Lecture 5 Group Communication
advertisement

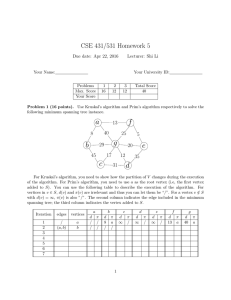
Lecture 5
Group Communication
Point to Multipoint
Communication
• Single source, Multiple Destinations
• Broadcast
–
1
2
All nodes in the network are destinations
• Multicast
– Some nodes in the network are destinations
• Only one copy of the information travels along
common edges
Message replication along forking points only.
• Normally, route of a session is a tree
– A tree is a portion of the graph without a cycle
(acylcic subgraph)
• A spanning tree is a tree which has all
vertices of the graph
• There may be multiple spanning trees
• We need to choose the minimum weight
tree for broadcast.
4
5
5
4
Blue edge spanning tree is
the minimum weight
spanning tree
Properties of a Tree
• A tree has V-1 edges
• There exists a unique path between any two
vertices of a tree.
• Adding any edge to a tree creates a unique
cycle. Breaking any edge on this cycle
restores a tree.
Minimum Spanning Tree
Construction
• We maintain a set of edges A, which is initially
empty.
• Edges are added to A one at a time such that
finally A becomes a minimum spanning tree.
• Edges are never removed from A.
• So ``safe’’ edges must be added to A, i.e., at any
stage A must be a part of a spanning tree.
Safe Edge Addition
• Consider a cut in a graph (a cut consists of
2 sets which partition the vertex set).
• A cut respects set A if no edge in A crosses
the cut.
• A minimum weight edge crossing a cut is
denoted a light weight edge in the cut.
• Let A be a subset of a MST (minimum
weight spanning tree).
• Let (S, V – S) be any cut that respects A
• Let edge (u, v) be a light edge crossing the
cut
• Then A (u, v) is subset of a MST
Assume that all the edge weights are distinct.
Let no MST containing A contain edge (u, v).
Consider a MST T containing A
Add the edge (u, v) to T
Since (u, v) is not in T, T
(u, v) contains a
cycle, and (u, v) is in the cycle.
Edge (u, v) are in the opposite sides of the cut.
Since any cycle must cross the cut even number
of times, there exists at least one other edge (x, y)
crossing the cut. Clearly, w(x, y) > w(u, v).
The edge (x, y) is not in A because (x, y) crosses the
cut, and the cut respects A.
Removing (x, y) from the cycle, breaks the cycle and hence
creates a spanning tree, T’, s.t. T’ = T
(u, v) – (x, y)
w(T’) = w(T) + w(u, v) – w(x, y)
w(T)
(as w(u, v) < w(x, y))
This contradicts the fact that T is a MST.
• So we always find a cut that respects A,
• And add a light edge across the cut to A.
• Kruskals and Prims algorithms find the cut
differently.
Kruskals Algorithm
•
1.
2.
3.
A=
For each vertex u in V, Create_Set(u)
Sort E in increasing order by weight w
For each edge (u,v) in the sorted list
–
If Set(u)= Set(v)
•
•
•
Add (u,v) to E
Union Set(u) and Set(v)
Return A;
Complexity Analysis
• The operations create set, testing whether set(u)
== set(v), union operations can be done in log V
operations, using Union find data structure.
• Step 1 can be done in Vlog V
• Step 2 can be done in Elog E
• Step 3 can be done in Elog V
• Overall complexity is O(Vlog V + Elog E + Elog
V) or O((V + E)log V)
1
7
7
8
2
0
2
5
2
5
1
2
2
7
8
1
2
0
2
1
7
2
0
5
5
7
5
5
8
2
0
0
1
2
8
5
5
8
5
5
Prims Algorithm
• Maintains a set of vertices S already in the
spanning tree.
• Initially, S consists of one vertex r, selected
arbitrarily.
