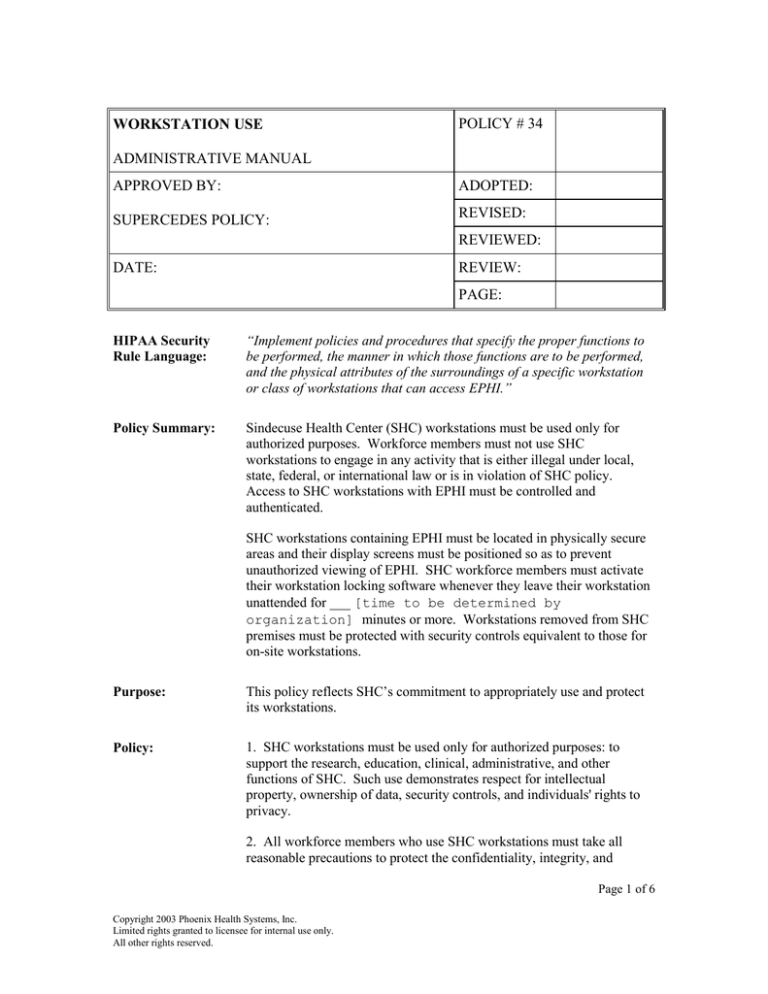
WORKSTATION USE
POLICY # 34
ADMINISTRATIVE MANUAL
APPROVED BY:
ADOPTED:
SUPERCEDES POLICY:
REVISED:
REVIEWED:
DATE:
REVIEW:
PAGE:
HIPAA Security
Rule Language:
“Implement policies and procedures that specify the proper functions to
be performed, the manner in which those functions are to be performed,
and the physical attributes of the surroundings of a specific workstation
or class of workstations that can access EPHI.”
Policy Summary:
Sindecuse Health Center (SHC) workstations must be used only for
authorized purposes. Workforce members must not use SHC
workstations to engage in any activity that is either illegal under local,
state, federal, or international law or is in violation of SHC policy.
Access to SHC workstations with EPHI must be controlled and
authenticated.
SHC workstations containing EPHI must be located in physically secure
areas and their display screens must be positioned so as to prevent
unauthorized viewing of EPHI. SHC workforce members must activate
their workstation locking software whenever they leave their workstation
unattended for ___ [time to be determined by
organization] minutes or more. Workstations removed from SHC
premises must be protected with security controls equivalent to those for
on-site workstations.
Purpose:
This policy reflects SHC’s commitment to appropriately use and protect
its workstations.
Policy:
1. SHC workstations must be used only for authorized purposes: to
support the research, education, clinical, administrative, and other
functions of SHC. Such use demonstrates respect for intellectual
property, ownership of data, security controls, and individuals' rights to
privacy.
