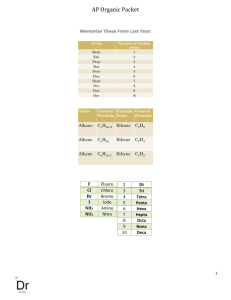
첩 자 PHY Covert Channels: Can you see the Idles?
advertisement

PHY Covert Channels: Can you see the Idles? Ki Suh Lee Cornell University 첩 자 Chupja Joint work with Han Wang, and Hakim Weatherspoon 1 첩자 (chupja) 2 Network Covert Channels • Hiding information – Through communication not intended for data transfer 3 Network Covert Channels • Hiding information – Through communication not intended for data transfer – Using legitimate packets (Overt channel) • Storage Channels: Packet headers • Timing Channels: Arrival times of packets 4 Network Covert Channels • Hiding information – Through communication not intended for data transfer – Using legitimate packets (Overt channel) • Storage Channels: Packet headers • Timing Channels: Arrival times of packets 5 Goals of Covert Channels • Bandwidth – How much information can be delivered in a second • Robustness – How much information can be delivered without loss / error • Undetectability – How well communication is hidden 6 Goals of Covert Channels • Bandwidth – How much information can be delivered in a second – 10~100s bits per second • Robustness – How much information can be delivered without loss / error Application – Cabuk’04, Shah’06 • Undetectability – How well communication is hidden – Liu’09, Liu’10 Transport Network Data Link Physical 7 Current network covert channels are implemented in L3~4 (TCP/IP) layers and are extremely slow. 8 Chupja: PHY Covert Channel • Bandwidth – How much information can be delivered in a second – 10~100s bits per second -> 10s~100s Kilo bits per second • Robustness – How much information can be delivered without loss / error Application – Bit Error Rate < 10% • Undetectability – How well communication is hidden – Invisible to detection software Transport Network Data Link Physical 9 Chupja is a network covert channel which is faster than priori art. It is implemented in L1 (PHY), robust and virtually invisible to software. 10 Outline • • • • Introduction Design Evaluation Conclusion 11 Outline • Introduction • Design – Threat Model – 10 Gigabit Ethernet • Evaluation • Conclusion 12 Threat Model Application Transport Network Data Link Passive Adversary Commodity Server Commodity NIC Application Transport Network Data Link Physical Physical Sender Receiver 13 10 Gigabit Ethernet • Idle Characters (/I/) Application Transport Packet i Packet i+1 Packet i+2 Network Data Link – – – – Each bit is ~100 picosecond wide 7~8 bit special character in the physical layer 700~800 picoseconds to transmit Only in PHY Physical 14 Terminology • Interpacket delays (D) and gaps (G) IPG Packet i Packet i+1 IPD • Homogeneous packet stream Packet i Packet i+1 Packet i+2 – Same packet size, – Same IPD (IPG), – Same destination 15 Chupja: Design • Homogeneous stream G Packet i IPG G Packet i+1 D • Sender IPG D G-Ɛ Packet i • Receiver ‘0’ G+Ɛ Packet i+1 D-Ɛ ‘1’ Di Packet i+2 D+Ɛ Gi Packet i Packet i+2 ‘0’ Gi+1 Packet i+1 ‘1’ Packet i+2 Di+1 16 Chupja: Design • With shared G – Encoding ‘1’: Gi = G + ε – Encoding ‘0’: Gi = G - ε G-Ɛ Packet i D-Ɛ ‘0’ G+Ɛ Packet i+1 ‘1’ Packet i+2 D+Ɛ 17 Implementation • SoNIC [NSDI ’13] – Software-defined Network Interface Card – Allows control and access every bit of PHY • In realtime, and in software Application Transport Network Data Link Physical • 50 lines of C code addition 18 Outline • Introduction • Design • Evaluation – Bandwidth – Robustness – Undetectability • Conclusion 19 Evaluation • What is the bandwidth of Chupja? • How robust is Chupja? – Why is Chupja robust? • How undetectable is Chupja? 20 What is the bandwidth of Chupja? 21 Evaluation: Bandwidth • Covert bandwidth equals to packet rate of overt channel Covert Channel Capacity (bps) 1.E+08 1.E+07 1.E+06 1.E+05 1.E+04 1518B 1Gbps 81kbps 1.E+03 1.E+02 0.01 64B 512B 1024B 1518B 0.1 0.5 1 3 6 Overt Channel Throughput (Gbps) 9 22 How robust is Chupja? 