Network Coding
advertisement
Network Coding: Applications and Implementations on
Mobile Devices
Frank H. P. Fitzek
Morten V. Pedersen
Aalborg University
Aalborg, Denmark
Aalborg University
Aalborg, Denmark
ff@es.aau.dk
Janus Heide
mvp@es.aau.dk
Muriel Médard
Aalborg University
Aalborg, Denmark
MIT
Boston, USA
jah@es.aau.dk
medard@mit.edu
ABSTRACT
Network coding has attracted a lot of attention lately. The
goal of this paper is to demonstrate that the implementation
of network coding is feasible on mobile platforms. The paper
will guide the reader through some examples and demonstrate uses for network coding. Furthermore the paper will
also show that the implementation of network coding is feasible today on commercial mobile platforms.
1.
INTRODUCTION AND MOTIVATION
Originally mobile communication systems were purely analog. With the introduction of digital mobile communication
systems, coding of the information that has to be carried
over the wireless medium was used to improve efficiency.
Nowadays coding is an essential part of any communication system. Source coding is used to compress information
at the sender in order to reduce the channel bandwidth used,
on successful reception the receiver can decompress the received data and retrieve the original information. Source
coding is referred to as end-to-end as encoding is only performed at the source and decoding is only performed at the
sink.
Channel coding, on the other side, adds redundancy to
make the transmission over any medium more robust against
transmission errors. Even channel coding is referred to be
end to end as it is applied on a single communication hop
between to communication nodes, e.g. mobile device and
base station.
Lately the coding family got a new member referred to
as network coding by Ahlswede[1]. From a system point-ofview it is not limited to a specific layer, but could be used
Permission to make digital or hard copies of all or part of this work for
personal or classroom use is granted without fee provided that copies are
not made or distributed for profit or commercial advantage and that copies
bear this notice and the full citation on the first page. To copy otherwise, to
republish, to post on servers or to redistribute to lists, requires prior specific
permission and/or a fee.
ACM MSWiM 2010 Bodrum, Turkey
Copyright 20XX ACM X-XXXXX-XX-X/XX/XX ...$10.00.
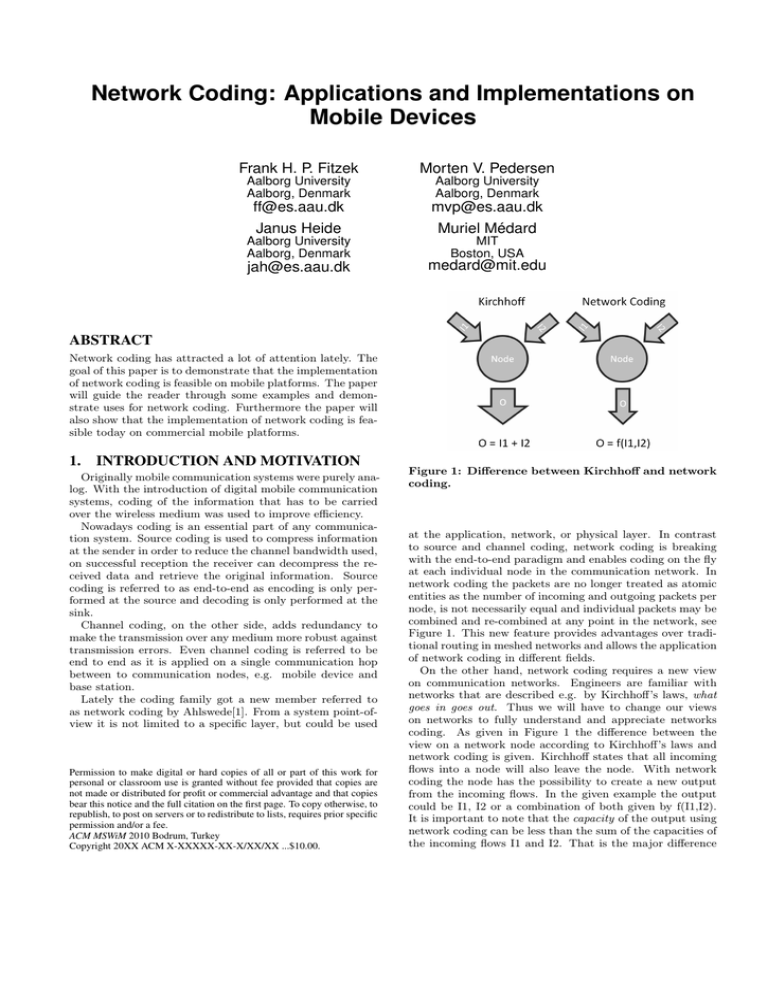
Figure 1: Difference between Kirchhoff and network
coding.
