Document 14681167
International Journal of Advancements in Research & Technology, Volume 2, Issue4, April-2013 261
ISSN 2278-7763
Securing Databases from Unauthorized Users
1
Prof.S.S.Asole,
2
Ms. S.M.Mundada
1
Associate Professor,Department of Computer Science and Engineering,Babasaheb Naik College of Engineering,Pusad,India ;
2
M.E.(Second Year),Department of Computer Science and Engineering,Babasaheb Naik College of Engineering,Pusad,India.
Email: suresh_asole@yahoo.com,snehal2006193@gmail.com
ABSTRACT
Database Technologies are a core component of many computing systems, applications and organisations.Data can be electronically stored, retained and shared in the database systems. As the amount of data contained in these systems grows continuously and exponentially, database security has become an issue of great concern owing to the increase in the number of incidents reporting the unauthorized exposure to sensitive data either intentionally or unintentionally.Hence, the databases should be protected in such a way so that no unauthorized access can take place to the database and both,content and access security be provided to the databases.
Keywords : Database; Notifications ;Security; Visual Cryptography;
1 I NTRODUCTION
D ATABASE security involves wide range of topics such as physical security, network security, encryption and authentication .
This paper discusses techniques that can be used to secure the databases concerning any kind of applications as medical databases, surveillance databases, banking sector related databases, defense system databases and so on.
The scheme implemented provides protection against unauthorized accesses to secure databases using notification system.Moreover,the system can be implemented with databases of any of the above mentioned applications so that alerts can be sent to the authorized user of the database on a device like cell phone whenever any unauthorized access takes place to database.
2 S ECURITY MECHANISMS
The paper discusses a system which aims to provide content as well as access security to the databases.Content security is provided with the use of visual cryptographic technique and access security is provided through a notification system.
2.1 Content Security
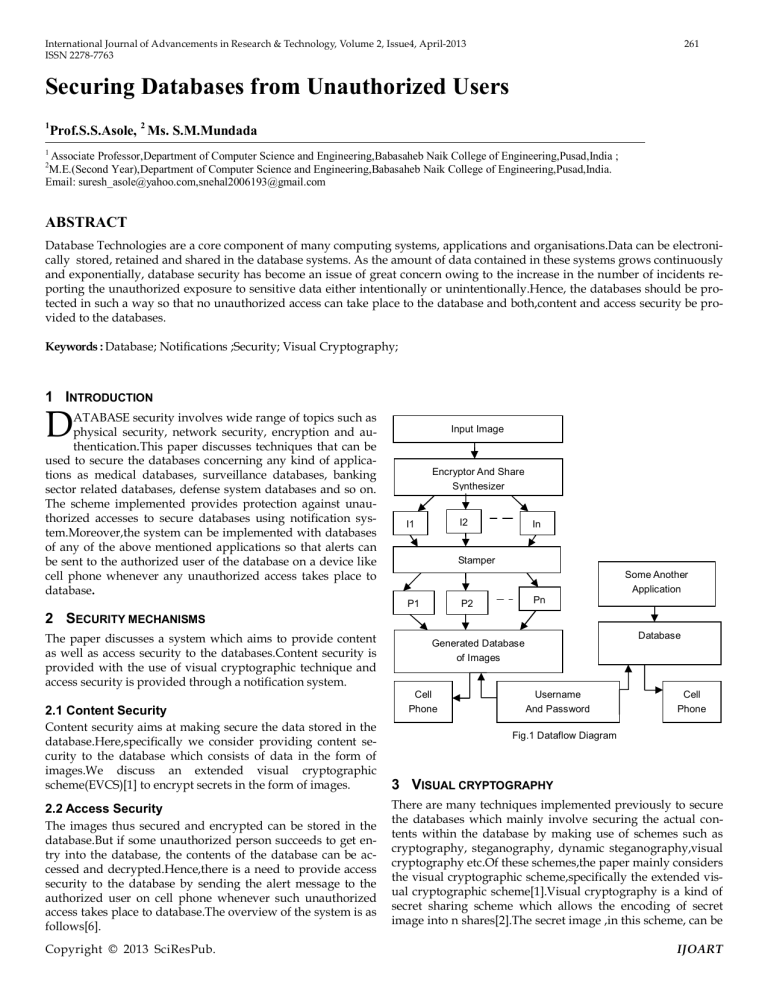
Content security aims at making secure the data stored in the database.Here,specifically we consider providing content security to the database which consists of data in the form of images.We discuss an extended visual cryptographic scheme(EVCS)[1] to encrypt secrets in the form of images.
