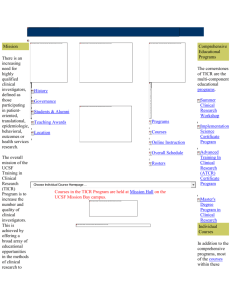
University of California Establishing a Data Security Compliance Program
advertisement

University of California 2015 Sautter Award Application Establishing a Data Security Compliance Program 1. Project title: UCSF Data Security Compliance Program - Establishing a culture of compliance 2. Submitter’s name, title, and contact information: Patrick Phelan Information Security Officer | Director of IT Security University of California San Francisco patrick.phelan@ucsf.edu | 415-502-0782 | http://it.ucsf.edu/security 3. Names of project leader(s) and team members: IT Security: Patrick Phelan, Toby Barber, Timothy Hoffman, Christine Ziegler, Joe Bengfort. These are 60 of the core participants – we consider them the project leaders. Dozens more were active in the planning and execution of the compliance activities. Clinical Labs (CL): Enrique Terrazas, James Reese; Langley Porter Psychiatric Institute (LPPI): Ann Saggio, Laverne Tarpley; Library & Center of Knowledge Management (LIB): Rich Trott; Medical Center (MC): Carrie Meer, Kevin Pattison, Brigid Ide, Tim Mahaney, David Steinmetz, Michael Skehan, Russ Cucina, Sunny Bang, David Morgan, Shirley Kedrowski; Office of VC, Finance & Administration (FAS): Jane Y. Wong, Cindy Yoxsimer, School of Dentistry (SOD): Tom Ferris, Tommy Kwong; School of Medicine (SOM): Chris Orsine, Ed Martin; School of Nursing (SON): David Kell, Doug McCracken, Mattice Harris; School of Pharmacy (SOP): Michael Nordberg, Valerie Starling, Student Academic Affairs (SAA): Doug Carlson, Kevin Yeung; University Development, Alumni Relations (UDAR): Jansen Lowe, Sushmita Sharma, Wanda Ware; Enterprise (IT): Karen O'Neill, Sian Shumway, Jane Wong, Pierre Brickey, Irene Brezman, Patrick Phelan, Andrew Clark, Quinn Hearne, Esther Silver, Jesse Anderson, John Arbolino, Mark Day, Greg Lennon, Manish Sompura, Kevin Dale, Kristina Mariscal, Christian Sisenstein, Toby Barber, Jann Fong, Rebecca Nguyen, Kevin Barney, Sarah Mays. 4. Project description: Technology utilized in the project IT Security risk management frameworks and regulatory guidance; risk profile calculation and tracking tools; technical test discovery tools. Timeframe of implementation October 2013 – April 2015 Files/exhibits Available on request Project Drivers included compliance with regulatory requirements, hardening of infrastructure Applicable Regulations and Standards HIPAA Security Rule, HITECH Act, Family Educational Rights and Privacy Act (FERPA), California Security Breach Information Act (S.B. 1386), Payment Card Industry (PCI), UC Office of the President Business Finance Bulletins, UCSF policies and many other laws, standards and frameworks. Document1 1 of 5 University of California 2015 Sautter Award Application Establishing a Data Security Compliance Program Establishing a Data Security Compliance Program At UCSF we have established a Data Security Compliance Program (DSCP) to address the HIPAA Security Rule and other regulations including the HITECH Act, Family Educational Rights and Privacy Act (FERPA), California Security Breach Information Act (S.B. 1386), Payment Card Industry (PCI), UC Office of the President Business Finance Bulletins, UCSF policies and many other laws, standards and frameworks. The DSCP is charged with ensuring UCSF implements and maintains the security controls required by these laws and regulations. In 2013-2014, UCSF retained Accuvant LABS to conduct an enterprise IT security risk assessment. The assessment covered 142 unique controls that must be satisfied by all 12 administrative control points, which include the schools, medical center, central IT and all of their departments, divisions and programs. The DSCP team is working with these control points to fill gaps and address findings identified in the 2013-2014 Enterprise Risk Assessment. All of the control points have been given recommendation plans for each risk identified. In some cases the recommendations can be addressed by the control point directly, while in other cases the risk identified belongs to the enterprise as well as the control point, and as such, a joint effort is required to satisfy the recommendation. The program is sponsored by UCSF Deans, Chancellors, and Executives including the CEO and CIO who championed and funded the enterprise-wide effort to review and reinforce security controls across the entire UCSF Medical Center and Campus. The program is founded on IT Security Risk Management principles and controls commonly recommended across NIST, SANS, ISO 27K, COBIT, PCI and many other frameworks. While HIPAA, FERPA, PCI