The 11th International Conference on System Safety and Cyber
advertisement
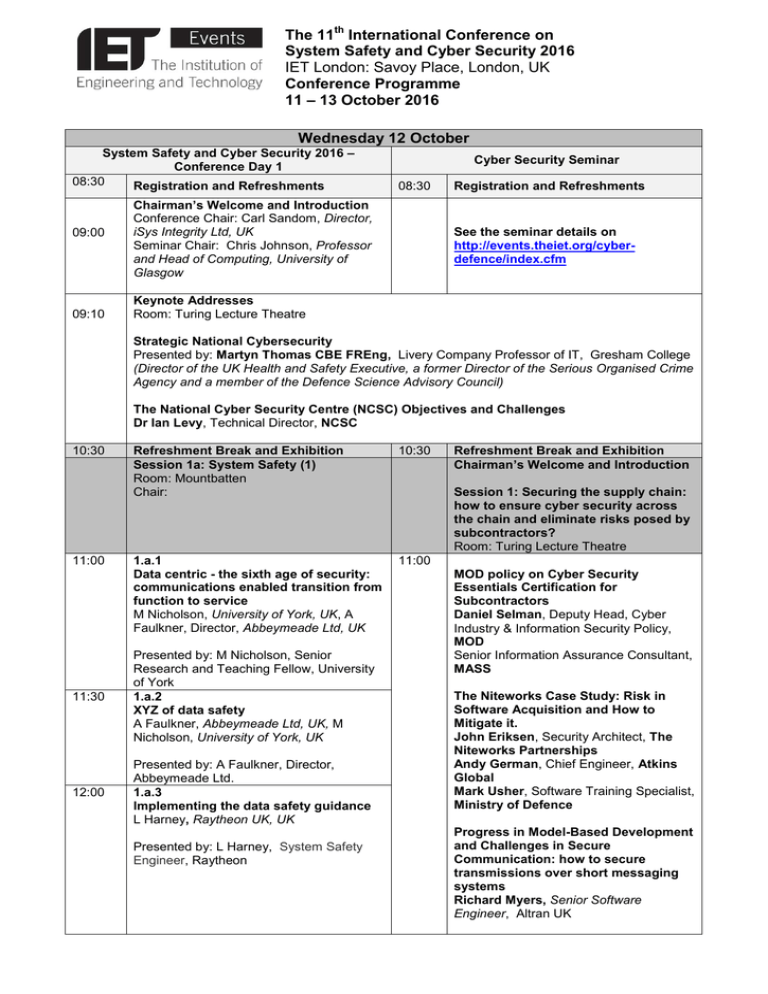
The 11th International Conference on System Safety and Cyber Security 2016 IET London: Savoy Place, London, UK Conference Programme 11 – 13 October 2016 Wednesday 12 October System Safety and Cyber Security 2016 – Conference Day 1 08:30 Registration and Refreshments 09:00 09:10 Cyber Security Seminar 08:30 Chairman’s Welcome and Introduction Conference Chair: Carl Sandom, Director, iSys Integrity Ltd, UK Seminar Chair: Chris Johnson, Professor and Head of Computing, University of Glasgow Registration and Refreshments See the seminar details on http://events.theiet.org/cyberdefence/index.cfm Keynote Addresses Room: Turing Lecture Theatre Strategic National Cybersecurity Presented by: Martyn Thomas CBE FREng, Livery Company Professor of IT, Gresham College (Director of the UK Health and Safety Executive, a former Director of the Serious Organised Crime Agency and a member of the Defence Science Advisory Council) The National Cyber Security Centre (NCSC) Objectives and Challenges Dr Ian Levy, Technical Director, NCSC 10:30 11:00 Refreshment Break and Exhibition Session 1a: System Safety (1) Room: Mountbatten Chair: 10:30 1.a.1 Data centric - the sixth age of security: communications enabled transition from function to service M Nicholson, University of York, UK, A Faulkner, Director, Abbeymeade Ltd, UK 11:00 11:30 Presented by: M Nicholson, Senior Research and Teaching Fellow, University of York 1.a.2 XYZ of data safety A Faulkner, Abbeymeade Ltd, UK, M Nicholson, University of York, UK 12:00 Presented by: A Faulkner, Director, Abbeymeade Ltd. 1.a.3 Implementing the data safety guidance L Harney, Raytheon UK, UK Presented by: L Harney, System Safety Engineer, Raytheon Refreshment Break and Exhibition Chairman’s Welcome and Introduction Session 1: Securing the supply chain: how to ensure cyber security across the chain and eliminate risks posed by subcontractors? Room: Turing Lecture Theatre MOD policy on Cyber Security Essentials Certification for Subcontractors Daniel Selman, Deputy Head, Cyber Industry & Information Security Policy, MOD Senior Information Assurance Consultant, MASS The Niteworks Case Study: Risk in Software Acquisition and How to Mitigate it. John Eriksen, Security Architect, The Niteworks Partnerships Andy German, Chief Engineer, Atkins Global Mark Usher, Software Training Specialist, Ministry of Defence Progress in Model-Based Development and Challenges in Secure Communication: how to secure transmissions over short messaging systems Richard Myers, Senior Software Engineer, Altran UK 12:30 Lunch and Exhibition 13:30 Keynote Address 14:30 15:00 12:30 Verified Trustworthy Software Systems Presented by: Philippa Gardner, Professor at Imperial College London, Director of the Research Institute in Automated Program Analysis and Verification Session 2: Counterattacking cyberSession 2a: System Safety (2) crime with disruptive technologies and Room: Mountbatten innovative strategies Chair: Room: Turing Lecture Theatre 2.a.1 14:30 Designing safe and secure autopilots for Threat actors – motivations and the urban environment capabilities overview S Norton, Quint Safety GmbH, Germany, H Henrik Kiertzner, Principal