Lecture 23
advertisement

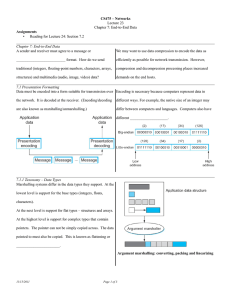
Lecture 23 Reminders: Programming Project 5 (reassigned Homework Problem 5.48) due on Thursday. Homework 7 due next Tuesday. Questions? Tuesday, November 15 CS 475 Networks - Lecture 23 1 Outline Chapter 7 - End-to-End Data 7.1 Presentation Formatting 7.2 Multimedia Data 7.3 Summary Tuesday, November 15 CS 475 Networks - Lecture 23 2 Introduction A sender and receiver must agree to a message or presentation format. How do we send traditional (integers, floating-point numbers, characters, arrays, structures) and multimedia (audio, image, video) data? We may want to use data compression to encode the data as efficiently as possible for network transmission. However, compression and decompression processing places increased demands on the end hosts. Tuesday, November 15 CS 475 Networks - Lecture 23 3 Presentation Formatting Data must be encoded into a form suitable for transmission over the network. It is decoded at the receiver. (Encoding/decoding are also known as marshalling/unmarshalling.) Tuesday, November 15 CS 475 Networks - Lecture 23 4 Presentation Formatting Encoding is necessary because computers represent data in different ways. For example, the native size of an integer may differ between computers and languages. Computers also have different endianess. Tuesday, November 15 CS 475 Networks - Lecture 23 5 Taxonomy – Data Types Marshalling systems differ in the data types they support. At the lowest level is support for the base types (integers, floats, characters). At the next level is support for flat types – structures and arrays. At the highest level is support for complex types that contain pointers. The pointer can not be simply copied across. The data pointed to must also be copied. This is known as flattening or serialization. Tuesday, November 15 CS 475 Networks - Lecture 23 6 Taxonomy – Data Types Argument marshalling: converting, packing and linearizing Tuesday, November 15 CS 475 Networks - Lecture 23 7 Taxonomy – Conversion Strategy Some systems convert all data to canonical intermediate form. For example a system may require that all integers be sent in big-endian regardless of the endianess of either the source or receiver. The alternative approach is receiver-makes-right in which the sender transmits data in its native form. The receiver is responsible for translating the data to its own local form. Tuesday, November 15 CS 475 Networks - Lecture 23 8 Taxonomy - Tags Tags can be sent with the data to indicate the type and length of a data item. A tag can also be used to indicate the endianess of the data in a receiver-makes-right system. If tags are not used then the receiver must be programmed to expect data of a particular type in a particular order. A 32-bit integer encoded in a tagged message Tuesday, November 15 CS 475 Networks - Lecture 23 9 Taxonomy - Stubs Stubs are typically used to implement argument marshalling in support of RPC. They may be either compiled or interpreted. Compiled stubs are more efficient while interpreted stubs are more flexible. Interpreted stubs translate data according to a data description file. Changing the data description file does not require recompilation. Tuesday, November 15 CS 475 Networks - Lecture 23 10 Taxonomy - Stubs A stub compiler produces stubs from an interface description. Tuesday, November 15 CS 475 Networks - Lecture 23 11 Examples - XDR External Data Representation (XDR) is used with SunRPC for argument marshalling. It supports the entire C type system except for function pointers. It uses a canonical intermediate form. It does not use tags (except to indicate array lengths) It uses compiled stubs. Tuesday, November 15 CS 475 Networks - Lecture 23 12 Examples - XDR Example XDR encoding of a structure containing a 32-bit integer, a 7 character string, and a 3 element 32-bit integer array. Tuesday, November 15 CS 475 Networks - Lecture 23 13 Examples - ASN.1 Abstract Syntax Notation One (ASN.1) is an ISO standard that defines a representation (the Basic Encoding Rules or BER) for data sent over a network. It supports all C types except function pointers, uses a canonical intermediate form, and it uses tags. The stubs can be either compiled or interpreted. Tuesday, November 15 CS 475 Networks - Lecture 23 14 Examples - ASN.1 Compound types (structures) can be created by means of nesting in ASN.1/BER. ASN.1/BER encoding of a 32-bit integer. The value is preceded by TYPE and LENGTH tags. Tuesday, November 15 CS 475 Networks - Lecture 23 15 Examples - ASN.1 ASN.1/BER LENGTH tags can be of variable size. If the data item is less than 128 bytes in length, the LENGTH tag is a single byte. If the data item is longer than 127 bytes, that LENGTH tag is multiple bytes long. The MSB of the leading byte is one. The remaining 7 bits indicate the length of the LENGTH tag. Tuesday, November 15 CS 475 Networks - Lecture 23 16 Examples - NDR Network Data Representation (NDR) uses receiver makes right. It supports the C type system. Data items are not tagged. Compiled stubs are generated from the Interface Description Language (IDL). NDR inserts an architecture tag (shown below) at the front of each message so that the receiver knows how to translate the data from source format to a local format. Tuesday, November 15 CS 475 Networks - Lecture 23 17 Markup Languages (XML) In XML all data are tagged and represented using text. <?xml version=”1.0”?> <employee> <name>John Doe</name> <title>Head Bottle Washer</title> <id>123456789</id> <hiredate> <day>5</day> <month>June</month> <year>1986</year> </hiredate> </employee> Tuesday, November 15 CS 475 Networks - Lecture 23 18 Markup Languages (XML) The XML data types and compound data type formats are defined in an XML Schema Definition (XSD) file. XSDs are also written in XML. XML messages are easy to read and edit. They are naturally portable between architectures. They are inefficient (compared to binary representations of data) and slow to parse. Tuesday, November 15 CS 475 Networks - Lecture 23 19 In-Class Exercise Write a C++ program that writes your name (first and last names), your age (as an integer) and the first 5 digits of π (3.1415) to memory using XDR (refer to the xdr man page). Normally this block of memory would then be sent across the network to another computer. Simulate this by copying the memory block to a new location (use memcpy) and then have your program read the values from the new location and display them to standard output. Email your program to the instructor. It is due by the beginning of the Thursday's class. Tuesday, November 15 CS 475 Networks - Lecture 23 20