at the application, network, or physical layer. In contrast
to source and channel coding, network coding is breaking
with the end-to-end paradigm and enables coding on the fly
at each individual node in the communication network. In
network coding the packets are no longer treated as atomic
entities as the number of incoming and outgoing packets per
node, is not necessarily equal and individual packets may be
combined and re-combined at any point in the network, see
Figure 1. This new feature provides advantages over traditional routing in meshed networks and allows the application
of network coding in different fields.
On the other hand, network coding requires a new view
on communication networks. Engineers are familiar with
networks that are described e.g. by Kirchhoff’s laws, what
goes in goes out. Thus we will have to change our views
on networks to fully understand and appreciate networks
coding. As given in Figure 1 the difference between the
view on a network node according to Kirchhoff’s laws and
network coding is given. Kirchhoff states that all incoming
flows into a node will also leave the node. With network
coding the node has the possibility to create a new output
from the incoming flows. In the given example the output
could be I1, I2 or a combination of both given by f(I1,I2).
It is important to note that the capacity of the output using
network coding can be less than the sum of the capacities of
the incoming flows I1 and I2. That is the major difference
Figure 2: Channel, source and network coding.
to standard network nodes such as Kirchhoff’s nodes.
Figure 2 shows the difference between channel, source, and
network coding. We assume that two communication pairs
are exchanging information. Both pairs {A,B} and {C,D}
are using some source coding according to the service that
is being provided. The end nodes are connected with each
other via a meshed network. The meshed network is formed
by the five relaying nodes in the middle and they are communicating via IEEE802.11a using channel coding B. Let us
assume each user node is using IEEE802.11b to connect to
the closest relay node of the given meshed network. The
link between user node and relaying node is using channel
coding A.
The outer nodes of the mesh are always connected with
two neighbors as well as with the center node, so three in
total. As we will show later, the network coding takes place
at all five nodes. More precisely the center node will encode
packets and the outer nodes are decoding packets. Note
that each meshed node is receiving four packets, is sending
only one and is performing one coding operation. In a stateof-the-art relaying scenario the center node would send four
packets, the same number as it has received beforehand from
the outer meshed nodes.
2.
lost the same packet, the base station only needs to transmit one packet. In the worst case where each device loses a
different packet, three retransmissions is needed. For each
retransmission only one device would benefit, for the other
two the retransmission is redundant, this problem is known
as the collector’s problem.
Network coding can be used to solve the coupon collector
problem. For the given example, network coding requires
transmission of only a single coded packet. In this case
the coded packet is a bitwise XOR combination of all packets. After receiving the coded packet each mobile device
could recreate its missing packet by combining the coded
packet with the uncoded received packets. Other error recovery mechanisms such as Hybrid ARQ Type II or RAPTOR codes would also perform better than the broadcast
with retransmissions.We note that network coding, if properly implemented, performs better or as well as any of these
techniques in any given scenario.
In Figure 3(b) and 3(c) the advantage of network coding
for meshed networks is given. We consider a simple meshed
network with three mobile devices which are partially connected. Two mobile devices are out of range of each other
and require the help of the third mobile phone, referred to as
relaying device, to exchange packets with each other. Figure 3(b) illustrates the exchange of two packets of the outer
devices using simple relaying mechanisms. Each packet is
sent to the relay and then forwarded, thus four transmission slots are required, when one packet can be transmitted
in one time slot. Network coding can help in this situation
as the two packets at the relay can be coded together The
coded packets then broadcast to both outer mobile devices
in one time slot.
