FortiGate-5060
Hot Swap
ETH0
Service
ETH0 ETH1
SAP
STATUS
SM1
5000SM
10/100
link/Act
10/100
link/Act
SM2
5060SAP
SERIAL
1
ALARM
1
RESET
FAN TRAY
RESET
FortiGate 5060
TOP
Chassis Guide
FAN TRAY
2
SERIAL
2
1
6
5
1
5
4
1
4
3
1
3
FILTER
6
2
2
1
1
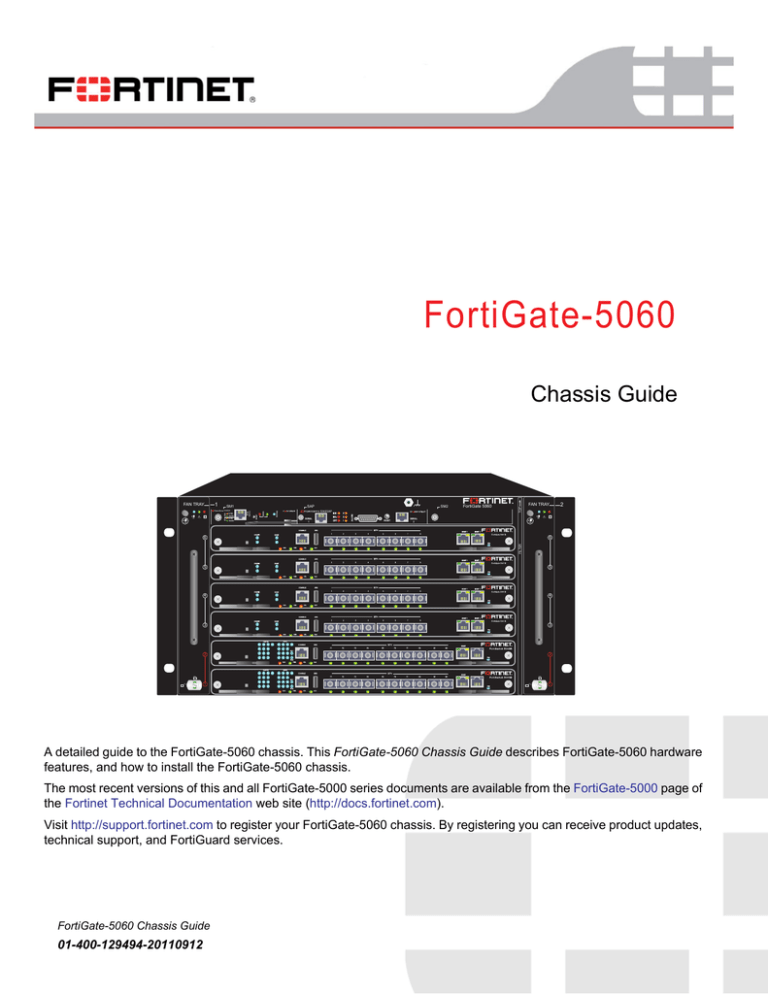
A detailed guide to the FortiGate-5060 chassis. This FortiGate-5060 Chassis Guide describes FortiGate-5060 hardware
features, and how to install the FortiGate-5060 chassis.
The most recent versions of this and all FortiGate-5000 series documents are available from the FortiGate-5000 page of
the Fortinet Technical Documentation web site (http://docs.fortinet.com).
Visit http://support.fortinet.com to register your FortiGate-5060 chassis. By registering you can receive product updates,
technical support, and FortiGuard services.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
Warnings and cautions
Warnings and cautions
Only trained and qualified personnel should be allowed to install or maintain
FortiGate-5000 series equipment. Read and comply with all warnings, cautions and
notices in this document.
CAUTION: Risk of Explosion if Battery is replaced by an Incorrect Type. Dispose of Used
Batteries According to the Instructions.
Caution: You should be aware of the following cautions and warnings before installing
FortiGate-5000 series hardware
•
•
•
•
•
•
•
•
•
•
•
•
Turning off all power switches may not turn off all power to the FortiGate-5000 series
equipment. Some circuitry in the FortiGate-5000 series equipment may continue to
operate even though all power switches are off.
FortiGate-5000 equipment must be protected by a readily accessible disconnect
device or circuit breaker that can be used for product power down emergencies.
Many FortiGate-5000 components are hot swappable and can be installed or removed
while the power is on. But some of the procedures in this document may require power
to be turned off and completely disconnected. Follow all instructions in the procedures
in this document that describe disconnecting FortiGate-5000 series equipment from
power sources, telecommunications links and networks before installing, or removing
FortiGate-5000 series components, or performing other maintenance tasks. Failure to
follow the instructions in this document can result in personal injury or equipment
damage.
Install FortiGate-5000 series chassis at the lower positions of a rack to avoid making
the rack top-heavy and unstable.
Do not insert metal objects or tools into open chassis slots.
Electrostatic discharge (ESD) can damage FortiGate-5000 series equipment. Only
perform the procedures described in this document from an ESD workstation. If no
such station is available, you can provide some ESD protection by wearing an
anti-static wrist strap and attaching it to an available ESD connector such as the ESD
sockets provided on FortiGate-5000 series chassis.
Make sure all FortiGate-5000 series components have reliable grounding. Fortinet
recommends direct connections to the building ground.
If you install a FortiGate-5000 series component in a closed or multi-unit rack
assembly, the operating ambient temperature of the rack environment may be greater
than room ambient. Make sure the operating ambient temperature does not exceed
Fortinet’s maximum rated ambient temperature.
Installing FortiGate-5000 series equipment in a rack should be such that the amount of
airflow required for safe operation of the equipment is not compromised.
FortiGate-5000 series chassis should be installed by a qualified electrician.
FortiGate-5000 series equipment shall be installed and connected to an electrical
supply source in accordance with the applicable codes and regulations for the location
in which it is installed. Particular attention shall be paid to use of correct wire type and
size to comply with the applicable codes and regulations for the installation / location.
Connection of the supply wiring to the terminal block on the equipment may be
accomplished using Listed wire compression lugs, for example, Pressure Terminal
Connector made by Ideal Industries Inc. or equivalent which is suitable for AWG-10.
Particular attention shall be given to use of the appropriate compression tool specified
by the compression lug manufacturer, if one is specified.
This product is only intended for use in a Restricted Access Location.
FortiGate-5060
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
2
Contents
Warnings and cautions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
FortiGate-5060 chassis
7
FortiGate-5060 front panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
FortiGate-5060 chassis back panel. . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Physical description of the FortiGate-5060 chassis . . . . . . . . . . . . . . . . . .
10
FortiGate-5060 shelf managers . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Using the shelf manager CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Shelf Manager fan and power control . . . . . . . . . . . . . . . . . . . . . . .
10
11
12
FortiGate-5060 shelf alarm panel. . . . . . . . . . . . . . . . . . . . . . . . . . . .
Shelf alarm panel telco alarms . . . . . . . . . . . . . . . . . . . . . . . . . . .
12
14
Air filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
15
Cooling fan trays . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
16
Power connection and configuration
17
About data center DC power . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
17
Connecting the FortiGate-5060 chassis to DC power and data center ground. . . . .
17
Connecting a FortiGate-5060 PEM to DC power . . . . . . . . . . . . . . . . . . . .
18
Connecting the FortiGate-5060 chassis to data center ground. . . . . . . . . . . . .
19
Connecting the FortiGate-5060 chassis to AC power using a FortiGate
power converter shelf. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
20
Turning on FortiGate-5060 chassis power . . . . . . . . . . . . . . . . . . . . . . .
20
FortiGate-5060 hardware procedures
23
Mounting the FortiGate-5060 chassis . . . . . . . . . . . . . . . . . . . . . . . . .
Air flow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
23
23
Inserting 5000 series boards and RTM modules into a FortiGate-5060 chassis . . . .
23
Using FortiSwitch-5003A boards for backplane communication . . . . . . . . . . . .
24
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
3
Contents
Using the shelf manager CLI
27
Connecting to the shelf manager CLI using a serial port . . .
Connecting to the shelf manager CLI . . . . . . . . . .
Changing the shelf manager root account password . .
The shelf manager command line interface agent (CLIA)
Using CLIA interactive mode . . . . . . . . . . . . . . .
4
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
27
28
28
29
29
IPMB addresses, logical and physical slot numbers, and FRU ids . . . . . . . . . . .
30
Basic shelf manager CLI Commands. . . . . . . . . . . . . . .
Change IP address of the primary Shelf Manager . . . . . .
Display the shelf manager firmware version . . . . . . . . .
List all FRUs in the chassis. . . . . . . . . . . . . . . . . .
List all sensors on a FRU. . . . . . . . . . . . . . . . . . .
List only sensors that are outside of established thresholds .
Display sensor data for a FRU . . . . . . . . . . . . . . . .
Display the FRU information for a FRU . . . . . . . . . . .
Change the speed for a fan tray . . . . . . . . . . . . . . .
Display the contents of the system event log (sel) . . . . . .
Clear the system event log (sel) . . . . . . . . . . . . . . .
.
.
.
.
.
.
.
.
.
.
.
31
31
31
31
31
31
31
31
31
31
31
Changing the shelf manager IP address and default gateway . . . . . . . . . . . . .
32
Sensor types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
33
activate/deactivate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
33
alarm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Clearing alarms. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Setting alarm output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
34
34
35
board . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Viewing information about a board . . . . . . . . . . . . . . . . . . . . . . . . .
35
35
clia . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
36
exit/quit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
36
fans . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
36
fru . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Display information for all FRUs . . . . . . . . . . . . . . . . . . . . . . . . . .
Display information for a specific FRU . . . . . . . . . . . . . . . . . . . . . . .
37
37
38
fruinfo . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
38
getlanconfig. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Displaying all configuration parameters for a channel . . . . . . . . . . . . . . .
Displaying specific parameters for a channel . . . . . . . . . . . . . . . . . . .
40
40
41
getthreshold/threshold . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Display threshold sensor values for a physical slot . . . . . . . . . . . . . . . .
Display threshold sensor values for a specific sensor . . . . . . . . . . . . . . .
41
42
45
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Contents
help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Displaying more information about a command . . . . . . . . . . . . . . . . . .
45
48
minfanlevel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
49
sel. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
50
sensor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
51
sensordata . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
52
setthreshold. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
53
shmstatus. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
54
showunhealthy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
55
switchover . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
55
terminate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
55
user . . . . . . . . . . . . . . . . . . . .
Display all user accounts . . . . . . .
Adding a user account . . . . . . . .
Deleting user accounts . . . . . . . .
Disabling and enabling user accounts
Changing a user account user name.
Changing a user account password .
.
.
.
.
.
.
.
56
56
56
57
57
57
58
version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
58
Generating SNMP traps for system events. . . . . . . . . . . . . . . . . . . . . . .
SNMP trap details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Removing and inserting a fan tray . . . . . . . . . . . . . . . . . . . . . . . . .
58
62
64
Using the chassis system event log (SEL)
Before you begin . . . . . . . . . . .
Chassis Design Background . . . . .
Alarm LEDs. . . . . . . . . . . . . .
Reading the System Event Log (SEL)
Clearing SEL logs . . . . . . . . . .
Example IPMC log output . . . . . .
Example FRU log output . . . . . . .
Example sensor log output . . . . . .
Sample sections of SEL Output . . .
64
64
64
65
66
67
67
68
69
77
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
For more information
79
Training . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
79
Documentation . . . . . . . . . . . . . . . . . . . .
Fortinet Tools and Documentation CD . . . . . .
Fortinet Knowledge Base . . . . . . . . . . . .
Comments on Fortinet technical documentation
.
.
.
.
79
79
79
79
Customer service and technical support . . . . . . . . . . . . . . . . . . . . . . . .
79
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
5
Contents
6
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
FortiGate-5060 chassis
You can install up to six FortiGate-5000 series boards in the six slots of the FortiGate-5060
ATCA chassis. The FortiGate-5060 is a 5U 19-inch rackmount ATCA chassis that contains
two redundant hot swappable DC power entry Modules (PEMs) connect to -48 VDC Data
Center DC power. The FortiGate-5060 chassis also includes two hot swappable cooling
fan trays and a front replaceable air filter. If all six slots contain FortiGate-5001B boards,
the FortiGate-5060 chassis provides a total of 48 FortiGate 10-gigabit ethernet interfaces.
You can also install FortiSwitch-5003B boards in FortiGate-5060 chassis slots 1 and 2 to
provide base backplane communications using the dual star base backplane interface.
Base backplane communications can be used for HA heartbeat communications and for
data communications.
FortiSwitch-5003B boards can also provide fabric backplane communication using the
FortiGate-5060 fabric backplane channels. The fabric backplane is a triple replicated
3-channel full mesh 10-gigabit switch fabric.
For both base and fabric backplane communications you can install a single
FortiSwitch-5003B board in slot 1. You can add a second FortiSwitch-5003B board to
slot 2 for redundancy.
Some of the boards installed in a FortiGate-5060 chassis can be operating in a FortiGate
HA cluster and some can be operating as standalone FortiGate units. You can also
operate multiple HA clusters and standalone FortiGate units in a single FortiGate-5060
chassis. You can also use FortiSwitch-5003B boards to operate HA clusters consisting of
FortiGate-5000 series boards installed in multiple FortiGate-5000 chassis. You can also
use FortiSwitch-5003B boards for data communication between chassis and for Enhanced
Load Balancing Cluster (ELBC) configurations. You can also install FortiSwitch-5203B
boards in slots 1 and 2, add FortiGate-5001B boards to slots 3 and up and operate the
FortiGate-5060 chassis in HA over chassis mode.
The FortiGate-5060 chassis also includes six rear transition module (RTM) slots. The
FortiGate-5060 chassis supports 10-gigabit fabric channel communication if you have
installed FortiGate-5001A boards with FortiGate-RTM-XB2 or FortiGate-RTM-XD2
modules and one or two FortiSwitch-5003A or FortiSwitch-5003B boards.
The FortiGate-5060 chassis requires -48VDC Data Center DC power. If DC power is not
available you can install a FortiGate power converter shelf and power supplies (purchased
separately).
This chapter describes the FortiGate-5060 chassis and includes the following sections:
•
FortiGate-5060 front panel
•
FortiGate-5060 chassis back panel
•
Physical description of the FortiGate-5060 chassis
•
FortiGate-5060 shelf managers
•
FortiGate-5060 shelf alarm panel
•
Air filter
•
Cooling fan trays
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
7
FortiGate-5060 front panel
FortiGate-5060 chassis
FortiGate-5060 front panel
Figure 1 shows the front of a FortiGate-5060 chassis. Two FortiSwitch-5003B boards are
installed in slots 1 and 2. Four FortiGate-5001B boards are installed in slots 3, 4, 5, and 6.
The FortiGate-5060 primary Shelf Manager and the Shelf Alarm Panel (SAP) are also
visible. The factory installed shelf alarm panel displays alarms, provides a telco alarm
interface, and also provides serial connections to the shelf managers. The factory installed
primary shelf manager provides power allocation, cooling, alarms, and shelf status for the
FortiGate-5060 chassis. You can also install a secondary shelf manager as a backup for
the primary shelf manager. For more information about these components, see
“FortiGate-5060 shelf alarm panel” on page 12 and “FortiGate-5060 shelf managers” on
page 10.
Figure 1: FortiGate-5060 front panel with FortiGate-5001B and FortiSwitch-5003B boards
installed
ESD socket
Hot-swappable
cooling fan tray 1
FortiSwitch-5003B
boards
slots 1 and 2
Hot Swap
ETH0
Service
ETH0 ETH1
SM2
5060SAP
SERIAL
1
RESET
FortiGate 5060
FAN TRAY
2
SERIAL
2
6
1
6
5
1
5
4
1
4
3
1
3
FILTER
FortiGate-5001B
boards, slots 3,
4, 5, and 6
SAP
STATUS
SM1
5000SM
10/100
link/Act
10/100
link/Act
ALARM
1
RESET
FAN TRAY
Secondary
Shelf Manager
(SM 2) Slot Cover
TOP
Primary
Shelf Manager Shelf Alarm
(SM 1)
Panel (SAP)
2
2
1
1
Front-replacable
air filter
Hot-swappable
cooling fan tray 2
Also visible on the front of the FortiGate-5060 chassis:
•
The location of the two hot-swappable FortiGate-5060 cooling fan trays.
•
The location of the front-replaceable air filter.
•
The Electrostatic discharge (ESD) socket, used for connecting an ESD wrist band
when working with the chassis.
Caution: Do not operate the FortiGate-5060 chassis with open slots on the front panel. For
optimum cooling performance and safety, the chassis slots must contain a FortiGate-5000
series board or an air baffle slot filler. For the same reason, both cooling fan trays and the
air filter should be installed while operating the chassis. As well both PEMs must be
installed in the back of the chassis.
8
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
FortiGate-5060 chassis
FortiGate-5060 chassis back panel
FortiGate-5060 chassis back panel
Figure 2 shows the back of a FortiGate-5060 chassis. The FortiGate-5060 chassis back
panel includes two redundant -48V to - 60 VDC power entry modules (PEMs) labelled
PEM A and PEM B. Fortinet ships the FortiGate-5060 chassis with PEM A and B installed.
The PEMs provide redundant DC power connections for the FortiGate-5060 chassis and
distribute DC power to the chassis slots and to the fan trays.
If you require redundant power you should connect both PEMs to DC power. If redundant
power is not required, you can connect PEM A or PEM B. Each PEM includes two power
terminals, one for connecting to -48V/-60 VDC and one for connecting to RTN. Use twohole lugs to connect the power terminals to DC power. Figure 2 shows the wiring required
to connect PEM B to a DC power source.
