Managing Caching for I/O Jeff Chase Duke University

Managing Caching for I/O
Jeff Chase
Duke University
Memory as a cache
data virtual address spaces
Processes access external storage objects through file
APIs and VM abstraction. The
OS kernel manages caching of pages/blocks in main memory.
data files and filesystems, databases, other storage objects page/block read/write accesses memory
(frames) disk and other storage network RAM backing storage volumes
(pages and blocks)
The DeFiler buffer cache
File abstraction implemented in upper DFS layer.
All knowledge of how files are laid out on disk is at this layer.
Access underlying disk volume through buffer cache API.
Obtain buffers (dbufs), write/read to/from buffers, orchestrate I/O.
DBuffer dbuf = getBlock (blockID) releaseBlock (dbuf) read (), write () startFetch (), startPush () waitValid (), waitClean ()
DBufferCache DBuffer
Device I/O interface
Asynchronous I/O to/from buffers block read and write
Blocks numbered by blockIDs
Managing files
create , destroy , read , write a dfile list dfiles
1.
Fetch blocks for data and metadata (or zero new ones fresh) into cache buffers (dbufs).
2. Copy bytes to/from dbufs with read and write .
3. Track which data/metadata blocks are valid , and which valid blocks are clean and which are dirty .
“inode” for DFileID
4. Clean the dirty blocks by writing them back to the disk with push .
DBuffer dbuf = getBlock (blockID) releaseBlock (dbuf) sync ()
DBufferCache DBuffer read (), write () startFetch (), startPush () waitValid (), waitClean ()
Page/block cache internals
HASH( blockID )
List(s) of free buffers (bufs) or eviction candidates . These dbufs might be listed in the cache directory if they contain useful data, or not, if they are truly free.
cache directory
To replace a dbuf
Remove from free/eviction list.
Remove from cache directory.
Change dbuf blockID and status.
Enter in directory w/ new blockID.
Re-register on eviction list.
Beware of concurrent accesses.
Anatomy of a read
2. Enter kernel for read syscall.
3. getBlock for maps, traverse cached maps, getBlock for data, and start fetch .
5. Copy data to user buffer in read .
6.
Return to user program.
1. Compute
(user mode)
4. sleep for I/O ( stall ) seek transfer
Time
CPU
Disk
Prefetching for high read throughput
• Read-ahead (prefetching)
– Fetch blocks into the cache in expectation that they will be used.
– Requires prediction. Common for sequential access.
1. Detect access pattern.
2. Start prefetching
Reduce I/O stalls
Sequential read-ahead
• Prediction is easy for sequential access.
• Read-ahead also helps reduce seeks by reading larger chunks if data is laid out sequentially on disk.
App requests block n
App requests block n+1 n n+1 n+2
System prefetches block n+2
System prefetches block n+3
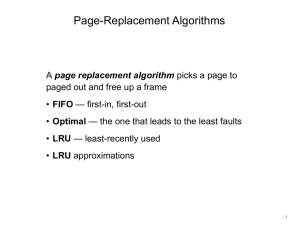
Page/block Caching Policy
Each thread/process/job utters a stream of page/block references.
– reference string: e.g., abcabcdabce ..
The OS tries to minimize the number of fetches/faults.
– Try to arrange for the resident set of blocks to match the set of blocks that will be needed in the near future.
Replacement policy is the key.
– On each access, select a victim block to evict from memory; read the new block into the victim ’s frame/dbuf.
– Simple : replace the page whose next reference is furthest in the future ( OPT ). It is provably optimal.
Selecting a victim: policy
• The oldest block? ( FIFO policy)
• The coldest block? ( L east R ecently U sed)
• The hottest block? ( M ost R ecently U sed)?
• The least popular block? ( L east F requently U sed)
• A random block?
• A block that has not been used recently?
X Y Z A Z B C D E Z A B C D E
Selecting a victim: policy
• The oldest block? ( FIFO policy)
– X Y Z A (evict X) Z (evict Y) B (evict Z) C Z…
• The coldest block? ( L east R ecently U sed)
– X Y Z A (evict X) Z (evict Y) B (evict A) C Z…
• The hottest block? ( M ost R ecently U sed)?
– Consider : A B C D E A B C D E …
• The least popular block? ( L east F requently U sed)
• A random block?
• A block that has not been used recently?
Replacement policy: file systems
• File systems often use a variant of LRU.
– A file system sees every block access (through syscall API), so it can do full LRU: move block to tail of LRU list on each access.
• Sequential files have a cache wiping effect with LRU.
