>> Arjmand Samuel: Well, it's my pleasure to introduce... to us from Indiana University. He's a Ph.D. candidate...
advertisement

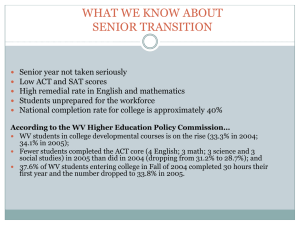
>> Arjmand Samuel: Well, it's my pleasure to introduce Zheng Dong, who comes to us from Indiana University. He's a Ph.D. candidate at School of Infomatics and Computing at Indiana University, and he's a lab manager for ETHOS, Ethical Technology In the Homes of Seniors. And today he's going to talk about some of the cool research they're doing there. Zheng, over to you. >> Zheng Dong: Thank you. As we are honored to be here representing the ETHOS group at Indiana University and talking about several technologies we have developed for the homes of seniors. Our key observation here is that the best technology is not necessarily the right technology. I'll start my talk with a situation of the aging demographic and brief introduction of the ETHOS projects. After reviewing some of the challenges that are faced by the seniors, I'm going to go ahead and introduce some of the technologies our lab has developed to, as solutions to address these challenges. According to the 2010 statistics conducted by the Administration on Aging, which is part of the U.S. Department of Health and Human Services, about 39.6 million Americans were above the age of 65 representing 13 percent of the U.S. population. The number of older adults reached 72.1 million by 2030 representing one-fifth of the U.S. population. Among non-institutionalized old adults, around one-third lived alone, which is about 11 million people. By stating non-institutionalized, we refer to people who are living in their own homes instead of institutionalized organizations such as nursing houses. Another large number come from old adults who reported to have some type of disability, for example difficulty in hearing, vision, cognition, ambulation, self care or independent living was reported by 37 percent in 2010. ETHOS stands for the Ethical Technology in the Homes of Seniors. The ETHOS team develops and also evaluates new technology to keep seniors safe in their homes and connect to their caregivers while giving special attention to issues of ethics and privacy. With the projects primarily located at Indiana University's Bloomington campus. Our team consisted of faculty members, graduates and grad students from School of Infomatics and Computing, School of Public Health and Pervasive Technology Institute. The interdisciplinary nature of our team enables us to develop technologies to support the personal privacy for the seniors and also care for their health and personal security. Current prototypes being evaluated at Indiana University is about encouraging the healthy behaviors, decrease isolation and also support independent living. For faculty members affiliated with ETHOS projects, professor Gene Kemp specializes in human centered security and privacy from technical design to public policy. Professor Kate Connelly focuses on pervasive technologies, development of technology, applications and devices that is related to user privacy. Professor Lisa Huber researches gerontology and issues related to the aging process, and Professor [inaudible] shanker studies issues of technology and infomatics from a social science perspective. As the left manager of the ETHOS project, I'd like to introduce you our living lab. The ETHOS lab is located in the center of Indiana University's Bloomington campus and the house is equipped to facilitate the prototype development and implementation of prototype in a real living space and also research with individuals and groups. We also had spaces for interviews with our focus groups. So specifically we have converted part of the house into a simulated apartment. We have a very small living room, a kitchen, a bathroom and a bedroom. That represents what a small efficiency apartment or living condition might be for a senior. The purpose of the lab is to study the technologies that are going to end up into people's homes in the near future. As we develop the technologies in our living lab, we're getting ready to test the possibility of placing our prototypes in a real outer community. Meadowood Retirement Community located in Bloomington, Indiana. We invited 60 people from Meadowood and also some other community residents to our living lab. We toured them around and showed them about our technologies. They were divided into groups and had conversations with our researchers and developers. We recorded their responses and also our researchers have spent a fair amount of time analyzing their data. Yes? >>: Was it actually related to [inaudible]. >> Zheng Dong: This one? >>: No don't have to go back to the slide. You talked about ethical technology, right, could you elaborate a little more? >> Zheng Dong: Right. So we are -- when we're developing the technologies, we are always incorporating the feedbacks from the seniors which is our focus group. And in some of the experiments, we could -- some of the experiments could be conducted in a certain way that might have an ethical concern with -- I'll actually explain in a minute. It's in one of our experiments was the browsing record processing. So there might be some ethical concern in conducting the research, right? >>: I think all the research you have to get IRB approval for that. >> Zheng Dong: Yes. >>: So you're saying beyond that you have more concerns because you're ->> Zheng Dong: People may have more concerns. But every user studies have been approved by the IRB at Indiana University. But there are certain designs that are actually beyond the requirement of IRB, where really care about the real feelings of the individuals that are actually participating in the experiment. >>: Is it because your participants are seniors or it's because that you are instrumenting their house or is it anything ->> Zheng Dong: Actually, a house is -- the seniors house is a good example, because we're communicating with seniors who do not actually have a lot of experience with the technologies. Something that may look normal