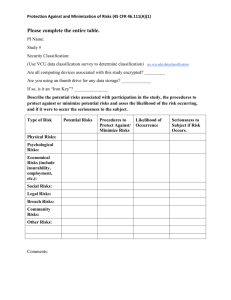
Information Security Standards
advertisement

Virginia Commonwealth University Information Security Standard Scope: This standard is applicable to all VCU faculty, staff, students, contractors, business partners, and IT service providers. Approval Date: 6/3/2009: Approved by Senior Vice President for Finance and Administration and Provost Effective Date: July 1, 2009 Compliance Date: January 1, 2010 Authority: VCU Information Security Officer Review Frequency: Annually, or as needed Information Security Standard Date: June 3, 2009 Table of Contents 1. Introduction ............................................................................................................................. 3 1.1. Intent ............................................................................................................................... 3 1.2. Information Security Roles and Responsibilities ............................................................ 4 1.3. Information Security Program Compliance .................................................................... 8 1.4. Exceptions to Information Security Requirements ......................................................... 9 2. Risk Management ................................................................................................................. 10 2.1. Business Impact Analysis ............................................................................................. 10 2.2. IT System and Data Sensitivity Classification.............................................................. 11 2.3. Sensitive IT Systems Inventory and Definition ............................................................ 12 2.4. Risk Assessment ........................................................................................................... 12 2.5. IT Security Audits ......................................................................................................... 13 3. IT Contingency Planning ...................................................................................................... 13 3.1. Continuity of Operations Planning ............................................................................... 13 3.2. IT Disaster Recovery Planning ..................................................................................... 14 3.3. IT System and Data Backup and Restoration ............................................................... 15 4. IT Systems Security .............................................................................................................. 16 4.1. IT System Security Plans .............................................................................................. 16 4.2. IT System Hardening .................................................................................................... 17 4.3. IT Systems Interoperability Security ............................................................................ 17 4.4. Malicious Code Protection ............................................................................................ 18 4.5. IT Systems Development Life Cycle Security.............................................................. 20 5. Logical Access Control ......................................................................................................... 22 5.1. Account Management ................................................................................................... 22 5.2. Password Management ................................................................................................. 24 5.3. Remote Access .............................................................................................................. 25 6. Data Protection...................................................................................................................... 26 6.1. Data Storage Media Protection ..................................................................................... 26 6.2. Encryption ..................................................................................................................... 27 7. Physical Security................................................................................................................... 27 7.1. IT Systems .................................................................................................................... 28 7.2. Human, Natural, and Environmental Risks .................................................................. 28 7.3. Environmental Controls ................................................................................................ 28 7.4. Unauthorized Personnel ................................................................................................ 28 7.5. IT infrastructure Components ....................................................................................... 28 8. Personnel Security ................................................................................................................ 28 8.1. Access Determination and Control ............................................................................... 28 8.2. Information Security Awareness and Training ............................................................. 29 8.3. Acceptable Use ............................................................................................................. 30 8.4. Email Communication .................................................................................................. 31 9. Threat Management .............................................................................................................. 31 9.1. Threat Detection............................................................................................................ 32 9.2. IT Security Monitoring and Logging ............................................................................ 32 9.3. Information Security Incident Handling ....................................................................... 33 Page 2 of 49 Information Security Standard Date: June 3, 2009 9.4. Data Breach Notification .............................................................................................. 34 10. IT Asset Management ........................................................................................................... 36 10.1. IT Asset Control ............................................................................................................ 37 10.2. Software License Management ..................................................................................... 37 10.3. Configuration Management and Change Control ......................................................... 37 11. Appendix A - Glossary of Information Security Definitions................................................ 38 12. Appendix B - Glossary of Information Security Definitions ................................................ 47 13. Appendix C - Information Security Policy and Standard Exception Request Form ............ 48 1. Introduction 1.1. Intent The intent of the Information Security Standard is to establish the baseline for information security controls that include, but are not limited to, the requirements of applicable state and federal statutes, as well as ISO 27002. These controls will provide protection of Virginia Commonwealth University (VCU) information systems and data. This Standard defines the minimum acceptable level of information security for VCU, and VCU must implement an information security program that complies with this Standard, in order to provide adequate protection of VCU’s information systems and data, commensurate with sensitivity and risk. The VCU Information Security Program consists of the following components: Risk Management IT Contingency Planning IT Systems Security Logical Access Control Data Protection Facilities Security Personnel Security Threat Management IT Asset Management These components provide the organizational framework for this Standard. This Standard recognizes that VCU may procure IT equipment, systems and services covered by this Standard from third parties. In such instances, VCU remains accountable for maintaining compliance with this Standard and VCU must enforce Page 3 of 49 Information Security Standard Date: June 3, 2009 these compliance requirements through documented agreements with third party providers. 1.2. Information Security Roles and Responsibilities This section defines the key information security roles and responsibilities included in the VCU Information Security Program. Individuals may be assigned multiple roles as long as there is adequate separation of duties, there is adequate protection against fraud, and it does not lead to a conflict of interests. The roles are President, Chief Information Officer, Information Security Officer, Privacy Officer, Authoritative Unit Head, System Owner, Data Owner, System Administrator, Data Custodian, Information Technology Professional and Information System User. 1.2.1. President The President is ultimately responsible for the security of VCU’s information systems and data. The President’s security responsibilities include the following: 1.2.2. Designate an Information Security Officer (ISO) for VCU and identify that individual to appropriate state and federal agencies. Determine the optimal place of the information security function within the VCU hierarchy. Ensure the resources and environment to enable employees to carry out their responsibilities for securing information systems and data. Chief Information Officer The Chief Information Officer (CIO) has operational responsibilities for the University’s information security program. The CIO’s security responsibilities include the following: Oversee a VCU information security program that is sufficient to protect the agency’s information systems and that is documented and effectively communicated. Establish a program of information security safeguards. Ensure that information security awareness and training programs are available to students, faculty and staff. Approve requests for exceptions to VCU’s information security standards based on risk, costs and compensating controls. Page 4 of 49 Information Security Standard 1.2.3. Date: June 3, 2009 Information Security Officer (ISO) The ISO is responsible for developing and managing VCU’s information security program. The ISO’s duties are as follows: 1.2.4. Develop and manage a VCU information security program that meets or exceeds the requirements of VCU information security policies and standards in a manner commensurate with risk. Verify and validate that all VCU IT systems and data are classified for sensitivity. Develop and maintain an information security awareness and training program for VCU faculty, staff, students, contractors, business partners, and IT service providers. Implement and maintain the appropriate balance of protective, detective and corrective controls for VCU IT systems commensurate with data sensitivity, risk and systems criticality. Authoritative Unit Head An authoritative unit head is a dean or equivalent administrative officer (e.g. associate vice president/provost). The authoritative unit head has responsibility for the security of data, systems and technology under their direct management control. Authoritative unit heads may receive advice and input from the CIO and ISO regarding security issues but ultimately must manage their data and technology in accordance with these standards commensurate with risk and cost. 1.2.5. Privacy Officer VCU must have a specified Privacy Officer if required by law or regulation, such as the Health Insurance Portability and Accountability Act (HIPAA), and may choose to have one where not required. Otherwise these responsibilities are carried out by the ISO. The Privacy Officer provides guidance on: The requirements of state and federal Privacy laws. Disclosure of and access to sensitive data. Security and protection requirements in conjunction with IT systems when there is some overlap among sensitivity, disclosure, privacy, and security issues. Page 5 of 49 Information Security Standard 1.2.6. Date: June 3, 2009 System Owner The System Owner is