Just Enough SAS to Identify Yourself in a
advertisement

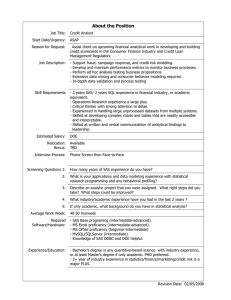
Article & Slides: www.idiom.com / ~sherman / paul / pubs / netcmd Just Enough SAS to Identify Yourself in a Networked World Paul Sherman Na Li Overview • What’s wrong with networking • Topology • Authentication Process • Pitfalls • The net.exe command • Example • A %netauth utility macro What’s Wrong With Networking • Permission denied. • Access is denied. • Lost connection ( Re-boot and forget to re-map? ) • But it runs on my local PC! The Network is Your Friend • Time, Share & Use – in a single command • %sysexec() “x” gets you to DOS prompt • Everything has a UNC path: \\ Host name \ Share name \ file system path • Tell %netauth() whenever you need to CONNECT or DISCONNECT a remote host Network Topology Domains • • • • Typical of many large corporate intranets Managed centrally Easier to administrate Synonymous access to all hosts BIOMETRIC MARY JEFF JLO CODCORDC01 PDC codcor.psug.org EFFICACY CRFPROT SAFETY Network Topology Workgroups • • • • • Small labs and home offices Managed individually Cumbersome to administrate Easier to develop applications within Less prone to system-wide failures MARY CRFPROT JEFF JLO BIOMETRIC EFFICACY SAFETY The Authentication Process • Client contacts Domain Controller (DC) • DC forwards request to host • Host responds to DC with accept or deny • DC grants access to Client • Client & Host can now communicate Workgroup The Authentication Process CLIENT Domain CLIENT proceed grant auth proceed grant auth HOST HOST respond DOMAIN CONTROLLER PDC request Pitfall #1 A Word About Scope Get Close Pitfall #1 John A Word About Scope map G: copy g:\raw.sd2 c:\ copy c:\ae.prn g:\ C:\user\john\sas ae.prn CRFPROT Mary raw.sd2 G: marydat.sd2 map G: copy g:\marydat.sd2 c:\ SAFETY marydat.sd2 ae.prn C:\user\mary\sas\dev John’s code (a) Fails (b) Writes output where it doesn’t belong (c) All of the above Pitfall #1 More Words of Scope • Network resources are global to all users • Avoid absolute drive letter mappings • Use “UNC” path references, always John: net use \\safety\c$\user\john\sas /user:john j Mary: net use \\safety\c$\user\mary\sas\dev /user:mary m Pitfall #2 Credential Conflict net use \\crfprot\ib /user:jeff j Read-only Jeff auth. Jeff BIOMETRIC Melissa auth. Melissa CRFPROT Read & Write net use \\crfprot\ib /user:melissa m This set of credentials conflicts with an existing set of credentials Pitfall #2 Avoiding Credential Conflict • Schedule remote jobs synchronously, or • Use dotted-decimal addressing net use \\crfprot\ib /user:jeff j net use \\1.2.3.4\ib /user:melissa m ping the host to find its dotted-decimal address Pitfall #3 The Case of the Wrong Case Jeff 123-45-6789.doc Permission Denied BIOMETRIC net use \\biometric\patprof\peopledata /user:jeff j copy c:\123-45-6789.doc \\biometric\PatProf\PeopleData Be careful with case in Auth & Usage ! Networking “Best Practice” • • • • Separate “Auth” and “Usage” tasks Assert credentials with IPC$ virtual share Work with remote host as normal De-auth the IPC$ share when finished net use \\safety\ipc$ /user:melissa m copy \\safety\ae\x.prn \\safety\lab\x.prn del \\safety\logs\myprog.txt net use \\safety\ipc$ /d The net.exe Command • Part of Windows since Win95 Check & Sync time C:\> net time C:\> net view C:\> net use Query shares & volumes Mount & Unmount drives Example Synchronizing Time John 2:43 PM 3:06 PM EFFICACY 3:06 PM x ”net time \\efficacy.psug.org /set /y”; Example Learning to Share Mary EFFICACY demog survival response net view \\efficacy.psug.org Using %netauth() • Send message at start & end of remote work • Be careful with case of host, share and path %netauth(CONNECT); x “net time \\host /set /y”; x “copy c:\sas\work\out\*.gif \\host\web\Charts”; libname inlib “c:\sas\work\lib”; libname outlib “\\host\web\SASLib”; proc datasets; copy inlib outlib; run; libname outlib clear; libname inlib clear; %netauth(DISCONNECT); How %netauth() Works %macro netauth( mode ); %local domain_a ua pa domain_b ub pb; %let domain_a=ddd; %let ua=uuu; %let pa=ppp; %let domain_b=ddd; %let ub=uuu; %let pb=ppp; options xsync noxwait; Very important %if %trim(%upcase(&mode.)) eq CONNECT %then %do; x “net use \\crfprot\ipc$ /user:&domain_a.\&ua. &pa.”; x “net use \\safety\ie /user:&domain_b.\&ub. &pb.”; %if %trim(%upcase(&mode.)) eq DISCONNECT %then %do; x “net use \\crfprot\ipc$ /d”; x “net use \\safety\ie /d”; %end; %else %do; put ERROR: bad &mode. Expected CONNECT or DISCONNECT); %end; %mend; Conclusion • Manage & control remote hosts with net.exe • Authenticate • What you need • When you neet it • Never longer than necessary • Never use drive letters! • UNC paths are Linux-compliant, too • Be careful with case More Info … • Microsoft Knowledge Base 219898 – “How the Bad Password Count is Incremented in Windows NT” 314984 – “How to create and delete hidden or administrative shares on client computers” • Na Li “Applications for Running DOS Commands within SAS” PharmaSUG 2005, Posters, PO-13. About the Speakers Speaker Na Li Sr. Project Analyst Telephone (408) 990 - 7293 E-Mail nli @ pcyc.com Paul D Sherman Electrical Engineer (408) 383 - 0471 sherman @ idiom.com Web Site www.idiom.com / ~sherman / paul / pubs / netcmd