Figure 2: FortiGate-5060 chassis back panel (shows PEM B connected to DC power source)
RTN
(red)
(upper)
-48V/-60 VDC
nom (black)
(lower)
Power
Entry Module
(PEM) B
Branch 1
Branch 2
Branch 1
RTN
PEM
ESD
socket
Power
Entry Module
(PEM) A
-48/-60 V
Branch 2
RTN
PEM
PEM B
-48/-60 V
PEM A
Chassis
Ground
Connector
(green)
RTM Air Baffle slot covers
The back panel includes the FortiGate-5060 chassis ground connector which must be
connected to Data Center ground. The FortiGate-5060 chassis also includes an ESD
socket on the back panel.
For detailed information about connecting power to the FortiGate-5060 chassis, see
“Connecting the FortiGate-5060 chassis to DC power and data center ground” on page 17
or “Connecting the FortiGate-5060 chassis to AC power using a FortiGate power
converter shelf” on page 20.
The back panel also contains 6 RTM slots numbered to correspond to the front panel
slots. The RTM slots are available for FortiGate-5000 RTM modules such as the
FortiGate-RTM-XB2 module or the FortiGate-RTM-XD2 module. When the
FortiGate-5060 chassis is shipped, these slots are covered by RTM air baffle slot covers.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
9
Physical description of the FortiGate-5060 chassis
FortiGate-5060 chassis
Physical description of the FortiGate-5060 chassis
The FortiGate-5060 chassis is a 5U chassis that can be installed in a standard 19-inch
rack. Table 1 describes the physical characteristics of the FortiGate-5060 chassis.
Table 1: FortiGate-5060 chassis physical description
Dimensions
8.75 x 17 x 18.9 in. (22.2 x 43.2 x 48cm) (H x W x D) The
depth is from the fan tray handles on the front panel to the
connectors on the PEMs on the back panel.)
Shipping weight completely
assembled
with packaging
65.7 lb. (30 kg)
Chassis weight completely
assembled with shelf manager
and air baffles (5 front and 6
RTM)
50.7 lb. (23 kg)
Torque Rating
1.2 N m to 1.5 N m
Operating environment
Temperature (long term): 41 to 104°F (+5 to 40°C)
Temperature (short term): 23 to 131°F (-5 to 45°C)
Relative humidity: 5 to 85% (Non-condensing)
Power consumption
Maximum: 350 W (Power consumed by an empty chassis with
two fan trays, 2 shelf managers, one shelf alarm panel and 2
PEMs installed and operating with the fans running at full
speed.)
Power input
2x redundant -40.5 VDC to -60 VDC, 45 A total per PEM
Overcurrent Protection
30 A Fused Switches on PEMs
Cooling Capacity
Front Boards: 300 W per board
RTM: 30 W per module
Protected Earth Test
EN60950-1, test current 25 A, resistance <100mOhm
Hipot Test
EN60950-1, 1000 V
FortiGate-5060 shelf managers
The FortiGate-5060 chassis includes one or two redundant hot-swappable shelf
managers, located in the dedicated shelf manager slots near the top of the FortiGate-5060
front panel. The primary shelf manager is installed on the left (SM 1) the secondary shelf
manager (if present) is installed on the right (SM 2). The secondary shelf manager is
optional.
The shelf managers support redundant operation with automatic switchover. If both shelf
managers are operating normally, one acts as the active shelf manager and the other as
the standby. Usually the primary shelf manager would be the active shelf manager and the
secondary shelf manager would be the standby shelf manager. The shelf managers
monitor each other and either can trigger a switchover if necessary. The active shelf
manager performs all shelf manager functions. If the active shelf manager fails or is
removed, the standby shelf manager takes over all shelf manager functions.
The FortiGate-5060 shelf managers control chassis power allocation, monitor chassis
operating parameters, monitor and control chassis cooling, and can signal alarms if the
chassis encounters problems. All FortiGate-5000 modules installed in the chassis
communicate with the shelf managers.
10
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
FortiGate-5060 chassis
FortiGate-5060 shelf managers
The FortiGate-5060 shelf managers are factory installed. In most cases users do not have
to install or configure the shelf managers.
Each shelf manager has two ethernet interfaces (ETH 0 and ETH 1). You can connect to
ETH 0 from the shelf manager front panel. ETH 1 connects to the FortiGate-5060
backplane.
The shelf managers detect alarm conditions and communicate alarm signals to the
FortiGate-5060 shelf alarm panel. The shelf alarm panel also contains serial interfaces for
connecting to the shelf manager’s console ports.
The shelf managers are hot swappable. You can remove a shelf manager by opening the
extraction lever until the hot swap LED starts blinking. When the hot swap LED turns solid
blue you can remove the shelf manager from the FortiGate-5060 chassis.
Figure 3: FortiGate-5060 shelf manager front panel
STATUS
RESET
10/100
link/Act
10/100
link/Act
ETH0
Service
ETH0 ETH1
5000SM
Retention
ETH0
Status
Screw 10/100/1000 LEDs
base-T Ethernet
Hot Swap
Hot Swap
LED
ETH 0 and 1 network Reset
activity LEDs
Button
Handle
Table 2: FortiGate-5060 shelf manager LEDs
LED
State
Description
ETH 0 10/100
ETH 1 link/Act
Yellow
The Ethernet interface is connected at 100 Mbps.
Green
Blinking LED indicates network traffic.
Off
No link.
Green
This shelf manager is operating normally as the active shelf
manager. Usually the primary shelf manager operates as the
active shelf manager.
Red
This shelf manager is operating normally as the backup shelf
manager. Usually the secondary shelf manager operates as the
standby shelf manager.
STATUS
HOT SWAP
Off
The shelf manager is not ready to be removed.
Blue
The shelf manager is ready to be removed.
Long blink
The shelf manager is starting up after being inserted into the
chassis.
Short blink
The shelf manager is shutting down in preparation for being
removed from the chassis.
Using the shelf manager CLI
You can use the shelf manager command line interface (CLI) to communicate with the
intelligent management controllers of the chassis, with boards in the chassis, and with the
shelf manager itself. The CLI is an IPMI-based set of commands that can be accessed
directly or through a higher-level management application or a script. Using the CLI, you
can access information about the current state of the chassis including current board
population, current sensor values, threshold settings, recent events, and overall chassis
health.
To get started using the shelf manager CLI, see “Using the shelf manager CLI” on
page 27.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
11
FortiGate-5060 shelf alarm panel
FortiGate-5060 chassis
Shelf Manager fan and power control
The FortiGate-5060 shelf managers monitor the internal temperature of the
FortiGate-5060 chassis and adjust the operating speed of the FortiGate-5060 chassis
cooling fans as required.
When the chassis is first powered on all cooling fans run at full speed. Once the shelf
manager is up and running, the shelf manager reduces cooling fan speeds to maintain an
optimum temperature in the chassis. If shelf managers are not installed or not operating
correctly the FortiGate-5060 chassis cooling fans always operate at full speed.
FortiGate-5060 shelf alarm panel
The FortiGate-5060 shelf alarm panel (SAP), located at the top of the FortiGate-5060 front
panel, provides LED indicators of FortiGate-5060 alarms, a telco alarm connector, an
alarm LED reset button, and console access to the FortiGate-5060 shelf managers. The
LED alarm indicators include critical, major, and minor alarms as well as three user
defined alarms.
The alarm LED reset button (RESET) on the shelf alarm panel activates the Alarm Cutoff
(ACO) state. When ACO is activated, the active alarm LEDs blink and all of the alarm
relays are deactivated.
Figure 4: FortiGate-5060 shelf alarm panel front panel
Minor Alarm (MIN) (Amber)
Major Alarm (MAJ) (Red)
Critical Alarm (CRT) (Red)
User 3 Alarm (Amber)
User 2 Alarm (Amber)
User 1 Alarm (Amber)
SERIAL
1
Retention
Screw
SERIAL 1 (Primary
Shelf Manager)
12
ALARM
5000SAP
RESET
SERIAL
2
Alarm
Telco Alarm LED Reset
Interface
Button
SERIAL 2 (Secondary
Shelf Manager)
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
FortiGate-5060 chassis
FortiGate-5060 shelf alarm panel
Table 3: FortiGate-5060 shelf alarm panel LEDs
LED
State
CRT
(critical)
Off
Normal operation.
Red
Indicates a critical alarm.
Blinking
Red
Alarm cutoff (ACO) activated by pressing the alarm LED reset button.
MAJ (major) Off
MIN (minor)
USER3
USER2
USER1
Description
Normal operation.
Red
Indicates a major alarm.
Blinking
Red
Alarm cutoff (ACO) activated by pressing the alarm LED reset button.
Off
Normal operation.
Amber
Indicates a minor alarm.
Blinking
Amber
Alarm cutoff (ACO) activated by pressing the alarm LED reset button.
Off
Normal operation
Amber
Indicates a user-definable alarm.
Blinking
Amber
Alarm cutoff (ACO) activated by pressing the alarm LED reset button.
Table 4: FortiGate-5060 shelf alarm panel connectors
Connector
Type
Speed
Protocol
Description
SERIAL 1
RJ-45
9600 bps,
8/N/1
RS-232
serial
Serial connection to the primary shelf manager
command line interface.
SERIAL 2
RJ-45
9600 bps,
8/N/1
RS-232
serial
Serial connection to the secondary shelf
manager command line interface.
ALARM
micro
DB-15
male
N/A
Telco
Form-c
The external dry relay Telco alarm interface
(48VDC) provides Telco form-c relay
connections for minor, major and critical power
faults. The cable required to connect to the
alarm interface is not supplied by Fortinet.
Figure 5 shows the connections between the primary and secondary shelf managers and
the shelf alarm panel.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
13
FortiGate-5060 shelf alarm panel
FortiGate-5060 chassis
Figure 5: Connections between the shelf managers and the shelf alarm panel
ALARM
5000SAP
SERIAL
2
Enable
Master-Only
I²C-bus
ShMM-500
Master-Only
I²C-bus
Buffer
LTC4300
I²C-Switch
PCA9545
Serial Console Interface
C H0
CH3
CH0
RESET
Buffer
LTC4300
I²C-Switch
PCA9545
Enable
Serial Console Interface
CH3
SERIAL
1
ShMM-500
Secondary Shelf Manager (Left)
Primary Shelf Manager (Right)
Shelf alarm panel telco alarms
The shelf alarm panel telco alarm interface relay circuits are capable of carrying 60 VDC
or 1 A with a max. rating of 30 VA. The shelf alarm panel accepts timed pulse inputs for
clearing minor and major alarm states. Reset is accomplished by asserting a voltage
differential from 3.3 V to 48 V for between 200 and 300 ms. The acceptance voltage range
is from 0 to 48 VDC continuous (handles up to 60 VDC at a 50% duty cycle). The current
drawn by a reset input does not exceed 12 mA.
The alarm LED reset button activates the alarm cutoff (ACO) state for major, minor, and
user-defined alarms. You cannot reset critical alarms with the alarm LED reset button.
When the ACO state is activated, active alarm LEDs blink and all of the alarm relays are
deactivated. The alarm reset button activates the ACO state but does not clear the alarm
completely.
Figure 6: The telco alarm connector (DB-15 male)
15
8
14
9
1
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
FortiGate-5060 chassis
Air filter
Table 5: Telco alarm connector pin assignment
Pin
Name
Description
1
AMIR+
MinorReset+
2
AMIR-
MinorReset-
3
AMAR+
MajorReset+
4
AMAR-
MajorReset-
5
ACNO
CriticalAlarm - NO
6
ACNC
CriticalAlarm - NC
7
ACCOM
CriticalAlarm - COM
8
AMINO
MinorAlarm -NO
9
AMINC
MinorAlarm - NC
10
AMINCOM
MinorAlarm - COM
11
AMANO
MajorAlarm - NO
12
AMANC
MajorAlarm - NC
13
AMACOM
MajorAlarm - COM
14
APRCO
PwrAlarm - NO
15
APRCOM
PwrAlarm - COM
Shield
Shelf-GND
Shelf Ground
Air filter
The FortiGate-5060 chassis includes a front replaceable air filter. The filter provides 80%
dust arrestance and meets the requirements of the Telcordia Technologies Generic
Requirements GR-78-CORE specification. The filter must be installed for the
FortiGate-5060 chassis to operate normally. If the air filter is not locked into place the air
filter presence switch causes an alarm.
Air filters should be inspected regularly. If dirty or damaged, the filter should be disposed
of and replaced.
The air filter can be removed using the air filter handle on the front of the FortiGate-5060
chassis. To install a new filter, push the new filter into the guide rails at each side of the
shelf until the filter locks into place.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
15
Cooling fan trays
FortiGate-5060 chassis
Cooling fan trays
The FortiGate-5060 chassis contains two identical hot-swappable cooling fan trays
installed on the left and right sides of the chassis. The chassis can run indefinitely with
only one fan tray operating. The fans move air in the right side of the chassis and out the
left side.
You can remove a fan tray by pressing the hot swap button on the fan tray front panel.
When the Hot Swap LED is solid blue unlock the latch and pull the fan tray out using the
extraction handle.
Each cooling fan tray contains six radial fans for cooling the boards and modules installed
in the FortiGate-5060 chassis. Fan speeds are monitored by a tachometer signal sent
from the cooling fan trays to the shelf manager. The shelf manager regulates the fan
speed by adjusting the DC voltage supplied to the fan trays.
Figure 7: Cooling fan tray front panel
Hot swap
button
FAN TRAY
6
OK LED
Alarm LED
Hot swap LED
5
4
3
2
1
Latch
Table 6: FortiGate-5060 fan tray LEDs and controls
LED/Control
Description
OK (operate)
LED
Green when the fan tray is powered and operating normally.
Alarm LED
Normally off. Turns red when there is a problem with the fan tray.
HS (hot swap)
LED
Normally off. Blinking blue indicates that the fan tray is entering the hot
swap mode. Solid blue indicates that the fan tray is in hot swap mode and
can be removed from the chassis.
HS (hot
Press the HS button to enter hot swap mode. When the HS LED becomes
swap) button solid blue you can remove the fan tray from the chassis.
16
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Power connection and configuration
This chapter describes how to connect DC power to a FortiGate-5060 chassis.
If main DC power supplied by the data center in which the FortiGate-5060 chassis is to be
installed is not available, you can use a FortiGate power converter shelf to convert AC to
DC to supply DC power to the FortiGate-5060 chassis.
This chapter describes:
•
About data center DC power
•
Connecting the FortiGate-5060 chassis to DC power and data center ground
•
Connecting a FortiGate-5060 PEM to DC power
•
Connecting the FortiGate-5060 chassis to data center ground
•
Connecting the FortiGate-5060 chassis to AC power using a FortiGate power
converter shelf
•
Turning on FortiGate-5060 chassis power
About data center DC power
The FortiGate-5060 chassis is designed to be installed in a data center or similar location
that has available -48VDC power fed from a 30A listed circuit breaker (also called battery
power or main DC power). Fortinet expects that most FortiGate-5060 customers will be
installing their chassis in a data center or similar location that is already equipped with a
-48VDC power system fed from a 30A listed circuit breaker that provides power to existing
networking or telecom equipment. The FortiGate-5060 chassis is designed to be
connected directly to this DC power system.
In this document, data center DC power refers to a -48VDC power system that is already
available at the location at which the FortiGate-5060 chassis is being installed.
Connecting the FortiGate-5060 chassis to DC power and data
center ground
Connect the FortiGate-5060 chassis to r DC power using the redundant -48V to - 60 VDC
power entry modules (PEMs) on the FortiGate-5060 back panel labelled PEM A and
PEM B. The specified voltage range of the PEMs is -40.5 VDC to -60 VDC. The chassis
ships with both PEM A and B installed. The PEMs provide redundant DC power
connections for the FortiGate-5060 chassis and distribute DC power to the chassis slots
and to the fan trays.
Each FortiGate-5060 PEM includes two connectors for two power terminals that connect
power to different power zones in the FortiGate-5060 chassis. In the PEM, each power
terminal is protected by a 30A fused switch. The power zones are connected together and
should be connected to a single -48VDC power source with a 30A listed circuit breaker.
Each power zone supplies power to different FortiGate-5060 slots and cooling fan trays.
You should always connect both power zones.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
17
Connecting a FortiGate-5060 PEM to DC power
Power connection and configuration
To connect the FortiGate-5060 PEMs to data center DC power you must use power
connectors that comply with the local electrical wiring code and the requirements of the
facility in which you are installing the FortiGate-5060 chassis.
Fortinet supplies two 3-ft. power cables with AWG-10 stranded wires and ring terminals:
Black for -48VDC and red for RTN. These cables should only be used to connect the
FortiGate-5060 PEMs to a FortiGate power convertor shelf if purchased with your
FortiGate-5060 chassis. If the power cable length needs to be longer than 3 ft., higher
gauge wires should be used.
Green AWG-6 wires are recommended for ground connections (not supplied with the
chassis).
If you are connecting both PEMs the -48VDC and RTN terminals on PEM A and PEM B
must be wired symmetrically. This means that the connections must be the same to both
PEMs.
FortiGate-5060 PEMs are hot-swappable, which means you can remove and replace a
defective PEM while the system is operating (assuming that the FortiGate-5060 system
has both PEMs connected for redundancy). It is not necessary to notify the software or
reset the system power. You can add, remove, or replace a second PEM without
interrupting FortiGate-5060 operation.
