Research into the hybridization of the PRoPHET and ERP network... algorithms George Mason University INFS 612 (Spring 2013)
advertisement

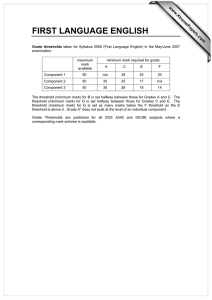
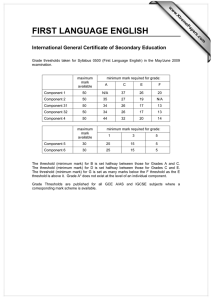
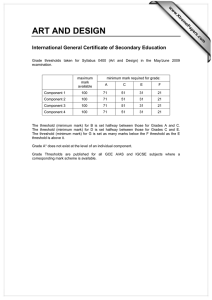
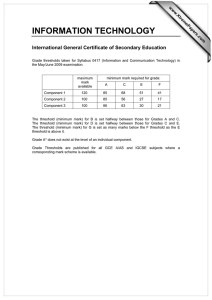
Research into the hybridization of the PRoPHET and ERP network routing algorithms George Mason University INFS 612 (Spring 2013) Project Group 4: Richard Joy, Miriam Joy, Serena Mei, and Suyog Parajuli Research Problem Background on ERP and PRoPHET Research Approach Results Demonstration Conclusion and Questions Delay Tolerant Network (DTN) addresses challenges in disconnected, disrupted networks without endto-end connection Over time, DTN routing protocols have developed in two areas: forwarding-based and replication-based Replication-based algorithms have higher message delivery rates, but are resource hungry Problem: Is there a way to combine two replicationbased algorithms which result in the same delivery rate with lower overhead? Mobile Sensor Networks Sensors with wireless connectivity deployed over a geographic area Periodically transmit their findings to a base station, perhaps for analysis or permanent storage. These sensors may be small and have limited communication range, implying that they are not always able to establish a connected path (leveraging other sensors as routers) back to base stations. Disaster Recovery/Military Deployment: People, in addition to sensors, are deployed over an area with limited wireless coverage (i.e., few, if any, base stations). Interplanetary/Spacecraft Communications ERP is a “greedy” replication algorithm Nodes continuously replicate and transmit messages to newly discovered contacts who do not already possess a copy Very effective at delivering messages Extremely inefficient for resources Time = t1 S C2 C3 D C1 Time = t2>t1 S C3 C2 C1 D PRoPHET is a “utility-based” replication protocol Not indiscriminate in its replication; uses an adaptive algorithm Set of probabilities for successful delivery Algorithm updates whenever a node is encountered. Nodes that are encountered frequently have a high delivery predictability. PRoPHET statistics are shared between each of the communicating nodes. Message Source: S Message Destination: D B D S D B C S C 1 2 D C S C B S 3 Message D B 4 Orbit and probability of encounter DTNNode DTNNode DTN Listener Connection List In our environment, the nodes have particular orbits; connection probabilities are assigned to reflect this design DTN Connector Message Stats JBDC Connector Database Message Manager •20 Nodes •4 connection partners per node with 25% probability •30 messages Ran a series of tests incrementing the threshold for switching to ERP (if it is the better solution) Each test (each threshold) was 40 minutes long Time-to-live for each message was 128 connections 40 min 100% PRoPHET 0 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 100% ERP 0 = 100% ProPHET 600 500 400 300 200 100 # of message deaths No.of Connections 18,000 16,000 14,000 12,000 10,000 8,000 6,000 4,000 2,000 0 0 0 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 Threshold ERP ProPHET Message Deaths 1 1 = 100% ERP Average and maximum message buffer size across all nodes at each threshold level 8 ERP first selected by node 7 6 5 4 3 2 1 0 0 0.1 0.2 0.3 0.4 AVG(MESSAGE_COUNT) 0.5 0.6 0.7 0.8 0.9 MAX(MESSAGE_COUNT) 1 12340 2.5 2 1.5 1 0.5 0 12342 12341 8 8 6 6 4 4 2 2 0 0 Threshold Threshold 12343 Threshold 12344 12345 4 4 8 3 3 6 2 2 4 1 1 2 0 0 0 Threshold Threshold Threshold 12346 12347 12348 4 4 8 3 3 6 2 2 4 1 1 2 0 0 0 Threshold Threshold 12349 8 12350 5 4 3 2 1 0 6 4 2 0 Threshold Threshold 12351 8 6 4 2 0 Threshold Threshold 12353 12352 2.5 2 1.5 1 0.5 0 4 8 3 6 2 4 1 2 0 0 Threshold Threshold 12355 2.5 2 1.5 1 0.5 0 Threshold 12354 Threshold 12356 12357 4 4 3 3 2 2 1 1 0 0 Threshold Threshold 12358 12359 8 8 6 6 4 4 2 2 0 0 Threshold Threshold Routing Under Uncertainty Resource Allocation Average latency in delivering messages; Average amount of system storage and bandwith consumed; Amount of energy consumed in transmission (particularly applicable to mobile devices serving as carriers for others) Reliability How do you properly elevate messages for priority handling? Managing buffers and still maximizing delivery Integrating a forwarding algorithm Performance Is information on location of target node reliable or being distorted by environmental conditions? How do you adjust for this? Sending back acknowledgements from message recipient Security New area of research into “reputation” protocol How to track messages through the entire path Encryption