the VCU manager responsible for operation and maintenance of a VCU IT system. With respect to information security, the System Owner’s responsibilities include the following: 1.2.7. Require that all IT system users complete required information security awareness and training activities prior to, or as soon as practicable after, receiving access to the system, and no less than annually, thereafter. Manage system risk and developing any additional information security policies and procedures required to protect the system in a manner commensurate with risk. Maintain compliance with VCU information security policies and standards in all IT system activities. Maintain compliance with requirements specified by Data Owners for the handling of data processed by the system. Designate a System Administrator for the system. Data Owner The Data Owner is the VCU manager responsible for the policy and practice decisions regarding data, and is responsible for the following: 1.2.8. Evaluate and classify sensitivity of the data. Define protection requirements for the data based on the sensitivity of the data, any legal or regulatory requirements, and business needs. Communicate data protection requirements to the System Owner. Define requirements for access to the data. System Administrator The System Administrator is an analyst, engineer, or consultant who implements, manages, and/or operates a system or systems at the direction of the System Owner, Data Owner, and/or Data Custodian. The System Administrator assists VCU management in the day-to-day administration of a VCU IT system, and implements security controls and other requirements of the VCU information security program on an IT system for which the System Administrator has been assigned responsibility. Page 6 of 49 Information Security Standard 1.2.9. Date: June 3, 2009 Data Custodian The Data Custodian is an individual or organization in physical or logical possession of data for Data Owners. The Data Custodian is responsible for the following: Protect the data in their possession from unauthorized access, alteration, destruction, or usage. Establish, monitor, and operate IT systems in a manner consistent with VCU information security policies and standards. Provide Data Owners with reports, when necessary and applicable. 1.2.10. Information Technology Professional Information technology professionals are employees in faculty or classified positions who have responsibility for managing or supporting data or information technology programs and activities in an academic or administrative unit. IT professionals are responsible for the following: Read, understand and comply with VCU information security standards and requirements. Ensure that data, systems and technology in their area complies with VCU information security standards and requirements. Interpret VCU information security standards and provide advice and guidance to end users in their area regarding appropriate information security practices. Report breaches of information security, actual or suspected, to the VCU Information Security Officer. 1.2.11. Information System User All users of VCU information systems, including faculty, staff, students, contractors, business partners, and IT service providers are responsible for the following: Read and comply with VCU information security program requirements. Report breaches of information security, actual or suspected, to the VCU Information Security Officer. Take reasonable and prudent steps to protect the security of IT systems and data to which they have access. Page 7 of 49 Information Security Standard 1.3. Date: June 3, 2009 Information Security Program Compliance In order to provide adequate protection of VCU’s information systems and data, compliance with information security policies, standards and procedures is critical. 1.3.1. Accountability All information system users are responsible for complying with VCU information security standards. Individuals and academic/administrative units will be held accountable for non-compliance with information security policies, standards, procedures and initiatives. The authoritative unit head has responsibility for the proper application of information security standards for information systems and data under their immediate management control. Information technology professionals are responsible for knowing and understanding information security standards and practice and how to apply them to the technology and data under their or their users’ authority. When appropriate and warranted, an academic/administrative unit may be required to pay fees, charges, fines and expenses incurred or resulting from or related to non-compliance for which the academic/administrative unit is deemed in whole or in part responsible. 1.3.2. Authority The ISO has the authority to perform or delegate the performance of risk assessments, audits, security scans and spot checks of all academic/administrative units, their IT resources, non-IT information resources and physical locations. The ISO has the authority to remove systems, suspend logical access, suspend physical access, monitor traffic, disable network service and take other action to eliminate threats to information resources and data or if there is failure to comply with requirements and requests. Unless there is threat of imminent exposure or loss of data or the disruption of critical services, the ISO will consult with the CIO and authoritative unit head prior to taking these actions. 1.3.3. Corrective Actions and Sanctions Appropriate sanctions will be imposed for non-compliance with information security policies, standards, procedures and initiatives. Sanctions will be commensurate with the actual and potential risk to information systems and data, the individual or academic/administrative unit’s role, the individual or academic/administrative unit’s history of non-compliance and the circumstances of the non-compliance. Page 8 of 49 Information Security Standard Date: June 3, 2009 Violations of Information Security policies, standards, procedures and initiatives may result in action up to and including termination of employment, services or relationship with VCU. Violations of local, state, federal or other laws and regulations will be reported to the appropriate, respective authorities. Corrective actions and sanctions available include, but are not limited to: 1.3.4. Requirement to bring individual or unit into compliance Mandating of corrective action Requirement to obtain appropriate training Temporary or permanent revocation of user accounts or logical access Temporary or permanent revocation of physical access Loss of access to data Confiscation of equipment Notification of supervisors and reporting to the Department of Assurance Services Personnel actions including counseling, written notices, and disciplinary actions including suspension, transfer or demotion, and termination Reporting Issues or Incidents Violations of information security policies, standards, procedures and initiatives should be reported to the ISO. The ISO, in consultation with the CIO and authoritative unit head, will develop a corrective action plan and proposed sanctions based on actual or potential damage or risk to VCU technology and data. The authoritative unit head is responsible for implementing the corrective action plan and sanctions. 1.4. Exceptions to Information Security Requirements Exceptions to this Standard require the approval of the Information Security Officer. For each exception, the requesting academic/administrative unit shall document: The business or technical need The scope and extent Mitigating safeguards Authoritative Unit Head approval Page 9 of 49 Information Security Standard Date: June 3, 2009 If the Information Security Officer denies a request for an exception to this Standard, the academic/administrative unit requesting the exception may appeal the denial to the VCU Chief Information Officer through the Information Security Officer. The form that academic/administrative units must use to document such exception requests is included as the Appendix to this document. 2. Risk Management Risk Management delineates the steps necessary to identify, analyze, prioritize, and mitigate risks that could compromise IT systems. This section defines requirements in the following areas: Business Impact Analysis IT System and Data Sensitivity Classification Sensitive IT System Inventory and Definition Risk Assessment IT Security Audits 2.1. Business Impact Analysis Business Impact Analysis (BIA) delineates the steps necessary for VCU to identify its business functions, identify VCU business functions that are essential to its mission, and identify the resources that are required to support these essential VCU business functions. VCU should create a single BIA which both meets the requirements of this Standard and the requirements specified by the Virginia Department of Emergency Management (VDEM) in VDEM’s Continuity of Operation Planning Manual. VCU shall: Page 10 of 49 Information Security Standard 2.2. Date: June 3, 2009 2.1.1. Require the participation of System Owners and Data Owners in the development of VCU’s BIA. 2.1.2. Identify VCU business functions and classify each function according to how essential it is based on the potential impact on VCU's mission if there was disruption or degradation of the function. 2.1.3. Identify dependent functions. Determine and document any additional functions on which each essential business function depends, classifying them as essential. 2.1.4. Determine and document the required Recovery Time Objectives (RTO) for each essential business function, based on VCU goals and objectives. 2.1.5. Determine and document the Recovery Point Objectives (RPO) for each essential business function. 2.1.6. Identify the IT resources that support each essential business function. 2.1.7. Use the IT information documented in the BIA report as a primary input to IT System and Data Sensitivity Classification (Section 2.2), Risk Assessment (Section 2.4), and IT Contingency Planning (Section 3). 2.1.8. Conduct periodic review and revision of VCU’s BIA, as needed, but at least once every three years. IT System and Data Sensitivity Classification IT System and Data Sensitivity Classification requirements identify the steps necessary to classify IT systems and data according to their sensitivity with respect to the following three criteria: Confidentiality, which addresses sensitivity to unauthorized disclosure Integrity, which addresses sensitivity to unauthorized modification Availability, which addresses sensitivity to outages. Sensitive Data is any data of which the compromise with respect to confidentiality, integrity, and/or availability could have a material adverse effect on VCU interests, the conduct of VCU programs, or the privacy to which individuals are entitled. Data sensitivity is directly proportional to the materiality of a compromise of the data with respect to these criteria. VCU must classify each IT system by sensitivity according to the most sensitive data that the IT system stores, processes, or transmits. Page 11 of 49 Information Security Standard 2.3. Date: June 3, 2009 2.2.1. The System Owner shall identify the type(s) of data handled by each VCU IT system for which they have been designated System Owner. 2.2.2. The System Owner, in consultation with Data Owners, shall determine whether each type of data is also subject to other regulatory requirements. 2.2.3. The System Owner shall determine the level of potential damages to VCU of a compromise of confidentiality, integrity or availability of each type of data handled by the IT system, and classify the sensitivity of the data accordingly. 2.2.4. The System Owner shall classify the IT system as sensitive if any type of data handled by the IT system has a sensitivity of high on any of the criteria of confidentiality, integrity, or availability. 2.2.5. The System Owner shall review the IT system and data classifications with the Authoritative Unit Head and obtain Authoritative Unit Head approval of these classifications. 2.2.6. The ISO shall verify and validate that all VCU IT systems and data have been classified for sensitivity. 