Securing the Platform
advertisement
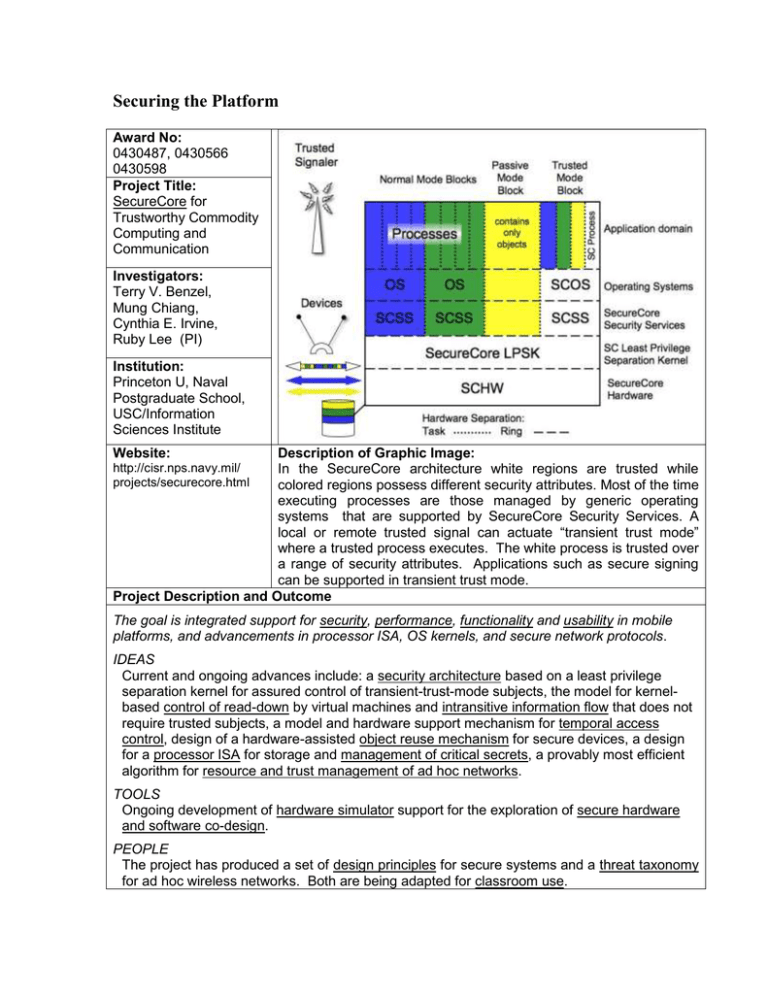
Securing the Platform Award No: 0430487, 0430566 0430598 Project Title: SecureCore for Trustworthy Commodity Computing and Communication Investigators: Terry V. Benzel, Mung Chiang, Cynthia E. Irvine, Ruby Lee (PI) Institution: Princeton U, Naval Postgraduate School, USC/Information Sciences Institute Website: Description of Graphic Image: In the SecureCore architecture white regions are trusted while colored regions possess different security attributes. Most of the time executing processes are those managed by generic operating systems that are supported by SecureCore Security Services. A local or remote trusted signal can actuate “transient trust mode” where a trusted process executes. The white process is trusted over a range of security attributes. Applications such as secure signing can be supported in transient trust mode. Project Description and Outcome http://cisr.nps.navy.mil/ projects/securecore.html The goal is integrated support for security, performance, functionality and usability in mobile platforms, and advancements in processor ISA, OS kernels, and secure network protocols. IDEAS Current and ongoing advances include: a security architecture based on a least privilege separation kernel for assured control of transient-trust-mode subjects, the model for kernelbased control of read-down by virtual machines and intransitive information flow that does not require trusted subjects, a model and hardware support mechanism for temporal access control, design of a hardware-assisted object reuse mechanism for secure devices, a design for a processor ISA for storage and management of critical secrets, a provably most efficient algorithm for resource and trust management of ad hoc networks. TOOLS Ongoing development of hardware simulator support for the exploration of secure hardware and software co-design. PEOPLE The project has produced a set of design principles for secure systems and a threat taxonomy for ad hoc wireless networks. Both are being adapted for classroom use. Taxonomy of Security Design Principles Security Design Principles Structure Logic and Function System Life Cycle Economy and Elegance Secure Defaults Repeatab le, Documented Procedures Secure Failure Procedural Rigor Least Common Mechanism Self Analysis Secure System Modification Clear Ab stractions Accountab ility and Traceab ility Sufficient User Documentation Partially Ordered Dependencies Continuous Protection of Information Efficiently Mediated Access Economic Security Minimized Sharing Performance Security Reduced Complexity Ergonomic Security Secure System Evolution Acceptab le Security Trust Trusted Components Hierarchical Trust for Components . Inverse Modification Threshold Hierarchical Protection Minimized Security Elements Least Privilege Self-Reliant Trustworthiness Composition Secure Distrib uted Composition Trusted Communication Channels The taxonomy of security design principles provides logical groupings of key notions that apply throughout the lifecycle of a secure system. This taxonomy reflects advances in technology that have introduced new concerns into the system design space.




