Document 14131100
advertisement
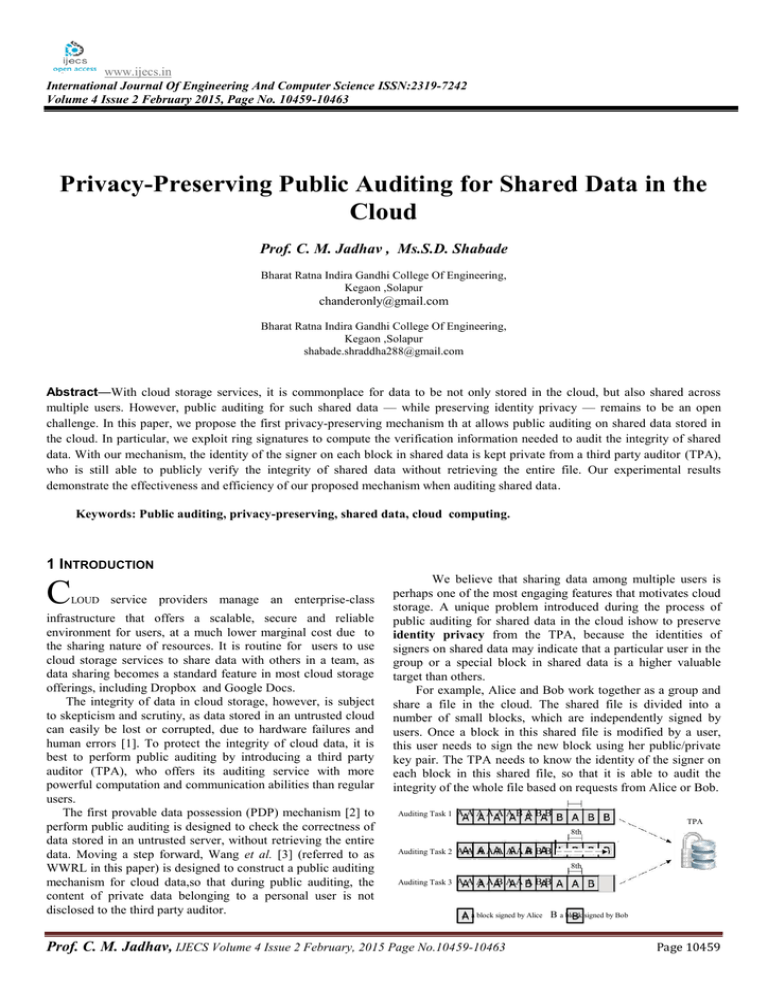
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 4 Issue 2 February 2015, Page No. 10459-10463 Privacy-Preserving Public Auditing for Shared Data in the Cloud Prof. C. M. Jadhav , Ms.S.D. Shabade Bharat Ratna Indira Gandhi College Of Engineering, Kegaon ,Solapur chanderonly@gmail.com Bharat Ratna Indira Gandhi College Of Engineering, Kegaon ,Solapur shabade.shraddha288@gmail.com Abstract—With cloud storage services, it is commonplace for data to be not only stored in the cloud, but also shared across multiple users. However, public auditing for such shared data — while preserving identity privacy — remains to be an open challenge. In this paper, we propose the first privacy-preserving mechanism th at allows public auditing on shared data stored in the cloud. In particular, we exploit ring signatures to compute the verification information needed to audit the integrity of shared data. With our mechanism, the identity of the signer on each block in shared data is kept private from a third party auditor (TPA), who is still able to publicly verify the integrity of shared data without retrieving the entire file. Our experimental results demonstrate the effectiveness and efficiency of our proposed mechanism when auditing shared data. Keywords: Public auditing, privacy-preserving, shared data, cloud computing. 1 INTRODUCTION C LOUD service providers manage an enterprise-class infrastructure that offers a scalable, secure and reliable environment for users, at a much lower marginal cost due to the sharing nature of resources. It is routine for users to use cloud storage services to share data with others in a team, as data sharing becomes a standard feature in most cloud storage offerings, including Dropbox and Google Docs. The integrity of data in cloud storage, however, is subject to skepticism and scrutiny, as data stored in an untrusted cloud can easily be lost or corrupted, due to hardware failures and human errors [1]. To protect the integrity of cloud data, it is best to perform public auditing by introducing a third party auditor (TPA), who offers its auditing service with more powerful computation and communication abilities than regular users. The first provable data possession (PDP) mechanism [2] to perform public auditing is designed to check the correctness of data stored in an untrusted server, without retrieving the entire data. Moving a step forward, Wang et al. [3] (referred to as WWRL in this paper) is designed to construct a public auditing mechanism for cloud data,so that during public auditing, the content of private data belonging to a personal user is not disclosed to the third party auditor. We believe that sharing data among multiple users is perhaps one of the most engaging features that motivates cloud storage. A unique problem introduced during the process of public auditing for shared data in the cloud ishow to preserve identity privacy from the TPA, because the identities of signers on shared data may indicate that a particular user in the group or a special block in shared data is a higher valuable target than others. For example, Alice and Bob work together as a group and share a file in the cloud. The shared file is divided into a number of small blocks, which are independently signed by users. Once a block in this shared file is modified by a user, this user needs to sign the new block using her public/private key pair. The TPA needs to know the identity of the signer on each block in this shared file, so that it is able to audit the integrity of the whole file based on requests from Alice or Bob. Auditing Task 1 AAAAAABABB TPA 8th Auditing Task 2 AAAAAAABBB Auditing Task 3 AAAABAAABB 8th A a block signed by Alice B a block signed by Bob Prof. C. M. Jadhav, IJECS Volume 4 Issue 2 February, 2015 Page No.10459-10463 Page 10459 Fig. 1. Alice and Bob share a file in the cloud. The TPA audits the integrity of shared data with existing mechanisms. verification information (i.e. signatures) are both stored in the cloud server. The third party auditor is able to verify the integrity of shared data in the cloud server on behalf of group members. As shown in Fig. 1, after performing