CSC 774 Advanced Network Security Wireless Sensor Networks
advertisement
Computer Science
CSC 774 Advanced Network Security
Topic 6. Random Key Pre-Distribution in
Wireless Sensor Networks
Dr. Peng Ning
CSC 774 Adv. Net. Security
1
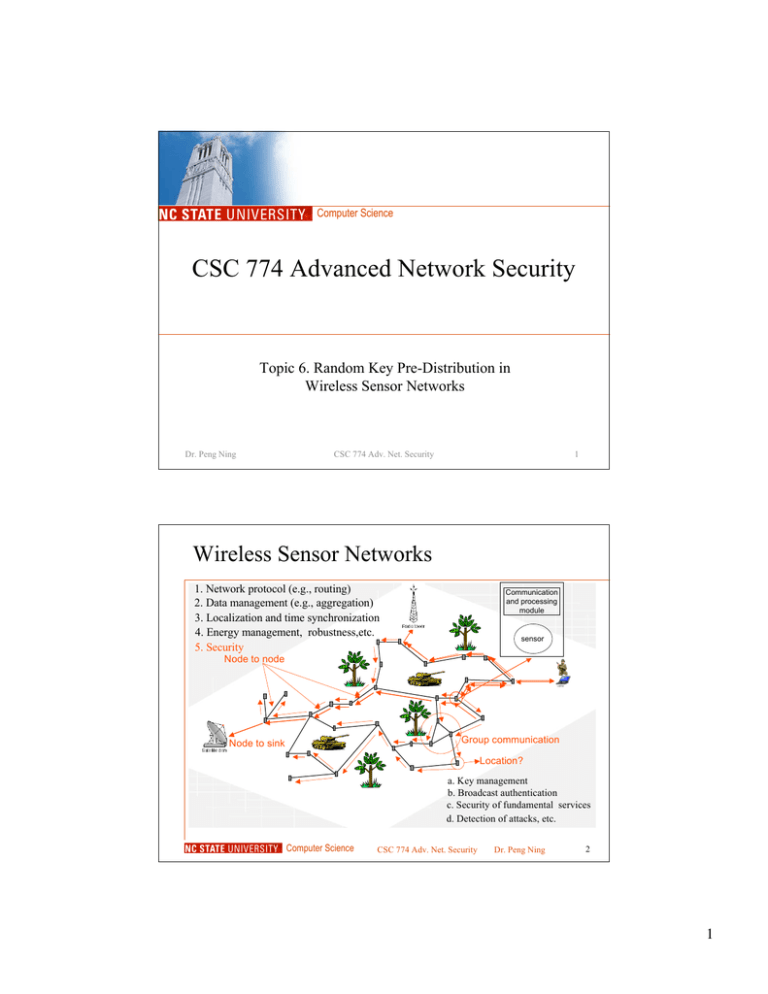
Wireless Sensor Networks
1. Network protocol (e.g., routing)
2. Data management (e.g., aggregation)
3. Localization and time synchronization
4. Energy management, robustness,etc.
5. Security
Communication
and processing
module
sensor
Node to node
Group communication
Node to sink
Location?
a. Key management
b. Broadcast authentication
c. Security of fundamental services
d. Detection of attacks, etc.