I1
Input Image
Encryptor And Share
Synthesizer
I2
In
P1
Cell
Phone
Stamper
P2
Generated Database of Images
Pn
Username
And Password
Fig.1 Dataflow Diagram
Some Another
Application
Database
Cell
Phone
2.2 Access Security
The images thus secured and encrypted can be stored in the database.But if some unauthorized person succeeds to get entry into the database, the contents of the database can be accessed and decrypted.Hence,there is a need to provide access security to the database by sending the alert message to the authorized user on cell phone whenever such unauthorized access takes place to database.The overview of the system is as follows[6].
3 V ISUAL CRYPTOGRAPHY
There are many techniques implemented previously to secure the databases which mainly involve securing the actual contents within the database by making use of schemes such as cryptography, steganography, dynamic steganography,visual cryptography etc.Of these schemes,the paper mainly considers the visual cryptographic scheme,specifically the extended visual cryptographic scheme[1].Visual cryptography is a kind of secret sharing scheme which allows the encoding of secret image into n shares[2].The secret image ,in this scheme, can be
Copyright © 2013 SciResPub. IJOART
International Journal of Advancements in Research & Technology, Volume 2, Issue4, April-2013 262
ISSN 2278-7763 obtained by stacking the n shares which helps recover the original image.The shares thus generated in visual cryptographic scheme have meaningless appearance,hence they can be identified of being a part of some other secret image.This problem is solved by the extended visual cryptographic scheme in which each share appears as meaningful image by stamping it with cover images[1][2].
4 V
ISUAL CRYPTOGRAPHY SCHEME AND NOTIFICATION
SYSTEM
The cover images are added over these shares in the second phase of EVCS to give them a meaningful appearance [1].This process is referred as stamping.
(a) (b) (c) (d)
A secret image encryption in extended visual cryptography scheme (EVCS)[1] consists of two phases.
The first phase employees an optimisation technique for given access structure. It constructs a set of noise-like shares of the secret image which don’t have any pixel expansions.The second phase involves a stamping algorithm which directly adds a cover image on each share to give meaningful appearance to the shares. For the purpose of decryption, these shares are printed over transparencies.After stacking these transparencies,the secret can be revealed.
In the first phase, the intermediate shares (i.e.I1,I2,I3…..In in Fig.1) are generated. In this, the secret image is broken into
I-shares by the encryptor and share synthesizer block.These shares are divided into two sets, a set of such shares, which after stacking can reveal the secret and another set of shares which don’t reveal anything about the secret when stacked.
The set which reveals the secret after stacking is called set of qualifying shares and the one which doesn’t reveal the secret is called set of forbidden shares.
Fig.3 (a) Cover image1 (b)Cover image2 (c)Cover image3 (d)Cover image4
In stamping,the black pixels of the cover image are stamped over the white pixels of the share image.The shares after stamping appear as follows.
(a) (b) (c) (d)
Fig.4 (a) Stamped share1 (b) Stamped share2 (c) Stamped shrare3
(d)Stamped share4
(a)
( b ) ( c ) ( d ) ( e )
(f) (g)
Fig.2 (a) Secret image (b)share1 (c)share2 (d)share3 (e)share4
(f)Recovered secret (g)unrecovered secret
Stacking any combination of shares from share1,share2 and share3 reveals the secret.Hence,these are the qualifying shares.Whereas,stacking share4 with any combinations of share1,share2,share3 don’t reveal the secret,forming forbidden set of shares.It is clear that the shares thus produced in the first phase of the scheme are meaningless in appearance.
