015 2981-2993 Unified Mitchell-Based Approximation for Efficient Logarithmic Conversion Circuit. Low, J.Y.L., +, TC June 2015 1783-1797 Estimation theory A Stochastic Model for Estimating the Power Consumption of a Processor. Dargie, W., TC May 2015 1311-1322 Accurate and Efficient Estimation of Logic Circuits Reliability Bounds. Ibrahim, W., +, TC May 2015 1217-1229 Online Energy Estimation of Relational Operations in Database Systems. Xu, Z., +, TC Nov. 2015 3223-3236 Evolutionary computation Evolutionary Computing and Particle Filtering: A Hardware-Based Motion Estimation System. Rodriguez, A., +, TC Nov. 2015 3140-3152 Exponential distribution A Stochastic Model for Estimating the Power Consumption of a Processor. Dargie, W., TC May 2015 1311-1322 Reliability-Aware Speedup Models for Parallel Applications with Coordinated Checkpointing/Restart. Zheng, Z., +, TC May 2015 1402-1415 F Failure analysis A Low-Cost Mechanism Exploiting Narrow-Width Values for Tolerating Hard Faults in ALU. Hong, S., +, TC Sept. 2015 2433-2446 Abort-on-Fail Test Scheduling for Modular SOCs without and with Preemption. Ingelsson, U., +, TC Dec. 2015 3335-3347 Characterization of Cascading Failures in Interdependent Cyber-Physical Systems. Huang, Z., +, TC Aug. 2015 2158-2168 Fast Fourier transforms Exploring the Feasibility of Fully Homomorphic Encryption. Wang, W., +, TC March 2015 698-706 Fault diagnosis Conditional (t,k)-Diagnosis in Graphs by Using the Comparison Diagnosis Model. Chen, C., +, TC June 2015 1622-1632 Fault Analysis-Based Logic Encryption. Rajendran, J., +, TC Feb. 2015 410-424 On the Generation of SIC Pairs in Optimal Time. Voyiatzis, I.K., +, TC Oct. 2015 2891-2901 Revisiting Vulnerability Analysis in Modern Microprocessors. Maniatakos, M., +, TC Sept. 2015 2664-2674 Testing Open Defects in Memristor-Based Memories. Hamdioui, S., +, TC Jan. 2015 247-259 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Two-Dimensional Static Test Compaction for Functional Test Sequences. Pomeranz, I., TC Oct. 2015 3009-3015 Fault tolerance A Low-Cost Mechanism Exploiting Narrow-Width Values for Tolerating Hard Faults in ALU. Hong, S., +, TC Sept. 2015 2433-2446 Cost-Efficient Mapping for Fault-Tolerant Virtual Networks. Jarray, A., +, TC March 2015 668-681 Deploying Wireless Sensor Networks with Fault-Tolerance for Structural Health Monitoring. Bhuiyan, M. Z. A., +, TC Feb. 2015 382-395 Piecewise-Functional Broadside Tests Based on Reachable States. Pomeranz, I., TC Aug. 2015 2415-2420 RDIS: Tolerating Many Stuck-At Faults in Resistive Memory. Maddah, R., +, TC March 2015 847-861 Fault Tolerance on Large Scale Systems using Adaptive Process Replication. George, C., +, TC Aug. 2015 2213-2225 Mission Reliability, Cost and Time for Cold Standby Computing Systems with Periodic Backup. Levitin, G., +, TC April 2015 1043-1057 Network Variation and Fault Tolerant Performance Acceleration in Mobile Devices with Simultaneous Remote Execution. Kim, K., +, TC Oct. 2015 2862-2874 Reconfiguring Three-Dimensional Processor Arrays for Fault-Tolerance: Hardness and Heuristic Algorithms. Jiang, G., +, TC Oct. 2015 2926-2939 Resilient and Power-Efficient Multi-Function Channel Buffers in Networkon-Chip Architectures. DiTomaso, D., +, TC Dec. 2015 3555-3568 RRAM Defect Modeling and Failure Analysis Based on March Test and a Novel Squeeze-Search Scheme. Chen, C., +, TC Jan. 2015 180-190 Selecting an Optimal Fault Tolerance Strategy for Reliable Service-Oriented Systems with Local and Global Constraints. Zheng, Z., +, TC Jan. 2015 219-232 Simulation of Quantum Circuits via Stabilizer Frames. Garcia, H.J., +, TC Aug. 2015 2323-2336 The -Diagnosability of Star Graph Networks. Zhou, S., +, TC Feb. 2015 547-555 Fault trees Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 Femtocell networks A Rewarding Framework for Network Resource Sharing in Co-Channel Hybrid Access Femtocell Networks. Shih, Y., +, TC Nov. 2015 3079-3090 Field programmable gate arrays STES: A Stream Cipher Based Low Cost Scheme for Securing Stored Data. Chakraborty, D., +, TC Sept. 2015 2691-2707 A Hardware Scheduler Based on Task Queues for FPGA-Based Embedded Real-Time Systems. Tang, Y., +, TC May 2015 1254-1267 A Low Complexity Scaling Method for the Lanczos Kernel in Fixed-Point Arithmetic. Jerez, J. L., +, TC Feb. 2015 303-315 A Split MAC Approach for SDR Platforms. Di Francesco, P., +, TC April 2015 912-924 Adaptive Voltage Scaling with In-Situ Detectors in Commercial FPGAs. Nunez-Yanez, J.L., TC Jan. 2015 45-53 Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs. Nechma, T., +, TC April 2015 1090-1103 Pipelined Decision Tree Classification Accelerator Implementation in FPGA (DT-CAIF). Saqib, F., +, TC Jan. 2015 280-285 Towards an Oscillator Based TRNG with a Certified Entropy Rate. Lubicz, D., +, TC April 2015 1191-1200 VLSI Computational Architectures for the Arithmetic Cosine Transform. Rajapaksha, N., +, TC Sept. 2015 2708-2715 File organization STES: A Stream Cipher Based Low Cost Scheme for Securing Stored Data. Chakraborty, D., +, TC Sept. 2015 2691-2707 Combining Efficiency, Fidelity, and Flexibility in Resource Information Services. Shen, H., +, TC Feb. 2015 353-367 Design and Implementation of a Journaling File System for Phase-Change Memory. Lee, E., +, TC May 2015 1349-1360 Efficient Rule Engine for Smart Building Systems. Sun, Y., +, TC June 2015 1658-1669 Fixed point arithmetic A Low Complexity Scaling Method for the Lanczos Kernel in Fixed-Point Arithmetic. Jerez, J. L., +, TC Feb. 2015 303-315 + Check author entry for coauthors 18 Flash memories Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 Block-Based Multi-Version B -Tree for Flash-Based Embedded Database Systems. Wang, J., +, TC April 2015 925-940 High-Performance and Lightweight Transaction Support in Flash-Based SSDs. Lu, Y., +, TC Oct. 2015 2819-2832 On-Demand Block-Level Address Mapping in Large-Scale NAND Flash Storage Systems. Chen, R., +, TC June 2015 1729-1741 RB-Explorer: An Accurate and Practical Approach to Write Amplification Measurement for SSDs. Sun, H., +, TC April 2015 1133-1148 Zombie Chasing: Efficient Flash Management Considering Dirty Data in the Buffer Cache. Lee, Y., +, TC Feb. 2015 569-581 Floating point arithmetic Parallel Reproducible Summation. Demmel, J., +, TC July 2015 2060-2070 Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs. Nechma, T., +, TC April 2015 1090-1103 VLSI Computational Architectures for the Arithmetic Cosine Transform. Rajapaksha, N., +, TC Sept. 2015 2708-2715 Formal specification Software Implementation of an Attribute-Based Encryption Scheme. Zavattoni, E., +, TC May 2015 1429-1441 Formal verification Compositional Model Checking of Concurrent Systems. Zheng, H., +, TC June 2015 1607-1621 Fourier transforms Simulation of Quantum Circuits via Stabilizer Frames. Garcia, H.J., +, TC Aug. 2015 2323-2336 Fuzzy control Coordinated Power and Performance Guarantee with Fuzzy MIMO Control in Virtualized Server Clusters. Lama, P., +, TC Jan. 2015 97-111 Fuzzy reasoning QoS-Based Composition of Service Specific Overlay Networks. Al Ridhawi, Y., +, TC March 2015 832-846 Fuzzy set theory By-Passing Infected Areas in Wireless Sensor Networks Using BPR. Yaakob, N., +, TC June 2015 1594-1606 G Game theory A Self-Adaptive Strategy for Evolution of Cooperation in Distributed Networks. Ye, D., +, TC April 2015 899-911 The Telephone Coordination Game Revisited: From Random to Deterministic Algorithms. Chen, L., +, TC Oct. 2015 2968-2980 A Rewarding Framework for Network Resource Sharing in Co-Channel Hybrid Access Femtocell Networks. Shih, Y., +, TC Nov. 2015 3079-3090 Gaussian distribution Multi-Granularity Locality-Sensitive Bloom Filter. Qian, J., +, TC Dec. 2015 3500-3514 Generators Efficient Attribute-Based Comparable Data Access Control. Wang, Z., +, TC Dec. 2015 3430-3443 Genetic algorithms CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm. Qiu, M., +, TC Dec. 2015 3528-3540 Genetics Evolutionary Computing and Particle Filtering: A Hardware-Based Motion Estimation System. Rodriguez, A., +, TC Nov. 2015 3140-3152 Global Positioning System NextCell: Predicting Location Using Social Interplay from Cell Phone Traces. Zhang, D., +, TC Feb. 2015 452-463 Global warming Ultra-Scalable CPU-MIC Acceleration of Mesoscale Atmospheric Modeling on Tianhe-2. Xue, W., +, TC Aug. 2015 2382-2393 Graph coloring Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 19 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Graph theory Conditional (t,k)-Diagnosis in Graphs by Using the Comparison Diagnosis Model. Chen, C., +, TC June 2015 1622-1632 Finding Multi-Constrained Multiple Shortest Paths. Feng, G., +, TC Sept. 2015 2559-2572 Safe Data Parallelism for General Streaming. Schneider, S., +, TC Feb. 2015 504-517 Symmetric Property and Reliability of Balanced Hypercube. Zhou, J.-X., +, TC March 2015 876-881 -Diagnosability of Star Graph Networks. Zhou, S., +, TC Feb. 2015 The 547-555 Graphics processing units A Cache Hierarchy Aware Thread Mapping Methodology for GPGPUs. Lai, B. C., +, TC April 2015 884-898 Data Partitioning on Multicore and Multi-GPU Platforms Using Functional Performance Models. Zhong, Z., +, TC Sept. 2015 2506-2518 Fast and Scalable Multi-Way Analysis of Massive Neural Data. Chen, D., +, TC March 2015 707-719 GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation. Yu, Z., +, TC Nov. 2015 3153-3166 GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs. Lee, J., +, TC Nov. 2015 3167-3180 Hyper-Real-Time Ice Simulation and Modeling Using GPGPU. Alawneh, S., +, TC Dec. 2015 3475-3487 Performance Optimization Using Partitioned SpMV on GPUs and Multicore CPUs. Yang, W., +, TC Sept. 2015 2623-2636 Ultra-Scalable CPU-MIC Acceleration of Mesoscale Atmospheric Modeling on Tianhe-2. Xue, W., +, TC Aug. 2015 2382-2393 Greedy algorithms Analysis of Server Provisioning for Distributed Interactive Applications. Zheng, H., +, TC Oct. 2015 2752-2766 Efficient Double Bases for Scalar Multiplication. Meloni, N., +, TC Aug. 2015 2204-2212 Efficient Victim Block Selection for Flash Storage Devices. Tsao, C., +, TC Dec. 2015 3444-3460 Green computing EXR: Greening Data Center Network with Software Defined Exclusive Routing. Li, D., +, TC Sept. 2015 2534-2544 Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm. Qiu, M., +, TC Dec. 2015 3528-3540 Groupware Collaborative Location-Based Sleep Scheduling for Wireless Sensor Networks Integratedwith Mobile Cloud Computing. Zhu, C., +, TC July 2015 1844-1856 On Synthesizing a Consistent Operational Transformation Approach. Randolph, A., +, TC April 2015 1074-1089 H Hardware Block-Precise Processors: Low-Power Processors with Reduced Operand Store Accesses and Result Broadcasts. Lakshminarayana, N.B., +, TC Nov. 2015 3102-3114 Fast Two-Level Address Translation for Virtualized Systems. Ahn, J., +, TC Dec. 2015 3461-3474 GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs. Lee, J., +, TC Nov. 2015 3167-3180 Hardware-software codesign Hardware–Software Coherence Protocol for the Coexistence of Caches and Local Memories. Alvarez, L., +, TC Jan. 2015 152-165 Heuristic algorithms ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds. Zhu, X., +, TC Dec. 2015 3389-3403 Energy Minimization in Multi-Task Software-Defined Sensor Networks. Zeng, D., +, TC Nov. 2015 3128-3139 Opportunistic Offloading of Deadline-Constrained Bulk Cellular Traffic in Vehicular DTNs. Yao, H., +, TC Dec. 2015 3515-3527 Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors. Zhang, Z., +, TC Nov. 2015 3249-3264 Hidden Markov models Evolutionary Computing and Particle Filtering: A Hardware-Based Motion Estimation System. Rodriguez, A., +, TC Nov. 2015 3140-3152 + Check author entry for coauthors High definition video A Generalization of Addition Chains and Fast Inversions in Binary Fields. Jarvinen, K., +, TC Sept. 2015 2421-2432 Design of Optimal Scan Tree Based on Compact Test Patterns for Test Time Reduction. Chen, L., +, TC Dec. 2015 3417-3429 High level synthesis Architecture Support for Tightly-Coupled Multi-Core Clusters with SharedMemory HW Accelerators. Dehyadegari, M., +, TC Aug. 2015 2132-2144 High-speed networks Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching. Chang, C., +, TC Dec. 2015 3404-3416 Hypercube networks Symmetric Property and Reliability of Balanced Hypercube. Zhou, J.