Network Security BY : SARA ALFURAIHY
advertisement

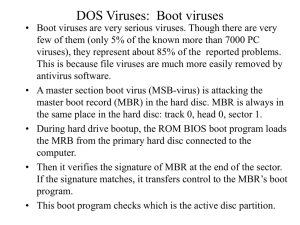
Network Security BY : SARA ALFURAIHY There are two extremes in Network safety: Absolute Security and Absolute open Absolute security is: unplugged from the network and power, locked in a safe, and thrown to the bottom of the ocean How to keep your network safe NOW or be sorry later! 4 Simple Rules Always keep your virus and Windows software updates “on” Always keep your firewall “on” Back up, Back up, Back up Always keep your passwords and key phrases safe Better Safe Than Sorry Do not use common words or phrases for passwords Do not keep your passwords written on a post-it taped to your computer monitor Back-up, back-up, back-up Strange But True •You cannot secure a laptop until you securethe laptop •Make sure everyone follows the security plan, even the boss •Smart people can be stupid too , even HR Human Nature Also Called Social Engineering Everyone Wants To Help Passwords are meant to be a SECRET ! Password Discovery Table Keep Your Email Safe Make sure to scan all email messages! Do not open email from unknown sources or that you are not expecting Once they are in, only unplugging and reinstalling OS will work New Type of Attack, Spear-Phising4 Keeping your data safe Identify and Authenticate Use a Surge Protector Safeguard against Unauthorized Access Server-side protection Password protect Wireless Networks Turn off the SSID broadcast Password protect your router Do not leave MAC addresses open to others Leave your hardware firewall on Use matching vendors Never use WEP protocols only the newer WPA2 and above Best Practices Do not pay more for your security than your data is worth! Password protect all of your important data! What is a computer virus? Computer virus is a program designed to spread itself by first infecting executable files or the system areas of hard and floppy disks and then making copies of itself. Viruses usually operate without the knowledge or desire of the computer user. What kind of files can spread viruses? Viruses have the potential to infect any type of executable code, not just the files that are commonly called 'program files'. For example, some viruses infect executable code in the boot sector of floppy disks or in system areas of hard drives. Another type of virus, known as a 'macro' virus, can infect word processing and spreadsheet documents that use macros. And it's possible for HTML documents containing JavaScript or other types of executable code to spread viruses or other malicious code. How do viruses spread? When you execute program code that's infected by a virus, the virus code will also run and try to infect other programs, either on the same computer or on other computers connected to it over a network. And the newly infected programs will try to infect yet more programs. When you share a copy of an infected file with other computer users, running the file may also infect their computers; and files from those computers may spread the infection to yet more computers. Where is the virus located? Boot sector viruses alter the program that is in the first sector (boot sector) of every DOS-formatted disk. Generally, a boot sector infector executes its own code (which usually infects the boot sector or partition sector of the hard disk), and then continues the PC bootup (start-up) process. In most cases, all write-enabled floppies used on that PC from then on will become infected How can I avoid infection? There is no way to guarantee that you will avoid infection. However, the potential damage can be minimized by taking the following precautions: * Make sure you have a clean boot disk - test with whatever (up-to-date!) antivirus software you can get hold of and make sure it is (and stays) write-protected. Boot from it and make a couple of copies. * Use reputable, up-to-date and properly-installed anti-virus software regularly. (See below) If you use a shareware package for which payment and/or registration is required, do it. Not only does it encourage the writer and make you feel virtuous, it means you can legitimately ask for technical support in a crisis.