2.2.7. The ISO shall communicate approved IT system and data classifications to System Owners, Data Owners, and end-users. 2.2.8. The ISO shall require that VCU prohibit posting any data classified as sensitive with respect to confidentiality on a publicly accessible medium. 2.2.9. The ISO shall use the information documented in the sensitivity classification as a primary input to the Risk Assessment process (Section 2.4). Sensitive IT Systems Inventory and Definition Sensitive IT System Inventory and Definition requirements identify the steps in listing and marking the boundaries of sensitive IT systems in order to provide cost-effective, risk-based security protection for IT systems and for VCU as a whole. VCU shall: 2.4. 2.3.1. Document each sensitive IT system owned by VCU, including its ownership and boundaries, and update the documentation as changes occur. 2.3.2. Assign a System Owner, Data Owner(s), and System Administrator(s) for each VCU-owned sensitive IT system. 2.3.3. Maintain updated network diagrams. Risk Assessment Risk Assessment requirements delineate the steps VCU must take for each IT system classified as sensitive to: Identify potential threats to an IT system and the environment in which it operates Page 12 of 49 Information Security Standard Date: June 3, 2009 Determine the likelihood that threats will materialize Identify and evaluate vulnerabilities Determine the loss impact if one or more vulnerabilities are exploited by a potential threat For each IT system classified as sensitive, VCU shall: 2.5. 2.4.1. Conduct a formal Risk Assessment of the IT system, as needed, but not less than once every three years. 2.4.2. Conduct an annual self-assessment to determine the continued validity of the formal Risk Assessment. 2.4.3. Prepare a report of each Risk Assessment that includes, at a minimum, identification of all vulnerabilities discovered during the assessment, and an executive summary, including major findings and risk mitigation recommendations. IT Security Audits IT Security Audit requirements define the steps necessary to assess whether IT security controls implemented to mitigate risks are adequate and effective. For each IT system classified as sensitive, VCU shall: 2.5.1. Require that the IT systems undergo an IT Security Audit as required by and in accordance with the current version of the Commonwealth of Virginia IT Security Audit Standard. 2.5.2. Assign an individual to be responsible for managing IT Security Audits. 3. IT Contingency Planning IT Contingency Planning delineates the steps necessary to plan for and execute recovery and restoration of IT systems and data if an event occurs that renders the IT systems and/or data unavailable. Requirements are defined in the following three areas: Continuity of Operations Planning Disaster Recovery Planning IT System Backup and Restoration 3.1. Continuity of Operations Planning COV Continuity of Operations Planning requirements are defined by VDEM. This section addresses only the Continuity of Operations Planning requirements for IT systems and data. VCU should consult the Continuity of Operations Planning Manual Page 13 of 49 Information Security Standard Date: June 3, 2009 published by VDEM for non-IT related requirements that address all essential business functions. VCU’s overall Continuity of Operations Plan (COOP) should include the manual processing procedures for critical functions that users can follow until the agency restores operations, as appropriate. These Continuity of Operations Planning requirements identify the steps necessary to provide continuity for essential VCU IT systems and data through the development, implementation, exercise, and maintenance of the IT component of Continuity of Operations Plans. VCU shall: 3.2. 3.1.1. Designate an employee to collaborate with the VCU Continuity of Operations Plan (COOP) coordinator as the focal point for IT aspects of COOP and related Disaster Recovery planning activities. 3.1.2. Based on BIA and RA results, develop VCU COOP IT-related documentation which identifies: Essential business functions that require restoration and the Recovery Time Objective (RTO) for each Recovery requirements for IT systems and data needed to support the essential business functions Personnel contact information and incident notification procedures 3.1.3. Require an annual exercise (or more often as necessary) of IT COOP components to assess their adequacy and effectiveness. 3.1.4. Require review and revision of IT COOP components following the exercise (and at other times as necessary). IT Disaster Recovery Planning IT Disaster Recovery Planning is the component of Continuity of Operations Planning that identifies the steps necessary to provide for restoring essential business functions on a schedule that support agency mission requirements. These steps lead to the creation of an IT Disaster Recovery Plan (DRP). VCU shall: Page 14 of 49 Information Security Standard 3.3. Date: June 3, 2009 3.2.1. Based on the COOP, develop and maintain an IT DRP, which supports the restoration of essential business functions. 3.2.2. Require approval of the IT DRP by the Senior VP of Finance and Administration. 3.2.3. Require periodic review, reassessment, testing, and revision of the IT DRP to reflect changes in essential business functions, services, IT system hardware and software, and personnel. 3.2.4. Establish communication methods to support IT system users’ local and remote access to IT systems, as necessary. IT System and Data Backup and Restoration IT System and Data Backup and Restoration requirements identify the steps necessary to protect the availability and integrity of VCU data documented in backup and restoration plans. For every IT system identified as sensitive, VCU shall implement backup and restoration plans to support restoration of systems and data in accordance with VCU requirements. At a minimum, these plans shall address the following: Page 15 of 49 Information Security Standard Date: June 3, 2009 3.3.1. Ensure secure off-site storage for backup media. 3.3.2. Require storage of off-site backup media in a location that is geographically/separate and distinct from the primary location. 3.3.3. Restrict performance of backups to authorized personnel. 3.3.4. Require review of backup logs after the completion of each backup job to verify successful completion. 3.3.5. Require a system’s backup schedules be approved by its System Owner. 3.3.6. Require a system’s emergency backup and operations restoration plans be approved by the System Owner. 3.3.7. Require protection of any backup media that is physically or logically sent off-site or shipped by the United States Postal Service or any commercial carrier. 3.3.8. Require authorization and logging of deposits and withdrawals of all media that is stored off-site. 3.3.9. Require retention of the data handled by an IT system in accordance with the VCU’s records retention policy. 3.3.10. Ensure management of electronic information in such a way that it can be produced in a timely and complete manner when necessary, such as during a legal discovery proceeding. 4. IT Systems Security IT Systems Security requirements delineate steps to protect IT systems in the following five areas: IT System Security Plans IT System Hardening IT Systems Interoperability Security Malicious Code Protection IT Systems Development Life Cycle 4.1. IT System Security Plans IT System Security Plans document the security controls required to demonstrate adequate protection of IT systems against IT security risks. Each System Owner of a sensitive IT system shall: Page 16 of 49 Information Security Standard 4.1.1. 4.2. Date: June 3, 2009 Document an IT System Security Plan for the IT system based on the results of the risk assessment. This documentation shall: Include a description of all IT existing and planned IT security controls for the IT system, including a schedule for implementing planned controls. Include a description of how these controls provide adequate mitigation of risks to which the IT system is subject. 4.1.2. Submit the IT System Security Plan to the ISO for approval. 4.1.3. Plan and document additional IT security controls for the IT system if the ISO disapproves the IT System Security Plan, and resubmit the IT System Security Plan to the ISO for approval. 4.1.4. Update the IT System Security Plan every three years, or more often if necessary, and resubmit the IT System Security Plan to the ISO for approval. IT System Hardening IT System Hardening requirements delineate technical security controls to protect IT systems against IT security vulnerabilities. VCU shall: 4.3. 4.2.1. Identify, document, and apply appropriate baseline security configurations to VCU IT systems, regardless of their sensitivity. 4.2.2. Identify, document, and apply more restrictive security configurations for sensitive VCU IT systems, as necessary. 4.2.3. Maintain records that document the application of baseline security configurations. 4.2.4. Review and revise all security configuration standards annually, or more frequently, as needed. 4.2.5. Reapply all security configurations to VCU-owned IT systems, as appropriate, when the IT system undergoes a material change, such as an operating system upgrade. 4.2.6. Require periodic vulnerability scanning of IT systems in a manner commensurate with sensitivity and risk, to verify whether security configurations are in place and if they are functioning effectively. 4.2.7. Modify individual IT system configurations or baseline security configuration standards, as appropriate, to improve their effectiveness based on the results of vulnerability scanning. IT Systems Interoperability Security Page 17 of 49 Information Security Standard Date: June 3, 2009 IT System Interoperability Security requirements identify steps to protect data shared with other IT systems. For every sensitive VCU-owned IT system, VCU shall require: 4.3.1. 4.4. The System Owner, in consultation with the Data Owner, document IT systems with which data is shared. This documentation shall include: The types of shared data The direction(s) of data flow Contact information for the organization that owns the IT system with which data is shared, including the System Owner and the System Administrator 4.3.2. The System Owners of the IT systems which share data develop a written agreement that delineates IT security requirements for each interconnected IT system and for each type of data shared. 4.3.3. The System Owners of the IT systems that share data inform one another regarding other IT systems with which their IT systems interconnect or share data, and inform one another prior to establishing any additional interconnections or data sharing. 4.3.4. The written agreement specifies if and how the shared data will be stored on each IT system. 4.3.5. The written agreement specifies that System Owners of the IT systems that share data acknowledge and agree to abide with any legal requirements (such as HIPAA, FERPA, GLBA, etc.) regarding handling, protection, and disclosure of the shared data. 4.3.6. The written agreement maintains each Data Owner’s authority to approve access to the shared data. 4.3.7. The System Owners approve and enforce the agreement. Malicious Code Protection VCU shall: Page 18 of 49 Information Security Standard Date: June 3, 2009 4.4.1. Prohibit all IT system users from intentionally developing or experimenting with malicious programs (including, but not limited to viruses, worms, Trojans, spyware and keystroke loggers), with the exception of VCU information security staff, VCU Information Systems faculty, VCU Information Systems students, VCU Computer Science faculty, and VCU Computer Science faculty students. 4.4.2. Prohibit all IT system users from knowingly propagating malicious programs. 4.4.3. Provide malicious program detection, protection, eradication, logging, and reporting capabilities. 4.4.4. Provide malicious code protection mechanisms on VCU-owned IT systems where feasible for all IT system users. 