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
2
1
Wireless Sensor Networks (Cont’d)
• Composed of
– Low cost, low power, and multifunctional nodes
– Wireless communication in short distances
• Sensor node
–
–
–
–
Sensing
Data processing
Communication
Unattended
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
3
Dr. Peng Ning
4
Security in Sensor Networks
• Sensor network security
–
–
–
–
–
–
–
Key management
Point-to-point authentication
Encryption
Broadcast authentication
Secure localization
Secure clock synchronization
…
Computer Science
CSC 774 Adv. Net. Security
2
Challenges in Sensor Network Security
• Resource constraints
– Limited storage, computation, and communication
• Expensive mechanisms such as public key cryptography
is not practical
– Depletable resources (e.g. battery power)
• Resource consumption attacks
• Threat of node compromises
– Sensor nodes are usually deployed in an
unattended fashion
– Subject to node captures
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
5
Challenges (Cont’d)
• Local computation/communication v.s. global
threat
– Sensor network applications often depend on local
computation and communication due to resource
constraints
– A determined attacker may
• Attack any node in a network, and
• Use information gathered from compromised nodes to
attack non-compromised ones
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
6
3
Establishing Pairwise Keys in Sensor
Networks
• Traditional techniques are not practical in
sensor networks
– Public cryptography: not practical
– Key distribution centers (KDC): not practical
Computer Science
CSC 774 Adv. Net. Security
7
Dr. Peng Ning
Computer Science
Probabilistic Key Pre-Distribution
Dr. Peng Ning
CSC 774 Adv. Net. Security
8
4
Probabilistic Key Pre-Distribution
• Basic idea
– Assign a random subset of keys of a key pool to
each node
– Two nodes can establish secure communication if
they have at least one common key
i
A set of random keys
Computer Science
j
CSC 774 Adv. Net. Security
Dr. Peng Ning
9
Probabilistic Key Pre-Distribution (Cont’d)
• Key distribution (three phases)
– Key pre-distribution
– Shared-key discovery
– Path-key establishment
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
10
5
Probabilistic Key Pre-Distribution (Cont’d)
• Key pre-distribution
– Generate a large pool of P keys and their ids
– For each sensor, random draw k keys out of P
without replacement
• This forms the key ring of the sensor
– Load the key ring into the memory of the sensor
– Save the key ids of each key ring and the sensor id
on a trusted controller
– For each node, load the i-th controller node with
the key shared with that node.
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
11
Probabilistic Key Pre-Distribution (Cont’d)
• Key pre-distribution (Cont’d)
– Parameters k and P are critical
• Only a small number of keys need to be placed on each
node’s key ring
• Any two nodes share at least a key with a chosen
probability
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
12
6
Probabilistic Key Pre-Distribution (Cont’d)
• Shared-key discovery
– Each node discovers its neighbors in wireless
communication range with which it shares keys
– Method 1:
• Each node broadcasts the list of key ids on its key ring
• Give an adversary additional knowledge of key
distribution
• No direct ways to comprise keys
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
13
Probabilistic Key Pre-Distribution (Cont’d)
• Shared-key discovery (Cont’d)
– Method 2 (private shared-key discovery)
• For each key on a key ring, each node broadcasts a list
– α, EKi(α), i= 1, …, k, where α is a challenge
• If a node receives this list, it tries to decrypt each ciphertext with every key it has
• The node establishes a shared key if it can successfully
decrypt a cipher-text
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
14
7
Probabilistic Key Pre-Distribution (Cont’d)
• Path-key establishment
– Assign a path-key to selected pairs of nodes that
• Are in wireless communication range
• Do not share a common key
• But are connected by two or more links at the end of
shared-key discovery
– Established through those links
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
15
Probabilistic Key Pre-Distribution (Cont’d)
• Revocation
– Revoke the entire key ring of a compromised node
– A controller node broadcasts a single revocation
message containing a signed list of key ids for the
revoked key ring
• The controller generates a signature key Ke, and unicasts
it to each node by encrypting it with the key they share.
– Each node verifies the signed list of key ids, and
removes those keys from its key ring
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
16
8
Probabilistic Key Pre-Distribution (Cont’d)
• Re-keying
– Restart shared-key discovery and path-key
discovery
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
17
Analysis
• Model a sensor network as a random graph
– All the sensor nodes are the vertices in the graph
– There is an edge between two vertices if the corresponding
nodes share a common key
• Analysis questions
– What should be the expected degree (d) of a node so that a
sensor network with n nodes is connected?
– Given d and the size of a neighborhood (n’), what should be
the key ring size (k) and key pool size (P) for a network
with n nodes?
