Pricing a Shared Access Link for Fair and Efficient Joy Kuri
advertisement

Pricing a Shared Access Link for Fair and Efficient
Operation with Variable User Data Rates
Joy Kuri
Sharmili Roy
Centre for Electronics Design and Technology
Indian Institute of Science
Bangalore, India
Centre for Electronics Design and Technology
Indian Institute of Science
Bangalore, India
kuri@cedt.iisc.ernet.in
sharmili@cedt.iisc.ernet.in
ABSTRACT
The literature on pricing implicitly assumes an “infinite data”
model, in which sources can sustain any data rate indefinitely. We assume a more realistic “finite data” model,
in which sources occasionally run out of data; this leads to
variable user data rates. Further, we assume that users have
contracts with the service provider, specifying the rates at
which they can inject traffic into the network. Our objective
is to study how prices can be set such that a single link can
be shared efficiently and fairly among users in a dynamically
changing scenario where a subset of users occasionally has
little data to send. User preferences are modelled by concave
increasing utility functions. Further, we introduce two additional elements: a convex increasing disutility function and a
convex increasing multiplicative congestion-penalty function.
The disutility function takes the shortfall (contracted rate
minus present rate) as its argument, and essentially encourages users to send traffic at their contracted rates, while the
congestion-penalty function discourages heavy users from
sending excess data when the link is congested. We obtain
simple necessary and sufficient conditions on prices for fair
and efficient link sharing; moreover, we show that a single
price for all users achieves this. We illustrate the ideas using
some simple experiments.
Categories and Subject Descriptors
C.2.5 [local and Wide-Area Networks]: Access Schemes
General Terms
Design, Performance, Theory
Keywords
Pricing, Congestion, Fairness
1. INTRODUCTION AND RELATED WORK
Pricing has been suggested as a mechanism to control congestion and ensure fair and efficient operation of networks.
In much of the published literature ([3] [4] [6] [12] [13], [1]
[5]), elastic traffic is considered and the context of operation
is as follows. Each user of the network has a utility function
that quantifies the benefit that she derives from the network.
The utility function is an increasing (often, concave increasing) function of the rate at which the user can send data
through the network. The system objective is maximization
of the sum of all users’ utility functions. The problem is to
find the vector of users’ rates such that the system objective
is realized.
The resulting constrained optimization problem can be
solved in a centralized manner if all the utility functions
were known. In practice, however, there is no central authority that computes rates and further, the users’ utility
functions are not known. In [3], Kelly proposed a decentralized method to arrive at the system-optimal rates. In this
method, the network declares prices, and each user individually solves the problem of maximizing her net benefit or net
utility, which is her utility minus the total cost paid to the
network. He shows that there exists a vector of prices such
that the vector of individually optimal rates arrived at by
the users is, indeed, the system-optimal rate vector.
Nevertheless, several authors have pointed out that it is
enough to work under the assumption of direct revelation,
in which the users’ utility functions are revealed to a central
controlling authority ([7], [2]). In other words, we do not
lose anything by assuming that the users’ utility functions
are known because there always exists an equivalent formulation based on direct revelation. Accordingly, we assume
in this paper that users’ utility functions are known to the
central authority (the service provider) which can then use
this knowledge to design appropriate prices. It will turn
out that the complete utility function need not be known;
actually, far less knowledge suffices — only the derivative
of the utility function at a single point is enough. Further,
[8] mentions that prices are used in two kinds of problems:
one in which the objective is to promote fair and efficient
resource sharing, and another in which the objective is maximization of the revenue earned by the central authority. As
in [8], our objective in this paper is the former, viz., fair and
efficient sharing of a single access link; we do not consider
the problem of revenue maximization.
The published literature, however, tacitly assumes an infinite data model. Every source is assumed to have an infinite
backlog of data. The implication is that a source can send
traffic at any rate (obtained from the solution to the individual optimization problem) continuously — there is never
a dearth of data. In practice, of course, sources will occasionally run out of data. We consider a finite data model,
in which, occasionally, a source does not have enough data
to send. Therefore, a source may not be able to sustain a
data rate that is suitable for a fair and efficient operation of
the system.
Further, in practice, users have contracts with the service
provider (SP) that specify the rates at which they can send
traffic into the network. Hence, the practical problem is
often not to find out the correct vector of rates by using
a distributed algorithm—the correct vector is simply the
vector of contracted rates. Rather, it is important to devise a
scheme of operation such that any slack caused by a user who
is sending traffic at a rate lower than her contracted rate—
referred to as an “underuser” henceforth—can be utilized by
others. Correspondingly, a user with plenty of data available
is referred to as an “overuser” because she can send data at
a rate higher than her contracted rate.
We also believe that one must have congestion-dependent
and user-dependent pricing. If the network is not congested,
then the price should remain low, so that users with excess
data can utilize the network. But when the network becomes congested, the price should not increase equally for
all users; rather, those users that have exceeded their contracted rates and have caused congestion should be charged
heavily, while those who are compliant should be charged at
no more than their nominal rates. Even though our framework allows different prices for different users, our analysis
shows that a single price for all users suffices. This is attractive, because the management problem of maintaining
prices for a possibly large number of users is solved very
simply.
Summarizing, our approach is different from that in the
literature in the following respects: (a) finite data model,
(b) contracted rates and (c) congestion-dependent as well
as user-dependent pricing.
We are interested in ensuring that network operation is
characterised by the following.
• When some users are underusers because of limited
available data, it should be possible for others to increase their rates so as to utilize the slack. Does there
exist a pricing scheme such that users with plenty of
data available are encouraged to become overusers?
This means that in this situation, these users’ net utilities should be maximized at values higher than the
corresponding contracted rates.
• Later, when underusers wish to increase their rates because they have more data to send, they should have
the incentive to do so and overusers should be encouraged to back down. Does their exist a pricing scheme
such that this happens? Again, this means that the
users’ net utility values should be maximized at the
appropriate points.