The simple meshed network example shows that network
coding is reducing the number of needed time slots to perform the exchange. Furthermore this simple example gives
some more valuable insights:
1. In IEEE802.11 the MAC protocol assures that the capacity of the wireless medium is fairly shared among
all mobile devices. If we assume that the outer devices
would send a large amount of packets, the relay node
would not get enough capacity to support the relaying
as it needs to send twice as much as the outer devices.
But with network coding all devices are sending the
same amount of packets.
NETWORK CODING BACKGROUND
In this section we provide the reader with some basic information to understand network coding. Network coding can
be applied to many different scenarios, but here we consider
examples with wireless communication.
In Figure 3(a) a multicast scenario is given. One base
station is conveying a number of packets to multiple mobile devices. In order to keep the spectral efficiency high,
each packet is broadcasted. As erasures occur on the wireless link not all mobile devices will receive a sent packet.
In order to have a fully reliable multicast service, erasure
recovery mechanisms need to be applied. Instead of repeating each packet until all devices have received it, network
coding can be applied. Figure 3(a) shows the example of
three packets that are conveyed from the base station to the
mobile device. In the given scenario we assume that each
mobile device is loosing one packet. Without network coding, the error pattern over the devices would have an impact
on the number of retransmitted packets. In case all devices
2. With network coding the order in which the nodes are
sending is important. If the relay node transmits a
received packet right away after reception, there is no
coding possibility. To exploit network coding, the relay needs to accumulate at least two packets, before it
starts to send. As we will show in Section 5 the detection/creation of coding potential is the key to success
using network coding.
3.
FIELD OF APPLICATION
Network coding has a large field of application. In the
following we give a list of the most interesting fields with
the largest potential for commercial mobile platforms.
3.1
Car Communication
Mario Gerla and his team showed in [9] that network coding is suitable for meshed networks with dynamic topology
(a) Network Coding in a Multicast Scenario. (b) Meshed Network without Network (c) Meshed Network with Network
Coding using 4 time slots.
Coding using 3 time slots.
Figure 3: Introduction to Network Coding.
The advantage of network coding in this context is that the
source devices only need a minimal amount of knowledge
about the targets received packets and therefore only a minimal amount of feedback is needed to ensure reliable data
delivery. In Figure 4 the progress of the transmitted information and the actual coding is shown until the full picture
of Lena has been received.
4.
Figure 4: PictureViewer.
and intermittent connectivity. E.g. a car that passes multiple access points on the highway is only within range of an
access point for a short time. As the time in which the car is
covered by the access point is small, it is difficult to detect
which packets the car has not received. Here network coding
can be useful as packets can be generated and transmitted
until the car has enough information to decode.
3.2
User Cooperation in the Cellular World
In [3] and [2] it is advocated to extend cellular links, in
mobile phone and base stations, with short range links to
connect to neighboring devices. By connecting to neighboring devices so called cooperative clusters can be created
which enables reduce energy costs, increased bandwidth and
higher level of robustness. In such a scenario network coding can be used to send multicast information to the mobile phones and the mobile phones will then exchange those
information among each other to speed up the download.
Even more important is that the mobile phones will not just
forward the received coded packets, but recode in order to
make the packet more interesting for the cluster, by creatingterms to coded packets that are less likely to be linear
dependet among each other, than simple forwarded packet.
3.3
Viral Mobile P2P Communication
In [12] the mobile application coined PictureViewer was
introduced. The main idea is to spread information in a device to device fashion among mobile phones. This is referred
to as viral P2P communication. The application was developed for S60 mobile devices and can convey pictures from
one source device to many neighboring devices using WiFi.
IMPLEMENTATION AND DESIGN RULES
In this section we summarize the implementation process
of network coding at Aalborg University in cooperation with
MIT over the last three years. We could list the current state
of art and what was achieved, but to go through the development process step by step will show some of the findings that
are important for the implementation of network coding.