to us as from the population, aged between 18 to 36, for example, we're pretty familiar with data sharing within the social network, for example. But the seniors may not be comfortable with sharing information with another people, some of the browsing information, for example. But do you consider that to be ethical or not? Because we're not trying to release that to a malicious third party, but we're respecting the seniors on opinion towards certain technologies. So in the next few slides I will actually explain some of the technologies. We thought it was a cool idea, but the seniors actually do not consider it in the same way and rejected our design. I hope that answers your question. Okay. >>: So quickly I think maybe what I would like to understand what Jane is trying to understand, too, what's the difference between something being ethical and what something being approved by IRB. So preferably your IRB or an IRB will not approve things that participants are not agreeing to. So what you're running into an IRB or ethical issue. >> Zheng Dong: I guess this is different from the agreed-to. Because we're not talking, just talking about a study that the participants are agreed to be joined. I mean, we're placing an object in the seniors homes for a long period of time. We're designing products that they would accept and they will use every day. So it's different if they're agreeing on participating in a study, and we are tailoring our design to their needs so that they feel comfortable of using these products without -- they might say, oh, okay, I agree participating in this study, but I won't use it in my everyday life. So we really want to design some assisted living technology for the seniors and help them to communicate and stay connected. Okay. So after the demonstration of our technologies in the lab, we have recruited eight senior households to participate in insitu testing of our research prototypes. Specifically we have placed our design technologies in four of the houses and consider that to be our test group. And for the rest four houses we did not place any of our technologies in these, any houses and consider that as our control group. I have to mention that the outcome of these insitu testing have extremely changed our initial design of many of the technologies and a lot of our technologies were actually originated from the gerontological theories and some of the things have been changed a lot. At ETHOS, building the innovative prototypes with the up-to-date technology is not the ultimate goal for our researchers. In stead we strictly follow the iterative design methodology of prototyping and keep on integrating the fax from a series of insitu testing in our designs. We always understand that we're designing for a special population, a population that may not have a positive attitude towards new technologies and is also demographically different from our developers. And after several rounds of revision and insitu testing, many of our prototypes have changed in forms of in the physical forms, for example, in our initial design. We sometimes need to reduce the number of functionalities so that the seniors would accept. And another finding we had was that the seniors were really concerned about their personal privacy in the use of these technologies. When we had -- we even had a prototype that was rejected by the seniors, either during the conversation with a focus group or after the insitu testing. So here's an example of a rejected prototype which our developers thought it was a cool technology. We called it mirror motive. So installing in the living room of the seniors the mirror motive actually works like a touch screen of big tablets. The functionality of the mirror motive includes responding to event invitations and also observe the active level of involvement in the community activities, for example. And real time videos can also be streamed to the mirror motive if there's an activity happening in the community room. >>: So this is in their living room or this is in the community room of the ->> Zheng Dong: This is in the senior's living room. We're transmitting ->>: [inaudible]. >> Zheng Dong: There should be a camera on the top, but I guess the picture just didn't ->>: Camera and a display in the living room. And it's recording ->> Zheng Dong: And it's not always on -- it's not always on recording solution. And I believe the primary functionality for the mirror motive is you can actually touch the magic mirror to respond to invitation to events. >>: I'm sorry. What events? >> Zheng Dong: Like, for example, if I'm organizing an activity in the community room and I can invite the community members and the event invitation will appear in the mirror motive. So there's a monitor ->>: Like seniors that live in that community? >> Zheng Dong: Yes. >>: Like an apartment ->> Zheng Dong: Yes, for example, in ->>: In a senior living room community or something. >> Zheng Dong: Right. >>: They each have one of these in their living room. And I'd say, hey, get together for cards. >> Zheng Dong: Right. Exactly. >>: And I would come up there. >> Zheng Dong: And real time video would be streamed. >>: From the room. >> Zheng Dong: From the community room. So the seniors they actually don't like the idea of having a magic mirror with touch screen in their houses, and therefore rejected our prototype. In the next few slides I will go through several challenges our researchers have identified that the seniors might experience when living alone. And also our proposed solutions to these challenges. The first set of challenge include the severe risk of rendering that come with the onset of dementia and other cognitive disabilities in elders. And elders suffering from these problems may leave their houses without proper clothing or at an unusual time and render. The second risk is social exploitation. Elders are known to be a vulnerable population and as such are targeted by various kinds of scams, both by external agents and maybe by some unscrupulous family members. Finally, there should be a system