4.4.5. Require malicious program protection that: Eliminates or quarantines malicious programs that it detects Provides an alert notification Automatically and periodically runs scans on memory and storage devices Automatically scans all files retrieved through a network connection, modem connection, or from an input storage device Allows only authorized personnel to modify program settings Maintains a log of protection activities Page 19 of 49 Information Security Standard Date: June 3, 2009 4.4.6. Provide the ability to eliminate or quarantine malicious programs in email messages and file attachments as they attempt to enter VCU’s email system. 4.4.7. Provide the ability for automatic download of definition files for malicious code protection programs whenever new files become available, and propagate the new files to all devices protected by the malicious code protection program. 4.4.8. Require all forms of malicious code protection to start automatically upon system boot. 4.4.9. Provide network designs that allow malicious code to be detected and removed or quarantined. 4.4.10. Provide procedures that instruct administrators and IT system users on how to respond to malicious program attacks, including shutdown, restoration, notification, and reporting requirements. 4.4.11. Require use of only new media or sanitized media for making copies of software for distribution. 4.4.12. Prohibit the use of common use workstations and desktops (e.g., training rooms) to create distribution media. 4.4.13. Establish Operating System (OS) update schedules commensurate with sensitivity and risk. 4.5. IT Systems Development Life Cycle Security IT Systems Development Life Cycle Security requirements document the securityrelated activities that must occur in each phase of the development life cycle for VCUowned IT application systems. 4.5.1. Incorporate IT security requirements in each phase of the life cycle, as well as for each substantial modification after initial implementation. 4.5.2. Project Initiation VCU shall: Perform an initial risk analysis based on system requirements and business objectives to provide high-level security guidelines for the system developers, including classification of the type and sensitivity of data that will be stored, processed or transmitted. Obtain data owner approval for collection and maintenance of sensitive data before incorporating such collection and maintenance in IT system requirements. Develop an initial IT System Security Plan (Section 4.1) that documents the existing and planned IT security controls that will provide adequate risk mitigation. Page 20 of 49 Information Security Standard 4.5.3. 4.5.4. Date: June 3, 2009 If the data classification identifies the system as sensitive, conduct a risk assessment prior to beginning development. Project Definition and Development Identify, develop, and document IT security requirements for the IT system during the Project Definition and Development phase. Adhere to the following programming practices, commensurate with sensitivity and risk: Input Validation – Validate input from all sources, testing for both expected and unexpected input and using whitelist input validation where practical. Default Deny – Access control should be based on specific permission rather than exclusion. Least Privilege – All processes should be performed with the least set of privileges required to complete the process. Quality Assurance – Penetration testing, fuzz testing or source code auditing should be used to identify and reduce software vulnerabilities. Verify that the IT system development process designs, develops, and implements IT security controls (including authentication, user access, logging and encryption) that meet the IT security requirements in the design specifications. Update the initial IT System Security Plan to document the IT security controls included in the design of the IT system to provide adequate protection against IT security risks. Implementation Host applications on servers that are compliant with the VCU requirements for IT system hardening (Section 4.2). Develop and execute IT security evaluation procedures to validate and verify that the IT security controls are working properly and are effective. Document results. Conduct a risk assessment (Section 2.4) to assess the risk level of the IT application system as implemented. Update the IT System Security Plan to document the IT security controls included in the IT system as implemented to provide adequate protection against IT security risks, and comply with the other requirements of Section 4.1. Applications classified as sensitive shall have vulnerability assessments performed on the applications and supporting server infrastructure at least annually and when significant changes have been made to the applications or to supporting server infrastructure. Page 21 of 49 Information Security Standard 4.5.5. Date: June 3, 2009 Disposition Require retention of the data handled by an IT system in accordance with the VCU’s records retention policy prior to disposing of the IT system. Verify the disposal of hardware and software in accordance with the current version of the Commonwealth of Virginia Removal of Commonwealth Data from Surplus Computer Hard Drives and Electronic Media Standard. 5. Logical Access Control Logical Access Control requirements delineate the steps necessary to protect IT systems and data by verifying and validating that users are who they say they are and that they are permitted to use the IT systems and data they are attempting to access. Users are accountable for any activity on the system performed with the use of their account. Requirements are defined in the following three areas: Account Management Password Management Remote Access 5.1. Account Management Account Management requirements identify those steps necessary to formalize the process of requesting, granting, administering, and terminating accounts. VCU should apply these Account Management practices to all accounts on IT systems, including accounts used by vendors and third parties. The requirements below distinguish between internal and customer-facing IT systems. Internal IT systems are designed and intended for use only by VCU employees, contractors, and business partners; customer-facing IT systems are designed and intended for use by VCU customers and by members of the public. VCU employees, contractors, and business partners may also use customer-facing IT systems. VCU shall document formal account management practices for requesting, granting, administering, and terminating accounts. At a minimum, these practices shall include the following components: 5.1.1. For all internal and customer-facing systems: Grant IT system users’ access to IT systems and data based on the principle of least privilege. Define authentication and authorization requirements, based on sensitivity and risk. Page 22 of 49 Information Security Standard 5.1.2. Date: June 3, 2009 Establish policies and procedures for approving and terminating authorization to IT systems, commensurate with sensitivity and risk. Require that the System Owner determine authorization requirements for remote access that meet the protection requirements defined by the Data Owner(s). Establish policies and procedures for approvals of emergency or temporary access to all sensitive IT systems. Review all IT system users’ accounts to assess the continued need for the accounts, at a frequency commensurate with sensitivity and risk. Notify the System Administrator when IT system user accounts are no longer required, or when an IT system user’s access level requirements change. Prohibit the use of guest and shared accounts on sensitive IT systems, where practical, or implement mechanisms to uniquely identify individuals associated with all user sessions. Disable an account with access to sensitive systems automatically if it is not used for a predefined period. Disable unneeded accounts and retain such accounts in a disabled state in accordance with VCU’s records retention policy. Configure applications to clear cached data and temporary files upon exit of the application or logoff of the system as applicable. Associate access levels with group membership, where practicable, and require that every IT system user account be a member of at least one user group. Require that the System Owner and the System Administrator investigate any unusual IT system access activities and that the System Owner approve changes to access level authorizations. Require that System Administrators have both an administrative account and at least one user account and require that administrators use their administrative accounts only when performing tasks that require administrative privileges. Limit Local Administrator rights, or the equivalent on non-Microsoft Windows-based IT systems, by requiring that such rights granted by the Authoritative Unit Head only to authorized individuals. Require that at least two individuals have administrative accounts to each IT system, to provide continuity of operations. For internal systems: Require a documented request from the user or user’s supervisor to establish an account on any internal IT system. Page 23 of 49 Information Security Standard 5.1.3. 5.2. Date: June 3, 2009 For a position in which a background check is required, complete any VCU-required background check before establishing accounts, or as soon as practicable thereafter. Require confirmation of the account request and approval by the IT system user’s supervisor and approval by the System Owner to establish accounts for sensitive IT systems. Require secure delivery of access credentials to the user based on information already on file. Notify supervisors, Human Resources, and the System Administrator in a timely manner about termination, transfer of employees and contractors with access rights to internal IT systems and data. For customer-facing systems: Require secure delivery of access credentials to users of all customerfacing IT systems. Require confirmation of the user’s request for access credentials based on information already on file prior to delivery of the access credentials to users of sensitive, customer-facing IT systems. Password Management Password Management requirements specify the means for password use to protect IT systems and data. VCU shall document formal password management practices. At a minimum, these practices shall include the following components: 5.2.1. Prohibit sharing of passwords on all accounts. 5.2.2. Require a unique password on all accounts on sensitive IT systems. 5.2.3. Require passwords on mobile devices issued by VCU, such as PDAs and smart phones. For mobile phones, use a PIN of at least 4 digits. 5.2.4. Require password complexity consisting of the following password requirements: The password must be at least 7 characters long. The password must contain at least one uppercase letter, one lowercase letter and one numeric character. Page 24 of 49 Information Security Standard Date: June 3, 2009 5.2.5. Require that default passwords be changed immediately after installation. 5.2.6. Require IT system users to maintain exclusive control and use of their passwords, to protect them from inadvertent disclosure to others. 5.2.7. Configure sensitive IT systems to allow users to change their password at will. 5.2.8. Require users of sensitive IT systems to include network systems to change their passwords after a period of no greater than 365 days. 5.2.9. Require that IT system users immediately change their passwords and notify the ISO if they suspect their passwords have been compromised. 5.2.10. Maintain the last 5 passwords used in the password history files to prevent the reuse of the same passwords, commensurate with sensitivity and risk. 5.2.11. Provide a unique initial password for each new user of sensitive IT systems, deliver the initial password to the IT system user in a secure and confidential manner, and require that the IT system user change the initial password upon the first login attempt. 5.2.12. Require that forgotten initial passwords be replaced rather than reissued. 5.2.13. Prohibit group account IDs and shared passwords on sensitive IT systems, where practical, or implement mechanisms to uniquely identify individuals associated with all user sessions. 