In [9], [11] and [10], the authors consider priority queueing to provide differentiated services to a mix of elastic and
real-time traffic. Users choose the priority class to which
their traffic belongs. Higher priority traffic experiences better service but its price is higher. Game-theoretic analysis is
used to investigate whether a system equilibrium exists. [9]
also considers how the network operator can set prices such
that revenue is maximized at equilibrium. In our work, we
do not have multiple classes and we do not consider priority queueing. There is only one traffic class, carrying elastic
traffic.
2. MODEL
2.1 Utility function
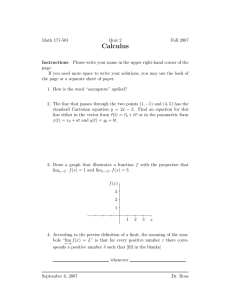
D(x)
i
Shortfall (x)
γi
λi
(shortfall = 0)
Figure 1: An example disutility function. The function need not be continuous at λi = γi . Disutility is
zero for λi ≥ γi , and convex increasing in shortfall
when the shortfall is strictly positive.
We consider a single link which is shared among N users,
where N is a given and fixed integer. The capacity of the
link is C bits/sec. We use a fluid model for traffic. User
i generates fluid at rate λi . We emphasize that this is a
variable, because the user may not be able to generate traffic
at a constant rate throughout.
User i has a contract to send traffic at rate γi , and the
price charged by the SP is πi ; this is the total price, not the
price per unit flow. When λi > γi , we call (λi − γi ) the
“excess rate.” Throughout this paper, we assume that the
sum of the contracted rates equals the link capacity, i.e.,
N
X
γi = C
i=1
The utility of user i is a concave strictly increasing function of the rate of user i traffic actually carried by the SP. We
assume that if a fraction β of the aggregate offered traffic is
dropped, then a fraction β of each user’s traffic is dropped.
This means that the dropped traffic is split equally among
all users. Then the utility for user i is Ui (λi (1 − β)).
2.2
Disutility function
When user i is not able to send traffic at her contracted
rate γi , i.e., the rate λi is less than γi , we consider a “disutility” for user i. This measures the amount of dissatisfaction
that user i suffers from at not being able to generate sufficient traffic. (γi − λi ) is referred to as the “shortfall” of user
i, and the disutility function is a convex increasing function
of shortfall. Further, the disutility function is defined to be
zero when λi ≥ γi . See Figure 1 for an example.
As mentioned in the previous section, one of our objectives is to design a scheme in which underusers have the
incentive to increase their rates of transmission when they
have sufficient data to send. The disutility function is crucial in making this possible. Intuitively, whenever a user
has sufficient data, it makes sense for her to send at a rate
λi ≥ γi because by doing so, the user can avoid paying the
“cost” imposed by the disutility function (because disutility is zero for λi ≥ γi ). The only situation where disutility
appears is when a user is hampered by not having enough
data to sustain a rate greater than or equal to γi .
2.3
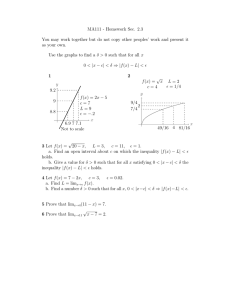
Multiplicative congestion-penalty function
The pricing scheme is characterized by the following fea-
Price
P(y)
i
Link congested
Congestion−penalty factor
convex−increasing with excess rate when link is congested
1
γi
(excess = 0)
Excess (y)
λi
Figure 2: An example congestion-penalty function.
The domain is λi ∈ [γi , ∞), i.e., the domain corresponds to excess ≥ 0.
tures. Underusers are charged less than their contracted
price. This is motivated by the goal of usage-based pricing.
If a user is sending at a rate which is a fraction f of her
contracted value, the charge is correspondingly a fraction f
of her contracted charge. However, overusers are charged
differently, depending upon whether the link is congested or
not.
When the link is not congested, overusers are charged
their contracted prices. The rationale for this is that as
long as there is no congestion, users should be permitted to
go above their contracted rates at no extra cost.
However, when the link is congested, overusers are charged
heavily, because the overusers are themselves responsible for
the congestion. If overuser i is sending at a rate λi > γi ,
then the price charged is πi Pi (λi − γi ), where Pi (.) is a
multiplicative congestion-penalty function, and it takes the
excess rate (λi − γi ) as its argument. Pi (λi − γi ) is a convex
increasing function of excess rate. Because the congestionpenalty function appears only when the link is congested
and user i is an overuser, we set Pi (0) = 1. An example is
shown in Figure 2.
In Figure 3, we give a schematic representation of the
pricing scheme. We plot the price paid by user i versus her
traffic rate λi . There are two curves: one for an uncongested link and the other for a congested link. As long as
λi < γi , i is an underuser and is therefore charged less than
πi . When λi increases beyond γi , the price is maintained
at πi for the uncongested link; but for the congested link,
the multiplicative congestion-penalty function appears, the
price is πi Pi (λi − γi ) and the price paid rises steeply.
2.4 Net utility function
The “net utility” of user i is defined to be her utility minus
disutility (which may be zero) minus the price paid to the
SP.
2.5 Fair and Efficient Link Sharing
Our intention is to understand how the prices πi , 1 ≤
i ≤ N , can be set, so that the system behaviour is “desirable” in the following sense. Let L and H denote the set of
underusers and overusers, respectively.
When the resource is not congested because users in L
are below their contracted rates, other users in the complement Lc are not prevented from going above their contracted
rates. This is desirable so that the resource is fully utilized.
Suppose that the resource is fully utilized and, further,
π
Link not congested
i
Price remains at contracted value
when link is not congested
γi
λi
Figure 3: Schematic showing how the price charged
by the SP changes, depending on both the rate at
which a user sends traffic and the state of congestion
of the link.
that there is no congestion. Now if users in L wish to increase their rates and go up to their contracted values, they
should have the incentive to do that; at the same time, users
in H should have the incentive to reduce their rates. This
is desirable so that users in L can reclaim their share of the
network resources from users in H when they wish to do so.
