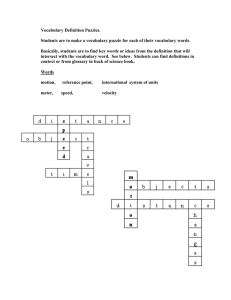
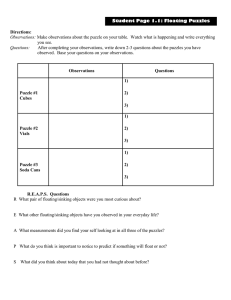
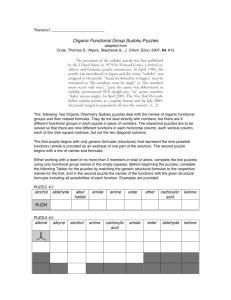
New Client Puzzle Outsourcing Techniques for DoS Resistance
advertisement

New Client Puzzle Outsourcing Techniques for DoS Resistance Brent Waters, Stanford University Ari Juels, RSA Laboratories Alex Halderman, Princeton University Ed Felten, Princeton University Client Puzzles • DoS attack the attackers consume resources quickly • May not be enough resources left for a regular client Attackers Server Request Request Request Request Request User Request Client Puzzles • • Client puzzles slow down an attacker by making him solve a moderately hard challenge before granting a resource Typically, partially invert a hash function Attackers Server Request y,z x, where H(x|y)=z User Request y’,z’ x’, where H(x|y)=z Client Puzzles Client Puzzles can potentially be used to protect many different kinds of resources – – – – Email SPAM [DN’92] TCP SYN buffers [JB’99] CPU on SSL connections [JB’99, DS’02] Database Queries • Resource intensive queries • DRM? – IP packets Shortcomings of Client Puzzles 1) Puzzle-solving delay after user request – User must wait for his machine to solve puzzle – Is this a problem? [JB’99] show 1s delay for TCP syn buffer… – However, they do their analysis under 20 attackers – Lesson: Delay depends upon number of attackers and scarcity of resource Shortcomings of Client Puzzles 2) Server hash computation per submitted solution – Hash overhead ~1us computation time – Typically small relative to resource given – Attack by flooding server with incorrect solutions – Impractical if protecting a low level service such as IP layer Our Solution • Outsource puzzle creation – Puzzles created are independent of client or server using them • Solve for access to “channels” on servers – Assume internal routing structure is resistant to eavesdropping Outsourcing Puzzles • Bastion service distributes puzzles – Global Service – Bastion operation is independent of servers and clients using it Scalability 1 2 N Outsourcing Puzzles • Since puzzles are independent of bastion can use robust systems to distribute puzzles • Leverage point 1 2 N Solving for Channels • Client solves for a random channel • Next time period uses solved channel as solution • Solution can be transformed to work on any server Time 507 1 2 N Solving for Channels • Client solves for a random channel • Next time period uses solved channel as solution • Solution can be transformed to work on any server Time 507 507 Solving for Channels • Client solves for a random channel • Next time period uses solved channel as solution • Solution can be transformed to work on any server Time Server A check PKA Server B B 507 507 507 PK 1 507 check 1 507 Attackers and Channels • Attacker can only get resources allotted to channels he has solved puzzles for Attackers 157 678 PKA 157 678 Server A 157 507 678 PKA 507 507 Puzzle Construction • • • • N Channels P(x,d): Puzzle hiding x of difficulty d H : Hash function xi : Randomly chosen each iteration Puzzle for channel i 1 2 Public Key of Server A Xi=gx mod p, P(xi,d) i Y=ga N H(gax ) i Token for channel i on server A Client and Server Operation Time j-1 Client j j+1 Solve puzzle for period j+1 • Pick random channel • Solve puzzle for channel Use solution computed during period j-1 •Have solution xi for channel i •For server with public key Y=ga compute Yx =gax as token for channel i i i Server Compute all N tokens for period j+1 • Public key = ga • For all Xi=gx compute Xia =gax i i •Use tokens computed during period j-1 •Request on channel i, do a quick comparison on token list •Keep track of resources granted per channel Key Points • User does not wait for puzzle to be solved • Bytestring comparison per claimed solution • Primary bottleneck is # of channels the server computes tokens for (exponentiations) – Will improve as processor speeds increase – Can give out Xi before Puz(xi,d) An Example Time cycles of 20 minutes N=20,000 channels ~5% of a high end server’s computing time Set puzzle difficulty so typical machine can have 2 solutions 1,000 attackers with 1,000 solutions; 1/10 of channels Regular user has 2 random channels each 10% chance of being occupied by adversary 1% that both are occupied Prototype Implementation Rate limits number of new TCP connections After SYN packet must wait n seconds before another on channel Sends two previously computed tokens 48 SYN 167 48 298 HTTP Server to simulate Bastion Flooding Attack Experiment Attacker submits several false solutions Comparison to Traditional Client Puzzles Our Approach • Proactive approach; solves puzzles in preparation Traditional Client Puzzles • Enter client puzzle operation in reaction to an attack – Uses resources when not under attack (server & client) • Solution is ready immediately for user request •User waits for client to solve • Bitstring comparison per claimed solution •Hash computation per claimed solution – IP layer Comparison to Traditional Client Puzzles Our Approach • Use solutions at multiple protocols (e.g. TCP, SSL, Database queries) • Number of channels available should increase as servers can do PK operations faster Traditional Client Puzzles • Unclear how should manage protecting multiple protocols Extensions • Identity-Based server public keys • More flexible number of channels per server • Random Beacon for Bastion – Loose universal puzzle property • More efficient PK crypto – Smaller key sizes (key life is shorter) Conclusions • Propose a new client puzzle outsourcing technique for protecting against DoS attacks • Trade off extra average case effort in exchange for low-user delay and efficient solution verification