5.2.14. Prohibit the transmission and storage of passwords in clear text. 5.2.15. Limit access to files containing passwords to the IT system and its System Administrators. 5.2.16. Suppress the display of passwords on the screen as they are entered, where practical. 5.2.17. Implement a device screen saver lockout on VCU-owned devices after a maximum of 30 minutes of inactivity. 5.2.18. Determine and implement requirements for hardware passwords based on sensitivity and risk. 5.2.19. Document and store hardware passwords securely. 5.2.20. Implement procedures to handle lost or compromised passwords and/or tokens. 5.2.21. Require adherence to the VCU Password Standard. 5.3. Remote Access Remote Access requirements identify the steps necessary to provide for the secure use of remote access within the VCU enterprise network. Commensurate with sensitivity and risk, VCU shall: Page 25 of 49 Information Security Standard Date: June 3, 2009 5.3.1. Protect the security of all remote access to VCU’s sensitive IT systems and data by means of encryption, in a manner consistent with Section 6.2. Encryption is required for session initiation and all transmission of sensitive data. 5.3.2. Protect the security of remote file transfer of sensitive data to and from VCU IT systems by means of encryption, in a manner consistent with Section 6.2. 5.3.3. Document requirements for use of remote access and for remote access to sensitive data, based on VCU policies, standards, guidelines, and procedures. 6. Data Protection Data Protection requirements delineate the steps necessary to protect VCU data from improper or unauthorized disclosure. Requirements are defined in the following two areas: Data Storage Media Protection Encryption 6.1. Data Storage Media Protection Data Storage Media Protection requirements identify the steps necessary for the appropriate handling of stored data to protect the data from compromise. VCU shall document Data Storage Media protection practices. At a minimum, these practices must include the following components: 6.1.1. Define protection of stored sensitive data as the responsibility of the Data Owner. 6.1.2. Prohibit the storage of sensitive data on any non-network storage device or media, except for backup media, unless the data is encrypted and there is a written exception approved by the ISO that includes the following elements: The business or technical justification The scope, including quantification and duration (not to exceed one year) A description of all associated risks Identification of controls to mitigate the risks, one of which must be encryption Identification of any unmitigated risks Page 26 of 49 Information Security Standard 6.2. Date: June 3, 2009 6.1.3. Require logical and physical protection for all data storage media containing sensitive data, commensurate with sensitivity and risk. 6.1.4. Such media include, but are not limited to, USB drives, cell phones, personal digital assistants, desktops, laptops, and digital music players owned by employees, contractors, and students. 6.1.5. Prohibit the forwarding of unencrypted emails containing sensitive information to external accounts. 6.1.6. Restrict the pickup, receipt, transfer, and delivery of all data storage media containing sensitive data to authorized personnel. 6.1.7. Procedures must be implemented and documented to safeguard handling of all backup media containing sensitive data. Encryption of backup media shall be considered when the data is Personal Health Information (PHI), Personally Identifiable Information (PII), or Critical Infrastructure Information/Sensitive Security Information (CII/SII). Where encryption is not a viable option, mitigating controls and procedures must be implemented and documented. 6.1.8. Implement processes to sanitize data storage media prior to disposal or reuse. Encryption Encryption requirements provide a framework for selecting and implementing encryption controls to protect sensitive data. See Section 9.4 for notification requirements regarding a breach of unencrypted sensitive data. Commensurate with sensitivity and risk, VCU shall: 6.2.1. Define and document VCU practices for selecting and deploying encryption technologies and for the encryption of data. 6.2.2. Document encryption processes before implementing encryption. These processes must include the following components: 6.2.3. Instructions in VCU’s Information Security Incident Response Plan on how to respond when keys are compromised Requirements to generate all encryption keys through an approved encryption package and securely store the keys in the event of key loss due to unexpected circumstances Require encryption during transmission of data that is sensitive relative to confidentiality and integrity. 7. Physical Security Physical Security requirements identify the steps necessary to safeguard the physical facilities that house IT equipment, systems, services, and personnel. Page 27 of 49 Information Security Standard Date: June 3, 2009 Commensurate with sensitivity and risk, VCU shall document Physical Security practices. These practices must include the following components, at a minimum: 7.1. IT Systems Safeguard IT systems and data residing in static facilities (such as buildings), mobile facilities (such as computers mounted in vehicles), and portable facilities (such as mobile command centers). 7.2. Human, Natural, and Environmental Risks Design safeguards to protect against human, natural, and environmental risks. 7.3. Environmental Controls Require appropriate environmental controls such as electric power, heating, fire suppression, ventilation, air-conditioning and air purification, as required by the IT systems and data. 7.4. Unauthorized Personnel Protect against physical access by unauthorized personnel. 7.5. IT infrastructure Components Control physical access to essential computer hardware, wiring, displays, and networks by the principle of least privilege. 8. Personnel Security Personnel Security requirements delineate the steps necessary to restrict access to IT systems and data to those individuals who require such access as part of their job duties. Requirements are defined in the following four areas: Access Determination and Control Security Awareness and Training Acceptable Use Email Communications 8.1. Access Determination and Control Access Determination and Control requirements identify the steps necessary to restrict access to IT systems and data to authorized individuals. VCU shall document access determination and control practices for all sensitive agency IT systems and all third-party IT systems with which sensitive agency IT Page 28 of 49 Information Security Standard Date: June 3, 2009 systems interconnect. At a minimum, these practices shall include the following components: 8.2. 8.1.1. Perform background investigations of all internal IT System users commensurate with risks associated with access to sensitive IT systems or data as directed by VCU Human Resources. Existing users may be grandfathered under the policy and may not be required to have background investigations. 8.1.2. Require non-disclosure and security agreements for access to IT systems and data, based on sensitivity and risk. 8.1.3. Remove physical and logical access rights upon personnel transfer or termination, or when requirements for access no longer exist, as required in Section 5.1 and Section 7. 8.1.4. Establish termination and transfer practices that require return of VCU logical and physical assets that provide access to sensitive IT systems and data and the facilities that house them. 8.1.5. Disable physical and logical access rights upon suspension of personnel for greater than 1 day for disciplinary purposes, at request of personnel's supervisor. 8.1.6. Establish separation of duties in order to protect sensitive IT systems and data, or establish compensating controls when constraints or limitations of VCU prohibit a complete separation of duties, as directed by VCU Controller’s Office. 8.1.7. Explicitly grant physical and logical access to sensitive IT systems and data and the facilities that house them based on the principle of least privilege. Information Security Awareness and Training Information Security Awareness and Training requirements identify the steps necessary to provide system owners, system administrators, and users of systems and data with awareness of information security requirements and of their responsibilities to protect information systems and data. VCU shall: Page 29 of 49 Information Security Standard 8.2.1. Designate an individual who is responsible for all aspects of VCU’s information security awareness and training program including development, implementation, testing, training, monitoring attendance, and periodic updates. 8.2.2. Include any VCU-specific information security training requirements in the VCU information security awareness and training program. 8.2.3. Require that all IT system users, including employees and contractors, receive information security awareness training annually, or more often as necessary. 8.2.4. Provide additional role-based information security training commensurate with the level of expertise required for those employees, contractors, vendors, business partners, and third parties who manage, administer, operate, and design IT systems or have specific information security duties, as practicable and necessary. Include System Owners, Data Owners, System Administrators, IT Disaster Recovery Team members, and Information Security Incident Response Team members. 8.2.5. Implement processes to monitor and track completion of information security training. 8.2.6. Require information security training before (or as soon as practicable after) IT system users receive access rights to VCU’s IT systems, and in order to maintain these access rights. 8.2.7. Develop an information security training program so that each IT system user is aware of and understands the following concepts: 8.2.8. 8.3. Date: June 3, 2009 VCU's policy for protecting IT systems and data, with a particular emphasis on sensitive IT systems and data Prevention and detection of IT security incidents, including those caused by malicious code Proper disposal of data storage media Access controls, including creating and changing passwords and the need to keep them confidential VCU acceptable use policies VCU Remote Access policies Intellectual property rights, including software licensing and copyright issues Require documentation of IT system users’ acceptance of the VCU’s information security policies after receiving information security training. Acceptable Use Acceptable Use requirements identify the steps necessary to define acceptable and permitted use of IT systems. Page 30 of 49 Information Security Standard Date: June 3, 2009 VCU shall: 8.4. 8.3.1. Document a VCU acceptable use policy that at a minimum adheres to Virginia Department of Human Resource Management Policy 1.75 – Use of Internet and Electronic Communication Systems. Require documentation of IT system users’ acceptance of the VCU's acceptable use policy before, or as soon as practicable after, gaining access to VCU IT systems. VCU’s acceptable use policy is accessible at http://www.ts.vcu.edu/policies/computeruse.html. 8.3.2. Inform IT system users that VCU reserves the right (with or without cause) to monitor, access, and disclose all data created, sent, received, processed, or stored on VCU systems. 8.3.3. Limit Local Administrator rights, or the equivalent on non-Microsoft Windows-based IT systems, by requiring that such rights granted by the Authoritative Unit Head only to authorized individuals, as stated in Section 5.1.1, so as to prevent users from: Installing or using proprietary encryption hardware/software on VCUowned systems Tampering with security controls configured on their workstations Installing personal software on a VCU-owned system Adding hardware to, removing hardware from, or modifying hardware on a VCU system 8.3.4. Prohibit the use of copyrighted and licensed materials on VCU systems unless such usage complies with applicable intellectual property and fair use laws and the VCU Intellectual Properties Policy. 