that protects the house against a certain threat that is not specific to the elders but is always associated with them which is robbery. And our conversations with our focus group showed that the seniors are sometimes exploited by unscrupulous individuals as well, from some of their family members instead of from external criminals. There are, however, a large number of existing monitoring solutions for houses with traditional always on solutions there are often two options. One proposed option is that the caregiver could come over to the houses of the seniors at a regular interval. For example, once a day, right, and upon discovering that the senior's missing from the house and determine that the absence is inappropriate, then the caregivers could go ahead and review the tapes. The problem with this approach is potentially the long response time. The rendering behavior may go on undetected until it's too late. Alternatively, the caregiver could observe a real time video at other times. However, the continuous recording system involved the capture and storage of large amount of sensitive information in the centralized location. As a solution to this problem, we build the portal monitor and event triggered monitoring system installed in houses of the seniors. We installed three cameras near the front door of the ETHOS house and these cameras could be triggered by different kinds of sensors. And the cameras are communicated with a control panel which is normally a tablet placed inside the house of the seniors. And what makes our portal monitor really different from the existing solutions on the market is that our system does not rely on a stable Internet connection. So specifically when the cameras are triggered, a series of images are sent from the control panel to the caregiver's cell phone through the cellular network as multimedia message. By using no permanent local storage, our system eliminates the risk of being compromised that exist in many, in a number of centralized data vaults. When a message is received, the interface of most of the cell phones presents a one click deletion. Actually, the nature of these cell phones motivates the user to remove extraneous information such as the images sent by portal monitor. And also to protect the elder's privacy, the system can be deactivated with cognitively challenging switch. So we could ask the senior to serve a very simple capture or to answer a very simple question. To deactivate our system in very short amount of time. And the seniors might want to do that if she is expecting a large number of visitors and do not want to flood the cell phone of the caregiver. The second type of challenge that the seniors really cared about was falling in their homes. Studies show that the estimated incidents of falls for the elders above the age of 75 was at least 30 percent each year. In 2003, more than 7,000 U.S. seniors actually died because of falling in their homes. Existing solutions include variable objects such as a necklace which can be attached to the seniors. And panic buttons in the personal emergency response system can also be used in case an accident occurs. Seniors, of course, could also call 911 or the caregiver if she's conscious and be able to pick up the phone. And alternatively there could be an always-on in-door monitoring solution for the senior. However, this solution is a clear violation to the senior's privacy. According to the discussion with our focus group, turning the light on in the middle of the night is a hassle for most of the seniors. And falling at night could also become undetected for seniors who really rely on a necklace, because many of them will remove the necklace for better sleep. We designed the beacon strip which is assisted living technology that would use the pressure paths to help the seniors navigate in the dark. So specifically it provides illuminated pathway between the bed and the bathroom. When a person gets out of the bed during the night the pathway would activate and as an aid of navigation. The prototype was constructed using the heavy industrial carpet, pressure sensors to detect the footsteps and two rows of LEDs to create a lighted path. And unlike many other existing solutions, our mechanism is designed for falling prevention instead of detection and does not require a device to be attached to a person. The pressure sensor in the bed was actually a very cool technology that we thought, because the pressure sensor can be placed under the mattress in the bed to detect the quality of the sleep. However, the seniors actually do not like the design. They thought it was a violation to their privacy, because it sounds weird to have a sensor in the bed. And with the industrial support from Microsoft Research, we're considering removing the sensors inside the bed and attaching key neck sensors on the wall to detect the falling in their homes and also we're considering using the home OS in our design for the new falling detection system. Yes? >>: It's easy to conclude actually the opposite to me. Like pressure sensor is -it's like low information sensor. It's sensing exactly what you want to sense. Like Kinect will have a lot of collateral information. >> Zheng Dong: Right. But actually we're placing the sensors in different places. The bedroom is considered to be a very private, private location, right? You're placing things inside of a bed which is different from placing something on the way to the bathroom, which is we're attaching the key neck sensor on the wall on the way to the bathroom ->>: In my pajamas instead of my -- it's interesting. It's an interesting thing. Was the problem that you didn't want to light the carpet up every time they step on it because ->> Zheng Dong: No. The beacon strip will still be there. And as an aid of navigation. But in addition to that, because right now we don't know if the senior have falls or has fallen or not on the floor. So we will need to have another sensor to see if they have actually fallen on the floor and we don't want to use the sensors on the bed because they