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
18
9
Analysis (Cont’d)
• What should be the expected degree (d) of a node so that a
sensor network with n nodes is connected?
– Answered by random graph theory
– G(n, p): a graph of n nodes for which the probability that a link exists
between two nodes is p.
– d = p * (n-1): expected degree of a node (i.e. the average number of
edges connecting that node with its neighbors).
• Erdös and Rényi’s Equation:
– Given a desired probability Pc for graph connectivity and number of
nodes, n, the threshold function p is defined by:
Pc = lim Pr[G(n, p) is connect] = e$e
n "#
– where
p=
!
$c
ln(n) c
+ and c is any real constant.
n
n
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
19
CSC 774 Adv. Net. Security
Dr. Peng Ning
20
!
Analysis (Cont’d)
Computer Science
10
Analysis (Cont’d)
• Given d and the size of a neighborhood (n’), what should be
the key ring size (k) and key pool size (P) for a network with n
nodes?
– p’: probability of sharing a key between any two nodes in a
neighborhood (p’=d/(n’-1))
– p’ = 1 − Pr[two nodes do not share any key]
p'= 1"
((P " k)!) 2
(P " 2k)!P!
• Simplify with Stirling’s approximation n!" 2# n
!
p'= 1"
(1" k P )
1
2 $n
e
1
2(P "k + )
2
(1" 2k P )
Computer Science
n+
1
(P "2k + )
2
!
CSC 774 Adv. Net. Security
Dr. Peng Ning
21
CSC 774 Adv. Net. Security
Dr. Peng Ning
22
!
Analysis (Cont’d)
Computer Science
11
Improvements for the Probabilistic Key
Pre-Distribution
• q-composite key pre-distribution
– Two nodes have to have at least q shared keys to
derive a valid pairwise key
– Better resilience when the number of compromised
nodes is small
• Multi-path enforcement
– Derive each path key through multiple nodedisjoint paths, each of which derives one sub-key
– Path key is the XOR of all sub keys
– Better resilience to compromised nodes in key
paths
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
23
Random Pairwise Keys Scheme
• Approach
– Calculate the smallest probability p of two nodes
being connected so that the entire network is
connected with a high probability.
– Consider a network of n nodes
– Each node needs to store np pairwise keys
• Limitation
– The network size is limited by n=m/p, where m is
the available memory on each node for keys
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
24
12
Computer Science
Polynomial Pool Based Key
Pre-Distribution
Dr. Peng Ning
CSC 774 Adv. Net. Security
25
Outline
• Background
– Polynomial based key predistribution
• A framework for key predistribution in sensor
networks
– Polynomial pool based key predistribution
• Two efficient key predistribution schemes
– Random subset assignment
– Grid based key predistribution
• Efficient implementation in sensor networks
• Conclusion and future work
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
26
13
Polynomial Based Key Predistribution
• By Blundo et al. [CRYPTO ‘92]
– Developed for group key predistribution
– We consider the special case of pairwise key predistribution
• Predistribution:
t
i j
– The setup server randomly generates f (x, y) = " aij x y ,
i, j= 0
where f (x,y) = f (y, x)
– Each sensor i is given a polynomial share f(i, y)
• Key establishment:
!
– Node i computes f (i, y = j) = f (i, j)
– Node j computes f (j, y =i) = f (j, i) = f (i, j)
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
27
Polynomial Based Key Predistribution
(Cont’d)
• Security properties (by Blundo et al.)