• For every vertex u in V – S, maintain the weight
of the lightest edge between u and any vertex in S.
• If there is no edge between u and S, then this
weight associated with u is infinity.
• Add the vertex with the least weight to S.
• This is in effect adding the light weight
edge crossing the cut S and V-S.
• Whenever a vertex is added to S, the
weights of all its neighbors are reduced, if
necessary.
Pseudo-Code
S=
For each u in V, key[u] =
Key[r] = 0
Pred[r] = NULL
While V = S
u = Extract_Min(V-S)
For each (v in Adj(u))
if (v not in S) key(v) = min(w(u, v), key(v))
and pred(v) = u
Add u in S
For each v in Adj[u]…. can be done in E
complexity
Rest of the loop can be done in V2 complexity
So, overall O(V2)
Using heaps we can solve in O((V + E)logV)
Example
1
7
s
8
3
0
2
5
3 1
s
0
7
2
5
2 5
s
3
0
2
5
2
s
5
8
3 1
5
3 1
7
1
3 8
7 1
7
3
0 2
2
5
8
3
5
2
2 5
5
1
3 1
1
3 8
5
5
5
8
5
s
0
7
8
5
5
s 7
0 2
2
Multicast
• Destination for a session is a subset of the
node set
• Need to find a minimum weight tree
spanning the source and the destinations
• Such a minimum weight tree is a steiner
tree
• This is a NP-complete problem
• We first consider the following decision
problem.
• Given a multicast group, find whether there
is a tree spanning the group of weight less
than a certain amount B
• Clearly the problem is NP
• We need to show that the problem is NPhard
Reduction
We will show that a known NP-hard problem can
be solved in polynomial complexity if the steiner
decision problem can be solved in polynomial
complexity
Exact cover by 3-sets is NP-hard
X = {x1, x2,……, x3p}, C={C1, C2,….. Cq}, Ci X , | |Ci|=3,
i=1,…..q
Is it possible to select some mutually disjoint subsets
from C such that their union is X?
This decision problem is NP-hard
We will show that if we have a subroutine to find out in
polynomial complexity whether a graph G has a tree of
weight less than 4p, then we can use the subroutine to
answer whether there is an exact 3-cover for the above
problem in polynomial complexity.
Construct a graph with vertices v, C1, C2,….. Cq , x1,
x2,……, x3p
Multicast group has source v and destinations x1,
x2,……, x3p
There is an edge from v to each of C1, C2,….. Cq , and
from Ci to xj if xj is in Ci
Every edge has weight 1
C1
v
C2
C3
C4
x1
x2
x3
x4
x5
x6
x7
x8
x9
x10
C1 = {x1 x2 x3}, C2 = {x4 x5 x8}, C3 = {x6x9 x10 }, C4 = {x3x7x10}
Let there be an exact 3-cover
Clearly it uses p Ci s, C1, C2, …..Cp (wlog)
The tree consisting of edges (v, C1), (v, C2), ….. (v, Cp), and
the edges from Ci to its constituents is a tree spanning the
multicast group.
This tree has weight 4p
So, if there is an exact 3-cover, then there is a steiner tree
of weight 4p
Let there be not be an exact 3-cover.
Consider the minimum weight multicast tree
connecting the source and the destinations.
Since the tree must span x1, x2,……, x3p , the intermediate
vertices Ci s in the tree must represent overlapping sets,
else these sets will constitute an exact 3-cover.
Also, none of these intermediate vertices have degree
more than 3.
It follows that there are at least p + 1 of them.
Thus the weight of the tree is at least 3p + p + 1 or 4p + 1
So there is no tree of weight 4p or less.
Thus the set has an exact 3-cover iff there is a tree of
weight 4p or less.
So, if we have a subroutine to find out in polynomial
time whether any graph has steiner tree of weight B or
less for any B, then we can use it to decide whether a
set has an exact 3-cover or not in polynomial time.