Connecting a FortiGate-5060 PEM to DC power
The following procedure describes how to connect power to PEM A. You can repeat this
procedure to connect PEM B.
Figure 8: Connecting a FortiGate-5060 PEM to DC power
DC Power Source
RTN connector
RTN (positive)
red to power
source RTN
Hot swap LED
Alarm LED
OK LED
Hot swap button
Branch 1
Branch 2
RTN
-48/-60 V
PEM
-48V/-60 VDC
black to power
source -48VDC
Power Switches
DC Power Source
-48VDC
connector
18
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Power connection and configuration
Connecting the FortiGate-5060 chassis to data center ground
Table 7: FortiGate-5060 PEM LEDs and controls
LED/Control
Description
HS (hot swap)
LED
Normally off. Blinking blue indicates that the PEM is entering the hot swap
mode. Solid Blue indicates that the PEM is in hot swap mode and can be
removed from the chassis.
Alarm LED
Normally off. Turns red when there is a problem with the power source, or if
one or more of the 8 PEM fuses are blown or missing.
OK (operate)
LED
Green when the PEM is powered and operating normally.
HS (hot
Press the HS button to enter hot swap mode. When the HS LED becomes
swap) button solid blue you can remove the PEM from the chassis.
You need the following tools and equipment to connect a FortiGate-5060 PEM to data
center DC power:
•
A hex socket wrench is recommended for loosening and tightening the nuts on the
PEM power terminals.
•
An electrostatic discharge (ESD) preventive wrist strap with connection cord.
•
Two black AWG-10 stranded wires labelled -48V with attached Listed closed loop
single hole lugs with insulating boot suitable for minimum 10AWG copper wire, such as
3M model MH10-14RX.
•
Two red AWG-10 stranded wires labelled RTN with attached Listed closed loop single
hole lugs with insulating boot suitable for minimum 10AWG copper wire, such as 3M
model MH10-14RX.
To connect a FortiGate-5060 PEM to data center DC power
1 Attach the ESD wrist strap to your wrist and to an ESD socket or to a bare metal
surface on the chassis or frame.
2 Turn off both power switches on the PEM.
3 Remove the clear plastic cover from the PEM power connectors.
4 Connect the DC power wires (see Figure 8):
• Connect two black -48V power wires from the DC power source to the connectors
on the FortiGate-5060 PEM labeled -48V/-60 V (the lower connectors on the PEM).
• Connect two red RTN return wires from data center RTN to the connectors on the
FortiGate-5060 PEM labeled RTN (the upper connectors on the PEM).
5 Make sure the power wires are secured using tie wraps if required.
6 If required, label the black wire -48V.
7 If required, label the red wire RTN.
8 Turn on the PEM switches.
Connecting the FortiGate-5060 chassis to data center ground
The FortiGate-5060 chassis includes a ground terminal on the lower left side of the
FortiGate-5060 back panel (see Figure 2 on page 9). The Shelf ground terminal provides
two threads (M6) with a 15.88 mm (5/8“) spacing between thread centers to connect a
two-hole lug. This connector must be connected to data center ground.
You need the following tools and equipment to connect the FortiGate-5060 chassis to
ground:
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
19
Connecting the FortiGate-5060 chassis to AC power using a FortiGate power converter shelf
Power connection and configuration
•
A number 2 Phillips screwdriver.
•
An electrostatic discharge (ESD) preventive wrist strap with connection cord.
•
One green AWG-6 stranded wire with M6 two-hole terminal lug with 45° angle tongue
with a 15.88 mm (5/8“) spacing between hole centers.
Figure 9: Connecting a FortiGate-5060 chassis to data center ground
Chassis
Ground
Connector
(green)
Data Center
ground
connector
FortiGate-5060
Ground
Connector
(green)
(Central office
ground system)
To connect the FortiGate-5060 chassis to data center ground
1 Attach the ESD wrist strap to your wrist and to an ESD socket or to a bare metal
surface on the chassis or frame.
2 Connect the green ground wire from the data center ground to the ground connector on
the FortiGate-5060 chassis (see Figure 9).
3 Secure the ground wire to the chassis.
4 Optionally label the wire GND.
Connecting the FortiGate-5060 chassis to AC power using a
FortiGate power converter shelf
If data center DC power is not available, you can use a Fortinet-supplied power converter
shelf with hot swappable power supplies to convert AC power to DC power. FortiGate
power converter shelves and power supplies are not supplied with the FortiGate-5060
chassis and must be purchased separately.
As already mentioned, the FortiGate-5060 chassis ships with two 3-ft. power cables with
AWG-10 stranded wires and ring terminals: Black for -48VDC and red for RTN. These
cables should only be used to connect the FortiGate-5060 PEMs to a FortiGate power
convertor shelf if purchased with your FortiGate-5060 chassis. If the power cable length
needs to be longer than 3 ft., higher gauge wires should be used.
Turning on FortiGate-5060 chassis power
If you are using a power converter shelf, connect the power convertor shelf to AC power
and verify that it is operating correctly.
If you are using data center DC power, turn own the power to the chassis according to the
requirements of your data center DC power system.
Once the FortiGate-5060 chassis is connected to DC power you can turn on power to the
chassis by turning on the switches on the PEMs (see Figure 8 on page 18 for location of
the switches on each PEM).
20
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Power connection and configuration
Turning on FortiGate-5060 chassis power
The FortiGate-5060 chassis powers up. If the FortiGate-5060 is operating correctly, the
OK LEDs on the PEMs and fan trays should be lit. As well, the Status LED on the
FortiGate-5060 shelf manager front panel should be lit (see Figure 3 on page 11). None of
the LEDs on the shelf alarm panel (SAP) should be lit (see Figure 4 on page 12).
When the chassis first starts up you should also hear the cooling fans operating.
In addition, if any FortiGate-5000 series modules have been installed in the chassis they
should power on and their front panel LEDs should indicate that they are operating
normally.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
21
Turning on FortiGate-5060 chassis power
22
Power connection and configuration
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
FortiGate-5060 hardware procedures
This chapter assumes the chassis has been mounted and connected to a power source
as detailed in “Power connection and configuration” on page 17.
This chapter discusses:
•
Mounting the FortiGate-5060 chassis
•
Inserting 5000 series boards and RTM modules into a FortiGate-5060 chassis
•
Using FortiSwitch-5003A boards for backplane communication
Mounting the FortiGate-5060 chassis
Note: Mount the FortiGate chassis before installing the FortiGate-5000 series modules.
The FortiGate-5060 chassis must be mounted in a standard 19-inch rack. The chassis
requires 5U of vertical space in the rack.
If you install the FortiGate-5060 chassis in a closed or multi-unit rack assembly, the
operating ambient temperature of the rack environment may be greater than room
ambient temperature. Make sure the operating ambient temperature does not exceed the
manufacturer's maximum rated ambient temperature.
Caution: The FortiGate-5060 chassis should not be operated as a free-standing appliance.
Caution: Install the FortiGate-5060 chassis at the lower positions in the rack to avoid
making the rack top-heavy and potentially falling over.
Air flow
For rack installation, make sure that the amount of air flow required for safe operation of
the FortiGate-5060 chassis is not compromised.
Inserting 5000 series boards and RTM modules into a
FortiGate-5060 chassis
You can insert FortiGate and FortiSwitch-5000 series boards into the front of the
FortiGate-5060 chassis and RTM modules into the back of the chassis. Arrange the
boards and modules in slots as required for your configuration. FortiGate-5000 series
boards can be installed in any FortiGate-5060 front panel slots. FortiSwitch boards can
only be installed in switch slots 1 and 2. FortiGate-5000 series RTM modules can be
installed in any FortiGate-5060 RTM slot.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
23
Using FortiSwitch-5003A boards for backplane communication
FortiGate-5060 hardware procedures
All FortiGate-5060 chassis are shipped with air baffle filler panels/cards on all but one front
slot that include a warning message to read the FortiGate-5000 documentation before
installing your product. The temporary slot fillers must be removed and all slots filled;
either with FortiGate-5000 series boards or with air baffle slot fillers. Air baffle slot fillers
are similar to blank FortiGate-5000 boards and are required for proper cooling air flow.
Caution: FortiGate-5000 series and FortiSwitch-5000 series modules must be protected
from static discharge and physical shock. Only handle or work with FortiGate-5000 series
and FortiSwitch-5000 series modules at a static-free workstation. Always wear a grounded
electrostatic discharge (ESD) preventive wrist strap when handling FortiGate-5000 series
or FortiSwitch-5000 series modules.
Caution: Do not operate the FortiGate-5060 chassis with open slots on the front panel or
rear panel. For optimum cooling performance and safety, front panel slots must contain a
FortiGate-5000 series module or an air baffle slot filler and rear panel slots must either be
covered or must contain a rear transition module or slot filler.
Caution: To avoid damaging components, you should install RTM modules (such as the
FortiGate-RTM-XD2 module) first before you install the corresponding FortiGate front panel
board. If you have already installed a FortiGate board, you should remove it before
installing the RTM module.
To install FortiGate-5000 boards or RTM modules, see the documentation supplied with
the board or module. You can find copies of all FortiGate-5000 series documentation on
the FortiGate-5000 Series documentation web page.
Using FortiSwitch-5003A boards for backplane communication
FortiSwitch-5003A boards installed in a FortiGate-5060 chassis in slot 1 or slot 2 provide
fabric backplane switching for all of the FortiGate-5000 series boards installed in the
chassis. Fabric backplane switching is most often used for data communication between
FortiGate-5000 series boards in a chassis. The fabric backplane is a triple replicated
3-channel full mesh switch fabric.
If one or more of the FortiGate boards installed in the chassis are operating in Transparent
mode, two FortiSwitch-5003A boards in a chassis may cause looping because the fabric
backplane results in three connections between the FortiSwitch-5003A boards which
could also result in FortiGate boards installed in the chassis and operating in Transparent
mode to have multiple connections to the same network.
These three connections use FortiSwitch-5003A slot-2/1, slot 7, and slot 12. To avoid
looping you should enable spanning tree on both FortiSwitch-5003A boards or disable at
least 2 of these interfaces on at least one of the FortiSwitch-5003A boards. For example,
you can use the following command to disable the slot-2/1 and slot-7 interfaces:
config switch fabric-channel physical-port
edit slot-2/1
set status down
next
edit slot-7
set status down
end
24
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
FortiGate-5060 hardware procedures
Using FortiSwitch-5003A boards for backplane communication
FortiSwitch-5003A boards installed in a FortiGate-5060 chassis in slot 1 or slot 2 provide
base backplane switching for all of the FortiGate-5000 series boards installed in the
chassis. Base backplane switching is usually used for HA heartbeat communication
between FortiGate-5000 series boards in HA clusters.
For complete information about using the FortiSwitch-5003A for backplane
communications (including the FortiSwitch-5003A CLI reference), see the
FortiSwitch-5003A and 5003 Fabric and Base Backplane Communication Guide.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
25
Using FortiSwitch-5003A boards for backplane communication
26
FortiGate-5060 hardware procedures
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
You can use the shelf manager command line interface (CLI) to communicate with the
intelligent management controllers of the chassis, with boards in the chassis, and with the
shelf manager itself. The CLI is an IPMI-based set of commands that can be accessed
directly or through a higher-level management application or a script. Using the CLI, you
can access information about the current state of the chassis including current board
population, current sensor values, threshold settings, recent events, and overall chassis
health.
The Shelf Manager communicates inside the chassis with Intelligent Platform
Management Controllers (IPMC), each of which is responsible for local management of
one or more Field Replaceable Units (FRUs), such as boards, fan trays or power entry
modules. Management communication within a chassis occurs primarily over the
Intelligent Platform Management Bus (IPMB), which is implemented on two redundant
physical buses.
The shelf manager CLI can be used to communicate with the intelligent management
controllers of the shelf, with boards, and with the Shelf Manager itself. The CLI is an IPMIbased set of commands. The Intelligent Platform Management Interface specification
(IPMI spec) can be found at http://www.intel.com/design/servers/ipmi/spec.htm while CLI
reference guides for the Shelf Manager are available at TBD.
PICMG 3.0 specifications (developed by the PCI Industrial Computer Manufacturers
Group) define extensions to the IPMI specification. These specifications can be ordered
from http://www.picmg.org.
Connecting to the shelf manager CLI using a serial port
You can connect to the shelf manager CLI by connecting the console cable supplied with
your chassis to a management PC console port and to the appropriate shelf alarm panel
serial port. To connect to the primary shelf manager use Serial 1. To connect to the
secondary shelf manager use Serial 2.
Figure 10: Connecting to a shelf manager serial port
FortiGate-5060 Shelf Alarm Panel
SERIAL1 (Primary
Shelf Manager)
ALARM
5050SAP
SERIAL
1
SERIAL
2
Fortinet
RJ-45 to
9-pin
Console
Cable
SERIAL2 (Secondary
Shelf Manager)
To PC
RS-232
Console
Port
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
27
Connecting to the shelf manager CLI using a serial port
Using the shelf manager CLI
Connecting to the shelf manager CLI
Use the following procedure to connect to the shelf manager CLI.
To connect to the shelf manager CLI
1 Connect the console cable supplied with your chassis to the shelf manager Serial 1 or
Serial 2 port.
2 Connect the console cable supplied with your chassis to your PC or other device RS232 console port.
3 Start a terminal emulation program (for example, HyperTerminal) on the management
computer. Use these settings:
Baud Rate (bps)
9600
Data bits
8
Parity
None
Stop bits
1
Flow Control
None
4 Press enter to connect to the CLI.
5 At the login prompt enter the shelf manager user name and password.
The default user name is root with no password. For security reasons, it is strongly
recommended that you add a password for the root account.
When you log into the shelf manager CLI you are logging into a Linux shell as root. You
can begin entering commands at the # prompt:
Changing the shelf manager root account password
Use the following procedure to change the shelf manager root account password.
To add or change the shelf manager root account password
For enhanced security you should use the following steps to add a password for the shelf
manager root account.
1 At the # prompt enter the following Linux command to add a password for the root
account:
# passwd
2 Enter and confirm a new password for the root account.
The password should be between 5 and 8 characters long and should include a
combination of upper and lower case letters and numbers.
You can use the passwd command to change the root account password at any time.
After setting up your own accounts, you can also use the passwd command to remove
the root account. Enter the passwd command and when prompted for a password,
press enter to add a blank password.
28
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Connecting to the shelf manager CLI using a serial port
The shelf manager command line interface agent (CLIA)
Once you have logged into the shelf manager CLI you use the Command Line Interface
Agent (CLIA) to enter shelf manager commands. Usually you do this from the Linux
command line by entering clia followed by the required CLIA command verb and
parameters. The CLIA executable connects to the main Shelf Manager software process,
passes the command information to it and retrieves the results.
For example, you can enter the following command to list the most commonly used CLIA
commands:
clia help
You can also the help command to get more information about specific CLIA commands.
For example, use the following command display help for the shelf pwrreorder
command:
clia help shelf pwrreorder
Pigeon Point Shelf Manager Command Line Interpreter
Change the order of FRU Activation and Power Descriptors
instead of <addr> <fru_id> user may use:
board <N>
shm <N>
power_supply <N> (valid in 2.x systems only)
fan_tray <N>
PwrReorder <addr1> <fru_id1> before/after <addr2> <fru_id2>
Using CLIA interactive mode
You can also enter clia without parameters to enter interactive mode. In the interactive
mode, the shelf manager CLI issues a prompt to the terminal, accepts user input as the
next command with parameters, executes that command and shows the results on the
terminal, until you enter the command exit or quit. For example:
# clia
Pigeon Point Shelf Manager Command Line Interpreter
CLI> version
Pigeon Point Shelf Manager ver. 2.6.4.4
Pigeon Point and the stylized lighthouse logo are trademarks of
Pigeon Point Systems
Copyright (c) 2002-2009 Pigeon Point Systems
All rights reserved
Build date/time: Dec 14 2009 10:09:35
Carrier: HPDL/ACB
Carrier subtype : 0; subversion: 0
Cooling Management Library: libcooling_acb.so; Version: 2.6.4.4
Carrier Product ID: 21990047
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
29
IPMB addresses, logical and physical slot numbers, and FRU ids
Using the shelf manager CLI
IPMB addresses, logical and physical slot numbers, and FRU ids
The shelf manager manages the chassis over the Intelligent Platform Management Bus
(IPMB). All of the chassis slots have IPMB addresses (as well as hardware addresses) on
this bus. When you enter shelf manager CLI commands you indicate chassis slot numbers
according to their IPMB addresses. The IPMB and hardware addresses are in
hexadecimal format.
Table 8: FortiGate-5060 chassis slot addresses
Hub/ Hub/ Node Node Node Node
Node Node
Physical
slot
1
2
3
4
5
6
Logical slot
1
2
3
4
5
6
Hardware
address
(Hex)
41
42
43
44
45
46
IPMB
address
(Hex)
82
84
86
88
8A
8C
Boards installed in chassis slots are called field replaceable units (FRUs). Many CLI
commands also require referencing a FRU. In most cases if a board is installed in a slot
the slot will have one FRU with an ID of FRU 0. However, if a FortiGate-5001A board is
installed in a slot with an AMC module, this slot has two FRUs (FRU 0 and FRU 1).
For example, a FortiGate-5001A board with an AMC module is installed in logical slot 4,
then at IPMB address 88, there will be FRU 0 (the FortiGate-5001A board) and FRU 1 (the
AMC module).
Table 9 shows IPMB addresses and FRU IDs for other chassis components.