– Unconditionally secure for up to t compromised nodes
• Performance
– Storage overhead at sensors: (t +1)log q bits
– Computational overhead at sensors: t modular
multiplications and t modular additions
– No communication overhead
• Limitation
– Insecure when more than t sensors are compromised
– An invitation for node compromise attacks
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
28
14
Polynomial Pool Based Key Predistribution
• A general framework for key predistribution
based on bivariate polynomials
– Let us use multiple polynomials
• A pool of randomly generated bivariate
polynomials
• Two special cases
– One polynomial in the polynomial pool
• Polynomial based key predistribution
– All polynomials are 0-degree ones
• Key pool by Eschenauer and Gligor
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
29
Polynomial Pool Based Key Predistribution
(Cont’d)
• Phase 1: Setup
– Randomly generates a set F of bivariate t-degree
polynomials
– Subset assignment: Assign a subset of polynomials in F to
each sensor
A subset: {fj(i, y), …, fk(i, y)}
f1 (x,y), f2(x,y),
…, fn (x,y)
i
Random polynomial pool
F
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
30
15
Polynomial Pool Based Key Predistribution
(Cont’d)
• Phase 2: Direct Key Establishment
– Polynomial share discovery: Communicating sensors
discover if they share a common polynomial
• Pairwise keys can be derived if they share a common
polynomial.
– Two approaches:
• Predistribution:
– Given predistributed information, a sensor can
decide if it can establish a direct pairwise key with
another sensor.
• Real-time discovery:
– Sensors discover on the fly if they can establish a
direct pairwise key.
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
31
Polynomial Pool Based Key Predistribution
(Cont’d)
• Phase 3: Path Key Establishment
– Establish pairwise keys through other sensors if two
sensors cannot establish a common key directly
– Path discovery
• Node i finds a sequence of nodes between itself and node j such
that two adjacent nodes can establish a key directly
• Key path: the above sequence of nodes between i and j
– Two approaches
• Predistribution
– Node i can find a key path to node j based on predistributed
information
• Real-time discovery
– Node i discover a key path to node j on the fly
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
32
16
Random Subset Assignment Scheme
• An instantiation of the polynomial pool-based
key predistribution.
• Subset assignment: random
A random subset: {fj(i, y), …, fk(i, y)}
f1 (x,y), f2(x,y),
…, fn (x,y)
i
Random polynomial pool
F
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
33
Random Subset Assignment (Cont’d)
• Polynomial share discovery
– Real-time discovery
Broadcast IDs in clear text.
fj, …, fk
i
Broadcast a list of challenges.
α, Ekv(α), v = 1, …, m.
i
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
34
17
Random Subset Assignment (Cont’d)
• Path discovery
– i and j use k as a KDC
– Alternatively, i contacts nodes with which it shares a key;
any node that also shares a key with j replies.
– Each key path has 2 hops
i
j
k
Computer Science
CSC 774 Adv. Net. Security
35
Dr. Peng Ning
Probability of Sharing Direct Keys between
Sensors
s'=2
s'=3
s'=4
s'=5
1.2
1
0.8
p 0.6
0.4
0.2
0
0
10
20
30
40
50
60
70
80
90
s
• s: polynomial pool size
• s’: number of polynomial shares for each sensor
• p: probability of sharing a polynomial between two sensors
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
36
18
Probability of Sharing Keys between
Sensors
d=20
d=40
d=60
d=80
d=100
1.2
1
0.8
Ps 0.6
0.4
0.2
0
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
p
• d: number of neighbors
• p: probability that two sensors share a polynomial
• ps: probability of sharing a common key
Note: each key path is at most two hops
Computer Science
CSC 774 Adv. Net. Security
37
Dr. Peng Ning
Dealing with Compromised Sensors
• Comparison with basic probability and q-composite schemes
– Probability to establish direct keys p = 0.33
– Each sensor has storage equivalent to 200 keys
Fraction of compromised
links between noncompromised sensors
RS(s'=2,s=11,t=99)
q-composite(q=1)
Basic probabilistic
RS(s'=3,s=25,t=66)
q composite(q=2)
RS(s'=4,s=43,t=49)
q composite(q=3)
1.2
1
0.8
0.6
0.4
0.2
0
0
100
200
300
400
500
600
700
800
900
1000
Number of compromised nodes
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
38
19
Dealing with Compromised Sensors
(Cont’d)
• Comparison with random pairwise keys scheme
– Assume perfect security against node compromises
• Each polynomial is used at most t times in our scheme
– Each sensor has storage equivalent to 200 keys
Probability of sharing a common
key
RS(s'=2,t=99)
RS(s'=6,t=32)
RS(s'=10,t=19)
Random pairwise keys
1.2
1
0.8
0.6
0.4
0.2
0
0
500
1000
1500
2000
2500
3000
3500
4000
Maximum supported network size
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
39
Dr. Peng Ning
40
Grid Based Key Predistribution
• Create a m×m grid
• Each row or column is
assigned a polynomial
• Assign each sensor to an
interaction
• Assign each sensor the
polynomials for the row
and the column of its
intersection
– Sensor ID: coordinate
• There are multiple ways
for any two sensors to
establish a pairwise key
Computer Science
CSC 774 Adv. Net. Security
20
Grid Based Key Predistribution (Cont’d)
• Order of node assignment
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
41
Grid Based Key Predistribution (Cont’d)
• Polynomial share discovery
– No communication overhead
Same column
Same row
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
42
21
Grid Key Predistribution (Cont’d)
• Path discovery
– Real-time discovery
– Paths with one
intermediate node
– Paths with two
intermediate nodes
– They know who to
contact!