23 Evaluation Setup • Small Network • National Lambda Rail – Six commercial switches – Average RTT: 0.154 ms SW1 SW2 – Nine routing hops – Average RTT: 67.6ms – 1~2 Gbps External Traffic Chicaco SW1 Boston Cleveland SW2 SW3 SW4 Sender Receiver Cornell (NYC) Sender NLR (NYC) Receiver Cornell (Ithaca) 24 Evaluation: Robustness • Overt Channel at 1 Gbps (D = 12211ns, G=13738 /I/s) • Covert Channel at 81 kbps 0.6 Small No Ext. Small Ext 3.6G NLR 0.5 BER 0.4 0.3 8.9% 0.2 7.7% 0.1 2.8% 0 16 32 64 128 256 512 1024 2048 4096 Ɛ (/I/s) ? Sender Receiver 25 Evaluation: Robustness • Overt Channel at 1 Gbps (D = 12211ns, G=13738 /I/s) • Covert Channel at 81 kbps • Modulating IPGS at 1.6us scale (=2048 /I/s) 0.6 Small No Ext. Small Ext 3.6G NLR 0.5 BER 0.4 0.3 8.9% 0.2 7.7% 0.1 2.8% 0 16 32 64 128 256 512 1024 2048 4096 Ɛ (/I/s) ? Sender Receiver 26 Why is Chupja robust? 27 Evaluation: Why? • Switches do not add significant perturbations to IPDs • Switches treat ‘1’s and ‘0’s as uncorrelated – Over multiple hops when there is no external traffic. – With external traffic 28 Evaluation: Why? • Switches do not add significant perturbations to IPDs • Switches treat ‘1’s and ‘0’s as uncorrelated – Over multiple hops when there is no external traffic. – With external traffic Homogeneous 1518B at 1 Gbps Sender Chupja (Ɛ = 256/I/s) 1518B at 1 Gbps Receiver Sender Receiver 29 Evaluation: Why? • Switches do not add significant perturbations to IPDs • Switches treat encoded ‘0’ and ‘1’ as uncorrelated – Over multiple hops when there is no external traffic. 1. 1. 15 12 1 hop 3 6 9 0.1 0.01 90% in D ± 100ns 250ns D+Ɛ 0.01 0.001 0.001 0.0001 0.0001 0.00001 0.00001 0.000001 11343.51515 12 15 1 hop 3 6 9 90% in 0.1 D D –- Ɛ ± 250ns 100ns D-Ɛ 12211.2 13078.88485 0.000001 11343.51515 12211.2 Interpacket Delay (ns) Interpacket Delayy (ns) Homogeneous stream Chupja stream ( Ɛ=256/I/s ) 13078.88485 30 Evaluation: Why? • Most of IPDs are within some range from original IPD – Even when there is external traffic. Ɛ (/I/s) (ns) 256 (=204.8ns) 512 (=409.6) 1024 (=819.2) 2048 (=1638.4) 4096 (=3276.8) BER 0.367 0.391 0.281 0.089 0.013 Encoded ‘Zero’ Boston Encoded ‘One’ Chicaco Cleveland Cornell (NYC) NLR (NYC) Cornell (Ithaca) Sender Receiver 31 Evaluation: Why? • Switches do not add significant perturbations to IPDs • Switches treat ‘1’s and ‘0’s as uncorrelated – Over multiple hops when there is no external traffic. – With external traffic With sufficiently large Ɛ, the interpacket spacing holds throughout the network, and BER is less than 10% 1518B at 1 Gbps Sender ? Receiver 32 How undetectable is Chupja? 33 Evaluation: Detection Setup • Commodity server with 10G NIC – Kernel timestamping Kernel timestamping SoNIC timestamping NLR Sender NLR Receiver Sender Receiver 34 Evaluation: Detection • Adversary cannot detect patterns of Chupja 1. 1. HOM 0.1 1024 Ɛ = 1024 0.01 4096 Ɛ = 4096 0.001 Ɛ = 1024 1024 0.01 Ɛ = 4096 4096 0.001 0.0001 0.0001 0.00001 1228 HOM 0.1 0.00001 12211 Interpacket Delay (ns) Kernel Timestamping 23194 0.000001 1228 12211 Interpacket Delay (ns) 23194 SoNIC Timestamping 35 Evaluation: Summary • What is the bandwidth of Chupja? – 10s~100s Kilo bits per second • How robust is Chupja? – BER < 10% over NLR – Why is Chupja robust? • Sufficiently large Ɛ holds throughout the network • How undetectable is Chupja? – Invisible to software 36 Conclusion • Chupja: PHY covert channel – High-bandwidth, robust, and undetectable • Based on understanding of network devices – Perturbations from switches – Inaccurate endhost timestamping 첩 자 • http://sonic.cs.cornell.edu & GENI (ExoGENI)!!! 37 Thank you 38