ISE TACACS+ Configuration Guide for Wireless LAN Controllers
advertisement

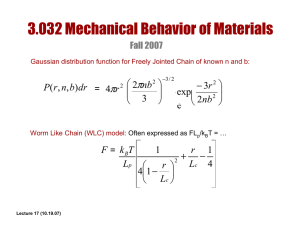
ISE TACACS+ Configuration Guide for Wireless LAN Controllers Secure Access How-to User Series Author: Aruna Yerragudi (Edited by Hsing-Tsu Lai) Date: December 2015 SECURE ACCESS HOW-TO GUIDES Table of Contents About this Guide ............................................................................................................................................................. 3 Overview .................................................................................................................................................... 3 Using this Guide ......................................................................................................................................... 3 Components Used ..................................................................................................................................... 3 ISE Configuration for Device Admin ............................................................................................................................. 4 Enabling Device Admin on ISE .................................................................................................................. 4 Device Admin Work Center ........................................................................................................................ 5 Configuring Network Device and Network Device Groups ......................................................................... 5 Defining Identity Stores .............................................................................................................................. 7 Configuring TACACS Profiles .................................................................................................................... 8 Device Admin Policy Sets .......................................................................................................................... 9 WLC Configuration for TACACS+ ................................................................................................................................ 12 Add a TACACS+ Authentication Server ................................................................................................... 12 Add a TACACS+ Authorization Server ..................................................................................................... 13 Add a TACACS+ Accounting Server ........................................................................................................ 13 Configure the Order of Authentication ...................................................................................................... 14 What’s Next? ................................................................................................................................................................. 15 Cisco Systems © 2015 Page 2 SECURE ACCESS HOW-TO GUIDES About this Guide Overview Terminal Access Controller Access Control System Plus (TACACS+) is a client-server protocol that provides centralized security control for users to gain management access to a router or any network access device. TACACS+ provides these AAA services: • Authentication – Who the users are • • Authorization – What they are allowed to do Accounting – Who did what and when This document provides configuration examples for TACACS+ with the Cisco Identity Services Engine (ISE) as the TACACS+ server and a Cisco Wireless LAN Controller (WLC) as the TACACS+ client. Using this Guide This guide divides into two parts for the activities to enable ISE to manage administrator accesses for WLC. • • Part 1 – Configuring ISE for Device Admin Part 2 – Configuring WLC for TACACS+ Components Used The information in this document is based on the software and hardware versions below: • • ISE Release 2.0 WLC with AireOS Software Versions 7.6 and 8.0 The materials in this document are created from the devices in a lab environment. All of the devices are started with a cleared (default) configuration. Cisco Systems © 2015 Page 3 SECURE ACCESS HOW-TO GUIDES ISE Configuration for Device Admin Licensing Device Admin on ISE Device Admin is licensed per deployment, but requires existing and valid ISE base or mobility licenses. Enabling Device Admin on ISE The Device Admin service (TACACS+) is not enabled by default in an ISE node. The first step is to enable it. Step 1 Step 2 Login to the ISE admin web portal using one of the supported browsers. Navigate to Administration > System > Deployment. Select the check box against the ISE node and click on Edit. Figure 1. ISE Deployment Page Step 3 Under General Settings, scroll down and select the check box against Enable Device Admin Service. Figure 2. ISE Deployment General Settings Step 4 Save the configuration. Device Admin Service is now enabled on ISE. Cisco Systems © 2015 Page 4 SECURE ACCESS HOW-TO GUIDES Device Admin Work Center ISE 2.0 introduces Work Centers for TrutSec and Device Administration. A work center contains all the elements for a particular feature. Step 1 Go to Work Centers > Device Administration > Overview Figure 3. Device Admin