consider that to be privacy violating, because it's weird to have a sensor ->>: It's sort of like a bifurcation. One is about I want to light things up when it's dark, you get out of bed. So you can imagine that completely encapsulated in your carpet, right, lights up, nighttime, lights are off, step on it, the light's come on. Kind of build modulo sensor, then it sounds like that's prevention. Then there's a separate problem of detection and in detection you need more sensors to know ->> Zheng Dong: If they've fallen. But actually we could actually use the same sensors that build in the beacon strip and build on more logic to see if they have fallen on the floor. And I have to say that the second part is all -- it's an ongoing project. And so I don't make separate slide for that. And we are doing this as our first step and after that it will go through conversations with our focus group and it will go through the insitu testing before it comes out as a solution. Thank you. And as many of us could imagine, the social isolation could be one of the challenges that people have when they're living alone. We think that it's critical to maintain a communication channel between the seniors and the caregivers. The current technology enables people to make phone calls or send text messages. However, this solution requires additional spending on the user's end and also may involve a long learning curve at least on the senior's end. We have a very cool idea in which we can place a pair of devices in houses of the caregivers and also the seniors. One in each house. The two devices can be connected through Internet or other technologies. For example, cellular network. On each device we place a motion sensor to detect if someone is around and also we have a light to indicate that the other side of communication is around right now. The question then becomes what kind of object should we choose to build our technology on. And we'd like to build our technology on a very common object so that it's not seen very intrusive to the seniors. And we have started our design with building our technology on a flower port which is cute. We thought it was a very good technology and it was a great integration of the gerontological theory and also modern technology. However, the seniors don't like that because they were worried about the risk of someone adding water to the fake plant. Although it was actually a silk plant they're still considering there's a risk of adding water and mess up with the electronic device so they have rejected our design. After several rounds of conversations with our focus group, we redesigned our technology and this time -- yes? >>: This is mostly for my amusement. Do you think you're worrying too much about this feedback? >> Zheng Dong: Yeah. Actually, we are not worrying too much about the feedback. Instead, we consider this population to be our target customer if we're building this technology. We really think if they can accept our technology, then they will buy it. And then we can actually sell our technology to the targeted focus group. It's not like we're caring too much. Because if they accept that, then there's potentially customers of our products. >>: In this case you may [inaudible] you're don't water this plant or something. >> Zheng Dong: Then in this case they might look intrusive to them. We really want to build our technology in an environment and on a common project -- on a common object that seems normal to the individuals. Do you place a sign on a normal plant in your home? No. Right? >>: If it has light on it so nobody -- a normal pot doesn't have any lights on it. So it's different. >> Zheng Dong: It's from our understanding that is the case. But during our conversations with the focus group, it's a different story. We really respect their suggestions and also we're not saying that the plant has been -- the plant is also in the products in our group and if in the future someone likes it, we will still be developing or improving on the plant. We're not saying -- the project has been rejected. >>: One interesting thing you might take, and I'm reading a ton into this, to me it says, oh, different people might come and care for objects in their home, that's out of their control. So like if you and I had a plant and we only watered our plants, there may be sort of a lack of control of the surrounding thing going on that's resonating into that so they don't want anything that looks like one thing but has other characteristics. Now, that doesn't mean like you could redesign a plant in so many different ways so that even if you watered it it wouldn't take the electronics out blah, blah, blah but there may be a subtle point underneath about that who is coming into their houses and doing things and so they don't want to have to think about telling each caregiver don't water, that's the fake plant. Something like that. There might be more going on there. But it appears -- I don't know. >>: Did they ever have fake Christmas trees like [inaudible]. >> Zheng Dong: I have no idea. Because I personally, I was not part of the user study team, because we're having large projects and a lot of teams of researchers. And I personally don't know. If you're interested I can point you to the right person to answer that question. >>: Can I ask a methodological question. Would you consider [inaudible] has to be consistent across some fraction of users or one person complained and you back off the idea because somebody complained? >> Zheng Dong: We actually haven't backed up the idea. I don't know the fraction of how the fraction would work for changing our prototype. But I can tell you that we're a kind of developing these products in many branches. We're not stopping the development of the plant. We could have many branches so that people would accept. At least when we talked with the 60 focus -- 60 people in the focus group, they thought that that plant was not so good and so that's why we have redesigned our clocks and so that we hope to cover as many individuals as possible. So this is another