2. All workforce members who use SHC workstations must take all
reasonable precautions to protect the confidentiality, integrity, and
Page 1 of 6
Copyright 2003 Phoenix Health Systems, Inc.
Limited rights granted to licensee for internal use only.
All other rights reserved.
WORKSTATION USE
availability of EPHI contained on the workstations.
3. Workforce members must not use SHC workstations to engage in any
activity that is either illegal under local, state, federal, or international law
or is in violation of WMU or SHC policy.
4. Activities that workforce members must not perform while using SHC
workstations include, but are not limited to:
Violations of the rights to privacy of protected healthcare
information of SHC’s patients.
Violations of the rights of any person or company protected by
copyright, trade secret, patent, or other intellectual property or
similar laws or regulations. This includes, but is not limited to,
the installation or distribution of "pirated" or other
inappropriately licensed software products.
Unauthorized copying of copyrighted material, including but not
limited to digitization and distribution of photographs from
magazines, books, or other copyrighted sources and copyrighted
music.
Purposeful introduction of malicious software onto a workstation
or network (e.g., viruses, worms, Trojan horses).
Actively engaging in procuring or transmitting material that is in
violation of WMU sexual harassment or hostile workplace
policies.
Making fraudulent offers of products, items, or services.
Purposefully causing security breaches. Security breaches
include, but are not limited to, accessing electronic data that the
workforce member is not authorized to access or logging into an
account that he or she is not authorized to access. SHC
employees that perform this activity as part of their defined job
are exempt from this prohibition.
Performing any form of network monitoring that will intercept
electronic data not intended for the workforce member. SHC
employees that perform this activity as part of their defined job
are exempt from this prohibition.
Circumvent or attempt to avoid the user authentication or
security of any SHC workstation or account. Employees that
perform this activity as part of their defined job are exempt from
this prohibition.
5. Access to all SHC workstations containing EPHI must be controlled
with a username and password or an access device such as a token.
6. Access to all SHC workstations with EPHI must be authenticated via a
process that includes, at a minimum:
Unique user IDs that enable users to be identified and tracked.
Group IDs may only be used to access SHC workstations not
Page 2 of 6
Copyright 2003 Phoenix Health Systems, Inc.
Limited rights granted to licensee for internal use only.
All other rights reserved.
WORKSTATION USE
containing EPHI.
The prompt removal of workstation access privileges for
workforce members who whose employment or contracted
service with SHC has ended.
Verification that redundant user IDs is not issued.
7. All password-based access control systems on SHC workstations must
mask, suppress, or otherwise obscure the passwords so that unauthorized
persons are not able to observe them.
8. SHC workforce members must not share passwords with others. If a
SHC workforce member believes that someone else is inappropriately
using a user-ID or password, they must immediately notify the
Information Systems manager.
9. Where possible, the initial password(s) issued to a new SHC
workforce member must be valid only for the new user's first logon to a
workstation. At initial logon, the user must be required to choose another
password. Where possible, this same process must be used when a
workforce member’s workstation password is reset.
10. SHC workstations containing EPHI must be physically located in
such a manner as to minimize the risk that unauthorized individuals can
gain access to them.
11. The display screens of all SHC workstations containing EPHI must
be positioned such that information cannot be readily viewed through a
window, by persons walking in a hallway, or by persons waiting in
reception, public, or other related areas.
12. WMU Information Security office approved anti-virus software must
be installed on workstations to prevent transmission of malicious
software. Such software must be regularly updated.
13. SHC workforce members must activate their workstation locking
software whenever they leave their workstation unattended for ___
[time to be determined by organization] minutes or
more. SHC workforce members must log off from their workstation(s)
when their shifts are complete.
14. Connections from one workstation to another computer must be
logged off after the session is completed.
15. Workstations removed from SHC premises must be protected with
security controls equivalent to those for on-site workstations.
16. Special precautions must be taken with portable workstations such as
laptops. The following guidelines must be followed with such systems:
Page 3 of 6
Copyright 2003 Phoenix Health Systems, Inc.