-X., +, TC March 2015 876-881 Hypercubes On Data Center Network Architectures for Interconnecting Dual-Port Servers. Li, D., +, TC Nov. 2015 3210-3222 I Ice Hyper-Real-Time Ice Simulation and Modeling Using GPGPU. Alawneh, S., +, TC Dec. 2015 3475-3487 TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage. Zheng, W., +, TC Nov. 2015 3278-3292 IEEE 802.11 Standards AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol. Liu, F., +, TC Nov. 2015 3051-3063 IEEE publishing 2014 Reviewers List*. , TC Jan. 2015 295-302 Image color analysis Design of Optimal Scan Tree Based on Compact Test Patterns for Test Time Reduction. Chen, L., +, TC Dec. 2015 3417-3429 Image processing An Analytical Framework for Evaluating the Error Characteristics of Approximate Adders. Liu, C., +, TC May 2015 1268-1281 Design and Analysis of Approximate Compressors for Multiplication. Momeni, A., +, TC April 2015 984-994 Image registration Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Image segmentation Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Indexes A Generalization of Addition Chains and Fast Inversions in Binary Fields. Jarvinen, K., +, TC Sept. 2015 2421-2432 Adaptive Selection of Cache Indexing Bits for Removing Conflict Misses. Ros, A., +, TC June 2015 1534-1547 An Adaptive Multilevel Indexing Method for Disaster Service Discovery. Wu, Y., +, TC Sept. 2015 2447-2459 Block-Precise Processors: Low-Power Processors with Reduced Operand Store Accesses and Result Broadcasts. Lakshminarayana, N.B., +, TC Nov. 2015 3102-3114 Inductive power transmission Collaborative Mobile Charging. Zhang, S., +, TC March 2015 654-667 Industrial property IIPS: Infrastructure IP for Secure SoC Design. Wang, X., +, TC Aug. 2015 2226-2238 Inference mechanisms Parallel Decodable Two-Level Unequal Burst Error Correcting Codes. Namba, K., +, TC Oct. 2015 2902-2911 Informatics Multi-Granularity Locality-Sensitive Bloom Filter. Qian, J., +, TC Dec. 2015 3500-3514 Information resources Combining Efficiency, Fidelity, and Flexibility in Resource Information Services. Shen, H., +, TC Feb. 2015 353-367 Information retrieval SCPS: A Social-Aware Distributed Cyber-Physical Human-Centric Search Engine. Shen, H., +, TC Feb. 2015 518-532 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Information systems CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Input-output programs Accelerate RDP RAID-6 Scaling by Reducing Disk I/Os and XOR Operations. Zhang, G., +, TC Jan. 2015 32-44 Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers. Wu, S., +, TC Sept. 2015 2637-2651 Instruction sets Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation. Yu, Z., +, TC Nov. 2015 3153-3166 Integer programming Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 Survivable Cloud Network Mapping for Disaster Recovery Support. Gu, F., +, TC Aug. 2015 2353-2366 Integrated circuit design A Cache Hierarchy Aware Thread Mapping Methodology for GPGPUs. Lai, B. C., +, TC April 2015 884-898 Design of Hybrid Second-Level Caches. Valero, A., +, TC July 2015 18841897 Fault Analysis-Based Logic Encryption. Rajendran, J., +, TC Feb. 2015 410-424 IIPS: Infrastructure IP for Secure SoC Design. Wang, X., +, TC Aug. 2015 2226-2238 Leaving One Slot Empty: Flit Bubble Flow Control for Torus Cache-Coherent NoCs. Ma, S., +, TC March 2015 763-777 Optimal Checkpoint Selection with Dual-Modular Redundancy Hardening. Kang, S., +, TC July 2015 2036-2048 Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 Revisiting Vulnerability Analysis in Modern Microprocessors. Maniatakos, M., +, TC Sept. 2015 2664-2674 Integrated circuit layout Interleaving in Systolic-Arrays: A Throughput Breakthrough. Causapruno, G., +, TC July 2015 1940-1953 Integrated circuit modeling Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 Simulation and Implication Using a Transfer Function Model for Switching Logic. Thornton, M.A., TC Dec. 2015 3580-3590 Testing Open Defects in Memristor-Based Memories. Hamdioui, S., +, TC Jan. 2015 247-259 Integrated circuit reliability Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 Optimal Checkpoint Selection with Dual-Modular Redundancy Hardening. Kang, S., +, TC July 2015 2036-2048 RDIS: Tolerating Many Stuck-At Faults in Resistive Memory. Maddah, R., +, TC March 2015 847-861 Integrated circuit testing Fault Analysis-Based Logic Encryption. Rajendran, J., +, TC Feb. 2015 410-424 IIPS: Infrastructure IP for Secure SoC Design. Wang, X., +, TC Aug. 2015 2226-2238 Piecewise-Functional Broadside Tests Based on Reachable States. Pomeranz, I., TC Aug. 2015 2415-2420 Testing Open Defects in Memristor-Based Memories. Hamdioui, S., +, TC Jan. 2015 247-259 Integrated circuits Abort-on-Fail Test Scheduling for Modular SOCs without and with Preemption. Ingelsson, U., +, TC Dec. 2015 3335-3347 Intelligent vehicles Opportunistic Offloading of Deadline-Constrained Bulk Cellular Traffic in Vehicular DTNs. Yao, H., +, TC Dec. 2015 3515-3527 Interference suppression A Rewarding Framework for Network Resource Sharing in Co-Channel Hybrid Access Femtocell Networks. Shih, Y., +, TC Nov. 2015 3079-3090 An Efficient I/O-Redirection-Based Reconstruction Scheme for Erasure-Coded Storage Clusters. Huang, J., +, TC Nov. 2015 3037-3050 + Check author entry for coauthors 20 Coexistence Wi-Fi MAC Design for Mitigating Interference Caused by Collocated Bluetooth. Hsu, A. C.-C., +, TC Feb. 2015 342-352 Virtual Resource Allocation Based on Link Interference in Cayley Wireless Data Centers. Luo, J., +, TC Oct. 2015 3016-3021 Internet Analysis of Server Provisioning for Distributed Interactive Applications. Zheng, H., +, TC Oct. 2015 2752-2766 Coordinated Power and Performance Guarantee with Fuzzy MIMO Control in Virtualized Server Clusters. Lama, P., +, TC Jan. 2015 97-111 Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand. Xu, D., +, TC March 2015 682-697 Packet Classification Using Dynamically Generated Decision Trees. Cheng, Y.-C., +, TC Feb. 2015 582-586 Scheme to Measure Packet Processing Time of a Remote Host through Estimation of End-Link Capacity. Salehin, K. M., +, TC Jan. 2015 205-218 Invasive software Fault Analysis-Based Logic Encryption. Rajendran, J., +, TC Feb. 2015 410-424 Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace. Yu, S., +, TC Jan. 2015 139-151 H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor. Jin, S., +, TC Oct. 2015 2833-2846 Inventory management Completely Pinpointing the Missing RFID Tags in a Time-Efficient Way. Liu, X., +, TC Jan. 2015 87-96 Iterative methods A Low Complexity Scaling Method for the Lanczos Kernel in Fixed-Point Arithmetic. Jerez, J. L., +, TC Feb. 2015 303-315 A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees. Zhang, B., +, TC June 2015 1548-1563 Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs. Nechma, T., +, TC April 2015 1090-1103 Reviewing High-Radix Signed-Digit Adders. Kornerup, P., TC May 2015 1502-1505 Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 J Java Automated Model-Based Testing of Role-Based Access Control Using Predicate/Transition Nets. Xu, D., +, TC Sept. 2015 2490-2505 Job shop scheduling Abort-on-Fail Test Scheduling for Modular SOCs without and with Preemption. Ingelsson, U., +, TC Dec. 2015 3335-3347 Just-in-time JEM: Just in Time/Just Enough Energy Management Methodology for Computing Systems. Jawad, M., +, TC June 2015 1798-1804 K Kernel GPGPU-MiniBench: Accelerating GPGPU Micro-Architecture Simulation. Yu, Z., +, TC Nov. 2015 3153-3166 GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs. Lee, J., +, TC Nov. 2015 3167-3180 Knowledge based systems Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers. Wu, S., +, TC Sept. 2015 2637-2651 L Large-scale systems A Quantitative Characterization of Cross Coverage. Zhou, J., +, TC Aug. 2015 2408-2414 Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers. Wu, S., +, TC Sept. 2015 2637-2651 Learning (artificial intelligence) Detection of Denial-of-Service Attacks Based on Computer Vision Techniques. Tan, Z., +, TC Sept. 2015 2519-2533 21 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Least mean squares methods Time Series Characterization of Gaming Workload for Runtime Power Management. Dietrich, B., +, TC Jan. 2015 260-273 Linear algebra A Low Complexity Scaling Method for the Lanczos Kernel in Fixed-Point Arithmetic. Jerez, J. L., +, TC Feb. 2015 303-315 Simulation of Quantum Circuits via Stabilizer Frames. Garcia, H.J., +, TC Aug. 2015 2323-2336 Linear programming Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 Survivable Cloud Network Mapping for Disaster Recovery Support. Gu, F., +, TC Aug. 2015 2353-2366 Linearization techniques Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 Linux iBuddy: Inverse Buddy for Enhancing Memory Allocation/Deallocation Performanceon Multi-Core Systems. Park, H., +, TC March 2015 720-732 Requester-Based Spin Lock: A Scalable and Energy Efficient Locking Scheme on Multicore Systems. Cui, Y., +, TC Jan. 2015 166-179 ViPZonE: Hardware Power Variability-Aware Virtual Memory Management for Energy Savings. Gottscho, M., +, TC May 2015 1483-1496 Load modeling Hyper-Real-Time Ice Simulation and Modeling Using GPGPU. Alawneh, S., +, TC Dec. 2015 3475-3487 Local area networks Sliding Mode Congestion Control for Data Center Ethernet Networks. Jiang, W., +, TC Sept. 2015 2675-2690 Logic circuits A Low-Cost Mechanism Exploiting Narrow-Width Values for Tolerating Hard Faults in ALU. Hong, S., +, TC Sept. 2015 2433-2446 A Post-Synthesis Optimization Technique for Reversible Circuits Exploiting Negative Control Lines. Datta, K., +, TC April 2015 1208-1214 Accurate and Efficient Estimation of Logic Circuits Reliability Bounds. Ibrahim, W., +, TC May 2015 1217-1229 Logic design Interleaving in Systolic-Arrays: A Throughput Breakthrough. Causapruno, G., +, TC July 2015 1940-1953 Optimal Checkpoint Selection with Dual-Modular Redundancy Hardening. Kang, S., +, TC July 2015 2036-2048 Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs. Nechma, T., +, TC April 2015 1090-1103 Pipelined Decision Tree Classification Accelerator Implementation in FPGA (DT-CAIF). Saqib, F., +, TC Jan. 2015 280-285 Logic gates Fault Analysis-Based Logic Encryption. Rajendran, J., +, TC Feb. 2015 410-424 Resilient and Power-Efficient Multi-Function Channel Buffers in Networkon-Chip Architectures. DiTomaso, D., +, TC Dec. 2015 3555-3568 Logic synthesis Using Flexibility in P-Circuits by Boolean Relations. Bernasconi, A., +, TC Dec. 2015 3605-3618 Low-power electronics Automated Design Architecture for 1-D Cellular Automata Using Quantum Cellular Automata. Mardiris, V.A., +, TC Sept. 2015 2476-2489 M Mainframes Ultra-Scalable CPU-MIC Acceleration of Mesoscale Atmospheric Modeling on Tianhe-2. Xue, W., +, TC Aug. 2015 2382-2393 Maintenance engineering Predicting Transient Downtime in Virtual Server Systems: An Efficient Sample Path Randomization Approach. Du, A.Y., +, TC Dec. 2015 3541-3554 Manufacturing processes Abort-on-Fail Test Scheduling for Modular SOCs without and with Preemption. Ingelsson, U., +, TC Dec. 2015 3335-3347 Marine vehicles Hyper-Real-Time Ice Simulation and Modeling Using GPGPU. Alawneh, S., +, TC Dec. 2015 3475-3487 + Check author entry for coauthors Markov chains Predicting Transient Downtime in Virtual Server Systems: An Efficient Sample Path Randomization Approach. Du, A.Y., +, TC Dec. 2015 3541-3554 Markov processes An Efficient I/O-Redirection-Based Reconstruction Scheme for Erasure-Coded Storage Clusters. Huang, J., +, TC Nov. 2015 3037-3050 Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace. Yu, S., +, TC Jan. 2015 139-151 Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 Mathematical model Bit-Width Optimization by Divide-and-Conquer for Fixed-Point Digital Signal Processing Systems. Chung, J., +, TC Nov. 2015 3091-3101 Evolutionary Computing and Particle Filtering: A Hardware-Based Motion Estimation System. Rodriguez, A., +, TC Nov. 2015 3140-3152 Simulation and Implication Using a Transfer Function Model for Switching Logic. Thornton, M.A., TC Dec. 2015 3580-3590 Mathematical operators Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Mathematics computing Automatic High-Level Data-Flow Synthesis and Optimization of Polynomial Datapaths Using Functional Decomposition. Ghandali, S., +, TC June 2015 1579-1593 Multiplicative Division Employing Independent Factors. Matula, D.W., +, TC July 2015 2012-2019 Matrix algebra Non-Binary Orthogonal Latin Square Codes for a Multilevel Phase Charge Memory (PCM). Namba, K., +, TC July 2015 2092-2097 On Compact Cauchy Matrices for Substitution-Permutation Networks. Cui, T., +, TC July 2015 2098-2102 Matrix decomposition Shifted Polynomial Basis Multipliers Based on Subquadratic Toeplitz Matrix-Vector Product Approach for All Irreducible Pentanomials. Han, J., +, TC March 2015 862-867 Matrix multiplication Accelerating Fully Homomorphic Encryption in Hardware. Doroz, Y., +, TC June 2015 1509-1521 Comment on “High Speed Parallel Decimal Multiplication With Redundant Internal Encodings”. Gorgin, S., +, TC Jan. 2015 293-294 Data Partitioning on Multicore and Multi-GPU Platforms Using Functional Performance Models. Zhong, Z., +, TC Sept. 2015 2506-2518 Performance Optimization Using Partitioned SpMV on GPUs and Multicore CPUs. Yang, W., +, TC Sept. 2015 2623-2636 Measurement Multiprocessor Capacity Metric and Analysis. Otoom, M., +, TC Nov. 2015 3181-3196 Media streaming STAR: Strategy-Proof Double Auctions for Multi-Cloud, Multi-Tenant Bandwidth Reservation. Zheng, Z., +, TC July 2015 2071-2083 Medical image processing Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Medical services Efficient Attribute-Based Comparable Data Access Control. Wang, Z., +, TC Dec. 2015 3430-3443 Medical signal processing Fast and Scalable Multi-Way Analysis of Massive Neural Data. Chen, D., +, TC March 2015 707-719 Memory architecture An Energy-Efficient Last-Level Cache Architecture for Process VariationTolerant 3D Microprocessors. Kong, J., +, TC Sept. 2015 2460-2475 Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 High-Performance and Lightweight Transaction Support in Flash-Based SSDs. Lu, Y., +, TC Oct. 2015 2819-2832 PC-TRIO: A Power Efficient TCAM Architecture for Packet Classifiers. Banerjee, T., +, TC April 2015 1104-1118 Memory management Fast Two-Level Address Translation for Virtualized Systems. Ahn, J., +, TC Dec. 2015 3461-3474 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs. Lee, J., +, TC Nov. 2015 3167-3180 Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm. Qiu, M., +, TC Dec. 2015 3528-3540 Memristor circuits Testing Open Defects in Memristor-Based Memories. Hamdioui, S., +, TC Jan. 2015 247-259 Memristors Improving Tolerance to Variations in Memristor-Based Applications Using Parallel Memristors. Rajendran, J., +, TC March 2015 733-746 Mesh generation A Unified Framework for Line-Like Skeleton Extraction in 2D/3D Sensor Networks. Liu, W., +, TC May 2015 1323-1335 Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 Message authentication A Novel En-Route Filtering Scheme Against False Data Injection Attacks in Cyber-Physical Networked Systems. Yang, X., +, TC Jan. 2015 4-18 Comment on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”. Li, C., +, TC March 2015 882-883 Message passing Community-Based Event Dissemination with Optimal Load Balancing. Xia, F., +, TC July 2015 1857-1869 Efficient Notification Ordering for Geo-Distributed Pub/Sub Systems. Baldoni, R., +, TC Oct. 2015 2796-2808 Fault Tolerance on Large Scale Systems using Adaptive Process Replication. George, C., +, TC Aug. 2015 2213-2225 Pubsub: An Efficient Publish/Subscribe System. Banerjee-Mishra, T., +, TC April 2015 1119-1132 SpiNNaker—Programming Model. Brown, A.D., +, TC June 2015 17691782 Meta data Similarity and Locality Based Indexing for High Performance Data Deduplication. Xia, W., +, TC April 2015 1162-1176 Microcontrollers Stackless Multi-Threading for Embedded Systems. McCartney, W.P., +, TC Oct. 2015 2940-2952 Microprocessor chips An Energy-Efficient Last-Level Cache Architecture for Process VariationTolerant 3D Microprocessors. Kong, J., +, TC Sept. 2015 2460-2475 Control-Flow Decoupling: An Approach for Timely, Non-Speculative Branching. Sheikh, R., +, TC Aug. 2015 2182-2203 Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 Revisiting Vulnerability Analysis in Modern Microprocessors. Maniatakos, M., +, TC Sept. 2015 2664-2674 Size-Aware Cache Management for Compressed Cache Architectures. Baek, S., +, TC Aug. 2015 2337-2352 Microprocessors 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching. Manoj P. D., S., +, TC Nov. 2015 3022-3036 DCCS: Double Circular Caching Scheme for DRAM/PRAM Hybrid Cache. Hsieh, J., +, TC Nov. 2015 3115-3127 Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm. Qiu, M., +, TC Dec. 2015 3528-3540 Middleware Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Community-Based Event Dissemination with Optimal Load Balancing. Xia, F., +, TC July 2015 1857-1869 Efficient Notification Ordering for Geo-Distributed Pub/Sub Systems. Baldoni, R., +, TC Oct. 2015 2796-2808 Service Composition in Opportunistic Networks: A Load and Mobility Aware Solution. Sadiq, U., +, TC Aug. 2015 2308-2322 MIMO communication Coordinated Power and Performance Guarantee with Fuzzy MIMO Control in Virtualized Server Clusters. Lama, P., +, TC Jan. 2015 97-111 Dynamic Antenna Management for Uplink Energy Efficiency on 802.11n Mobile Devices. Cheng, S., +, TC Oct. 2015 2767-2780 + Check author entry for coauthors 22 Minimax techniques Approximation Algorithms for Min-Max Cycle Cover Problems. Xu, W., +, TC March 2015 600-613 Minimization Dynamic Antenna Management for Uplink Energy Efficiency on 802.11n Mobile Devices. Cheng, S., +, TC Oct. 2015 2767-2780 On the Interplay between Global DVFS and Scheduling Tasks with Precedence Constraints. Gerards, M.E., +, TC June 2015 1742-1754 Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors. Zhang, Z., +, TC Nov. 2015 3249-3264 Mobile ad hoc networks Joint Optimal Data Rate and Power Allocation in Lossy Mobile Ad Hoc Networks with Delay-Constrained Traffics. Guo, S., +, TC March 2015 747-762 Maximizing P2P File Access Availability in Mobile Ad Hoc Networks though Replication for Efficient File Sharing. Chen, K., +, TC April 2015 1029-1042 Service Composition in Opportunistic Networks: A Load and Mobility Aware Solution. Sadiq, U., +, TC Aug. 2015 2308-2322 Mobile communication AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol. Liu, F., +, TC Nov. 2015 3051-3063 Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 Opportunistic Offloading of Deadline-Constrained Bulk Cellular Traffic in Vehicular DTNs. Yao, H., +, TC Dec. 2015 3515-3527 Mobile computing A Lightweight Virtualization Solution for Android Devices. Chen, W., +, TC Oct. 2015 2741-2751 Collaborative Location-Based Sleep Scheduling for Wireless Sensor Networks Integratedwith Mobile Cloud Computing. Zhu, C., +, TC July 2015 1844-1856 Energy-Efficient Real-Time Human Mobility State Classification Using Smartphones. Oshin, T.O., +, TC June 2015 1680-1693 Multi-User Computation Partitioning for Latency Sensitive Mobile Cloud Applications. Yang, L., +, TC Aug. 2015 2253-2266 New Regular Radix-8 Scheme for Elliptic Curve Scalar Multiplication without Pre-Computation. Abdulrahman, E. A. H., +, TC Feb. 2015 438-451 NextCell: Predicting Location Using Social Interplay from Cell Phone Traces. Zhang, D., +, TC Feb. 2015 452-463 Opportunistic Offloading of Deadline-Constrained Bulk Cellular Traffic in Vehicular DTNs. Yao, H., +, TC Dec. 2015 3515-3527 Service Composition in Opportunistic Networks: A Load and Mobility Aware Solution. Sadiq, U., +, TC Aug. 2015 2308-2322 Mobile handsets AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol. Liu, F., +, TC Nov. 2015 3051-3063 Efficient Attribute-Based Comparable Data Access Control. Wang, Z., +, TC Dec. 2015 3430-3443 NextCell: Predicting Location Using Social Interplay from Cell Phone Traces. Zhang, D., +, TC Feb. 2015 452-463 Service Composition in Opportunistic Networks: A Load and Mobility Aware Solution. Sadiq, U., +, TC Aug. 2015 2308-2322 Mobile radio Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 Dynamic Antenna Management for Uplink Energy Efficiency on 802.11n Mobile Devices. Cheng, S., +, TC Oct. 2015 2767-2780 Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 QoS-Based Composition of Service Specific Overlay Networks. Al Ridhawi, Y., +, TC March 2015 832-846 Mobile robots Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 Mobility management (mobile radio) An Effective Area-Based Localization Algorithm for Wireless Networks. Lasla, N., +, TC Aug. 2015 2103-2118 Exploiting Small World Properties for Message Forwarding in Delay Tolerant Networks. Wei, K., +, TC Oct. 2015 2809-2818 23 Molecular communication (telecommunication) A Promise of Realizable, Ultra-Scalable Communications at Nano-Scale:A Multi-Modal Nano-Machine Architecture. Liaskos, C., +, TC May 2015 1282-1295 Monte Carlo methods A Quantitative Characterization of Cross Coverage. Zhou, J., +, TC Aug. 2015 2408-2414 Evolutionary Computing and Particle Filtering: A Hardware-Based Motion Estimation System. Rodriguez, A., +, TC Nov. 2015 3140-3152 Multi-robot systems Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 Multi-threading A Cache Hierarchy Aware Thread Mapping Methodology for GPGPUs. Lai, B. C., +, TC April 2015 884-898 Effective Cost Reduction for Elastic Clouds under Spot Instance Pricing Through Adaptive Checkpointing. Jangjaimon, I., +, TC Feb. 2015 396-409 MINIME: Pattern-Aware Multicore Benchmark Synthesizer. Deniz, E., +, TC Aug. 2015 2239-2252 MUCH: Multithreaded Content-Based File Chunking. Won, Y., +, TC May 2015 1375-1388 Stackless Multi-Threading for Embedded Systems. McCartney, W.P., +, TC Oct. 2015 2940-2952 Multicast communication A Hybrid Multicast Routing for Large Scale Sensor Networks with Holes. Won, M., +, TC Dec. 2015 3362-3375 On Nonblocking Multicast Fat-Tree Data Center Networks with Server Redundancy. Guo, Z., +, TC April 2015 1058-1073 Multicast protocols A Hybrid Multicast Routing for Large Scale Sensor Networks with Holes. Won, M., +, TC Dec. 2015 3362-3375 Multimedia communication Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 Multiplexing 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching. Manoj P. D., S., +, TC Nov. 2015 3022-3036 Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network. Huang, H., +, TC Dec. 2015 34883499 Multiplying circuits Comments on “Low-Latency Digit-Serial Systolic Double Basis Multiplier over GF (2 ) Using Subquadratic Toeplitz Matrix-Vector Product Approach”. Reyhani-Masoleh, A., TC April 2015 1215-1216 Design and Analysis of Approximate Compressors for Multiplication. Momeni, A., +, TC April 2015 984-994 New Hardware Implementations of WG (29, 11) and WG- 16 Stream Ciphers Using Polynomial Basis. El-Razouk, H., +, TC July 2015 2020-2035 Multiprocessing programs TSAC: Enforcing Isolation ofVirtual Machines in Clouds. Weng, C., +, TC May 2015 1470-1482 Multiprocessing systems A Stochastic Model for Estimating the Power Consumption of a Processor. Dargie, W., TC May 2015 1311-1322 Adaptive Cache Coherence Mechanisms with Producer–Consumer Sharing Optimization for Chip Multiprocessors. Kayi, A., +, TC Feb. 2015 316-328 Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Conditional (t,k)-Diagnosis in Graphs by Using the Comparison Diagnosis Model. Chen, C., +, TC June 2015 1622-1632 Data Partitioning on Multicore and Multi-GPU Platforms Using Functional Performance Models. Zhong, Z., +, TC Sept. 2015 2506-2518 Hardware–Software Coherence Protocol for the Coexistence of Caches and Local Memories. Alvarez, L., +, TC Jan. 2015 152-165 iBuddy: Inverse Buddy for Enhancing Memory Allocation/Deallocation Performanceon Multi-Core Systems. Park, H., +, TC March 2015 720-732 ICCI: In-Cache Coherence Information. Garcia-Guirado, A., +, TC April 2015 995-1014 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 MINIME: Pattern-Aware Multicore Benchmark Synthesizer. Deniz, E., +, TC Aug. 2015 2239-2252 MUCH: Multithreaded Content-Based File Chunking. Won, Y., +, TC May 2015 1375-1388 New Parallel Approaches for Scalar Multiplication in Elliptic Curve over Fields of Small Characteristic. Negre, C., +, TC Oct. 2015 2875-2890 On the Interplay between Global DVFS and Scheduling Tasks with Precedence Constraints. Gerards, M.E., +, TC June 2015 1742-1754 Performance Optimization Using Partitioned SpMV on GPUs and Multicore CPUs. Yang, W., +, TC Sept. 2015 2623-2636 Performance-Energy Optimizations for Shared Vector Accelerators in Multicores. Beldianu, S. F., +, TC March 2015 805-817 Regional ACO-Based Cascaded Adaptive Routing for Traffic Balancing in Mesh-Based Network-on-Chip Systems. Chang, E., +, TC March 2015 868-875 Requester-Based Spin Lock: A Scalable and Energy Efficient Locking Scheme on Multicore Systems. Cui, Y., +, TC Jan. 2015 166-179 SLA: A Stage-Level Latency Analysisfor Real-Time Communicationin a Pipelined Resource Model. Kashif, H., +, TC April 2015 1177-1190 SpiNNaker—Programming Model. Brown, A.D., +, TC June 2015 17691782 The -Diagnosability of Star Graph Networks. Zhou, S., +, TC Feb. 2015 547-555 Multiprocessor interconnection networks Ant Colony Optimization-Based Adaptive Network-on-Chip Routing Framework Using Network Information Region. Hsin, H., +, TC Aug. 2015 2119-2131 N-Dimensional Twin Torus Topology. Andujar-Munoz, F.J., +, TC Oct. 2015 2847-2861 Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 The -Diagnosability of Star Graph Networks. Zhou, S., +, TC Feb. 2015 547-555 N NAND circuits On-Demand Block-Level Address Mapping in Large-Scale NAND Flash Storage Systems. Chen, R., +, TC June 2015 1729-1741 RB-Explorer: An Accurate and Practical Approach to Write Amplification Measurement for SSDs. Sun, H., +, TC April 2015 1133-1148 Nanoelectronics Automated Design Architecture for 1-D Cellular Automata Using Quantum Cellular Automata. Mardiris, V.A., +, TC Sept. 2015 2476-2489 Nanotechnology A Promise of Realizable, Ultra-Scalable Communications at Nano-Scale:A Multi-Modal Nano-Machine Architecture. Liaskos, C., +, TC May 2015 1282-1295 Network coding An Improved Stochastic Modeling of Opportunistic Routing in Vehicular CPS. Zeng, D., +, TC July 2015 1819-1829 Comment on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”. Li, C., +, TC March 2015 882-883 Comments on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”. Kim, Y., TC Dec. 2015 3619-3620 Network routing Ant Colony Optimization-Based Adaptive Network-on-Chip Routing Framework Using Network Information Region. Hsin, H., +, TC Aug. 2015 2119-2131 Regional ACO-Based Cascaded Adaptive Routing for Traffic Balancing in Mesh-Based Network-on-Chip Systems. Chang, E., +, TC March 2015 868-875 Network servers Analysis of Server Provisioning for Distributed Interactive Applications. Zheng, H., +, TC Oct. 2015 2752-2766 Network theory (graphs) Characterization of Cascading Failures in Interdependent Cyber-Physical Systems. Huang, Z., +, TC Aug. 2015 2158-2168 Efficient Rule Engine for Smart Building Systems. Sun, Y., +, TC June 2015 1658-1669 Physarum