3.
ANALYSIS
In this section, we explore how the prices πi , 1 ≤ i ≤ N ,
can be set so that desirable behaviour occurs. We focus on
user i and assume that the transmission rates λj of the other
users j, 1 ≤ j ≤ N, j 6= i, are given and fixed.
We provide the proof-outlines of the following results in
the Appendix. In all cases, the proofs are based on the
definition of net utility for that case, elementary calculus
and simple algebra. Throughout the rest of the paper we
denote the aggregate
P sum of rates of all users except user i
by θi , i.e., θi = N
j=1 λj .
j6=i
3.1
Other users below aggregate contracted
rate
In this section, we consider a system where θi < (C − γi ).
In such a system, user i should have the incentive to transmit
at a rate (C − θi ), so that the link is fully utilized, but
without causing congestion. We wish to find out how to set
the price πi such that this goal is achieved. The net utility
function for user i is denoted as N Ui . Following are the
three different situations which can arise depending upon
the flow rate of user i.
• When λi < γi ,
N Ui
= Ui (λi ) − Di (γi − λi ) −
λ i
γi
πi
• When γi ≤ λi ≤ (C − θi ),
N Ui
=
• When λi ≤ (C − θi ),
Ui (λi ) − πi
• When λi > (C − θi ),
N Ui
=
Ui (λi (1 − β)) − πi Pi (λi − γi )
Ui
> 0, then i has incentive to increase her rate beyond
If dN
dλi
λi . Corresponding conclusions apply when the derivative at
λi is negative or zero.
Lemma 3.1. When the total traffic from users j ∈ {1, 2, ..
., N }, j 6= i, is less than their aggregate contracted rate, N Ui
is maximized at the point λ∗i = (C − θi ) if and only if the
price πi satisfies
Ui0 (C − θi )
θi
≤ πi ≤ γi (Ui0 (γi ) + lim Di0 (x)) (1)
0
x→0+
C Pi (C − θi − γi )
Further, N Ui is an increasing function of λi to the left of
λ∗i and a decreasing function of λi to the right of λ∗i .
Here, limx→0+ Di0 (x) indicates the right-hand limit of Di0 (x)
as x goes to zero, i.e., as x goes to zero while remaining
positive always. This is necessitated by the definition of the
disutility function D(x) with x denoting the shortfall; as
Figure 1 showed, D(x) need not be continuous at x = 0.
3.2 Other users at aggregate contracted rate
Here we have θi = (C − γi ). User i needs to transmit
at a rate γi so that the link is fully utilized and yet there
is no congestion. The net utility function for the different
situations in this case are defined as follows.
• When λi < γi ,
N Ui
=
Ui (λi ) − Di (γi − λi ) −
λ i
γi
πi
• When λi ≥ γi ,
N Ui
=
= Ui (λi ) − Di (γi − λi ) −
N Ui
Ui (λi (1 − β)) − πi Pi (λi − γi )
Lemma 3.2. When the total traffic from users j ∈ {1, 2, ..
., N }, j 6= i, is equal to their aggregate contracted rate, N Ui
is maximized at the point λ∗i = γi if and only if the price πi
satisfies
Ui0 (γi )
C − γi
≤ πi ≤ γi (Ui0 (γi ) + lim Di0 (x))
x→0+
C
limx→0+ Pi0 (x)
(2)
Further, N Ui is an increasing function of λi to the left of
λ∗i and a decreasing function of λi to the right of λ∗i .
We note that the interval in Equation 2 is a subset of that
in Equation 1 because the lower bounds are ordered. So, a
choice of πi satisfying Equation 2 will always satisfy Equation 1.
3.3 Other users above aggregate contracted
rate
Because the other users are sending an aggregate amount
of traffic that exceeds the sum of their contracted rates,
we have θi > (C − γi ). In this case, it is desirable that,
notwithstanding the congested link, user i be able to increase
her rate to her “rightful” share γi while other users back
down. We can write the expressions for net utility function
in different situations as
λ i
γi
• When (C − θi ) < λi < γi ,
N Ui
Ui (λi (1 − β)) − Di (γi − λi ) −
=
πi
λ i
γi
πi
• When λi ≥ γi ,
N Ui
=
Ui (λi (1 − β)) − πi Pi (λi − γi )
Lemma 3.3. When the total traffic from users j ∈ {1, 2, ..
., N }, j 6= i, is more than their aggregate contracted rate,
N Ui is maximized at the point λ∗i = γi if and only if the
price πi satisfies
ηi Ui0 (µi γi )
0
0
≤ πi ≤ γi ηi Ui (µi γi ) + lim Di (x)
(3)
x→0+
limx→0+ Pi0 (x)
θi
and ηi = γµi i+θ
. Further, N Ui is an
where µi = γi C
+θi
i
increasing function of λi to the left of λ∗i and a decreasing
function of λi to the right of λ∗i .
Having obtained the three ranges of πi , we would like to
know what the intersection of the three ranges looks like.
The significance of this is that it may be possible to choose
a value of πi that will work (i.e., lead to desirable behaviour)
irrespective of whether the aggregate traffic from users j ∈
{1, 2, . . . , N }, j 6= i, is below, at or above the corresponding
aggregate contracted rate.