– Most file systems detect sequential access and prefer eviction of blocks from the same file, e.g., using MRU.
– That also prevents any one file/object from consuming more than its “fair share” of the cache.
VM systems
• VM memory management is similar to file systems.
– Page caching in physical memory frames
– Unified with file block caching in most systems
– Virtual address space is a collection of regions/segments, which may be considered as “objects” similar to files.
• Only it ’s different.
– Mapped by page tables
– VM system software does not see most references, since they are accelerated by M emory M anagement U nit hardware.
– Requires a sampling approximation for page replacement.
– All data goes away on a system failure: no write atomicity.
VM Page Tables: Cartoon View
process page table (map)
PFN 0
PFN 1
PFN i
PFN i
+ offset page #i offset user virtual address
Each process/VAS has its own page table.
Virtual addresses are translated relative to the current page table.
In this example, each
VPN j maps to PFN j, but in practice any physical frame may be used for any virtual page.
physical memory page frames
The maps are themselves stored in memory; a protected register holds a pointer to the current map.
Example: Windows/IA32
• Each address space has a page directory
• One page: 4K bytes, 1024 4-byte entries (PTEs)
• Each PDIR entry points to a “ page table ”
• Each “ page table ” is one page with 1024 PTEs
• each PTE maps one 4K page of the address space
• Each page table maps 4MB of memory: 1024*4K
• One PDIR for a 4GB address space, max 4MB of tables
• Load PDIR base address into a register to activate the VAS
[from Tanenbaum]
Top-level page table
32 bit address with 2 page table fields
Two-level page tables
Virtual Address Translation
Example : typical 32-bit architecture with 4KB pages.
Virtual address translation maps a virtual page number (VPN) to a physical page frame number
(PFN): the rest is easy.
0 VPN address translation
Deliver exception to
OS if translation is not valid and accessible in requested mode.
physical address
{
PFN
12 offset
+ offset
Virtual Addressing: Under the Hood
MMU start here probe page table load
TLB access physical memory probe
TLB zero-fill access valid?
raise exception load
TLB fetch from disk page on disk?
allocate frame
OS page fault?
signal process
LRU Approximations for Paging
• Pure LRU and LFU are prohibitively expensive to implement.
– most references are hidden by the TLB
– OS typically sees less than 10% of all references
– can ’ t tweak your ordered page list on every reference
• Most systems rely on an approximation to LRU for paging.
– periodically sample the reference bit on each page
• visit page and set reference bit to zero
• run the process for a while (the reference window)
• come back and check the bit again
– reorder the list of eviction candidates based on sampling
VM page replacement
• Try to guess the working set of pages in active use for each VAS.
• To determine if a page is being used, arrange for MMU to notify OS on next use.
– E.g., reference bit, or disable read access to trigger a fault.
• Sample pages systematically to approximate LRU: e.g., CLOCK algorithm, or FIFO-with-Second-Chance (FIFO-2C)
Page fault rate by resident set size
Page fault rate over time
Threads in an address space may change their working sets.
FIFO-2C in Action (FreeBSD)
What Do the Pretty Colors Mean?
This is a plot of selected internal kernel events during a run of a process that randomly reads/writes its virtual memory.
– x-axis: time in milliseconds (total run is about 3 seconds)
– y-axis: each event pertains to a physical page frame, whose
PFN is given on the y-axis
The machine is an Alpha with 8000 8KB pages (64MB total)
The process uses 48MB of virtual memory: force the paging daemon to do FIFO-2C bookkeeping, but little actual paging.
– events: page allocate (yellow-green), page free (red), deactivation
(duke blue), reactivation (lime green), page clean (carolina blue).
What to Look For
– Some low physical memory ranges are reserved to the kernel.
– Process starts and soaks up memory that was initially free.
– Paging daemon evicts pages allocated to other processes, and the system reallocates the frames to the test process.
– After an initial flurry of demand-loading activity, things settle down after most of the process memory is resident.
– Paging daemon begins to scan more frequently as memory becomes overcommitted (dark blue deactivation stripes).
– Test process touches pages deactivated by the paging daemon, causing them to be reactivated.
– Test process exits (heavy red bar).
page alloc
deactivate
activate
clean
free
“ Filers ”
• Network-attached (IP)
• RAID appliance
• Multiple protocols
– iSCSI, NFS, CIFS
• Admin interfaces
• Flexible configuration
• Lots of virtualization: dynamic volumes
• Volume cloning, mirroring, snapshots, etc.
• NetApp technology leader since 1994 (WAFL)
Network File System
[ucla.edu]