Optimization: A Biology-Inspired Algorithm for the Steiner Tree Problem in Networks. Liu, L., +, TC March 2015 818-831 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Network topology A Hybrid Multicast Routing for Large Scale Sensor Networks with Holes. Won, M., +, TC Dec. 2015 3362-3375 On the Network Power Effectiveness of Data Center Architectures. Shang, Y., +, TC Nov. 2015 3237-3248 Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors. Zhang, Z., +, TC Nov. 2015 3249-3264 Network-on-chip Ant Colony Optimization-Based Adaptive Network-on-Chip Routing Framework Using Network Information Region. Hsin, H., +, TC Aug. 2015 2119-2131 Leaving One Slot Empty: Flit Bubble Flow Control for Torus Cache-Coherent NoCs. Ma, S., +, TC March 2015 763-777 Regional ACO-Based Cascaded Adaptive Routing for Traffic Balancing in Mesh-Based Network-on-Chip Systems. Chang, E., +, TC March 2015 868-875 Nonlinear programming Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 Number theory Efficient Double Bases for Scalar Multiplication. Meloni, N., +, TC Aug. 2015 2204-2212 Numerical analysis A Cognitive TCP Design for a Cognitive Radio Network with an UnstableBandwidth Link. Yu-Chun, C., +, TC Oct. 2015 2730-3740 Hyper-Real-Time Ice Simulation and Modeling Using GPGPU. Alawneh, S., +, TC Dec. 2015 3475-3487 Joint Optimal Data Rate and Power Allocation in Lossy Mobile Ad Hoc Networks with Delay-Constrained Traffics. Guo, S., +, TC March 2015 747-762 The Optimal Node Placement for Long Belt Coverage in Wireless Networks. Wang, B., +, TC Feb. 2015 587-592 O Obituaries In Memoriam [Ivan Stojmenovic]. Zomaya, A.Y., TC Jan. 2015 3 Object-oriented programming CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Online front-ends Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace. Yu, S., +, TC Jan. 2015 139-151 Open Access A Rewarding Framework for Network Resource Sharing in Co-Channel Hybrid Access Femtocell Networks. Shih, Y., +, TC Nov. 2015 3079-3090 Operating systems (computers) Stackless Multi-Threading for Embedded Systems. McCartney, W.P., +, TC Oct. 2015 2940-2952 Optimization A Post-Synthesis Optimization Technique for Reversible Circuits Exploiting Negative Control Lines. Datta, K., +, TC April 2015 1208-1214 A Time Fairness-Based MAC Algorithm for Throughput Maximization in 802.11 Networks. Le, Y., +, TC Jan. 2015 19-31 Bit-Width Optimization by Divide-and-Conquer for Fixed-Point Digital Signal Processing Systems. Chung, J., +, TC Nov. 2015 3091-3101 Cost-Efficient Mapping for Fault-Tolerant Virtual Networks. Jarray, A., +, TC March 2015 668-681 Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network. Huang, H., +, TC Dec. 2015 34883499 Mission Reliability, Cost and Time for Cold Standby Computing Systems with Periodic Backup. Levitin, G., +, TC April 2015 1043-1057 Optimal Task Placement with QoS Constraints in Geo-Distributed Data Centers Using DVFS. Gu, L., +, TC July 2015 2049-2059 Optimization of Composite Cloud Service Processing with Virtual Machines. Di, S., +, TC June 2015 1755-1768 Physarum Optimization: A Biology-Inspired Algorithm for the Steiner Tree Problem in Networks. Liu, L., +, TC March 2015 818-831 + Check author entry for coauthors 24 Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers. Wu, S., +, TC Sept. 2015 2637-2651 QoS-Based Composition of Service Specific Overlay Networks. Al Ridhawi, Y., +, TC March 2015 832-846 Selecting an Optimal Fault Tolerance Strategy for Reliable Service-Oriented Systems with Local and Global Constraints. Zheng, Z., +, TC Jan. 2015 219-232 Synergy of Dynamic Frequency Scaling and Demotion on DRAM Power Management: Models and Optimizations. Lu, Y., +, TC Aug. 2015 23672381 Unified Mitchell-Based Approximation for Efficient Logarithmic Conversion Circuit. Low, J.Y.L., +, TC June 2015 1783-1797 Oscillations Towards an Oscillator Based TRNG with a Certified Entropy Rate. Lubicz, D., +, TC April 2015 1191-1200 Outsourcing Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers. Wu, S., +, TC Sept. 2015 2637-2651 Verifiable Auditing for Outsourced Database in Cloud Computing. Wang, J., +, TC Nov. 2015 3293-3303 Overlay networks QoS-Based Composition of Service Specific Overlay Networks. Al Ridhawi, Y., +, TC March 2015 832-846 P Packet radio networks Scheme to Measure Packet Processing Time of a Remote Host through Estimation of End-Link Capacity. Salehin, K. M., +, TC Jan. 2015 205-218 Packet switching A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees. Zhang, B., +, TC June 2015 1548-1563 Packet Classification Using Dynamically Generated Decision Trees. Cheng, Y.-C., +, TC Feb. 2015 582-586 Paged storage H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor. Jin, S., +, TC Oct. 2015 2833-2846 Parallel algorithms Performance Optimization Using Partitioned SpMV on GPUs and Multicore CPUs. Yang, W., +, TC Sept. 2015 2623-2636 Parallel architectures Adaptive Cache Coherence Mechanisms with Producer–Consumer Sharing Optimization for Chip Multiprocessors. Kayi, A., +, TC Feb. 2015 316-328 Computer Architecture with Associative Processor Replacing Last-Level Cache and SIMD Accelerator. Yavits, L., +, TC Feb. 2015 368-381 MUCH: Multithreaded Content-Based File Chunking. Won, Y., +, TC May 2015 1375-1388 Predicting the Effect of Memory Contention in Multi-Core Computers Using Analytic Performance Models. Bardhan, S., +, TC Aug. 2015 2279-2292 Parallel machines Ultra-Scalable CPU-MIC Acceleration of Mesoscale Atmospheric Modeling on Tianhe-2. Xue, W., +, TC Aug. 2015 2382-2393 Parallel memories Parallel Decodable Two-Level Unequal Burst Error Correcting Codes. Namba, K., +, TC Oct. 2015 2902-2911 Parallel processing Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Comment on “High Speed Parallel Decimal Multiplication With Redundant Internal Encodings”. Gorgin, S., +, TC Jan. 2015 293-294 Design and Analysis of 3D-MAPS (3D Massively Parallel Processor with Stacked Memory). Kim, D. H., +, TC Jan. 2015 112-125 New Regular Radix-8 Scheme for Elliptic Curve Scalar Multiplication without Pre-Computation. Abdulrahman, E. A. H., +, TC Feb. 2015 438-451 Parallel Reproducible Summation. Demmel, J., +, TC July 2015 2060-2070 Reconfiguring Three-Dimensional Processor Arrays for Fault-Tolerance: Hardness and Heuristic Algorithms. Jiang, G., +, TC Oct. 2015 2926-2939 Reliability-Aware Speedup Models for Parallel Applications with Coordinated Checkpointing/Restart. Zheng, Z., +, TC May 2015 1402-1415 25 Safe Data Parallelism for General Streaming. Schneider, S., +, TC Feb. 2015 504-517 Scheduling Precedence Constrained Stochastic Tasks on Heterogeneous Cluster Systems. Li, K., +, TC Jan. 2015 191-204 Statistical Performance Comparisons of Computers. Chen, T., +, TC May 2015 1442-1455 Parallel programming Architecture Support for Tightly-Coupled Multi-Core Clusters with SharedMemory HW Accelerators. Dehyadegari, M., +, TC Aug. 2015 2132-2144 SpiNNaker—Programming Model. Brown, A.D., +, TC June 2015 17691782 Virtual Shuffling for Efficient Data Movement in MapReduce. Yu, W., +, TC Feb. 2015 556-568 Parity check codes Unequal Error Protection of Memories in LDPC Decoders. Condo, C., +, TC Oct. 2015 2981-2993 Pattern classification Energy-Efficient Real-Time Human Mobility State Classification Using Smartphones. Oshin, T.O., +, TC June 2015 1680-1693 Pattern clustering An Efficient and Trustworthy P2P and Social Network Integrated File Sharing System. Liu, G., +, TC Jan. 2015 54-70 By-Passing Infected Areas in Wireless Sensor Networks Using BPR. Yaakob, N., +, TC June 2015 1594-1606 Efficient Notification Ordering for Geo-Distributed Pub/Sub Systems. Baldoni, R., +, TC Oct. 2015 2796-2808 Hybrid Search Scheme for Social Networks Supported by Dynamic Weighted Distributed Label Clustering. Leu, J., +, TC Sept. 2015 2586-2594 Proximity-Aware Local-Recoding Anonymization with MapReduce for Scalable Big Data Privacy Preservation in Cloud. Zhang, X., +, TC Aug. 2015 2293-2307 Safe Data Parallelism for General Streaming. Schneider, S., +, TC Feb. 2015 504-517 Pattern matching Detection of Denial-of-Service Attacks Based on Computer Vision Techniques. Tan, Z., +, TC Sept. 2015 2519-2533 Efficient Rule Engine for Smart Building Systems. Sun, Y., +, TC June 2015 1658-1669 Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 Peer-to-peer computing An Efficient and Trustworthy P2P and Social Network Integrated File Sharing System. Liu, G., +, TC Jan. 2015 54-70 Maximizing P2P File Access Availability in Mobile Ad Hoc Networks though Replication for Efficient File Sharing. Chen, K., +, TC April 2015 1029-1042 Swarm Intelligence Based File Replication and Consistency Maintenance in Structured P2P File Sharing Systems. Shen, H., +, TC Oct. 2015 2953-2967 Percolation Characterization of Cascading Failures in Interdependent Cyber-Physical Systems. Huang, Z., +, TC Aug. 2015 2158-2168 Performance evaluation A Cache Hierarchy Aware Thread Mapping Methodology for GPGPUs. Lai, B. C., +, TC April 2015 884-898 A Stochastic Model for Estimating the Power Consumption of a Processor. Dargie, W., TC May 2015 1311-1322 Adaptive Cache Coherence Mechanisms with Producer–Consumer Sharing Optimization for Chip Multiprocessors. Kayi, A., +, TC Feb. 2015 316-328 Efficient Victim Block Selection for Flash Storage Devices. Tsao, C., +, TC Dec. 2015 3444-3460 High-Performance and Lightweight Transaction Support in Flash-Based SSDs. Lu, Y., +, TC Oct. 2015 2819-2832 N-Dimensional Twin Torus Topology. Andujar-Munoz, F.J., +, TC Oct. 2015 2847-2861 Predicting the Effect of Memory Contention in Multi-Core Computers Using Analytic Performance Models. Bardhan, S., +, TC Aug. 2015 2279-2292 Unified Mitchell-Based Approximation for Efficient Logarithmic Conversion Circuit. Low, J.Y.L., +, TC June 2015 1783-1797 Petri nets Automated Model-Based Testing of Role-Based Access Control Using Predicate/Transition Nets. Xu, D., +, TC Sept. 2015 2490-2505 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Phase change materials Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm. Qiu, M., +, TC Dec. 2015 3528-3540 Phase change memories Design and Implementation of a Journaling File System for Phase-Change Memory. Lee, E., +, TC May 2015 1349-1360 Non-Binary Orthogonal Latin Square Codes for a Multilevel Phase Charge Memory (PCM). Namba, K., +, TC July 2015 2092-2097 Phase change random access memory DCCS: Double Circular Caching Scheme for DRAM/PRAM Hybrid Cache. Hsieh, J., +, TC Nov. 2015 3115-3127 Pipeline processing Block-Precise Processors: Low-Power Processors with Reduced Operand Store Accesses and Result Broadcasts. Lakshminarayana, N.B., +, TC Nov. 2015 3102-3114 Interleaving in Systolic-Arrays: A Throughput Breakthrough. Causapruno, G., +, TC July 2015 1940-1953 Multiprocessor Capacity Metric and Analysis. Otoom, M., +, TC Nov. 2015 3181-3196 Pipelined Decision Tree Classification Accelerator Implementation in FPGA (DT-CAIF). Saqib, F., +, TC Jan. 2015 280-285 Safe Data Parallelism for General Streaming. Schneider, S., +, TC Feb. 2015 504-517 SLA: A Stage-Level Latency Analysisfor Real-Time Communicationin a Pipelined Resource Model. Kashif, H., +, TC April 2015 1177-1190 Pollution Comments on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”. Kim, Y., TC Dec. 2015 3619-3620 Polynomials Shifted Polynomial Basis Multipliers Based on Subquadratic Toeplitz Matrix-Vector Product Approach for All Irreducible Pentanomials. Han, J., +, TC March 2015 862-867 A Novel En-Route Filtering Scheme Against False Data Injection Attacks in Cyber-Physical Networked Systems. Yang, X., +, TC Jan. 2015 4-18 Automatic High-Level Data-Flow Synthesis and Optimization of Polynomial Datapaths Using Functional Decomposition. Ghandali, S., +, TC June 2015 1579-1593 New Hardware Implementations of WG (29, 11) and WG- 16 Stream Ciphers Using Polynomial Basis. El-Razouk, H., +, TC July 2015 2020-2035 Ports (Computers) On Data Center Network Architectures for Interconnecting Dual-Port Servers. Li, D., +, TC Nov. 2015 3210-3222 On the Network Power Effectiveness of Data Center Architectures. Shang, Y., +, TC Nov. 2015 3237-3248 Power aware computing PowerTracer: Tracing Requests in Multi-Tier Services to Reduce Energy Inefficiency. Lu, G., +, TC May 2015 1389-1401 A Stochastic Model for Estimating the Power Consumption of a Processor. Dargie, W., TC May 2015 1311-1322 Adaptive Voltage Scaling with In-Situ Detectors in Commercial FPGAs. Nunez-Yanez, J.L., TC Jan. 2015 45-53 Compiler-Assisted Refresh Minimization for Volatile STT-RAM Cache. Li, Q., +, TC Aug. 2015 2169-2181 Control-Flow Decoupling: An Approach for Timely, Non-Speculative Branching. Sheikh, R., +, TC Aug. 2015 2182-2203 Coordinated Power and Performance Guarantee with Fuzzy MIMO Control in Virtualized Server Clusters. Lama, P., +, TC Jan. 2015 97-111 Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand. Xu, D., +, TC March 2015 682-697 EXR: Greening Data Center Network with Software Defined Exclusive Routing. Li, D., +, TC Sept. 2015 2534-2544 ICCI: In-Cache Coherence Information. Garcia-Guirado, A., +, TC April 2015 995-1014 JEM: Just in Time/Just Enough Energy Management Methodology for Computing Systems. Jawad, M., +, TC June 2015 1798-1804 On