U 0 (0)
i
Lemma 3.4. πi = limx→0+
lies within all the three
Pi0 (x)
intervals if we choose γi such that
γi ≥
Ui0 (0)
0
(limx→0+ Di (x))(limx→0+
(4)
Pi0 (x))
Proof. The left edge in Equation 1 is smaller than the left
edge in Equation 2. Also, the right edges in the two cases
are the same. So, it is enough to ensure that the second
case is a valid interval. We know that the utility function
is a concave increasing function and penalty function is a
convex increasing function. So
C − γ Ui0 (γi )
Ui0 (0)
i
≤
0
C
limx→0+ Pi (x)
limx→0+ Pi0 (x)
If we choose γi such that it satisfies Equation 4,
γi (Ui0 (γi ) + lim Di0 (x)) ≥
x→0+
Ui0 (0)
limx→0+ Pi0 (x)
U 0 (0)
i
Equations 1 and 2 are non-void intervals and limx→0+
Pi0 (x)
lies within both the intervals. Similarly
in
Equation
3,
the
θi
lower bound on πi has µi < 1 and γi +θi ≤ 1. So the
U 0 (0)
i
lower bound is less than limx→0+
. And if γi is chosen
Pi0 (x)
according to Equation 4, the upper bound will definitely
Ui0 (0)
exceed limx→0+
, therefore allowing us to choose πi =
P 0 (x)
Ui0 (0)
.
limx→0+ Pi0 (x)
i
U 0 (0)
i
Hence, γi ≥ (limx→0+ P 0 (x))(lim
for i = 1, 2, ..
0
x→0+ Di (x))
i
., N , ensures that the intersection interval for each i is nonUi0 (0)
empty, and πi = limx→0+
lies within this intersection
Pi0 (x)
interval.
2
Lemma 3.5. If we choose a γi such that
γi ≥ (5)
where the maximization and minimization are done over
l = {1, 2, ..., N }, one single value of price for all users irrespective of the congestion state of the link, is sufficient for
the desirable behaviour. That value of price is
πi =
maxl limx→0+ Ul0 (x)
minl limx→0+ Pl0 (x)
∀i ∈ {1, 2, . . . , N }
EXPERIMENTAL RESULTS WITH MULTIPLE USERS ACCESSING A SINGLE
LINK
In this section we provide experimental results of two simulations done in MATLAB 7.0. In these simulations multiple
users access a single link and we study the dynamics of the
rates of all the users when some of them are occasionally
data limited.
4.1
maxl Ul0 (0)
minl limx→0+ Pl0 (x) minl limx→0+ Dl0 (x)
∀i ∈ {1, 2, . . . , N }
4.
(6)
4 users accessing a link of capacity 5 units
The link capacity C is assumed to be 5 units and the number of users N = 4. In this experiment we assume a simple
utility function for all users, the utility is just the carried
traffic rate i.e., Ui (λi ) = λi for all i ∈ {1, 2, . . . , N }. If β
is the fraction of traffic dropped by the link then Ui (λi (1 −
β)) = λi (1 − β). We choose the disutility function to be exponential function of the shortfall. So, Di (γi −λi ) = e(γi −λi )
for all users. Finally, the penalty function is also taken to
be an exponential function of the excess rate. Pi (λi − γi ) =
e(λi −γi ) for all users. According to Lemma 3.5, for all i ∈
{1, 2, . . . , N }
γi
≥
=
Proof. We have already shown that for all users i =
{1, 2, ..., N }, the lower bound of πi can attain a maximum
Ui0 (0)
value of limx→0+
. So if πi is chosen according to EquaPi0 (x)
tion 6, for all users, πi will exceed their respective lower
limits.
If γi is such that it satisfies Equation 5, then
γi lim Di0 (x)
x→0+
≥
maxl Ul0 (0) limx→0+ Di0 (x)
minl limx→0+ Pl0 (x) minl limx→0+ Dl0 (x)
≥
maxl Ul0 (0)
minl limx→0+ Pl0 (x)
Therefore, the upper bound of πi for all i = {1, 2, ..., N } is
maxl Ul0 (0)
bigger than min limx→0+
.
P 0 (x)
l
l
2
It can be seen that when prices are set according to Equation 6, (γ1 , γ2 , . . . , γN )t is a Nash equilibrium. Considering
any i ∈ {1, 2, . . . , N }, we find that the aggregate rate from
the other users is equal to the sum of their contracted rates,
and therefore, Lemma 3.2 applies. This means that user i
has no incentive to change her rate from γi , and this conclusion applies to all the users. Hence, (γ1 , γ2 , . . . , γN )t is a
Nash equilibrium when prices are set according to the intervals mentioned in Lemma 3.4.
Moreover, it can be seen that (γ1 , γ2 , . . . , γN )t is the unique
Nash
PN equilibrium in this problem. We consider a λ with
j=1 λj = C, but with one i for which λi > γi . Then,
there
PNmust be aPkNfor which λk < γk . With respect to this
k,
j=1 λj >
j=1 γj , and the third case above applies.
j6=k
j6=k
Therefore, by Lemma 3.3, k would like to increase her rate to
γP
k . Hence λ is not a Nash
PN equilibrium. In other cases as well
( N
j=1 λj > C and
j=1 λj < C) we can argue similarly.
Hence, (γ1 , γ2 , . . . , γN )t is the unique Nash equilibrium here.
πi
=
=
1
U 0 (0)
limx→0+ P 0 (x) limx→0+ D0 (x)
U 0 (0)
limx→0+ P 0 (x)
1
So we choose the vector of contracted rates to be [1 1 1 2].
We observe that the contracted rates of all the users add up
to the capacity of the link. An initial rate vector λ is chosen
in which some users are above their contracted rates and
some are below theirs. For this four-user system we take λ
= [1.5 2 0.5 1.5]. So users 1 and 2 are overusers and users
3 and 4 are underusers. This means that at the start of the
simulation, some users have limited data to send and hence
they are not able to utilize their contracted rates fully. Just
after the start, we assume that the limited data condition
is removed, and each user now has sufficient data to sustain
any data rate. Each user explores the neighbourhood of her
present rate value to see if her net utility can be improved.
In the MATLAB experiment, we use a step size of 0.01.
From Lemma 3.5, we can set a price of πi = 1, 1 ≤ i ≤ 4.