solution that I will introduce. And after several rounds of conversations with the group, we have redesigned the technology and this time we build ambient clock which allows the caregivers to be aware of the movement of the seniors while being minimally invasive. So we still have the motion sensor on the top of the clock and also we have upgraded the display of the activity indicator. So this time we're not only showing that if the other end is here right now but we're showing the previous activity for the past 12 hours on the clock. So the ambient clock should be placed in the seniors' home and is paired with another clock in the caregivers' home. Whenever a senior is around the present clock, the other clock -- I mean the paired clock would light up to show that the seniors is around. And for the caregivers clock as well. If the caregiver is around, the senior's clock will light up. The advantage of our design over other existing solutions is that a clock is a common object in the home environment and so that it's less intrusive than a camera, for example, and in addition since activities are transmitted over the Internet, the running of the clock actually does not require spending on the user's end. If the Internet connection is not available, we also provide an option of transmitting the information by using text message, for example. I'll spend most of my time today focusing on the next identified challenge, which is online fraud. While seniors are known to be one of the most vulnerable populations to both online and off line thoughts people seem to be more worried about safety when they're surfing online. Since a large portion of the senior population may not have received a sufficient training on even how to visit a website, we could not expect them to distinguish a good website from a bad website. During the interview with our focus group, we found that they're really concerned about the possibility of visiting a malicious website that would look exactly the same as legitimate website. And the problem becomes more severe when personal information such as their banking account or credit card number has been included in malicious website. Even though many security solutions have been proposed and implemented, according to the anti-phishing working group, we're still facing the problem in which an increasing number of fraudulent websites are reported every day. However, in the real world threats and off-line scams can often be mitigated pretty easily. For example, people who wanted to buy a Big Mac would definitely choose the McDonald's restaurant instead of the one shown on the right-hand side which has a very similar logo. How about KFG? It looks exactly the same as the layout of a KFC restaurant except the last letter in the logo. Even for people who are fooled by the logo or the layout of the KFG restaurant for the first time, since experiences are often shared within a social network, and the knowledge about the KFG will soon become the group knowledge of a bigger social network. So why can't we apply the same approach to the virtual online space? Unlike places in the real world, the virtual sites would be distinguished only by the website design, the domain name and possibly the SSL certificates. We think that at least in part the Internet fraud was enabled by a lack of reliable trusted sources of information. We think that and ideally there should be a website reputation system that could provide clear security indicator to the user and help them to make an informed and adaptive decision. As an example of attack that is enabled by a lack of information is a phishing attack. Phishing attack is very hard to prevent because they raise directly to the absence of resource identification information. And absent any other information other than an e-mail from a self-proclaimed bank a user must decide whether to trust the website that looks exactly the same as the one he or she has visited before without much consideration. Sorry. So popular Web browsers usually equipped with website black lists when a malicious URL is entered a warning page is displayed before the actual content is displayed. So they communicate the potential risk of this Web page. However, there could be delay in updating the warning messages. And as an example I have randomly picked a phishing site from the phish tank, which is a source for verified phishing websites and I actually enter that exactly the same URL into a popular Web browser, and unfortunately that URL is still accessible from that browser without triggering any type of warning and alert messages. Therefore, instead of some trusted third-party alone, we'd like to learn from the solutions to address the off line scans and incorporate our social network idea in this simple design. So we have Alice here who has a friend named Bob. And Alice trusts Bob's opinion. Although Alice has never been to this website before, Bob's suggestion about this website can really help Alice in making a decision about trustworthiness of the website. In 2006, Professor Gene Kemp at Indiana University had proposed a net trust system to protect the browsing security for the individual users. As shown in the figure, the net trust tool bar contains true indicators from the friends and colleagues shown in the middle. The natural trust tool bar also have the white list from the trusted third-party shown on the right. The design net trust is to assist the online users to make an informed and educated decision about a website, even when they're visiting a website for the first time. That's an important feature of net trust is the integration of contextual information shown on the left-hand side. So specifically upon registration an individual could actually create multiple Web pseudonyms to indicate different Web browsing contacts. Each visited website is associated with one or more of the predefined Web contacts. For example, YouTube.com may be in someone's play contacts while a visit to turbotax.com may be part of someone's private contacts. In net trust, the contacts are primarily utilized