Overview The Device Administration Overview provides the high-level steps needed for the Device Admin Use Case. Configuring Network Device and Network Device Groups Let us now explore Network Devices and Network Device Groupings. ISE provides powerful device grouping in the form of multiple device group hierarchies. Each hierarchy represents a distinct and independent classification of network devices. Step 1 Navigate to Work Centers > Device Administration > Network Device Groups Figure 4. Network Device Groups Cisco Systems © 2015 Page 5 SECURE ACCESS HOW-TO GUIDES Step 2 All Device Types and All Locations are default hierarchies provided by ISE. You may add your own hierarchies or define the various components for identifying a Network Device which will be used later in the Policy Conditions. After defining various hierarchies, the Network Device Groups will look similar to the following: Figure 5. Network Device Group Tree View Step 3 Here we added the various device types and also locations. Now, add a WLC as a Network Device. Go to Work Centers > Device Administration > Network Resources. Click on Add to add a new Network Device DMZ_BLDO_vWLC. Figure 6. Adding Network Device Cisco Systems © 2015 Page 6 SECURE ACCESS HOW-TO GUIDES Enter the IP address of the Device and make sure to map the Location and Device Type for the Device. Finally, Enable the TACACS+ Authentication Settings and specify the Shared Secret. Defining Identity Stores This section is to define an Identity Store for the Device Administrators. The Identity Store can be ISE Internal Users and/or any supported External Identity Sources. For this configuration, we will use Active Directory (AD), an External Identity Source. Step 1 Go to Administration > Identity Management > External Identity Stores > Active Directory. Click on Add to define a new Active Directory Joint Point. Specify the Join Point name and the AD domain name and click on Submit. Figure 3. Adding AD Join Point Step 2 Click Yes when prompted “Would you like to Join all ISE Nodes to this Active Directory Domain?” Input the credentials with AD join privileges, and Join ISE to AD. Check the Status to verify it operational. Figure 4. Joining ISE to AD Step 3 Go to the Groups tab, and click on Add to get all the groups needed based on which the users are authorized for the device access. Below shows the groups used in the Authorization Policy in this guide Cisco Systems © 2015 Page 7 SECURE ACCESS HOW-TO GUIDES Figure 5. AD Groups Configuring TACACS Profiles We will define the three TACACS Profiles, to be used in the Authorization Policies – • • • WLC_Monitor_Only: Helpdesk with access to the Monitor tab WLC_Security_Access: Security Operators with access to Security and Commands tabs WLC_Admin: Administrators with full access. WLC uses TACACS+ Custom Attributes, which need to be defined as role1, role2, etc. The available roles are MONITOR, WLAN, CONTROLLER, WIRELESS, SECURITY, MANAGEMENT, COMMAND, ALL, and LOBBY. The first seven correspond to the menu options on the WLC admin web UI. You may enter one or more roles to allow read and write access to the particular features, and read-only for the rest. To grant read and write access to WLAN, SECURITY and CONTROLLER, then enter the following text: role1=WLAN role2=SECURITY role3=CONTROLLER Step 1 On the ISE GUI, go to Work Centers > Device Administration > Policy Results > TACACS Profiles. Add a new TACACS Profile called WLC_Monitor_Only. Scroll down to the Custom Attributes section to define access to only the MONITOR. Cisco Systems © 2015 Page 8 SECURE ACCESS HOW-TO GUIDES Figure 6. TACACS Profile for WLC_Monitor_Only Step 2 Click on Save to save the profile. Add another profile called WLC_Security_Access to provide access to the SECURITY and COMMANDS. Figure 7. TACACS Profile for WLC_Security_Access Step 3 Click on Save to save the profile. Add a third profile called WLC_Admin which provides access to all the tabs with role1=ALL as the attribute. Figure 8. TACACS Profile for WLC_Admin Device Admin Policy Sets Policy Sets are enabled by default for Device Admin. Policy Sets can divide polices based on the Device Types so to ease application of TACACS profiles. For example, Cisco IOS devices use Privilege Levels and/or Command Sets whereas WLC devices use Custom Attributes. Step 1 Navigate to Work Centers > Device Administration > Device Admin Policy Sets. Add a new Policy Set called WirelessLanControllers with the condition DEVICE:Device Type EQUALS Device Type#All Device Types#Network Device#Wireless Devices Figure 9. Policy Set Condition Step 2 Create the Authentication Policy. For Authentication, we will be using the Active Directory as the ID Store. Cisco Systems © 2015 Page 9 SECURE ACCESS HOW-TO GUIDES Figure 10. Authentication Policy Step 3 Define the Authorization Policy. Here we will be defining the authorization policy based on the users Group in Active Directory and the location of the device. For example, the users in Active Directory group West Coast can access only the devices located in West Coast whereas the users in Active Directory group East Coast can access only the devices located in East Coast. S Rule Name