On applying this price-value, we observe that each user converges to her contracted rate in the process of maximizing
her respective net utility. Figure 4 illustrates these results.
Now suppose user 1 and 2 run out of data and their rates
drop to 0.5 and 0.7, respectively. We would like users 3 and
4 to use up the spare capacity left by users 1 and 2. At this
point, λ= [0.5 0.7 1 2]. According to Lemma 3.5, π3 = 1 and
π4 = 1 will allow users 3 and 4 to go above their contracted
rates and use the spare bandwidth.
In the simulation, we keep user 1 and 2 fixed at 0.5 and 0.7
respectively and allow users 3 and 4 to keep checking their
net utilities at each iteration and trying to maximize it as
described previously. We observe that user 3 increases her
rate from 1 to 1.4 and user 4 increases hers from 2 to 2.4, thus
equally sharing the extra bandwidth between themselves.
Figure 5 shows these results.
Now let us assume that user 1 and 2 again have large
amounts of data to send, and can sustain any rate. We
Change in the rates of all users assuming "infinite data model"
2.2
user 1
user 2
user 3
user 4
1.6
2
1.8
Rates of all users
Rates of all users
1.8
1.4
1.2
1
1.6
1.4
1.2
1
0.8
0.8
0.6
0.6
0
50
100
150
200
Number of iterations
250
0.4
300
Figure 4: Just before the start, λ = [1.5 2 0.5 1.5].
At the start of the simulation, all users have sufficient data to sustain any rate. The pricing scheme
ensures that the rates of all the users converge to
their respective contracted values.
would like to find out whether they can reclaim their share
of bandwidths again. At this point, λ = [0.5 0.7 1.4 2.4].
We know that price-values equal to one unit for all users will
allow this recapture of bandwidth share. In the simulation,
all users monitor their respective net utilities at each iteration and try to maximize it. We find that at equilibrium,
all users again converge to their respective contracted rates.
Figure 6 shows these results.
This experiment illustrates that it is possible to assign
prices once and for all at the beginning, such that this price
vector ensures fair and efficient link sharing no matter what
the sets of underusers and overusers may be. Also, the SP
need not have to store N different prices for N users.
4.2
user 1
user 2
user 3
user 4
2.2
2
0.4
Once all users converge to their contracted rates, some of them run out of data.
The others then share the spare bandwidth among themselves.
2.4
users accessing a link of capacity
units
20
27
In this experiment 20 users are trying to access a link having a capacity of 27 units. We choose the following utility,
penalty and disutility functions for all users.
U (λi )
=
log(1 + λi )
P (λi − γi )
D(γi − λi )
=
=
1 + (λi − γi )2 + 2(λi − γi )
(γi − λi )2 + 2(γi − λi )
From Lemma 3.5, we know that the contracted rate γi and
the contracted price πi for all i ∈ {1, 2, . . . , N } should satisfy
γi
≥
=
πi
=
=
U 0 (0)
limx→0+ P 0 (x) limx→0+ D0 (x)
0.25
U 0 (0)
limx→0+ P 0 (x)
0.5
Accordingly, we divide these 20 users into 4 groups. Users
1, 2, 3 and 4 belong to the first group and they have a
0
100
200
300
Number of iterations
400
500
600
Figure 5: Just before time 250, all users are at their
contracted values. At time 250, users 1 and 2 are
limited to sending traffic at rates 0.5 and 0.7, respectively. The pricing scheme ensures that users 3 and
4 are able to go beyond their contracted rates and
utilize the link fully.
contracted rate of 0.5 units each. So the contracted rate
vector for users in group 1 is γg1 = [0.5 0.5 0.5 0.5]. Users 5,
6, 7, 8 and 9 belong to second group and have a contracted
rate of 1 unit each. So γg2 = [1.0 1.0 1.0 1.0 1.0] where the
first element of the vector is the contracted rate of user 5 and
so on. Group 3 consists of users 10, 11, 12 and 13 with γg3 =
[1.5 1.5 1.5 1.5]. And users 14, 15, 16, 17, 18, 19 and 20 form
the fourth group having the contracted rate vector as γg4 =
[2.0 2.0 2.0 2.0 2.0 2.0 2.0]. We can see that the contracted
rates sum up to the capacity of the link. We choose an intial
rate vector in which some users are underusers and some are
overusers. For this experiment, we select the initial rates in
the following manner. For the users in group 1 we choose
rate vector to be λg1 = [0.1 0.1 0.7 0.7]. So users 1 and 2 are
underusers and users 3 and 4 are overusers. Similarly, we
take the rate vector for group 2 as λg2 = [1.0 1.0 1.2 1.7 0.2].
Here users 7 and 8 are overusers and user 9 is underuser. In
case of group 3, λg3 = [1.8 2.0 0.1 0.2] with users 10 and
11 being overusers and 12 and 13 being underusers. Finally,
λg4 = [2.0 2.0 1.1 0.6 0.2 2.8 4.0] having users 16, 17 and 18
as underusers and users 19 and 20 as overusers.
Now we remove the finite data restriction and assume that
all users can sustain any rate. Each user explores the neighbourhood of her present rate to see where her net utility
can be improved. Again we keep the step size as 0.01. On
applying a price of 0.5 units for each user, we would expect
the underusers to go upto their contracted rates and the
overusers to come down to their contracted rates. Figure 7
shows the experimental results for this situation. At the
end of 250th iteration, all the users have converged to their
respective contracted rates thereby making the flow rate vector equal to the contracted rate vector.
Now we assume that some of the users run out of data and
therefore cannot sustain their contracted rates. Specifically,
user 1
user 2
user 3
user 4
Rates of all users
1.8
1.6
1.4
1.2
1
0.8
0.6
0.4
0.2
100
200
300
400
500
Number of iterations
600
700
800
Figure 6: Continuation of the experiment in Figures 4 and 5. At time 500, underusers 1 and 2 are
again ready to send traffic at high rates. The pricing scheme ensures that the underusers reclaim their
bandwidth shares while the overusers 3 and 4 back
down.
in group 1 we assume that users 1 and 4 run out of data
and can sustain rates of only 0.2 and 0.1 units respectively.