The target platform for implementation is commercial mobile phones, so called smart phones. At Aalborg University
we have a huge interest in cooperating mobile phones. Cooperation among mobile phones involves mesh networking and
network coding seemed to be viable solution in order to reduce the traffic in the mesh and to make the communication
more robust.
4.1
XOR based Network Coding
The first network coding implementation was on three
Nokia N95 mobile phones that exchanged data among each
other as given in Figure 3(c) and presented in [11]. Each of
the phones received an individual stream over 3G and exchanged it with the others over WiFi. Later we increased
the number of phones as given in Figure 5(a). Inspired by
[7], our first demonstrator was using XOR network coding.
This type of network coding is relatively easy to implement
but the tricky part is that all devices involved needs to keep
track of which packets have been received at the other devices. On the positive side, the energy consumption doing
the actual XOR coding was extremely low. One challenge
was to create coding potential and in the first trials only few
packets were actually coded together. The interest reader is
referred to [11].
A second demonstrator was implemented on the Nokia
N810 as given in Figure 5(b). The testbed allowed to distribute packets to 16 mobile devices and let them exchange
the packets according to some given protocols [10]. A lot of
effort was put into the exchange of knowledge which packets
are needed at the neighboring nodes.
(a) XOR and RLNC on N95
mobile phone (Symbian).
(b) XOR implementation on Nokia N810
(Linux).
(c) Partial Network Coding (DSP).
Figure 5: Implementation of Network Coding on different platforms.
4.2
RLNC
The next logical step was the introduction of random linear network coding (RLNC) [5]. In RLNC the protocol no
longer decides which packets should be coded together, instead packets are combined randomly. This has two implications; Firstly the sending device does not necessarily require
the receiver status which packets have been received. Secondly, the coded packets are less likely to be linear depend
and therefore it is more likely that a coded packet is useful. Because computers cannot represent real numbers with
infinite precision, Galois field elements are used to represent the data. The larger the field size, the more possible
combinations, and thus the possibility of linear dependent
packets is smaller. RLNC has been implemented on N95
phones, but the results were not very promising as the encoding and decoding speeds were only around 100 kB/s as
given in Figure 6(a). Even for WiFi oriented ad-hoc meshed
networking these coding speeds are insufficient. Therefore
two different approaches to overcome the described problem
were undertaken. One approach was to use the graphic accelerator of the mobile phone to do some number crunching.
This gave a remarkable speed up factor as given in [14]. If
as special graphic card is used the performance could even
be imporved as shown in [13]. Unfortunately not all phones
have graphic accelerators or do not provide access to the
graphic accelerator. A second possibility is to reduce the
GF size to a minimum of GF(2) [4] and introduce the use of
systematic codes. All in all this ended up in increasing the
coding speed from 100 kB/s to 15 MB/s.
In [6] partial random linear network coding was realized
on the opensensor board. The opensensor board has a Microchip dsPIC30f3013 as main operational device. Interested readers are referred to the cited work.
5.
CONCLUSION AND FUTURE WORK
As seen in the previous section the implementation of network coding is possible, if it is done in the right way. Over
the next years researchers will likely improve the coding
speed by further simplification or standard procedure such
as parallelization or accelerating hardware. But the next big
challenge lies in the design of protocols for network coding.
In this paper we have shown some application fields of
network coding explaining the basic concept. Network coding has two main application fields in mobile communication
systems, namely multicast and meshed networks.
While other coding schemes are end-to-end oriented, network coding allows to merge incoming streams on a per node
basis. This is in contrast to most network engineering concepts we know and is important reason why network coding
can complicated to fully understand.
Over the last years it has been claimed that network coding has limited benefits [15, 8] or it is hard to implement.
Some of the reasons and pitfalls are explained in this paper. However, it is important to stress that network coding
must be applied correctly otherwise the outcome may not
be beneficial.
In this paper we have shown that the implementation of
network coding is possible. Solutions have been found and
further improvements will be done over the next years. The
next challenge is to design network coding aware protocols
to increase the benefit created by the new coding form.
6.