8.3.5. Prohibit the transmission of unencrypted sensitive data over the Internet. Either the data file or the data stream must be encrypted. Email Communication Email shall not be used to send sensitive data unless there is encryption. As stated in Section 6.2.3 of this Standard, encryption is required for the transmission of data that is sensitive relative to confidentiality and integrity. The ISO should consider and plan for the issue of agency email being intercepted, incorrectly addressed, or infected with a virus. An email disclaimer is a set of statements that are either pre-pended or appended to emails. These statements are frequently used to create awareness of how to treat the data in the email. An email disclaimer is not a substitute for judgment on what content to put into an email. 9. Threat Management Page 31 of 49 Information Security Standard Date: June 3, 2009 Threat Management delineates the steps necessary to protect IT systems and data by preparing for and responding to IT security incidents. Requirements are defined in the following four areas: Threat Detection IT Security Monitoring and Logging Information Security Incident Handling Data Breach Notification 9.1. Threat Detection Threat Detection requirements identify the practices for implementing intrusion detection and prevention. VCU shall document threat detection practices that include the following components, at a minimum: 9.1.1. Designate an individual responsible for VCU’s threat detection program, including planning, development, acquisition, implementation, testing, training, and maintenance. 9.2. 9.1.2. Conduct Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) log reviews to detect new attack patterns as quickly as practicable. 9.1.3. Develop and implement required mitigation measures based on the results of IDS and IPS log reviews. 9.1.4. Maintain regular communication with security research and coordination organizations, such as US CERT, to obtain information about new attack types, vulnerabilities, and mitigation measures. IT Security Monitoring and Logging IT Security Monitoring and Logging requirements identify the steps necessary to monitor and record IT system activity. Commensurate with sensitivity and risk, VCU shall, or shall require that its service provider, document IT security monitoring and logging practices that include the following components, at a minimum: Page 32 of 49 Information Security Standard 9.3. Date: June 3, 2009 9.2.1. Designate individuals responsible for the development and implementation of IT security logging capabilities, as well as detailed procedures for reviewing and administering the logs. 9.2.2. Commensurate with sensitivity and risk, enable logging on IT systems as appropriate. 9.2.3. Monitor IT system event logs in real time, correlate information with other automated tools, identifying suspicious activities, and provide alert notifications. 9.2.4. Document standards that specify the type of actions an IT system should take when a suspicious or apparent malicious activity is taking place. 9.2.5. Prohibit the use of keystroke logging, except when required for security investigations and approved in writing by the ISO. Information Security Incident Handling Information Security Incident Handling requirements identify the steps necessary to respond to suspected or known breaches to information security safeguards. VCU shall document information security incident handling practices that include the following components, at a minimum: Page 33 of 49 Information Security Standard 9.4. Date: June 3, 2009 9.3.1. Designate an Information Security Incident Response Team that includes personnel with appropriate expertise for responding to cyber attacks. 9.3.2. Identify controls to deter and defend against attacks to best minimize loss or theft of information and disruption of services. 9.3.3. Implement proactive measures based on cyber attacks to defend against new forms of attacks. 9.3.4. Establish information security incident categorization and prioritization based on the immediate and potential adverse effect of the information security incident and the sensitivity of affected IT systems and data. 9.3.5. Identify immediate mitigation procedures, including specific instructions, based on information security incident categorization level, on whether or not to shut down or disconnect affected IT systems. 9.3.6. Establish a process for reporting information security incidents to the Office of Attorney General in accordance with §18.2-186.6 of the Code of Virginia if it involves unencrypted or unredacted personal information that was or is reasonably believed to have been accessed and acquired by an unauthorized person and causes or is reasonably believed to have caused or have the potential to cause identity theft or another fraud to any resident of Virginia. 9.3.7. Establish requirements for internal VCU information security incident recording and reporting requirements, including a template for the incident report. 9.3.8. Establish procedures for information security incident investigation, preservation of evidence, and forensic analysis. 9.3.9. Report information security incidents only through channels that have not been compromised. Data Breach Notification To specify the notification requirements for VCU by identifying the triggering factors and necessary responses to unauthorized release of unencrypted sensitive information. VCU shall: 9.4.1. Identify all VCU systems, processes, and logical and physical data storage locations (whether held by the agency or a third party) that contain Personal Information which means the first name or first initial and last name in combination with and linked to any one or more of the following data elements, when the data elements are neither encrypted nor redacted: Social Security number Drivers license number or state identification card number issued in lieu of a driver’s license number Page 34 of 49 Information Security Standard Date: June 3, 2009 Financial account number, or credit card or debit card number, in combination with any required security code, access code, or password that would permit access to an individual’s financial accounts Other personal identifying information. “Redact” means alteration or truncation of data such that no more than the following are accessible as part of the information: Five digits of a Social Security number or The last four digits of a driver’s license number, state identification card number, or account number 9.4.2. Include provisions in any third party contracts requiring that the third party and third party subcontractors provide immediate notification to VCU of suspected breaches and report findings. 9.4.3. Provide appropriate notice to affected individuals upon the unauthorized release of unencrypted and/or un-redacted Personal Information by any mechanism, including, but not limited to: Theft or loss of digital media Theft or loss of physical hardcopy Security compromise of any system An individual or entity shall disclose the breach of the security of the system if encrypted information is accessed and acquired in an unencrypted form, or if the security breach involves a person with access to the encryption key. If a data custodian is the entity involved in the data breach they must alert the data owner so that the data owner can notify the affected individuals. VCU shall provide this notice without undue delay as soon as verification of the unauthorized release is confirmed, except as delineated in Section 9.4.8. 9.4.4. In the case of a computer found to be infected with malware capable of exposing data to unauthorized access and which is reasonably believed to have led to or have potentially led to the unauthorized access and acquisition of personal information, individuals that may have had their information exposed must be alerted in accordance with data breach rules. 9.4.5. Provide notification that consists of: A general description of what occurred and when The type of personal information that was involved What actions have been taken to protect the individual’s personal information from further unauthorized access Page 35 of 49 Information Security Standard 9.4.6. Date: June 3, 2009 A telephone number that the person may call for further information and assistance, if one exists What actions VCU recommends that the individual take, to include monitoring their credit reports and reviewing their account statements Provide this notification by one or more of the following methodologies, listed in order of preference: Written notice to the last known postal address in the records of the individual or entity Telephone notice Electronic notice Substitute notice by email, conspicuous posting of the notice on the website of VCU and notice to major statewide media if one of the following conditions is met: VCU demonstrates that the cost of providing notice will exceed $50,000 The affected class of Virginia residents to be notified exceeds 100,000 residents VCU doesn’t have sufficient contact information or legal consent to provide notice 9.4.7. In the event an individual or entity provides notice to more than 1,000 persons at one time pursuant to section E. of Code of Virginia, §18.2-186.6, the individual or entity shall notify, without unreasonable delay, the Office of the Attorney General and all consumer reporting agencies that compile and maintain files on consumers on a nationwide basis, as defined in 15 U.S.C.§1681(a)(p), of the timing, distribution, and content of the notice. 9.4.8. Not provide notification immediately following verification of unauthorized data disclosure only if law-enforcement is notified and the law-enforcement agency determines and advises the individual or entity that the notice would impede a criminal or civil investigation, or homeland security or national security. Notice shall be made without unreasonable delay after the lawenforcement agency determines that the notification will no long impede the investigation or jeopardize national or homeland security. 10. IT Asset Management IT Asset Management delineates the steps necessary to protect IT systems and data by managing the IT assets themselves in a planned, organized, and secure fashion. Requirements are defined in the following three areas: IT Asset Control Software License Management Page 36 of 49 Information Security Standard Date: June 3, 2009 Configuration Management and Change Control 10.1. IT Asset Control IT Asset Control requirements identify the steps necessary to control and collect information about IT assets. Commensurate with sensitivity and risk, VCU shall document inventory management practices that address the following components, at a minimum: 10.1.1. Identify whether IT assets may be removed from premises that house IT systems and data, and if so, identify the controls over such removal. 10.1.2. Identify whether personal IT assets are allowed onto premises that house IT systems and data, and if so, identify the controls necessary to protect these IT systems and data. 10.1.3. Remove data from IT assets prior to disposal in accordance with the current version of the Commonwealth of Virginia Removal of Commonwealth Data from Surplus Computer Hard Drives and Electronic Media Standard. 10.1.4. Require creation and periodic review of a list of VCU hardware and software assets. 10.2. Software License Management Software License Management requirements identify the steps necessary to protect against use of computer software in violation of applicable laws. VCU shall document software license management practices that address the following components, at a minimum: 10.2.1. Prohibit the use of unauthorized software and software which is in violation of license agreements. 