Therefore, at 251th iteration, λg1 = [0.2 0.5 0.5 0.1]. In
group 2, we assume users 6 and 7 are stuck at 0.5 and 0.4
respectively therefore making λg2 = [1.0 0.5 0.4 1.0 1.0]. Let
us say users 10 and 11 in group 3 are data limited to a rate
of 1.2 and 0.8 units which gives λg3 = [1.2 0.8 1.5 1.5]. Users
14, 15, 16 and 20 in group 4 are stuck at 1.4, 1.6, 1.8 and 1.2
respectively. So λg4 = [1.4 1.6 1.8 2.0 2.0 2.0 1.2]. At this
point, we would want the users who are not data limited
to utilize the spare room created by these underusers. We
observe that the price of 0.5 units for all users is sufficient
for this to happen. Figure 8 shows the simulation results
where we see that users 2, 3, 5, 8, 9, 12, 13, 17, 18 and 19 go
above their contracted rates to use up the link fully. At the
500th iteration, the flow rate converges to λg1 = [0.200 0.975
0.995 0.100], λg2 = [1.475 0.500 0.400 1.495 1.475], λg3 =
[1.200 0.800 1.975 1.975] and λg4 = [1.400 1.600 1.800 2.475
2.475 2.475 1.200]. Although some users are underusers,
cummulatively all the users are able to use up 26.99 units
of bandwidth out of the full capacity of 27 units.
At the 501th iteration, we assume that the underusers now
have enough data to sustain any rate. Now the overusers
should back down and let underusers gain back their share
of the bandwidth. Figure 9 shows this behaviour. By the
end of 600th iteration, all the users again converge to their
respective contracted rates. So a fixed price of 0.5 units for
all users was sufficient to enforce desirable behaviour in the
link.
5. STABILITY
When no user is constrained by limited amounts of available data, what is the rate vector that the collection of users
converges to? When prices are set according to Equation 4,
lambda for users with gamma=1.5
0
user 1
user 2
user 3
user 4
0.8
0.6
0.4
lambda for users with gamma=1
2
Changes in the rates of all users assuming "infinite backlog model"
2
1
0
0
50
2.5
100 150 200
Number of iterations
250
2
1.5
1
user 10
user 11
user 12
user 13
0.5
0
0
50
100 150 200
Number of iterations
250
300
1.5
1
user 5
user 6
user 7
user 8
user 9
0.5
0
300
lambda for users with gamma=2
2.2
lambda for users with gamma=0.5
Dynamics of rates of all users
2.4
0
50
3.5
100 150 200
Number of iterations
250
300
3
2.5
2
1.5
1
0.5
0
0
50
100 150 200
Number of iterations
user 14
user 15
user 16
user 17
user 18
user 19
250user 20300
Figure 7: Just before the start, λ =[λg1 λg2 λg3
λg4 ]=[0.1 0.1 0.7 0.7 1.0 1.0 1.2 1.7 0.2 1.8 2.0 0.1 0.2
2.0 2.0 1.1 0.6 0.2 2.8 4.0]. At the start of the simulation, all users have sufficient data to sustain any
rate. The pricing scheme ensures that the rates of
all the users converge to their respective contracted
values.
it has been argued earlier that (γ1 , γ2 , . . . , γN )t is the unique
Nash equilibrium. Hence, when prices are set in accordance
with the conditions, system stability is assured.
6.
CONCLUSION
We considered sources that could occasionally be constrained by limited amounts of available data. Further, each
user has a contract with the service provider, specifying the
rate at which she can send traffic into the network. We
were interested in a congestion-dependent as well as userdependent pricing scheme that would ensure fair and efficient sharing of the single link shared by the sources.
We introduced the idea of disutility for underusers and
noted that the disutility term encourages underusers to increase their rates whenever they have sufficient data. We
presented simple necessary and sufficient conditions for setting prices such that fair and efficient sharing of the link is
possible and observed that one value of price for all users
can achieve this. The SP is not required to store different
0.4
0.2
0
0
100
2.5
200 300 400
Number of iterations
500
2
1.5
1
0.5
0
600
0
100
200 300 400
Number of iterations
user 5
user 6
user 7
user 8
user 9
1
0.5
0
1
0.8
0.6
0.4
0.2
0
0
100
3.5
200 300 400
Number of iterations
500
600
3
2.5
user 14
user 15
user 16
user 17
user 18
user 19
user 20
2
1.5
user 10
1
user 11
0.5
user 12
user 13
0
500 600 0
100
200 300 400
Number of iterations
500
600
lambda for users with gamma=1
0.6
1.5
Dynamics of rates of all users
2
user 1
user 2
user 3
1.5
user 4
1.2
0
200
2.5
400
600
Number of iterations
1.5
1
0
user 10
user 11
user 12
user 13
0
200
400
600
Number of iterations
0.5
0
200
3.5
2
0.5
user 5
user 6
user 7
user 8
user 9
1
0
800
lambda for users with gamma=2
user 1
user 2
user 3
user 4
lambda for users with gamma=0.5
0.8
lambda for users with gamma=1.5
1
lambda for users with gamma=1
1.2
lambda for users with gamma=2
lambda for users with gamma=0.5
lambda for users with gamma=1.5
When all users converge to their contracted rates, some of them run out of data.
The others then share the spare bandwidth among themselves.
2
800
400
600
Number of iterations
800
3
2.5
2
1.5
1
0.5
0
0
200
400
Number of iterations
user 14
user 15
user 16
user 17
user 18
user 19
600 user 20800
Figure 8: Just before time 250, all users are at their
contracted values. At time 250, users 1, 4, 6, 7, 10,
11, 14, 15, 16 and 20 are limited to sending traffic
at rates 0.2, 0.1, 0.5, 0.4, 1.2, 0.8, 1.4, 1.6, 1.8 and 1.2
respectively. The pricing scheme ensures that users
2, 3, 5, 8, 9, 12, 13, 17, 18 and 19 are able to go beyond
their contracted rates and utilize the link fully.