ACKNOWLEDGMENTS
This work was partially financed by the CONE project
(grant No. 09-066549/FTP) by the Danish Ministry of Science, Technology and Innovation and through collaboration
with NOKIA NRC, Oulu throughout the ENOC project.
7.
REFERENCES
[1] R. Ahlswede, N. Cai, S. Y. R. Li, and R. W. Yeung.
Network information flow. IEEE Transactions on
Information Theory, 46(4):1204–1216, 2000.
[2] F. Fitzek and M. Katz. Cooperation in Wireless
Networks – Cooperation in Nature and Wireless
Communications, chapter 1, pages 1–27. Springer,
2006.
[3] F. Fitzek and M. Katz, editors. Cognitive Wireless
Networks: Concepts, Methodologies and Visions
Inspiring the Age of Enlightenment of Wireless
Communications. ISBN 978-1-4020-5978-0. Springer,
July 2007.
[4] J. Heide, M. Pedersen, F. Fitzek, and T. Larsen.
Network coding for mobile devices - systematic binary
random rateless codes. In Workshop on Cooperative
Mobile Networks 2009 - ICC09. IEEE, June 2009.
[5] T. Ho, Médard, R. Koetter, D. Karger, M. Effros,
J. Shi, and B. Leong. A random linear network coding
(a) RLNC implementation on Nokia N95 over large Galois fields.
(b) RLNC implementation on Nokia N95 using the binary Galois field, GF(2).
Figure 6: Performance result of RLNC on Nokia N95.
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
approach to multicast. IEEE Transactions on
Information Theory, 52(10):4413–4430, 2006.
R. Jacobsen, K. Jakobsen, P. Ingtoft, T. Madsen, and
F. Fitzek. Practical Evaluation of Partial Network
Coding in Wireless Sensor Networks. In 4th
International Mobile Multimedia Communications
Conference (MobiMedia 2008), Oulu, Finland, July
2008. ICTS/ACM.
S. Katti, H. Rahul, W. Hu, D. Katabi, M. Medard,
and J. Crowcroft. Xors in the air: practical wireless
network coding. In Proceedings of the 2006 conference
on Applications, technologies, architectures, and
protocols for computer communications (SIGCOMM
’06), pages 243–254. ACM Press, 2006.
J. Le, J. Lui, and D. M. Chiu. How many packets can
we encode? - an analysis of practical wireless network
coding. April 2008.
U. Lee, J.-S. Park, J. Yeh, G. Pau, and M. Gerla.
Code torrent: content distribution using network
coding in vanet. In MobiShare ’06: Proceedings of the
1st international workshop on Decentralized resource
sharing in mobile computing and networking, pages
1–5, New York, NY, USA, 2006. ACM.
K. Nielsen, T. Madsen, and F. Fitzek. Network coding
opportunities for wireless grids formed by mobile
devices. In S. in the ICST Lecture Notes
(LNICST) series, editor, The Second International
Conference on Networks for Grid Applications. ICST,
Oct. 2008.
M. Pedersen, F. Fitzek, and T. Larsen.
Implementation and Performance Evaluation of
Network Coding for Cooperative Mobile Devices. In
IEEE International Conference on Communications
(ICC 2008) - CoCoNet Workshop, May 2008.
M. Pedersen, J. Heide, F.H.P.Fitzek, and T. Larsen.
Pictureviewer - a mobile application using network
coding. In European Wireless 2009, Aalborg,
Denmark, may 2009.
P. Vingelmann and F. Fitzek. Implementation of
random linear network coding using nvidia’s cuda
toolkit. In Wireless Grids 2009, Sept. 2009.
[14] P. Vingelmann, P. Zanaty, F.H.P.Fitzek, and
H. Charaf. Implementation of random linear network
coding on opengl-enabled graphics cards. In European
Wireless 2009, Aalborg, Denmark, may 2009.
[15] Z. Wang, S. Karande, H. Sadjadpour, and
J. Garcia-Luna-Aceves. On the capacity improvement
of multicast traffic with network coding. In Military
Communications Conference, 2008. MILCOM 2008.
IEEE, pages 1 –7, 16-19 2008.