Table 9: IPMB addresses and FRU IDs for FortiGate-5060 chassis components
30
IPMB address
FRU ID
Description
10
0
Shelf manager in slot 0x10
12
0
Shelf manager in slot 0x12
20
1
Shelf EEPROM 1
20
2
Shelf EEPROM 2
20
3
Fan Tray 1
20
4
Fan Tray 2
20
5
PEM A
20
6
PEM B
20
7
SAP
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Basic shelf manager CLI Commands
Basic shelf manager CLI Commands
From the FortiGate-5050 chassis shelf manager CLI you can view system information,
FRU information and sensor data with the following basic commands. If your chassis has
two shelf managers, you must connect to the active shelf manager to access sensor data.
Change IP address of the primary Shelf Manager
The default IP address of the primary shelf manager is 192.168.0.2. Use the following
command to change this IP address.
# clia setlanconfig <channel> ip <ip_address>
<channel> is the shelf manager channel and can be 1 or 2. <ip_address> is the new
IP address in dotted decimal notation. For example:
# clia setlanconfig 1 ip 192.168.0.2
Display the shelf manager firmware version
# clia version
To display a complete list of all information enter version with no other parameters.
List all FRUs in the chassis
# clia fru
List all sensors on a FRU
# clia sensor <IPMB_address>
List only sensors that are outside of established thresholds
# clia sensor -t
Display sensor data for a FRU
# clia sensordata <IPMB_address> <sensor_number>
Display the FRU information for a FRU
# clia fruinfo <IPMB_address> <FRU_id>
Change the speed for a fan tray
# clia setfanlevel <IPMB-address> <FRU_id> <speed>
<speed> can be from 0 to 14.
Display the contents of the system event log (sel)
# clia sel
Clear the system event log (sel)
# clia sel clear
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
31
Changing the shelf manager IP address and default gateway
Using the shelf manager CLI
Changing the shelf manager IP address and default gateway
You can configure the shelf manager IP address and gateway so that you can use telnet
or ssh to access the Shelf Manager instead of the serial console port. You can view the
current LAN configuration with the following command:
# clia getlanconfig 1
Pigeon Point Shelf Manager Command Line Interpreter
Authentication Type Support: 0x15 ( None MD5 Straight
Password/Key )
Authentication Type Enables:
Callback level: 0x00
User level: 0x15 ( "None" "MD5" "Straight Password/Key" )
Operator level: 0x15 ( "None" "MD5" "Straight Password/Key" )
Administrator level: 0x15 ( "None" "MD5" "Straight
Password/Key" )
OEM level: 0x00
IP Address: 192.168.0.2
IP Address Source: Static Address (Manually Configured) (0x01)
MAC Address: 00:50:c2:3f:f0:9a
Subnet Mask: 255.255.255.0
IPv4 Header Parameters: 0x40:0x40:0x10
Primary RMCP Port Number: 0x026f
Secondary RMCP Port Number: 0x0298
BMC-generated ARP Control: 0x02
Enable BMC-generated ARP Response
Gratuitous ARP Interval: 2.0 seconds
Default Gateway Address: 192.168.0.1
Default Gateway MAC Address: 00:09:0f:09:32:03
Backup Gateway Address: 0.0.0.0
Backup Gateway MAC Address: N/A
Community String: "public"
Number of Destinations: 16
Destination Type:
DST Type # 2, Type: Unacknowledged PET Trap Destination
(0x00), ACK Timeout / Retry Interval: 0 seconds,
Retries: 0
Destination Address:
DST Addresses # 2, Address Format: IPv4 IP Address followed by
DIX ethernet / 802.3 MAC Address (0x00) Gateway: Default
(0x00), Alerting IP: 192.168.182.86, Alerting MAC:
00:09:0f:09:32:03
You can use the clia setlanconfig command to modify the shelf manager LAN
configuration.
To change the IP address, subnet mask, default gateway, enter the following commands:
# clia setlanconfig 1 3 x.x.x.x
# clia setlanconfig 1 6 x.x.x.x
# clia setlanconfig 1 12 x.x.x.x
32
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Sensor types
Sensor types
Access to monitored information, such as temperatures and voltages, fan status, etc., is
provided by the IPMI Sensor Module Instead of providing direct access to the monitoring
hardware, IPMI provides access by abstracted sensor commands implemented using a
management controller. This approach isolates software from changes in the platform
management hardware implementation.
Sensors are classified according to the type of readings they provide and/or the type of
events they generate. A sensor can return either an analog or discrete reading. Sensor
events can be discrete or threshold-based. The different event types, sensor types, and
monitored entities are represented using numeric codes (in hexadecimal) defined in the
IPMI specification.
Example of sensor type:
•
01 for temperature sensor
•
02 for voltage sensor
•
C0-FF for OEM reserved sensors (F0 is the hot swap sensor and F1 is the IPMB link
sensor).
activate/deactivate
clia activate <IPMB-address> <FRU-id>
clia deactivate <IPMB-address> <FRU-id>
Use these commands to activate and deactivate a specified FRU. After you enter the
deactivate command to deactivate a FortiGate board the board’s IPM or hot swap LED
changes to blue and the board will no longer be accessible. The board is ready to be hotswapped.
For example, to deactivate a board in physical slot 4 of a FortiGate-5060 chassis (IPMB
address 88, logical slot 4), enter:
# clia deactivate 88 0
Pigeon Point Shelf Manager Command Line Interpreter
Command issued via IPMB, status = 0 (0x0)
Command executed successfully
You can re-activate this deactivated board with the following command:
# clia activate 88 0
Pigeon Point Shelf Manager Command Line Interpreter
Command issued via IPMB, status = 0 (0x0)
Command executed successfully
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
33
alarm
Using the shelf manager CLI
alarm
clia alarm [clear | info| minor | major | critical]
This command provides access to the TELCO alarm outputs.
Enter clia alarm without parameters to view the current status of TELCO alarm
outputs:
# clia alarm
Pigeon Point Shelf Manager Command Line Interpreter
alarm mask: 0x00
Alarm mask 0x00 means no alarm.
Clearing alarms
Enter clia alarm clear to clear the minor and major alarm outputs. By default, critical
alarm outputs cannot be cleared. However, the shelfman.conf file contains the
following lines:
# ALLOW_CLEARING_CRITICAL_ALARM: This parameter of boolean type
enables the
# ability to clear the critical alarm condition without the
alarm cutoff
# button. Default is FALSE.
#
ALLOW_CLEARING_CRITICAL_ALARM = FALSE
If you change ALLOW_CLEARING_CRITICAL_ALARM to TRUE you can use the clia
alarm clear command to clear critical alarms.
Note: For more recent versions of the shelf manager firmware, ALLOW_CLEARING_CRITICAL_ALARM is set
to TRUE by default and the clia alarm clear command also clears critical alarms.
Enter clia alarm info to display information about the last alarm that occurred:
# clia alarm info
Pigeon Point Shelf Manager Command Line Interpreter
Last saved alarm information:
Alarm mask: 0x00
Alarm date/time: Sun Jun 8 21:56:47 2009
Alarm source: Schroff Carrier
Alarm reason: Cooling state alert
Note: Clearing the alarm changes the information displayed by the clia alarm command but not the
information displayed by the clia alarm info command.
34
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
board
Setting alarm output
Use minor, major and critical to set the corresponding alarm output. These actions
are cumulative; that is, after the commands clia alarm minor and clia alarm
major, both minor and major alarms will be set.
board
clia board [-v] [<physical-slot-address>]
Enter clia board without any parameters to view information about each IPM controller
and about each additional FRU controlled by these controllers.
This command is different from most of the rest of the commands because its works with
ATCA boards and takes as arguments physical slot numbers, instead of IPM controller
addresses and FRU device IDs.
This makes this command easier to use when boards may not include an IPM controller
and therefore, are not easily addressable using the IPMB address – FRU device ID pair.
Viewing information about a board
Enter the following command to view information about a particular board, for example the
board in physical slot 4 (logical slot 4, IPMB address 88):
# clia board 4
Pigeon Point Shelf Manager Command Line Interpreter
Physical Slot # 4
88: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
PICMG Version 2.1
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State
Change (0x0)
88: FRU # 0
Entity: (0xa0, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State
Change (0x0)
Device ID String: "FG5005A"
Add –v to the command to display more information (verbose).
The command output includes the hot swap state. M4 is the normal hot swap state.
Table 10 lists the FRU states defined in the PICMG 3.0 specification as follows:
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
35
clia
Using the shelf manager CLI
Table 10: PICMG FRU states
FRU state
M0
M1
M2
M3
M4
M5
M6
M7
Description
Not Installed
Inactive
Activation Request
Activation in Progress
FRU Active
Deactivation Request
Deactivation in Progress
Communication Lost
clia
clia
Start the CLI interactive mode. Using the interactive mode you can enter commands
without including the clia prefix.
exit/quit
exit
quit
If you start the CLI interactive mode by entering clia without any parameters you can
enter exit or quit to exit interactive mode.
fans
clia fans [-v] [ <IPMB_address> [ <FRU_device_ID> ] ]
Display information about the specified fan FRU. If <FRU_device_ID> is omitted, the
command displays information about all fan FRUs controlled by the IPM controller at the
specified address. If <IPMB_address> is also omitted, the command displays
information about all fan FRUs known to the shelf manager. The command displays the
following information for each fan:
•
IPMB address and FRU device ID
•
Current Level
•
Minimum Speed Level
•
Maximum Speed Level
# clia fans
# clia fans
20: FRU # 4
Current Level: 8
Minimum Speed Level: 1, Maximum Speed Level: 15 Dynamic minimum fan
level: 8
20: FRU # 3
Current Level: 8
Minimum Speed Level: 1, Maximum Speed Level: 15 Dynamic minimum fan
level: 8
36
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
fru
fru
clia fru [-v] [<IPMB_address> [id=<fru_device_id> |
type=<site_type>]] | [type=<site_type> [/<site_number>]]
This command displays information about a specific FRU. If <FRU_device_ID> is
omitted, the command shows information about all FRUs controlled by the IPM controller
at the specified address. If <IPMB_address> is also omitted, the command displays
information about all FRUs known to the shelf manager.
Display information for all FRUs
Enter the following command to display all of the FRUs at IPMB address 20 (fans, PEMs,
and so on):
# clia fru 20
Pigeon Point Shelf Manager Command Line Interpreter
20: FRU # 0
Entity: (0xf0, 0x1)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
Device ID String: "PPS BMC"
20: FRU # 1
Entity: (0xf2, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
Device ID String: "Shelf EEPROM 1"
20: FRU # 2
Entity: (0xf2, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
Device ID String: "Shelf EEPROM 2"
20: FRU # 3
Entity: (0x1e, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
Device ID String: "FanTray1"
20: FRU # 4
Entity: (0x1e, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
Device ID String: "FanTray2"
20: FRU # 5
Entity: (0x15, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
37
fruinfo
Using the shelf manager CLI
Device ID String: "PEM_A"
20: FRU # 6
Entity: (0x15, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
Device ID String: "PEM_B"
20: FRU # 7
Entity: (0xf3, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change
(0x0)
Device ID String: "SAP Board"
For information about hot swap states, see “board” on page 35.
Display information for a specific FRU
Enter this command with an IPMB address that refers to a physical slot to display
information similar to that displayed by the clia board command (see “board” on
page 35). For example, to display information about the board in physical slot 4 (logical
slot 4, IPMB address 88) enter:
# clia fru 88
Pigeon Point Shelf Manager Command Line Interpreter
88: FRU # 0
Entity: (0xa0, 0x60)
Hot Swap State: M4 (Active), Previous: M4 (Active), Last State
Change Cause: Normal State Change (0x0)
Device ID String: "FG5005A"
fruinfo
clia fruinfo [-v] [-x]<addr> <fru_id>
This command displays FRU Information in a user-friendly format.
For example to display FRU information for fan tray 0:
# clia fruinfo -v 20 2 3
Pigeon Point Shelf Manager Command Line Interpreter
20: FRU # 3, FRU Info
Common Header:
Format Version = 1
Internal Use Area:
Version = 1
Board Info Area:
Version
= 1
Language Code
38
= 25
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
fruinfo
Mfg Date/Time
minutes since 1996)
Board Manufacturer
Board Product Name
Board Serial Number
Board Part Number
FRU Programmer File ID
Custom Board Info
Product Info Area:
Version
= 1
Language Code
Manufacturer Name
Product Name
Product Part / Model#
Product Version
Product Serial Number
Asset Tag
FRU Programmer File ID
Custom Product Info
= Jul 14 11:01:00 2010 (7644181
=
=
=
=
=
=
Schroff
Fantray Controller
=
=
=
=
=
=
=
=
=
25
Schroff
Fantray
21990-024
AB
1261002969
0000000000000001
21990024AABIN.bin
23098-644
21990024AABIN.bin
PWR_CONSUMPTION=150000
Multi Record Area:
Record Type
= 0xc0 OEM Defined Record
Version = 2
Nothing is known about this PPS record 0x01
Record Type
= 0xc0 OEM Defined Record
Version = 2
Nothing is known about this PPS record 0x02
# clia fruinfo 20 3
Pigeon Point Shelf Manager Command Line Interpreter
20: FRU # 3, FRU Info
Common Header: Format Version = 1
Internal Use Area:
Version = 1
Board Info Area:
Version
Language Code
Mfg Date/Time
since 1996)
Board Manufacturer
Board Product Name
Board Serial Number
Board Part Number
FRU Programmer File ID
Product Info Area:
Version = 1
Language Code
Manufacturer Name
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
= 1
= 25
= Apr 7 06:39:00 2006 (5398959 minutes
=
=
=
=
=
Schroff
Fantray Controller
23098-533
21593100CABIN.bin
= 25
= Schroff
39
getlanconfig
Using the shelf manager CLI
Product Name
Product Part / Model#
Product Version
Product Serial Number
Asset Tag
FRU Programmer File ID
=
=
=
=
=
=
Fantray
21593-100
01
0000000000000001
00000000000000001
21593100CABIN.bin
Multi Record Area:
Record Type
= 0xc0 OEM Record
Version = 2
Nothing is known about this PPS record 0x01
Record Type
= 0xc0 OEM Record
Version = 2
Nothing is known about this PPS record 0x02
getlanconfig
clia getlanconfig <channel> [[<parameter_name>
[<additional_parameters>]] | [<parameter_number>
[<additional_parameters>]]
This command displays the LAN configuration parameters on the specified <channel>.
You can enter a <parameter_name> or the corresponding <parameter_number>
number to display information for a configuration parameter. Table 11 lists some
commonly used <parameter_names> and <parameter_numbers>.
Displaying all configuration parameters for a channel
If you do not include a <parameter_name> or <parameter_number> all configuration
parameters for the specified channel are displayed. See “Changing the shelf manager IP
address and default gateway” on page 32 for an example of using this command to
display the shelf manager LAN configuration.
Table 11: Commonly used getlanconfig parameter name and parameter numbers
40
<parameter_name>
<parameter_number>
Description
ip
3
A string value that contains the IP address
assigned to the LAN channel in dotted
decimal notation. For example, 192.168.0.2.
subnet_mask
6
A string value that contains the subnet mask
assigned to the LAN channel in dotted
decimal notation. For example,
255.255.255.0.