The secret image is thus broken into shares and covered with meaningful cover images so that none can recognize that these are the parts of some secret image.The secret can be revealed after overlapping the qualifying set of shares over tranperancies while the forbidden set can reveal nothing.These share images can now be stored in the database.This database needs to be secured by some alerting system so that any unauthorized user if accesses this database,the authorized person can get an alert by receiving an appropriate notification over his cell phone,so that he gets aware of some unauthorized activity taking place to the database.
Fig.5 Database screen asking for username and password
Username and password is an obvious first level of security to every kind of database.After entering the username and password,a random transaction password will be generated.Unless this password is entered,the database cannot be opened.
Copyright © 2013 SciResPub. IJOART
International Journal of Advancements in Research & Technology, Volume 2, Issue4, April-2013 263
ISSN 2278-7763 raphy scheme” IEEE TRANSACTIONS ON INFORMATION FO-
RENSICS AND SECURITY, VOL. 6, NO. 2, JUNE 2011 .
[3] Meg Coffin Murray Kennesaw State University, Kennesaw, GA,
USA” Database Security: What Students Need to Know ” Journal of
Information Technology Education: Volume 9, 2010 Innovations in
Practice.
[4] Ching-Nung Yang, Hsiang-Wen Shih, Chih-Cheng Wu, and Lein
Harn,”k out of n region incrementing scheme in visual cryptography”,IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR
Fig.6 The second password, after which notification is sent.
VIDEO TECHNOLOGY, VOL. 22, NO. 5, MAY
2012TRANSACTIONS ON SIGNAL PROCESSING, VOL. 48, NO. 8,
AUGUST 2000
[5] T Morkel,J H P Eloff,M.S.Olivier”An Overview Of Image stegnogra phy” Information and Computer Security Architecture (ICSA) Re-
As soon as, the transaction password is entered, a notification will be sent to the cell phone of authorized user to alert him that the database is being opened.So, the authorized person will be alerted everytime an attempt is made to access the database.Thus, whenever an unauthorized person, intentionally or unintentionally tries to access the database,a notification makes the authorized person aware of the undesired activity taking place to the database. search Group.images and videos” IEEE TRANSACTIONS ON SIG-
NAL PROCESSING, VOL. 48, NO. 8, AUGUST 2000
[6] Prof.S.S.Asole,S.M.Mundada “A Survey On Securiong Databases from Unauthorized Users”,International Journal of Scientific and
Technology Research(accepted for publication)
[7] Yu-Chi Chen, Gwoboa Horng, and Du-Shiau Tsai,”Comment on
“Cheating Prevention” in Visual cryptography”,IEEE TRANSAC-
TIONS ON IMAGE PROCESSING, VOL. 21, NO. 7, JULY 2012
Fig.7 Notification received on cell phone .
5 C
ONCLUSION
Thus, the paper discusses a dual security mechanism that can secure the contents stored in the database as well as the use of notification system ensures that the authorized user of database gets aware of the unauthorized activity taking place to the database.Thus, two levels of security can be provided to the databases.The notification system can be applied to any kind of applications which makes use of databases. The notification system can also be applied to any existing system’s databases.
A CKNOWLEDGMENT
We acknowledge our overwhelming gratitude and immense respect to our Head of the Department, Prof. S. Y. Amdani Sir and our Principal, Prof. Dr. K. Ravi Sir, who inspired us a lot to achieve the highest goal.
R EFERENCES
[1] Kai-Hui Lee and Pei-Ling Chiu,”An Extended Visual Cryptography
Algorithm for General Access Structures”, IEEE TRANSACTIONS
ON INFORMATION FORENSICS AND SECURITY, VOL. 7, NO. 1,
FEBRUARY 2012.
[2] Feng Liu and Chuankun Wu,”Embedded extended visual cryptog-
Copyright © 2013 SciResPub. IJOART