Limited rights granted to licensee for internal use only.
All other rights reserved.
WORKSTATION USE
EPHI must not be stored on a portable workstation unless such
information is appropriately protected. SHC security office
approved encryption should be used.
Locking software for unattended laptops must activate after
______ [time to be determined by
organization] minutes.
SHC portable workstations must be carried as carry-on (hand)
baggage when workforce members use public transport. They
must be concealed and/or locked when in private transport (e.g.,
locked in the trunk of an automobile).
Scope/Applicability: This policy is applicable to all departments that use or disclose electronic
protected health information for any purposes.
This policy’s scope includes all electronic protected health information,
as described in Definitions below.
Regulatory
Category:
Physical Safeguards
Regulatory Type:
Standard
Regulatory
Reference:
45 CFR 164.310(b)
Definitions:
Electronic protected health information means individually identifiable
health information that is:
Transmitted by electronic media
Maintained in electronic media
Electronic media means:
(1) Electronic storage media including memory devices in computers
(hard drives) and any removable/transportable digital memory medium,
such as magnetic tape or disk, optical disk, or digital memory card; or
(2) Transmission media used to exchange information already in
electronic storage media. Transmission media include, for example, the
internet (wide-open), extranet (using internet technology to link a
business with information accessible only to collaborating parties), leased
lines, dial-up lines, private networks, and the physical movement of
removable/transportable electronic storage media. Certain transmissions,
including of paper, via facsimile, and of voice, via telephone, are not
considered to be transmissions via electronic media, because the
information being exchanged did not exist in electronic form before the
Page 4 of 6
Copyright 2003 Phoenix Health Systems, Inc.
Limited rights granted to licensee for internal use only.
All other rights reserved.
WORKSTATION USE
transmission.
Information system means an interconnected set of information resources
under the same direct management control that shares common
functionality. A system normally includes hardware, software,
information, data, applications, communications, and people.
Workforce member means employees, volunteers, and other persons
whose conduct, in the performance of work for a covered entity, is under
the direct control of such entity, whether or not they are paid by the
covered entity. This includes full and part time employees, affiliates,
associates, students, volunteers, and staff from third party entities who
provide service to the covered entity.
Workstation means an electronic computing device, for example, a laptop
or desktop computer, or any other device that performs similar functions,
and electronic media stored in its immediate environment.
Virus means a piece of code, typically disguised, that causes an
unexpected and often undesirable event. Viruses are frequently designed
to automatically spread to other computers. They can be transmitted by
numerous methods: as e-mail attachments, as downloads, and on floppy
disks or CDs.
Worm means a piece of code, usually disguised, that spreads itself by
attacking and copying itself to other machines. Some worms carry
destructive payloads that delete files or distribute files; others alter Web
pages or launch denial of service attacks.
Trojan horse means a program in which malicious or harmful code is
contained inside apparently harmless programming or data.
Authentication means the corroboration that a person or entity is the one
claimed.
Password means confidential authentication information composed of a
string of characters.
Token means a physical device which, together with something that a
user knows, will enable authorized access to an information system.
Anti-virus software means software that detects or prevents malicious
software.
Responsible
Department:
Supervisors; Information Systems
Policy Authority/
SHC’s Security Official is responsible for monitoring and enforcement of
Page 5 of 6
Copyright 2003 Phoenix Health Systems, Inc.
Limited rights granted to licensee for internal use only.
All other rights reserved.
WORKSTATION USE
Enforcement:
this policy, in accordance with Procedure # (TBD).
Related Policies:
Workstation Security
Renewal/Review:
This policy is to be reviewed annually to determine if the policy complies
with current HIPAA Security regulations. In the event that significant
related regulatory changes occur, the policy will be reviewed and updated
as needed.
Procedures:
TBD
Page 6 of 6
Copyright 2003 Phoenix Health Systems, Inc.
Limited rights granted to licensee for internal use only.
All other rights reserved.