Conditions Shell Profiles WLC HelpDesk West demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/HelpDesk AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/West_Coast AND DEVICE:Location CONTAINS All Locations#West_Coast WLC_Monitor_Only WLC HelpDesk East demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/HelpDesk AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/East_Coast AND DEVICE:Location CONTAINS All Locations#East_Coast WLC_Monitor_Only WLC Security West demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/Security_Operators AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/West_Coast AND DEVICE:Location CONTAINS All Locations#West_Coast WLC_Security_Access WLC Security East demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/Security_Operators AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/East_Coast AND DEVICE:Location CONTAINS All Locations#East_Coast WLC_Security_Access WLC Admin E and W demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/Network_Operators AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/West_Coast AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/West_Coast Cisco Systems © 2015 WLC_Admin Page 10 SECURE ACCESS HOW-TO GUIDES S Rule Name Conditions Shell Profiles WLC Admin West demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/Network_Operators AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/West_Coast AND DEVICE:Location CONTAINS All Locations#West_Coast WLC_Admin WLC Admin East demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/Network_Operators AND demoAD:ExternalGroups EQUALS securitydemo.net/DemoGroups/East_Coast AND DEVICE:Location CONTAINS All Locations#East_Coast WLC_Admin Default DenyAllCommands Figure 11. Authorization Policy We are now done with the ISE configuration for Device Admin for WLC devices Cisco Systems © 2015 Page 11 SECURE ACCESS HOW-TO GUIDES WLC Configuration for TACACS+ In order to configure TACACS+ in the WLC controller, you need to complete these steps: 1. 2. 3. 4. Add a TACACS+ Authentication Server Add a TACACS+ Authorization Server Add a TACACS+ Accounting Server Configure the Priority Order of Management User Authentication Add a TACACS+ Authentication Server Complete these steps in order to add a TACACS+ Authentication Server. Step 1 From the WLC GUI, navigate to Security > AAA > TACACS+ > Authentication, and click New... Figure 12. TACACS+ Authentication Server Step 2 Enter the IP address of the ISE server as the TACACS+ server and the shared secret key. Figure 13. Adding TACACS+ Authentication Server Step 3 Click Apply. Cisco Systems © 2015 Page 12 SECURE ACCESS HOW-TO GUIDES Add a TACACS+ Authorization Server Complete these steps in order to add a TACACS+ Authorization Server. Step 1 From the WLC GUI, navigate to Security > AAA > TACACS+ > Authorization, and click New... Step 2 Add the IP address of the ISE server as the server IP address and the shared secret key. Figure 14. Adding TACACS+ Authorization Server Step 3 Click Apply Add a TACACS+ Accounting Server Complete these steps in order to add a TACACS+ Accounting Server. Step 1 From the WLC GUI, navigate to Security > AAA > TACACS+ > Accounting, and click New... Step 2 Enter the IP address of the ISE server as the server IP address and the shared secret key. Figure 15. Adding TACACS+ Accounting Server Step 3 Click Apply Cisco Systems © 2015 Page 13 SECURE ACCESS HOW-TO GUIDES Configure the Priority Order of Management User Authentication This step explains how to configure the priority order for management user authentication. The default controller configuration is local and RADIUS. With TACACS+, the order of authentication can be TACACS+ and local, or local and TACACS+. Step 1 From the GUI, go to Security > Priority Order > Management User. Using the arrows, Up, and Down buttons, select and order the Authentication to be TACACS+ followed by LOCAL Figure 16. Configuring the Order of Authentication Step 2 Click Apply. We are done with the WLC configuration for TACACS+. Cisco Systems © 2015 Page 14 SECURE ACCESS HOW-TO GUIDES What’s Next? At this point, all the needed configuration for Device Admin for WLC is completed. You will need to validate the configuration. Step 1 Step 2 Step 3 Login to WLC as various users belonging to the different groups and accessing different devices. When you login, verify that the user has access to the right tabs. For a user, who is a Helpdesk user, navigate to the different tabs and try to add/modify/delete. For example, go to WLANs and try to delete one of the WLAN. As this user has only MONITOR access, the operation should be denied with the following error Figure 17. Error message for Authorization Failure on WLC Step 4 From the ISE GUI, navigate to Operations > TACACS Livelog. All the TACACS authentication and authorization requests are captured here and the details button will give detailed information of why a particular transaction passed/failed. Figure 18. TACACS Livelogs Step 5 For historic reports, on ISE go to Work Centers > Device Administration > Reports > Device Administration to get the authentication, authorization and accounting reports. Cisco Systems © 2015 Page 15