the Interplay between Global DVFS and Scheduling Tasks with Precedence Constraints. Gerards, M.E., +, TC June 2015 1742-1754 Performance-Energy Optimizations for Shared Vector Accelerators in Multicores. Beldianu, S. F., +, TC March 2015 805-817 Power and Thermal-Aware Workload Allocation in Heterogeneous Data Centers. Al-Qawasmeh, A.M., +, TC Feb. 2015 477-491 Power Budgeting Techniques for Data Centers. Zhan, X., +, TC Aug. 2015 2267-2278 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Reconfiguring Three-Dimensional Processor Arrays for Fault-Tolerance: Hardness and Heuristic Algorithms. Jiang, G., +, TC Oct. 2015 2926-2939 Requester-Based Spin Lock: A Scalable and Energy Efficient Locking Scheme on Multicore Systems. Cui, Y., +, TC Jan. 2015 166-179 Stabilizing CPU Frequency and Voltage for Temperature-Aware DVFS in Mobile Devices. Kim, J. M., +, TC Jan. 2015 286-292 Synergy of Dynamic Frequency Scaling and Demotion on DRAM Power Management: Models and Optimizations. Lu, Y., +, TC Aug. 2015 23672381 Time Series Characterization of Gaming Workload for Runtime Power Management. Dietrich, B., +, TC Jan. 2015 260-273 Virtual Shuffling for Efficient Data Movement in MapReduce. Yu, W., +, TC Feb. 2015 556-568 Power consumption On the Interplay between Global DVFS and Scheduling Tasks with Precedence Constraints. Gerards, M.E., +, TC June 2015 1742-1754 Power and Thermal-Aware Workload Allocation in Heterogeneous Data Centers. Al-Qawasmeh, A.M., +, TC Feb. 2015 477-491 Unequal Error Protection of Memories in LDPC Decoders. Condo, C., +, TC Oct. 2015 2981-2993 Power demand Block-Precise Processors: Low-Power Processors with Reduced Operand Store Accesses and Result Broadcasts. Lakshminarayana, N.B., +, TC Nov. 2015 3102-3114 Energy Minimization in Multi-Task Software-Defined Sensor Networks. Zeng, D., +, TC Nov. 2015 3128-3139 On the Network Power Effectiveness of Data Center Architectures. Shang, Y., +, TC Nov. 2015 3237-3248 Power engineering computing JEM: Just in Time/Just Enough Energy Management Methodology for Computing Systems. Jawad, M., +, TC June 2015 1798-1804 Prediction theory Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 Predictive models Predicting Transient Downtime in Virtual Server Systems: An Efficient Sample Path Randomization Approach. Du, A.Y., +, TC Dec. 2015 3541-3554 Prefetching AppATP: An Energy Conserving Adaptive Mobile-Cloud Transmission Protocol. Liu, F., +, TC Nov. 2015 3051-3063 Pricing A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing. Mei, J., +, TC Nov. 2015 3064-3078 Principal component analysis Near-Optimal Thermal Monitoring Framework for Many-Core Systems-onChip. Ranieri, J., +, TC Nov. 2015 3197-3209 Private key cryptography Micro-Architectural Analysis of Time-Driven Cache Attacks: Quest for the Ideal Implementation. Rebeiro, C., +, TC March 2015 778-790 Probabilistic logic Design of Optimal Scan Tree Based on Compact Test Patterns for Test Time Reduction. Chen, L., +, TC Dec. 2015 3417-3429 Probability Energy-Efficient Real-Time Human Mobility State Classification Using Smartphones. Oshin, T.O., +, TC June 2015 1680-1693 Time-Series Pattern Based Effective Noise Generation for Privacy Protection on Cloud. Zhang, G., +, TC May 2015 1456-1469 Probability distribution Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits. Lee, D.T., +, TC Dec. 2015 3376-3388 Process monitoring End-to-End Communication Delay Analysis in Industrial Wireless Networks. Saifullah, A., +, TC May 2015 1361-1374 Processor scheduling Composition of Schedulability Analyses for Real-Time Multiprocessor Systems. Lee, J., +, TC April 2015 941-954 End-to-End Communication Delay Analysis in Industrial Wireless Networks. Saifullah, A., +, TC May 2015 1361-1374 Local-Deadline Assignment for Distributed Real-Time Systems. Hong, S., +, TC July 2015 1983-1997 On the Interplay between Global DVFS and Scheduling Tasks with Precedence Constraints. Gerards, M.E., +, TC June 2015 1742-1754 + Check author entry for coauthors 26 Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors. Zhang, Z., +, TC Nov. 2015 3249-3264 The Quadratic Utilization Upper Bound for Arbitrary Deadline Real-Time Tasks. Bini, E., TC Feb. 2015 593-599 Production Multiprocessor Capacity Metric and Analysis. Otoom, M., +, TC Nov. 2015 3181-3196 Program compilers Automatic Application of Power Analysis Countermeasures. Bayrak, A. G., +, TC Feb. 2015 329-341 Compiler-Assisted Refresh Minimization for Volatile STT-RAM Cache. Li, Q., +, TC Aug. 2015 2169-2181 Enabling Concurrent Failure Recovery for Regenerating-Coding-Based Storage Systems: From Theory to Practice. Li, R., +, TC July 2015 1898-1911 Safe Data Parallelism for General Streaming. Schneider, S., +, TC Feb. 2015 504-517 Software Support and Evaluation of Hardware Transactional Memory on Blue Gene/Q. Wang, A., +, TC Jan. 2015 233-246 Program debugging A Quantitative Characterization of Cross Coverage. Zhou, J., +, TC Aug. 2015 2408-2414 A Scalable Formal Debugging Approach with Auto-Correction Capability Based on Static Slicing and Dynamic Ranking for RTL Datapath Designs. Alizadeh, B., +, TC June 2015 1564-1578 Parallel Reproducible Summation. Demmel, J., +, TC July 2015 2060-2070 Program diagnostics Two-Dimensional Static Test Compaction for Functional Test Sequences. Pomeranz, I., TC Oct. 2015 3009-3015 Program processors Block-Precise Processors: Low-Power Processors with Reduced Operand Store Accesses and Result Broadcasts. Lakshminarayana, N.B., +, TC Nov. 2015 3102-3114 Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors. Zhang, Z., +, TC Nov. 2015 3249-3264 Program slicing A Scalable Formal Debugging Approach with Auto-Correction Capability Based on Static Slicing and Dynamic Ranking for RTL Datapath Designs. Alizadeh, B., +, TC June 2015 1564-1578 Program testing Automated Model-Based Testing of Role-Based Access Control Using Predicate/Transition Nets. Xu, D., +, TC Sept. 2015 2490-2505 Two-Dimensional Static Test Compaction for Functional Test Sequences. Pomeranz, I., TC Oct. 2015 3009-3015 Program verification A Scalable Formal Debugging Approach with Auto-Correction Capability Based on Static Slicing and Dynamic Ranking for RTL Datapath Designs. Alizadeh, B., +, TC June 2015 1564-1578 Programming GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs. Lee, J., +, TC Nov. 2015 3167-3180 Protocols A Deadline-Floor Inheritance Protocol for EDF Scheduled Embedded RealTime Systems with Resource Sharing. Burns, A., +, TC May 2015 12411253 A Promise of Realizable, Ultra-Scalable Communications at Nano-Scale:A Multi-Modal Nano-Machine Architecture. Liaskos, C., +, TC May 2015 1282-1295 A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 ICCI: In-Cache Coherence Information. Garcia-Guirado, A., +, TC April 2015 995-1014 Maximizing P2P File Access Availability in Mobile Ad Hoc Networks though Replication for Efficient File Sharing. Chen, K., +, TC April 2015 1029-1042 STEP: A Time-Efficient Tag Searching Protocol in Large RFID Systems. Liu, X., +, TC Nov. 2015 3265-3277 Public domain software Statistical Performance Comparisons of Computers. Chen, T., +, TC May 2015 1442-1455 Public key cryptography Cost-Effective Authentic and Anonymous Data Sharing with Forward Security. Huang, X., +, TC April 2015 971-983 27 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Fault Attacks on Pairing-Based Protocols Revisited. Chatterjee, S., +, TC June 2015 1707-1714 Identity-Based Encryption with Outsourced Revocation in Cloud Computing. Li, J., +, TC Feb. 2015 425-437 New Parallel Approaches for Scalar Multiplication in Elliptic Curve over Fields of Small Characteristic. Negre, C., +, TC Oct. 2015 2875-2890 New Regular Radix-8 Scheme for Elliptic Curve Scalar Multiplication without Pre-Computation. Abdulrahman, E. A. H., +, TC Feb. 2015 438-451 Question answering (information retrieval) Knowledge Sharing in the Online Social Network of Yahoo! Answers and Its Implications. Shen, H., +, TC June 2015 1715-1728 Queueing theory A Hardware Scheduler Based on Task Queues for FPGA-Based Embedded Real-Time Systems. Tang, Y., +, TC May 2015 1254-1267 A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees. Zhang, B., +, TC June 2015 1548-1563 R Q Quality of service A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees. Zhang, B., +, TC June 2015 1548-1563 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing. Mei, J., +, TC Nov. 2015 3064-3078 By-Passing Infected Areas in Wireless Sensor Networks Using BPR. Yaakob, N., +, TC June 2015 1594-1606 CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Credit-Based Runtime Placement of Virtual Machines on a Single NUMA System for QoS of Data Access Performance. Kim, C., +, TC June 2015 1633-1646 Efficient Server Provisioning and Offloading Policies for Internet Data Centers with Dynamic Load-Demand. Xu, D., +, TC March 2015 682-697 Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network. Huang, H., +, TC Dec. 2015 34883499 Optimal Task Placement with QoS Constraints in Geo-Distributed Data Centers Using DVFS. Gu, L., +, TC July 2015 2049-2059 Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 QoS-Based Composition of Service Specific Overlay Networks. Al Ridhawi, Y., +, TC March 2015 832-846 Selecting an Optimal Fault Tolerance Strategy for Reliable Service-Oriented Systems with Local and Global Constraints. Zheng, Z., +, TC Jan. 2015 219-232 STAR: Strategy-Proof Double Auctions for Multi-Cloud, Multi-Tenant Bandwidth Reservation. Zheng, Z., +, TC July 2015 2071-2083 Quantum computing A Post-Synthesis Optimization Technique for Reversible Circuits Exploiting Negative Control Lines. Datta, K., +, TC April 2015 1208-1214 Automated Design Architecture for 1-D Cellular Automata Using Quantum Cellular Automata. Mardiris, V.A., +, TC Sept. 2015 2476-2489 Simulation of Quantum Circuits via Stabilizer Frames. Garcia, H.J., +, TC Aug. 2015 2323-2336 Query processing An Efficient and Trustworthy P2P and Social Network Integrated File Sharing System. Liu, G., +, TC Jan. 2015 54-70 Block-Based Multi-Version B -Tree for Flash-Based Embedded Database Systems. Wang, J., +, TC April 2015 925-940 Hybrid Search Scheme for Social Networks Supported by Dynamic Weighted Distributed Label Clustering. Leu, J., +, TC Sept. 2015 2586-2594 Maximizing P2P File Access Availability in Mobile Ad Hoc Networks though Replication for Efficient File Sharing. Chen, K., +, TC April 2015 1029-1042 Multi-Granularity Locality-Sensitive Bloom Filter. Qian, J., +, TC Dec. 2015 3500-3514 Online Energy Estimation of Relational Operations in Database Systems. Xu, Z., +, TC Nov. 2015 3223-3236 QoS-Based Composition of Service Specific Overlay Networks. Al Ridhawi, Y., +, TC March 2015 832-846 Swarm Intelligence Based File Replication and Consistency Maintenance in Structured P2P File Sharing Systems. Shen, H., +, TC Oct. 2015 2953-2967 + Check author entry for coauthors Radiation hardening (electronics) Optimal Checkpoint Selection with Dual-Modular Redundancy Hardening. Kang, S., +, TC July 2015 2036-2048 Radio direction-finding Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 Radio links A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 Scheme to Measure Packet Processing Time of a Remote Host through Estimation of End-Link Capacity. Salehin, K. M., +, TC Jan. 2015 205-218 Radio networks A Cognitive TCP Design for a Cognitive Radio Network with an UnstableBandwidth Link. Yu-Chun, C., +, TC Oct. 2015 2730-3740 A Promise of Realizable, Ultra-Scalable Communications at Nano-Scale:A Multi-Modal Nano-Machine Architecture. Liaskos, C., +, TC May 2015 1282-1295 An Effective Area-Based Localization Algorithm for Wireless Networks. Lasla, N., +, TC Aug. 2015 2103-2118 The Optimal Node Placement for Long Belt Coverage in Wireless Networks. Wang, B., +, TC Feb. 2015 587-592 Radio receivers A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 Radio spectrum management Channel-Hopping Scheme and Channel-Diverse Routing in Static MultiRadio Multi-Hop Wireless Networks. Lin, T.-Y., +, TC Jan. 2015 71-86 Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 Radio transceivers RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Radiofrequency identification Completely Pinpointing the Missing RFID Tags in a Time-Efficient Way. Liu, X., +, TC Jan. 2015 87-96 STEP: A Time-Efficient Tag Searching Protocol in Large RFID Systems. Liu, X., +, TC Nov. 2015 3265-3277 Zero Knowledge Grouping Proof Protocol for RFID EPC C1G2 Tags. Sundaresan, S., +, TC Oct. 2015 2994-3008 RAID Accelerate RDP RAID-6 Scaling by Reducing Disk I/Os and XOR Operations. Zhang, G., +, TC Jan. 2015 32-44 Random access memory RNS Scalers for Extended 4-Moduli Sets. Sousa, L., TC Dec. 2015 33223334 Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 An Efficient I/O-Redirection-Based Reconstruction Scheme for Erasure-Coded Storage Clusters. Huang, J., +, TC Nov. 2015 3037-3050 Efficient Victim Block Selection for Flash Storage Devices. Tsao, C., +, TC Dec. 2015 3444-3460 Phase-Change Memory Optimization for Green Cloud with Genetic Algorithm. Qiu, M., +, TC Dec. 2015 3528-3540 WEC: Improving Durability of SSD Cache Drives by Caching Write-Efficient Data. Chai, Y., +, TC Nov. 2015 3304-3316 Random codes Reducing Code Length of Second-Order Spectral-Null Code. Yang, C.