dft_gw_mac
13
A string value that contains the MAC address
of the default gateway as 6 hexadecimal byte
values delimited by ‘:’ symbols. For example,
00 : 1A : a0 : 2F : BC : C6.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
getthreshold/threshold
Displaying specific parameters for a channel
Enter the following command to display the IP address associated with channel 1:
# clia getlanconfig 1 ip
Pigeon Point Shelf Manager Command Line Interpreter
IP Address: 192.168.0.2
The following command also displays the IP address associated with channel 1:
# clia getlanconfig 1 3
Pigeon Point Shelf Manager Command Line Interpreter
IP Address: 192.168.0.2
The following command displays the subnet mask associated with channel 1:
# clia getlanconfig 1 subnet_mask
Pigeon Point Shelf Manager Command Line Interpreter
Subnet Mask: 255.255.255.0
The following command also displays the subnet mask associated with channel 1:
# clia getlanconfig 1 6
Pigeon Point Shelf Manager Command Line Interpreter
Subnet Mask: 255.255.255.0
The following command displays the default gateway IP address associated with channel
1:
# clia getlanconfig 1 dft_gw_ip
Pigeon Point Shelf Manager Command Line Interpreter
Default Gateway Address: 192.168.0.1
The following command also displays the default gateway IP address associated with
channel 1:
# clia getlanconfig 1 12
Pigeon Point Shelf Manager Command Line Interpreter
Default Gateway Address: 192.168.0.1
getthreshold/threshold
clia getthreshold [<IPMB-address> [<sensor-name> |
[<lun>:]<sensor-number>]]
clia threshold [<IPMB-address> [<sensor-name> | [<lun>:]<sensornumber>]]
This command displays the current threshold values for the supported thresholds of the
specified sensor(s). The sensor must be a threshold-based sensor. Both raw and
processed values are displayed. The following attributes for each sensor are also
displayed:
• IPMB address of the owning IPM controller
• Sensor number, sensor name and the LUN by which the sensor can be accessed
• The Sensor type and Event/reading type code
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
41
getthreshold/threshold
Using the shelf manager CLI
Display threshold sensor values for a physical slot
For example, to display the values for threshold sensors on physical slot 4 (in this
example, a FortiGate-5005FA2), enter the following command:
# clia threshold 88
Pigeon Point Shelf Manager Command Line Interpreter
88: LUN: 0, Sensor # 4 ("CPU1 Voltage")
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0x6c Processed data:
1.058400 Volts
Lower Critical Threshold, Raw Data: 0x67 Processed data:
1.009400 Volts
Lower Non-Recoverable Threshold, Raw Data: 0x61 Processed
data: 0.950600 Volts
Upper Non-Critical Threshold, Raw Data: 0xa9 Processed data:
1.656200 Volts
Upper Critical Threshold, Raw Data: 0xae Processed data:
1.705200 Volts
Upper Non-Recoverable Threshold, Raw Data: 0xb3 Processed
data: 1.754200 Volts
88: LUN: 0, Sensor # 5 ("CPU2 Voltage")
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0x6c Processed data:
1.058400 Volts
Lower Critical Threshold, Raw Data: 0x67 Processed data:
1.009400 Volts
Lower Non-Recoverable Threshold, Raw Data: 0x61 Processed
data: 0.950600 Volts
Upper Non-Critical Threshold, Raw Data: 0xa9 Processed data:
1.656200 Volts
Upper Critical Threshold, Raw Data: 0xae Processed data:
1.705200 Volts
Upper Non-Recoverable Threshold, Raw Data: 0xb3 Processed
data: 1.754200 Volts
88: LUN: 0, Sensor # 6 ("+5.0V")
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0xbe Processed data:
4.655000 Volts
Lower Critical Threshold, Raw Data: 0xb8 Processed data:
4.508000 Volts
Lower Non-Recoverable Threshold, Raw Data: 0xb0 Processed
data: 4.312000 Volts
Upper Non-Critical Threshold, Raw Data: 0xdb Processed data:
5.365500 Volts
Upper Critical Threshold, Raw Data: 0xe1 Processed data:
5.512500 Volts
Upper Non-Recoverable Threshold, Raw Data: 0xe9 Processed
data: 5.708500 Volts
88: LUN: 0, Sensor # 7 ("+3.3V")
42
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
getthreshold/threshold
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0xc0 Processed data:
3.110400 Volts
Lower Critical Threshold, Raw Data: 0xba Processed data:
3.013200 Volts
Lower Non-Recoverable Threshold, Raw Data: 0xb4 Processed
data: 2.916000 Volts
Upper Non-Critical Threshold, Raw Data: 0xd9 Processed data:
3.515400 Volts
Upper Critical Threshold, Raw Data: 0xdf Processed data:
3.612600 Volts
Upper Non-Recoverable Threshold, Raw Data: 0xe5 Processed
data: 3.709800 Volts
88: LUN: 0, Sensor # 8 ("+2.5V CPU 1")
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0xbd Processed data:
2.305800 Volts
Lower Critical Threshold, Raw Data: 0xb5 Processed data:
2.208200 Volts
Lower Non-Recoverable Threshold, Raw Data: 0xad Processed
data: 2.110600 Volts
Upper Non-Critical Threshold, Raw Data: 0xde Processed data:
2.708400 Volts
Upper Critical Threshold, Raw Data: 0xe6 Processed data:
2.806000 Volts
Upper Non-Recoverable Threshold, Raw Data: 0xee Processed
data: 2.903600 Volts
88: LUN: 0, Sensor # 9 ("+2.5V CPU 2")
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0xbd Processed data:
2.305800 Volts
Lower Critical Threshold, Raw Data: 0xb5 Processed data:
2.208200 Volts
Lower Non-Recoverable Threshold, Raw Data: 0xad Processed
data: 2.110600 Volts
Upper Non-Critical Threshold, Raw Data: 0xde Processed data:
2.708400 Volts
Upper Critical Threshold, Raw Data: 0xe6 Processed data:
2.806000 Volts
Upper Non-Recoverable Threshold, Raw Data: 0xee Processed
data: 2.903600 Volts
88: LUN: 0, Sensor # 10 ("+1.2V 1")
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0x76 Processed data:
1.156400 Volts
Lower Critical Threshold, Raw Data: 0x71 Processed data:
1.107400 Volts
Lower Non-Recoverable Threshold, Raw Data: 0x6c Processed
data: 1.058400 Volts
Upper Non-Critical Threshold, Raw Data: 0x80 Processed data:
1.254400 Volts
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
43
getthreshold/threshold
Using the shelf manager CLI
Upper Critical Threshold, Raw Data: 0x85 Processed data:
1.303400 Volts
Upper Non-Recoverable Threshold, Raw Data: 0x8a Processed
data: 1.352400 Volts
88: LUN: 0, Sensor # 11 ("+1.2V 2")
Type: Threshold (0x01), "Voltage" (0x02)
Lower Non-Critical Threshold, Raw Data: 0x76 Processed data:
1.156400 Volts
Lower Critical Threshold, Raw Data: 0x71 Processed data:
1.107400 Volts
Lower Non-Recoverable Threshold, Raw Data: 0x6c Processed
data: 1.058400 Volts
Upper Non-Critical Threshold, Raw Data: 0x80 Processed data:
1.254400 Volts
Upper Critical Threshold, Raw Data: 0x85 Processed data:
1.303400 Volts
Upper Non-Recoverable Threshold, Raw Data: 0x8a Processed
data: 1.352400 Volts
88: LUN: 0, Sensor # 12 ("Incoming Air-Flo")
Type: Threshold (0x01), "Temperature" (0x01)
Upper Non-Critical Threshold, Raw Data: 0x28 Processed data:
40.000000 degrees C
Upper Critical Threshold, Raw Data: 0x2d Processed data:
45.000000 degrees C
Upper Non-Recoverable Threshold, Raw Data: 0x32 Processed
data: 50.000000 degrees C
88: LUN: 0, Sensor # 13 ("CPU Board Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Upper Non-Critical Threshold, Raw Data: 0x4b Processed data:
75.000000 degrees C
Upper Critical Threshold, Raw Data: 0x51 Processed data:
81.000000 degrees C
Upper Non-Recoverable Threshold, Raw Data: 0x55 Processed
data: 85.000000 degrees C
88: LUN: 0, Sensor # 14 ("CPU1 Temp")
Type: Threshold (0x01), "Temperature" (0x01)
88: LUN: 0, Sensor # 15 ("CPU2 Temp")
Type: Threshold (0x01), "Temperature" (0x01)
44
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
help
Display threshold sensor values for a specific sensor
Enter the following command to display the threshold for sensor 13, which for the
FortiGate-5005FA2 is the CPU board temperature:
# clia threshold 88 13
Pigeon Point Shelf Manager Command Line Interpreter
88: LUN: 0, Sensor # 13 ("CPU Board Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Upper Non-Critical Threshold, Raw Data: 0x4b Processed data:
75.000000 degrees C
Upper Critical Threshold, Raw Data: 0x51 Processed data:
81.000000 degrees C
Upper Non-Recoverable Threshold, Raw Data: 0x55 Processed
data: 85.000000 degrees C
You can also enter the name of the sensor in quotes:
# clia threshold 88 "CPU Board Temp"
Pigeon Point Shelf Manager Command Line Interpreter
88: LUN: 0, Sensor # 13 ("CPU Board Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Upper Non-Critical Threshold, Raw Data: 0x4b Processed data:
75.000000 degrees C
Upper Critical Threshold, Raw Data: 0x51 Processed data:
81.000000 degrees C
Upper Non-Recoverable Threshold, Raw Data: 0x55 Processed
data: 85.000000 degrees C
help
clia help [<command> [<sub_command>] ]
This command displays help information about supported commands and their syntax.
Enter the command with no parameters to display all commands,
# clia help
Pigeon Point Shelf Manager Command Line Interpreter
Command Line Interface command set:
Parameters are case insensitive
In general:
IPMB address is hexadecimal ALWAYS.
All other numbers may be either decimal and hexadecimal (0x
notation required for hexadecimal notation)
-v turns on verbose output
activate <addr> <fru_id>
airfilterreplaced [<date>]
alarm <alarm status/action>
amcportstate [-v] <ipmc> [ amc <N> | <fru_id> ]
board [slot_number]
boardreset <slot number>
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
45
help
Using the shelf manager CLI
busres force <res>
busres info [<res>]
busres lock <res>
busres query [-v] <res> [<target> [noupdate]]
busres release <res>
busres sendbusfree <res> <target>
busres setowner <res> <target>
busres unlock <res>
deactivate <addr> <fru_id>
debuglevel [<mask> [<console mask>] ]
dhcp <restart> | <status>
exit
fans <addr> <fru id>
firewall [<info [[[[<channel>]:<LUN>]:<NetFn>]:<command>] |
<[all]>> | <stop> | <start>]
fru [<addr> [id=<fru_id> | type=<site_type>]] |
[type=<site_type> [/<site_number>]]
frucontrol <addr> <fru_id> <command>
frudata [<addr>] [<fru id>] [<block number>]
frudata shm <N> [<block number>]
frudata <addr> <fru id> <byte offset> <byte_1> [byte2 ..
[byte_16]]
frudatar <addr> <fru id> <file name>
frudataw [-s|-d|-p|-l] <addr> <fru id> <file name>
frudataw <-s|-d|-p|-l> -c <addr> <fru id>
fruinfo <addr> <fru_id>
getbootdev <addr> [<fru-id> | <amc-addr>]
getconfigparam [<parameter name>]
getfanlevel <addr> <fru_id>
getfanpolicy [<addr> [<fru_id>]] [-s <addr>|site_type
[<fru_id>|site_number]]
getfruledstate [-v] [<addr> [<fru_id> [<LedId>|ALL]]]
gethysteresis [ <addr> [ [ lun: ]<sensor id> | <sensor name> ]
]
gethysteresis [ <addr> -f <fru id> ]
gethysteresis [ <addr> -f amc <amc number> ]
getipmbstate <addr> [<link>]
getlanconfig <channel number> <parameter number> | <parameter
name>
getpefconfig <parameter name> | <parameter number> [<set
selector>]
getsensoreventenable [ <addr> [ [ lun: ]<sensor_id> | <sensor
name> ] ]
getsensoreventenable [ <addr> -f <fru id> ]
getsensoreventenable [ <addr> -f amc <amc number> ]
getthreshold [ <addr> [ [ lun: ]<sensor id> | <sensor name> ]
]
getthreshold [ <addr> -f <fru id> ]
getthreshold [ <addr> -f amc <amc number> ]
help [<command>]
ipmc [-v] [-x] [<addr>]
localaddress
minfanlevel <addr> <fru_id> <min fan level>
minfanlevel [<min fan level>]
46
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
help
poll
quit
sel [clear] [ <addr> [ <number of items> [<number of first
item>] ] ]
sel info [<addr>]
sendamc <addr> <amc> <netfn> <command> [<parameters ...>]
sendcmd <addr> <netfn> <command> [<parameters ...>]
sensor [ <addr> [ [ lun: ]<sensor id> | <sensor name> ] ]
sensor [ <addr> -f <fru id> ]
sensor [ <addr> -f amc <amc number> ]
sensordata [-t] [-d <state>] [ <addr> [ [ lun: ]<sensor id> |
<sensor name> ] ]
sensordata [-t] [-d <state>] [ <addr> -f <fru id> ]
sensordata [-t] [-d <state>] [ <addr> -f amc <amc number> ]
sensorread <addr> [ lun: ]<sensor id>
session
setbootdev <addr> <fru-id | amc-addr> <boot-device>
setcommandpolicy <Enable|Disable> <NetFn> <CMD> [<channel>]
[<LUN>]
setextracted <addr> <fru_id>
setfanlevel <addr> <fru_id> <state>
setfanpolicy <addr> <fru_id> <ENABLE | DISABLE [timeout]> [-s
<addr> | site_type <fru_id> | site_n
umber]
setfruledstate <addr> <fru_id> <LedId> | ALL <LedOp | tail>
[LedColor]
setfunctionpolicy <EnableDisableMask> <NetFn> <CMD>
[<channel>] [<LUN>]
sethysteresis <addr> [ lun: ]<sensor_id> | <sensor name> pos |
neg <value>
setipmbstate <addr> A | B [<link>] 0|1
setlanconfig <channel number> <parameter number> | parameter
name <parameters ...>
setlocked <addr> <fru_id> <value>
setpefconfig <parameter name> | <parameter number> [<set
selector>] <parameters ...>
setpowerlevel <addr> <fru_id> [<pwr_lvl> | OFF] [Copy]
setsensordata <addr> [ lun: ]<sensor_id> | <sensor name> [
reading [-r] <value> ]
[ assertion <mask> ] [ deassertion <mask> ]
[ event_data <b1> <b2> <b3> | event_data_no_offset <b1> <b2>
<b3>]
setsensoreventenable <addr> [ lun: ]<sensor_id> | <sensor
name> global [assertion_events [deassert
ion_events]]
setthreshold <addr> [ lun: ]<sensor_id> | <sensor name> unc |
uc | unr | lnc | lc | lnr [-r] value
shelf <parameters>
shelf address_table
shelf at
shelf board_lan_cfg_params
shelf cooling_state
shelf cs
shelf fans_state
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
47
help
Using the shelf manager CLI
shelf fs
shelf h110_connectivity
shelf h110c
shelf ha_connectivity
shelf hac
shelf pci_connectivity
shelf pcic
shelf point-to-point_connectivity
shelf ppc
shelf power_distribution
shelf pd
shelf power_management
shelf pm
shelf shm_cfg_params
shelfaddress [-x] ["<shelf address>"]
shmstatus
showunhealthy
switchover [-force]
terminate [-reboot]
threshold [ <addr> [ [ lun: ]<sensor id> | <sensor name> ] ]
threshold [ <addr> -f <fru id> ]
threshold [ <addr> -f amc <amc number> ]
user [<user id>]
user add <user id> <user name> <flags> <privilege level>
<password>
user channel <user id> <channel number> <flags> <privilege
level>
user delete <user id>
user enable <user id> 1|0
user name <user id> <user name>
user passwd <user id> <user password>
version
Displaying more information about a command
Enter the following command to display more information about the threshold
command:
# clia help threshold
Pigeon Point Shelf Manager Command Line Interpreter
Shows the threshold of the specified sensor
instead of <addr> user may use:
board <N>
shm <N>
to access the sensor on the specified board
getthreshold board 21 "IPMB LINK"
getthreshold 20 8
threshold [ <addr> [ [ lun: ]<sensor id> | <sensor name> ] ]
Enter the following command to display more information about the fruinfo command:
# clia help fruinfo
Pigeon Point Shelf Manager Command Line Interpreter
48
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
minfanlevel
Display the FRU Info of the dedicated FRU in the readable
format
instead of <addr> <fru_id> user may use:
power_supply <N> (valid in 2.x systems only)
fan_tray <N>
board <N>
shm <N>
to access the FRU on the specified board
fruinfo board 21 8
fruinfo power_supply 4
fruinfo <addr> <fru_id>
minfanlevel
clia minfanlevel [<level>]
This command displays or sets the minimum fan level. Under normal conditions, the
cooling management algorithm gradually decreases the level for the fans in the chassis
while thermal conditions stay normal. The cooling management algorithm will not try to
decrease the fan level below the minimum level specified by the configuration parameter
MIN_FAN_LEVEL or by this command. The minimum fan level affects only the automatic
management of the fan level by the cooling management facility.
Enter the command with no parameters to display the current minimum fan level.
Enter the command with an integer to set the minimum fan level.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
49
sel
Using the shelf manager CLI
sel
clia sel [-v] [<IPMB-address> [<record-count> [starting-entry]]]
clia sel clear [<IPMB-address>]
clia sel info [<IPMB-address>]
The System Event Log (SEL) is useful for troubleshooting as shown in the examples
below.
Note: You can also use the Linux command cat /var/log/messages to view shelf manager system log
messages. This information can be useful for diagnosing system problems. This information can also help
Fortinet Support diagnose shelf manager system problems.
The sel command shows the contents of the SEL on the specified IPM Controller (at
IPMB address 20h by default). The optional <record-count> indicates how many
records from the record number <starting-entry> in the SEL are displayed. The
optional parameter <starting-entry> is the entry number of the first SEL record to
print, relative to the beginning of the SEL. Both <record-count> and <startingentry> must be within the range of 1 to the total number of records in the SEL. The
default value of the optional parameter <starting-entry> is 1. The <startingentry> is independent of the RecordID field of the SEL record.
The command displays the following information fields for each SEL record:
• Record ID
• Record type (currently only events are supported, for which the word “Event” is shown
• Timestamp (for timestamped records)
• Source address parameters: IPMB address, LUN and channel number
• Type and number of the sensor that generated the event
• Event/reading type code
• 3 bytes of event data, in raw and processed (if available) formats.
The command sel clear clears the SEL on the specified IPM Controller (at IPMB
address 20h by default). The -v option makes the command output more user-readable.
The following example messages show that the hot swap state of FRU 0 at address 0x86
(a FortiGate-5000 series board in physical slot 6) has been M7 (communication lost) for 11
seconds. The first message indicates when the board went from the M4 state (active) to
the M7 state (communication lost) and the second message shows when the board went
from the M7 state back to the M4 state.
0x0332: Event: at Aug 5 11:07:18 2009; from:(0x86,0,0);
sensor:(0xf0,0); event:0x6f(asserted): HotSwap: FRU 0 M4>M7, Cause=0x4
0x0333: Event: at Aug 5 11:07:29 2009; from:(0x86,0,0);
sensor:(0xf0,0); event:0x6f(asserted): HotSwap: FRU 0 M7>M4, Cause=0x4
•
from:(0x86,0,0) indicates the event comes from physical slot 6 of a FortiGate
chassis.
•
sensor:(0xf0,0) indicates a hot swap sensor.