to indicate different groups of browsing history sharing. So that is the individuals are only share their browsing experience with a subgroup in their social network. >>: This does sound complicated. >> Zheng Dong: Yes, but we're not expecting the seniors to understand our underlying logic here. I will explain in a minute about our integration into the browser and how the seniors actually respond to our design. The browser tool bar was liked by a lot of younger population. We had user study with younger population and they liked the idea of social network and the browsing contacts idea. But the seniors don't like it. You're absolutely correct. So based on our previous research, the phishing website usually go up and are identified after a short period of time and are then taken down. In other words, the phishing website do not stay up a long period of time. The net trust tool bar takes advantage of this important feature of phishing and usage features that are not under control by the malicious agents. For example, the user's social network, user's browsing history and friend's social network and friend's browsing history. This visual would potentially be used to prevent the phishing victim from misdirecting individuals. The net trust is more secure than some easy-to-copy visual cues, for example, of some log images that are placed in a Web page, for example. And are more understandable than some online certificate information. So in net trust people in the social network could contribute in the ratings in two ways. A visit to a website by a member in the social network is considered as an implicit rating. The lowest implicit rating is zero, meaning that a website has never been visited before. And initial visit will create a rating of one. Consider the fact that the phishing website often have a shorter lifetime. We have designed the delay factor so that it really takes a few days before a rating takes effect. Once the ratings are entered into the social network and also the local database, it will subject to a decay factor. So if a website is not visited again, the original rating will drop to maybe half of the original ones so the phishing website could receive a lower rating if they don't have any more visits after a short period of time. Explicit rating is more intuitive. Users of a system could explicitly rate a website using a numeric scale between negative and positive vibe. When designing the net trust system, one of the questions we had was how large does the social network has to be to cover the majority of the sites that has been visited. In other words, would it be possible to limit the number of participants that you share your browsing history with while still receive enough information to make the right decision. The Metcalf law argues that the value of the network increases proportionately to the square of the number of participants. So that means -- okay -- it's always an increase if we add more people to the collaborative network. Yet in terms of security and trust, the activities of spammers, phishers and malwear distributors make the converse case. We think a trade-off will need to be made within the degree of sharing browsing history and user privacy. On the one hand, certain amount of browsing information is clearly useful. Nearly every collaborative network is improved by increasing the number of participants. The more information received from the other participants potentially the more accurate the results. On the other hand, more participants inherently increase the information disclosure regardless of the benefits. The more people whom you share your browsing history with potentially the larger the data, the data or the information disclosure is. So therefore we need a balance between the privacy and information sharing. We have examined the value of the network and also the value of network size in two domains according to what the Web browsing history is useful. Discovery and evaluation. Discovery is commonly seen in a lot of collaborative search engines for online resources. These Web services allow the expert to guide the less experienced individuals in their Web searches. Online services like collaborative search are looking for a broader view of the Web. Therefore, each participants ideally contribute some new information to the community. Evaluation on the other hand only requires certain degree of homogeneity so that suggestions or ratings made by one person is useful to the others. Evaluating ratings have been widely implemented in many social networking-related devices or services to help users make decisions on the online services. So, for example, our net trust tool bar is certainly part of the evaluation services. We have run experiments to find out recommended site for the resource sharing network and the discovery and evaluation services respectively. The data that is used in the experiments was compiled based on the Internet browsing history of over 1,000 participants who were undergrad students living in the same [inaudible] at India University's Bloomington campus. This is a fairly homogenous population and inherently students in that dorm were similar in H living conditions and course loads and current degree objectives. Browsing data were compiled in 80 and any HTTPS traffic was not compiled or reported. URLs were trimmed so that no session information gets recorded. Participants were distinguished by the hash of their MAC or MAC address. And then we have designed the identification number from 0 to 1,083 to preserve the anonymity. >>: So this is still part of this spam detection [inaudible]. >> Zheng Dong: One of the questions we had in mind is because in the net trust system, we're relying on the social network to provide the rating. >>: So this came from input, right, I go to this event website and make sure that all the other people have been to that bank website and this is a visit to my bank website, kind of, but if you could exclude https URLs, then I don't think you get any legitimate bank website visitors, a lot of -- I hope most of the