10.3. Configuration Management and Change Control Configuration Management and Change Control requirements identify the steps necessary to document and monitor the configuration of IT systems, and to control changes to these items during their lifecycles. VCU shall, or shall require that its service provider, document configuration management and change control practices so that changes to the IT environment do not compromise IT security controls. Page 37 of 49 Information Security Standard Date: June 3, 2009 11. Appendix A - Glossary of Information Security Definitions Academic Instruction and Research Systems: Those systems used by institutions of higher education for the purpose of providing instruction to students and/or by students and/or faculty for the purpose of conducting research. Access: The ability to use, modify or affect an IT system or to gain entry to a physical area or location. Accountability: The association of each log-on ID with one and only one user, so that the user can always be tracked while using an IT system, providing the ability to know which user performed what system activities. Alert: Notification that an event has occurred or may occur. Application: A computer program or set of programs that meet a defined set of business needs. Application System: An interconnected set of IT resources under the same direct management control that meets a defined set of business needs. Asset: Any software, data, hardware, administrative, physical, communications, or personnel resource. Assurance: Measurement of confidence in a control or activity. Attack: An attempt to bypass security controls on an IT system in order to compromise the data. Audit: An independent review and examination of records and activities to test for adequacy of controls, measure compliance with established policies and operational procedures, and recommend changes to controls, policies, or procedures. Authentication: The process of verifying an identity of a user to determine the right to access specific types of data or IT system. Authorization: The process of granting access to data or IT system by designated authority after proper identification and authentication. Availability: Protection of IT systems and data so that they are accessible to authorized users when needed without interference or obstruction. Backup: The process of producing a reserve copy of software or electronic files as a precaution in case the primary copy is damaged or lost. Business Continuity Plan: A set of processes and procedures to recover an organization’s essential business functions in a manner and on a schedule to provide for the ongoing viability of the organization if a disruption to normal operations occurs. Baseline Security Configuration: The minimum set of security controls that must be implemented on all IT systems of a particular type. Page 38 of 49 Information Security Standard Date: June 3, 2009 Business Function: A collection of related structural activities that produce something of value to the organization, its stakeholders or its customers. Business Impact Analysis (BIA): The process of determining the potential consequences of a disruption or degradation of business functions. Change Control: A management process to provide control and traceability for all changes made to an application system or IT system. Commonwealth of Virginia (COV): The government of the Commonwealth of Virginia, and its agencies and departments. Confidentiality: The protection of data from unauthorized disclosure to individuals or IT systems. Configuration Management: A formal process for authorizing and tracking all changes to an IT system during its life cycle. Continuity of Operations Planning: The process of developing plans and procedures to continue the performance of essential business functions in the event of a business interruption or threat of interruption. Continuity of Operations Plan (COOP): A set of documented procedures developed to provide for the continuance of essential business functions during an emergency. Credential: Information, such as a user ID and password passed from and IT system or IT system user to an IT system to establish access rights. Cryptography: The process of transforming plain text into cipher text, and cipher text into plain text. Customer-Facing IT System: An IT system designed and intended for by external agency customers and or by the public. COV employees, contractors, and business partners may also use such systems. See also IT System and Internal IT System. Data: An arrangement of numbers, characters, and/or images that represent concepts symbolically. Database: A collection of logically related data (and a description of this data), designed to meet the information needs of an organization. Data Classification: A process of categorizing data according to its sensitivity. Data Custodian: An individual or organization in physical or logical possession of data for Data Owners. Data Custodians are responsible for protecting the data in their possession from unauthorized access, alteration, destruction, or usage and for providing and administering general controls, such as back-up and recovery systems. Data Owner: A VCU Manager, designated by the VCU President or Information Security Officer, who is responsible for the policy and practice decisions regarding data. For business data, the individual may be called a business owner of the data. Page 39 of 49 Information Security Standard Date: June 3, 2009 Data Security: Data Security refers to those practices, technologies, and/or services used to apply security appropriately to data. Digital Certificate: An electronic document attached to a file that certifies the file is from the organization it claims to be from and has not been modified from the original format. Digital Signature: A number that uniquely identifies the sender of a message and proves the message is unchanged since transmission. Disaster Recovery Plan (DRP): A set of documented procedures that identify the steps to restore essential business functions on a schedule that supports agency mission requirements. Data Storage Media: A device used to store IT data. Examples of data storage media include floppy disks, fixed disks, CD-ROMs, and USB flash drives. Electronic Information: Any information stored in a format that enables it to be read, processed, manipulated, or transmitted by an IT system. Encryption: The process or the means of converting original data to an unintelligible form so it cannot be read by unauthorized users. Essential Business Function: A business function is essential if disruption or degradation of the function prevents the agency from performing its mission as described in the agency mission statement. Evaluation: Procedures used in the analysis of security mechanisms to determine their effectiveness and to support or refute specific system weaknesses. Firewall: Traffic-controlling gateway that controls access, traffic, and services between two networks or network segments, one trusted and the other untrusted. Function: A purpose, process, or role. Fuzz Testing: This is a software testing technique that provides random data ("fuzz") to the inputs of a program. If the program fails (for example, by crashing, or by failing built-in code assertions), the defects can be noted. Group: A named collection of IT system users; created for convenience when stating authorization policy. Group-based Access: Authorization to use an IT system and/or data based on membership in a group. Harden: The process of implementing software, hardware, or physical security controls to mitigate risk associated with COV infrastructure and/or sensitive IT systems and data. Identification: The process of associating a user with a unique user ID or login ID. Information: Data organized in a manner to enable their interpretation. Information Security: The protection afforded to IT systems and data in any format, in order to preserve their availability, integrity, and confidentiality. Page 40 of 49 Information Security Standard Date: June 3, 2009 Information Security Incident: An adverse event or situation, whether intentional or accidental, that poses a threat to the integrity, availability, or confidentiality of an IT system or data in any format. Information Security Incident Response Team: An organization within VCU constituted to monitor information security threats and prepare for and respond to attacks. Information Security Officer (ISO): The individual designated by the VCU President to be responsible for the development, implementation, oversight, and maintenance of VCU’s information security program. Information Security Policy: A statement of the information Security objectives of VCU, and what employees, contractors, vendors, business partners, and third parties of VCU must do to achieve these objectives. Information Security Program: A collection of security processes, standards, rules, and procedures that represents the implementation of VCU’s security policy. Information Security Requirements: The types and levels of protection necessary to adequately secure an IT system or data in any format. Information Security Standards: Detailed statements of how employees, contractors, vendors, business partners, and third parties of VCU must comply with VCU’s Information Security policy. Information Technology (IT): Telecommunications, automated data processing, databases, the Internet, management information systems, and related information, equipment, goods, and services. Information Technology (IT) Assurance: Measures that protect and defend information and IT systems by providing for their availability, integrity, authentication, confidentiality, and non-repudiation. Information Technology (IT) Contingency Planning: The component of Continuity of Operations Planning that prepares for continuity and/or recovery of an organization’s IT systems and data that support its essential business functions in the event of a business interruption or threat of interruption. Information Technology (IT) Security Audit: The examination and assessment of the adequacy of IT system controls and compliance with established IT security policy and procedures. Information Technology (IT) Security Breach: The violation of an explicit or implied security policy that compromises the integrity, availability, or confidentiality of an IT system. Information Technology (IT) Security Controls: The protection mechanisms prescribed to meet the security requirements specified for an IT system. Information Technology (IT) Security Logging: Chronological recording of system activities sufficient to enable the reconstruction, review, and examination of the sequence of environments and activities surrounding or leading to an operation, a procedure, or an event in a transaction from its inception to its final results. Information Technology (IT) System: An interconnected set of IT resources under the same direct management control. Page 41 of 49 Information Security Standard Date: June 3, 2009 Information Technology (IT) System Users: As used in this document, a term that includes VCU employees, contractors, vendors, third-party providers, and any other authorized users of IT systems, applications, telecommunication networks, data, and related resources. Integrity: The protection of data or IT system from intentional or accidental unauthorized modification. Internal IT System: An IT system designed and intended for use only by VCU employees, students, contractors, and business partners. Internet: An external worldwide public data network using Internet protocols to which VCU can establish connections. Intranet: A trusted multi-function (data, voice, video, image, facsimile, etc.) private digital network using Internet protocols, which can be developed, operated and maintained for the conduct of VCU business. Intrusion Detection: A method of monitoring traffic on the network to detect break-ins or break-in attempts, either manually or via software expert systems. Intrusion Detection Systems (IDS): Software that detects an attack on a network or computer system. A Network IDS (NIDS) is designed to support multiple hosts, whereas a Host IDS (HIDS) is set up to detect illegal actions within the host. Most IDS programs typically use signatures of known cracker attempts to signal an alert. Others look for deviations of the normal routine as indications of an attack. Intrusion Prevention Systems (IPS): Software that prevents an attack on a network or computer system. An IPS is a significant step beyond an IDS (intrusion detection system), because it stops the attack from damaging or retrieving data. Whereas an IDS passively monitors traffic by sniffing packets off of a switch port, an IPS resides inline like a firewall, intercepting and forwarding packets. It can thus block