and other regulations are long instituted and familiar to most at UCSF, leadership and staff wanted to refresh operating procedures and bring data security to top of mind for all employees, faculty, educators, researchers and care givers. Document1 2 of 5 University of California 2015 Sautter Award Application Establishing a Data Security Compliance Program The strategic objectives of the program are to: Improve UCSF IT security posture Empower business units to identify and remediate risks Assist in prioritizing remediation tasks Educate the organization regarding real threats and weaknesses Increase visibility and capability to track risks Improve the consistency of risk assessment approaches Establish a common formula for risk evaluations Meet audit and regulatory requirements, and customer expectations that we protect their information Cross-functional collaboration Once the interviews were completed in winter 2013 - spring 2014, UCSF control points were given their final deliverables. All five deliverables were customized by control point. Risk Assessment Executive Summary Reports: Provided overview of the risk assessment and the key risks and areas of concern. The report recommends remediation as short or long term goals. Risk Assessment Detailed Findings Reports: Provided the control point a detailed report of information about the process used and discrete risks identified during the risk assessment. Gap Tracker: Provided a detailed assessment of compliance with each compliance control including HIPAA Security, FERPA, & California SB1386. Risk Analysis: Provided ownership mapping of each risk to the control point, enterprise, or both. Impact and likelihood of occurrence are assigned to each risk and risk scores are documented. Final Presentation: Presentations included context of risk assessments, consequences of ignoring data security related risks, and recommendations on priority of remediation actions. With these tools in hand, people stepped up to the work of remediating gaps. Between July and October 2014, the Data Security Compliance Program team reached out to more than 60 core participants – we consider the participants “champions” and “task leaders”. Dozens of additional technical and business staff were drawn in to the planning and execution of the remediation activities. The scale of the effort was massive: roughly 30,000 workforce members who somehow interact with UCSF technology resources, including PHI, PII, sensitive or restricted data. We had to communicate the information that would help secure the humans. We had to convey necessary business practice type guidance. Simultaneously, we planned, funded and began implementation of technical controls by reaching administrators, developers and other resource proprietors who could assist with securing the environments. Plan the work – work the plan Program goals were laid out in spring 2014. In the year that followed, the DSCP experienced unprecedented momentum and incredible success. The table below outlines the milestone activities including their general start and end dates. Document1 3 of 5 University of California 2015 Sautter Award Application Establishing a Data Security Compliance Program Milestone Activities Enterprise Risk Assessment Brief Description 12 control points, 408 individuals interviewed, 120 documents reviewed; 6 data rooms visited' 200+ applications assessed Start 01/01/14 Complete 07/01/14 Distribute Final Deliverables 5 deliverables prepared for each of the 12 control points; technical test report; applications inventory 04/01/14 07/31/14 Assign Enterprise DSCP Program Manager Temporary and permanent staff were identified to develop and then sustain the data security compliance program. 04/01/14 07/01/14 Assemble and Distribute Control Point Training Materials Assign Control Point Champions Over 30 individuals participated in 2-hour data security risk management training. 04/01/14 07/30/14 Director, manager and staff commitment was obtained from each control point. Garnering bottom-up and peer-to-peer support. 05/01/14 07/31/14 Create Control Point Communication Plans More than 60 control point champions and task leads were drawn in to the data security compliance program. 07/01/14 08/01/14 Conduct Senior Leadership Roadshow Leadership commitment was obtained for each control point. Securing top down support. 04/01/14 08/31/14 Schedule and Hold Kickoff Meetings Roughly 30 meetings, working sessions and phone calls were held to on board, orient, train and update the participants. 