several auditing tasks, some private and sensitive information may reveal to the TPA. On one hand, most of the blocks in shared file are signed by Alice, which may indicate that Alice is a important role in this group, such as a group leader. On the other hand, the 8-th block is frequently modified by different users. It means this block may contain high value data, such as a final bid in an auction, that Alice and Bob need to discuss and change it several times. As described in the example above, the identities of signers on shared data may indicate which user in the group or block in shared data is a higher valuable target than others. Such information is confidential to the group and should not be revealed to any third party. However, no existing mechanism in the literature is able to perform public auditing on shared data in the cloud while still preserving identity privacy. 2. Auditing Request Message 3. 1 In this paper, we propose Oruta , a new privacy-preserving public auditing mechanism for shared data in an untrusted cloud. In Oruta, we utilize ring signatures [4], [5] to construct homomorphic authenticators [2], [6], so that the third party auditor is able to verify the integrity of shared data for a group of users without retrieving the entire data — while the identity of the signer on each block in shared data is kept private from the TPA. In addition, we further extend our mechanism to support batch auditing, which can audit multiple shared data simultaneously in a single auditing task. Meanwhile, Oruta continues to use random masking [3] to support data privacy during public auditing, and leverage index hash tables [7] to support fully dynamic operations on shared data. A dynamic operation indi-cates an insert, delete or update operation on a single block in shared data. To our best knowledge, this paper represents the first attempt towards designing an effective privacy-preserving public auditing mechanism for shared data in the cloud. 2 EXISTING SYSTEM The first provable data possession (PDP) mechanism to perform public auditing is designed to check the correctness of data stored in an un trusted server, without retrieving the entire data. Moving a step forward, Wang et al. (referred to asWWRL in this paper) is designed to construct a public auditing mechnism for cloud data, so that during public auditing, the content of private data belonging to a personal user is not disclosed to the third party auditor. 3 PROBLEM STATEMENT 3.1 System Model As illustrated in Fig. 2, our work in this paper involves three parties: the cloud server, the third party auditor (TPA) and users. There are two types of users in a group: the original user and a number of group users. The original user and group users are both members of the group. Group members are allowed to access and modify shared data created by the original user based on access control polices [8]. Shared data and its . AuditingAuditing 1 Report Auditing Proof . 4 Shared Data Flow Fig. 2. Our system model includes the cloud server, the third party auditor and users. In this paper, we only consider how to audit the integrity of shared data in the cloud with static groups.It means the group is predefined before shared data is created in the cloud and the membership of users in the group is not changed during data sharing. The original user is responsible for deciding who is able to share her data before outsourcing data to the cloud. Another interesting problem is how to audit the integrity of shared data in the cloud with dynamic groups — a new user can be added into the group and an existing group member can be revoked during data sharing —while still preserving identity privacy. We will leave this problem to our future work. When a user (either the original user or a group user) wishes to check the integrity of shared data, she first sends an auditing request to the TPA. After receiving the auditing request, the TPA generates an auditing message to the cloud server, and retrieves an auditing proof of shared data from the cloud server. Then the TPA verifies the correctness of the auditing proof. Finally, the TPA sends an auditing report to the user based on the result of the verification. 