attacks in real time. Key: A sequence of data used in cryptography to encrypt or decrypt information. Least Privilege: The minimum level of data, functions, and capabilities necessary to perform a user’s duties. Logon ID: An identification code (normally a group of numbers, letters, and special characters) assigned to a particular user that identifies the user to the IT system. Malicious Code: Harmful code (such as viruses and worms) introduced into a program or file for the purpose of contaminating, damaging, or destroying IT systems and/or data. Malicious code includes viruses, Trojan horses, trap doors, worms, spyware, and counterfeit computer instructions (executables). Management Control: A set of mechanisms designed to manage organizations to achieve desired objectives. Monitoring: Listening, viewing, or recording digital transmissions, electromagnetic radiation, sound, and visual signals. Non-repudiation: A characteristic of a message that validates that the message was sent by a particular organization or individual, and cannot be refuted. Page 42 of 49 Information Security Standard Date: June 3, 2009 Off-site Storage: The process of storing vital records in a facility that is physically remote from the primary site. To qualify as off-site, the facility should be geographically/separately and distinct from the primary site and offer environmental and physical access protection. Operational Controls: IT security measures implemented through processes and procedures. Operational Risk: The possibility of loss from events related to technology and infrastructure failure, from business interruptions, from staff related problems and from external events such as regulatory changes. Password: A unique string of characters that, in conjunction with a logon ID, authenticates a user’s identity. Penetration testing: A penetration test is a method of evaluating the security computer system or network simulating an attack by a malicious user. Personal Digital Assistant (PDA): A digital device, which can include the functionality of a computer, a cellular telephone, a music player and a camera. Personal Identification Number (PIN): A short sequence of digits used as a password. Personal Information: All information that describes, locates or indexes anything about an individual including his real or personal property holdings derived from tax returns, and his education, financial transactions, medical history, ancestry, religion, political ideology, criminal or employment record, or that affords a basis for inferring personal characteristics, such as finger and voice prints, photographs, or things done by or to such individual; and the record of his presence, registration, or membership in an organization or activity, or admission to an institution. "Personal information" shall not include routine information maintained for the purpose of internal office administration whose use could not be such as to affect adversely any data subject nor does the term include real estate assessment information. Code of Virginia § 2.2-3801. Personally Identifiable Information (PII): Any piece of information that can potentially be used to uniquely identify, contact, or locate a single person. Personnel: All VCU employees, contractors, and subcontractors, both permanent and temporary. Phishing: A form of criminal activity characterized by attempts to acquire sensitive information fraudulently, such as passwords and credit card details, by masquerading as a trustworthy person or business in an apparently official electronic communication. Privacy: The rights and desires of an individual to limit the disclosure of individual information to others. Privacy Officer: The privacy officer, if required by statute (such as HIPAA) provides guidance on the requirements of state and federal Privacy laws; disclosure of and access to sensitive data; and security and protection requirements in conjunction with the IT system when there is some overlap among sensitivity, disclosure, privacy, and security issues. Public web site: A public web site is the most visible and readily accessible to the average Web user. A site on the Web that is accessible by anyone with a Web browser and access to the Internet. Page 43 of 49 Information Security Standard Date: June 3, 2009 Recovery: Activities beyond the initial crisis period of an emergency or disaster that are designed to return IT systems and/or data to normal operating status. Residual Risk: The portion of risk that remains after security measures have been applied. Restoration: Activities designed to return damaged facilities and equipment to an operational status. Risk: The possibility of loss or injury based on the likelihood that an event will occur and the amount of harm that could result. Risk Assessment (RA): The process of identifying and evaluating risks so as to assess their potential impact. Risk Management: Identification and implementation of IT security controls in order to reduce risks to an acceptable level. Risk Mitigation: The continuous process of minimizing risk by applying security measures commensurate with sensitivity and risk. Role-based Access Control: A type of access control in which IT system users receive access to the IT systems and data based on their positions or roles in an organization. Roles and Responsibility: Roles represent a distinct set of operations and responsibilities required to perform some particular function that an individual may be assigned. Roles may differ from the individual’s business title. This document contains the roles and responsibilities associated with implementing information security. Recovery Point Objective (RPO): The measurement of the point in time to which data must be restored in order to resume processing transactions. Directly related to the amount of data that can be lost between the point of recovery and the time of the last data backup. Recovery Time Objective (RTO): The period of time in which systems, applications or functions must be recovered after an outage. Secure: A state that provides adequate protection of IT systems and data against compromise, commensurate with sensitivity and risk. Sensitivity: A measurement of adverse affect on VCU interests, the conduct of agency programs, or the privacy to which individuals are entitled that compromise of IT systems and data with respect to confidentiality, integrity, and/or availability could cause.. IT systems and data are sensitive in direct proportion to the materiality of the adverse effect caused by their compromise. Sensitivity Classification: The process of determining whether and to what degree IT systems and data are sensitive. Separation of Duties: Assignment of responsibilities such that no one individual or function has control of an entire process. It is a technique for maintaining and monitoring accountability and responsibility for IT systems and data. Shared Accounts: A logon ID or account utilized by more than one entity. Page 44 of 49 Information Security Standard Date: June 3, 2009 Source Code Auditing: A software (source) code audit is a comprehensive analysis of source code in a programming project with the intent of discovering bugs, security breaches or violations of programming conventions. It is an integral part of the defensive programming paradigm, which attempts to reduce errors before the software is released. Spyware: A category of malicious software designed to intercept or take partial control of a computer's operation without the informed consent of that machine's owner or legitimate user. While the term taken literally suggests software that surreptitiously monitors the user, it has come to refer more broadly to software that subverts the computer's operation for the benefit of a third party. State: See Commonwealth of Virginia (COV). Support System: An interconnected set of IT resources under the same direct management control that shares common functionality and provides services to other systems. System: See Information Technology (IT) System. System Administrator: An analyst, engineer, or consultant who implements, manages, and/or operates a system at the direction of the System Owner, Data Owner, and/or Data Custodian. System Owner: A VCU Manager, designated by the VCU President or Information Security Officer, who is responsible for the operation and maintenance of a VCU IT system. Technical Controls: IT security measures implemented through technical software or hardware. Third-Party Provider: A company or individual that supplies IT equipment, systems, or services to VCU. Threat: Any circumstance or event (human, physical, or environmental) with the potential to cause harm to an IT system in the form of destruction, disclosure, adverse modification of data, and/or denial of service by exploiting vulnerability. Token: A small tangible object that contains a built-in microprocessor utilized to store and process information for authentication. Trojan Horse: A malicious program that is disguised as or embedded within legitimate software. Trusted System or Network: An IT system or network that is recognized automatically as reliable, truthful, and accurate, without continual validation or testing. Universal Serial Bus (USB): A standard for connecting devices. Untrusted: Characterized by absence of trusted status. Assumed to be unreliable, untruthful, and inaccurate unless proven otherwise. USB Flash Drive: A small, lightweight, removable and rewritable data storage device. User ID: A unique symbol or character string that is used by an IT system to identify a specific user. See Logon ID. Page 45 of 49 Information Security Standard Date: June 3, 2009 Virginia Department of Emergency Management (VDEM): A COV department that protects the lives and property of Virginia's citizens from emergencies and disasters by coordinating the state's emergency preparedness, mitigation, response, and recovery efforts. Version Control: A management process that provides traceability of updates to operating systems and supporting software. Virus: See Malicious Code. Vital Record: A document, regardless of media, which, if damaged or destroyed, would disrupt business operations. Vulnerability: A condition or weakness in security procedures, technical controls, or operational processes that exposes the system to loss or harm. Vulnerability Assessment: A process by which system vulnerabilities are identified and have their importance quantified. Workstation: A terminal, computer, or other discrete resource that allows personnel to access and use IT resources. Page 46 of 49 Information Security Standard Date: June 3, 2009 12. Appendix B - Glossary of Information Security Definitions BIA: Business Impact Analysis DHRM: Department of Human Resource Management DRP: Disaster Recovery Plan FTP: File Transfer Protocol HIPAA: Health Insurance Portability and Accountability Act IDS: Intrusion Detection Systems IPS: Intrusion Prevention Systems ISO: Information Security Officer PCI: Payment Card Industry PDA: Personal Digital Assistant PII: Personally Identifiable Information PIN: Personal Identification Number RA: Risk Assessment RPO: Recovery Point Objective RTO: Recovery Time Objective SDLC: Systems Development Life Cycle VDEM: Virginia Department of Emergency Management Page 47 of 49 Information Security Standard Date: June 3, 2009 13. Appendix C - Information Security Policy and Standard Exception Request Form Unit Name: Authoritative Unit Head: Requirement to which an exception is requested: Date: 1. Provide the business or technical justification: 2. Describe the scope, including quantification and requested duration (not to exceed 1 year): 3. Describe all associated risks: 4. Identify the controls to mitigate the risks: 5. Identify any unmitigated risks: By submitting this form, the Authoritative Unit Head acknowledges that they have evaluated the business issues associated with this request and accepts any and all associated risks as being reasonable under the circumstances. VCU Information Security Officer (ISO) Use Only Approval: Comments: Date: Page 48 of 49 Information Security Standard Date: June 3, 2009 VCU Chief Information Officer (CIO) Use Only (Used for Appeal) Approval: Comments: Date: Page 49 of 49