07/01/14 10/01/14 Control Points Prepare Risk Management Plans Each control point prepared risk response plans to address each of their 8-12 priority group findings (recommendations related to 142 controls grouped in themes) 08/01/14 12/31/14 Report Control Point Results to Privacy Office Findings and progress were shared with the UCSF Privacy Office and Ethics and Compliance Board 10/01/14 12/31/14 DSCP Return Comments on Mitigation Plans to Control Points Control points submitted plans, discussed with DSCP, compared notes on enterprise solutions that would cover their gaps, common controls, etc. 09/01/14 03/31/15 Bi-monthly Progress Reporting Informal check points as well as scheduled status reporting sessions were held with DSCP and control points. UCSF-wide status published bimonthly 10/01/14 10/31/14 04/01/14 02/28/15 Budget Planning for Risk Assessment Remediation Data security compliance activities are being organized by IT Security and executed by hundreds of workforce members across UCSF. During the assessment phase over 400 interviews were conducted and hundreds of systems and documents were reviewed. The energy carried through technical testing and remediation of the findings; as a result, UCSF closed numerous high profile gaps in first year of the program. The focus was on building momentum by developing a multifaceted strategy involving estimating and securing staff, and starting the work. Realizing that “perfect is the enemy of the done”, we are taking action whether the plan was perfect or not. The result of the program has been first year mitigation plans that set scope, priority, and strategy for addressing findings from the initial assessment. In many cases the control points have also prepared detailed work plans for managing the more complex projects. The champions are assembling workgroups to simplify and streamline remediation efforts as well as share solutions. Business and Document1 4 of 5 University of California 2015 Sautter Award Application Establishing a Data Security Compliance Program technical teams are executing the work; they are implementing control technologies, procedures and other solutions. As they progress, they are ensuring that they are set up to collect evidence of compliance. Progress amidst competing priorities One of the amazing things about the creation of the Data Security Risk Management Program at UCSF is that the progress took place amidst the most demanding of competing priorities. All of the work was completed in the same years that UCSF prepared for the national Affordable Care Act / Covered California (via the WellPoint contract) and stood up the technology infrastructure at the Mission Bay Hospital. UCSF compliance staff operated on the premise that there was always something else we could move forward on without taking key staff attention away from mission critical work. We developed a compliance infrastructure, built relationships, and developed seemingly small but helpful items such as template, samples and pre-populated accelerators. We “practiced” with the least busy and caught the saturated in 10-30 minute increments. Another key factor to our success was the top-down, middle-middle, and bottom-up approaches applied consecutively, not as gates one to another. The executive road show was well received and firm sponsorship was established. Technology for the journey The DSCP is managed largely with spreadsheet tools that capture regulatory controls, assessment results, gaps and recommendations. The tools also support risk ranking and prioritization and will be used later to adjust to residual risk levels as remediation of the risk item is confirmed. Although we will be moving to a GRC software tool as the program matures, we believe that a DSCP program can be successfully managed using simple Microsoft Office-based tools. The value of the program The DSCP program has already allowed UCSF to measurably reduce its risk profile. In it we have established a repeatable framework for future assessments and ongoing risk management. Importantly, we have also established the foundation for a new culture of compliance at UCSF. Our investment in dedicated resources is bringing security and value to UCSF. Continuing to execute and mature this program will: Protect customer data against technology-related security breaches Establish a posture that is proactive and prepared Reduce risk and demonstrate due diligence (minimize OCR fines, protect reputation) Strengthen relationships and heighten awareness among IT service providers. Address HIPAA requirements by standardizing on the National Institute for Standards and Technology (NIST) control framework Document1 5 of 5