The following example messages show that the upper non-critical threshold (0x28 = 40) of
the temperature sensor number 12 on slot 6 has been reached for two seconds.
0x0386: Event: at Aug 5 16:16:12 2009; from:(0x86,0,0);
sensor:(0x01,12); event:0x1(asserted): "Upper Non-Critical",
Threshold: 0x28, Reading: 0x28
50
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
sensor
0x0387: Event: at Aug 5 16:16:14 2009; from:(0x86,0,0);
sensor:(0x01,12); event:0x1(deasserted): "Upper NonCritical", Threshold: 0x28, Reading: 0x27
You can use the threshold command (see “getthreshold/threshold” on page 41) to
check the threshold values of these sensors.
# clia threshold 86 12
Pigeon Point Shelf Manager Command Line Interpreter
86: LUN: 0, Sensor # 12 ("TEMP1")
Type: Threshold (0x01), "Temperature" (0x01)
Upper Non-Critical Threshold, Raw Data: 0x28 Processed data:
40.000000 degrees C
Upper Critical Threshold, Raw Data: 0x32 Processed data:
50.000000 degrees C
Upper Non-Recoverable Threshold, Raw Data: 0x3c Processed
data: 60.000000 degrees C
The first two SEL lines below indicate a problem (last hex number is not 0x88) for the
IPMB link (sensor F1) on slot 9 and 10. The problem has cleared quickly because the last
two lines show last hex number is 0x88.
0x0219: Event: at Aug 6 10:39:54 2009; from:(0x88,0,0);
sensor:(0xf1,1); event:0x6f(asserted): 0xA2 0x00 0x89
0x021A: Event: at Aug 6 10:39:55 2009; from:(0x8c,0,0);
sensor:(0xf1,1); event:0x6f(asserted): 0xA2 0x00 0x8F
0x021C: Event: at Aug 6 10:39:55 2009; from:(0x88,0,0);
sensor:(0xf1,1); event:0x6f(asserted): 0xA3 0x00 0x88
0x021E: Event: at Aug 6 10:39:56 2009; from:(0x88,0,0);
sensor:(0xf1,1); event:0x6f(asserted): 0xA3 0x00 0x88
sensor
clia sensor [-v] [<IPMB-address> [<sensor-name> |
[<lun>:]<sensor-number>]]
This command displays information about specific sensor(s). The target sensor is selected
by its IPM controller’s IPMB address and by sensor number or by sensor name. If neither
sensor name nor sensor number is specified, information about all sensors on the
specified IPM controller is displayed. If no parameters are specified, information about all
known sensors is displayed.
The following information is shown for each sensor in standard mode (non verbose mode):
•
IPMB address of the owning IPM controller
•
Sensor number, sensor name (device ID string from the Sensor Data Records (SDRs))
and the LUN by which the sensor can be accessed
•
The sensor type and event/reading type code
•
The Entity ID, Entity Instance of the related entity (the FRU device ID if the sensor is
associated with a FRU)
Example for slot 11 and sensor 13:
# clia sensor 88 13
Pigeon Point Shelf Manager Command Line Interpreter
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
51
sensordata
Using the shelf manager CLI
88: LUN: 0, Sensor # 13 ("CPU Board Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0x3, 96) [FRU # 0]
# clia sensor 88 "CPU Board Temp"
Pigeon Point Shelf Manager Command Line Interpreter
88: LUN: 0, Sensor # 13 ("CPU Board Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0x3, 96) [FRU # 0]
sensordata
clia sensordata [-v] [-t] [<IPMB-address> [<sensor-name> |
[<lun>:]<sensor-number>]]
This command displays the actual value of the specified sensor or sensors (for a threshold
based sensor) or the currently asserted states (for a discrete sensor). The target sensor is
selected by entering the IPM controller’s IPMB address and the sensor number or the
sensor name. If you do not include the sensor name or number, the command displays the
values of all sensors on the specified IPM controller. If you do not enter any parameters,
the command displays values of all known sensors.
The following information is displayed for each sensor:
•
IPMB address of the owning IPM controller.
•
Sensor number, sensor name (device ID string from the SDR) and the LUN by which
the sensor can be accessed.
•
The sensor type and event/reading type code.
•
The sensor value (for threshold-based sensors) or the mask of currently asserted
states (for discrete sensors) in raw form.
•
The threshold crossing status, in hexadecimal format and with decoding.
Use the -t to displayed information only for threshold-based sensors, that have at least
one of their thresholds crossed.
Example for physical slot 4 (logical slot 4 and IPMB address 88) and sensor 13, a
temperature sensor:
# clia sensordata 88 13
Pigeon Point Shelf Manager Command Line Interpreter
88: LUN: 0, Sensor # 13 ("CPU Board Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Status: 0xc0
All event messages enabled from this sensor
Sensor scanning enabled
Initial update completed
Raw data: 44 (0x2c)
Processed data: 44.000000 degrees C
Status: 0x00
52
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
setthreshold
setthreshold
setthreshold <IPMB-address> <sensor-name> <threshold-type> [-r]
<value>
setthreshold <IPMB-address> [<lun>:]<sensor-number> <thresholdtype> [-r] <value>
Where <IPMB-address> can be board <board-number> or shm <shelfmanager-number>.
<threshold-type> can be:
•
upper_non_recoverable (can be abbreviated to unr)
•
upper_critical (can be abbreviated to uc)
•
upper_non_critical (can be abbreviated to unc)
•
lower_non_recoverable (can be abbreviated to lnr)
•
lower_critical (can be abbreviated to lc)
•
lower_non_critical (can be abbreviated to lnc)
By default, the target value is specified in real units (for example, in Volts for voltage
sensors or in Celsius degrees for temperature sensors). Option –r means that a raw value
is used instead (usually a byte-size quantity, converted according to sensor-specific rules).
Using this command you can qualify the sensor number with the logical unit number (LUN)
if the target controller supports sensors on multiple LUNs. <lun> can take the value 0, 1
or 3. (LUN 2 is reserved.) If the LUN is omitted, the command applies to the sensor with
the specified sensor number on the lowest LUN. (For example, if the command specifies
sensor 3 without explicit LUN qualification, and the target controller exposes sensor 3 on
LUN 1 and another sensor 3 on LUN 3, the command is applied to the sensor 3 on LUN
1.)
This command can also be issued on the backup Shelf Manager; in that case, threshold
values can only be set for sensors that are local to the backup Shelf Manager.
Use the following example to set the upper non-critical threshold value for the temperature
sensor “emulated temp” on IPM controller 88 to 99 degrees Celsius.
# clia threshold 88 2
Pigeon Point Shelf Manager Command Line Interpreter
88: LUN: 0, Sensor # 2 ("emulated temp")
Type: Threshold (0x01), "Temperature" (0x01)
Lower Non-Critical Threshold, Raw Data: 0x03, Processed Data:
3.000000 degrees C
Lower Critical Threshold, Raw Data: 0x14, Processed Data:
20.000000 degrees C
Lower Non-Recoverable Threshold, Raw Data: 0xfb, Processed
Data: -5.000000 degrees C
Upper Non-Critical Threshold, Raw Data: 0x46, Processed Data:
70.000000 degrees C
Upper Critical Threshold, Raw Data: 0x50, Processed Data:
80.000000 degrees C
Upper Non-Recoverable Threshold, Raw Data: 0x5a, Processed
Data: 90.000000 degrees C
# clia setthreshold 88 0:2 unc 99
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
53
shmstatus
Using the shelf manager CLI
Pigeon Point Shelf Manager Command Line Interpreter
Threshold set successfully
# clia threshold 88 0:2
Pigeon Point Shelf Manager Command Line Interpreter
88: LUN: 0, Sensor # 2 ("emulated temp")
Type: Threshold (0x01), "Temperature" (0x01)
Lower Non-Critical Threshold, Raw Data: 0x03, Processed Data:
3.000000 degrees C
Lower Critical Threshold, Raw Data: 0x14, Processed Data:
20.000000 degrees C
Lower Non-Recoverable Threshold, Raw Data: 0xfb, Processed
Data: -5.000000 degrees C
Upper Non-Critical Threshold, Raw Data: 0x63, Processed Data:
99.000000 degrees C
Upper Critical Threshold, Raw Data: 0x50, Processed Data:
80.000000 degrees C
Upper Non-Recoverable Threshold, Raw Data: 0x5a, Processed
Data: 90.000000 degrees C
shmstatus
clia shmstatus [-v]
This command displays the Shelf Manager status in redundant configurations: Active or
Backup. In verbose mode (using -v) the command displays more information including
the status of the Shelf FRU Info, status of the Remote Management Control Protocol
(RMCP) interface, and state of the backup Shelf Manager (if the Shelf Manager being
queried is the active one).
The command output includes a Ready For Operation flag that shows Yes:
•
For the active Shelf Manager if the active shelf manger finds valid shelf FRU
information and successfully initializes its RMCP interface.
•
For the backup Shelf Manager if the backup shelf manager successfully receives
redundancy state information from the active Shelf Manager.
Example verbose mode output for an active shelf manager:
# clia shmstatus -v
Pigeon Point Shelf Manager Command Line Interpreter
Host: "Active"
Ready For Operation: Yes
Detailed State Flags: "Shelf FRU Found" "Backup Healthy" "Initial
Update Sent" "RMCP Up"
54
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
showunhealthy
showunhealthy
clia showunhealthy
This command displays the list of FRUs that appear to have a problem. In the PICMG 3.0
context, problems are defined as FRUs for which the cause of the last hot swap state
change is one of the following:
• Communication Lost
• Communication lost due to local failure
• Unexpected deactivation
If no FRUs have a problem, the command displays
There are no unhealthy components in the shelf.
The following information is shown for each FRU considered to have a problem:
•
IPMB address and FRU device ID
•
Current Hot Swap state
•
Previous hot swap state
•
Cause of the last state change.
switchover
clia switchover [-force]
If a chassis has two shelf managers, you can enter this command to switch the active
shelf manager to running as the backup shelf manager and the backup shelf manager to
switch to running as the active shelf manager. You can enter this command from the active
or backup shelf manger. When you enter the command the shelf managers negotiate a
smooth switchover.
If you enter this command from the backup shelf manager you can include -force to
force the switchover without any negotiation. The backup shelf manager immediately
becomes the active shelf manager and the active shelf manager reboots and starts up as
the backup shelf manager.
terminate
clia terminate [-reboot]
This command terminates the Shelf Manager. If you include -reboot the ShMM
unconditionally reboots. If you do not include -reboot, the command terminates the
Shelf Manager without rebooting the ShMM.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
55
user
Using the shelf manager CLI
user
clia user [add | delete | enable | name | passwd | channel]
clia user [-v] [<user_id>]
Use this command to add, delete, modify and display RMCP user accounts for a shelf
manager.
Display all user accounts
Enter the following command to display user account information:
clia user -v
Pigeon Point Shelf Manager Command Line Interpreter
1: ""
Channels 0-15 Privilege level: "Administrator"
Flags: "IPMI Messaging"
7: "TEST1" Disabled
Channels 0-15 Privilege level: "NO ACCESS"
Include -v to display disabled user accounts. For each user account the command
displays:
• User ID
• User name
• Channel access information for each IPMI channel: the maximum privilege level of that
user account on that channel, and channel access flags. If the channel access
information is the same for several channels, the output displays the information for the
channel number range.
Adding a user account
Use the following command syntax to add a user account:
user add <user_id> <user_name> <channel_access_flags>
<privilege_level> <password>
This command adds a new RMCP user account to the shelf manager. The command also
sets the same maximum privilege level and channel access flags for all channels. Where:
•
<user_id> is a valid user ID
•
<user_name> is a user name (truncated to the 16 characters without notice)
•
<channel_access_flags> is the first byte of the SetUserInfo commands (only bits
4,5,6 are meaningful)
•
bit 6 enables IPMI messaging
•
bit 5 enables link authentication
•
bit 4 restricts the user to callback
•
<privilege_level> is the user account privilege level
•
<password> is the user account password (truncated to the 16 characters without
notice).
For example, add a user account with user ID 9, user name user_1, administrator
privilege level, and password my-password.
clia user
56
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
user
Pigeon Point Shelf Manager Command Line Interpreter
1: ""
Channels 0-15 Privilege level: "Administrator"
Flags: "IPMI Messaging"
clia user add 9 "user_1" 0x40 4 "my-password"
Pigeon Point Shelf Manager Command Line Interpreter
User 9 added successfuly
clia user
Pigeon Point Shelf Manager Command Line Interpreter
1: ""
Channels 0-15 Privilege level: "Administrator"
Flags: "IPMI Messaging"
9: "user_1"
Channels 0-15 Privilege level: "Administrator"
Flags: "IPMI Messaging"
Deleting user accounts
Use the following command syntax to delete user accounts:
clia user delete <user_id>
For example, enter the following command to delete user account 23:
clia user delete 23
Disabling and enabling user accounts
Use the following command syntax to disable and enable user accounts.
clia user enable <user_id> {1 | 0}
Where 1 enables the user account and 2 disables the user account.
User accounts are enabled when you add them. You can use the command clia user
-v to display enabled user accounts. When you use the clia user-v command to
display user accounts, entries for disabled user accounts include Disabled. If you don’t
include -v the command only displays enabled user accounts.
For example, enter the following command to disable user account 34:
clia user enable 34 0
Changing a user account user name
Use the following command syntax to change a user account user name:
clia user name <user_id> <new_user_name>
Where <user_id> is the user account user ID and <new_user_name> is the new user
name.
For example, enter the following command to change the user name of user account 2 to
new-name:
clia user name 2 new-name
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
57
version
Using the shelf manager CLI
Changing a user account password
Use the following command syntax to change a user account password:
clia user passwd <user_id> <new_password>
Where <user_id> is the user account ID and <new_password> is the new password.
For example, enter the following command to change the user name of user account 6 to
NEW-password:
clia user password 6 NEW-password
version
clia version
This command displays version information for the Shelf Manager software.
# clia version
Pigeon Point Shelf Manager Command Line Interpreter
Pigeon Point Shelf Manager ver. 2.6.4.4
Pigeon Point and the stylized lighthouse logo are trademarks of
Pigeon Point Systems
Copyright (c) 2002-2009 Pigeon Point Systems
All rights reserved
Build date/time: Dec 14 2009 10:09:35
Carrier: HPDL/ACB
Carrier subtype : 0; subversion: 0
Cooling Management Library: libcooling_acb.so; Version: 2.6.4.4
Carrier Product ID: 21990047
#
Generating SNMP traps for system events
This section describes how to configure the shelf manager to send SNMP traps when a
component of a chassis or a board in a chassis fails or encounters a problem (for
example, a temperature sensor exceeds its range). This section describes how to
configure the shelf manager to send traps when a chassis FRU changes its FRU state.
FRU state changes are listed in Table 10 on page 36.
This section describes how to configure a FortiGate-5000 series chassis shelf manager to
send SNMP traps to an SNMP manager. The shelf manger IP address is 172.20.120.150
and the SNMP manager IP address is 172.20.120.11. The SNMP manager does not
require MIBs or any special configuration to receive traps from the shelf manager.
58
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Generating SNMP traps for system events
Figure 11: Example SNMP network configuration
FortiGate-5000
F
iG
000 series
i
Chassis
Shelf Manager
IP: 172.20.120.150
SNMP Manager
IP: 172.20.120.11
MAC: 00:1A:A0:2F:BC:C6
For this example, the FortiGate-5000 series chassis is a FortiGate-5140 chassis with a
FortiSwitch-5003A board in logical slot 1, FortiGate-5005FA2 boards in logical slots 6, 8,
10, and 11. The same settings will work for a FortiGate-5050 or FortiGate-5060 chassis
after making adjustments for the slot numbers.
To configure the shelf manager to send SNMP traps you must configure shelf manager
Platform Event Filtering (PEF) to provide a mechanism for sending SNMP traps. To
configure PEF you add an event filter table that sets the events that trigger an action and
the action to take. The events can be a FRU state change or a sensor alert. The action to
take is to send an SNMP trap to the SNMP server.
When PEF triggers an alert, the shelf manager uses an Alert Policy to determine the
action to take. An alert policy is a collection of one or more alert destinations. You can
create multiple alert policies and configure multiple destinations for each policy. This
section describes how to create one alert policy, called alert policy number 5. The alert
policy number is used in an Event Filter Entry to select the alert policy to use when an alert
filter matches an event.
The combination of event filter entry and alert destination are used to select a given Alert
String from a set of strings kept in the PEF configuration parameters. This enables
different strings to be sent based on what event filter was matched and where the alert is
being sent.
This example configuration of an Event filter table, Alert Policy table and Alert String table
sends alerts following FRU state changes. The alerts which will be sent from the shelf
manager will be SNMP traps whose format is defined in the Platform Event Trap Format
specification. The example is for alert channel 1 which is the Eth0 interface of shelf
manager number 1.
The basic requirements for configuring SNMP traps are the same for all shelf manager
firmware versions. However, some more recent versions of the shelf manager firmware
support more options (for example, you can set the Platform Event Trap Format to
different levels only on some shelf manager firmware releases).
To configure the shelf manager LAN alert destination
1 Log into the shelf manager CLI using the procedure described in “Connecting to the
shelf manager CLI using a serial port” on page 27. You can also connect to the CLI
using Telnet.
2 Set alert type for channel 1 and destination number 2. This command sets the alert
type to 0 0 0 which means an unacknowledged PET trap, with 0 timeout and 0 retry
count:
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
59
Generating SNMP traps for system events
Using the shelf manager CLI
# clia setlanconfig 1 destination_type 2 0 0 0
3 Set the destination IP and MAC address, which is the IP and MAC address of the
SNMP server. The SNMP server can be on a different subnet.