-N., +, TC Feb. 2015 492-503 Random number generation Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits. Lee, D.T., +, TC Dec. 2015 3376-3388 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 On the Quality of Random Sequences Produced with a Combined Random Bit Generator. Jessa, M., TC March 2015 791-804 Towards an Oscillator Based TRNG with a Certified Entropy Rate. Lubicz, D., +, TC April 2015 1191-1200 Random sequences On the Quality of Random Sequences Produced with a Combined Random Bit Generator. Jessa, M., TC March 2015 791-804 Zero Knowledge Grouping Proof Protocol for RFID EPC C1G2 Tags. Sundaresan, S., +, TC Oct. 2015 2994-3008 Random-access storage Compiler-Assisted Refresh Minimization for Volatile STT-RAM Cache. Li, Q., +, TC Aug. 2015 2169-2181 On-Demand Block-Level Address Mapping in Large-Scale NAND Flash Storage Systems. Chen, R., +, TC June 2015 1729-1741 RRAM Defect Modeling and Failure Analysis Based on March Test and a Novel Squeeze-Search Scheme. Chen, C., +, TC Jan. 2015 180-190 Zombie Chasing: Efficient Flash Management Considering Dirty Data in the Buffer Cache. Lee, Y., +, TC Feb. 2015 569-581 Reachability analysis Piecewise-Functional Broadside Tests Based on Reachable States. Pomeranz, I., TC Aug. 2015 2415-2420 Read-only storage Address Scrambling and Data Inversion Techniques for Yield Enhancement of NROM-Based ROMs. Lu, S., +, TC May 2015 1230-1240 Real-time systems ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds. Zhu, X., +, TC Dec. 2015 3389-3403 Completely Pinpointing the Missing RFID Tags in a Time-Efficient Way. Liu, X., +, TC Jan. 2015 87-96 Composition of Schedulability Analyses for Real-Time Multiprocessor Systems. Lee, J., +, TC April 2015 941-954 End-to-End Communication Delay Analysis in Industrial Wireless Networks. Saifullah, A., +, TC May 2015 1361-1374 FESTAL: Fault-Tolerant Elastic Scheduling Algorithm for Real-Time Tasks in Virtualized Clouds. Wang, J., +, TC Sept. 2015 2545-2558 Local-Deadline Assignment for Distributed Real-Time Systems. Hong, S., +, TC July 2015 1983-1997 SLA: A Stage-Level Latency Analysisfor Real-Time Communicationin a Pipelined Resource Model. Kashif, H., +, TC April 2015 1177-1190 Receivers Comments on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”. Kim, Y., TC Dec. 2015 3619-3620 Reconfigurable architectures Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 Redundancy On Nonblocking Multicast Fat-Tree Data Center Networks with Server Redundancy. Guo, Z., +, TC April 2015 1058-1073 Reed-Solomon codes Low Delay Single Symbol Error Correction Codes Based on Reed Solomon Codes. Pontarelli, S., +, TC May 2015 1497-1501 Relay networks (telecommunication) Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits. Lee, D.T., +, TC Dec. 2015 3376-3388 A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 Exploiting Small World Properties for Message Forwarding in Delay Tolerant Networks. Wei, K., +, TC Oct. 2015 2809-2818 Reliability theory Accurate and Efficient Estimation of Logic Circuits Reliability Bounds. Ibrahim, W., +, TC May 2015 1217-1229 Adaptive ECC Scheme for Hybrid SSD’s. Hsieh, J., +, TC Dec. 2015 33483361 An Efficient I/O-Redirection-Based Reconstruction Scheme for Erasure-Coded Storage Clusters. Huang, J., +, TC Nov. 2015 3037-3050 Analytical Fault Tolerance Assessment and Metrics for TSV-Based 3D Network-on-Chip. Eghbal, A., +, TC Dec. 2015 3591-3604 Mission Reliability, Cost and Time for Cold Standby Computing Systems with Periodic Backup. Levitin, G., +, TC April 2015 1043-1057 Symmetric Property and Reliability of Balanced Hypercube. Zhou, J.-X., +, TC March 2015 876-881 Replicated databases Swarm Intelligence Based File Replication and Consistency Maintenance in Structured P2P File Sharing Systems. Shen, H., +, TC Oct. 2015 2953-2967 + Check author entry for coauthors 28 Resistive RAM RDIS: Tolerating Many Stuck-At Faults in Resistive Memory. Maddah, R., +, TC March 2015 847-861 Testing Open Defects in Memristor-Based Memories. Hamdioui, S., +, TC Jan. 2015 247-259 Resource allocation A Deadline-Floor Inheritance Protocol for EDF Scheduled Embedded RealTime Systems with Resource Sharing. Burns, A., +, TC May 2015 12411253 Accelerate RDP RAID-6 Scaling by Reducing Disk I/Os and XOR Operations. Zhang, G., +, TC Jan. 2015 32-44 Community-Based Event Dissemination with Optimal Load Balancing. Xia, F., +, TC July 2015 1857-1869 iBuddy: Inverse Buddy for Enhancing Memory Allocation/Deallocation Performanceon Multi-Core Systems. Park, H., +, TC March 2015 720-732 Maximizing P2P File Access Availability in Mobile Ad Hoc Networks though Replication for Efficient File Sharing. Chen, K., +, TC April 2015 1029-1042 Multi-User Computation Partitioning for Latency Sensitive Mobile Cloud Applications. Yang, L., +, TC Aug. 2015 2253-2266 Optimization of Composite Cloud Service Processing with Virtual Machines. Di, S., +, TC June 2015 1755-1768 Power and Thermal-Aware Workload Allocation in Heterogeneous Data Centers. Al-Qawasmeh, A.M., +, TC Feb. 2015 477-491 Similarity and Locality Based Indexing for High Performance Data Deduplication. Xia, W., +, TC April 2015 1162-1176 Survivable Cloud Network Mapping for Disaster Recovery Support. Gu, F., +, TC Aug. 2015 2353-2366 The Quadratic Utilization Upper Bound for Arbitrary Deadline Real-Time Tasks. Bini, E., TC Feb. 2015 593-599 TSAC: Enforcing Isolation ofVirtual Machines in Clouds. Weng, C., +, TC May 2015 1470-1482 Utility Functions and Resource Management in an Oversubscribed Heterogeneous Computing Environment. Khemka, B., +, TC Aug. 2015 2394-2407 Virtual Resource Allocation Based on Link Interference in Cayley Wireless Data Centers. Luo, J., +, TC Oct. 2015 3016-3021 WaFS: A Workflow-Aware File System for Effective Storage Utilization in the Cloud. Wang, Y., +, TC Sept. 2015 2716-2729 Resource management Efficient Victim Block Selection for Flash Storage Devices. Tsao, C., +, TC Dec. 2015 3444-3460 Energy Minimization in Multi-Task Software-Defined Sensor Networks. Zeng, D., +, TC Nov. 2015 3128-3139 Fast Two-Level Address Translation for Virtualized Systems. Ahn, J., +, TC Dec. 2015 3461-3474 Routing protocols A Hybrid Multicast Routing for Large Scale Sensor Networks with Holes. Won, M., +, TC Dec. 2015 3362-3375 Channel-Hopping Scheme and Channel-Diverse Routing in Static MultiRadio Multi-Hop Wireless Networks. Lin, T.-Y., +, TC Jan. 2015 71-86 Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network. Huang, H., +, TC Dec. 2015 34883499 On the Network Power Effectiveness of Data Center Architectures. Shang, Y., +, TC Nov. 2015 3237-3248 Resilient and Power-Efficient Multi-Function Channel Buffers in Networkon-Chip Architectures. DiTomaso, D., +, TC Dec. 2015 3555-3568 S Safety-critical software FESTAL: Fault-Tolerant Elastic Scheduling Algorithm for Real-Time Tasks in Virtualized Clouds. Wang, J., +, TC Sept. 2015 2545-2558 Sampling methods A Quantitative Characterization of Cross Coverage. Zhou, J., +, TC Aug. 2015 2408-2414 Scheduling A Deadline-Floor Inheritance Protocol for EDF Scheduled Embedded RealTime Systems with Resource Sharing. Burns, A., +, TC May 2015 12411253 29 A Hardware Scheduler Based on Task Queues for FPGA-Based Embedded Real-Time Systems. Tang, Y., +, TC May 2015 1254-1267 Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Collaborative Mobile Charging. Zhang, S., +, TC March 2015 654-667 FESTAL: Fault-Tolerant Elastic Scheduling Algorithm for Real-Time Tasks in Virtualized Clouds. Wang, J., +, TC Sept. 2015 2545-2558 Multi-User Computation Partitioning for Latency Sensitive Mobile Cloud Applications. Yang, L., +, TC Aug. 2015 2253-2266 Scheduling Divisible Loads in Gaussian, Mesh and Torus Network of Processors. Zhang, Z., +, TC Nov. 2015 3249-3264 Scheduling Precedence Constrained Stochastic Tasks on Heterogeneous Cluster Systems. Li, K., +, TC Jan. 2015 191-204 SLA: A Stage-Level Latency Analysisfor Real-Time Communicationin a Pipelined Resource Model. Kashif, H., +, TC April 2015 1177-1190 Utility Functions and Resource Management in an Oversubscribed Heterogeneous Computing Environment. Khemka, B., +, TC Aug. 2015 2394-2407 WaFS: A Workflow-Aware File System for Effective Storage Utilization in the Cloud. Wang, Y., +, TC Sept. 2015 2716-2729 Scheduling algorithms ANGEL: Agent-Based Scheduling for Real-Time Tasks in Virtualized Clouds. Zhu, X., +, TC Dec. 2015 3389-3403 Search engines SCPS: A Social-Aware Distributed Cyber-Physical Human-Centric Search Engine. Shen, H., +, TC Feb. 2015 518-532 WEC: Improving Durability of SSD Cache Drives by Caching Write-Efficient Data. Chai, Y., +, TC Nov. 2015 3304-3316 Search problems CCLS: An Efficient Local Search Algorithm for Weighted Maximum Satisfiability. Luo, C., +, TC July 2015 1830-1843 Finding Multi-Constrained Multiple Shortest Paths. Feng, G., +, TC Sept. 2015 2559-2572 STEP: A Time-Efficient Tag Searching Protocol in Large RFID Systems. Liu, X., +, TC Nov. 2015 3265-3277 Secondary cells Collaborative Mobile Charging. Zhang, S., +, TC March 2015 654-667 Security IIPS: Infrastructure IP for Secure SoC Design. Wang, X., +, TC Aug. 2015 2226-2238 Multi-Granularity Locality-Sensitive Bloom Filter. Qian, J., +, TC Dec. 2015 3500-3514 Security of data A Lightweight Virtualization Solution for Android Devices. Chen, W., +, TC Oct. 2015 2741-2751 MuR-DPA: Top-Down Levelled Multi-Replica Merkle Hash Tree Based Secure Public Auditing for Dynamic Big Data Storage on Cloud. Liu, C., +, TC Sept. 2015 2609-2622 Semantic networks QoS-Based Composition of Service Specific Overlay Networks. Al Ridhawi, Y., +, TC March 2015 832-846 Sensor placement Deploying Wireless Sensor Networks with Fault-Tolerance for Structural Health Monitoring. Bhuiyan, M. Z. A., +, TC Feb. 2015 382-395 Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 Localization for Wireless Sensor and Actor Networks with Meandering Mobility. Akbas, M.I., +, TC April 2015 1015-1028 Sensors Energy Minimization in Multi-Task Software-Defined Sensor Networks. Zeng, D., +, TC Nov. 2015 3128-3139 Storage Placement in Path Networks. Bertossi, A.A., +, TC April 2015 12011207 Servers A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud Computing. Mei, J., +, TC Nov. 2015 3064-3078 On Data Center Network Architectures for Interconnecting Dual-Port Servers. Li, D., +, TC Nov. 2015 3210-3222 On the Network Power Effectiveness of Data Center Architectures. Shang, Y., +, TC Nov. 2015 3237-3248 Online Energy Estimation of Relational Operations in Database Systems. Xu, Z., +, TC Nov. 2015 3223-3236 Secure Distributed Deduplication Systems with Improved Reliability. Li, J., +, TC Dec. 2015 3569-3579 + Check author entry for coauthors IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 STEP: A Time-Efficient Tag Searching Protocol in Large RFID Systems. Liu, X., +, TC Nov. 2015 3265-3277 TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage. Zheng, W., +, TC Nov. 2015 3278-3292 Verifiable Auditing for Outsourced Database in Cloud Computing. Wang, J., +, TC Nov. 2015 3293-3303 WEC: Improving Durability of SSD Cache Drives by Caching Write-Efficient Data. Chai, Y., +, TC Nov. 2015 3304-3316 Service-oriented architecture An Adaptive Multilevel Indexing Method for Disaster Service Discovery. Wu, Y., +, TC Sept. 2015 2447-2459 Selecting an Optimal Fault Tolerance Strategy for Reliable Service-Oriented Systems with Local and Global Constraints. Zheng, Z., +, TC Jan. 2015 219-232 Service Composition in Opportunistic Networks: A Load and Mobility Aware Solution. Sadiq, U., +, TC Aug. 2015 2308-2322 Set theory Radix-2 Division Algorithms with an Over-Redundant Digit Set. Ebergen, J., +, TC Sept. 2015 2652-2663 Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 The Telephone Coordination Game Revisited: From Random to Deterministic Algorithms. Chen, L., +, TC Oct. 2015 2968-2980 Shared memory systems A Cache Hierarchy Aware Thread Mapping Methodology for GPGPUs. Lai, B. C., +, TC April 2015 884-898 Architecture Support for Tightly-Coupled Multi-Core Clusters with SharedMemory HW Accelerators. Dehyadegari, M., +, TC Aug. 2015 2132-2144 Predicting the Effect of Memory Contention in Multi-Core Computers Using Analytic Performance Models. Bardhan, S., +, TC Aug. 2015 2279-2292 Signal detection RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Signal processing algorithms Bit-Width Optimization by Divide-and-Conquer for Fixed-Point Digital Signal Processing Systems. Chung, J., +, TC Nov. 2015 3091-3101 Simulation Two-Dimensional Static Test Compaction for Functional Test Sequences. Pomeranz, I., TC Oct. 2015 3009-3015 Smart phones A Lightweight Virtualization Solution for Android Devices. Chen, W., +, TC Oct. 2015 2741-2751 Energy-Efficient Real-Time Human Mobility State Classification Using Smartphones. Oshin, T.O., +, TC June 2015 1680-1693 Network Variation and Fault Tolerant Performance Acceleration in Mobile Devices with Simultaneous Remote Execution. Kim, K., +, TC Oct. 2015 2862-2874 Stabilizing CPU Frequency and Voltage for Temperature-Aware DVFS in Mobile Devices. Kim, J. M., +, TC Jan. 2015 286-292 Social network services