Business I Akram, Matrickz GmbH, Germany Solutions Manager, SAS Taking the Offensive – Working together to disrupt digital crime David Ferbrache, Technical Director Cybersecurity, KPMG Presented by: H I Akram, Matrickz GmbH, Germany 2.a.2 Safer marine and offshore software with formal-verification-based guidelines L Duboc, H Marteau, F Sadmi, Bureau Veritas, France, S Flanc, Sirenha, France, F Kirchner, V Prevosto, F Vedrine, CEA, France Information Security Standards for Critical Infrastructures: a cost-benefit model for policymakers Alessandro Guarino, CEO, StudioAG / CEN‐CENELEC Cybersecurity Coordination Group Presented by: F Sadmi, Lead safety software engineer, Bureau Veritas 15:30 16:00 Refreshment Break and Exhibition Session 3a: System Safety (3) Room: Mountbatten Chair: 3.a.1 Creating safe and secure C: using MISRAC Guidelines Presented by: Chris Hills, CTO, Phaedrus Systems Ltd 16:30 Lunch and Networking 3.a.2 Comparing SPAD severity assessments between train drivers and railway safety advisors A L Aas, NSB, Norway Presented by: A L Aas, Chief Advisor, NSB 15:30 Refreshments and Networking Session 3: Evolution of threats to the UK Critical National Infrastructure Room: Turing Lecture Theatre 16:00 Industrial and National Infrastructure Cyber Threats: The Kaspersky Lab View Andrey Nikishin, Special Projects Director & Head of Future Technologies, Kaspersky Lab Case study: Cyber Security provisions for the Hinkley Point nuclear plant project Phil Litherland, Head of Electrical, Control & Instrumentation Systems, Nuclear New Build Design Authority, EDF Energy Case study: APT attacks on Critical National Infrastructure in context of Russia's Hybrid War against Ukraine Oleh Starodubov, Digital Forensic Investigator, Department of Information Security of the Security Service of Ukraine 17:00 Close of Conference Day 1 (IET Functional Safety TPN Annual Open Panel discussion: The next five years: what could the UK’s 2016-2021 CyberSecurity Strategy look like? Meeting) 17:00 Martyn Thomas CBE FREng, Livery Company Professor of IT, Gresham College Daniel Selman, Deputy Head, Cyber Industry & Information Security Policy, MOD Bryan Lillie, Chief Technology Officer, Cyber-Security, QinetiQ Dr Ian Levy, Technical Director, NCSC 17:45 17:45 – 19:00 17:00 – 17:45 Chairman’s final remarks and Close Drinks reception and exhibition IET Functional Safety TPN Annual Open Meeting Thursday 13 October - Conference Day 2 09:00 09:30 10:30 Morning Refreshments Keynote Address Integrity: Recognising, acting and saving our own souls Presented by: L. Chambers, Director, Chambers & Associates Pty Ltd. Session 4a: Software, Safety Cases and Standards Room: Mountbatten Chair: 4.a.1 Evaluation of a total aviation system approach for the certification of aeronautical products, systems and services S Rozzi, L Save, Deep Blue s.r.l, Italy, R Wever, Netherland Aerospace Center, Netherlands, S Bull, Ebeni Ltd., UK Session 4: Integrating Safety and Cyber Security (2) Room: Turing Lecture Theatre Chair: 4.b.1 Defending European Airports: cyberphysical threat analysis in total airport management C Johnson, University of Glasgow, UK, P Sirko, A Helios, UK, O Delain, O Ruhlmann, E Vautier, Group ADP, France, B Graham, M-T Meloni, EUROCONTROL Experimental