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
43
Properties
1. Any two sensors can establish a pairwise key when
there is no compromised node;
2. Even if some sensors are compromised, there is still
a high probability to establish a pairwise key
between non-compromised sensors;
3. A sensor can directly determine whether it can
establish a pairwise key with another node.
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
44
22
Dealing with Compromised Sensors
• Comparison with basic probabilistic scheme, q-composite
scheme, and random subset assignment scheme
Fraction of compromised links
between non-compromised sensors
– Assume each sensor has storage equivalent to 200 keys
Basic probabilistic(p=0.014)
q-composite(q=1,p=0.014)
RS(s'=2,s=287,t=99,p=0.014)
Grid-based(N=20000,p=0.014)
1.2
Basic probabilistic(p=0.33)
q-composite(q=1,p=0.33)
RS(s'=2,s=11,t=99,p=0.33)
1
0.8
0.6
0.4
0.2
0
0
2000
4000
6000
8000
10000
12000
14000
16000
18000
20000
Number of compromised nodes
Computer Science
CSC 774 Adv. Net. Security
45
Dr. Peng Ning
Dealing with Compromised Sensors (Cont’d)
• Probability to establish pairwise keys when there are
compromised sensors
– d: number of non-compromised sensors to contact
– Assume each sensor has storage equivalent to 200 keys
Probability to establish pairwise
keys
d=1
d=7
d=3
d=9
d=5
1.2
1
0.8
0.6
0.4
0.2
0
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
Fraction of compromised nodes
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
46
23
Implementation
• Observations
– Sensor IDs are chosen from a field much smaller than cryptographic
keys
• Field for cryptographic keys: Fq
• Field for sensor IDs: Fq’
– Special fields: q’=216+1, q’ = 28+1
• No division operation is needed for modular multiplications
Key: n bits
l bits each
f1 (i,y)
Polynomials over Fq’
f2 (i,y)
fr(i,y)
Sensor ID j
Computer Science
CSC 774 Adv. Net. Security
Same storage as 1
polynomial over Fq
Dr. Peng Ning
47
Implementation (Cont’d)
• Lemma 1. In this implementation, the entropy of the
key for a coalition of no more than t other sensors is
r " [log 2 q'#(2 #
2 l +1
)]
q'
"n $
where l = "log 2 q'# and r = # % .
#l%
• Examples
– 64 !
bit keys
! – When q’=216+1, the above entropy is 63.9997 bits
!
– When q’ = 28+1, the above entropy is 63.983 bits
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
48
24
TinyKeyMan
• Polynomial pool based key pre-distribution on
TinyOS
– http://discovery.csc.ncsu.edu/software/TinyKeyMan/
Computer Science
CSC 774 Adv. Net. Security
Dr. Peng Ning
49
25