A Sword with Two Edges: Propagation Studies on Both Positive and Negative Information in Online Social Networks. Wen, S., +, TC March 2015 640-653 An Efficient and Trustworthy P2P and Social Network Integrated File Sharing System. Liu, G., +, TC Jan. 2015 54-70 Hybrid Search Scheme for Social Networks Supported by Dynamic Weighted Distributed Label Clustering. Leu, J., +, TC Sept. 2015 2586-2594 Knowledge Sharing in the Online Social Network of Yahoo! Answers and Its Implications. Shen, H., +, TC June 2015 1715-1728 Multi-Granularity Locality-Sensitive Bloom Filter. Qian, J., +, TC Dec. 2015 3500-3514 NextCell: Predicting Location Using Social Interplay from Cell Phone Traces. Zhang, D., +, TC Feb. 2015 452-463 SCPS: A Social-Aware Distributed Cyber-Physical Human-Centric Search Engine. Shen, H., +, TC Feb. 2015 518-532 Sociology Evolutionary Computing and Particle Filtering: A Hardware-Based Motion Estimation System. Rodriguez, A., +, TC Nov. 2015 3140-3152 Software defined networking EXR: Greening Data Center Network with Software Defined Exclusive Routing. Li, D., +, TC Sept. 2015 2534-2544 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network. Huang, H., +, TC Dec. 2015 34883499 Software fault tolerance FESTAL: Fault-Tolerant Elastic Scheduling Algorithm for Real-Time Tasks in Virtualized Clouds. Wang, J., +, TC Sept. 2015 2545-2558 Software libraries Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 MINIME: Pattern-Aware Multicore Benchmark Synthesizer. Deniz, E., +, TC Aug. 2015 2239-2252 Software performance evaluation iBuddy: Inverse Buddy for Enhancing Memory Allocation/Deallocation Performanceon Multi-Core Systems. Park, H., +, TC March 2015 720-732 Software radio A Split MAC Approach for SDR Platforms. Di Francesco, P., +, TC April 2015 912-924 Software tools Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Solid modeling Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 Source code (software) Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Sparse matrices Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs. Nechma, T., +, TC April 2015 1090-1103 Performance Optimization Using Partitioned SpMV on GPUs and Multicore CPUs. Yang, W., +, TC Sept. 2015 2623-2636 SPICE Parallel Sparse Matrix Solution for Circuit Simulation on FPGAs. Nechma, T., +, TC April 2015 1090-1103 SRAM chips Design of Hybrid Second-Level Caches. Valero, A., +, TC July 2015 18841897 Ensuring Cache Reliability and Energy Scaling at Near-Threshold Voltage With Macho. Mahmood, T., +, TC June 2015 1694-1706 PC-TRIO: A Power Efficient TCAM Architecture for Packet Classifiers. Banerjee, T., +, TC April 2015 1104-1118 Statistical analysis Detection of Denial-of-Service Attacks Based on Computer Vision Techniques. Tan, Z., +, TC Sept. 2015 2519-2533 Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace. Yu, S., +, TC Jan. 2015 139-151 Granular Evaluation of Anomalies in Wireless Sensor Networks Using Dynamic Data Partitioning with an Entropy Criteria. Kumarage, H., +, TC Sept. 2015 2573-2585 Revisiting Vulnerability Analysis in Modern Microprocessors. Maniatakos, M., +, TC Sept. 2015 2664-2674 Statistical Performance Comparisons of Computers. Chen, T., +, TC May 2015 1442-1455 Statistical distributions Performance Optimization Using Partitioned SpMV on GPUs and Multicore CPUs. Yang, W., +, TC Sept. 2015 2623-2636 Scheduling Precedence Constrained Stochastic Tasks on Heterogeneous Cluster Systems. Li, K., +, TC Jan. 2015 191-204 Stochastic processes A Stochastic Model for Estimating the Power Consumption of a Processor. Dargie, W., TC May 2015 1311-1322 A Stochastic Time-Domain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks. Haghighi, M.S., +, TC March 2015 627-639 Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits. Lee, D.T., +, TC Dec. 2015 3376-3388 An Improved Stochastic Modeling of Opportunistic Routing in Vehicular CPS. Zeng, D., +, TC July 2015 1819-1829 CCLS: An Efficient Local Search Algorithm for Weighted Maximum Satisfiability. Luo, C., +, TC July 2015 1830-1843 Stojmenovic, Ivan In Memoriam [Ivan Stojmenovic]. Zomaya, A.Y., TC Jan. 2015 3 + Check author entry for coauthors 30 Storage allocation Address Scrambling and Data Inversion Techniques for Yield Enhancement of NROM-Based ROMs. Lu, S., +, TC May 2015 1230-1240 Storage automation Secure Distributed Deduplication Systems with Improved Reliability. Li, J., +, TC Dec. 2015 3569-3579 Storage management Accelerate RDP RAID-6 Scaling by Reducing Disk I/Os and XOR Operations. Zhang, G., +, TC Jan. 2015 32-44 Cost-Effective Authentic and Anonymous Data Sharing with Forward Security. Huang, X., +, TC April 2015 971-983 Design and Analysis of 3D-MAPS (3D Massively Parallel Processor with Stacked Memory). Kim, D. H., +, TC Jan. 2015 112-125 Dynamic On-the-Fly Minimum Cost Benchmarking for Storing Generated Scientific Datasets in the Cloud. Yuan, D., +, TC Oct. 2015 2781-2795 iBuddy: Inverse Buddy for Enhancing Memory Allocation/Deallocation Performanceon Multi-Core Systems. Park, H., +, TC March 2015 720-732 MUCH: Multithreaded Content-Based File Chunking. Won, Y., +, TC May 2015 1375-1388 MuR-DPA: Top-Down Levelled Multi-Replica Merkle Hash Tree Based Secure Public Auditing for Dynamic Big Data Storage on Cloud. Liu, C., +, TC Sept. 2015 2609-2622 On-Demand Block-Level Address Mapping in Large-Scale NAND Flash Storage Systems. Chen, R., +, TC June 2015 1729-1741 Parallel Decodable Two-Level Unequal Burst Error Correcting Codes. Namba, K., +, TC Oct. 2015 2902-2911 Proactive Data Migration for Improved Storage Availability in Large-Scale Data Centers. Wu, S., +, TC Sept. 2015 2637-2651 SCPS: A Social-Aware Distributed Cyber-Physical Human-Centric Search Engine. Shen, H., +, TC Feb. 2015 518-532 Unequal Error Protection of Memories in LDPC Decoders. Condo, C., +, TC Oct. 2015 2981-2993 ViPZonE: Hardware Power Variability-Aware Virtual Memory Management for Energy Savings. Gottscho, M., +, TC May 2015 1483-1496 WaFS: A Workflow-Aware File System for Effective Storage Utilization in the Cloud. Wang, Y., +, TC Sept. 2015 2716-2729 Structural engineering computing Deploying Wireless Sensor Networks with Fault-Tolerance for Structural Health Monitoring. Bhuiyan, M. Z. A., +, TC Feb. 2015 382-395 Swarm intelligence Swarm Intelligence Based File Replication and Consistency Maintenance in Structured P2P File Sharing Systems. Shen, H., +, TC Oct. 2015 2953-2967 Switches 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching. Manoj P. D., S., +, TC Nov. 2015 3022-3036 On Data Center Network Architectures for Interconnecting Dual-Port Servers. Li, D., +, TC Nov. 2015 3210-3222 Simulation and Implication Using a Transfer Function Model for Switching Logic. Thornton, M.A., TC Dec. 2015 3580-3590 Switching circuits Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits. Lee, D.T., +, TC Dec. 2015 3376-3388 Switching systems Bit-Stuffing Algorithms for Crosstalk Avoidance in High-Speed Switching. Chang, C., +, TC Dec. 2015 3404-3416 Synchronization SpiNNaker—Programming Model. Brown, A.D., +, TC June 2015 17691782 System recovery Enabling Concurrent Failure Recovery for Regenerating-Coding-Based Storage Systems: From Theory to Practice. Li, R., +, TC July 2015 1898-1911 System-on-chip 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching. Manoj P. D., S., +, TC Nov. 2015 3022-3036 Abort-on-Fail Test Scheduling for Modular SOCs without and with Preemption. Ingelsson, U., +, TC Dec. 2015 3335-3347 Architecture Support for Task Out-of-Order Execution in MPSoCs. Wang, C., +, TC May 2015 1296-1310 Architecture Support for Tightly-Coupled Multi-Core Clusters with SharedMemory HW Accelerators. Dehyadegari, M., +, TC Aug. 2015 2132-2144 31 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Conformal ALU: A Conformal Geometric Algebra Coprocessor for Medical Image Processing. Franchini, S., +, TC April 2015 955-970 IIPS: Infrastructure IP for Secure SoC Design. Wang, X., +, TC Aug. 2015 2226-2238 Near-Optimal Thermal Monitoring Framework for Many-Core Systems-onChip. Ranieri, J., +, TC Nov. 2015 3197-3209 Optimal Checkpoint Selection with Dual-Modular Redundancy Hardening. Kang, S., +, TC July 2015 2036-2048 Optimization of Latency Insensitive Systems Through Back Pressure Minimization. Xue, B., +, TC Feb. 2015 464-476 Systolic arrays Interleaving in Systolic-Arrays: A Throughput Breakthrough. Causapruno, G., +, TC July 2015 1940-1953 T Table lookup Micro-Architectural Analysis of Time-Driven Cache Attacks: Quest for the Ideal Implementation. Rebeiro, C., +, TC March 2015 778-790 Multiplicative Division Employing Independent Factors. Matula, D.W., +, TC July 2015 2012-2019 Target tracking Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 Task analysis An FPTAS for Response Time Analysis of Fixed Priority Real-Time Tasks with Resource Augmentation. Nguyen, T.H.C., +, TC July 2015 1805-1818 Telecommunication congestion control A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Sliding Mode Congestion Control for Data Center Ethernet Networks. Jiang, W., +, TC Sept. 2015 2675-2690 Telecommunication control End-to-End Communication Delay Analysis in Industrial Wireless Networks. Saifullah, A., +, TC May 2015 1361-1374 Telecommunication network reliability End-to-End Communication Delay Analysis in Industrial Wireless Networks. Saifullah, A., +, TC May 2015 1361-1374 Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 Telecommunication network routing A Unified Framework for Line-Like Skeleton Extraction in 2D/3D Sensor Networks. Liu, W., +, TC May 2015 1323-1335 An Improved Stochastic Modeling of Opportunistic Routing in Vehicular CPS. Zeng, D., +, TC July 2015 1819-1829 By-Passing Infected Areas in Wireless Sensor Networks Using BPR. Yaakob, N., +, TC June 2015 1594-1606 Exploiting Small World Properties for Message Forwarding in Delay Tolerant Networks. Wei, K., +, TC Oct. 2015 2809-2818 EXR: Greening Data Center Network with Software Defined Exclusive Routing. Li, D., +, TC Sept. 2015 2534-2544 Joint Optimal Data Rate and Power Allocation in Lossy Mobile Ad Hoc Networks with Delay-Constrained Traffics. Guo, S., +, TC March 2015 747-762 Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 Packet Classification Using Dynamically Generated Decision Trees. Cheng, Y.-C., +, TC Feb. 2015 582-586 Service Composition in Opportunistic Networks: A Load and Mobility Aware Solution. Sadiq, U., +, TC Aug. 2015 2308-2322 Telecommunication network topology A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 End-to-End Communication Delay Analysis in Industrial Wireless Networks. Saifullah, A., +, TC May 2015 1361-1374 + Check author entry for coauthors Granular Evaluation of Anomalies in Wireless Sensor Networks Using Dynamic Data Partitioning with an Entropy Criteria. Kumarage, H., +, TC Sept. 2015 2573-2585 Localization for Wireless Sensor and Actor Networks with Meandering Mobility. Akbas, M.I., +, TC April 2015 1015-1028 On Nonblocking Multicast Fat-Tree Data Center Networks with Server Redundancy. Guo, Z., +, TC April 2015 1058-1073 Telecommunication power management Energy-Efficient Cooperative Communications for Multimedia Applications in Multi-Channel Wireless Networks. Li, P., +, TC June 2015 1670-1679 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Telecommunication scheduling A Nearly Optimal Packet Scheduling Algorithm for Input Queued Switches with Deadline Guarantees. Zhang, B., +, TC June 2015 1548-1563 Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Telecommunication security Comment on “An Efficient Homomorphic MAC with Small Key Size for Authentication in Network Coding”. Li, C., +, TC March 2015 882-883 Zero Knowledge Grouping Proof Protocol for RFID EPC C1G2 Tags. Sundaresan, S., +, TC Oct. 2015 2994-3008 Telecommunication standards Unequal Error Protection of Memories in LDPC Decoders. Condo, C., +, TC Oct. 2015 2981-2993 Telecommunication switching Sliding Mode Congestion Control for Data Center Ethernet Networks. Jiang, W., +, TC Sept. 2015 2675-2690 Telecommunication traffic A Stochastic Time-Domain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks. Haghighi, M.S., +, TC March 2015 627-639 Joint Optimal Data Rate and Power Allocation in Lossy Mobile Ad Hoc Networks with Delay-Constrained Traffics. Guo, S., +, TC March 2015 747-762 Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 Temperature measurement Near-Optimal Thermal Monitoring Framework for Many-Core Systems-onChip. Ranieri, J., +, TC Nov. 2015 3197-3209 Temperature sensors Near-Optimal Thermal Monitoring Framework for Many-Core Systems-onChip. Ranieri, J., +, TC Nov. 2015 3197-3209 Thermal management (packaging) Power and Thermal-Aware Workload Allocation in Heterogeneous Data Centers. Al-Qawasmeh, A.M., +, TC Feb. 2015 477-491 Stabilizing CPU Frequency and Voltage for Temperature-Aware DVFS in Mobile Devices. Kim, J. M., +, TC Jan. 2015 286-292 Thermal stresses Analytical Fault Tolerance Assessment and Metrics for TSV-Based 3D Network-on-Chip. Eghbal, A., +, TC Dec. 2015 3591-3604 Three dimensional displays 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching. Manoj P. D., S., +, TC Nov. 2015 3022-3036 Abort-on-Fail Test Scheduling for