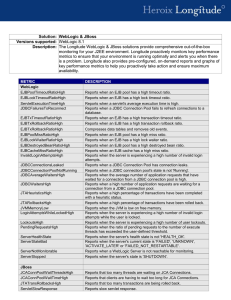
Static Analysis of Role-Based Access Control in J2EE Applications
advertisement

Static Analysis of Role-Based
Access Control in J2EE
Applications
TAV–WEB 2004
Gleb Naumovich and Paolina Centonze
Department of Computer and Information Science
Polytechnic University
gleb@poly.edu & pcento02@utopia.poly.edu
Introduction
• New technique for security analysis of J2EE
applications
• It identifies situations in which too much or too little
access is given to security sensitive resources
• It uses static analysis to analyze J2EE programs and
access control policies with respect to securitysensitive EJB fields
2
Architecture of J2EE Applications
RMI-IIOP
RMI-IIOP/local
HTTP
HTTP/
HTTPS
Client tier
HTTP
Server
Servlet/JSP
Proprietary
Protocol
RMIIIOP
Servlet
Container
Enterprise bean
EJB Container
Web tier
Business tier
JDBC
JDBC
Database
Information System tier
3
Role-Based Access Control in J2EE
• In J2EE, resources, are EJB methods, servlets, JSPs, and URLs
• Developers and deployers must determine:
– Which roles make sense for an application
– Which EJB methods and Web resources each role should be allowed to
call
r1
r2
r3
Protected Resources
Roles
4
EJB Interface and Implementation
public interface Gradebook
extendsjavax.ejb.EJBObject {
public Grade getGrade(Student s,
Homework h) throws RemoteException;
public Map getAllGrades(Student s)
throws RemoteException
public void addHomework(Homework h)
throws RemoteException;
public void removeHomework(Homework h)
throws RemoteException;
public Set homeworks() throws
RemoteException;
public void setGrade(Grade g, Student s,
Homework h) throws RemoteException;
public Grade getGrade(Student s,
Homework h) throws RemoteException;
public Map getAllGrades(Student s)
throws RemoteException
}
getGrade()
getAllGrades()
Client
Remote Interface
public class StoreBean implements
javax.ejb.EntityBean {
private Set homeworks;
private Map studentsToHomeworksToGrades;
getGrade()
getAllGrades()
log()
EJB Class
public Grade getGrade(
Student s, Homework h) {
if (! this.homeworks.contains(h))
throw new
NoSuchHomeworkException(h);
log();
return (Grade) ((Map)
this.getAllGrades(s)).get(h);
}
public Map getAllGrades(Student s) {
Map result = (Map) this.
studentsToHomeworksToGrades.get(s);
if (result == null)
throw new
NoSuchStudentException(s);
return result;
}
public void log() {
// ...
}
// Other remote methods implemented here
}
5
J2EE Access Policy
<assembly-descriptor>
<security-role>
<description>Students</description>
<role-name>Student</role-name>
</security-role>
<security-role>
<description>Teachers</description>
<role-name>Professor</role-name>
</security-role>
<method-permission>
<role-name>Professor</role-name>
<method>
<ejb-name>Gradebook</ejb-name>
<method-name>
addHomework
</method-name>
</method>
<method>
<ejb-name>Gradebook</ejb-name>
<method-name>
removeHomework
</method-name>
</method>
<method>
addHomework()
<ejb-name>Gradebook</ejb-name>
<method-name>
removeHomeworks()
setGrade
homeworks()
</method-name>
getGrade()
</method>
setGreade()
<method>
getAllGrades()
<ejb-name>Gradebook</ejb-name>
<method-name>getAllGrades</method-name>
</method>
</method-permission>
Greadebook Interface
</assembly-descriptor>
public interface Gradebook
extendsjavax.ejb.EJBObject {
public Grade getGrade(Student s,
Homework h) throws RemoteException;
public Map getAllGrades(Student s)
throws RemoteException
public void addHomework(Homework h)
throws RemoteException;
public void removeHomework(Homework h)
throws RemoteException;
public Set homeworks() throws
RemoteException;
public void setGrade(Grade g, Student s,
Homework h) throws RemoteException;
public Grade getGrade(Student s,
Homework h) throws RemoteException;
public Map getAllGrades(Student s)
throws RemoteException
}
Student
Professor
Client
Roles
6
Limitation of the
J2EE Access Control Model
• Today, access control is defined in terms of
operations on components, instead of data
encapsulated and used by the components
• This potential inconvenience may lead to
security problems and our work intends to
solve it
7
Access Control on Methods
May Create Security Problems
Professor
• Multiple methods for
reading and writing the
same data
setGrade()
getAllGrades()
removeGrade() getHomeworkGrades()
modifyGrade() getMidtermGrades()
getAllGrades()
getHomeworkGrades()
setData()
getMidtermGrades()
getFinalGrades()
•grades
Student
Security Sensitive Fields
8
Access Control on Data
Can Enhance Security
• Access control on data can
be more straightforward and
convenient, and less error
prone
Professor
read,write
read
•grades
Student
Security Sensitive Fields
9
Static Analysis
Can Help Validate Existing Policies
• Even when access control is
specified on the basis of
methods, it may still be
useful to validate the security
policy based on the data
accessed by these methods
Professor
setGrade()
getAllGrades()
removeGrade() getHomeworkGrades()
modifyGrade() getMidtermGrades()
getAllGrades()
getHomeworkGrades()
setData()
getMidtermGrades()
getFinalGrades()
•grades
Student
Security Sensitive Fields
10
Steps of Our Analysis
Bytecode
to be Analyzed
input
Static Analyzer
output
Points-to
Graph
input
Points-to Analyzer
output
EJB Fields
(Written/Read
)
input
input
J2EE Access
Policy
J2EE Security
Analyzer
output
Inconsistencies/
Security Problems
Deployer / Analyst
11
APE Graph
• Our analysis requires computation of which EJB
fields may be read and/or modified by an EJB method
• It uses a points-to graph for computing this
information
• The specific graph used is the Annotated Points-to
Escape (APE) graph of Souter and Pollok
– A. L. Souter and L. L. Pollock. The construction of
contextual def-use associations for object-oriented systems.