# clia setlanconfig 1 destination_address 172.20.120.11
00:1A:A0:2F:BC:C6
4 Set the community name used in PET traps. This can be any community name, the
default is public.
# clia setlanconfig 1 community “<community_name>”
To configure the PEF event filter table
1 Enable PEF and enter a PEF control flag:
# clia setpefconfig control f
This command sets an 8-bit value, entered in hexadecimal and treated as a bit mask,
that represents control flags for PEF. The control value f enables PEF, enable the
generation of event messages for PEF actions, enables startup delays and enables
alert startup delays.
2 Enable alert actions:
# clia setpefconfig action_control 1
An 8-bit value entered in hexadecimal and treated as a bit mask. Setting
action_control to 1 enables alert actions.
3 Delay PEF and delay alerts for 60 seconds after the system powers up:
# clia setpefconfig startup_delay 60
# clia setpefconfig alert_startup_delay 60
4 Add event filter entries. The syntax of the command is:
# clia setpefconfig event_filter <entry_number>
<flter_configuration> <filter_action> <alert_policy_number>
<severity> <IPMB_address> <channel> <sensor_type>
<sensor_number> <event_type> <event_offset> 0 0 0 0 0 0 0 0 0
Each even filter command adds or edits and event filter table entry. Each entry consists
of a <entry_number> and a <filter_action> followed by 19 numeric values, in
hexadecimal, encoded according to the definition in table 15-2 of the IPMI specification
version 1.5 (http://download.intel.com/design/servers/ipmi/IPMIv1_5rev1_1.pdf).
<entry_number> is the filter entry number. Each entry must have a different number.
Adding a second entry with the same number overwrites the first entry with that
number.
<filter_configuration>. In this example the filter configuration is ways set to 80
to enable the filter.
<filter_action>. In this example the filter action is ways set to 1 to set the action
to alert.
<alert_policy_number>. In this example the alert policy number is 5.
<severity>. In this example the severity is 02 which means information level
messages and higher can trigger traps. Normally you would set severity to 08 for noncritical conditions, 10 for critical conditions, or 20 for non-recoverable conditions to limit
the number of traps sent.
<IPMB_address> is the IPMB address of the FRU for which the alert is generated.
See “IPMB addresses, logical and physical slot numbers, and FRU ids” on page 30.
<channel> is the channel to match. FF means any channel.
60
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Generating SNMP traps for system events
<sensor_type> is the type of sensor. FF means any sensor, F0 means hot swap.
See “Sensor types” on page 33.
<sensor_number> is the number of the sensor. FF means any sensor.
<event_type> is the event or reading type. FF means any event type.
<event_offset> is the event offset mask. FF FF means any event offset mask.
0 0 0 0 0 0 0 0 0 are additional settings to add granularity and boolean logic for
selecting particluar events. In this example they are all set to 0 which means they have
no effect.
Example filter entries for a FortiGate-5000-series chassis with a FortiSwitch-5003A
board in logical slot 1 and a FortiGate-5005FA2 board in logical slot 5. The example
also includes an event filter for FRUs at IPMB address 20 (PEMs, Fans, etc). For
clarity the filter entry numbers match the IPMB numbers, but this is not a requirement.
These filter entries set the alert level to 02 which means SNMP traps are generated for
all events. You could raise the alert levels to 10 to only receive traps for critical events.
Add filter entry 1 for the FortiSwitch-5003A board in logical slot 1. The filter entry uses
filter configuration 80, sets the action to alert (1), references alert policy 5, sets the
severity level to 02, is for IPMB address 82 (the first hub slot), any channel (FF), is for
the hot swap sensor (F0), is for any sensor number (FF), any sensor offset (FF), any
event type (FF), and any event offset (FF).
clia setpefconfig event_filter 1 80 1 5 02 82 FF F0 FF FF FF FF
0 0 0 0 0 0 0 0 0
Add filter entry 20 for the FRUs at IPMB address 20 (PEMs, Fans, etc)
clia setpefconfig event_filter 20 80 1 5 02 20 FF FF FF FF FF
FF 0 0 0 0 0 0 0 0 0
To configure the alert policy and string tables
1 Set alert policy table entry 8 with alert policy number 5, policy enabled, alert always
sent, destination channel 1, destination address 2 and alert string selector 7
clia setpefconfig alert_policy 8 5 8 1 2 7
2 Set the alert string selector 7 equal to test alert message.
clia setpefconfig alert_string 7 “test alert message”
Testing the configuration
A simple test of the configuration to make sure the SNMP manager can receive traps.
Since in most cases in this example the event filter is set for any channel and any sensor
any simple state change should trigger a trap. The following steps show to enter a
command to deactivate selected FRUs which will result in a trap being sent.
Note: The format of SNMP traps produced by the shelf manager is specified in the IPMI
Platform Event Trap Format Specification v1.0 document
(http://download.intel.com/design/servers/ipmi/PET100.pdf).
1 Enter the following command to view the state of PEM 1 in a FortiGate-5000 series
chassis.
# clia fru 20 7
20: FRU # 7
Entity: (0xa, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change
Cause: Normal State Change (0x0)
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
61
Generating SNMP traps for system events
Using the shelf manager CLI
Device ID String: "PEM B"
2 Enter the following command to deactivate this PEM:
# clia deactivate 20 7
3 Enter the following command to display the system event log.
# clia sel
0x0001: Event: at Jul 8 17:12:21 2008; from:(0x20,0,0);
sensor:(0xf0,9);
event:0x6f(asserted): HotSwap: FRU 7 M4->M6, Cause=0x1
0x0002: Event: at Jul 8 17:12:21 2008; from:(0x20,0,0);
sensor:(0x12,133);
event:0x6f(asserted): 0xC4 0x01 0x00
0x0003: Event: at Jul 8 17:12:21 2008; from:(0x20,0,0);
sensor:(0xf0,9);
event:0x6f(asserted): HotSwap: FRU 7 M6->M1, Cause=0x0
0x0004: Event: at Jul 8 17:12:21 2008; from:(0x20,0,0);
sensor:(0x12,133);
event:0x6f(asserted): 0xC4 0x01 0x00
The event log shows two state changes: M4 -> M6 -> M1 Two SNMP traps are
generated.
4 Enter the following command to re-activate this PEM:
# clia activate 20 7
When activating again the PEM B, there are three state changes (M1 -> M2 -> M3 > M4) and three traps sent.
SNMP trap details
The trap below could be sent when PEM B state changes from M4 to M6. The important
trap fields are the specific trap field (in red below) and the variable bindings fields (in blue).
Byte 2 of the specific trap field shows the sensor type (f0 = hot swap) and the 4th byte is
the event offset (06 = assertion to state 6= M6).
The variable bindings fields which are in bold in the trace below are the following bytes:
•
Byte 26 = Event Source Type = Class of device or type of software that originated the
event
•
Byte 27 = Event Severity
•
Byte 28 = Sensor Device byte = Identifies the instance of the device that holds the
sensor that generated the event
•
Byte 29 = Sensor Number
Sensor number 9 is the hot swap sensor for PEM B:
# clia sensor 20 9
20: LUN: 0, Sensor # 9 ("FRU 7 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0xa, 97) [FRU # 7]
No. Time
Source
Destination
Protocol
Info
1
17:11:21.469567 192.168.181.66 192.168.182.86 SNMP
trap
Frame 1 (177 bytes on wire, 177 bytes captured)
Ethernet II, Src: RapidCit_5f:cc:97 (00:e0:16:5f:cc:97), Dst:
Vmware_3c:55:c0 (00:0c:29:3c:55:c0)
62
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Generating SNMP traps for system events
Destination: Vmware_3c:55:c0 (00:0c:29:3c:55:c0)
Source: RapidCit_5f:cc:97 (00:e0:16:5f:cc:97)
Type: IP (0x0800)
Internet Protocol, Src: 192.168.181.66 (192.168.181.66), Dst:
192.168.182.86 (192.168.182.86)
User Datagram Protocol, Src Port: 1024 (1024), Dst Port:
snmptrap (162)
Simple Network Management Protocol
version: version-1 (0)
community: public
data: trap (4)
trap
enterprise: 1.3.6.1.4.1.3183.1.1 (SNMPv2SMI::enterprises.3183.1.1)
agent-addr: internet (0)
internet: 192.168.181.66 (192.168.181.66)
generic-trap: enterpriseSpecific (6)
specific-trap: 15757062
time-stamp: 1975765011
variable-bindings: 1 item
Item
name: 1.3.6.1.4.1.3183.1.1.1 (SNMPv2SMI::enterprises.3183.1.1.1)
valueType: value (0)
value: simple (4294967295)
simple: string-value (1)
Value: Hex-STRING: 54 FA FC B6 41 50 11 DD 00 80 00
50 C2 3F F0 9A 00 4F 13 C8 C3 75 00 00 20 20 02
20 09 00 00 A6 14 07 00 00 00 00 00 19 0A 40 00
00 00 00 80 53 01 74 65 73 74 20 61 6C 65 72 74
20 6D 65 73 73 61 67 65 00 C1
Packet bytes :
0000 00 0c 29 3c 55 c0 00 e0 16 5f cc 97 08 00 45 00
..)<U...._....E.
0010 00 a3 00 00 40 00 3e 11 4f 60 c0 a8 b5 42 c0 a8
....@.>.O`...B..
0020 b6 56 04 00 00 a2 00 8f 6a 28 30 81 84 02 01 00
.V......j(0.....
0030 04 06 70 75 62 6c 69 63 a4 77 06 09 2b 06 01 04
..public.w..+...
0040 01 98 6f 01 01 40 04 c0 a8 b5 42 02 01 06 02 04
..o..@....B.....
0050 00 f0 6f 06 43 04 75 c3 c8 13 30 55 30 53 06 0a
..o.C.u...0U0S..
0060 2b 06 01 04 01 98 6f 01 01 01 04 45 54 fa fc b6
+.....o....ET...
0070 41 50 11 dd 00 80 00 50 c2 3f f0 9a 00 4f 13 c8
AP.....P.?...O..
0080 c3 75 00 00 20 20 02 20 09 00 00 a6 14 07 00 00 .u.. .
........
0090 00 00 00 19 0a 40 00 00 00 00 80 53 01 74 65 73
.....@.....S.tes
00a0 74 20 61 6c 65 72 74 20 6d 65 73 73 61 67 65 00 t alert
message.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
63
Using the chassis system event log (SEL)
Using the shelf manager CLI
00b0 c1
Some releases of the Shelf Manager allow selecting between three PET formats. The
values are defined as follows:
0 = the default IPMI format defined by IPMI Platform Event Trap Format v1.0
specification.
1 = plain text format; all the event details are sent as plain ASCII text in a single
variable.
2 = multi-variable format; each event field is encoded as a separate variable
Removing and inserting a fan tray
You could also test traps by removing and then inserting fan tray 1. When removed, it
caused a state change (M4 -> M7) and a SNMP trap sent with byte 4 of specific trap field
= 07. Byte 29 of variable binding fields was equal to 06 = FRU 4 hot swap sensor.
# clia fru 20 4
20: FRU # 4
Entity: (0x1e, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change
Cause: Normal State Change (0x0)
Device ID String: "Fan Tray 1"
# clia sensor 20 6
20: LUN: 0, Sensor # 6 ("FRU 4 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0x1e, 97) [FRU # 4]
When inserted, there are 4 state changes and 4 SNMP traps sent.
Using the chassis system event log (SEL)
This section document describes the components that make up a FortiGate-5000-series
chassis, describes how to read the system event logs stored on the shelf manager and
record all system events. For more information about the SEL, see “sel” on page 50.
Before you begin
Before going further in this section, you should log into your active shelf manager and
enter the following commands. This will be a good reference for what you physically have
in your system and will help with understanding other areas of this section.
# clia ipmc
# clia fru
# clia sensor
# clia sel
See “Example IPMC log output” on page 67, “Example FRU log output” on page 68 and
“Example sensor log output” on page 69.
Chassis Design Background
All the devices in an ATCA chassis are controlled and monitored through an IPMC. Each
shelf manager and all ATCA boards have their own physical IPMC chip and are assigned
an IPMC address. Their unique address is assigned based on what chassis slot they are
physically inserted into. Additionally, there is a reserved logical chassis IPMC address of
20 hex which is created and controlled by the active shelf manager.
64
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Using the chassis system event log (SEL)
•
Shelf Manager slot 1 = IPMC address 10 hex
•
Shelf Manager slot 2 = IPMC address 12 hex
•
ATCA slot 1 = IPMC address 82 hex
•
ATCA slot 14 = IPMC address 9C hex
•
Logical IPMC from Active Shelf Manager = IPMC address 20 hex
The IPMC connects to and monitors the readings on various sensors located on devices in
the system. These devices are typically called FRUs. The term FRU generally refers to
any removable or field replaceable component, but in a more technical view can be any
unique device in the system even if it is not removable, such as a backplane.
•
FortiGate-5001A in ATCA slot 1 = (IPMC 82) FRU 0
•
Shelf Manager in SM slot 1 = (IPMC 10) FRU 0
•
Shelf Manager in SM slot 2 = (IPMC 12) FRU 0
All the other FRU devices that make up a chassis are referenced through the logical IPMC
address 20.
•
SAP (Shelf Alarm Panel) = (IPMC 20) FRU 8
•
Fan tray 1 = (IPMC 20) FRU 4
•
Fan tray 2 = (IPMC 20) FRU 5
•
PEM A (Power Entry Module A) = (IPMC 20) FRU 6
See “IPMB addresses, logical and physical slot numbers, and FRU ids” on page 30 for a
complete list.
The sensors on the various FRUs report back to their respective IPMC. Sensors
connected to chassis FRU devices like the fan trays or power entry modules can report
back their sensor readings through either IPMC 10h/12h or through the Logical 20h
address, but not both. Sensors on ATCA boards always report back through their
respective blade IPMC address.
•
Backup battery voltage sensor on SM1 = (IPMC 10) Sensor #6
•
RPM of fan 1 of 2 in Fan Tray 0 = (IPMC 10) Sensor #7
•
RPM of fan 2 of 2 in Fan Tray 2 = (IPMC 10) Sensor #14
•
Physical presence of Fan Tray 2 = (IPMC 20) Sensor #14
•
Chassis center exhaust temperature = (IPMC 20) sensor #120
•
Slot 1 FG-5005FA2 ambient incoming temp = (IPMC 82) Sensor #12
You can check the IPMB bus state (if the bus it in failure, nothing works). A backup bus
exists so there are 2 IPMB buses handled by the active shelf manager (and not one bus
per shelf manager). Use the following command to check the IPMB bus state:
# clia getipmbstate 10
Pigeon Point Shelf Manager Command Line Interpreter
10: Link: 0, LUN: 0, Sensor # 1 ("IPMB LINK")
Bus Status: 0x8 (IPMB-A Enabled, IPMB-B Enabled)
IPMB A State: 0x08 (LocalControl, No failure)
IPMB B State: 0x08 (LocalControl, No failure)
Alarm LEDs
Alarms are also reported by LEDs on the chassis shelf alarm panel or shelf manager.
FRUs such as fan trays and PEMs also have alarm LEDs. So for example, if a FAN goes
into an alarm state, the alarm LED located on the FAN turns to RED.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
65
Using the chassis system event log (SEL)
Using the shelf manager CLI
For information about shelf alarm panel LEDs see, “FortiGate-5060 shelf alarm panel” on
page 12. For information about cooling fan tray LEDs see “Cooling fan trays” on page 16.
For information about PEM LEDs, see “Connecting a FortiGate-5060 PEM to DC power”
on page 18.
Reading the System Event Log (SEL)
Every time an event occurs in a chassis, the respective IPMC controller sends notification
to the shelf manager that the event has happened and an entry is added to the SEL. The
log entry that is created depends on the sensor that triggered the event and the type of
data that the sensor reads.
All events are logged, this includes normal system events as well as alarms and critical
events. For example, insertion a board generate a number of event log messages
because the board is now present, has notified the shelf manager that it’s ready to work,
that it’s received the command to power up into operational mode, and that it’s now active
in the chassis. This is seen as clustered entries in the SEL where the same IPMC moves
from M0-M1 all the way up to M3-M4, where M4 is fully operating.
Alarm events such as fans starting to spin at slower rates due to age, or dips in the 48VDC power input or even blown fuses are also added to the SEL.
The following example event log entry records that the rear fan in Fan Tray 1 (middle fan
tray) is spinning below the required RPM rate.
0x018D: Event: at Jan 1 00:02:15 1970; from:(0x10,0,0);
sensor:(0x04,10); event:0x1(asserted): "Upper Critical",
Threshold: 0xff, Reading: 0xff
Where:
0x018D The event ID, every new event increments by 1h. So the next event in the log
file will be tagged with 0x018E. You can use this to keep track of what line you are on
in the file.
Event: at Jan
1 00:02:15 1970; The date and time that the event occurred.
from:(0x10,0,0); In this string, 0x10 is the IPMC controller to which the sensor is
attached. In this message its referencing an event monitored by the shelf manager in
slot #1.
sensor:(0x04,10); The first part 0x04 can be ignored, the 10 shows the ID of the
Sensor that generated the alarm.
event:0x1(asserted): Sensors show when an event is triggered because of
something going wrong, but also when they return to normal. In this case, asserted is
the key point, meaning that the sensor has observed that the device has gone outside
the bounds or thresholds that have been set for it. Had this contained deasserted it
would mean the device has returned to its normal operating mode.