Centre, France Presented by: C W Johnson, Professor and Head of Computing, University of Glasgow 11:00 11:30 12:00 Refreshment Break and Exhibition 4.a.2 Comparing software safety standards EUROCAE ED-153 and IEC 61508:2010 P B Ladkin, University of Bielefeld & Causalis, Germany Presented by: P B Ladkin, Professor of Computer Networks and Distributed Systems, University of Bielefeld 4.a.3 Visualising properties of Simulink models G Anderson, University of Virginia, USA, A B Hocking, Dependable Computing LLC, USA, J C Knight, University of Virginia, United States/ Dependable Computing LLC, USA 4.b.2 Securing the Participation of Safety-Critical SCADA Systems in the Internet of Things C W Johnson, University of Glasgow, UK Presented by: C W Johnson, Professor and Head of Computing, University of Glasgow 4.b.3 Automotive cyber security integrity levels D Ward, P Wooderson, HORIBA MIRA Ltd, UK Presented by: P Wooderson, Senior Functional Safety and Cyber Security Engineer, HORIBA MIRA Ltd Presented by: J C Knight, Professor of Computer Science, University of Virginia 12:30 13:30 Lunch and Exhibition Keynote Address Anthony Finkelstein, Chief Scientific Adviser for National Security to HM Government, Government Office for Science and The Alan Turing Institute Session 5a: Room: Mountbatten Chair: 14:30 5.a.1 Claims and architectures to ratiocinate on automatic and autonomous functions P R Caseley, Defence Science Technology Laboratory, UK Presented by: P R Caseley, Senior Fellow, Defence Science Technology Laboratory Session 5b: Implementing and adoption of security approaches Room: Turing Lecture Theatre Chair: 5.b.1 Nuclear safety and cyber security: achieving the balance R Piggin, Atkins; P. Litherland, Head of Electrical, Control & Instrumentation Systems, Nuclear New Build Design Authority, EDF Energy; R. Orr, Office for Nuclear Regulation, United Kingdom Presented by: R Orr, Head of Cyber Security & Information Assurance Regulation, Office for Nuclear Regulation 15:00 Refreshment Break and Exhibition 15:30 16:00 16:30 5.a.2 Autonomous vehicle systems: a method for assessing on-road risk S Bromage, M Cousen, H E Monkhouse, D Ward, Horiba Mira Ltd., United Kingdom 5.b.2 Security and safety of FPGAs in nuclear safety systems: benefits and challenges R S H Piggin, C Sampson, Atkins, United Kingdom Presented by: Dr David Ward, Head of Functional Safety, Horiba Mira Ltd Presented by: Fred Pollard, Atkins Session 6a: Room: Mountbatten Chair: 6.a.1 An approach for the assurance of legacy systems based on programmable electronic hardware J S Sagoo, QinetiQ, UK Session 6b: Room: Turing Lecture Theatre Chair: 6.b.1 Active defence using an Operational Technology honeypot R Piggin, I Buffey, Atkins, United Kingdom Presented by: J Sagoo, Senior Consultant, QinetiQ 6.a.2 System software quality assurance for safety critical systems J Evans, Bombardier Transportation, Sweden Presented by: J Evans, Safety Critical System Software / Senior Design Engineer, Bombardier Transportation 17:00 Close of Conference Presented by: R Piggin, Security Consultant, Atkins Posters P2 Cyberattacks across academic organisations: Analysis of attacks and guidelines to improve defence D A Maia, Open University, UK Presented by: D Maia, Master student, Open University

