Adaptive Security and Separation in Reconfigurable Hardware
advertisement
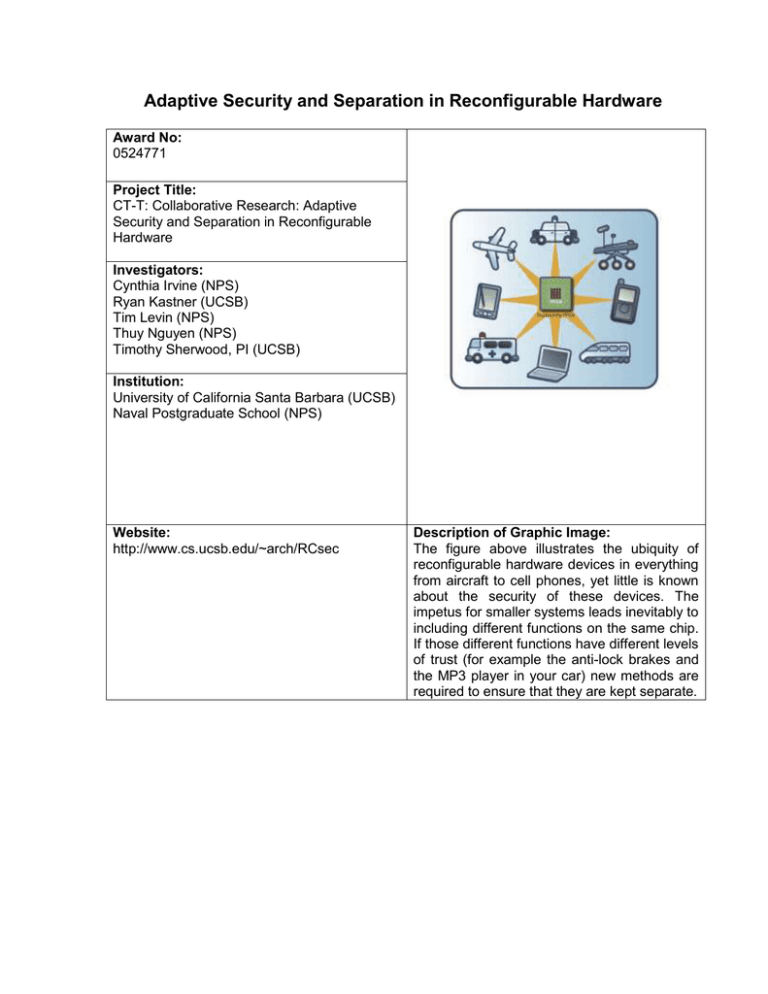
Adaptive Security and Separation in Reconfigurable Hardware Award No: 0524771 Project Title: CT-T: Collaborative Research: Adaptive Security and Separation in Reconfigurable Hardware Investigators: Cynthia Irvine (NPS) Ryan Kastner (UCSB) Tim Levin (NPS) Thuy Nguyen (NPS) Timothy Sherwood, PI (UCSB) Institution: University of California Santa Barbara (UCSB) Naval Postgraduate School (NPS) Website: http://www.cs.ucsb.edu/~arch/RCsec Description of Graphic Image: The figure above illustrates the ubiquity of reconfigurable hardware devices in everything from aircraft to cell phones, yet little is known about the security of these devices. The impetus for smaller systems leads inevitably to including different functions on the same chip. If those different functions have different levels of trust (for example the anti-lock brakes and the MP3 player in your car) new methods are required to ensure that they are kept separate. Project Description and Outcome – The RCsec project is developing the first method for composing secure systems on reconfigurable hardware. The team from UCSB and NPS has extended the latest advancements from hardware and system security research to provide a new approach for secure data management using reconfigurable hardware. We address this problem with a set of novel security primitives, a new architecture for establishing separation on the device, and the complementary use of both static and dynamic techniques for ensuring the controlled sharing between cores. Blurring the line between software and hardware, reconfigurable hardware offers the raw high speed of custom-built circuits and the flexibility of a general-purpose (e.g., desktop) processor. The flexibility of reconfigurable hardware is a boon for embedded system developers, who can now rapidly prototype and deploy solutions that include a variety of “soft cores” – which execute programs from different third-party vendors – with performance approaching that of custom silicon designs. However, the various cores may have divergent levels of trustworthiness and, unlike traditional computers in which resources are managed by an operating system (such as Windows), reconfigurable hardware typically gives each core fine grain control over the underlying hardware resources. Given that reconfigurable hardware is already trusted to carry out many critical tasks such as flight control and anti-lock braking, an adversary or rogue nation could potentially craft a soft core to intercept or even interfere with the secure operation of the device. Our results show how reconfigurable hardware can be built to provide a trustworthy processing environment for a whole class of current and future computing systems. Please select the Primary Strategic Outcome Goal that BEST DESCRIBES the highlight: Foster research that will advance the frontiers of knowledge, emphasizing areas of greatest opportunity and potential and establishing the nation as a global leader in fundamental transformational science and engineering. Secondary Strategic Outcome Goals that BEST DESCRIBES the highlight: Learning: Cultivate a world-class, broadly inclusive science and engineering workforce, and expand the scientific literacy of all citizens. This work is notable because: This work is the first to address the security of systems built with reconfigurable hardware. Does this Highlight Represent Transformative or Multidisciplinary Research? This work is high risk since it is the first time the security of reconfigurable systems has been carefully considered (1). Most information assurance professionals lack the hardware background required to analyze the security of these reconfigurable systems, while most embedded system designers treat security as an afterthought. Our research has the potential to transform the way a large, and growing, class of systems is engineered (3). We place a large deal of trust in these systems, and a failure due to an attack would have disastrous consequences (4).