Hence, the steiner tree problem is NP-hard.
Approximation Algorithms
Approximation algorithms are used for
providing approximate solutions to NP-hard
problems in polynomial complexity.
Suppose, we are trying to minimize a quantity.
An approximation algorithm is one which
guarantees a solution which is at most k
times the minimum value, where k is a
constant. This constant is the approximation
ratio.
An approximation algorithm for
Steiner Tree
Start with any vertex in the multicast group.
Choose another vertex in the multicast group, which is
closest to the first vertex and add the shortest path between
the two to the tree (which is now empty).
Choose that vertex of the multicast group which is
closest to the tree (distance between a vertex and a
tree is the minimum distance between the vertex
and a node in the tree).
Augment the tree by the shortest path between
the vertex and the tree.
Repeat this procedure till all vertices of the multicast
group are in the tree.
The resulting tree has weight at most (2 – 2/n)
times the minimum weight tree, where n is the
number of vertices in the tree.
Intuitive Argument
Consider a walk around the steiner tree travelling
every edge twice.
Weight of the walk is 2 times
that of the steiner tree
Remove the longest terminal
terminal path
z4
z2
z5
z7
z6
z1
z3
z8
Weight of the longest terminal to terminal path is at
least 2/n the weight of the steiner tree, n is the number
of members in the multicast group (source +
destination)
Weight of the remaining portion of the walk is at
most (2 – 2/n) the weight of the steiner tree.
Weight of the approximate tree is at most the weight of
the remaining part of the tree
It is possible to partition this portion into disjoint
paths Lk, connecting terminals of index less than k
to terminals of index greater than or equal to k
Clearly, Lk is not less than the shortest path to
index k.
Given any , there exists a graph for which the
algorithm will give a tree greater than 2 - times the
weight of the steiner tree.
Counter Example
1+
1+
1+
2
1+
2
2
Green vertices are in the multicast group
The algorithm chooses the red tree and hence has n – 1 edges of
weight 2. Total weight is 2n - 2
The optimal tree consists of only the 1 +
edges, and hence has weight n(1 + )
As goes to 0, the ratio goes to 2-2/n, greater than
2 - for sufficiently small .
There are approximation algorithms which
give an approximation ratio of 11/6 or 16/9
However, the approximation ratio is a worst
case ratio. Generally, the minimum path
heuristic performs much better than the
approximation ratio of 2.
``The Steiner Tree Problem’’, F. Hwang, D.
Richards and P. Winter
Internet Multicast Routing
• Multicast groups
– All multicast receivers constitute the multicast group
• Every group has a unique IP address
• Source sends packets to the group address
• Multicast capable routers forward on appropriate
links
• Receivers join and leave groups dynamically
• Source may not know the constitution of the group
Multicast Routing Protocols
• Source based Protocols
– Multicast trees consist of shortest paths between source
and the receivers
• Distance vector multicast routing
protocols(DVMRP)
– Shortest paths are constructed based on unicast distance
vector algorithms
– S. Deering, C. Patridge, and D. Waitzman, ``Distance
Vector Multicast Routing Protocol’’, RFC 1075, Nov.
1988
• Multicast open shortest path protocols
(MOSPF)
– Shortest paths are constructed based on link
state protocols
– J. Moy, ``OSFP version 2’’, Internet RFC 1247,
p. 189, July 1991
Group Shared Trees
• Source based trees suffer from scalability problem.
• A multicast group may consist of several
members.
• Each member may potentially be a source and a
receiver (video teleconferencing)
• Intermediate routers need to maintain separate
trees for every source (O(n) memory, where n is
the number of members in the group)
• Instead, there can be a single tree per group (group shared
tree)
• There is a core node in the tree
• Every source sends its packet towards the core node.
• The core node sends the packets towards all the receivers.
• The core node uses shortest paths to all the receivers.