Modular SOCs without and with Preemption. Ingelsson, U., +, TC Dec. 2015 3335-3347 Analytical Fault Tolerance Assessment and Metrics for TSV-Based 3D Network-on-Chip. Eghbal, A., +, TC Dec. 2015 3591-3604 Through-silicon vias 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching. Manoj P. D., S., +, TC Nov. 2015 3022-3036 Analytical Fault Tolerance Assessment and Metrics for TSV-Based 3D Network-on-Chip. Eghbal, A., +, TC Dec. 2015 3591-3604 Throughput Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network. Huang, H., +, TC Dec. 2015 34883499 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 Multiprocessor Capacity Metric and Analysis. Otoom, M., +, TC Nov. 2015 3181-3196 On the Network Power Effectiveness of Data Center Architectures. Shang, Y., +, TC Nov. 2015 3237-3248 Time factors An Efficient I/O-Redirection-Based Reconstruction Scheme for Erasure-Coded Storage Clusters. Huang, J., +, TC Nov. 2015 3037-3050 Efficient Victim Block Selection for Flash Storage Devices. Tsao, C., +, TC Dec. 2015 3444-3460 Time series Time Series Characterization of Gaming Workload for Runtime Power Management. Dietrich, B., +, TC Jan. 2015 260-273 Time-Series Pattern Based Effective Noise Generation for Privacy Protection on Cloud. Zhang, G., +, TC May 2015 1456-1469 Time-domain analysis A Stochastic Time-Domain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks. Haghighi, M.S., +, TC March 2015 627-639 Timing Algorithms for Generating Probabilities with Multivalued Stochastic Relay Circuits. Lee, D.T., +, TC Dec. 2015 3376-3388 Toeplitz matrices Shifted Polynomial Basis Multipliers Based on Subquadratic Toeplitz Matrix-Vector Product Approach for All Irreducible Pentanomials. Han, J., +, TC March 2015 862-867 Comments on “Low-Latency Digit-Serial Systolic Double Basis Multiplier over GF (2 ) Using Subquadratic Toeplitz Matrix-Vector Product Approach”. Reyhani-Masoleh, A., TC April 2015 1215-1216 Training GREEN Cache: Exploiting the Disciplined Memory Model of OpenCL on GPUs. Lee, J., +, TC Nov. 2015 3167-3180 Transaction processing High-Performance and Lightweight Transaction Support in Flash-Based SSDs. Lu, Y., +, TC Oct. 2015 2819-2832 Transfer functions Simulation and Implication Using a Transfer Function Model for Switching Logic. Thornton, M.A., TC Dec. 2015 3580-3590 Transient response A Stochastic Time-Domain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks. Haghighi, M.S., +, TC March 2015 627-639 Transistors Resilient and Power-Efficient Multi-Function Channel Buffers in Networkon-Chip Architectures. DiTomaso, D., +, TC Dec. 2015 3555-3568 Transport protocols A Cognitive TCP Design for a Cognitive Radio Network with an UnstableBandwidth Link. Yu-Chun, C., +, TC Oct. 2015 2730-3740 Adaptive-Acceleration Data Center TCP. Zhang, T., +, TC June 2015 15221533 Community-Based Event Dissemination with Optimal Load Balancing. Xia, F., +, TC July 2015 1857-1869 Fault Attacks on Pairing-Based Protocols Revisited. Chatterjee, S., +, TC June 2015 1707-1714 Tree data structures Block-Based Multi-Version B -Tree for Flash-Based Embedded Database Systems. Wang, J., +, TC April 2015 925-940 Mining Associated Patterns from Wireless Sensor Networks. Rashid, M.M., +, TC July 2015 1998-2011 MuR-DPA: Top-Down Levelled Multi-Replica Merkle Hash Tree Based Secure Public Auditing for Dynamic Big Data Storage on Cloud. Liu, C., +, TC Sept. 2015 2609-2622 Virtual Shuffling for Efficient Data Movement in MapReduce. Yu, W., +, TC Feb. 2015 556-568 Trees (mathematics) An Improved Approximation Ratio to the Partial-Terminal Steiner Tree Problem. Lee, C.-W., +, TC Jan. 2015 274-279 Approximation Algorithms for Min-Max Cycle Cover Problems. Xu, W., +, TC March 2015 600-613 On Nonblocking Multicast Fat-Tree Data Center Networks with Server Redundancy. Guo, Z., +, TC April 2015 1058-1073 Physarum Optimization: A Biology-Inspired Algorithm for the Steiner Tree Problem in Networks. Liu, L., +, TC March 2015 818-831 Pubsub: An Efficient Publish/Subscribe System. Banerjee-Mishra, T., +, TC April 2015 1119-1132 + Check author entry for coauthors 32 Trusted computing An Efficient and Trustworthy P2P and Social Network Integrated File Sharing System. Liu, G., +, TC Jan. 2015 54-70 U Unicast Joint Optimization of Rule Placement and Traffic Engineering for QoS Provisioning in Software Defined Network. Huang, H., +, TC Dec. 2015 34883499 Uninterruptible power systems TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage. Zheng, W., +, TC Nov. 2015 3278-3292 Unsolicited e-mail Knowledge Sharing in the Online Social Network of Yahoo! Answers and Its Implications. Shen, H., +, TC June 2015 1715-1728 Upper bound A Generalization of Addition Chains and Fast Inversions in Binary Fields. Jarvinen, K., +, TC Sept. 2015 2421-2432 On Data Center Network Architectures for Interconnecting Dual-Port Servers. Li, D., +, TC Nov. 2015 3210-3222 US Department of Homeland Security Multi-Granularity Locality-Sensitive Bloom Filter. Qian, J., +, TC Dec. 2015 3500-3514 User interfaces k-Times Attribute-Based Anonymous Access Control for Cloud Computing. Yuen, T.H., +, TC Sept. 2015 2595-2608 Optimization of Composite Cloud Service Processing with Virtual Machines. Di, S., +, TC June 2015 1755-1768 V Value engineering STAR: Strategy-Proof Double Auctions for Multi-Cloud, Multi-Tenant Bandwidth Reservation. Zheng, Z., +, TC July 2015 2071-2083 Variable structure systems Sliding Mode Congestion Control for Data Center Ethernet Networks. Jiang, W., +, TC Sept. 2015 2675-2690 Vehicle dynamics Opportunistic Offloading of Deadline-Constrained Bulk Cellular Traffic in Vehicular DTNs. Yao, H., +, TC Dec. 2015 3515-3527 Vehicle routing Approximation Algorithms for Min-Max Cycle Cover Problems. Xu, W., +, TC March 2015 600-613 Vehicular ad hoc networks A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 An Improved Stochastic Modeling of Opportunistic Routing in Vehicular CPS. Zeng, D., +, TC July 2015 1819-1829 Very large scale integration RNS Scalers for Extended 4-Moduli Sets. Sousa, L., TC Dec. 2015 33223334 Video streaming A Reactive and Scalable Unicast Solution for Video Streaming over VANETs. Rezende, C., +, TC March 2015 614-626 Virtual machine monitors Fast Two-Level Address Translation for Virtualized Systems. Ahn, J., +, TC Dec. 2015 3461-3474 Virtual machines A Lightweight Virtualization Solution for Android Devices. Chen, W., +, TC Oct. 2015 2741-2751 CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Credit-Based Runtime Placement of Virtual Machines on a Single NUMA System for QoS of Data Access Performance. Kim, C., +, TC June 2015 1633-1646 H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor. Jin, S., +, TC Oct. 2015 2833-2846 Optimization of Composite Cloud Service Processing with Virtual Machines. Di, S., +, TC June 2015 1755-1768 33 IEEE TRANSACTIONS ON COMPUTERS, VOL. 65, NO. 1, JANUARY 2016 TSAC: Enforcing Isolation ofVirtual Machines in Clouds. Weng, C., +, TC May 2015 1470-1482 Virtual machining Fast Two-Level Address Translation for Virtualized Systems. Ahn, J., +, TC Dec. 2015 3461-3474 Virtualization A Lightweight Virtualization Solution for Android Devices. Chen, W., +, TC Oct. 2015 2741-2751 Coordinated Power and Performance Guarantee with Fuzzy MIMO Control in Virtualized Server Clusters. Lama, P., +, TC Jan. 2015 97-111 Cost-Efficient Mapping for Fault-Tolerant Virtual Networks. Jarray, A., +, TC March 2015 668-681 Fast Two-Level Address Translation for Virtualized Systems. Ahn, J., +, TC Dec. 2015 3461-3474 FESTAL: Fault-Tolerant Elastic Scheduling Algorithm for Real-Time Tasks in Virtualized Clouds. Wang, J., +, TC Sept. 2015 2545-2558 H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor. Jin, S., +, TC Oct. 2015 2833-2846 Predicting Transient Downtime in Virtual Server Systems: An Efficient Sample Path Randomization Approach. Du, A.Y., +, TC Dec. 2015 3541-3554 Survivable Cloud Network Mapping for Disaster Recovery Support. Gu, F., +, TC Aug. 2015 2353-2366 TSAC: Enforcing Isolation ofVirtual Machines in Clouds. Weng, C., +, TC May 2015 1470-1482 VLSI Automated Design Architecture for 1-D Cellular Automata Using Quantum Cellular Automata. Mardiris, V.A., +, TC Sept. 2015 2476-2489 VLSI Computational Architectures for the Arithmetic Cosine Transform. Rajapaksha, N., +, TC Sept. 2015 2708-2715 Voltage control 3D Many-Core Microprocessor Power Management by Space-Time Multiplexing Based Demand-Supply Matching. Manoj P. D., S., +, TC Nov. 2015 3022-3036 W Water heating TE-Shave: Reducing Data Center Capital and Operating Expenses with Thermal Energy Storage. Zheng, W., +, TC Nov. 2015 3278-3292 Web services Combining Efficiency, Fidelity, and Flexibility in Resource Information Services. Shen, H., +, TC Feb. 2015 353-367 Selecting an Optimal Fault Tolerance Strategy for Reliable Service-Oriented Systems with Local and Global Constraints. Zheng, Z., +, TC Jan. 2015 219-232 Web sites Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace. Yu, S., +, TC Jan. 2015 139-151 Weibull distribution Reliability-Aware Speedup Models for Parallel Applications with Coordinated Checkpointing/Restart. Zheng, Z., +, TC May 2015 1402-1415 WiMax Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 Wireless channels A Time Fairness-Based MAC Algorithm for Throughput Maximization in 802.11 Networks. Le, Y., +, TC Jan. 2015 19-31 Channel-Hopping Scheme and Channel-Diverse Routing in Static MultiRadio Multi-Hop Wireless Networks. Lin, T.-Y., +, TC Jan. 2015 71-86 Performance Analysis of IEEE 802.15.6 MAC Protocol under Non-Ideal Channel Conditions and Saturated Traffic Regime. Sarkar, S., +, TC Oct. 2015 2912-2925 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Wireless LAN A Time Fairness-Based MAC Algorithm for Throughput Maximization in 802.11 Networks. Le, Y., +, TC Jan. 2015 19-31 + Check author entry for coauthors Coexistence Wi-Fi MAC Design for Mitigating Interference Caused by Collocated Bluetooth. Hsu, A. C.-C., +, TC Feb. 2015 342-352 Dynamic Antenna Management for Uplink Energy Efficiency on 802.11n Mobile Devices. Cheng, S., +, TC Oct. 2015 2767-2780 Network Variation and Fault Tolerant Performance Acceleration in Mobile Devices with Simultaneous Remote Execution. Kim, K., +, TC Oct. 2015 2862-2874 Wireless sensor networks A Hybrid Multicast Routing for Large Scale Sensor Networks with Holes. Won, M., +, TC Dec. 2015 3362-3375 A Stochastic Time-Domain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks. Haghighi, M.S., +, TC March 2015 627-639 A Unified Framework for Line-Like Skeleton Extraction in 2D/3D Sensor Networks. Liu, W., +, TC May 2015 1323-1335 Approximation Algorithms for Min-Max Cycle Cover Problems. Xu, W., +, TC March 2015 600-613 By-Passing Infected Areas in Wireless Sensor Networks Using BPR. Yaakob, N., +, TC June 2015 1594-1606 Collaborative Location-Based Sleep Scheduling for Wireless Sensor Networks Integratedwith Mobile Cloud Computing. Zhu, C., +, TC July 2015 1844-1856 Collaborative Mobile Charging. Zhang, S., +, TC March 2015 654-667 Data Collection Maximization in Renewable Sensor Networks via Time-Slot Scheduling. Ren, X., +, TC July 2015 1870-1883 Deploying Wireless Sensor Networks with Fault-Tolerance for Structural Health Monitoring. Bhuiyan, M. Z. A., +, TC Feb. 2015 382-395 Efficient Rule Engine for Smart Building Systems. Sun, Y., +, TC June 2015 1658-1669 End-to-End Communication Delay Analysis in Industrial Wireless Networks. Saifullah, A., +, TC May 2015 1361-1374 Energy Minimization in Multi-Task Software-Defined Sensor Networks. Zeng, D., +, TC Nov. 2015 3128-3139 Granular Evaluation of Anomalies in Wireless Sensor Networks Using Dynamic Data Partitioning with an Entropy Criteria. Kumarage, H., +, TC Sept. 2015 2573-2585 Local Area Prediction-Based Mobile Target Tracking in Wireless Sensor Networks. Bhuiyan, M.Z.A., +, TC July 2015 1968-1982 Localization for Wireless Sensor and Actor Networks with Meandering Mobility. Akbas, M.I., +, TC April 2015 1015-1028 Mining Associated Patterns from Wireless Sensor Networks. Rashid, M.M., +, TC July 2015 1998-2011 Physarum Optimization: A Biology-Inspired Algorithm for the Steiner Tree Problem in Networks. Liu, L., +, TC March 2015 818-831 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161 Robot Coordination for Energy-Balanced Matching and Sequence Dispatch of Robots to Events. Lukic, M., +, TC May 2015 1416-1428 Stackless Multi-Threading for Embedded Systems. McCartney, W.P., +, TC Oct. 2015 2940-2952 Workstation clusters CloudGenius: A Hybrid Decision Support Method for Automating the Migration of Web Application Clusters to Public Clouds. Menzel, M., +, TC May 2015 1336-1348 Writing Block-Precise Processors: Low-Power Processors with Reduced Operand Store Accesses and Result Broadcasts. Lakshminarayana, N.B., +, TC Nov. 2015 3102-3114 WEC: Improving Durability of SSD Cache Drives by Caching Write-Efficient Data. Chai, Y., +, TC Nov. 2015 3304-3316 Z Zigbee A Stochastic Time-Domain Model for Burst Data Aggregation in IEEE 802.15.4 Wireless Sensor Networks. Haghighi, M.S., +, TC March 2015 627-639 RC-MAC: A Receiver-Centric MAC Protocol for Event-Driven Wireless Sensor Networks. Huang, P., +, TC April 2015 1149-1161