3.2 Threat Model 2.2.1 Integrity Threats Two kinds of threats related to the integrity of shared data are possible. First, an adversary may try to corrupt the integrity of shared data and prevent users from using data correctly. Second, the cloud service provider may inadvertently corrupt (or even remove) data in its storage due to hardware failures and human errors. Making matters worse, in order to avoid jeopardizing its reputation, the cloud server provider may be reluctant to inform users about such corruption of data. Prof. C. M. Jadhav, IJECS Volume 4 Issue 2 February, 2015 Page No.10459-10463 Page 10460 2.2.2 Privacy Threats The identity of the signer on each block in shared data is private and confidential to the group. During the process of auditing, a semi-trusted TPA, who is only responsible for auditing the integrity of shared data, may try to reveal the identity of the signer on each block in shared data based on verification information. Once the TPA reveals the identity of the signer on each block, it can easily distinguish a high-value target (a particular user in the group or a special block in shared data). 3.3 Design Objectives To enable the TPA efficiently and securely verify shared data for a group of users, Oruta should be designed to achieve following properties: (1) Public Auditing: The third party auditor is able to publicly verify the integrity of shared data for a group of users without retrieving the entire data. (2) Correctness: The third party auditor is able to correctly detect whether there is any corrupted block in shared data. (3) Unforgeability: Only a user in the group can generate valid verification information on shared data. (4) Identity Privacy: During auditing, the TPA cannot distinguish the identity of the signer on each block in shared data. 4 PRELIMINARIES In this section, we briefly introduce cryptographic primitives and their corresponding properties that we implement in Oruta. 4.1 Bilinear Maps We first introduce a few concepts and properties related to bilinear maps. We follow notations from [5], [9]: 1) G1, G2 and GT are three multiplicative cyclic groups of prime order p; 2) g1 is a generator of G1, and g2 is a generator of G2; 3) is a computable isomorphism from G2 to G1, with (g2) = g1; 4) e is a bilinear map e: G1 × G2 ! GT with the following properties: Computability: there exists an efficiently computable algorithm for computing the map e. Bilinearity: for all u 2 G1, v 2 G2 and a, b 2 Zp, e(ua, vb) = e(u, v)ab. Non-degeneracy: e(g1, g2) 6= 1. These properties further imply two additional properties:(1) for any u1, u2 2 G1 and v 2 G2, e(u1 ・ u2, v) =e(u1, v) ・ e(u2, v); (2) for any u, v 2 G2, e( (u), v) = e( (v), u). 4.2 Ring Signatures The concept of ring signatures is first proposed by Rivest et al. [4] in 2001. With ring signatures, a verifier is convinced that a signature is computed using one of group members’ private keys, but the verifier is not able to determine which one. This property can be used to preserve the identity of the signer from a verifier. The ring signature scheme introduced by Boneh et al. [5] (referred to as BGLS in this paper) is constructed on bilinear maps. We will extend this ring signature scheme to construct our public auditing mechanism. Homomorphic authenticators (also called homomorphic verifiable tags) are basic tools to construct data auditing mechanisms [2], [3], [6]. Besides unforgeability (only a user with a private key can generate valid signatures), a homomorphic authenticable signature scheme, which denotes a homomorphic authenticator based on signatures, should also satisfy the following properties: Let (pk, sk) denote the • signer’s public/private key pair, _1 denote a signature on block m1 2 Zp, _2 denote a signature on block m2 2 Zp. Blockless verification: Given _1 and _2, two random values _1, _2 2 Zp and a block m0 = _1m1 + _2m2 2 Zp, a verifier is able to check the correctness of block m0 without knowing block m1 and m2. • • Non-malleability Given _1 and _2, two random values _1, _2 2 Zp and a block m0 = _1m1 + _2m2 2 Zp, a user, who does not have private key sk, is not able to generate a valid signature _0 on block m0 by linearly combining signature _1 and _2. Blockless verification allows a verifier to