• Memory scales with number of groups and not ``that
much’’ with the number of group members.
Group Shared Protocols
• Core Based Trees
– T. Ballardie, ``Core Based tree (CBT) multicast:
Architectural Overview and specification,’’ Internet
Draft RFC, July 1994
• Protocol Independent Multicast (PIM)
– S. Deering, D. Estrin, D. Farinacci, V. Jacobson, C. Liu
and L. Wei, ``Protocol Independent Multicast (PIM):
Protocol Specification,’’ Internet Draft, RFC, Jan 11,
1995
• Group shared trees are scalable, but they
suffer from congestion because the entire
traffic is concentrated in the core node, and
the protocol stops functioning if the core
fails.
• PIM switches between group shared and
source based trees on an ``on demand’’
basis
• PIM starts with group shared trees.
• Particular receivers may request source specific
trees
• In the event of request, PIM switches to source
based trees for the requesting receivers.
• Both PIM and CBT are ``protocol independent’’ as
they can acquire distance information from any
underlying unicast protocol, e.g., OSPF, Distance
vector protocols etc.
Multicast specific Issues
• Heterogeneity
– Different receivers of the same session have
different QoS requirements and different pah
bandwidths
• Scalability
– Routing
– Reliable Multicast
– Multicast Security
•
•
Varying path capacities, e.g.
Varying receiver processing capabilities
u1
ISDN
(128 kbps)
T3 (45 Mbps)
v
Ethernet (100Mbps)
T3 (45 Mbps)
Modem
(28.8 kbps)
u2
u3
u4
A single rate of transmission for all members
of the session is not sufficient
Multirate Transmission
• Normally used for loss tolerant real traffic like
audio, video transmission.
• Different receivers of the same session can receive
different rates
• Transmission rate of a session in a link is the
maximum of the rates of the receivers downstream
• Layered transmission of loss tolerant traffic in the
internet
– Source encodes signal into multiple layers.
– Lowest layer gives basic information.
– Reception of subsequent layers gives better reception
quality.
Multirate Multicast Transmission
r = max (r3,, r4)
r3
S
r1
r4 = max (r1,, r2)
r2
Fractional layer reception meaningful: Continuous bandwidth reception
L4
L3
L2
L1
r3
r2
r1
Multirate Multicast Transmission
r = max (r3,, r4)
r3
S
r1
r4 = max (r1,, r2)
r2
Fractional layer reception not meaningful: Discrete bandwidth reception
L4
L3
L2
L1
r3
r2
r1
NETWORK MODEL
• N sessions
• One predetermined route for each session
• M virtual sessions
– Every receiver of every session is a distinct virtual
session
u1
ISDN
Ethernet (100Mbps)
(128 kbps)
T3 (45 Mbps)
v
T3 (45 Mbps)
Modem
(28.8 kbps)
u2
u3
u4
Virtual sessions: (v, u1), (v,u2), (v,u3), (v,u4)
• Minimum rate requirements of virtual
sessions
– QOS requirements
• Maximum rate constraints of virtual
sessions
Feasible Set
• rji is the rate allocated to the jth virtual session
of the ith session
• Rate allocation vector: (r11,….rt1,....,r1N,…ruN)
1,….r 1,....,r N,…r N):
=
{(r
1
t
1
u
• Feasible Set:
max
i: session i
traverses link l
m r
i
i
j
j
r ji
Cl
j: virtual session j of
session i traverses link l
p
i
j
(Capacity Constraint)
(minimum, maximum rate constraint)
Good operating point in the feasible region
Capacity Constraint For Unicast
Case
ri
Cl
i: session i
traverses link l
(Capacity Constraint)
Homework! Formulate the feasible set for a single rate
multicast problem, under the assumption that there is a
single predetermined tree for every session
Show that given any multicast network with M virtual
sessions, there exists a unicast network with M sessions
such that every feasible vector in the multicast network,
is a feasible vector in the unicast network