Figure 9: Continuation of the experiment in Figures 7 and 8. At time 500, underusers 1, 4, 6, 7, 10,
11, 14, 15, 16 and 20 are again ready to send traffic
at high rates. The pricing scheme ensures that the
underusers reclaim their bandwidth shares while the
overusers 2, 3, 5, 8, 9, 12, 13, 17, 18 and 19 back down.
prices for different users and keep changing them dynamically depending upon the congestion state of the link. Some
simple experiments in MATLAB demonstrated the utility of
our approach.
We recognize the following limitations of our work. Firstly,
we considered the resource to be only a single link; in general, of course, the resource is a full network. This is the
topic of ongoing work. Secondly, we have not explicitly considered the problem of revenue maximization for the service
provider. While our goals of fair and efficient sharing of the
link are natural and would, indirectly, lead to high revenue
for the provider, we would like to consider the problem of
explicit revenue maximization as well.
France Telecom – R & D, 2002.
[3] F. Kelly. Charging and rate control for elastic traffic
(corrected version). European Transaction on
Telecommunication, 8(1):33–37, Jan 1997.
[4] F. Kelly, A. K. Maulloo, and D. Tan. Rate control for
communication networks: shadow prices, proportional
fairness and stability. J. Oper. Res. Soc.,
49(3):237–252, Mar 1998.
[5] S. Kunniyar and R. Srikant. End-to-end congestion
control schemes: Utility functions, random losses and
ecn marks. IEEE/ACM Transactions on Networking,
11(5):689–702, Oct 2003.
[6] R. J. La and V. Anantharam. Utility-based rate
control in the internet for elastic traffic. IEEE
Transactions on Networking, 10(2):272–286, Apr 2002.
[7] A. A. Lazar and N. Semret. Design and analysis of the
progressive second bid auction for network bandwidth
sharing. Telecommunication Systems – Special Issue
on Network Economics, 1999.
[8] P. Maillé and B. Tuffin. Multi-bid auctions for
7. REFERENCES
[1] T. Alpcan and T. Basar. A utility-based congestion
control scheme for internet-style networks with delay.
Proceedings of IEEE InfoCom, Apr 2003.
[2] A. Delenda. Mécanismes dèncheres pour le partage de
ressources télécom. Technical Report Tech Rep 7831,
[9]
[10]
[11]
[12]
[13]
bandwidth allocation in communication networks. In
Proceedings of IEEE Infocom, April 2004.
M. Mandjes. Pricing strategies under heterogeneous
service requirements. Proceedings of the IEEE
Infocom, Mar 2003.
P. Marbach. Priority service and max-min fairness.
IEEE/ACM Transactions on Networking,
11(5):733–746, Oct 2003.
P. Marbach. Analysis of a static pricing scheme for
priority services. IEEE/ACM Transactions on
Networking, 12(2):312–325, Apr 2004.
J. Mo and J. Walrand. Fair end-to-end window-based
congestion control. IEEE/ACM Transactions on
Networking, 8(5):556–567, Oct 2000.
J. Shu and P. Varaiya. Pricing network services.
Proceedings of the IEEE Infocom, Mar 2003.
Pi (x) is an convex increasing function of x, and Pi (0) = 1,
Pi (C −θi −γi ) > 1. So we can choose any non-negative price
value below the upper bound found above. Apart from this,
we want to ensure that N Ui decreases with λi when λi is
greater than (C − θi ). For this to happen,
dN Ui
≤0
dλi
when λi > (C − θi ). Let λi = C − θi + δ, for some δ > 0.
Then, by definition
N Ui
=
Ui ((C − θi + δ)(1 − β)) − πi Pi (C − θi + δ − γi )
where
β
=
=
APPENDIX
Proof of Lemma 3.1
As long as user i stays below her contracted rate γi , there
is no congestion in the link and hence zero packet dropping
probability. Also, the price charged by the service provider
is proportional to the fraction of link capacity utilized by
the user. So the net utility (N Ui ) is,
λ i
N Ui = Ui (λi ) − Di (γi − λi ) −
πi
γi
User i has incentive to increase her rate if and only if her
net utility increases with increase in λi . That is,
dN Ui
dλ
πi
i
0
0
Ui (λi ) + Di (γi − λi ) −
γi
≥
0
≥
0
For N Ui to keep increasing till user i reaches γi , it is sufficient to have
πi
≤
γi (Ui0 (γi ) + lim Di0 (x))
x→0+
This condition is also necessary because if πi > γi (Ui0 (γi ) +
Ui
limx→0+ Di0 (x)), then there exists a λi < γi such that dN
<
dλi
0
0. This can be seen as follows. If πi > γi (Ui (γi )+limx→0+ Di0
(x)), then ( πγii − Ui0 (γi )) > limx→0+ Di0 (x). Also,
π
dN Ui
i
= Di0 (γi − λi ) −
− Ui0 (γi )
dλi
γi
When λi is sufficiently close to γi , Di0 (γi − λi ) drops beUi
low the fixed quantity ( πγii − Ui0 (γi )). At this point, dN
dλi
becomes negative.
Since the total traffic from users j ∈ {1, 2, . . . , N }, j 6= i,
is less than their aggregate contracted rate, user i should
have the incentive to increase her rate further till the link
is fully utilized, i.e., till λi is equal to (C − θi ). When
λi ∈ [γi , (C − θi )], N Ui is simply Ui (λi ) − πi which is an
increasing function of λi . This in turn gives user i every
reason to increase λi in this range.