audit the correctness of data stored in the cloud server with a single block, which is a linear combination of all the blocks in data. If the combined block is correct, the verifier believes that the blocks in data are all correct. In this way, the verifier does not need to download all the blocks to check the integrity of data. Non-malleability indicates that an attacker cannot generate valid signatures on invalid blocks by linearly combining existing signatures. Other cryptographic techniques related to homomorphic authenticable signatures includes aggregate signatures [5], homomorphic signatures [10] and batchverification signatures [11]. If a signature scheme is blockless verifiable and malleable, it is a homomorphic signature scheme. In the construction of data auditing mechanisms, we should use homomorphic authenticable signatures, not homomorphic signatures. 5 HOMOMORPHIC AUTHENTICABLE RING SIGNATURES 5.1 Overview In this section, we introduce a new ring signature scheme, which is suitable for public auditing. Then, we will show how to build the privacy-preserving public auditing mechanism for shared data in the cloud based on this new ring signature scheme in the next section. As we introduced in previous sections, we intend to utilize ring signatures to hide the identity of the signer on each block, so that private and sensitive information of the group is not disclosed to the TPA. However, traditional ring signatures [4], [5] cannot be directly used into public auditing mechanisms, because these ring signature schemes do not support blockless verification. Without blockless verification, the TPA has to download the whole data file to verify the correctness of shared data, which consumes excessive bandwidth and takes long verification times. Therefore, we first construct a new homomorphic authenticable ring signature (HARS) scheme, which is extended from a classic ring signature scheme [5], denoted as BGLS. The ring signatures generated by HARS is able not only to preserve identity privacy but also to support blockless verification. 5.2 Construction of HARS 4.3 Homomorphic Authenticators Prof. C. M. Jadhav, IJECS Volume 4 Issue 2 February, 2015 Page No.10459-10463 Page 10461 HARS contains three algorithms: KeyGen, RingSign and RingVerify. In KeyGen, each user in the group generates her public key and private key. In RingSign, a user in the group is able to sign a block with her private key and all the group members’ public keys. A verifier is allowed to check whether a given block is signed by a group member in RingVerify. 6 Batch Auditing With the usage of public auditing in the cloud, the TPA may receive amount of auditing requests from different users in a very short time. Unfortunately, allowing the TPA to verify the integrity of shared data for these users in several separate auditing tasks would be very inefficient. Therefore, with the properties of bilinear maps, we further extend Oruta to support batch auditing, which can improve the efficiency of verification on multiple auditing tasks. . 7 CONCLUSION In this paper, we propose Oruta, the first privacypreserving public auditing mechanism for shared data in the cloud. We utilize ring signatures to construct homomorphic authenticators, so the TPA is able to audit the integrity of shared data, yet cannot distinguish who is the signer on each block, which can achieve identity privacy. To improve the efficiency of verification for multiple auditing tasks, we further extend our mechanism to support batch auditing. An interesting problem in our future work is how to efficiently audit the integrity of shared data with dynamic groups while still preserving the identity of the signer on each block from the third party auditor. REFERENCES [1] M. Armbrust, A. Fox, R. Griffith, A. D.Joseph, R. H.Katz, A. Konwinski, G. Lee, D. A. Patterson, A. Rabkin, I. Stoica, and M. Zaharia, “A View of Cloud Computing,” Communications of the ACM, vol. 53, no. 4, pp. 50–58, Apirl 2010. [2] G. Ateniese, R. Burns, R. Curtmola, J. Herring, L. Kissner, Z. Peterson,and D. Song, “Provable Data Possession at Untrusted Stores,” in Proc. ACM Conference on Computer and Communications Security(CCS), 2007, pp. 598–610. [3] C. Wang, Q. Wang, K. Ren, and