banks -- the banks they employ https, so you don't see any of the website visit history for ->> Zheng Dong: You're talking about the malicious website may not use https. >>: No, you also want to have Web browsing history for good bank websites, right, well you won't get that from your trace if you exclude it. >> Zheng Dong: Right. I mean, the Web browser may have different sources of information displayed as different security indicators but net trust provides -- we also have external third-party lists which is a list of legitimate banking website. That is an important indicator that were shown to the user and especially for the senior. There were no directly from the tool bar okay this one is a banking website and this rating is not generated by a social network. It's the third party. What we're saying here is in addition to the third party, we're relying on the ideas of your social network, like the wisdom of the crowds. Like how do you get information from other people and generate a big picture of a website even though you have never been that before. It's not necessarily that the website is a banking website or not. >>: Maybe we can take it off line, but if you want to collect Web representative samples of websites, if you exclude all https traffic for the URLs, then you're going to miss a lot of legitimate sites that people visit not just banking websites. >> Zheng Dong: We can actually talk about the Web traffic that we have collected later. I mean, I do have the data somewhere. But we could actually talk about it later after the talk, maybe. So each browsing record is in the form of time and the URL and user ID. Individuals were given the option of not being included in the experiment in two ways. First, there's the VPN available so that we're not trying to compile that kind of traffic. And also in an announcement of experiment, we have included the contact information of our researchers so that the undergrad students could actually contact us and opt out. And also there is a two-week period which before the contact of our experiment, so that our researchers have time to provide a workshop for tour installation to the undergrad students. And our experimental data actually covers a period of eight weeks from March to May 2008. We use the browsing history for over 1,000 users to build a simulation of the social network. We started with browsing history randomly selected user and then keeps on adding the browsing history of other users to a size of 50. And in order to better capture the relative value of the browsing record, we evaluate the record in three ways. The first approach is the domain name in which the URLs is considered just according to the domain name and the host is our second approach, which would consider the entire URL up to the third forward slash. The third method is called the first level directory where we consider up to the first subdirectory in the URL. This graph shows the results of our experiment for evaluation Web services. As more people join the pool, we found a rapid increase in the percentage of websites that people had in common in their browsing histories. After ten participants were added into the pool, about 95 percent of the domains have already been covered. At that point, however, the average value of adding each additional participant brings very little increase. After 40 additional participants, nearly 99 percent of the clicks will go to no insights. The experiment shows that with a homogenous population, evaluation Web services such as net trust do not require a large number of participants. After consulting our focus group we felt we could further improve the net trust system and make it more accessible and more easy to operate. We therefore designed the net trust cube, which is in visualization of our security design. The translucent cube is connected to the computer through the USB cable. And the cube is equipped with green and red LED lights. The net trust cube risked ratings from the current website by using the same underlying code of net trust system. So as we could see from the graph here, the lowest rate of the net trust is negative 5. In the cube it shows QE red, and highest ate deposited by is shown in purely green. And in addition to showing the current rating, we also enable user to make changes to the explicit rating. So as you could see from the left-hand side figure, we have two arrows built on the two sides of the cube. One up arrow and one down arrow. The user could change the rating of the current website by pressing one of the arrows. For most of the time, the color of the net trust cube will change accordingly. However, according to some conversations with our focus group, some important external ratings such as the legitimate banking website would dominate the color of the net trust cube. In one study, participants aged from 18 to 36 responded pretty positively to our net trust tool bar. They particularly like the idea of having a social network design and you could share and rate a website, you could comment on a website and share with your friends. However, when we presented the net trust tool bar and also our net trust cube to the senior population, they seemed to like the net trust cube better. They thought the net trust cube provides physical forms that are easy to see and immediately understandable, rather than being very small on the screen. One of the participants even expressed a concern about colorblind users being able to distinguish good website and bad website, which actually formulates the idea of using a parsing design or a parsing pattern of the red LEDs in the net trust cube. We installed our net trust cube and browser tool bar in our recruited test and control groups, and we have simulated a phishing attack by sending a phishing e-mail to both the groups. The outcome was pretty encouraging, because none of the seniors actually responded to the phishing e-mail. However, after the in situ testing, we have received a lot of criticism on the Web browser tool bar because they have complained about the tool bar being