When λi becomes more than (C − θi ), the link gets congested. We would like to ensure that user i has no incentive
to increase her rate beyond (C −θi ). It can be observed that
as long as we choose πi ≥ 0 and Pi (C − θi − γi ) ≥ 1 the
net utility function for user i at a rate just above (C − θi )
is less than the net utility function at (C − θi ). Since
(λi + θi − C)
(λi + θi )
δ
(C + δ)
So, the requirement becomes
(C − θ + δ)C d
i
− πi Pi (C − θi + δ − γi )
Ui
dδ
(C + δ)
!
≤0
On simplification, the above gives the following condition on
πi .
Cθi
1
0 (C − θi + δ)C
πi ≥
U
× 0
i
(C + δ)2
(C + δ)
Pi (C − θi − γi + δ)
Because we want the lower bound to hold for every δ > 0, we
now take the supremum of the lower bound over all δ > 0.
This yields
θ U 0 (C − θ )
i
i
i
πi ≥
C Pi0 (C − θi − γi )
This proves that the lower bound on πi is sufficient. Necessity is shown
0 be a given small number.
as follows. Let > Ui0 (C−θi )
θi
If we take
− as the lower bound, then
C P 0 (C−θi −γi )
i
simple algebra shows that there exists a δ > 0 such that
dN Ui
> 0. This contradicts our requirement and concludes
dλi
the proof.
2
Proof of Lemma 3.2
There is no congestion in the link and no packets are
dropped unless user i overshoots her contracted rate. The
price charged by the service provider is proportional to the
link capacity utilized by the user when she is below her contracted rate. The expression for net utility is,
λ i
πi
N Ui = Ui (λi ) − Di (γi − λi ) −
γi
Following similar algebra as done in the proof of Lemma 3.1
we can show that the necessary and sufficient condition for
user i to increase her rate up to γi is
πi ≤ γi (Ui0 (γi ) + lim Di0 (x))
x→0+
Since the total traffic from users j ∈ {1, 2, . . . , N }, j 6= i, is
equal to their aggregate contracted rate, once user i reaches
her contracted rate, the link is fully utilized. So, the user
should have no more incentive to increase her rate any further. From the definition of net utility function it is clear
that when πi ≥ 0 and Pi (0) ≥ 1, N Ui at λi = γi is greater
than N Ui at λi > γi . And for N Ui to be a decreasing with
λi once λi > γi ,
C(γi + δ) d
− πi Pi (δ)
≤ 0
Ui
dδ
(C + δ)
This can be reduced to
πi
≥
=
Ui0 (C − θi )
since (C − θi ) = γi in this case. Because we want the lower
bound to hold for every δ > 0, we now take the supremum
of the lower bound over all δ > 0. This gives
C − γ Ui0 (γi )
i
πi ≥
C
limx→0+ Pi0 (x)
This proves that the lower bound on πi is sufficient. The
necessity of the lower bound can be proved in exactly the
same way as done in the case of previous Lemma.
2
Proof of Lemma 3.3
Since the total traffic from users other than i is more than
their aggregate contracted rates, user i has room to increase
her rate only up to (C − θi ) without causing congestion in
the link. This is possible if,
λ d
i
πi
Ui (λi ) − Di (γi − λi ) −
≥ 0
dλi
γi
This N Ui should not cease to increase till λi reaches (C −θi ).
We can simplify the above to get the following sufficient
condition on πi .
(7)
Since (C − θi ) < γi , we want user i to increase her rate
further up to her rightful share of γi . So, for δ > 0,
(C − θi + δ)C d
− Di (γi − (C − θi + δ))
Ui
dδ
(C + δ)
C − θ + δ i
−
πi ≥ 0
γi
which reduces to
yθi
Ui0 ((C − θi + δ)y) + Di0 (γi − C + θi − δ)
πi ≤ γ i
(C + δ)
C
where y = ( C+δ
). User i should be allowed to go only up to
γi . So, δ cannot exceed γi − (C − θi ). This leads to further
simplification of the condition on πi
γC Cθi
i
0
0
+ lim Di (x)
(8)
Ui
πi ≤ γ i
x→0+
(γi + θi )2
γi + θ i
To prove that the upper bound of Equation 8 is less than
the upper bound of Equation 7 we proceed as follows. Since,
Di (x) is a convex increasing function of x, and θi > (C −γi ),
x→0+
θi (C − θi − γi )
θi (C − θi − γi ) + γi C
(C − θi )
C(C − γi )
(γi + δ)C
Ui0
(C + δ)2 Pi0 (δ)
(C + δ)
(C
− θi + δ)C
C(C − γi )
0
U
i
(C + δ)2 Pi0 (δ)
(C + δ)
Di0 (γi − C + θi ) > lim Di0 (x)
θi
C − θi − γi
(C − θi )(θi + γi )
πi ≤ γi (Ui0 (C − θi ) + Di0 (γi − C + θi ))
Also,
> (C − γi )
< 0
< 0
< γi C
< γi C
Cγi
<
(θi + γi )
Cγi
> Ui0
θi + γ i
i
and (γ Cθ
2 < 1. This proves that Equation 8 is a subset
i +θi )
of Equation 7.
Now, N Ui at λi = γi should exceed N Ui at λi > γi and
N Ui should keep reducing with λi when λi ∈ (γi , ∞). Mathematically, for a small δ > 0,
(γi + δ)C
γi C
Ui
− πi ≥ U i
− πi Pi (δ)
γi + θ i
γi + δ + θ i
which can be ensured if πi ≥ 0 and Pi (0) ≥ 1. Also,
(γi + δ)C d
− πi Pi (δ) ≤ 0
Ui
dδ
γi + δ + θ i
Simplification of this results in the following lower bound on
πi .
γC Cθi
i
πi ≥
Ui0
0
2
(γi + θi ) limx→0+ Pi (x)
γi + θ i
The necessity of both upper bound and lower bound can
be proved by doing similar algebra as has been done in
Lemma 3.1.
2