W. Lou, “PrivacyPreserving Public Auditing for Data Storage Security in Cloud Computing,” in Proc. IEEE International Conference on Computer Communications(INFOCOM), 2010, pp. 525–533. [4] R. L. Rivest, A. Shamir, and Y. Tauman, “How to Leak a Secret,” in Proc. International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT). Springer-Verlag, 2001, pp. 552–565. [5] D. Boneh, C. Gentry, B. Lynn, and H. Shacham, “Aggregate and Verifiably Encrypted Signatures from Bilinear Maps,” in Proc. International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT). Springer-Verlag, 2003, pp. 416–432. [6] H. Shacham and B. Waters, “Compact Proofs of Retrievability,”in Proc. International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT). Springer Verlag, 2008, pp. 90–107.[7] Y. Zhu, H.Wang, Z.Hu, G.-J. Ahn, H. Hu, and S. S.Yau, “DynamicAudit Services for Integrity Verification of Outsourced Storage in Clouds,” in Proc. ACM Symposium on Applied Computing (SAC),2011, pp. 1550–1557. [8] S. Yu, C. Wang, K. Ren, and W. Lou, “Achieving Secure, Scalable,and Fine-grained Data Access Control in Cloud Computing,” in Proc. IEEE International Conference on Computer Communications(INFOCOM), 2010, pp. 534–542. [9] D. Boneh, B. Lynn, and H. Shacham, “Short Signature from the Weil Pairing,” in Proc. International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT).Springer-Verlag, 2001, pp. 514– 532.[10] D. Boneh and D. M. Freeman, “Homomorphic Signatures for Polynomial Functions,” in Proc. International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT). Springer-Verlag, 2011, pp. 149– 168.[11] A. L. Ferrara, M. Green, S. Hohenberger, and M. Ø. Pedersen,“Practical Short Signature Batch Verification,” in Proc. RSA Conference, the Cryptographers’ Track (CT-RSA). Springer-Verlag, 2009,pp. 309–324.[12] V. Goyal, O. Pandey, A. Sahai, and B. Waters, “Attribute-Based Encryption for FineGrained Access Control of Encrypted Data,”in Proc. ACM Conference on Computer and Communications Security (CCS), 2006, pp. 89–98. [13] A. Juels and B. S. Kaliski, “PORs: Proofs pf Retrievability for Large Files,” in Proc. ACM Conference on Computer and Communications Security (CCS), 2007, pp. 584–597.[14] G. Ateniese, R. D. Pietro, L. V. Mancini, and G. Tsudik, “Scalable and Efficient Provable Data Possession,” in Proc. International Conference on Security and Privacy in Communication Networks (SecureComm), 2008. [15] C. Erway, A. Kupcu, C. Papamanthou, and R. Tamassia, “Dynamic Provable Data Possession,” in Proc. ACM Conference on Computer and Communications Security (CCS), 2009, pp. 213–222. [16] C. Wang, Q. Wang, K. Ren, and W. Lou, “Ensuring Data Storage Security in Cloud Computing,” in Proc. IEEE/ACM International Workshop on Quality of Service (IWQoS), 2009, pp. 1–9. [17] B. Chen, R. Curtmola, G. Ateniese, and R. Burns, “Remote Data Checking for Network Coding-based Distributed Stroage Systems,” in Proc. ACM Cloud Computing Security Workshop (CCSW), 2010, pp. 31–42. [18] N. Cao, S. Yu, Z. Yang, W. Lou, and Y. T. Hou, “LT Codesbased Secure and Reliable Cloud Storage Service,” in Proc. IEEE International Conference on Computer Communications (INFOCOM), 2012. [19] S. Halevi, D. Harnik, B. Pinkas, and A. Shulman-Peleg, “Proofs of Ownership in Remote Storage Systems,” in Proc. ACM Conference on Computer and Communications Security (CCS), 2011, pp. 491–500. [20] Q. Zheng and S. Xu, “Secure and Efficient Proof of Storage with Deduplication,” in Proc. ACM Conference on Data and Application Security and Privacy (CODASPY), 2012. Prof. C. M. Jadhav, IJECS Volume 4 Issue 2 February, 2015 Page No.10459-10463 Page 10462 [21] M. Franz, P. Williams, B. Carbunar, S. Katzenbeisser, and R. Sion, “Oblivious Outsourced Storage with Delegation,” in Proc. Financial Cryptography and Data Security Conference (FC), 2011, pp. 127–140. [22] S. D. C. di Vimercati, S. Foresti, S. Paraboschi, G. Pelosi, and P. Samarati, “Efficient and Private Access to Outsourced Data,”WANG et al.: ORUTA: PRIVACY-PRESERVING PUBLIC AUDITING FOR SHARED DATA IN THE CLOUD 15in Proc. IEEE International Conference on Distributed Computing Systems (ICDCS), 2011, pp. 710–719. Prof. C. M. Jadhav, IJECS Volume 4 Issue 2 February, 2015 Page No.10459-10463 Page 10463

