A Multi-Dimensional Configurable Access Control Framework for Mobile Applications
advertisement
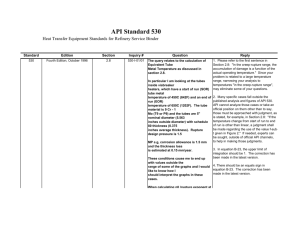
A Multi-Dimensional Configurable Access Control Framework for Mobile Applications By: Yaira K. Rivera Sánchez Major Advisor: Steven A. Demurjian Introduction • Mobile devices are rapidly replacing desktop computers • Users can do a wide variety of tasks in mobile devices • Mobile applications come into play http://www.sdgc.com/sites/default/files/pdfs/mobile_applicaton_security_framework_wp.pdf • Ubiquitous Technology 2 Motivation • Can Access Control be Leveraged for Mobile Computing? • Role-Based, Discretionary, Mandatory • Other Possible Access Control Models? • Where do we Define and Enforce Access Control? • User Interface? • Mobile App API? • Server/Database/Repository? 3 Main Research Questions • Issue: Highly-sensitive data in mobile applications • How to protect it? • Who should be able to access it? • What should be shown to each user? • How to integrate fine grained access control in mobile applications? • Where to do the integration? 4 Big Picture 5 Proposed Configurable Framework Configurable Framework RBAC, MAC, and DAC Direct UI Modifications Intercepting API Calls Direct Server Modifications Optional Permissions on Screens, UI Widgets, etc. Optional Permissions on APIs Realize & Enforce Permissions Existing mobile App Existing mobile App API Existing Mobile App Server (Database, Web and/or Cloud) The Configurable Framework and its Interactions with the Mobile App Infrastructure. 6 Expected Research Contributions • Multiple and Configurable Access Control Models • Fine-grained Permission Definition and Enforcement • Security Policy Generation: – Use of Access Control models in security policies • Security Policy Integration: – Security policies in diverse layers of a mobile application 7 Remainder of Presentation • Background • Proposed Framework – Focus on RBAC • Direct UI Modifications – – – – General Idea Authorization & Enforcement Process Implementation Permission Definition • Intercepting API calls – – – – Architecture General Idea Policies & Pseudo Code Implementation Example • Conclusion & Future Work 8 Background • Mobile Application – Native, Hybrid, Web • Access Control – Role-Based Access Control (RBAC) • Application Programming Interface (API) – JSON/REST 9 Mobile Application Structure Logical Architecture Proposed Framework 10 Direct UI Modifications • Role-Based Access Control (RBAC) for Mobile Applications • Apply RBAC to a mobile app’s UI • Policies stored in the Database • Conditional statements are placed throughout the code • Communication through APIs 11 General Idea 12 Authorization & Enforcement Process 13 Implementation • Connecticut Concussion Tracker (CT2) • Developed in support of a new law passed in the state of Connecticut to track concussions of kids between ages 7 to age 19 in public schools (CT Law HB6722) • Roles: Nurse, Athletic Trainer, Coach, Parent Nurse AT/Parent Coach 14 Permission Definition in CT2 • Screens: • Show • Hide • Buttons: • Enabled • Disabled • Text Fields, Drop Downs, Date Pickers: • View • Edit • Edit Once 15 Intercepting API Calls • Place all the security policies in the API/DB • Do not change source code (look-and-feel) • Disable the delivery of content: Return filtered data to the mobile application • Insert/update actions: Before inserting information in the database • Retrieval actions: Perform RBAC checks after the information is retrieved from the database 16 Architecture • Part 1: • Existing components of mobile application • Define permissions on these • Part 2: • Data in the DB (does not get modified) • Part 3: • Addition and enforcement of security policies in DB and API 17 General Idea 18 Policies & Pseudo Code Security policy tables in the database API function pseudo code 19 Implementation Example • Coach role: – Add basic information about a student – Add information in the ‘Cause’ screen -> view it but not edit it – Attempts to edit cause -> Blocks the attempt – Does not have permission to view nor edit the ‘Symptoms’, ‘Follow-Up’ and ‘Return’ screens -> Will block the content 20 Conclusion & Future Work • Proposed a framework to achieve finegrained access control in mobile applications • Presented two approaches that could be part of the framework • Mobile Application Management (MAM) – Application Wrapper • Focus on the backend of the mobile application (API/server/DB) 21 Questions? • Introduction • Motivation • Main Research Questions • Big Picture • Expected Research Contributions • Background • Proposed Framework • Direct UI Modifications • Intercepting API Calls • Conclusion & Future Work 22

![Subject Line: Dear [insert name of manager],](http://s2.studylib.net/store/data/017768406_1-c50aef4b9b58b03a50d5284bdf8bfcdd-300x300.png)