IEEE Trans. Softw. Eng., 29(11):1005–1018, 2003
• For our approach to be useful, we also have to
analyze fields of primitive types
12
Example of an APE Graph
o3
public class StoreBean implements
javax.ejb.EntityBean {
private Map studentsToHomeworksToGrades;
// ...
public Map getAllGrades(Student s) {
TreeMap result = (Map) this.
studentsToHomeworksToGrades.get(s);
if (result == null)
throw new
NoSuchStudentException(s);
return result;
}
// ...
}
this
o1
o2
o4
load
s
result
o5
APE Graph for method getAllGrades()
13
Read/Write for EJB Fields
An EJB field f is read/written by a method m if the value of f is
accessed/modified by the thread executing m while m is on the call
stack
m
m1
m2
Write/Read field f
Thread Executing m
14
Field Sequences
public class Semester implements EntityBean {
Course calculus;
//...
}
public class Course {
Student assistant;
//...
}
public class Student {
String name;
int ssn;
//...
}
o
1
calculus
o
2
• It is important to analyze the reads/writes of
fields of objects that are referenced by EJB
fields, beside the EJB fields themselves
• A field sequence f0,f1,…,fk is a series of field
dereferences, where f0 is an EJB field, and
i=1,…,k, fi is a field in one of the possible
classes for object fi–1
• Essentially, f0,f1,…,fk represents objects that
can potentially be reached from an EJB object
via a number of field dereferences
assistant
o
3
name
o
4
Field Sequence
15
Determining Whether a Field Sequence
May Be Written by a Method
• A field sequence f0,f1,…,fk is written by a method m if a
prefix f0,…,fj, j ≤ k, of this sequence in the APE graph for m,
and the edge for fj is labeled store
EJB field
Scenario
f0
o0
f1
f2
o2
o1
load
o4
o3
load
t
Field Sequences Written:
f0,f1,f2
f0,f1,f2,f3
Field Sequences Partially Written:
f0
f0,f1
f3
f2
store
o5
f3
o6
u
APE graph before statement t.f2 = u
16
Determining Whether a Field Sequence
May Be Read by a Method
• f0,f1,…,fk is read by a method m if this sequence is present in
the APE graph and the edge for fk is labeled with load
EJB field
f0
o0
f1
o1
f2
f3
o2
f4
o3
o4
o5
load
t
Field Sequences Read:
f0,f1,f2,f3
Field Sequences Partially Read:
f0
f0,f1
f0,f1f2
u
APE graph after statement u = t.f3
17
Action of the J2EE Security Analyzer
Bytecode
to be Analyzed
input
Static Analyzer
output
Points-to
Graph
input
Points-to Analyzer
Methods to Fields
output
& Access Modes
EJB Field
Sequences (R/W)
input
input
Roles to Methods
J2EE Access
Policy
J2EE Security
Analyzer
output
Roles
Methods
setGrade()
Student
Fields &
Access Modes
•grades
(write)
Inconsistencies/
Security Problems
Deployer / Analyst
Roles to Methods
to Fields &
Access Modes18
Computing Field Sequences Accessed
By EJB Methods
f0, f1
f0, f1
f0, f3, f5
read
m2
m1
partially read
f2, f3, f4
f2, f3, f4
f4, f2, f5, f7
f4, f2, f5,f7
f0
written
f0, f1
partially written
f0, f1
m3
read
partially read
f2, f3, f4
f2, f3, f4
written
EJB Methods
f2, f4, f5, f7
partially written
Field Sequences
(Read/Written)
19
Potential Inconsistencies Detected And
Reasons
•
1.
2.
3.
4.
An inconsistency may indicate
that:
Professor should have been
granted access to method m3
Professor should not have been
granted access to method m1
m1 contains a bug: it should not
have accessed field grades
m3 contains a bug: it should
have accessed another security
sensitive field, address
Professor
m1
m3
write
write
•grades
•ssn
•salary
•address
20
Current Access Control in J2EE
METHODS
ROLES
setGrade()
Professor
Student
getAllGrades()
Professor
Student
setData()
Professor
Student
22
Future Work
• Implement our technique as a tool
with a GUI that presents problems
to the analysts
• Implement a J2EE deployment
tool that allows a deployer to
specify role-based access control
policies in terms of fields, not
only methods
• The tool will convert
specifications based on fields to
specifications based on methods
using a dependency analysis
similar to the one described
• Experiment with a variety of Web
applications to evaluate the tool’s
usefulness
METHODS
ROLES
setGrade()
Professor
Student
getAllGrades()
Professor
Student
setData()
Professor
Student
FIELDS
READ
WRITE
grades
Professor
Student
Professor
Student
ssn
Professor
Student
Professor
Student
23
For More Information
• e-mail to:
gleb@poly.edu & paolina@photon.poly.edu
Thank you for you presence and participation!
26