Upper Critical", Threshold: ss a reference to the specific threshold level that
the device exceeded. Some events like thermal events could have multiple threshold
levels. The first event could simply notify the shelf manager that it’s getting too hot, to
which the shelf manager would then notify the fans in the system to speed up to help
cool the board better, at which point the sensor would deassert the event. Another,
higher level thermal event could notify the shelf manager that the board has now
exceeded its maximum thermal operating limit, to which the shelf manager would tell it
to deactivate and shut down.
Reading: 0xff represents a raw value sent with the event, typically for more
technical troubleshooting review by the manufacturer. Data is rarely published for
these values.
66
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Using the chassis system event log (SEL)
Reviewing the SEL messages from the IPMC, FRU and Sensor commands will show you
exactly what devices are in your chassis, what the FRU IDs are for the devices that
connect to them, and all the sensor numbers that each of these devices contain. You
should be able to no identify the vast majority of both good and bad events that have
happened to your chassis and blades.
For more advanced users you can try using “–v” after many of the Shelf Manager
commands or running the “Sensordata”, “Threshold”, and “Fruinfo” commands to get more
detailed information on each sensor and FRU device.
Clearing SEL logs
Use the following command to clear SEL logs:
# clia sel clear
Example IPMC log output
# clia IPMC
Pigeon Point Shelf Manager Command Line Interpreter
10: Entity: (0xf0, 0x60) Maximum FRU device ID: 0x08
PICMG Version 2.2
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
20: Entity: (0xf0, 0x1) Maximum FRU device ID: 0x10
PICMG Version 2.2
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
82: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
84: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
86: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
88: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
8a: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M6
(Deactivation In Progress), Last State Change Cause: Unknown
(0xf)
8c: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
67
Using the chassis system event log (SEL)
Using the shelf manager CLI
8e: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
90: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
94: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M5
(Deactivation Request), Last State Change Cause: Unknown
(0xf)
9a: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M5
(Deactivation Request), Last State Change Cause: Unknown
(0xf)
9c: Entity: (0xa0, 0x60) Maximum FRU device ID: 0x00
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
Example FRU log output
# clia fru
Pigeon Point Shelf Manager Command Line Interpreter
10: FRU # 0
Entity: (0xf0, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "ShMM-300"
20: FRU # 0
Entity: (0xf0, 0x1)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "PPS BMC"
20: FRU # 1
Entity: (0xf2, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "Shelf EEPROM 1"
20: FRU # 2
Entity: (0xf2, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "Shelf EEPROM 2"
20: FRU # 3
68
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Using the chassis system event log (SEL)
Entity: (0x1e, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "Fan Tray 0"
20: FRU # 4
Entity: (0x1e, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "Fan Tray 1"
20: FRU # 5
Entity: (0x1e, 0x62)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "Fan Tray 2"
20: FRU # 6
Entity: (0xa, 0x60)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "PEM A"
20: FRU # 7
Entity: (0xa, 0x61)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "PEM B"
20: FRU # 8
Entity: (0x7, 0x6f)
Hot Swap State: M4 (Active), Previous: M3 (Activation In
Process), Last State Change Cause: Normal State Change (0x0)
Device ID String: "SAP Board"
82: FRU # 0
Entity: (0xa0, 0x60)
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
Device ID String: "FS-5003A"
82: FRU # 1
Entity: (0xf2, 0x60)
Hot Swap State: M7 (Communication Lost), Previous: M4
(Active), Last State Change Cause: Unknown (0xf)
Device ID String: "BMR-H8S Shelf FR"
Example sensor log output
# clia sensor
Pigeon Point Shelf Manager Command Line Interpreter
10: LUN: 0, Sensor # 0 ("FRU 0 HOT_SWAP")
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
69
Using the chassis system event log (SEL)
Using the shelf manager CLI
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 1 ("IPMB LINK")
Type: Discrete (0x6f), "IPMB Link" (0xf1)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 2 ("Local Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 3 ("3V3_local")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 4 ("I2C_PWR_A")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 5 ("I2C_PWR_B")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 6 ("VBAT")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 7 ("Fan Tach. 0")
Type: Threshold (0x01), "Fan" (0x04)
Belongs to entity: (0x1e, 96)
10: LUN: 0, Sensor # 8 ("Fan Tach. 1")
Type: Threshold (0x01), "Fan" (0x04)
Belongs to entity: (0x1e, 96)
10: LUN: 0, Sensor # 10 ("Fan Tach. 2")
Type: Threshold (0x01), "Fan" (0x04)
Belongs to entity: (0x1e, 97)
10: LUN: 0, Sensor # 11 ("Fan Tach. 3")
Type: Threshold (0x01), "Fan" (0x04)
Belongs to entity: (0x1e, 97)
10: LUN: 0, Sensor # 13 ("Fan Tach. 4")
Type: Threshold (0x01), "Fan" (0x04)
Belongs to entity: (0x1e, 98)
10: LUN: 0, Sensor # 14 ("Fan Tach. 5")
Type: Threshold (0x01), "Fan" (0x04)
Belongs to entity: (0x1e, 98)
10: LUN: 0, Sensor # 15 ("-48A Bus voltage")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf0, 96) [FRU # 0]
70
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Using the chassis system event log (SEL)
10: LUN: 0, Sensor # 16 ("-48B Bus voltage")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 17 ("-48A ACB voltage")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 18 ("-48B ACB voltage")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 19 ("-48A ACB Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 20 ("-48B ACB Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf0, 96) [FRU # 0]
10: LUN: 0, Sensor # 128 ("CPLD State")
Type: Discrete (0x6f), "OEM reserved" (0xde)
Belongs to entity: (0xf0, 96) [FRU # 0]
20: LUN: 0, Sensor # 0 ("FRU 0 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0xf0, 1) [FRU # 0]
20: LUN: 0, Sensor # 1 ("IPMB LINK")
Type: Discrete (0x6f), "IPMB Link" (0xf1)
Belongs to entity: (0xf0, 1) [FRU # 0]
20: LUN: 0, Sensor # 2 ("FRU 1 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0xf2, 96) [FRU # 1]
20: LUN: 0, Sensor # 3 ("FRU 2 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0xf2, 97) [FRU # 2]
20: LUN: 0, Sensor # 4 ("FRU 8 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0x7, 111) [FRU # 8]
20: LUN: 0, Sensor # 5 ("FRU 3 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 6 ("FRU 4 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 7 ("FRU 5 HOT_SWAP")
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
71
Using the chassis system event log (SEL)
Using the shelf manager CLI
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 8 ("FRU 6 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 9 ("FRU 7 HOT_SWAP")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 12 ("Fan Tray 0")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 13 ("Fan Tray 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 14 ("Fan Tray 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 120 ("Center Exhaust")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0xf0, 1) [FRU # 0]
20: LUN: 0, Sensor # 121 ("Left Exhaust")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0xf0, 1) [FRU # 0]
20: LUN: 0, Sensor # 122 ("Right Exhaust")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0xf0, 1) [FRU # 0]
20: LUN: 0, Sensor # 123 ("SAP Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0x7, 111) [FRU # 8]
20: LUN: 0, Sensor # 124 ("Temp_In Left")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 125 ("Temp_In Center")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 126 ("Temp_In Right")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 131 ("TELCO Alarms")
Type: Discrete (0x6f), "OEM reserved" (0xdf)
Belongs to entity: (0xf0, 1) [FRU # 0]
72
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Using the chassis system event log (SEL)
20: LUN: 0, Sensor # 132 ("BMC Watchdog")
Type: Discrete (0x6f), "Watchdog 2" (0x23)
Belongs to entity: (0xf0, 1) [FRU # 0]
20: LUN: 0, Sensor # 133 ("SYSTEM EVENT")
Type: Discrete (0x6f), "System Event" (0x12)
Belongs to entity: (0xf0, 1) [FRU # 0]
20: LUN: 0, Sensor # 150 ("Air Filter")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf1, 0)
20: LUN: 0, Sensor # 152 ("SAP")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x7, 111) [FRU # 8]
20: LUN: 0, Sensor # 162 ("PEM A In 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 163 ("PEM A In 2 Fused")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 164 ("PEM A In 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 165 ("PEM A In 1 Fused")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 166 ("PEM A In 4")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 167 ("PEM A In 4 Fused")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 168 ("PEM A In 3")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 169 ("PEM A In 3 Fused")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 174 ("PEM B In 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 175 ("PEM B In 2 Fused")
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
73
Using the chassis system event log (SEL)
Using the shelf manager CLI
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 176 ("PEM B In 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 177 ("PEM B In 1 Fused")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 178 ("PEM B In 4")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 179 ("PEM B In 4 Fused")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 180 ("PEM B In 3")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 181 ("PEM B In 3 Fused")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 192 ("PEM A")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 193 ("PEM B")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 194 ("Shelf EEPROM 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf2, 96) [FRU # 1]
20: LUN: 0, Sensor # 195 ("Shelf EEPROM 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0xf2, 97) [FRU # 2]
20: LUN: 0, Sensor # 200 ("PEM A Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0xa, 96) [FRU # 6]
20: LUN: 0, Sensor # 201 ("PEM B Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity: (0xa, 97) [FRU # 7]
20: LUN: 0, Sensor # 208 ("24V FT 0")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
74
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Using the chassis system event log (SEL)
20: LUN: 0, Sensor # 209 ("-48A bus FT 0")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 210 ("-48A FT 0")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 211 ("-48B bus FT 0")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 212 ("-48B FT 0")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 213 ("-48A FT 0 Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 214 ("-48B FT 0 Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 96) [FRU # 3]
20: LUN: 0, Sensor # 215 ("24V FT 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 216 ("-48A bus FT 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 217 ("-48A FT 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 218 ("-48B bus FT 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 219 ("-48B FT 1")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 220 ("-48A FT 1 Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 221 ("-48B FT 1 Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 97) [FRU # 4]
20: LUN: 0, Sensor # 222 ("24V FT 2")
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
75
Using the chassis system event log (SEL)
Using the shelf manager CLI
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 223 ("-48A bus FT 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 224 ("-48A FT 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 225 ("-48B bus FT 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 226 ("-48B FT 2")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 227 ("-48A FT 2 Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
20: LUN: 0, Sensor # 228 ("-48B FT 2 Fuse")
Type: Discrete (0x6f), "Entity Presence" (0x25)
Belongs to entity: (0x1e, 98) [FRU # 5]
86: LUN: 0, Sensor # 0 ("Hot Swap")
Type: Discrete (0x6f), "Hot Swap" (0xf0)
Belongs to entity (0xa0, 96): [FRU # 0]
86: LUN: 0, Sensor # 1 ("IPMB Physical")
Type: Discrete (0x6f), "IPMB Link" (0xf1)
Belongs to entity (0xa0, 96): [FRU # 0]
86: LUN: 0, Sensor # 2 ("BMC Watchdog")
Type: Discrete (0x6f), "Watchdog 2" (0x23)
Belongs to entity (0x3, 96): [FRU # 0]
86: LUN: 0, Sensor # 4 ("CPU1 Voltage")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
86: LUN: 0, Sensor # 5 ("CPU2 Voltage")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
86: LUN: 0, Sensor # 6 ("+5.0V")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
86: LUN: 0, Sensor # 7 ("+3.3V")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
76
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Using the shelf manager CLI
Using the chassis system event log (SEL)
86: LUN: 0, Sensor # 8 ("+2.5V CPU 1")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
86: LUN: 0, Sensor # 9 ("+2.5V CPU 2")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
86: LUN: 0, Sensor # 10 ("+1.2V 1")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
86: LUN: 0, Sensor # 11 ("+1.2V 2")
Type: Threshold (0x01), "Voltage" (0x02)
Belongs to entity (0x14, 96): [FRU # 0]
86: LUN: 0, Sensor # 3 ("BTI")
Type: Discrete (0x6f), "OEM reserved" (0xe0)
Belongs to entity (0xa0, 96): [FRU # 0]
86: LUN: 0, Sensor # 12 ("Incoming Air-Flo")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity (0x3, 96): [FRU # 0]
86: LUN: 0, Sensor # 13 ("CPU Board Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity (0x3, 96): [FRU # 0]
86: LUN: 0, Sensor # 14 ("CPU1 Temp")
Type: Threshold (0x01), "Temperature" (0x01)
Belongs to entity (0x3, 96): [FRU # 0]
Sample sections of SEL Output
Shows the active shelf manager moving from M0 to M4 state (active and working):
0x0285: Event: at Jan 1 00:01:46 1970; from:(0x20,0,0);
sensor:(0xf0,0); event:0x6f(asserted): HotSwap: FRU 0 M0>M1, Cause=0x0
0x0286: Event: at Jan 1 00:01:51 1970; from:(0x20,0,0);
sensor:(0xf0,0); event:0x6f(asserted): HotSwap: FRU 0 M1>M2, Cause=0x2
0x0287: Event: at Jan 1 00:01:51 1970; from:(0x20,0,0);
sensor:(0xf0,0); event:0x6f(asserted): HotSwap: FRU 0 M2>M3, Cause=0x1
0x0288: Event: at Jan 1 00:01:52 1970; from:(0x20,0,0);
sensor:(0xf0,0); event:0x6f(asserted): HotSwap: FRU 0 M3>M4, Cause=0x0
Shows fan #2 in middle Fan Tray is spinning slower than required:
0x018D: Event: at Jan 1 00:02:15 1970; from:(0x10,0,0);
sensor:(0x04,10); event:0x1(asserted): "Upper Critical",
Threshold: 0xff, Reading: 0xff
Shows a low voltage warning on the backup battery on shelf manager 1:
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
77
Using the chassis system event log (SEL)
Using the shelf manager CLI
0x022C: Event: at Jan 1 23:09:06 2010; from:(0x10,0,0);
sensor:(0x02,6); event:0x1(asserted): "Lower Critical",
Threshold: 0xb3, Reading: 0x99
Shows the board in ATCA slot 4 has exceeded the incoming air temperature limit:
0x0080: Event: at Jan 1 00:25:25 1970; from:(0x8e,0,0);
sensor:(0x01,12); event:0x1(asserted): "Upper Critical",
0x09 0xFF 0xFF
Shows the board in ATCA slot 4 has exceeded the CPU board temperature limit:
0x0081: Event: at Jan 1 00:30:40 1970; from:(0x8e,0,0);
sensor:(0x01,13); event:0x1(asserted): "Upper Critical",
0x09 0xFF 0xFF
78
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
For more information
Training
Fortinet Training Services provides courses that orient you quickly to your new equipment,
and certifications to verify your knowledge level. Fortinet provides a variety of training
programs to serve the needs of our customers and partners world-wide.
To learn about the training services that Fortinet provides, visit the Fortinet Training
Services web site at http://campus.training.fortinet.com, or email training@fortinet.com.
Documentation
The Fortinet Technical Documentation web site, http://docs.fortinet.com, provides the
most up-to-date versions of Fortinet publications, as well as additional technical
documentation such as technical notes.
In addition to the Fortinet Technical Documentation web site, you can find Fortinet
technical documentation on the Fortinet Tools and Documentation CD, and on the Fortinet
Knowledge Center.
Fortinet Tools and Documentation CD
Many Fortinet publications are available on the Fortinet Tools and Documentation CD
shipped with your Fortinet product. The documents on this CD are current at shipping
time. For current versions of Fortinet documentation, visit the Fortinet Technical
Documentation web site, http://docs.fortinet.com.
Fortinet Knowledge Base
The Fortinet Knowledge Base provides additional Fortinet technical documentation, such
as troubleshooting and how-to-articles, examples, FAQs, technical notes, a glossary, and
more. Visit the Fortinet Knowledge Base at http://kb.fortinet.com.
Comments on Fortinet technical documentation
Please send information about any errors or omissions in this or any Fortinet technical
document to techdoc@fortinet.com.
Customer service and technical support
Fortinet Technical Support provides services designed to make sure that your Fortinet
products install quickly, configure easily, and operate reliably in your network.
To learn about the technical support services that Fortinet provides, visit the Fortinet
Technical Support web site at https://support.fortinet.com.
You can dramatically improve the time that it takes to resolve your technical support ticket
by providing your configuration file, a network diagram, and other specific information. For
a list of required information, see the Fortinet Knowledge Base article FortiGate
Troubleshooting Guide - Technical Support Requirements.
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
79
Customer service and technical support
For more information
© Copyright 2010 Fortinet, Inc. All rights reserved. No part of this publication including
text, examples, diagrams or illustrations may be reproduced, transmitted, or translated in
any form or by any means, electronic, mechanical, manual, optical or otherwise, for any
purpose, without prior written permission of Fortinet, Inc.
Trademarks
Dynamic Threat Prevention System (DTPS), APSecure, FortiASIC, FortiBIOS,
FortiBridge, FortiClient, FortiGate®, FortiGate Unified Threat Management System,
FortiGuard®, FortiGuard-Antispam, FortiGuard-Antivirus, FortiGuard-Intrusion,
FortiGuard-Web, FortiLog, FortiAnalyzer, FortiManager, Fortinet®, FortiOS, FortiPartner,
FortiProtect, FortiReporter, FortiResponse, FortiShield, FortiVoIP, and FortiWiFi are
trademarks of Fortinet, Inc. in the United States and/or other countries. The names of
actual companies and products mentioned herein may be the trademarks of their
respective owners.
80
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
For more information
FortiGate-5060 Chassis Guide
01-400-129494-20110912
http://docs.fortinet.com/ • Feedback
Customer service and technical support
81