too complicated and took up space on this browser. And the feedback we received about the browser, the net trust cube is actually pretty positive. To conclude, we understand the goal of our technology is for the homes of seniors. So design for a special population means that we cannot simply utilize the most recent technology or some existing technologies that are designed for the entire general public. Instead, we're tailoring the technology to the senior population right from the very beginning and be prototype design. As I explained, in a couple of prototypes, we had in mind both the physical forms and the underlying algorithms have changed a lot from our initial design. And I'd like to also point out that we're not just applying one technology, one existing technology to another field. By saying designing for the seniors and the homes of seniors, we're looking at a completely different world of technology needs. And at last I would like to acknowledge the MSF grant titled older adults perception of privacy and I'd like to thank some of my colleagues, and thanks for your attention. [applause] >> Arjmand Samuel: Do we have questions. >>: How would you rate the seniors who are actually a little bit younger who do understand some of this technology? Have you come across them and their reactions any different. >> Zheng Dong: Actually for the net trust system, I believe you were talking about that, we had -- because of the limitations of the focus group that we have. So we would not be able to distinguish different ages. But I believe that a certain amount of these senior adults will -- they will like our net trust tool bar as well. But we actually didn't actually consider that in the paper. >>: So what are the key insights that you learned? >> Zheng Dong: One of the key insights here is the best technology is not always the right technology, especially when you're designing for a special population. >>: In the conclusion, but what are the kind of what are the characteristics of these elders that we need to consider when we design? >> Zheng Dong: I think that there will always be several guidelines that you will find in our papers but I personally think that we really could improve our design by consulting the focus group and really perform some in situ testing. I can't tell you exactly you should follow these guidelines and then you will have successful products. But our experience was we're following certain kind of cycles so we always are consulting them and invite them here to the house because we are demographically different. We're in a different age. So a lot of perception that we had may not be applied to a special population like them. So that's my personal opinion about that. >>: Going back to my point, seniors range from 60 to 90. Those who are 60 could well be very happy with technology, whereas maybe the 80 is not. So you didn't encounter that kind of ->> Zheng Dong: Right. And I have to also mention that our system is highly modelized. So it's not necessarily that the seniors are actually applying older technologies in their homes. Some of them might like the ambient clock while others might like the trusted cube. We have other technologies that design for perhaps the seniors beyond the age of 90. And I have to say that the point is it's not applying every technology in the seniors' homes. We're trying to help them and tailoring the technology to their actual need. So you could actually -- if this is actually products you can actually choose whatever you want as modules. >>: I think maybe you tried to touch on this, but somehow you have to make this tailoring scaleable. If the amount of work -- if you have to do like market testing for like the intent you're developing and the effort in that market testing is the same as the first thing, then it seems there's a problem here with respect to like how frequently and how many products you can design. So you have to kind of learn something such that your chances of getting it right with fewer iterations go higher. So what are some of the things you're learning? >> Zheng Dong: I actually -- I personally think that this is a very good question. And I don't have the answer right now. I think that we are considering this problem right now because we're having many groups of people who are designing the technology. And regarding the questions that you were asking, I think we will do that in the next step. And I believe that. And we also have other projects that would -- we have faculty members, we have graduate students who will be evaluating like the expenses of designing the technologies and as I said how is the probability of designing these, the right technology. >>: There's two ways -- there's two ways to look at it. One is like having a list of common mistakes to avoid, which is easy to compile maybe and then one is a list of best current practices. So what I'm hearing from you is you're not ready to lay down your best current practices. Do you have a list of common mistakes? Is that something from your experience you'd say I'd never do that again? >> Zheng Dong: I personally am not part of the user study or every development team. So I really don't have the answer. But I'd like to discuss with you maybe after the talk if we could talk about that and/or direct you to the right person to talk to. >>: Which part are you working on? >> Zheng Dong: I am working on the coding and development of the net trust system and also the ambient trust. And as a lab manager I'm also maintaining the entire lab and organizing demonstrations, and I'm also doing the data analysis for the experiment that I just explained. Like to measure how many people do you need to actually share your browsing history with. >>: The monitor system is just -- is that just at the lab or deployed in individual's homes the doorway. >> Zheng Dong: The portal monitor we currently have one unit that's implemented in our ETHOS lab, and we're expanding the prototype and we're hoping to install that in many of real people's homes. >> Arjmand Samuel: Thank you very much. [applause]